Data Governance Plan for DAS
VerifiedAdded on 2020/05/11
|26
|5634
|103
AI Summary
This assignment details the creation of a data governance plan for the Digital Asset System (DAS). The plan must address security measures for storing personal identifiable information (PII) of both DAS staff and contractors. It emphasizes training DAS staff to identify and mitigate security risks, maintaining data consistency and integrity, and implementing limited access controls for PII. The plan also references relevant cybersecurity literature and concepts.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: PERSONAL IDENTIFIABLE INFORMATION STRATEGY
Personal Identifiable Information Strategy
Name of Student
Name of University
Personal Identifiable Information Strategy
Name of Student
Name of University
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
1
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
Table of Contents
1. Threat and Risk Assessment.........................................................................................................................................................................2
2. PII strategy proposal for DAS MY License portal.....................................................................................................................................12
3. Protection of Informal digital identity........................................................................................................................................................16
4. Governance of PII and digital identities for users of the portal.................................................................................................................19
4.1. PII and digital identities for the users of My license Portal................................................................................................................20
4.2. Personal and PII data for DAS users of the HR personnel Management Suite...................................................................................21
4.3. Personal and PII data for Contractors..................................................................................................................................................22
4.4. Personal and PII data for users and DAS staffs...................................................................................................................................23
Bibliography:..................................................................................................................................................................................................24
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
Table of Contents
1. Threat and Risk Assessment.........................................................................................................................................................................2
2. PII strategy proposal for DAS MY License portal.....................................................................................................................................12
3. Protection of Informal digital identity........................................................................................................................................................16
4. Governance of PII and digital identities for users of the portal.................................................................................................................19
4.1. PII and digital identities for the users of My license Portal................................................................................................................20
4.2. Personal and PII data for DAS users of the HR personnel Management Suite...................................................................................21
4.3. Personal and PII data for Contractors..................................................................................................................................................22
4.4. Personal and PII data for users and DAS staffs...................................................................................................................................23
Bibliography:..................................................................................................................................................................................................24
2
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
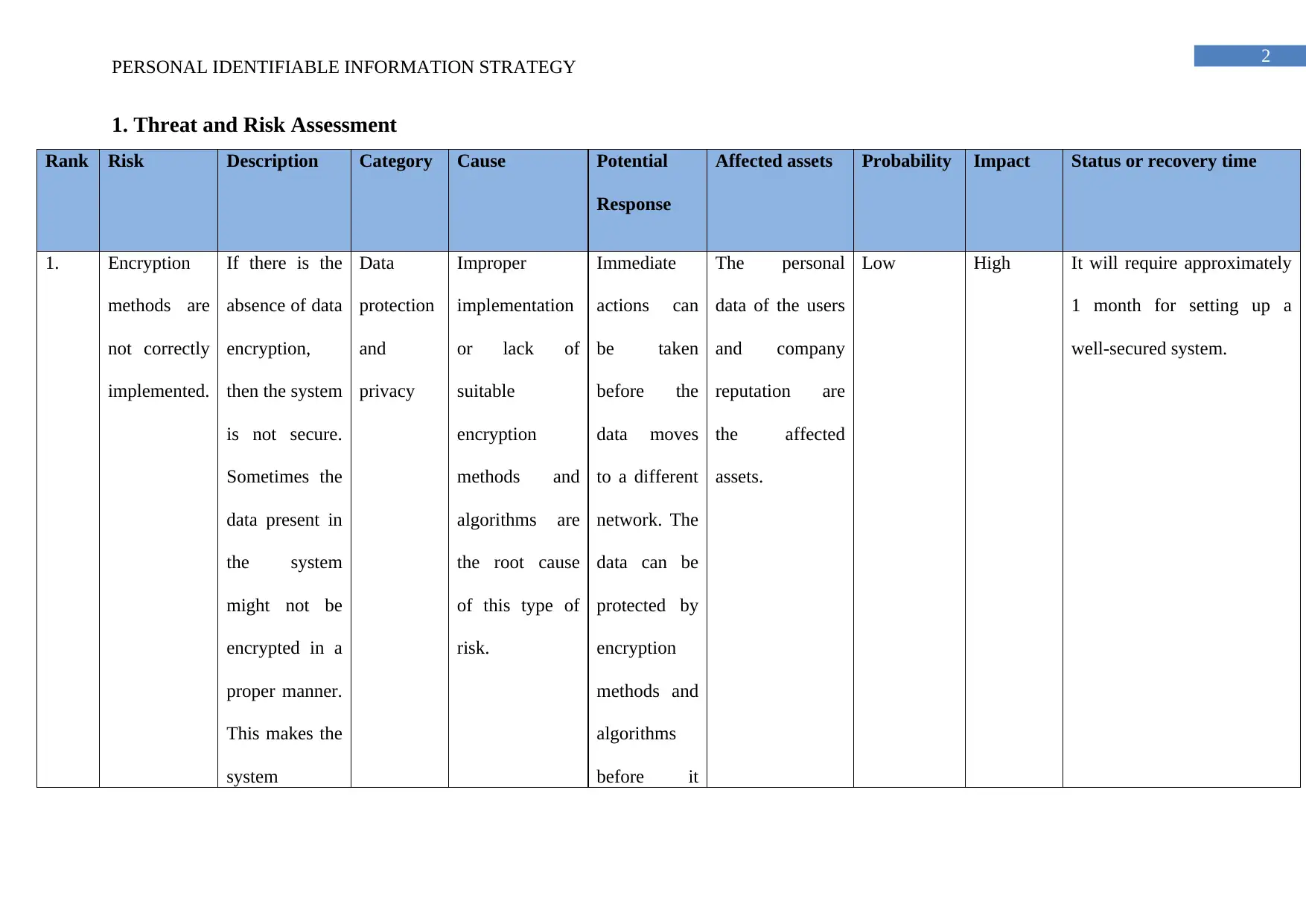
1. Threat and Risk Assessment
Rank Risk Description Category Cause Potential
Response
Affected assets Probability Impact Status or recovery time
1. Encryption
methods are
not correctly
implemented.
If there is the
absence of data
encryption,
then the system
is not secure.
Sometimes the
data present in
the system
might not be
encrypted in a
proper manner.
This makes the
system
Data
protection
and
privacy
Improper
implementation
or lack of
suitable
encryption
methods and
algorithms are
the root cause
of this type of
risk.
Immediate
actions can
be taken
before the
data moves
to a different
network. The
data can be
protected by
encryption
methods and
algorithms
before it
The personal
data of the users
and company
reputation are
the affected
assets.
Low High It will require approximately
1 month for setting up a
well-secured system.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
1. Threat and Risk Assessment
Rank Risk Description Category Cause Potential
Response
Affected assets Probability Impact Status or recovery time
1. Encryption
methods are
not correctly
implemented.
If there is the
absence of data
encryption,
then the system
is not secure.
Sometimes the
data present in
the system
might not be
encrypted in a
proper manner.
This makes the
system
Data
protection
and
privacy
Improper
implementation
or lack of
suitable
encryption
methods and
algorithms are
the root cause
of this type of
risk.
Immediate
actions can
be taken
before the
data moves
to a different
network. The
data can be
protected by
encryption
methods and
algorithms
before it
The personal
data of the users
and company
reputation are
the affected
assets.
Low High It will require approximately
1 month for setting up a
well-secured system.
3
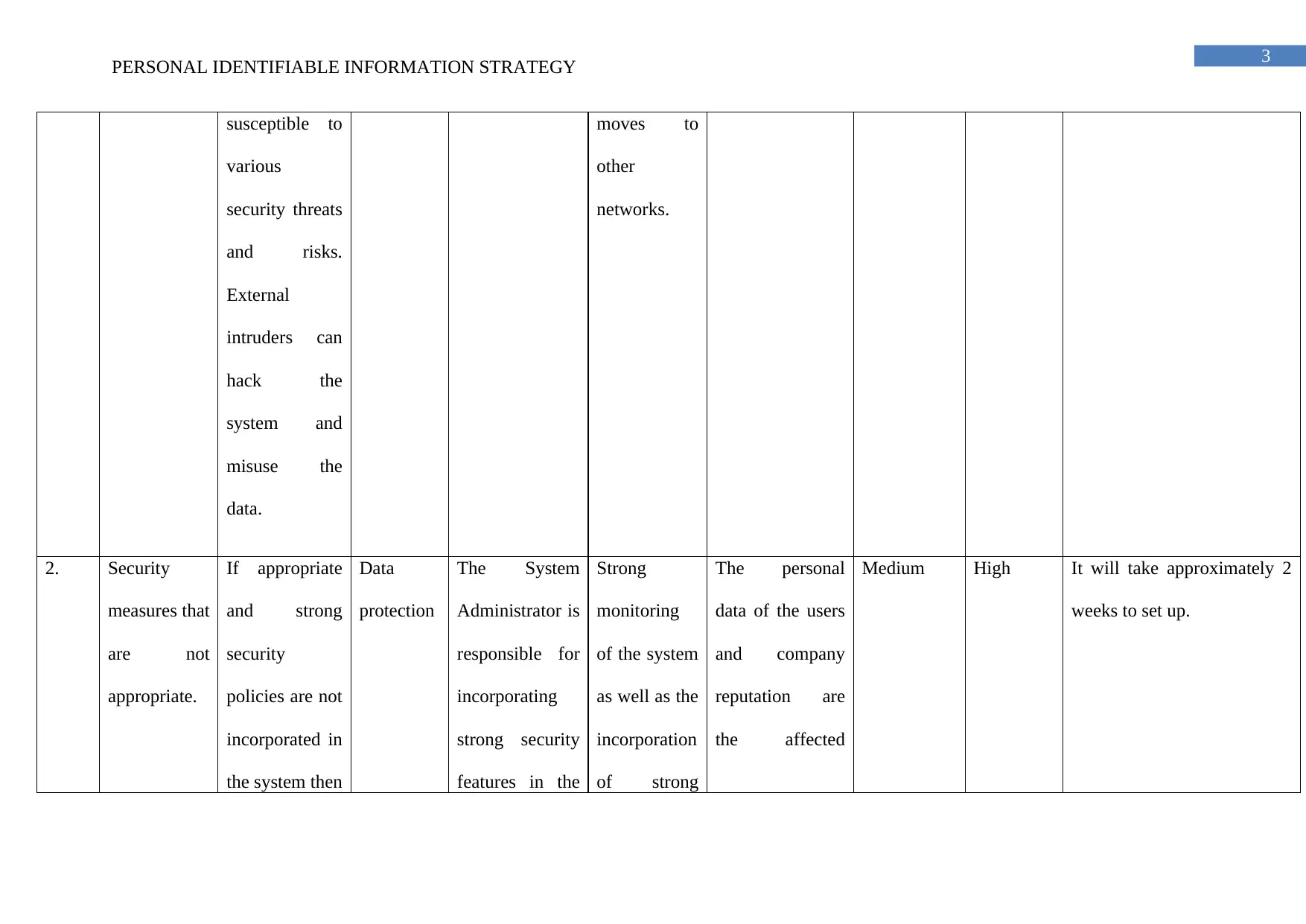
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
susceptible to
various
security threats
and risks.
External
intruders can
hack the
system and
misuse the
data.
moves to
other
networks.
2. Security
measures that
are not
appropriate.
If appropriate
and strong
security
policies are not
incorporated in
the system then
Data
protection
The System
Administrator is
responsible for
incorporating
strong security
features in the
Strong
monitoring
of the system
as well as the
incorporation
of strong
The personal
data of the users
and company
reputation are
the affected
Medium High It will take approximately 2
weeks to set up.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
susceptible to
various
security threats
and risks.
External
intruders can
hack the
system and
misuse the
data.
moves to
other
networks.
2. Security
measures that
are not
appropriate.
If appropriate
and strong
security
policies are not
incorporated in
the system then
Data
protection
The System
Administrator is
responsible for
incorporating
strong security
features in the
Strong
monitoring
of the system
as well as the
incorporation
of strong
The personal
data of the users
and company
reputation are
the affected
Medium High It will take approximately 2
weeks to set up.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
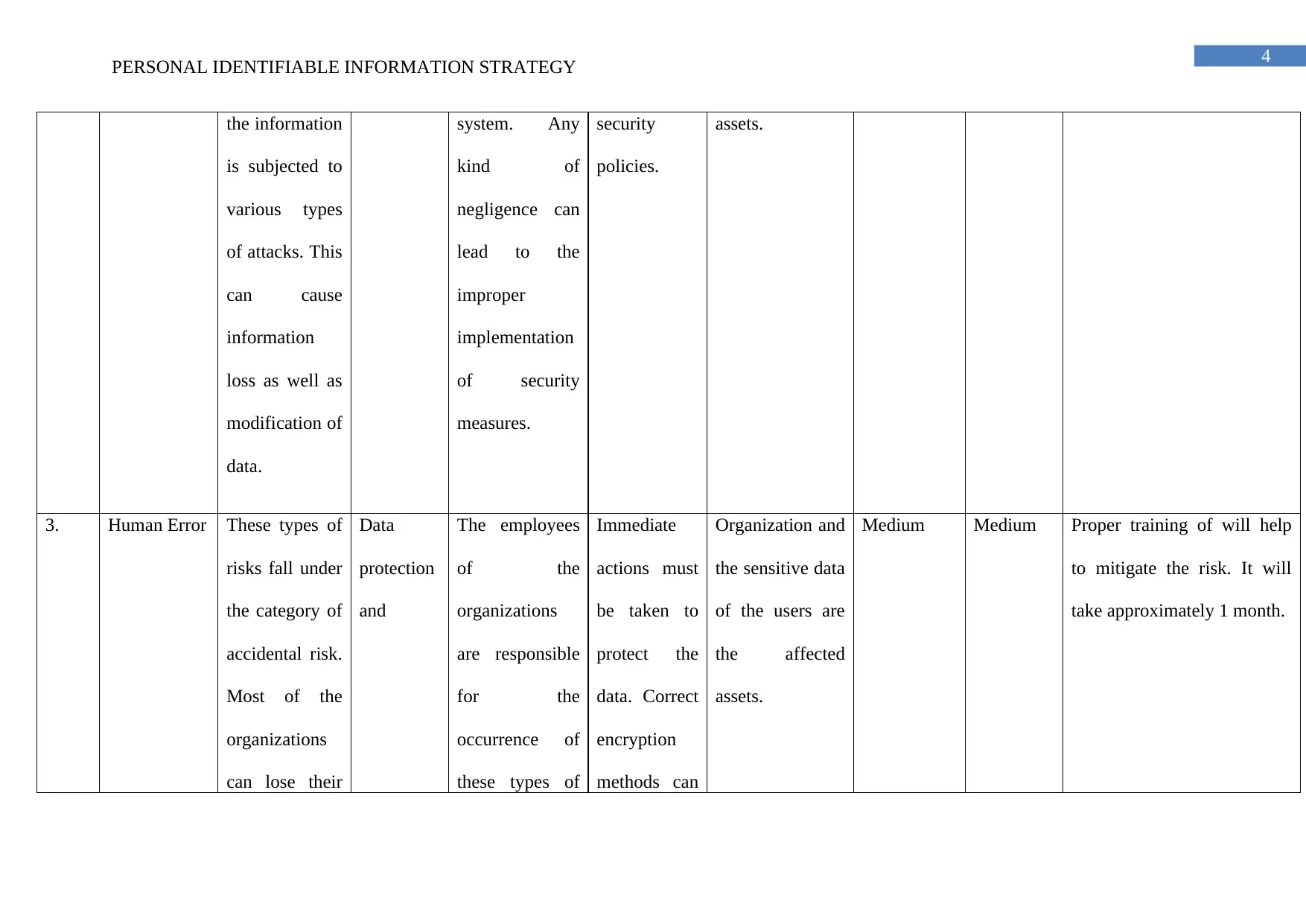
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
the information
is subjected to
various types
of attacks. This
can cause
information
loss as well as
modification of
data.
system. Any
kind of
negligence can
lead to the
improper
implementation
of security
measures.
security
policies.
assets.
3. Human Error These types of
risks fall under
the category of
accidental risk.
Most of the
organizations
can lose their
Data
protection
and
The employees
of the
organizations
are responsible
for the
occurrence of
these types of
Immediate
actions must
be taken to
protect the
data. Correct
encryption
methods can
Organization and
the sensitive data
of the users are
the affected
assets.
Medium Medium Proper training of will help
to mitigate the risk. It will
take approximately 1 month.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
the information
is subjected to
various types
of attacks. This
can cause
information
loss as well as
modification of
data.
system. Any
kind of
negligence can
lead to the
improper
implementation
of security
measures.
security
policies.
assets.
3. Human Error These types of
risks fall under
the category of
accidental risk.
Most of the
organizations
can lose their
Data
protection
and
The employees
of the
organizations
are responsible
for the
occurrence of
these types of
Immediate
actions must
be taken to
protect the
data. Correct
encryption
methods can
Organization and
the sensitive data
of the users are
the affected
assets.
Medium Medium Proper training of will help
to mitigate the risk. It will
take approximately 1 month.
5
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
sensitive
information
because of
human error.
risks. be used for
protecting
the data. The
errors can be
corrected and
rectified after
it has been
detected.
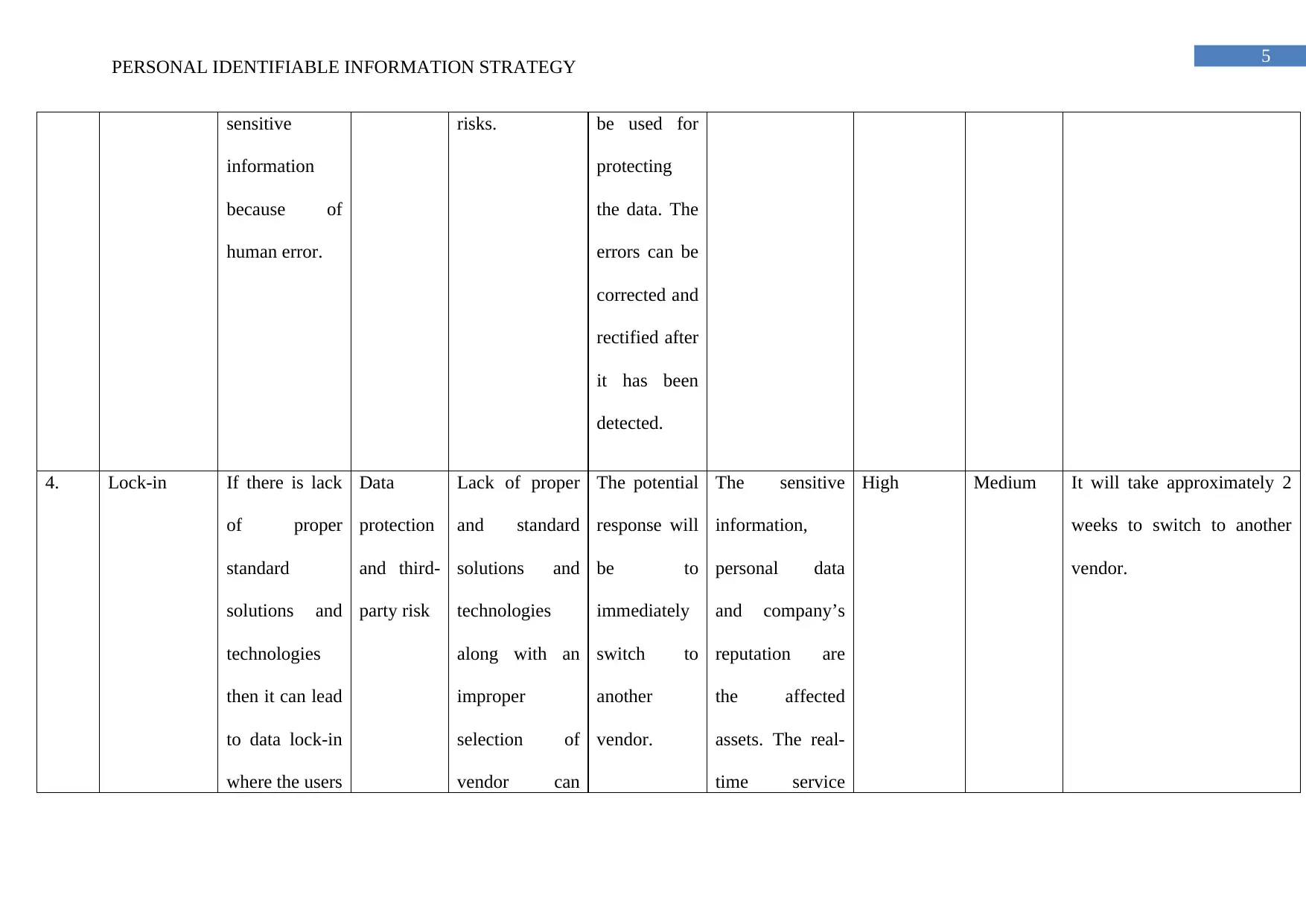
4. Lock-in If there is lack
of proper
standard
solutions and
technologies
then it can lead
to data lock-in
where the users
Data
protection
and third-
party risk
Lack of proper
and standard
solutions and
technologies
along with an
improper
selection of
vendor can
The potential
response will
be to
immediately
switch to
another
vendor.
The sensitive
information,
personal data
and company’s
reputation are
the affected
assets. The real-
time service
High Medium It will take approximately 2
weeks to switch to another
vendor.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
sensitive
information
because of
human error.
risks. be used for
protecting
the data. The
errors can be
corrected and
rectified after
it has been
detected.
4. Lock-in If there is lack
of proper
standard
solutions and
technologies
then it can lead
to data lock-in
where the users
Data
protection
and third-
party risk
Lack of proper
and standard
solutions and
technologies
along with an
improper
selection of
vendor can
The potential
response will
be to
immediately
switch to
another
vendor.
The sensitive
information,
personal data
and company’s
reputation are
the affected
assets. The real-
time service
High Medium It will take approximately 2
weeks to switch to another
vendor.
6
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
get totally
dependent on
the vendors of
the cloud
provider.
cause these
risks.
delivery is also
affected.
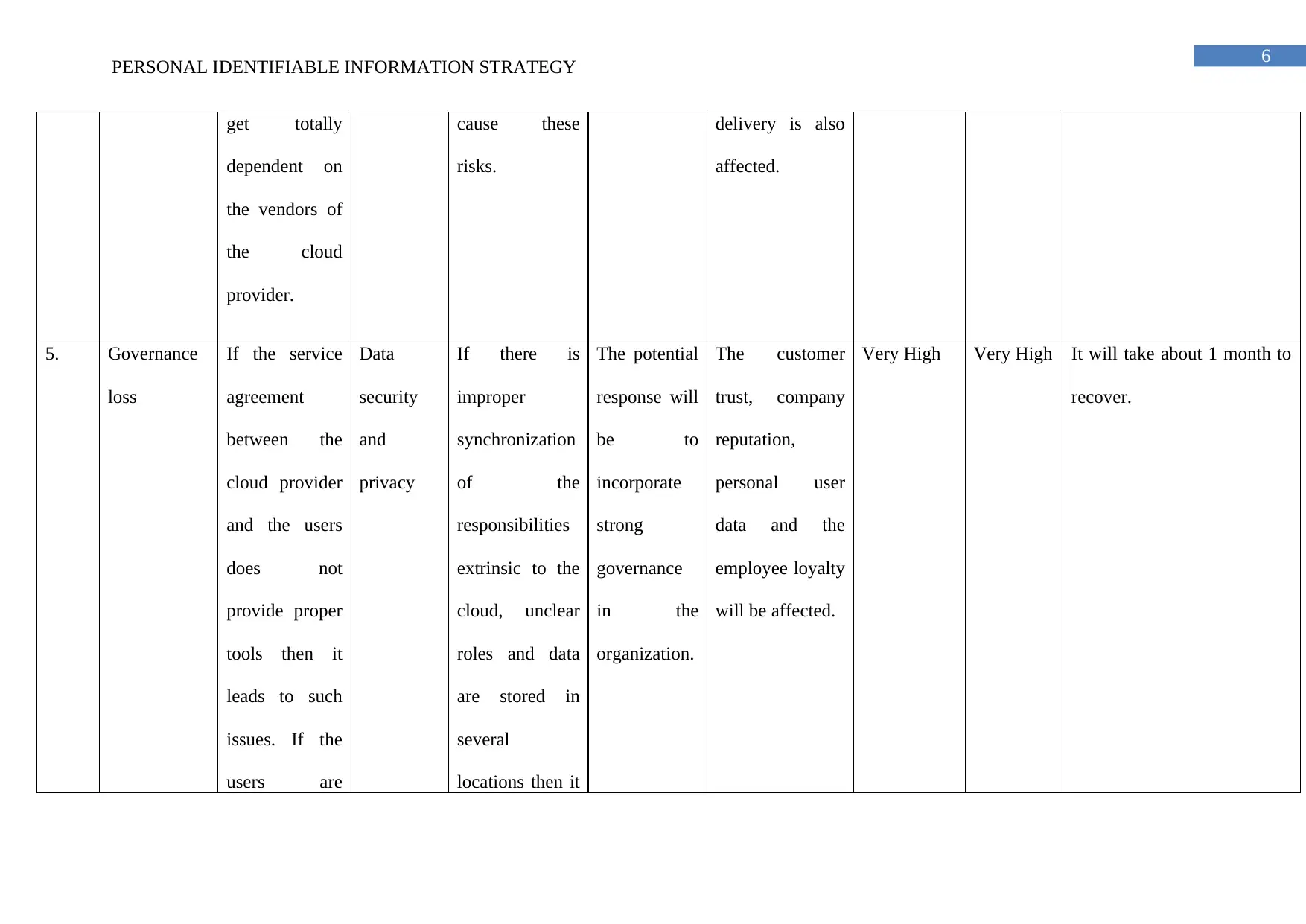
5. Governance
loss
If the service
agreement
between the
cloud provider
and the users
does not
provide proper
tools then it
leads to such
issues. If the
users are
Data
security
and
privacy
If there is
improper
synchronization
of the
responsibilities
extrinsic to the
cloud, unclear
roles and data
are stored in
several
locations then it
The potential
response will
be to
incorporate
strong
governance
in the
organization.
The customer
trust, company
reputation,
personal user
data and the
employee loyalty
will be affected.
Very High Very High It will take about 1 month to
recover.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
get totally
dependent on
the vendors of
the cloud
provider.
cause these
risks.
delivery is also
affected.
5. Governance
loss
If the service
agreement
between the
cloud provider
and the users
does not
provide proper
tools then it
leads to such
issues. If the
users are
Data
security
and
privacy
If there is
improper
synchronization
of the
responsibilities
extrinsic to the
cloud, unclear
roles and data
are stored in
several
locations then it
The potential
response will
be to
incorporate
strong
governance
in the
organization.
The customer
trust, company
reputation,
personal user
data and the
employee loyalty
will be affected.
Very High Very High It will take about 1 month to
recover.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
unable to get
proper and
timely backup
then it leads to
this risk.
leads to loss of
governance.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
unable to get
proper and
timely backup
then it leads to
this risk.
leads to loss of
governance.
8
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
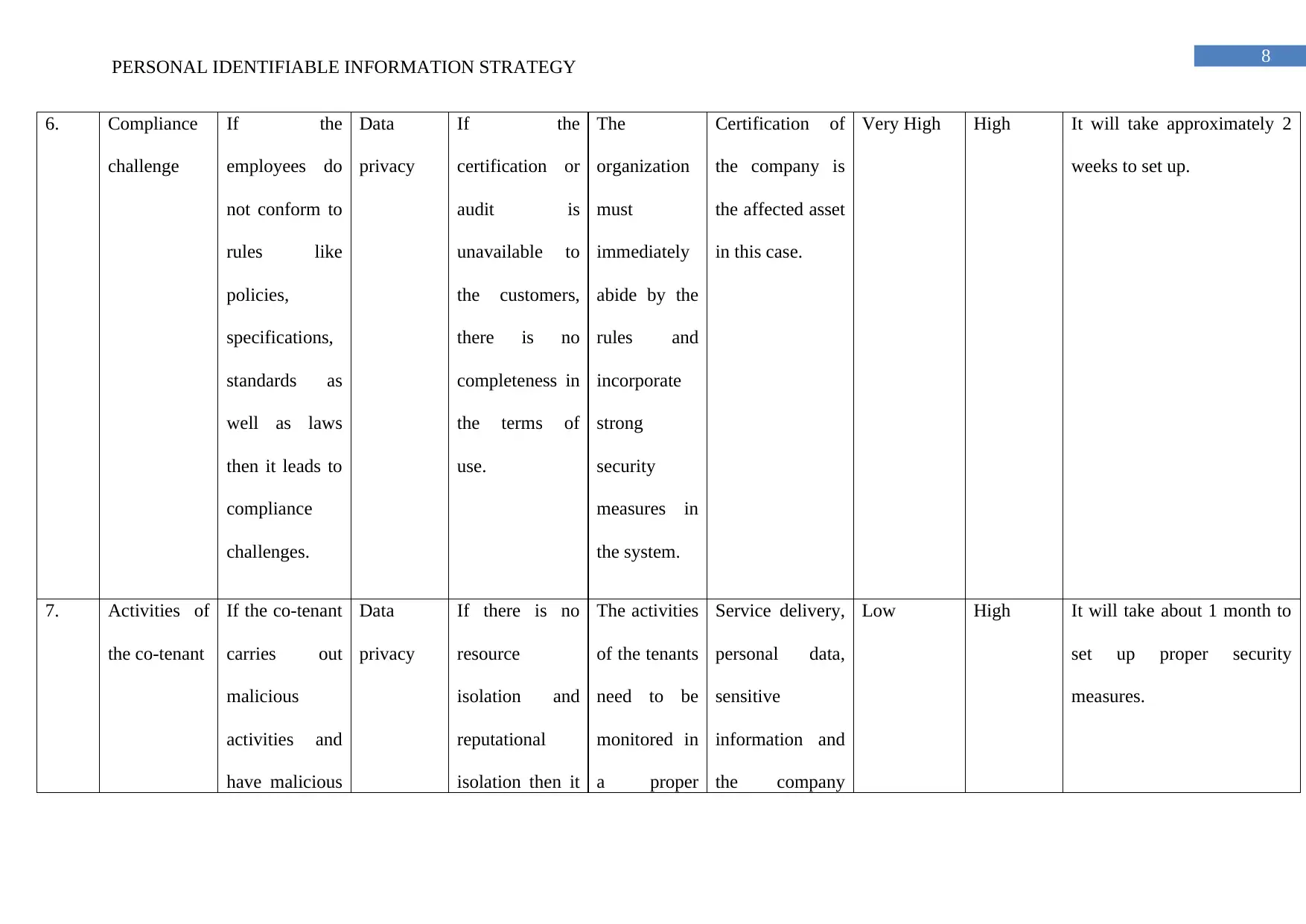
6. Compliance
challenge
If the
employees do
not conform to
rules like
policies,
specifications,
standards as
well as laws
then it leads to
compliance
challenges.
Data
privacy
If the
certification or
audit is
unavailable to
the customers,
there is no
completeness in
the terms of
use.
The
organization
must
immediately
abide by the
rules and
incorporate
strong
security
measures in
the system.
Certification of
the company is
the affected asset
in this case.
Very High High It will take approximately 2
weeks to set up.
7. Activities of
the co-tenant
If the co-tenant
carries out
malicious
activities and
have malicious
Data
privacy
If there is no
resource
isolation and
reputational
isolation then it
The activities
of the tenants
need to be
monitored in
a proper
Service delivery,
personal data,
sensitive
information and
the company
Low High It will take about 1 month to
set up proper security
measures.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
6. Compliance
challenge
If the
employees do
not conform to
rules like
policies,
specifications,
standards as
well as laws
then it leads to
compliance
challenges.
Data
privacy
If the
certification or
audit is
unavailable to
the customers,
there is no
completeness in
the terms of
use.
The
organization
must
immediately
abide by the
rules and
incorporate
strong
security
measures in
the system.
Certification of
the company is
the affected asset
in this case.
Very High High It will take approximately 2
weeks to set up.
7. Activities of
the co-tenant
If the co-tenant
carries out
malicious
activities and
have malicious
Data
privacy
If there is no
resource
isolation and
reputational
isolation then it
The activities
of the tenants
need to be
monitored in
a proper
Service delivery,
personal data,
sensitive
information and
the company
Low High It will take about 1 month to
set up proper security
measures.
9
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
intentions then
it can harm the
information
present in the
cloud storage.
leads to this
type of risk.
manner.
Strong
security
policies must
be
implemented
in the cloud
infrastructure
.
reputation will
be affected by
this type of risk.
8. Failure or
termination
of cloud
service
If there is lack
of proper
business
strategy, high
competition
and no
financial
Data
privacy
If there is no
completeness in
the terms of use
and there is no
supplier
redundancy
then it causes
The Proper
vendor must
be selected
by evaluating
their
financial and
business
Employee
loyalty, company
reputation,
service delivery
and customer
trust are the
affected assets of
NA Very High It will take approximately 2
weeks to overcome this
situation.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
intentions then
it can harm the
information
present in the
cloud storage.
leads to this
type of risk.
manner.
Strong
security
policies must
be
implemented
in the cloud
infrastructure
.
reputation will
be affected by
this type of risk.
8. Failure or
termination
of cloud
service
If there is lack
of proper
business
strategy, high
competition
and no
financial
Data
privacy
If there is no
completeness in
the terms of use
and there is no
supplier
redundancy
then it causes
The Proper
vendor must
be selected
by evaluating
their
financial and
business
Employee
loyalty, company
reputation,
service delivery
and customer
trust are the
affected assets of
NA Very High It will take approximately 2
weeks to overcome this
situation.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
support can
cause the cloud
providers to
terminate their
services.
this type of risk. capabilities. the organization.
9. Exhaustion
of resources
The allocation
of resources
takes place
based on
statistical
projections and
because this is
an on-demand
service then it
leads to
exhaustion of
Authentic
ation and
access
control
If there is no
supplier
redundancy, no
accurate
resource usage
modelling and
improper
resource
provisioning is
the cause
behind these
Accurate
resource
usage
modelling
must be done
in order to
keep proper
track of
resource
usage.
Company
reputation,
service delivery
and customer
trust are the
affected assets of
the organization.
Additional
capacity
cannot be
provided to
customers:
Medium
Agreed
capacity
cannot be
provided:
Low
Low or
medium
It will take about 1 month to
overcome this situation.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
support can
cause the cloud
providers to
terminate their
services.
this type of risk. capabilities. the organization.
9. Exhaustion
of resources
The allocation
of resources
takes place
based on
statistical
projections and
because this is
an on-demand
service then it
leads to
exhaustion of
Authentic
ation and
access
control
If there is no
supplier
redundancy, no
accurate
resource usage
modelling and
improper
resource
provisioning is
the cause
behind these
Accurate
resource
usage
modelling
must be done
in order to
keep proper
track of
resource
usage.
Company
reputation,
service delivery
and customer
trust are the
affected assets of
the organization.
Additional
capacity
cannot be
provided to
customers:
Medium
Agreed
capacity
cannot be
provided:
Low
Low or
medium
It will take about 1 month to
overcome this situation.
11
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
resources. risks.
High
10. Malicious
insiders
Insiders are the
people who
have access to
sensitive
information of
the
organization.
These people
can leak the
data to the
external
attackers for
harming the
Deliberate
insider
attack
The insiders
might transfer
information to
the competitor
organization.
Strong
security
policies must
be
implemented
and the
organization
must monitor
the activities
of the people.
The user data
and company
reputation will
be affected.
Low Medium It will take around 2 months
to set up a proper employee
monitoring system in the
organization.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
resources. risks.
High
10. Malicious
insiders
Insiders are the
people who
have access to
sensitive
information of
the
organization.
These people
can leak the
data to the
external
attackers for
harming the
Deliberate
insider
attack
The insiders
might transfer
information to
the competitor
organization.
Strong
security
policies must
be
implemented
and the
organization
must monitor
the activities
of the people.
The user data
and company
reputation will
be affected.
Low Medium It will take around 2 months
to set up a proper employee
monitoring system in the
organization.
12
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
organization.
2. PII strategy proposal for DAS MY License portal
PII is the data which is utilised to uniquely identify and locate a person. It basically involves the information and the data by which the
individual can be identified, the information also involves the credit card information, the date of birth and much more. The use of the IT
technology can help to manage the data that are accumulated in the My License Portal of DAS. The risks, threats and vulnerabilities related to
the accumulation and collection of data via My license Portal are discussed in the following-
i. The data and the information of the My License Portal are sensitive and confidential and the major risks involved with the portal are the loss of
data, malware attack and the data breach.
ii. Un-patched system and the unpatched software is another major risk which is related to the data privacy of the online portal.
iii. The flaws in the network architecture can enhance the possibilities of the loss of data and the data breach.
iv. The data stored in the database can be vulnerable and can be prone to major risks and threats.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
organization.
2. PII strategy proposal for DAS MY License portal
PII is the data which is utilised to uniquely identify and locate a person. It basically involves the information and the data by which the
individual can be identified, the information also involves the credit card information, the date of birth and much more. The use of the IT
technology can help to manage the data that are accumulated in the My License Portal of DAS. The risks, threats and vulnerabilities related to
the accumulation and collection of data via My license Portal are discussed in the following-
i. The data and the information of the My License Portal are sensitive and confidential and the major risks involved with the portal are the loss of
data, malware attack and the data breach.
ii. Un-patched system and the unpatched software is another major risk which is related to the data privacy of the online portal.
iii. The flaws in the network architecture can enhance the possibilities of the loss of data and the data breach.
iv. The data stored in the database can be vulnerable and can be prone to major risks and threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
v. The malware attack and the virus attack can prove disastrous to the enterprise as it can slow down the server, it can shut down the server and
can cause major disputes to the company.
vi. The risks associated with the identity theft and atomicity risk is the high case. This mainly occurs due to the robbing of the vital and sensitive
data of the employees and the clients associated with the company. This is a major risk of the company related with PII.
The risk control procedures can prove fruitful to the enterprise. The process of encryption of the sensitive data can assist in authorized
access, only the authorised persons can gain access to the system and the database. The secured access control can help in the limited use of the
data of the database and only the persons who are a charge of data can access or view the data, in this way the security can be assured. The
employees of the organisations must have the proper training, they should have sound knowledge of the BYOD as these aspects can check or
diminish the correlated risks associated with the organisation.
Identification of all the Personal Identification Information which is prevalent in the system- The organisations must be aware of all the
data flow, the employees and the management team must know all the beneficial aspects of the data and the data flow, in this way they get an
overview on how to safeguard the sensitive information. They can get to know which procedures should be initiated in the organization. The
organization must make a habit of all the review and auditing of all the data flow within the organization, with the help of Personal Identifiable
Information the management team and the employees can be able to manage, maintain the data flow and can manage the clients and the business
partners.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
v. The malware attack and the virus attack can prove disastrous to the enterprise as it can slow down the server, it can shut down the server and
can cause major disputes to the company.
vi. The risks associated with the identity theft and atomicity risk is the high case. This mainly occurs due to the robbing of the vital and sensitive
data of the employees and the clients associated with the company. This is a major risk of the company related with PII.
The risk control procedures can prove fruitful to the enterprise. The process of encryption of the sensitive data can assist in authorized
access, only the authorised persons can gain access to the system and the database. The secured access control can help in the limited use of the
data of the database and only the persons who are a charge of data can access or view the data, in this way the security can be assured. The
employees of the organisations must have the proper training, they should have sound knowledge of the BYOD as these aspects can check or
diminish the correlated risks associated with the organisation.
Identification of all the Personal Identification Information which is prevalent in the system- The organisations must be aware of all the
data flow, the employees and the management team must know all the beneficial aspects of the data and the data flow, in this way they get an
overview on how to safeguard the sensitive information. They can get to know which procedures should be initiated in the organization. The
organization must make a habit of all the review and auditing of all the data flow within the organization, with the help of Personal Identifiable
Information the management team and the employees can be able to manage, maintain the data flow and can manage the clients and the business
partners.

14
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
Laws and the contractual requirements that should be recognised to cater the security and privacy to the data of Personal Identifiable
Information-The policies and the regulations from the contractual sectors must be given the protection to protect and secure the data of the
Personal Identifiable Information. The laws, policies and the regulations that are adopted by the organization are COPPA (Children’s Online
Privacy Protection Act), GLB (Gramm Leach Bliley) and HIPAA (Health Insurance Portability and Accountability Act). The laws, policies and
the regulations must be implied to the local level as on the Local level to get the safeguard the Personal Identifiable Information.
All the risks, threats, vulnerabilities associated with the system must be assessed and the security controls must be implied to mitigate the
risk. To mitigate the risk, threats and the vulnerabilities of the organization compliance regulations and the privacy must be considered as that
secure and protect the Personal Identifiable Information. The corporate for good governance is very crucial and vital for the aforesaid
organization. For protecting and securing the data of the database of the organization the risk, threats and the vulnerabilities must be analysed
and best solutions for controlling the database must be catered. All the standardaized PII data must be analysed and the personal sensitive data
must be identified and the risks associated with reputational and the reputational must be well examined to get the best outcome. The
commitments which are needed to comply the policies and the regulations and the laws must be identified and necessary actions must be taken to
apply the same. Compliance threats that are related to internal commitments and the external commitments must be detected. Also, the
likelihood of the threats associated with the threats must also be examined. There are various risk management strategies that can embellish the
business operations of the organizations and they are mitigation, avoidance, acceptance and the sharing. To assure the security and privacy,
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
Laws and the contractual requirements that should be recognised to cater the security and privacy to the data of Personal Identifiable
Information-The policies and the regulations from the contractual sectors must be given the protection to protect and secure the data of the
Personal Identifiable Information. The laws, policies and the regulations that are adopted by the organization are COPPA (Children’s Online
Privacy Protection Act), GLB (Gramm Leach Bliley) and HIPAA (Health Insurance Portability and Accountability Act). The laws, policies and
the regulations must be implied to the local level as on the Local level to get the safeguard the Personal Identifiable Information.
All the risks, threats, vulnerabilities associated with the system must be assessed and the security controls must be implied to mitigate the
risk. To mitigate the risk, threats and the vulnerabilities of the organization compliance regulations and the privacy must be considered as that
secure and protect the Personal Identifiable Information. The corporate for good governance is very crucial and vital for the aforesaid
organization. For protecting and securing the data of the database of the organization the risk, threats and the vulnerabilities must be analysed
and best solutions for controlling the database must be catered. All the standardaized PII data must be analysed and the personal sensitive data
must be identified and the risks associated with reputational and the reputational must be well examined to get the best outcome. The
commitments which are needed to comply the policies and the regulations and the laws must be identified and necessary actions must be taken to
apply the same. Compliance threats that are related to internal commitments and the external commitments must be detected. Also, the
likelihood of the threats associated with the threats must also be examined. There are various risk management strategies that can embellish the
business operations of the organizations and they are mitigation, avoidance, acceptance and the sharing. To assure the security and privacy,

15
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
participation is the main goal or the main objective if the risk assessment procedures, the participation involve the experts who are skilled in the
subjects and the stakeholders. The outside examiners must participate in the assuring the security and privacy as well.
Accumulation of Personal Identifiable Information are absolute necessity to carry out the business activities inside the organsiation- The
data or the identification that is necessary for the organization that can cater the security and the privacy must be protected and secured and those
must be obtained and accumulated by proper means and must save them for the future use. Here the big data plays a significant role to store all
the vital information of the data of the database and the organisation by storing all the data that are required for the organisation. Therefore, to
keep a record of all the information be it the financial data and the customers’ sensitive data can be stored efficiently by the big data and the big
data can also help to assess the data with simplicity and with ease. In this way, the credentials of the Personal Identifiable Information can be
protected and secured.
The data and the information used by the Personal Identifiable Information must be prioritized and based on that the organisation must
choose the data which is more important and should store accordingly to the database, the username of the customer is less confidential
compared to the passwords and also compared to the credentials of the clients of the bank. If the intruders or the hackers hack the information of
the system they can get the basic information of the clients and thus they do not gain access to the passwords and the private bank details. Thus
the privacy can safeguard from the clients. Thus the intruder's attack will cause less harm to the organization. Every organization follows a
different strategy and in this case, DAS must choose the best solution to secure the Personal Identifiable Information of the enterprise.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
participation is the main goal or the main objective if the risk assessment procedures, the participation involve the experts who are skilled in the
subjects and the stakeholders. The outside examiners must participate in the assuring the security and privacy as well.
Accumulation of Personal Identifiable Information are absolute necessity to carry out the business activities inside the organsiation- The
data or the identification that is necessary for the organization that can cater the security and the privacy must be protected and secured and those
must be obtained and accumulated by proper means and must save them for the future use. Here the big data plays a significant role to store all
the vital information of the data of the database and the organisation by storing all the data that are required for the organisation. Therefore, to
keep a record of all the information be it the financial data and the customers’ sensitive data can be stored efficiently by the big data and the big
data can also help to assess the data with simplicity and with ease. In this way, the credentials of the Personal Identifiable Information can be
protected and secured.
The data and the information used by the Personal Identifiable Information must be prioritized and based on that the organisation must
choose the data which is more important and should store accordingly to the database, the username of the customer is less confidential
compared to the passwords and also compared to the credentials of the clients of the bank. If the intruders or the hackers hack the information of
the system they can get the basic information of the clients and thus they do not gain access to the passwords and the private bank details. Thus
the privacy can safeguard from the clients. Thus the intruder's attack will cause less harm to the organization. Every organization follows a
different strategy and in this case, DAS must choose the best solution to secure the Personal Identifiable Information of the enterprise.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
The safety measurements must be initiated to cater the best security solution to the Personal Identifiable Information of the enterprise-
The risks assessment must utilize the safety measures so that Personal Identifiable Information can be securely utilized in the organization. The
security, as well as the privacy, must be ensured within the organisation that is an absolute necessity. The risk controlling techniques showcase
that the safeguards need to be adopted to ensure the security and the privacy. The safeguards methods that are needed to follow within the
organisation are-
Creation of procedures and the policies- the policies, regulations, the process must be maintained by the organization so that the Personal
Identifiable Information efficiently. The employees of the organization, as well as the clients of the organization, must follow the procedures and
the policies to efficiently utilize the security and the privacy features within the organization. The employees of the enterprise must be trained so
that they can use the security and the privacy features effectively on their premises, they can control and protect the data to assist the clients and
can mitigate the risks occurring in the organization. The training can help to assess the risks in the first place. The de-identification can
safeguard, protect and secure the data and can assist in the security procedure. The encryption is the procedure to safeguard the database and the
system.
3. Protection of Informal digital identity
The mentioned digital identity is the set of rules which involves an organization and specific individuals and it associates the confidential
and the private data like the username, password security pin and the security number and the birth. The proper strategies must be implemented
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
The safety measurements must be initiated to cater the best security solution to the Personal Identifiable Information of the enterprise-
The risks assessment must utilize the safety measures so that Personal Identifiable Information can be securely utilized in the organization. The
security, as well as the privacy, must be ensured within the organisation that is an absolute necessity. The risk controlling techniques showcase
that the safeguards need to be adopted to ensure the security and the privacy. The safeguards methods that are needed to follow within the
organisation are-
Creation of procedures and the policies- the policies, regulations, the process must be maintained by the organization so that the Personal
Identifiable Information efficiently. The employees of the organization, as well as the clients of the organization, must follow the procedures and
the policies to efficiently utilize the security and the privacy features within the organization. The employees of the enterprise must be trained so
that they can use the security and the privacy features effectively on their premises, they can control and protect the data to assist the clients and
can mitigate the risks occurring in the organization. The training can help to assess the risks in the first place. The de-identification can
safeguard, protect and secure the data and can assist in the security procedure. The encryption is the procedure to safeguard the database and the
system.
3. Protection of Informal digital identity
The mentioned digital identity is the set of rules which involves an organization and specific individuals and it associates the confidential
and the private data like the username, password security pin and the security number and the birth. The proper strategies must be implemented

17
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
to assure the security of the individuals, for securing the data protection of the individuals. Digital identity is generally network identity. The
digital identity is one of the vital are the security and privacy. The concept of digital identity gets linked to the various identifiers like emails,
domain name and the URL. Now with the advent of IT technology the cybercrimes have increased a lot. The risks have increased related to
identity theft, digital security and the digital authenticity, and validation must be done to assure the web infrastructure and the network
architecture. The digital identity comprises of various data attributes and the data attributes involve the social security number. To ensure the
privacy and the confidentiality and digital identity and atomicity of the clients in the My License portal is an absolute necessity.
The various procedures associated with the protection of the digital identity and atomicity have been elaborated below-
i. The accessibility of the data of the clients and the employees are made in such a way that only the authorized users can only gain into the
system accounts and the database accounts. Authentication is the process by which the device’s identity and the clients’ identity can be accessed
and verified. There is a security technique called the single sign-on and it contains the authentication keys those keys are valid for the single time
use. The one-time authentic key eliminates the possibilities of the leaked keys by any means and also eliminates the access of the unauthorized
access of the clients and the employees into the system. Thus the management team and the admin will have the full access of the database and
the system and the employees will have finite access to the HR database, HR system and will only access those areas that fall under their
working category. Moreover, there is a three-layer authentication protocol that can assist finite usage of the data that the authorized individuals
use. In this way, the risks of unauthorized access can be mitigated by the authorization techniques and the procedures.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
to assure the security of the individuals, for securing the data protection of the individuals. Digital identity is generally network identity. The
digital identity is one of the vital are the security and privacy. The concept of digital identity gets linked to the various identifiers like emails,
domain name and the URL. Now with the advent of IT technology the cybercrimes have increased a lot. The risks have increased related to
identity theft, digital security and the digital authenticity, and validation must be done to assure the web infrastructure and the network
architecture. The digital identity comprises of various data attributes and the data attributes involve the social security number. To ensure the
privacy and the confidentiality and digital identity and atomicity of the clients in the My License portal is an absolute necessity.
The various procedures associated with the protection of the digital identity and atomicity have been elaborated below-
i. The accessibility of the data of the clients and the employees are made in such a way that only the authorized users can only gain into the
system accounts and the database accounts. Authentication is the process by which the device’s identity and the clients’ identity can be accessed
and verified. There is a security technique called the single sign-on and it contains the authentication keys those keys are valid for the single time
use. The one-time authentic key eliminates the possibilities of the leaked keys by any means and also eliminates the access of the unauthorized
access of the clients and the employees into the system. Thus the management team and the admin will have the full access of the database and
the system and the employees will have finite access to the HR database, HR system and will only access those areas that fall under their
working category. Moreover, there is a three-layer authentication protocol that can assist finite usage of the data that the authorized individuals
use. In this way, the risks of unauthorized access can be mitigated by the authorization techniques and the procedures.

18
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
ii. The efficient use of the digital signature enhances the integrity and the accountability of accessing the data. Data integrity ensures the data
accuracy and the data integrity. Therefore, it can be taken into consideration as one of the effective secured ways to protect the digital identity of
the clients. The maintenance of integration of data is the main requirement of protecting and securing the digital identity. Data integrity is the
method by which the entire completeness, consistency and the accuracy of the data. The database administrators and the database managers must
ensure that the atomicity is maintained while storing the data into the database, the data must be stored and the duplication of data must be
avoided otherwise any disruption causes within the database. Hence, the data integrity should be implied within the My License Portal through
effective usage of standard rules and standard procedures.
iii. Encryption of data is another mean of protecting the contents of the database of the organisation and prevention of data loss. The encryption
enables the procedures to access the information in a limited way and it only grants access to the system who has the required authenticity to
access and access the database and the system. It is considered as another major risk mitigation procedure by which data theft and loss of data
can be prevented and checked. That will help to ensure the digital identity in the My License Portal.
iv. The employment of proper security suites can assist in securing and protecting the digital identity. The blockchain technology security
measures can help to verify the transaction of data flow within the organisation premises. This security measures can be conducted by investing
a digital ledger contained in the blockchain technology. The blockchain technology is known to cater the best privacy and the security-based
solutions, it involves the procedures of the cryptography which has the capability to diminish the scope of the data theft and the data loss, it
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
ii. The efficient use of the digital signature enhances the integrity and the accountability of accessing the data. Data integrity ensures the data
accuracy and the data integrity. Therefore, it can be taken into consideration as one of the effective secured ways to protect the digital identity of
the clients. The maintenance of integration of data is the main requirement of protecting and securing the digital identity. Data integrity is the
method by which the entire completeness, consistency and the accuracy of the data. The database administrators and the database managers must
ensure that the atomicity is maintained while storing the data into the database, the data must be stored and the duplication of data must be
avoided otherwise any disruption causes within the database. Hence, the data integrity should be implied within the My License Portal through
effective usage of standard rules and standard procedures.
iii. Encryption of data is another mean of protecting the contents of the database of the organisation and prevention of data loss. The encryption
enables the procedures to access the information in a limited way and it only grants access to the system who has the required authenticity to
access and access the database and the system. It is considered as another major risk mitigation procedure by which data theft and loss of data
can be prevented and checked. That will help to ensure the digital identity in the My License Portal.
iv. The employment of proper security suites can assist in securing and protecting the digital identity. The blockchain technology security
measures can help to verify the transaction of data flow within the organisation premises. This security measures can be conducted by investing
a digital ledger contained in the blockchain technology. The blockchain technology is known to cater the best privacy and the security-based
solutions, it involves the procedures of the cryptography which has the capability to diminish the scope of the data theft and the data loss, it
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
19
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
provides the solutions relatively fast. Blockchains cater the best private and public cloud-based solutions and the technologies discussed are
capable to secure the sensitive data and the confidential data.
The aforesaid risks must be mitigated, the organization must be safeguard, the mitigation techniques mentioned should be managed to
secure the database and the system. The data of the database must be controlled by proper encryption and proper authentication method. The risk
mitigation techniques have been illustrated in the report.
4. Governance of PII and digital identities for users of the portal
Personally identifiable information or PII is susceptible to several threats and risks. The cybercriminals and hackers mainly target the
sensitive information that is present in the cloud storage of the organization. They can misuse the data. The data might also be lost because of
their wrong activities. PII can be lost also because of lost hard drives, equipment as good documents along with cyber attacks. If PII is stolen or
lost then it can cause financial loss and also harm the reputation of the organization. A data breach can harm the organization in several ways.
Therefore, it can be said that it is essential to develop strong governance policies in the organization for protecting the personally identifiable
information of the users. The governance of PII is a complex process and must be well planned and implemented. PII governance forms an
essential and integral part of managing PII as well as digital identities. This also helps in social progress as well as economic development. PII
foundation forms the basis for a secure organization as well as a cloud platform. The digital identity of the organization can be made effective by
implementing strong governance policy for protecting the PII. Initially, the PII dealt with the telephone numbers of the people. With the growth
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
provides the solutions relatively fast. Blockchains cater the best private and public cloud-based solutions and the technologies discussed are
capable to secure the sensitive data and the confidential data.
The aforesaid risks must be mitigated, the organization must be safeguard, the mitigation techniques mentioned should be managed to
secure the database and the system. The data of the database must be controlled by proper encryption and proper authentication method. The risk
mitigation techniques have been illustrated in the report.
4. Governance of PII and digital identities for users of the portal
Personally identifiable information or PII is susceptible to several threats and risks. The cybercriminals and hackers mainly target the
sensitive information that is present in the cloud storage of the organization. They can misuse the data. The data might also be lost because of
their wrong activities. PII can be lost also because of lost hard drives, equipment as good documents along with cyber attacks. If PII is stolen or
lost then it can cause financial loss and also harm the reputation of the organization. A data breach can harm the organization in several ways.
Therefore, it can be said that it is essential to develop strong governance policies in the organization for protecting the personally identifiable
information of the users. The governance of PII is a complex process and must be well planned and implemented. PII governance forms an
essential and integral part of managing PII as well as digital identities. This also helps in social progress as well as economic development. PII
foundation forms the basis for a secure organization as well as a cloud platform. The digital identity of the organization can be made effective by
implementing strong governance policy for protecting the PII. Initially, the PII dealt with the telephone numbers of the people. With the growth

20
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
of technology, people are able to access and process data at a faster speed. This has also led to the increase in loss of data and therefore the
personally identifiable information is subjected to various risks and threats. The data loss can be divided into two categories called intentional
and unintentional data loss. Accidental loss of data is not much harmful because there are no malicious intentions behind such loss. The data loss
can be caused due to the carelessness of the employees and some kind of errors that are made by the employees. These employees do not have
any wrong intention to harm the organization. Lack of strong security policies can also cause accidental loss of data. The other type of threat is
the deliberate threat that can harm the organization in a severe manner. The exposure of this risk is high because there are malicious intentions
behind such attacks. These attacks can be either external or internal. PII can contain sensitive information like name, address, phone numbers
and financial details of the user. It can also contain health-related information and payroll information of the employees of the organization.
Preventive measures must be taken in order to protect these valuable data from any types of attacks. There can be malware attacks like virus
attacks, worms, phishing attacks and Trojan horse attacks as well. Spyware can enter the system and quietly steal data from the system. Data
must be protected in a proper manner in order to protect the reputation of the company as well as the sensitive data of the users. Therefore, a
proper strategy must be implemented for the governance of PII and for protecting the digital identity of users of My License portal. The
governance plan is discussed below.
4.1. PII and digital identities for the users of My license Portal
1. The users need to have proper knowledge regarding storage of the data. They must be aware of all the various types of security threats and
risks that can harm the sensitive information. Proper knowledge about the importance of security measures forms the basic step for forming the
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
of technology, people are able to access and process data at a faster speed. This has also led to the increase in loss of data and therefore the
personally identifiable information is subjected to various risks and threats. The data loss can be divided into two categories called intentional
and unintentional data loss. Accidental loss of data is not much harmful because there are no malicious intentions behind such loss. The data loss
can be caused due to the carelessness of the employees and some kind of errors that are made by the employees. These employees do not have
any wrong intention to harm the organization. Lack of strong security policies can also cause accidental loss of data. The other type of threat is
the deliberate threat that can harm the organization in a severe manner. The exposure of this risk is high because there are malicious intentions
behind such attacks. These attacks can be either external or internal. PII can contain sensitive information like name, address, phone numbers
and financial details of the user. It can also contain health-related information and payroll information of the employees of the organization.
Preventive measures must be taken in order to protect these valuable data from any types of attacks. There can be malware attacks like virus
attacks, worms, phishing attacks and Trojan horse attacks as well. Spyware can enter the system and quietly steal data from the system. Data
must be protected in a proper manner in order to protect the reputation of the company as well as the sensitive data of the users. Therefore, a
proper strategy must be implemented for the governance of PII and for protecting the digital identity of users of My License portal. The
governance plan is discussed below.
4.1. PII and digital identities for the users of My license Portal
1. The users need to have proper knowledge regarding storage of the data. They must be aware of all the various types of security threats and
risks that can harm the sensitive information. Proper knowledge about the importance of security measures forms the basic step for forming the

21
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
governance plan of PII. Proper track of the data record of the users is important. Proper access control strategies must be developed that will
allow specific users to access specific information. Access control can be considered to be a key feature for protecting the PII. Every user will
not be able to access all the available users. This access control mechanism will allow protecting the information from any unauthorized access
of data. Unauthorized access can harm the integrity as well as confidentiality of the information. Implementing strong access control policies
will help to protect PII of the users in an effective manner.
2. Another effective governance plan will be to create effective policies for secure storage, access, retrieval as well as transmission of data.
Keeping proper track of the data helps to handle data in an efficient as well as effective manner. This will help to develop an important strategy
for protecting PII. Proper track record of the data that is received or transmitted must be maintained so that it is easy to identify any type of
discrepancy in the transmission of data. Therefore, it can be said that proper handling as well as maintaining proper track record of information
is important for developing an effective governance plan.
3. The users must be trained so that they are able to handle the documents of digital identity in an effective manner. Imparting proper education
to the users will help to develop a strong strategy for the governance of PII. The users must be aware of the various privacy issues and it will be
help in protecting the PII from any type data breach and data loss. Imparting proper training to the users and employees will promote effective
handling of data ensuring high level security of PII.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
governance plan of PII. Proper track of the data record of the users is important. Proper access control strategies must be developed that will
allow specific users to access specific information. Access control can be considered to be a key feature for protecting the PII. Every user will
not be able to access all the available users. This access control mechanism will allow protecting the information from any unauthorized access
of data. Unauthorized access can harm the integrity as well as confidentiality of the information. Implementing strong access control policies
will help to protect PII of the users in an effective manner.
2. Another effective governance plan will be to create effective policies for secure storage, access, retrieval as well as transmission of data.
Keeping proper track of the data helps to handle data in an efficient as well as effective manner. This will help to develop an important strategy
for protecting PII. Proper track record of the data that is received or transmitted must be maintained so that it is easy to identify any type of
discrepancy in the transmission of data. Therefore, it can be said that proper handling as well as maintaining proper track record of information
is important for developing an effective governance plan.
3. The users must be trained so that they are able to handle the documents of digital identity in an effective manner. Imparting proper education
to the users will help to develop a strong strategy for the governance of PII. The users must be aware of the various privacy issues and it will be
help in protecting the PII from any type data breach and data loss. Imparting proper training to the users and employees will promote effective
handling of data ensuring high level security of PII.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
4.2. Personal and PII data for DAS users of the HR personnel Management Suite
1. The PII of DAS users is vulnerable to several threats and attacks. The risk exposure is high for all the data and documents that are stored in the
cloud. An effective preventive measure is to apply encryption algorithms for encrypting the sensitive information. Encryption algorithm
translates the plain texts into ciphertexts to protect it from any unauthorized access. Encryption can be considered to be a strategy for the
governance of PII of DAS users.
2. Poor configuration or misconfiguration of system can lead to major loss of information. The systems and applications must be updated on a
regular basis to avoid such issues. The data governance plan should focus on monitoring the system versions and updates.
3. Designing effective and advanced security infrastructure for the DAS can be considered to be a risk mitigation strategy of the organization.
The governance of PII must include the development of strong security infrastructure for the purpose of preventing any attack. Well, designed
security architectures will help the organization to fight against any attacks. Organizations will be able to prevent virus attacks, phishing attacks
and other malware attacks.
4.3. Personal and PII data for Contractors
1. The contractors must have a licence and it must be ensured that the license meets the prerequisites of the DAS. One main strategy of
mitigating risk is to hire licensed contractors. The governance plan must include this strategy because the licensed contractors have proper
knowledge regarding privacy issues and risks and they will know how to protect the data that is stored in the cloud storage space.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
4.2. Personal and PII data for DAS users of the HR personnel Management Suite
1. The PII of DAS users is vulnerable to several threats and attacks. The risk exposure is high for all the data and documents that are stored in the
cloud. An effective preventive measure is to apply encryption algorithms for encrypting the sensitive information. Encryption algorithm
translates the plain texts into ciphertexts to protect it from any unauthorized access. Encryption can be considered to be a strategy for the
governance of PII of DAS users.
2. Poor configuration or misconfiguration of system can lead to major loss of information. The systems and applications must be updated on a
regular basis to avoid such issues. The data governance plan should focus on monitoring the system versions and updates.
3. Designing effective and advanced security infrastructure for the DAS can be considered to be a risk mitigation strategy of the organization.
The governance of PII must include the development of strong security infrastructure for the purpose of preventing any attack. Well, designed
security architectures will help the organization to fight against any attacks. Organizations will be able to prevent virus attacks, phishing attacks
and other malware attacks.
4.3. Personal and PII data for Contractors
1. The contractors must have a licence and it must be ensured that the license meets the prerequisites of the DAS. One main strategy of
mitigating risk is to hire licensed contractors. The governance plan must include this strategy because the licensed contractors have proper
knowledge regarding privacy issues and risks and they will know how to protect the data that is stored in the cloud storage space.

23
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
2. The management suite of the contractor must include an option for automatically updating the firewalls of the system. The operating system
needs to be updated and original. Automatic update, as well as essential security policies, will help to enable an effective governance plan of PII.
An advanced version of operating systems will help to protect the data from any external as well as internal attacks. Older versions of
applications and operating systems are vulnerable to various attacks. The contractor management suite must include this auto-update feature in
order to promote an effective governance plan.
3. Trained contractors must be selected so that they are able to prevent any data breach. Trained contractors will be able to detect and prevent
any type of risks that can harm the system and its data.
4. Access control must be well implemented. It is considered to be an effective method of governance of the stored data in the suite of the
contractor. This helps to promote effective management as well as administration of the PII. It forms a major component of the governance plan
for protecting the personal as well as PII of the contractors.
4.4. Personal and PII data for users and DAS staffs
1. The DAS staffs must be trained in an effective manner so that they are able to detect and mitigate any type of security issue that occurs.
Proper training will help to ensure proper security mechanism in the organization. They will know how to optimally use the data. They will also
know about the issues that are related to the cloud storage. This ensures effective risk mitigation strategy.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
2. The management suite of the contractor must include an option for automatically updating the firewalls of the system. The operating system
needs to be updated and original. Automatic update, as well as essential security policies, will help to enable an effective governance plan of PII.
An advanced version of operating systems will help to protect the data from any external as well as internal attacks. Older versions of
applications and operating systems are vulnerable to various attacks. The contractor management suite must include this auto-update feature in
order to promote an effective governance plan.
3. Trained contractors must be selected so that they are able to prevent any data breach. Trained contractors will be able to detect and prevent
any type of risks that can harm the system and its data.
4. Access control must be well implemented. It is considered to be an effective method of governance of the stored data in the suite of the
contractor. This helps to promote effective management as well as administration of the PII. It forms a major component of the governance plan
for protecting the personal as well as PII of the contractors.
4.4. Personal and PII data for users and DAS staffs
1. The DAS staffs must be trained in an effective manner so that they are able to detect and mitigate any type of security issue that occurs.
Proper training will help to ensure proper security mechanism in the organization. They will know how to optimally use the data. They will also
know about the issues that are related to the cloud storage. This ensures effective risk mitigation strategy.

24
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
2. The consistency, as well as integrity of the information, needs to be maintained so that there is no misuse and loss of data. Maintaining
consistency and integrity ensures an effective data governance plan. The financial data needs to be well protected so that it is not lost. This plan
will help in protecting the payroll-related information of the employees.
3. The governance plan must include limited data access by specific users. This will help to protect the PII of the DAS staffs and users.
Bibliography:
Amin, R., & Biswas, G. P. (2015). A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. Journal
of medical systems, 39(8), 78.
Biham, E., & Shamir, A. (2012). Differential cryptanalysis of the data encryption standard. Springer Science & Business Media.
Chen, H. C., & Lee, P. P. (2012, October). Enabling data integrity protection in regenerating-coding-based cloud storage. In Reliable Distributed
Systems (SRDS), 2012 IEEE 31st Symposium on (pp. 51-60). IEEE.
De Montjoye, Y. A., Radaelli, L., & Singh, V. K. (2015). Unique in the shopping mall: On the reidentifiability of credit card metadata. Science,
347(6221), 536-539.
Kayworth, T., & Whitten, D. (2012). Effective information security requires a balance of social and technology factors.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
2. The consistency, as well as integrity of the information, needs to be maintained so that there is no misuse and loss of data. Maintaining
consistency and integrity ensures an effective data governance plan. The financial data needs to be well protected so that it is not lost. This plan
will help in protecting the payroll-related information of the employees.
3. The governance plan must include limited data access by specific users. This will help to protect the PII of the DAS staffs and users.
Bibliography:
Amin, R., & Biswas, G. P. (2015). A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. Journal
of medical systems, 39(8), 78.
Biham, E., & Shamir, A. (2012). Differential cryptanalysis of the data encryption standard. Springer Science & Business Media.
Chen, H. C., & Lee, P. P. (2012, October). Enabling data integrity protection in regenerating-coding-based cloud storage. In Reliable Distributed
Systems (SRDS), 2012 IEEE 31st Symposium on (pp. 51-60). IEEE.
De Montjoye, Y. A., Radaelli, L., & Singh, V. K. (2015). Unique in the shopping mall: On the reidentifiability of credit card metadata. Science,
347(6221), 536-539.
Kayworth, T., & Whitten, D. (2012). Effective information security requires a balance of social and technology factors.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
Latif, R., Abbas, H., Assar, S., & Ali, Q. (2014). Cloud computing risk assessment: a systematic literature review. In Future Information
Technology (pp. 285-295). Springer, Berlin, Heidelberg.
Schwartz, P. M., & Solove, D. J. (2014). Reconciling personal information in the United States and European Union. Cal. L. Rev., 102, 877.
Shatnawi, A. (2017). Estimating Accuracy of Personal Identifiable Information in Integrated Data Systems.
Tucker, C. E. (2014). Social networks, personalized advertising, and privacy controls. American Marketing Association.
Wu, D., & Shan, S. (2015). Meta-analysis of network information security and Web data mining techniques. In First International Conference on
Information Sciences, Machinery, Materials and Energy (pp. 1974-1977). Atlantis Press.
Yang, Y. P. O., Shieh, H. M., & Tzeng, G. H. (2013). A VIKOR technique based on DEMATEL and ANP for information security risk control
assessment. Information Sciences, 232, 482-500.
PERSONAL IDENTIFIABLE INFORMATION STRATEGY
Latif, R., Abbas, H., Assar, S., & Ali, Q. (2014). Cloud computing risk assessment: a systematic literature review. In Future Information
Technology (pp. 285-295). Springer, Berlin, Heidelberg.
Schwartz, P. M., & Solove, D. J. (2014). Reconciling personal information in the United States and European Union. Cal. L. Rev., 102, 877.
Shatnawi, A. (2017). Estimating Accuracy of Personal Identifiable Information in Integrated Data Systems.
Tucker, C. E. (2014). Social networks, personalized advertising, and privacy controls. American Marketing Association.
Wu, D., & Shan, S. (2015). Meta-analysis of network information security and Web data mining techniques. In First International Conference on
Information Sciences, Machinery, Materials and Energy (pp. 1974-1977). Atlantis Press.
Yang, Y. P. O., Shieh, H. M., & Tzeng, G. H. (2013). A VIKOR technique based on DEMATEL and ANP for information security risk control
assessment. Information Sciences, 232, 482-500.
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




