Potential Threats and Mitigation Tools for Ransomware
VerifiedAdded on 2023/06/10
|10
|2689
|368
AI Summary
This report discusses the potential threats and mitigation tools for ransomware attacks. It covers the working mechanism of ransomware, recent attacks, and variants of ransomware. It also provides information on mitigation tools such as Windows AppLocker and Enhanced Mitigation Experience Toolkit (EMET).
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
Potential Threats and Mitigation Tools for Ransomware
Name of the Student
Name of the University
Author’s note
Potential Threats and Mitigation Tools for Ransomware
Name of the Student
Name of the University
Author’s note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
Table of Contents
1. Introduction.......................................................................................................................................2
2. Variants of Ransomware....................................................................................................................2
3. Working Mechanism of Ransomware................................................................................................3
4. Potential Threats...............................................................................................................................3
5. Recent Attacks...................................................................................................................................4
6. Mitigation Tools.................................................................................................................................4
7. Summary...........................................................................................................................................5
8. References.........................................................................................................................................7
Table of Contents
1. Introduction.......................................................................................................................................2
2. Variants of Ransomware....................................................................................................................2
3. Working Mechanism of Ransomware................................................................................................3
4. Potential Threats...............................................................................................................................3
5. Recent Attacks...................................................................................................................................4
6. Mitigation Tools.................................................................................................................................4
7. Summary...........................................................................................................................................5
8. References.........................................................................................................................................7

2POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
1. Introduction
Ransomware is a form of malicious software that would be able to threaten the computer of
users with the denial of access on the personal data of the user. It could be defined as the subset of
a malware. The data would be locked with the help of encryption and then payment is demanded.
The primary motive for ransomware is based on monetary aspects. The access to the files are denied
and the victims are charged with ransom amounts for decrypting the files [10].
Unlike most of the other forms of malware, the ransomware normally infects computers by
clicking on any unsafe link or while downloading some form of unsafe programs. The society
normally gets affected as the data, which is stored in various servers of top companies gets affected.
This might lead to permanent or temporary loss of information and also incur financial losses.
Another form of social impacts would include the disruption of regular operations within the
targeted organization. This would lead to potential harm to the concerned organization.
2. Variants of Ransomware
The five variants of ransomware in the recent times are: CryptoLocker, TeslaCrypt,
SimpleLocker, WannaCry and NotPetya.
The report would primarily focus on the WannaCry ransomware. The WannaCry
ransomware is a recent form of ransomware worm that is capable of spreading a vast number of
computing networks that had attacked the computers in the month of May in 2017. The
ransomware spreads by affecting and infecting a Windows computer. It would encrypt the user data
that is stored on the hard drive, thus making it extremely impossible for the users for accessing
them. The system would then demand a ransom amount of money that would be paid in terms of
bitcoin cryptocurrency. After the money is received by the hackers, they would grant the access to
the user [1]. The ransomware mainly broadcasted through an exploit, EternalBlue within the older
model of the Windows operating system. The WannaCry ransomware took the advantages of
installation within the backdoors of the older systems.
The WannaCry ransomware had struck a vast number of important and high-profile systems
that had included the National Health Service of Britain. The ransomware had exploited the
vulnerability within the Windows based computers. The ransomware was firstly detected by the
United States National Security Agency. The agency had links with Symantec and other researchers
based within the Lazarus Group. The spread of the ransomware was stopped within few days of
discovery with the latest security patches that were released by Microsoft. A discovery that was
1. Introduction
Ransomware is a form of malicious software that would be able to threaten the computer of
users with the denial of access on the personal data of the user. It could be defined as the subset of
a malware. The data would be locked with the help of encryption and then payment is demanded.
The primary motive for ransomware is based on monetary aspects. The access to the files are denied
and the victims are charged with ransom amounts for decrypting the files [10].
Unlike most of the other forms of malware, the ransomware normally infects computers by
clicking on any unsafe link or while downloading some form of unsafe programs. The society
normally gets affected as the data, which is stored in various servers of top companies gets affected.
This might lead to permanent or temporary loss of information and also incur financial losses.
Another form of social impacts would include the disruption of regular operations within the
targeted organization. This would lead to potential harm to the concerned organization.
2. Variants of Ransomware
The five variants of ransomware in the recent times are: CryptoLocker, TeslaCrypt,
SimpleLocker, WannaCry and NotPetya.
The report would primarily focus on the WannaCry ransomware. The WannaCry
ransomware is a recent form of ransomware worm that is capable of spreading a vast number of
computing networks that had attacked the computers in the month of May in 2017. The
ransomware spreads by affecting and infecting a Windows computer. It would encrypt the user data
that is stored on the hard drive, thus making it extremely impossible for the users for accessing
them. The system would then demand a ransom amount of money that would be paid in terms of
bitcoin cryptocurrency. After the money is received by the hackers, they would grant the access to
the user [1]. The ransomware mainly broadcasted through an exploit, EternalBlue within the older
model of the Windows operating system. The WannaCry ransomware took the advantages of
installation within the backdoors of the older systems.
The WannaCry ransomware had struck a vast number of important and high-profile systems
that had included the National Health Service of Britain. The ransomware had exploited the
vulnerability within the Windows based computers. The ransomware was firstly detected by the
United States National Security Agency. The agency had links with Symantec and other researchers
based within the Lazarus Group. The spread of the ransomware was stopped within few days of
discovery with the latest security patches that were released by Microsoft. A discovery that was

3POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
known as kill switch was installed within the computers in order to prevent the infected computers
from the further spread of the WannaCry ransomware [1].
3. Working Mechanism of Ransomware
The ransomware depends on the deep web technology. This allows the cybercriminals in
order to purchase and thus use a software tool in order to create a form of ransomware that would
have specific capabilities. The malware would then be generated for their own purposes [6].
The working principle of ransomware is as follows:
1. The end user would receive an email that would appear as important.
2. The link within the email would open to a browser that would direct the user to a certain
website, which would appear to be legitimate.
3. Upon opening the page, the hosting web server would exploit the toolkit that would begin
to communicate with the machine of the victim.
4. Whenever a vulnerable version of toolkit would be confirmed, the kit would attempt to
exploit the vulnerability.
5. After the encryption of the files of the victims, the malware would send the encryption
key to the command and control server.
6. The server would then send a message to the victim to whom the malware has been sent
[8].
4. Potential Threats
Screen Lockup – These are one type of ransomware attacks on the computer systems in
which the malware that infects the host computer would be able to hold direct access to the data
within the hard drive of the computer. The main hosts of the malware would include the private and
confidential information of the customers or organization. The screen locking ransomware mainly
holds the entire system as a hostage [4]. The ransomware spreads by affecting and infecting a
Windows computer. It would encrypt the user data that is stored on the hard drive, thus making it
extremely impossible for the users for accessing them. The system would then demand a ransom
amount of money that would be paid in terms of bitcoin cryptocurrency. When these kinds of
ransomware affects the systems, they ensure that the screen of the user would freeze and that the
affected user would not be able to access the computing system. It would be extremely hard to
known as kill switch was installed within the computers in order to prevent the infected computers
from the further spread of the WannaCry ransomware [1].
3. Working Mechanism of Ransomware
The ransomware depends on the deep web technology. This allows the cybercriminals in
order to purchase and thus use a software tool in order to create a form of ransomware that would
have specific capabilities. The malware would then be generated for their own purposes [6].
The working principle of ransomware is as follows:
1. The end user would receive an email that would appear as important.
2. The link within the email would open to a browser that would direct the user to a certain
website, which would appear to be legitimate.
3. Upon opening the page, the hosting web server would exploit the toolkit that would begin
to communicate with the machine of the victim.
4. Whenever a vulnerable version of toolkit would be confirmed, the kit would attempt to
exploit the vulnerability.
5. After the encryption of the files of the victims, the malware would send the encryption
key to the command and control server.
6. The server would then send a message to the victim to whom the malware has been sent
[8].
4. Potential Threats
Screen Lockup – These are one type of ransomware attacks on the computer systems in
which the malware that infects the host computer would be able to hold direct access to the data
within the hard drive of the computer. The main hosts of the malware would include the private and
confidential information of the customers or organization. The screen locking ransomware mainly
holds the entire system as a hostage [4]. The ransomware spreads by affecting and infecting a
Windows computer. It would encrypt the user data that is stored on the hard drive, thus making it
extremely impossible for the users for accessing them. The system would then demand a ransom
amount of money that would be paid in terms of bitcoin cryptocurrency. When these kinds of
ransomware affects the systems, they ensure that the screen of the user would freeze and that the
affected user would not be able to access the computing system. It would be extremely hard to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
manipulate the system in any form. The system would then only be accessible to the owner once the
entire sum of money has been paid to the attacker.
Encrypting and Decrypting of Files - The encryption of ransomware is the technique based
on the combination of innovative algorithms that are primarily intended for blocking access to
confidential files [3]. Hence they would require a huge amount from the victim for the decryption of
files. Some of the encrypting ransomware are CryptoLocker and the most recent form of encrypting
ransomware is WannaCrypt.
There are various decryption tools, which are provided by various antivirus companies that
are available at free costs. Some of the companies such as AVG Technologies and AVAST Softwares
mainly offer various decryption tools such as Alcatraz Locker, BadBlock, CrySiS, TeslaCrypt and many
others [5].
5. Recent Attacks
One of the recent attacks of ransomware is WannaCry, which occurred in May 2017. It was a
worldwide attack on cyber systems that had mainly spread with the help of cryptoworm. The
ransomware mainly targeted those computers that were operated on the Microsoft Windows
operating system [14]. The ransomware had encrypted all the necessary files within the targeted
computer. The affected user had to pay an amount of $300 in bitcoin cryptocurrency in order to
decrypt the files. The attack by the ransomware had impacted on a huge number of businesses,
hospitals and various institutions from all over the world. There was an estimate that around
2,00,000 to 3,00,000 systems of computers were affected within this attack that had spread across
150 countries. Cyber security experts advised the people from all over the world to prevent the
payment functionality within the application. Microsoft had immediately launched their emergency
patches of security based on Windows 7, Windows 8 and also out of the band patches of security for
their other products such as Windows XP, Windows Server 2003 and other products [12].
manipulate the system in any form. The system would then only be accessible to the owner once the
entire sum of money has been paid to the attacker.
Encrypting and Decrypting of Files - The encryption of ransomware is the technique based
on the combination of innovative algorithms that are primarily intended for blocking access to
confidential files [3]. Hence they would require a huge amount from the victim for the decryption of
files. Some of the encrypting ransomware are CryptoLocker and the most recent form of encrypting
ransomware is WannaCrypt.
There are various decryption tools, which are provided by various antivirus companies that
are available at free costs. Some of the companies such as AVG Technologies and AVAST Softwares
mainly offer various decryption tools such as Alcatraz Locker, BadBlock, CrySiS, TeslaCrypt and many
others [5].
5. Recent Attacks
One of the recent attacks of ransomware is WannaCry, which occurred in May 2017. It was a
worldwide attack on cyber systems that had mainly spread with the help of cryptoworm. The
ransomware mainly targeted those computers that were operated on the Microsoft Windows
operating system [14]. The ransomware had encrypted all the necessary files within the targeted
computer. The affected user had to pay an amount of $300 in bitcoin cryptocurrency in order to
decrypt the files. The attack by the ransomware had impacted on a huge number of businesses,
hospitals and various institutions from all over the world. There was an estimate that around
2,00,000 to 3,00,000 systems of computers were affected within this attack that had spread across
150 countries. Cyber security experts advised the people from all over the world to prevent the
payment functionality within the application. Microsoft had immediately launched their emergency
patches of security based on Windows 7, Windows 8 and also out of the band patches of security for
their other products such as Windows XP, Windows Server 2003 and other products [12].
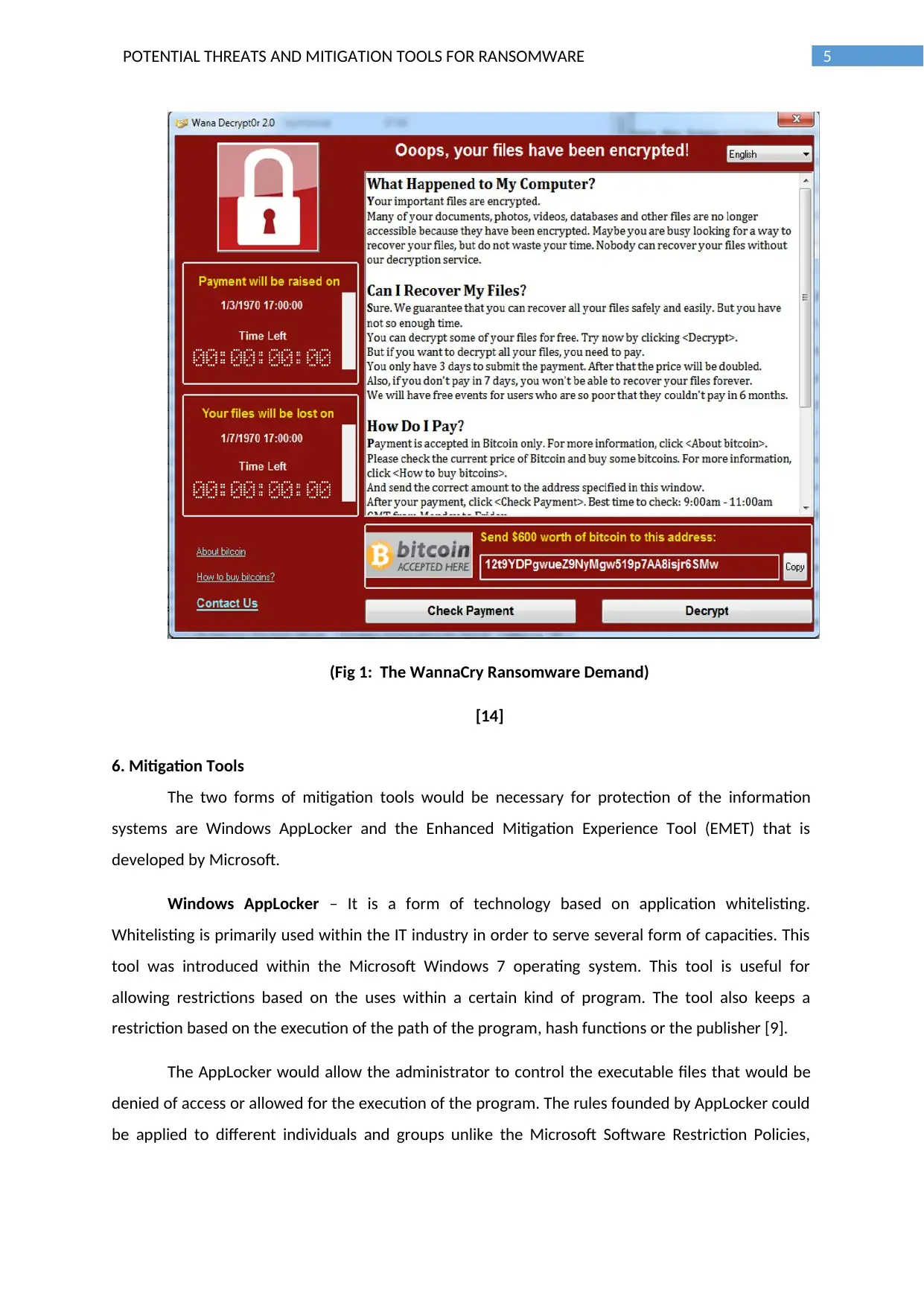
5POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
(Fig 1: The WannaCry Ransomware Demand)
[14]
6. Mitigation Tools
The two forms of mitigation tools would be necessary for protection of the information
systems are Windows AppLocker and the Enhanced Mitigation Experience Tool (EMET) that is
developed by Microsoft.
Windows AppLocker – It is a form of technology based on application whitelisting.
Whitelisting is primarily used within the IT industry in order to serve several form of capacities. This
tool was introduced within the Microsoft Windows 7 operating system. This tool is useful for
allowing restrictions based on the uses within a certain kind of program. The tool also keeps a
restriction based on the execution of the path of the program, hash functions or the publisher [9].
The AppLocker would allow the administrator to control the executable files that would be
denied of access or allowed for the execution of the program. The rules founded by AppLocker could
be applied to different individuals and groups unlike the Microsoft Software Restriction Policies,
(Fig 1: The WannaCry Ransomware Demand)
[14]
6. Mitigation Tools
The two forms of mitigation tools would be necessary for protection of the information
systems are Windows AppLocker and the Enhanced Mitigation Experience Tool (EMET) that is
developed by Microsoft.
Windows AppLocker – It is a form of technology based on application whitelisting.
Whitelisting is primarily used within the IT industry in order to serve several form of capacities. This
tool was introduced within the Microsoft Windows 7 operating system. This tool is useful for
allowing restrictions based on the uses within a certain kind of program. The tool also keeps a
restriction based on the execution of the path of the program, hash functions or the publisher [9].
The AppLocker would allow the administrator to control the executable files that would be
denied of access or allowed for the execution of the program. The rules founded by AppLocker could
be applied to different individuals and groups unlike the Microsoft Software Restriction Policies,

6POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
which was primarily set for the operating systems of Windows XP and Windows Server. The set
policies are meant to group the different individuals within different levels of enforcement [2].
Enhanced Mitigation Experience Toolkit (EMET) – This is a form of freeware toolkit meant
for security options within the Microsoft Windows operating system and was developed by
Microsoft. This tool provides a unified form of interface that would be able to finely tune the security
features of Windows. This toolkit can be added as an additional level of security defence against any
form of malware attacks. The EMET helps in supporting for the protection of ransomware that the
distributor would have to defeat before the exploitation of the vulnerabilities of security on a
personal computer [11].
The EMET also possesses the feature of Certificate Trust. This feature would be able to
prevent and stop the man-in-the-middle attacks on the system that would mainly make use of the
public key infrastructure (PKI). The individual customers would be able to make use of the EMET
toolkit and thus would be able to deploy the tool across several levels of the enterprise. The EMET
toolkit is primarily targeted at various system administrators [13]. However the newest version
would be mostly supported for any version of Windows that are running on the Windows 7 or later
versions of the operating system. The older versions of the tool could be used on Windows XP but
has certain exceptions as all the features would not be implemented. The version 4.1 of the EMET
was one of the last version for supporting Windows XP.
These tools are extremely crucial for protecting against the severe forms of ransomware
attacks. The attacks are highly important for consideration as they charge huge level of bitcoin
cryptocurrency. The users have to pay the charged amount in order to gain access to their important
contents [7].
7. Summary
Based on the discussion from the above report, it can be concluded that the ransomware
attacks are a matter of deep consideration. The ransomware attacks has proved to have a major
level of impact, which could be highly devastating for various small business organizations and their
respective owners. Ransomware does not only provides threats to various kind of small or medium-
sized businesses but they also have a huge level of impact on the people. Based on the reports of
FBI, it could be discussed that the simply paying a ransom amount would not ensure that the
affected victim would be provided with the necessary files. The report also puts focus on the various
form of tools that would be necessary in order to secure the computers against the various forms of
attacks. Different types of efficient tools would be highly necessary in order to secure the system.
which was primarily set for the operating systems of Windows XP and Windows Server. The set
policies are meant to group the different individuals within different levels of enforcement [2].
Enhanced Mitigation Experience Toolkit (EMET) – This is a form of freeware toolkit meant
for security options within the Microsoft Windows operating system and was developed by
Microsoft. This tool provides a unified form of interface that would be able to finely tune the security
features of Windows. This toolkit can be added as an additional level of security defence against any
form of malware attacks. The EMET helps in supporting for the protection of ransomware that the
distributor would have to defeat before the exploitation of the vulnerabilities of security on a
personal computer [11].
The EMET also possesses the feature of Certificate Trust. This feature would be able to
prevent and stop the man-in-the-middle attacks on the system that would mainly make use of the
public key infrastructure (PKI). The individual customers would be able to make use of the EMET
toolkit and thus would be able to deploy the tool across several levels of the enterprise. The EMET
toolkit is primarily targeted at various system administrators [13]. However the newest version
would be mostly supported for any version of Windows that are running on the Windows 7 or later
versions of the operating system. The older versions of the tool could be used on Windows XP but
has certain exceptions as all the features would not be implemented. The version 4.1 of the EMET
was one of the last version for supporting Windows XP.
These tools are extremely crucial for protecting against the severe forms of ransomware
attacks. The attacks are highly important for consideration as they charge huge level of bitcoin
cryptocurrency. The users have to pay the charged amount in order to gain access to their important
contents [7].
7. Summary
Based on the discussion from the above report, it can be concluded that the ransomware
attacks are a matter of deep consideration. The ransomware attacks has proved to have a major
level of impact, which could be highly devastating for various small business organizations and their
respective owners. Ransomware does not only provides threats to various kind of small or medium-
sized businesses but they also have a huge level of impact on the people. Based on the reports of
FBI, it could be discussed that the simply paying a ransom amount would not ensure that the
affected victim would be provided with the necessary files. The report also puts focus on the various
form of tools that would be necessary in order to secure the computers against the various forms of
attacks. Different types of efficient tools would be highly necessary in order to secure the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
The IT systems should be updated according to the latest security patches such that they would be
able to detect any form of unwanted intrusion within the system.
The IT systems should be updated according to the latest security patches such that they would be
able to detect any form of unwanted intrusion within the system.

8POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
8. References
[1]. Chen, Q. and Bridges, R.A., 2017. Automated Behavioral Analysis of Malware A Case Study of
WannaCry Ransomware. arXiv preprint arXiv:1709.08753.
[2]. Durve, R. and Bouridane, A., 2017, September. Windows 10 security hardening using device
guard whitelisting and Applocker blacklisting. In Emerging Security Technologies (EST), 2017 Seventh
International Conference on (pp. 56-61). IEEE.
[3]. Scaife, N., Carter, H., Traynor, P. and Butler, K.R., 2016, June. Cryptolock (and drop it): stopping
ransomware attacks on user data. In Distributed Computing Systems (ICDCS), 2016 IEEE 36th
International Conference on (pp. 303-312). IEEE.
[4]. Lincke, S., 2015. Security Awareness: Brave New World. In Security Planning (pp. 3-18). Springer,
Cham.
[5]. Wyke, J. and Ajjan, A., 2015. The current state of ransomware. SophosLabs technical paper.
[6]. Ganorkar, S.S. and Kandasamy, K., 2017. Understanding and defending crypto-
ransomware. ARPN Journal of Engineering and Applied Sciences, 12, pp.3920-3925.
[7]. Pappas, V., Polychronakis, M. and Keromytis, A.D., 2014, September. Dynamic reconstruction of
relocation information for stripped binaries. In International Workshop on Recent Advances in
Intrusion Detection (pp. 68-87). Springer, Cham.
[8]. Wu, Y., Fong, S. and Zhuang, Y., 2017, December. General Precautions against Security Threats
for Computer Networks in SMEs: From the Perspective of Big Data and IOT. In Proceedings of the
International Conference on Big Data and Internet of Thing (pp. 134-140). ACM.
[9]. Salah, K., Calero, J.M.A., Bernabé, J.B., Perez, J.M.M. and Zeadally, S., 2013. Analyzing the
security of Windows 7 and Linux for cloud computing. computers & security, 34, pp.113-122.
[10]. Mercaldo, F., Nardone, V., Santone, A. and Visaggio, C.A., 2016, June. Ransomware steals your
phone. formal methods rescue it. In International Conference on Formal Techniques for Distributed
Objects, Components, and Systems (pp. 212-221). Springer, Cham.
[11]. Vlaszaty, B. and Rohani, H., 2014. Test the Effectiveness of the Enhanced Mitigation Experience
Toolkit Using Well-known Attacks on Well-known Binaries.
[12]. DeMuro, P.R., 2016. Keeping Internet Pirates at Bay: Ransomware Negotiation in the
Healthcare Industry. Nova L. Rev., 41, p.349.
8. References
[1]. Chen, Q. and Bridges, R.A., 2017. Automated Behavioral Analysis of Malware A Case Study of
WannaCry Ransomware. arXiv preprint arXiv:1709.08753.
[2]. Durve, R. and Bouridane, A., 2017, September. Windows 10 security hardening using device
guard whitelisting and Applocker blacklisting. In Emerging Security Technologies (EST), 2017 Seventh
International Conference on (pp. 56-61). IEEE.
[3]. Scaife, N., Carter, H., Traynor, P. and Butler, K.R., 2016, June. Cryptolock (and drop it): stopping
ransomware attacks on user data. In Distributed Computing Systems (ICDCS), 2016 IEEE 36th
International Conference on (pp. 303-312). IEEE.
[4]. Lincke, S., 2015. Security Awareness: Brave New World. In Security Planning (pp. 3-18). Springer,
Cham.
[5]. Wyke, J. and Ajjan, A., 2015. The current state of ransomware. SophosLabs technical paper.
[6]. Ganorkar, S.S. and Kandasamy, K., 2017. Understanding and defending crypto-
ransomware. ARPN Journal of Engineering and Applied Sciences, 12, pp.3920-3925.
[7]. Pappas, V., Polychronakis, M. and Keromytis, A.D., 2014, September. Dynamic reconstruction of
relocation information for stripped binaries. In International Workshop on Recent Advances in
Intrusion Detection (pp. 68-87). Springer, Cham.
[8]. Wu, Y., Fong, S. and Zhuang, Y., 2017, December. General Precautions against Security Threats
for Computer Networks in SMEs: From the Perspective of Big Data and IOT. In Proceedings of the
International Conference on Big Data and Internet of Thing (pp. 134-140). ACM.
[9]. Salah, K., Calero, J.M.A., Bernabé, J.B., Perez, J.M.M. and Zeadally, S., 2013. Analyzing the
security of Windows 7 and Linux for cloud computing. computers & security, 34, pp.113-122.
[10]. Mercaldo, F., Nardone, V., Santone, A. and Visaggio, C.A., 2016, June. Ransomware steals your
phone. formal methods rescue it. In International Conference on Formal Techniques for Distributed
Objects, Components, and Systems (pp. 212-221). Springer, Cham.
[11]. Vlaszaty, B. and Rohani, H., 2014. Test the Effectiveness of the Enhanced Mitigation Experience
Toolkit Using Well-known Attacks on Well-known Binaries.
[12]. DeMuro, P.R., 2016. Keeping Internet Pirates at Bay: Ransomware Negotiation in the
Healthcare Industry. Nova L. Rev., 41, p.349.

9POTENTIAL THREATS AND MITIGATION TOOLS FOR RANSOMWARE
[13]. Wu, J., Arrott, A. and Osorio, F.C.C., 2014, October. Protection against remote code execution
exploits of popular applications in Windows. In Malicious and Unwanted Software: The Americas
(MALWARE), 2014 9th International Conference on (pp. 26-31). IEEE.
[14]. Mohurle, S. and Patil, M., 2017. A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
[13]. Wu, J., Arrott, A. and Osorio, F.C.C., 2014, October. Protection against remote code execution
exploits of popular applications in Windows. In Malicious and Unwanted Software: The Americas
(MALWARE), 2014 9th International Conference on (pp. 26-31). IEEE.
[14]. Mohurle, S. and Patil, M., 2017. A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





