Adatum Network Project: Hierarchical Network Planning & Implementation
VerifiedAdded on 2023/04/03
|11
|438
|208
Project
AI Summary
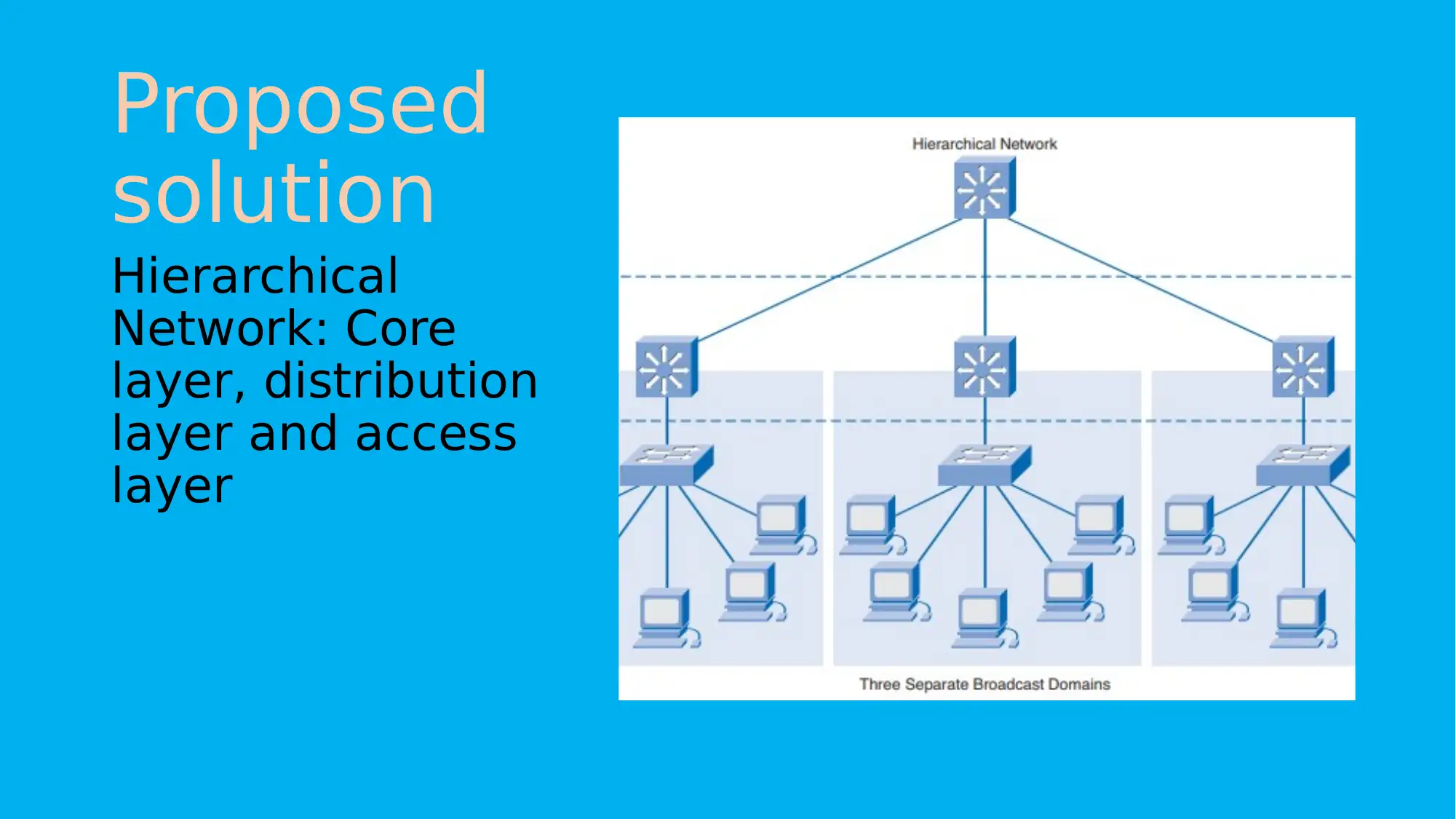
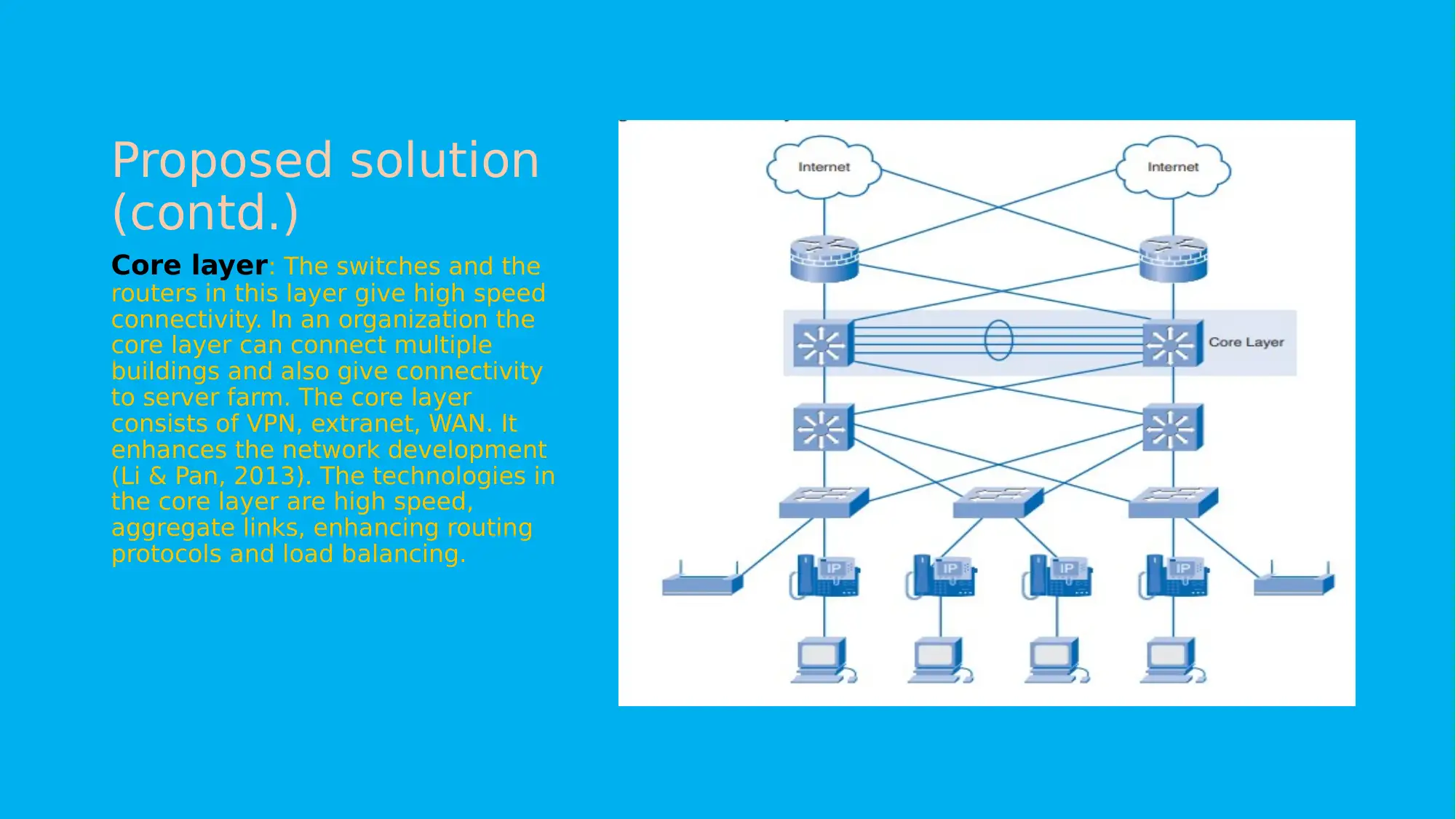
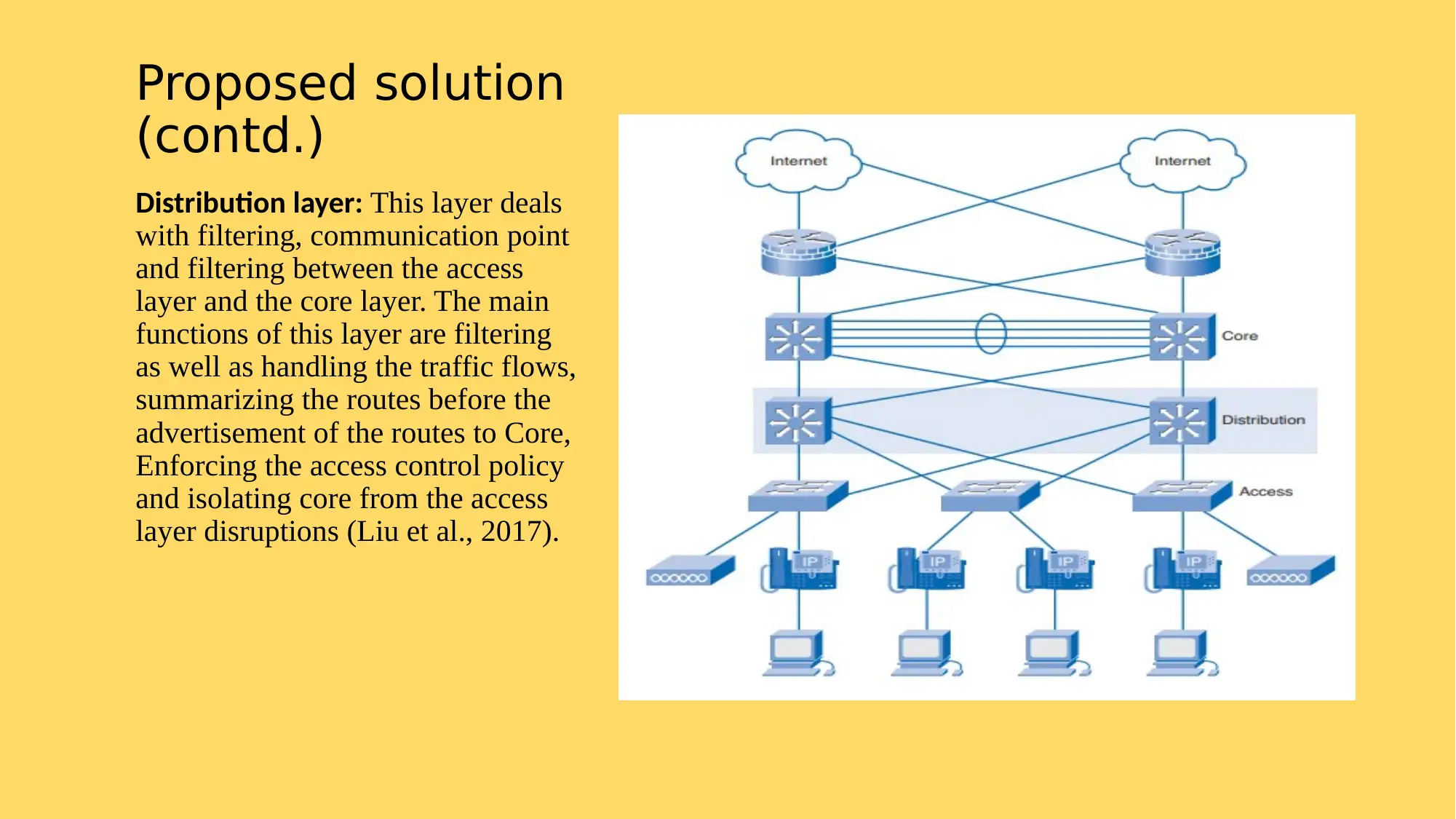
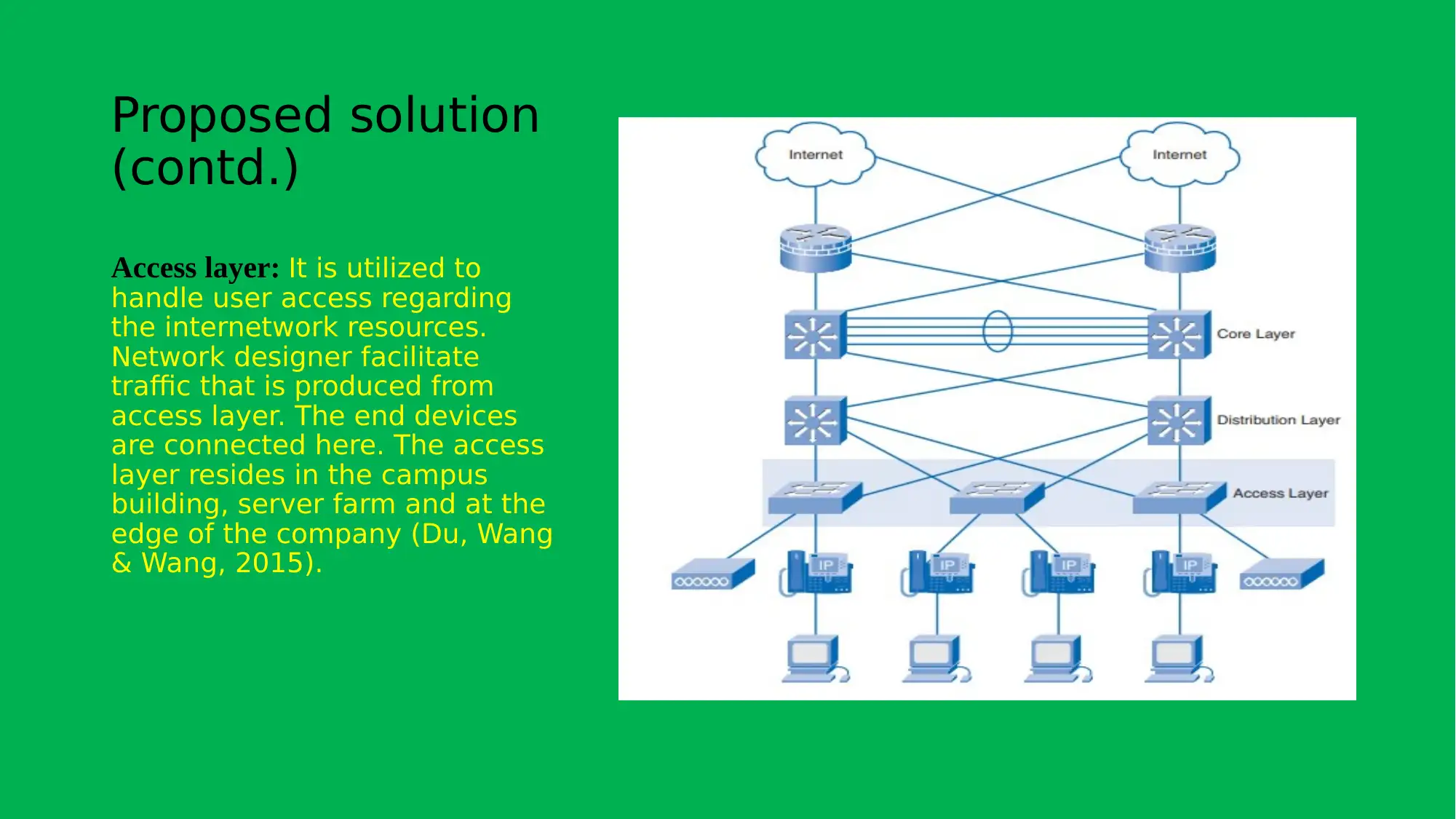
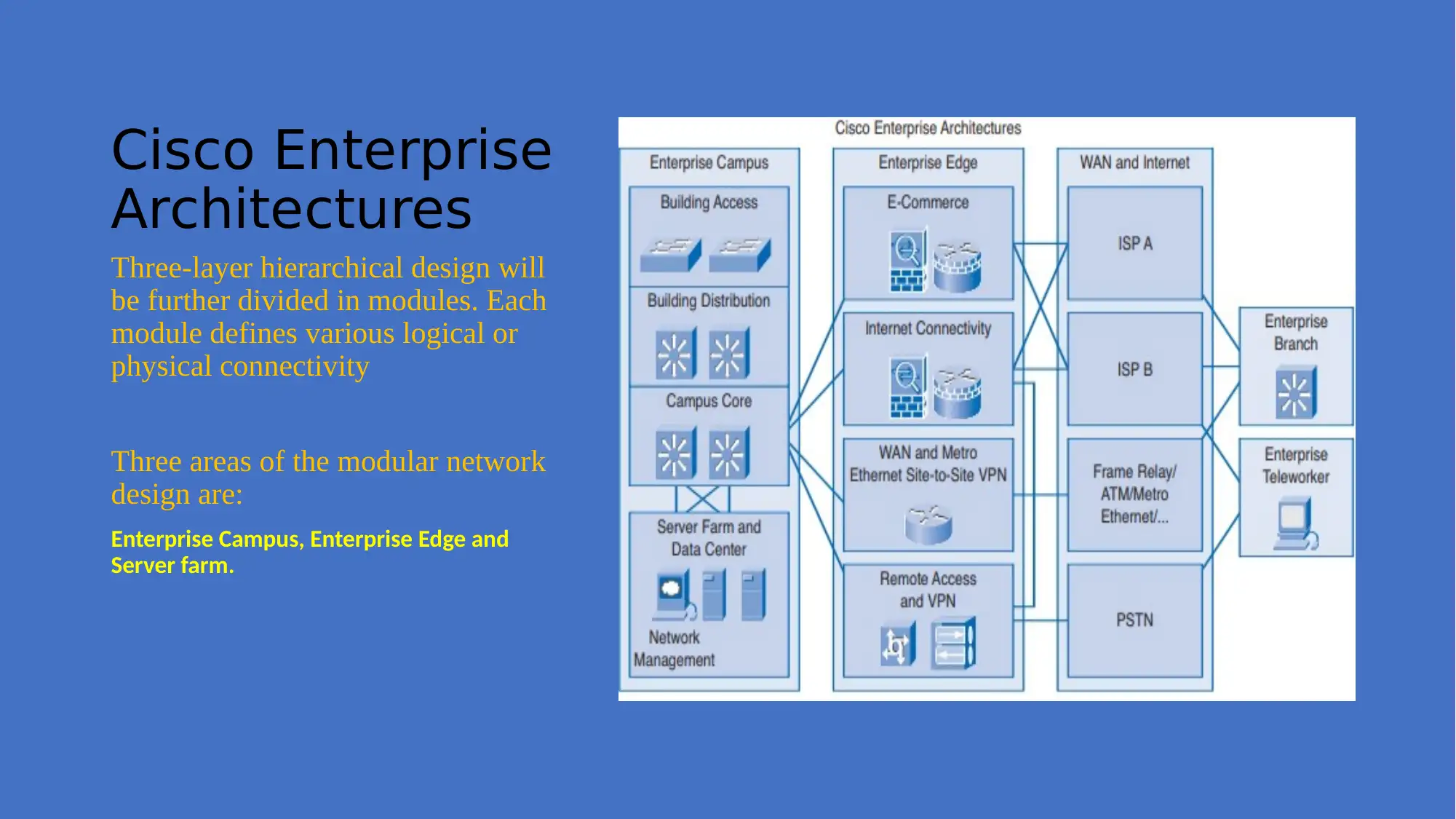
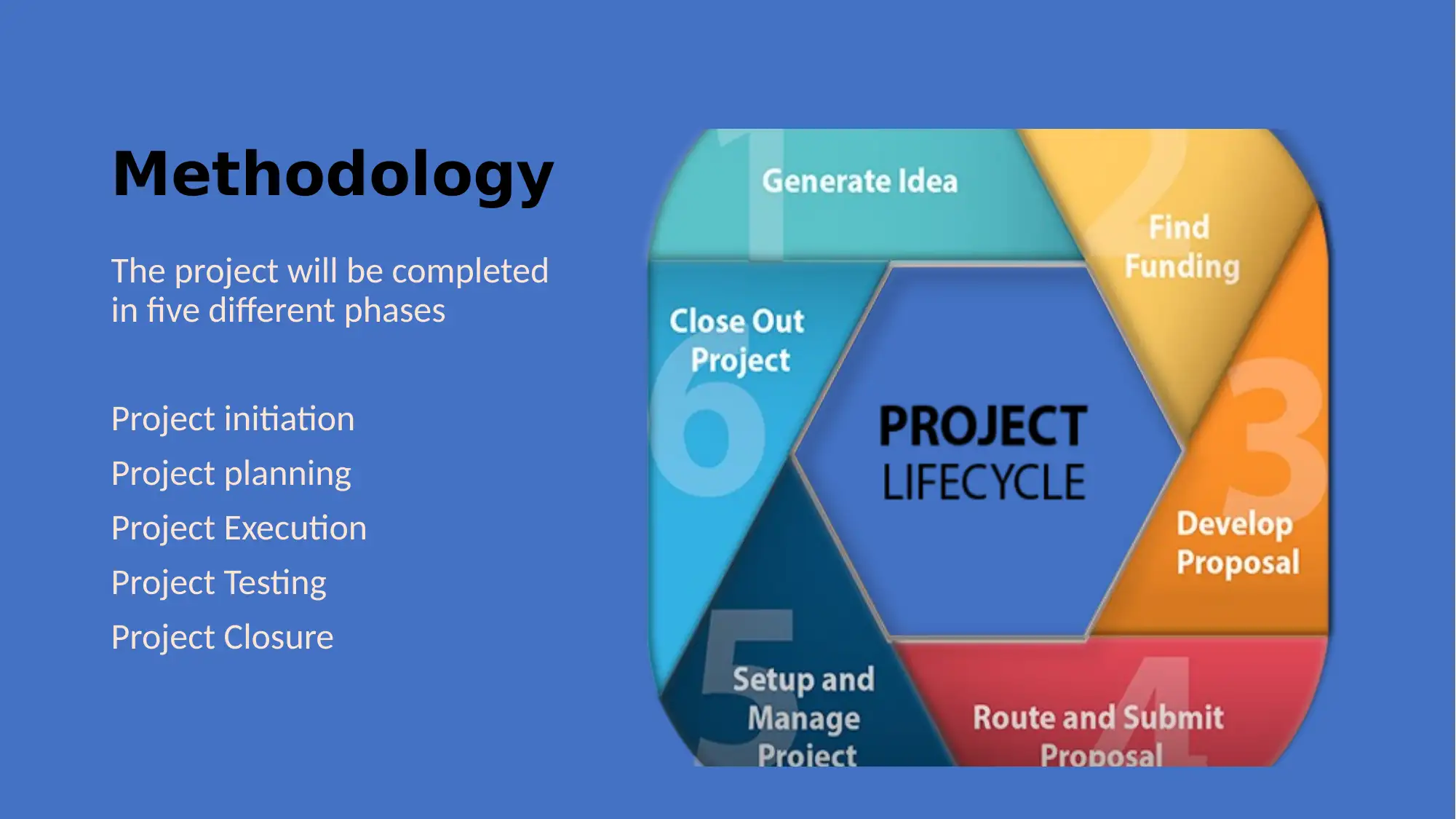
This project focuses on planning and implementing a network solution for Adatum, aiming to control operational costs, prevent issues, enhance security, and ensure high network availability. The proposed solution involves a hierarchical network design consisting of core, distribution, and access layers. The core layer provides high-speed connectivity, the distribution layer manages traffic and enforces access control, and the access layer handles user access to internetwork resources. The project methodology includes initiation, planning, execution, testing, and closure phases. References to relevant research articles support the design and implementation strategies.
1 out of 11










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)