Physical Security and How It Relates to Cybersecurity
VerifiedAdded on 2022/12/26
|14
|1219
|55
Presentation
AI Summary
This presentation explores the importance of physical security in relation to cybersecurity. It discusses the interrelationship between physical and cyber security and how cyber security helps protect physical assets. The presentation also provides examples of physical security measures and the role of cyber security in mitigating physical risks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

PHYSICAL SECURITY AND HOW
IT RELATES TO
CYBERSECURITY
IT RELATES TO
CYBERSECURITY
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTRODUCTION
• In today’s technological era there is rapid increase in cybercrimes. It
has led to theft of personal data and info. Along with it, physical
security related to protection of personnel, hardware, software, etc.
• This has resulted in damage in loss of reputation of firm. However, it
is important for enterprise to protect its software, hardware, date, etc.
so data is protected. The power point will describe about physical
security and how it relate to cyber security
• In today’s technological era there is rapid increase in cybercrimes. It
has led to theft of personal data and info. Along with it, physical
security related to protection of personnel, hardware, software, etc.
• This has resulted in damage in loss of reputation of firm. However, it
is important for enterprise to protect its software, hardware, date, etc.
so data is protected. The power point will describe about physical
security and how it relate to cyber security

Physical security
• The technological development has led to resulting in rise in crimes due to which it has become important
to protect people, property from any type of damage or loss.
• Usually, physical security is overlooked and is not protected.
• The breach of security can be due to malware, hacking, cyberespionage, etc.
• But it has been evaluated that internet of things is widely used in physical systems. It has enabled in
connecting of smart devices, applications, etc. With software. Hence, with that it has become easy to protect
them from cyber crimes and threats.
• The technological development has led to resulting in rise in crimes due to which it has become important
to protect people, property from any type of damage or loss.
• Usually, physical security is overlooked and is not protected.
• The breach of security can be due to malware, hacking, cyberespionage, etc.
• But it has been evaluated that internet of things is widely used in physical systems. It has enabled in
connecting of smart devices, applications, etc. With software. Hence, with that it has become easy to protect
them from cyber crimes and threats.
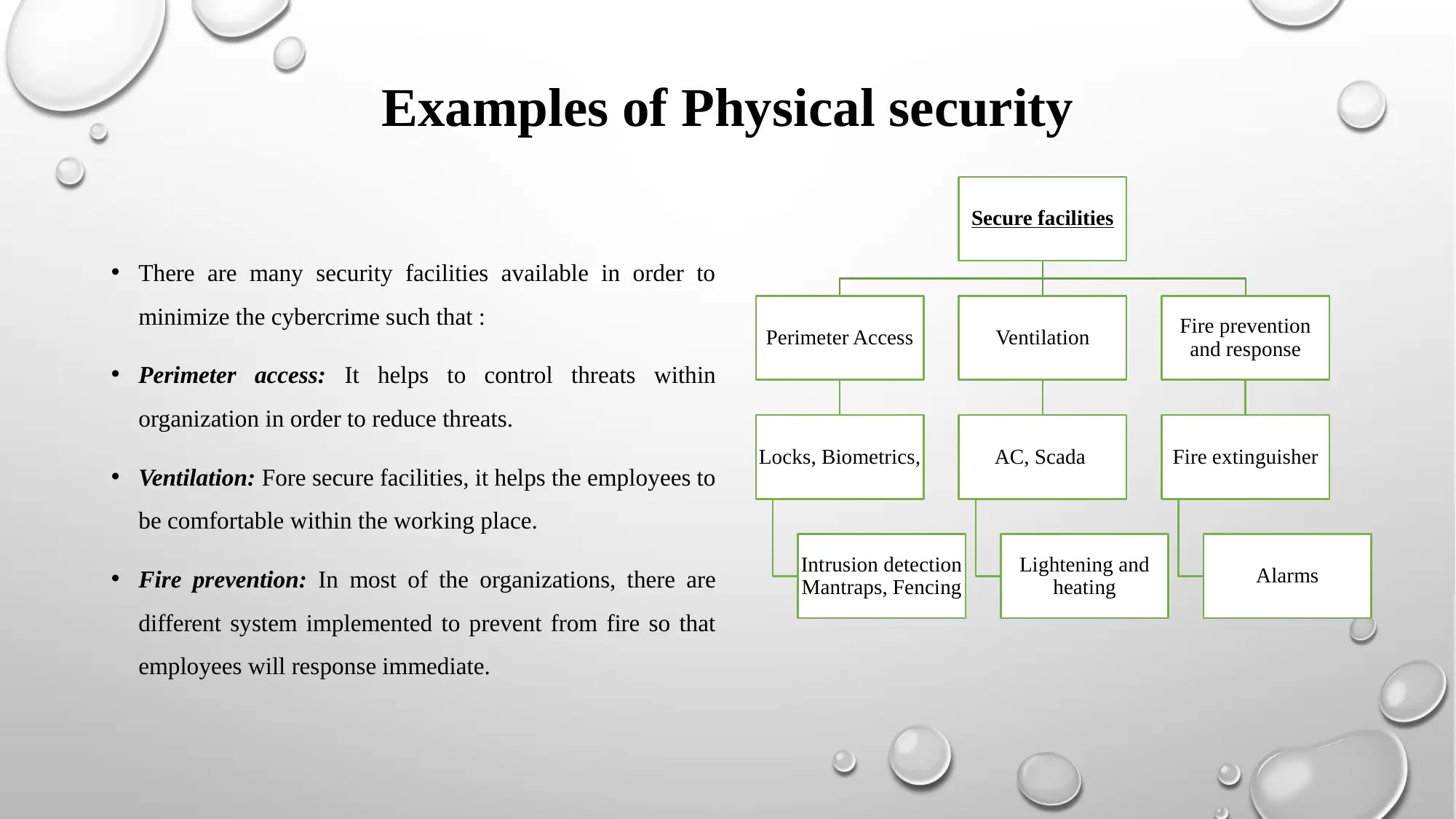
• There are many security facilities available in order to
minimize the cybercrime such that :
• Perimeter access: It helps to control threats within
organization in order to reduce threats.
• Ventilation: Fore secure facilities, it helps the employees to
be comfortable within the working place.
• Fire prevention: In most of the organizations, there are
different system implemented to prevent from fire so that
employees will response immediate.
Examples of Physical security
Secure facilities
Perimeter Access
Locks, Biometrics,
Intrusion detection
Mantraps, Fencing
Ventilation
AC, Scada
Lightening and
heating
Fire prevention
and response
Fire extinguisher
Alarms
minimize the cybercrime such that :
• Perimeter access: It helps to control threats within
organization in order to reduce threats.
• Ventilation: Fore secure facilities, it helps the employees to
be comfortable within the working place.
• Fire prevention: In most of the organizations, there are
different system implemented to prevent from fire so that
employees will response immediate.
Examples of Physical security
Secure facilities
Perimeter Access
Locks, Biometrics,
Intrusion detection
Mantraps, Fencing
Ventilation
AC, Scada
Lightening and
heating
Fire prevention
and response
Fire extinguisher
Alarms
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Physical security
• Cyber security means protection of internet connected systems that is
hardware, software, data, information from cyber crimes and threats.
• Hence, usually, it is used by organisation by which they are able to
protect physical asset from any damage or threats. Alongside, cyber
security helps in protecting data centre, server, computer systems
from unauthorised access.
• However, it is analysed that physical and cyber security are inter
related to each other. This can be said because with help of cyber
security, physical asset can be easily protected.
• Cyber security means protection of internet connected systems that is
hardware, software, data, information from cyber crimes and threats.
• Hence, usually, it is used by organisation by which they are able to
protect physical asset from any damage or threats. Alongside, cyber
security helps in protecting data centre, server, computer systems
from unauthorised access.
• However, it is analysed that physical and cyber security are inter
related to each other. This can be said because with help of cyber
security, physical asset can be easily protected.

Physical security
Furthermore, cyber security play vital role in this which is defined
• It helps build a physical security framework
• It allows for streamline alert and response
• Cyber security help mitigate physical risk-.
Furthermore, cyber security play vital role in this which is defined
• It helps build a physical security framework
• It allows for streamline alert and response
• Cyber security help mitigate physical risk-.

Physical security
• The security of data is essential as it prevent loss of data, info. And also damage of hardware software, files
and many others.
• Generally, physical security is integrated into cyber security. The use of IT infrastructure that is server,
system, etc. By which it becomes easy to integrate all information system together and ensure its security is
maintained.
• The security of data is essential as it prevent loss of data, info. And also damage of hardware software, files
and many others.
• Generally, physical security is integrated into cyber security. The use of IT infrastructure that is server,
system, etc. By which it becomes easy to integrate all information system together and ensure its security is
maintained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Physical security
• There are different ways through which physical security can be maintained. In that cyber security can also
be installed in it. So, it gives a double layer protection in computer system. Hence, ways are described as
below:
• Password protect phone
• Use of anti virus software
• Back up of data
• There are different ways through which physical security can be maintained. In that cyber security can also
be installed in it. So, it gives a double layer protection in computer system. Hence, ways are described as
below:
• Password protect phone
• Use of anti virus software
• Back up of data

Physical security
• Therefore, these are security practices that is used in securing physical asset.
• This makes simple to get things done in proper way. Besides, it enable in preventing of threat on asset.
• However, there are some principles which is followed in it such as what to protect, who to protect from,
likelihood and what consequences it can have on it.
• Therefore, these are security practices that is used in securing physical asset.
• This makes simple to get things done in proper way. Besides, it enable in preventing of threat on asset.
• However, there are some principles which is followed in it such as what to protect, who to protect from,
likelihood and what consequences it can have on it.

Physical security
• In present times, there are various new and advance technologies which can be used to protect physical
security. For example- IOT, AI, data integration, block chain, etc.
• Through which it becomes easy to protect and secure physical asset. The use of sensors helps in detecting
and giving alert on security breaches.
• The advance technology has enabled in ease in protecting physical asset. There is need to convergence in
this concept as integration shows what are changes done into it so that threat impact is mitigated.
• In present times, there are various new and advance technologies which can be used to protect physical
security. For example- IOT, AI, data integration, block chain, etc.
• Through which it becomes easy to protect and secure physical asset. The use of sensors helps in detecting
and giving alert on security breaches.
• The advance technology has enabled in ease in protecting physical asset. There is need to convergence in
this concept as integration shows what are changes done into it so that threat impact is mitigated.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CONCLUSION
• From presentation it can be stated that physical security related to protection of personnel, hardware,
software.
• There are 2 components of physical security that is access control and surveillance.
• Physical and cyber security are inter related to each other as with help of cyber security, physical asset can
be easily protected.
• Also, cyber security play vital role in this as it helps build a physical security framework, it allows for
streamline alert and response and cyber security help mitigate physical risk.
• From presentation it can be stated that physical security related to protection of personnel, hardware,
software.
• There are 2 components of physical security that is access control and surveillance.
• Physical and cyber security are inter related to each other as with help of cyber security, physical asset can
be easily protected.
• Also, cyber security play vital role in this as it helps build a physical security framework, it allows for
streamline alert and response and cyber security help mitigate physical risk.

REFERENCES
Books and journals
• Corallo, A., Lazoi, M. and lezzi, M., 2020. Cybersecurity in the context of industry 4.0: A structured classification of
critical assets and business impacts. Computers in industry. 114. p.103165.
• Coventry, l. And branley, D., 2018. Cybersecurity in healthcare: a narrative review of trends, threats and ways
forward. Maturitas. 113. pp.48-52.
• Crumpler, w. And lewis, J. A., 2019. Cybersecurity workforce gap. Center for strategic and international studies (CSIS).
• Lezzi, m., Lazoi, M. And corallo, A., 2018. Cybersecurity for industry 4.0 in the current literature: A reference
framework. Computers in industry. 103. pp.97-110.
• Li, l., He, W. And yuan, X., 2019. Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity
behavior. International journal of information management. 45. pp.13-24.
Books and journals
• Corallo, A., Lazoi, M. and lezzi, M., 2020. Cybersecurity in the context of industry 4.0: A structured classification of
critical assets and business impacts. Computers in industry. 114. p.103165.
• Coventry, l. And branley, D., 2018. Cybersecurity in healthcare: a narrative review of trends, threats and ways
forward. Maturitas. 113. pp.48-52.
• Crumpler, w. And lewis, J. A., 2019. Cybersecurity workforce gap. Center for strategic and international studies (CSIS).
• Lezzi, m., Lazoi, M. And corallo, A., 2018. Cybersecurity for industry 4.0 in the current literature: A reference
framework. Computers in industry. 103. pp.97-110.
• Li, l., He, W. And yuan, X., 2019. Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity
behavior. International journal of information management. 45. pp.13-24.

REFERENCES
• Lu, y. And da xu, L., 2018. Internet of things (iot) cybersecurity research: A review of current research topics. IEEE
internet of things journal. 6(2). pp.2103-2115.
• Mahdavifar, s. And ghorbani, A.A., 2019. Application of deep learning to cybersecurity: A survey. Neurocomputing. 347.
pp.149-176.
• Sarker, i.H., Kayes, A.S.M. And ng, A., 2020. Cybersecurity data science: an overview from machine learning
perspective. Journal of big data. 7(1). pp.1-29.
• Sun, n., Zhang, J. And xiang, Y., 2018. Data-driven cybersecurity incident prediction: A survey. IEEE communications
surveys & tutorials. 21(2). pp.1744-1772.
• Xin, y., Kong, L. And wang, C., 2018. Machine learning and deep learning methods for cybersecurity. Ieee access. 6.
pp.35365-35381.
• Lu, y. And da xu, L., 2018. Internet of things (iot) cybersecurity research: A review of current research topics. IEEE
internet of things journal. 6(2). pp.2103-2115.
• Mahdavifar, s. And ghorbani, A.A., 2019. Application of deep learning to cybersecurity: A survey. Neurocomputing. 347.
pp.149-176.
• Sarker, i.H., Kayes, A.S.M. And ng, A., 2020. Cybersecurity data science: an overview from machine learning
perspective. Journal of big data. 7(1). pp.1-29.
• Sun, n., Zhang, J. And xiang, Y., 2018. Data-driven cybersecurity incident prediction: A survey. IEEE communications
surveys & tutorials. 21(2). pp.1744-1772.
• Xin, y., Kong, L. And wang, C., 2018. Machine learning and deep learning methods for cybersecurity. Ieee access. 6.
pp.35365-35381.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





