University Project: Developing a Security Awareness Policy Document
VerifiedAdded on 2022/09/18
|4
|1089
|180
Project
AI Summary
This document presents a comprehensive security awareness and training policy project. It begins with a structured overview of the policy document, including elements such as policy definition, purpose, scope, target audience, objectives, standards, roles, responsibilities, procedures, compliance, non-compliance, references, and contact information. The document also includes a revision history to track updates. The project addresses IT asset inventory, including asset classification schema, and delves into the auditing of network devices, specifically routers, highlighting key aspects to examine. It references security frameworks like NIST, HIPAA, PCI-DSS, and ISO 27001. The assignment requires students to develop and document a security policy for an organization, covering various aspects of security awareness and training, and includes an example policy framework and elements for the final project.
Final project
Policy Document Structure &
Policy Elements
Please refer to the policy elements and the policy document
structure written below for your final project. You shall consider
most of policy elements that given below when you are writing or
developing your organization policy.
1. You need to use the table below to document the policy that you are going
to develop and give a brief information about the approved policy.
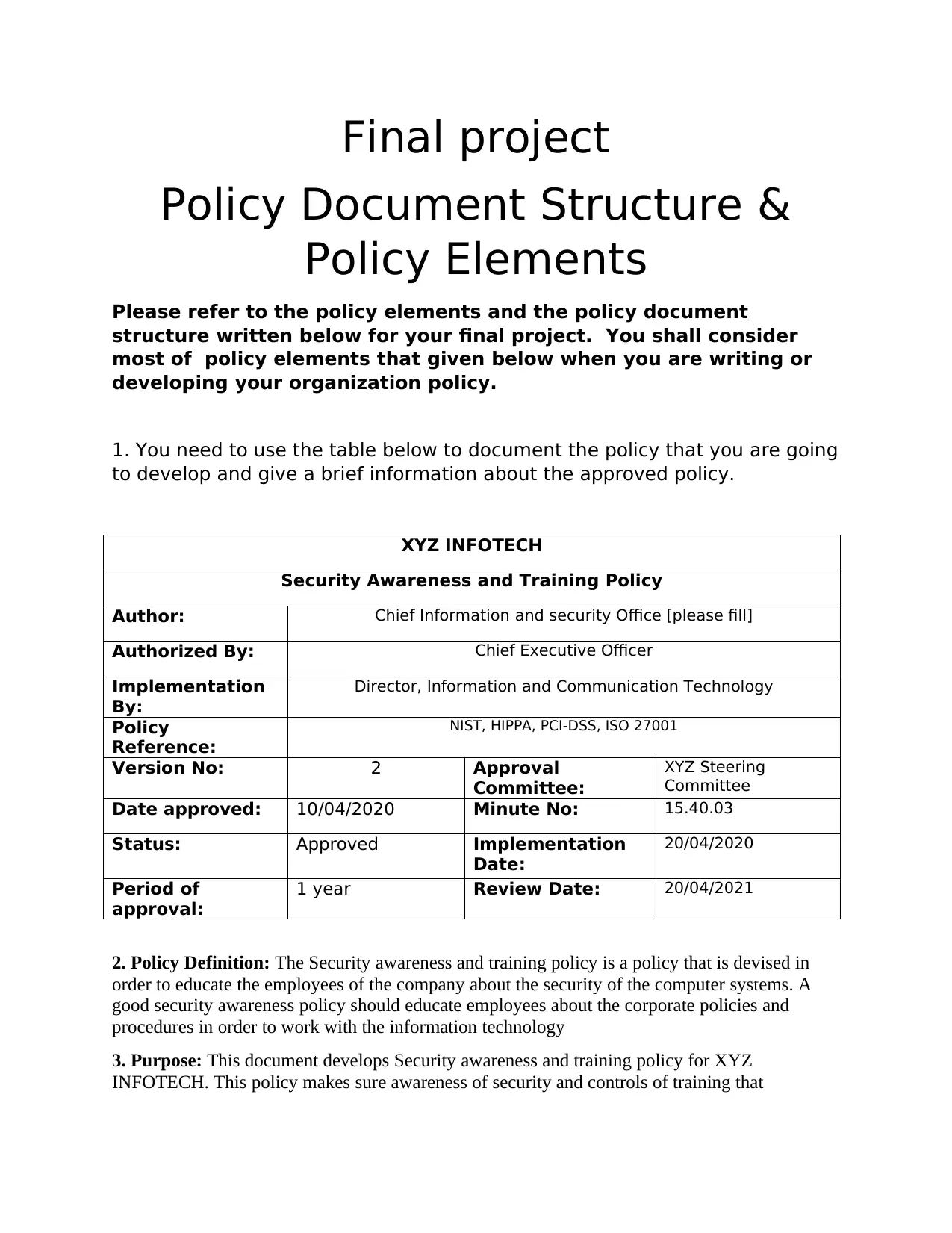
XYZ INFOTECH
Security Awareness and Training Policy
Author: Chief Information and security Office [please fill]
Authorized By: Chief Executive Officer
Implementation
By:
Director, Information and Communication Technology
Policy
Reference:
NIST, HIPPA, PCI-DSS, ISO 27001
Version No: 2 Approval
Committee:
XYZ Steering
Committee
Date approved: 10/04/2020 Minute No: 15.40.03
Status: Approved Implementation
Date:
20/04/2020
Period of
approval:
1 year Review Date: 20/04/2021
2. Policy Definition: The Security awareness and training policy is a policy that is devised in
order to educate the employees of the company about the security of the computer systems. A
good security awareness policy should educate employees about the corporate policies and
procedures in order to work with the information technology
3. Purpose: This document develops Security awareness and training policy for XYZ
INFOTECH. This policy makes sure awareness of security and controls of training that
Policy Document Structure &
Policy Elements
Please refer to the policy elements and the policy document
structure written below for your final project. You shall consider
most of policy elements that given below when you are writing or
developing your organization policy.
1. You need to use the table below to document the policy that you are going
to develop and give a brief information about the approved policy.
XYZ INFOTECH
Security Awareness and Training Policy
Author: Chief Information and security Office [please fill]
Authorized By: Chief Executive Officer
Implementation
By:
Director, Information and Communication Technology
Policy
Reference:
NIST, HIPPA, PCI-DSS, ISO 27001
Version No: 2 Approval
Committee:
XYZ Steering
Committee
Date approved: 10/04/2020 Minute No: 15.40.03
Status: Approved Implementation
Date:
20/04/2020
Period of
approval:
1 year Review Date: 20/04/2021
2. Policy Definition: The Security awareness and training policy is a policy that is devised in
order to educate the employees of the company about the security of the computer systems. A
good security awareness policy should educate employees about the corporate policies and
procedures in order to work with the information technology
3. Purpose: This document develops Security awareness and training policy for XYZ
INFOTECH. This policy makes sure awareness of security and controls of training that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

safeguard the confidentiality, integrity and availability of the information resource of the
company.
4. Scope: The security policies concerns to all the employees, contractors, vendors, guests and
the other people that connect to the systems and the network of the Company that uses any
devices of computing. This policy also applies to all the connections of network and the access
connections those are remote. This security policy covers all the technical deployments of remote
or local access that is utilized in order to connect to the network of the Company.
5. Target Audience or Applicability: The security framed by the XYZ INFORTECH will be
applicable to all the members of the company, the employees of the company, guests, vendors,
contractors and the third parties that utilize the systems and the network of the Company.
6. Objectives:
Information security is believed to protect three major goals:
Confidentiality – the assets of data and information must be restricted to
people those are authorized to access and not be revealed to others;
Integrity – keeping the data undamaged, absolute and exact, and IT systems
operational;
Availability – an aim representing that information or system that is at
removal of users those are authorized when required.
7. Standard: The Company should maintain several standards regarding the security
awareness and the training policies. The standards include:
The awareness of security must be conducted once a year by the Company
Upgrading the awareness of the requirement in order to safeguard the assets of
information
Making sure that users appreciate their responsibilities in order to protect the information
resources
Making sure that users are knowledgeable about the security policies of the company and
develop skills in order to perform their skills securely
The employees will be trained as soon as they will be recruited to the company.
8. Roles and Responsibilities: In association with the human resources, the department of
information technology will develop and facilitate the Security and awareness program, make
sure that all the employees of the company get proper security training related to their
responsibilities and maintain records of the training that is received. This policy is owned by
the Vice President and the CEO of the company and they will co-ordinate and revisions in
the security policy
9. Procedures and Guidelines: The procedures and the guidelines of the XYZ INFOTECH
include the following:
Employee security awareness training: All the employees of the company that have access to the
information resources of the company must complete their training within first 30 days of their
recruitment in the company. The training must be completed yearly and a person must be hired
in order to train the employees
company.
4. Scope: The security policies concerns to all the employees, contractors, vendors, guests and
the other people that connect to the systems and the network of the Company that uses any
devices of computing. This policy also applies to all the connections of network and the access
connections those are remote. This security policy covers all the technical deployments of remote
or local access that is utilized in order to connect to the network of the Company.
5. Target Audience or Applicability: The security framed by the XYZ INFORTECH will be
applicable to all the members of the company, the employees of the company, guests, vendors,
contractors and the third parties that utilize the systems and the network of the Company.
6. Objectives:
Information security is believed to protect three major goals:
Confidentiality – the assets of data and information must be restricted to
people those are authorized to access and not be revealed to others;
Integrity – keeping the data undamaged, absolute and exact, and IT systems
operational;
Availability – an aim representing that information or system that is at
removal of users those are authorized when required.
7. Standard: The Company should maintain several standards regarding the security
awareness and the training policies. The standards include:
The awareness of security must be conducted once a year by the Company
Upgrading the awareness of the requirement in order to safeguard the assets of
information
Making sure that users appreciate their responsibilities in order to protect the information
resources
Making sure that users are knowledgeable about the security policies of the company and
develop skills in order to perform their skills securely
The employees will be trained as soon as they will be recruited to the company.
8. Roles and Responsibilities: In association with the human resources, the department of
information technology will develop and facilitate the Security and awareness program, make
sure that all the employees of the company get proper security training related to their
responsibilities and maintain records of the training that is received. This policy is owned by
the Vice President and the CEO of the company and they will co-ordinate and revisions in
the security policy
9. Procedures and Guidelines: The procedures and the guidelines of the XYZ INFOTECH
include the following:
Employee security awareness training: All the employees of the company that have access to the
information resources of the company must complete their training within first 30 days of their
recruitment in the company. The training must be completed yearly and a person must be hired
in order to train the employees

Role-based security awareness training: Additional role-based security awareness training will be
provided to the employees of the company whose responsibilities need elevated access such as
access to the confidential information. The role based training must be finished on a annual basis
as needed by the compliance programs.
10. Compliance and Enforcement: the compliance with the security policy of the company is
compulsory. If the employees, contractors, consultants and third parties breach these policies,
the organization has the right to take the corresponding actions and termination of the employee
or the other members.
11. Non-Compliance and Exceptions: Exceptions to any of the compliance with the security
policy should be approved by the department of information technology of the Company. This
may need authorization from the Vice president of the Company, the Committee of Corporate
Affairs or the CEO of the Company. These Policies must be documented, recorded and examined
formally by the XYZ INFOTECH.
provided to the employees of the company whose responsibilities need elevated access such as
access to the confidential information. The role based training must be finished on a annual basis
as needed by the compliance programs.
10. Compliance and Enforcement: the compliance with the security policy of the company is
compulsory. If the employees, contractors, consultants and third parties breach these policies,
the organization has the right to take the corresponding actions and termination of the employee
or the other members.
11. Non-Compliance and Exceptions: Exceptions to any of the compliance with the security
policy should be approved by the department of information technology of the Company. This
may need authorization from the Vice president of the Company, the Committee of Corporate
Affairs or the CEO of the Company. These Policies must be documented, recorded and examined
formally by the XYZ INFOTECH.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

12. References: Several frameworks must be followed by the company. The frameworks that
will be followed by the company include NIST, HIPAA, PCI-DSS and ISO 27000 and NIST
SP 800-53
13. Contacts: In order to know about the security and awareness policies of the company, the
chief security information officer must be contacted for more information. The contact number
of the CISO will be provided in the website of the company. The Steering committee can also be
contacted for more supported. All these information will be available in the website of the XYZ
INFOTECH.
14. Revision History
You need to use the table below to record the latest approved policy and
append it to the list in the revision history.
Revision History
Revision Date Revision Revision Made by
20/08/2019
References were
made to several
standards like NIST,
HIPAA and more
[Please Fill]
15/01/2020
Non-compliance and
exceptions were
added to the
security policies
[Please Fill]
15. Authorized and signed by:
[Please Fill], Chief information security officer
[Please Fill], XYZ INFOTECH Chief Executive Officer
will be followed by the company include NIST, HIPAA, PCI-DSS and ISO 27000 and NIST
SP 800-53
13. Contacts: In order to know about the security and awareness policies of the company, the
chief security information officer must be contacted for more information. The contact number
of the CISO will be provided in the website of the company. The Steering committee can also be
contacted for more supported. All these information will be available in the website of the XYZ
INFOTECH.
14. Revision History
You need to use the table below to record the latest approved policy and
append it to the list in the revision history.
Revision History
Revision Date Revision Revision Made by
20/08/2019
References were
made to several
standards like NIST,
HIPAA and more
[Please Fill]
15/01/2020
Non-compliance and
exceptions were
added to the
security policies
[Please Fill]
15. Authorized and signed by:
[Please Fill], Chief information security officer
[Please Fill], XYZ INFOTECH Chief Executive Officer
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





