Cloud Computing Forensics Investigation Problems, Solutions and SDN
VerifiedAdded on 2022/08/15
|11
|2391
|12
Report
AI Summary
This report delves into the complexities of performing a forensics investigation within cloud computing environments. It identifies key challenges such as data volatility, physical inaccessibility of hardware, integrity and stability of evidence, internal staffing requirements, chain of custody maintenance, bandwidth limitations, and the lack of specialized forensic tools. The report also discusses the impact of the volume of data stored and the network architecture on investigations, contrasting peer-to-peer and client/server models. Furthermore, it explores the relationship between virtualizing the desktop and back-end infrastructure, and the roles of Software-Defined Networking (SDN) and Intent-Based Networking (IBN) in enhancing network management and automation, crucial for addressing the dynamic nature of cloud environments. The report also examines the evolution of SDN, its benefits, and the IBN's functionalities in the cloud computing industry.

1
Problem of Performing a Forensics Investigation Involving Cloud Computing Resources
Name:
Course
Problem of Performing a Forensics Investigation Involving Cloud Computing Resources
Name:
Course
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
1 Introduction
Cloud computing is one of the most important topics in the field of information technology in current
time thus its popularity is rising very fast Computing through cloud has play major roles in the
organization growth. Companies migrate their services to the cloud for easy accessibility of the
services. Hence it has become a major trend in the modern industry of computing in the cloud.
Through cloud computing a space of storage for companies is created for easy carrying of their
activities in the internet. The forensic investigators use this platform as a major point for evidence
acquisition, imaging and data analysis of the organization in necessary for any organization in order to
thrive will in cloud computing industry. Need to do more research especially on the forensic problems
and the necessary solution necessary
Cloud forensic problems
Major problem regarding to cloud computing occurs in the public operations of cloud more than in the
private architecture of computing in the clouds. This is because through government major investments
are made in cloud computing (Duan et al, 2015).
Cloud Forensic Solutions
Volatility of data
The information stored in virtual machine is lost in most cases when the virtual machine is rebooted or
turned off by the clients. This shows how relevant evidence of processes and registry entries and the
internet files temporary stored can be lost during this process. In case of eternal adversary attracts to
adversary machine no continues synchronization will occur. After completion of the adversary attack,
the adversary can end up shutting down the virtual machine leading to the loss of volatile data in the
virtual machine. This will occur severally if the necessary actions will not be taken into place.
The given places of information accessibility can cause a major challenge on the hence need Alt-
Sahalia (2012).
1 Introduction
Cloud computing is one of the most important topics in the field of information technology in current
time thus its popularity is rising very fast Computing through cloud has play major roles in the
organization growth. Companies migrate their services to the cloud for easy accessibility of the
services. Hence it has become a major trend in the modern industry of computing in the cloud.
Through cloud computing a space of storage for companies is created for easy carrying of their
activities in the internet. The forensic investigators use this platform as a major point for evidence
acquisition, imaging and data analysis of the organization in necessary for any organization in order to
thrive will in cloud computing industry. Need to do more research especially on the forensic problems
and the necessary solution necessary
Cloud forensic problems
Major problem regarding to cloud computing occurs in the public operations of cloud more than in the
private architecture of computing in the clouds. This is because through government major investments
are made in cloud computing (Duan et al, 2015).
Cloud Forensic Solutions
Volatility of data
The information stored in virtual machine is lost in most cases when the virtual machine is rebooted or
turned off by the clients. This shows how relevant evidence of processes and registry entries and the
internet files temporary stored can be lost during this process. In case of eternal adversary attracts to
adversary machine no continues synchronization will occur. After completion of the adversary attack,
the adversary can end up shutting down the virtual machine leading to the loss of volatile data in the
virtual machine. This will occur severally if the necessary actions will not be taken into place.
The given places of information accessibility can cause a major challenge on the hence need Alt-
Sahalia (2012).

3
Physical inaccessibility
The geographic distribution of the hardware devices is challenging in a cloud environment, data
location. The established digital forensic procedures and tools assume that the hardware fact is
physically accessible. In cloud forensics, however, the fact that the devices to be purchased will reside
on different physical devices that are used by multiple cloud consumers and that the device
configuration is static. Makes any physical acquisition nearly impossible for CSP. There is also no
possibility to seize the data-containing hardware, because usually jurisdictions are stored in distributed
systems. This challenge does not apply to any type of globally distributed corporation, where all
resources are located at the premises of the company.
In the event of a crash, all machines can be easily accessed because they belong to private p
remises where the institutions have full control. The challenge extends to all three versions in
operations.
Integrity and stability
In cloud investigation for IaaS, PaaS, and SaaS, the integrity preservation reliability of evidence is
important. In our effort, we will protect data in multi-jurisdictional contexts, a daunting challenge,
without violating any rule. If the dignity is not protected then the evidence will not be admissible to the
court. Dignity will add additional confidence to cloud forensics that is appropriate for an investigator
parties to accredit to verify in question. A process to be trusted by the courts was created by the
integrity testing authority; otherwise it would be difficult to justify using them as a source for
verification of integrity. The transitory existence and dedicated explanation of the Cloud is also difficult
(Nasreidin et al, 2015).
Internal staffing
The problem affects four rates on all three-service models, from description to protection. A number of
people have to be involved as a team to carry out a cloud forensics investigation. The team should be
Physical inaccessibility
The geographic distribution of the hardware devices is challenging in a cloud environment, data
location. The established digital forensic procedures and tools assume that the hardware fact is
physically accessible. In cloud forensics, however, the fact that the devices to be purchased will reside
on different physical devices that are used by multiple cloud consumers and that the device
configuration is static. Makes any physical acquisition nearly impossible for CSP. There is also no
possibility to seize the data-containing hardware, because usually jurisdictions are stored in distributed
systems. This challenge does not apply to any type of globally distributed corporation, where all
resources are located at the premises of the company.
In the event of a crash, all machines can be easily accessed because they belong to private p
remises where the institutions have full control. The challenge extends to all three versions in
operations.
Integrity and stability
In cloud investigation for IaaS, PaaS, and SaaS, the integrity preservation reliability of evidence is
important. In our effort, we will protect data in multi-jurisdictional contexts, a daunting challenge,
without violating any rule. If the dignity is not protected then the evidence will not be admissible to the
court. Dignity will add additional confidence to cloud forensics that is appropriate for an investigator
parties to accredit to verify in question. A process to be trusted by the courts was created by the
integrity testing authority; otherwise it would be difficult to justify using them as a source for
verification of integrity. The transitory existence and dedicated explanation of the Cloud is also difficult
(Nasreidin et al, 2015).
Internal staffing
The problem affects four rates on all three-service models, from description to protection. A number of
people have to be involved as a team to carry out a cloud forensics investigation. The team should be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
composed of professionals with technical knowledge, legal counsel and qualified professional workers
with deep knowledge of new technology and talents.
Chain of custody
The most important thing to present evidence in a court of law is to ensure that throughout the process
the chain of evidence custody is maintained in security forensics. Any custody interruption chain,
questionable facts. The gathering staff qualified to retain unique forensic techniques in evidence. The
chain of custody will be upheld in this situation. For a case in court, the investigators the chain of
custody should contain information who collected the evidence, how and where the evidence was
collected, how the evidence was stored, and who accessed the evidence (Prayudi & Sn, 2015).
Bandwidth limitation
The volume is increasing rapidly resulting to of evidence. In the previous paragraph, we referred on the
VM imaging in IaaS model. In order to collect data, investigators need to download the VM instance's
image. The bandwidth must be taken into consideration are downloading these large images.
Lack of forensic tools
The process of analyzing data in the cloud usually requires use of the forensic tools during the work.
The tools used for cloud investigation are used during the process of forensic investigation and during
cloud design investigation. Since they are not available the devises are not accessed physical and many
systems are distributed the SaaS model, PaaS model and LaaS model cannot be covered fully during
the investigation
Volume of data
The information stored In the CSP center is very large hence. This amount of information can bring
trouble during process of searching relevant digital data in an organization. The results of this
composed of professionals with technical knowledge, legal counsel and qualified professional workers
with deep knowledge of new technology and talents.
Chain of custody
The most important thing to present evidence in a court of law is to ensure that throughout the process
the chain of evidence custody is maintained in security forensics. Any custody interruption chain,
questionable facts. The gathering staff qualified to retain unique forensic techniques in evidence. The
chain of custody will be upheld in this situation. For a case in court, the investigators the chain of
custody should contain information who collected the evidence, how and where the evidence was
collected, how the evidence was stored, and who accessed the evidence (Prayudi & Sn, 2015).
Bandwidth limitation
The volume is increasing rapidly resulting to of evidence. In the previous paragraph, we referred on the
VM imaging in IaaS model. In order to collect data, investigators need to download the VM instance's
image. The bandwidth must be taken into consideration are downloading these large images.
Lack of forensic tools
The process of analyzing data in the cloud usually requires use of the forensic tools during the work.
The tools used for cloud investigation are used during the process of forensic investigation and during
cloud design investigation. Since they are not available the devises are not accessed physical and many
systems are distributed the SaaS model, PaaS model and LaaS model cannot be covered fully during
the investigation
Volume of data
The information stored In the CSP center is very large hence. This amount of information can bring
trouble during process of searching relevant digital data in an organization. The results of this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
investigation play a major role in the analysis of relevant evidence digital evidence. Appropriate
features are developed during this process to enable process of cloud computing to be effective
Network architecture
This is the physical and logical design which refers to the software, hardware, protocols and the media
of transmission of data. In other terms it refers to how tasks are allocated among these computers. The
widely used network architecture are peer to peer and client/server (Varior et al,2016).
In peer-to-peer network task are allocated to each device on the network hence in-case one system fails
the rest will keep functioning while client/server network the sever is centralized hence if it fails then
the entire system is compromised. Its commonly used and oldest among the architecture of the
network. Peer to peer communication is also easy to set up
Peer-to-peer Architecture
In this architecture, task is allocated to every device on the network. There is no real hierarchy in this
network since all computers are considered equal and all have the same abilities to use the resources
available on that particular network. Instead of having a central server which would act as the shared
drive, each computer that's connected to this network would act as the sever for the files stored in it.
investigation play a major role in the analysis of relevant evidence digital evidence. Appropriate
features are developed during this process to enable process of cloud computing to be effective
Network architecture
This is the physical and logical design which refers to the software, hardware, protocols and the media
of transmission of data. In other terms it refers to how tasks are allocated among these computers. The
widely used network architecture are peer to peer and client/server (Varior et al,2016).
In peer-to-peer network task are allocated to each device on the network hence in-case one system fails
the rest will keep functioning while client/server network the sever is centralized hence if it fails then
the entire system is compromised. Its commonly used and oldest among the architecture of the
network. Peer to peer communication is also easy to set up
Peer-to-peer Architecture
In this architecture, task is allocated to every device on the network. There is no real hierarchy in this
network since all computers are considered equal and all have the same abilities to use the resources
available on that particular network. Instead of having a central server which would act as the shared
drive, each computer that's connected to this network would act as the sever for the files stored in it.

6
resource is shared among equals in peer-to-peer network
Pros of a peer-to-peer network
1. Its less costly since it does not require a dedicated server
2. If one of the computers stop working, the rest of the computer connected in the same network will
continue working
3. Installation and setup is quite easy because of the built-in support in modern operating systems
cons of peer-to-peer network
1. Security and backup will have to be done in each and every computer
2. As the number of computers increase on P2P network, the performance, security and access become
a very big problem.
resource is shared among equals in peer-to-peer network
Pros of a peer-to-peer network
1. Its less costly since it does not require a dedicated server
2. If one of the computers stop working, the rest of the computer connected in the same network will
continue working
3. Installation and setup is quite easy because of the built-in support in modern operating systems
cons of peer-to-peer network
1. Security and backup will have to be done in each and every computer
2. As the number of computers increase on P2P network, the performance, security and access become
a very big problem.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
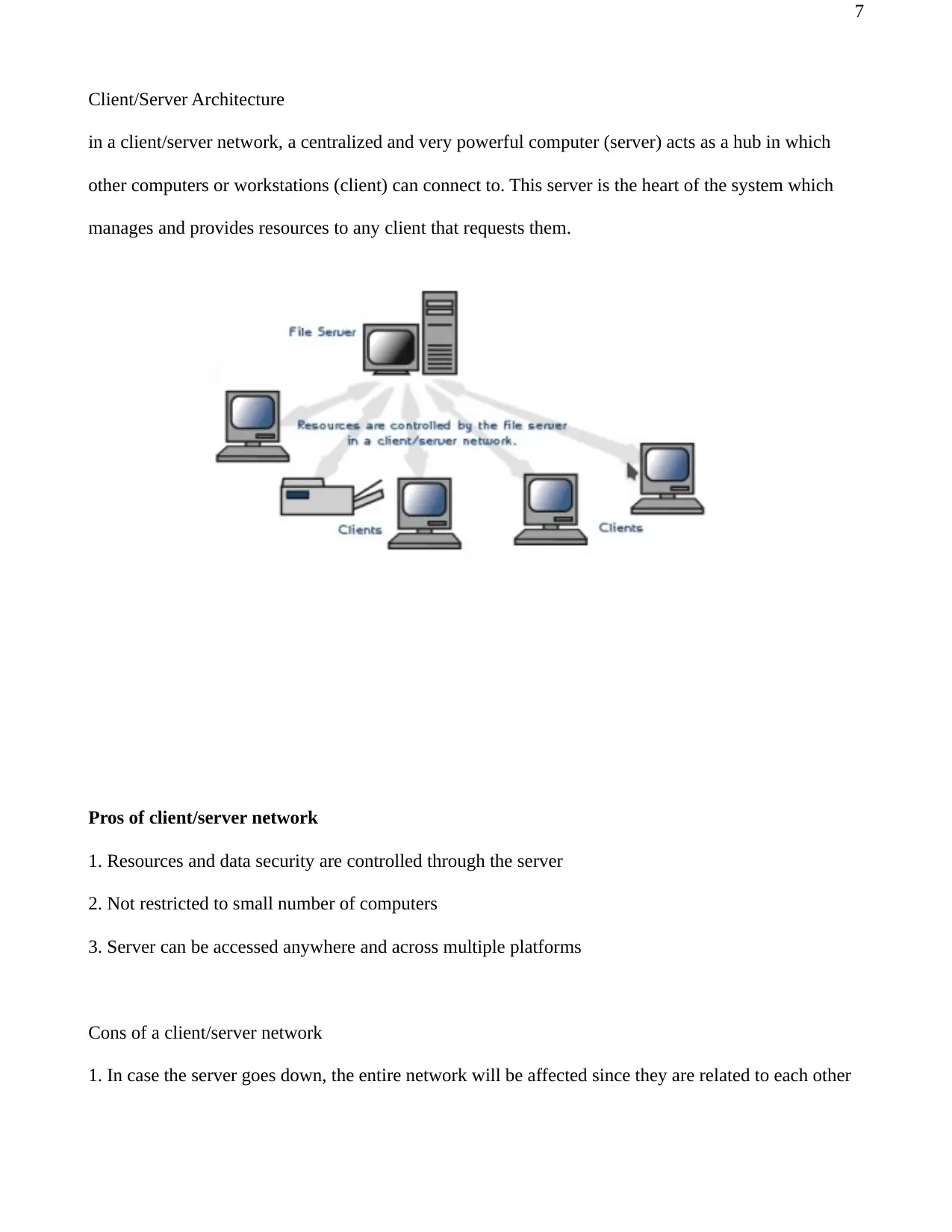
Client/Server Architecture
in a client/server network, a centralized and very powerful computer (server) acts as a hub in which
other computers or workstations (client) can connect to. This server is the heart of the system which
manages and provides resources to any client that requests them.
Pros of client/server network
1. Resources and data security are controlled through the server
2. Not restricted to small number of computers
3. Server can be accessed anywhere and across multiple platforms
Cons of a client/server network
1. In case the server goes down, the entire network will be affected since they are related to each other
Client/Server Architecture
in a client/server network, a centralized and very powerful computer (server) acts as a hub in which
other computers or workstations (client) can connect to. This server is the heart of the system which
manages and provides resources to any client that requests them.
Pros of client/server network
1. Resources and data security are controlled through the server
2. Not restricted to small number of computers
3. Server can be accessed anywhere and across multiple platforms
Cons of a client/server network
1. In case the server goes down, the entire network will be affected since they are related to each other
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
2. Can become very costly due to the need of a server as well as networking devices such as hubs,
routers and switches
3. Technical staff are needed to maintain and ensure network functions efficiently.
Relation between virtualizing the desktop and back-end infrastructure
Virtualizing the desktop reduce on cost by running fewer servers while back-end infrastructure can
comprise a single host or can be distributed over a number of machines available in the local network
or in a wide area network. The physical placement of the back-end system depends on the scales of the
system Sareen (2013).
How SDN and IBN are related
They share a similar principle that is using software to run the network while shifting away the focus
on hardware facilities. SDN is very popular among cloud service providers but this popularity has not
yet tippled in the sector that relies on automation of network. Manual input of command-line interface
for any needed configuration to network courses delays in responsiveness and indirectly or directly
hinder competitiveness. This is where IBN comes in. Just like SDN, IBN offers an abstraction layer for
the administrator to implement policy and instruction across all the physical hardware within the
network infrastructure hence no more manual configuration. Besides the virtualization nature like SDN,
IBN is more oriented to the translation and implementation which are essential element for automated
networking (Aziz et al, 2015).
2. Can become very costly due to the need of a server as well as networking devices such as hubs,
routers and switches
3. Technical staff are needed to maintain and ensure network functions efficiently.
Relation between virtualizing the desktop and back-end infrastructure
Virtualizing the desktop reduce on cost by running fewer servers while back-end infrastructure can
comprise a single host or can be distributed over a number of machines available in the local network
or in a wide area network. The physical placement of the back-end system depends on the scales of the
system Sareen (2013).
How SDN and IBN are related
They share a similar principle that is using software to run the network while shifting away the focus
on hardware facilities. SDN is very popular among cloud service providers but this popularity has not
yet tippled in the sector that relies on automation of network. Manual input of command-line interface
for any needed configuration to network courses delays in responsiveness and indirectly or directly
hinder competitiveness. This is where IBN comes in. Just like SDN, IBN offers an abstraction layer for
the administrator to implement policy and instruction across all the physical hardware within the
network infrastructure hence no more manual configuration. Besides the virtualization nature like SDN,
IBN is more oriented to the translation and implementation which are essential element for automated
networking (Aziz et al, 2015).

9
3. Introduction to software-defined networking (SDN)
This is a network management technique that allows for dynamic, algorithmically efficient network
configuration to enhance network performance and management, making it more like cloud computing
than conventional network management. Software-defined networking that vastly simplifies the static
nature of traditional networking while allowing further flexibility and troubleshoot the existing
network. SDN centralizes network knowledge in one part of the network by disassociating the
transmission process from the control plane the command plane comprises of one or several controllers
perceived to be the brains of the SDN infrastructure where the entire intelligence becomes
incorporated. Furthermore, when it comes to security, intelligence centralization has its own
disadvantages scalability and elasticity being SDN's main issue Jane (2013).
Software-define networking was commonly the open flow protocol for remote communication with
network plane elements for of determining of network packets across network switches since the
latter’s emergence in 2011. Since 2012 open flow is no longer an exclusive solution for many
companies, they added proprietary techniques. This technique includes Open Network Environment,
Cisco System and Nocera’s network virtualization platform.
Software-define networking is currently available for industrial control applications that require
extremely fast fail over. A company boasts 100x faster fail over for mission critical processes the
elimination of certain Cyber Vulnerabilities that are traditional network management switches.
3. Introduction to software-defined networking (SDN)
This is a network management technique that allows for dynamic, algorithmically efficient network
configuration to enhance network performance and management, making it more like cloud computing
than conventional network management. Software-defined networking that vastly simplifies the static
nature of traditional networking while allowing further flexibility and troubleshoot the existing
network. SDN centralizes network knowledge in one part of the network by disassociating the
transmission process from the control plane the command plane comprises of one or several controllers
perceived to be the brains of the SDN infrastructure where the entire intelligence becomes
incorporated. Furthermore, when it comes to security, intelligence centralization has its own
disadvantages scalability and elasticity being SDN's main issue Jane (2013).
Software-define networking was commonly the open flow protocol for remote communication with
network plane elements for of determining of network packets across network switches since the
latter’s emergence in 2011. Since 2012 open flow is no longer an exclusive solution for many
companies, they added proprietary techniques. This technique includes Open Network Environment,
Cisco System and Nocera’s network virtualization platform.
Software-define networking is currently available for industrial control applications that require
extremely fast fail over. A company boasts 100x faster fail over for mission critical processes the
elimination of certain Cyber Vulnerabilities that are traditional network management switches.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
Since the users, devices and distributed application have grown in number, it has made the networking
environment become more complex. A hardware-centric manual network is transformed by IBN into
policies that can easily be automated and applied across the network consistently. This is meant to
ensure network continuously adjust network the performance of the network and monitor to help assure
desired business outcomes.
The IBN has built on SDN by use of network controller which acts as the central control point for
network process. Such controllers are crucial for network abstraction that treats network as a whole
integrated. These controllers lead networks from all domains including access cloud, WAN and data
center collaborate and their benefits being extended throughout the enterprise thus help making digital
transformation a reality. The IBN system operates with very functional building blocks deliver intent
support for the IT outcomes any organization needs or the business. Translation: The capture and
translation of intent into policies that can be worked on by the network
Activation: Is the installation of policies across virtual and physical network infrastructure using a
wide automation network.
Assurance: The use of machine learning and analytic to continuously monitor that network so as to
verify that the business outcomes are achieved and desired intent being applied
Since the users, devices and distributed application have grown in number, it has made the networking
environment become more complex. A hardware-centric manual network is transformed by IBN into
policies that can easily be automated and applied across the network consistently. This is meant to
ensure network continuously adjust network the performance of the network and monitor to help assure
desired business outcomes.
The IBN has built on SDN by use of network controller which acts as the central control point for
network process. Such controllers are crucial for network abstraction that treats network as a whole
integrated. These controllers lead networks from all domains including access cloud, WAN and data
center collaborate and their benefits being extended throughout the enterprise thus help making digital
transformation a reality. The IBN system operates with very functional building blocks deliver intent
support for the IT outcomes any organization needs or the business. Translation: The capture and
translation of intent into policies that can be worked on by the network
Activation: Is the installation of policies across virtual and physical network infrastructure using a
wide automation network.
Assurance: The use of machine learning and analytic to continuously monitor that network so as to
verify that the business outcomes are achieved and desired intent being applied
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
References
Azizi, M., Benaini, R., & Mamoun, M. B. (2015). Delay measurement in OpenFlow-enabled MPLS-TP
network. Modern Applied Science, 9(3), 90.
Duan, Y., Fu, G., Zhou, N., Sun, X., Narendra, N. C., & Hu, B. (2015, June). Everything as a service
(XaaS) on the cloud: origins, current and future trends. In 2015 IEEE 8th International
Conference on Cloud Computing (pp. 621-628). IEEE.
Nasreldin, M. M., El-Hennawy, M., Aslan, H. K., & El-Hennawy, A. (2015). Digital forensics evidence
acquisition and chain of custody in cloud computing. International Journal of Computer
Science Issues (IJCSI), 12(1), 153.
Sareen, P. (2013). Cloud computing: types, architecture, applications, concerns, virtualization and role
of it governance in cloud. International Journal of Advanced Research in Computer Science
and Software Engineering, 3(3).
Varior, R. R., Haloi, M., & Wang, G. (2016, October). Gated siamese convolutional neural network
architecture for human re-identification. In European conference on computer vision (pp. 791-
808). Springer, Cham.
References
Azizi, M., Benaini, R., & Mamoun, M. B. (2015). Delay measurement in OpenFlow-enabled MPLS-TP
network. Modern Applied Science, 9(3), 90.
Duan, Y., Fu, G., Zhou, N., Sun, X., Narendra, N. C., & Hu, B. (2015, June). Everything as a service
(XaaS) on the cloud: origins, current and future trends. In 2015 IEEE 8th International
Conference on Cloud Computing (pp. 621-628). IEEE.
Nasreldin, M. M., El-Hennawy, M., Aslan, H. K., & El-Hennawy, A. (2015). Digital forensics evidence
acquisition and chain of custody in cloud computing. International Journal of Computer
Science Issues (IJCSI), 12(1), 153.
Sareen, P. (2013). Cloud computing: types, architecture, applications, concerns, virtualization and role
of it governance in cloud. International Journal of Advanced Research in Computer Science
and Software Engineering, 3(3).
Varior, R. R., Haloi, M., & Wang, G. (2016, October). Gated siamese convolutional neural network
architecture for human re-identification. In European conference on computer vision (pp. 791-
808). Springer, Cham.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





