PRJM 6003: Risk Management Report on Electronic Health Records
VerifiedAdded on 2023/04/07
|7
|2738
|191
Report
AI Summary
This report identifies and analyzes the risks associated with implementing Electronic Health Records (EHR) in a hospital setting, focusing on data leakage as a primary concern. It explores causes such as hacking and malware, and uses a consequence table to qualitatively analyze risks like data breaching, financial exposure, lack of interoperability, and reduced face time with patients. The report proposes risk mitigation strategies including HIPAA security risk analysis, data encryption, and firewall implementation, evaluating the residual risks associated with each. Secondary risks, such as malicious activities embedded in encrypted code, are also addressed. The risk register summarizes identified risks, their categories, probabilities, impacts, and proposed responses, emphasizing the importance of mitigation and retention strategies. The report concludes with a personal belief in the value of EHR implementation despite the identified risks.
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Part 1
The risk event that is taken into consideration in this report is the risks that might be present in
the introduction of Electronic Health Record in the Hospital where I am working right now.
A. The one risk that is present in this project is the leaking of data.
There has been a high demand in the implementation of the Electronic Heath Record in
hospitals. The main reason of implementing this terminology is because f storage of data in
large quantity over the time period. This section also ensures that the management of the
entire data that are stored in the database gets easier as the access to the data that are
present in the database of the Electronic Health Record are higher and better. Despite these
advantage the main disadvantage that can be seen includes leaking of data through the
platform. In case the data that are stored in the database of the Electronic Health Record
includes the fact that usage of cumulative attack is performed. This helps the imposters to
get the track of data that reveals the personal informations of patients specially their name,
gender, the disease that they are having. Accessing of the entire database is performed in
this data breaching process. This data breaching is not very well intended and wanted by the
patients and their family.
B. The two major causes that are responsible for the management of the data leakage includes
hacking of the Electronic Health Record Database and introduction of Malware in the
database of the Electronic Health Record. In case of Hacking the imposter’s cracks the
security layer of the database and the password that is set is exposed and with the help of
the exposing of the password the imposters gets in the database and accesses the data that
they want to gain access to. Stealing of access credentials are the mostly used method. Over
49% of the total cyber-attacks and thefts are performed with the help of the stolen
credentials. Over 20.9% of the total attacks are performed with the help of the Brute force.
Another method is by introduction of malware in the system. This section endures the fact
that the ransomware is introduced in the system. This process has been affecting the data
storage process in a negative manner. In the section of the Malware attacks being
prosecuted, Ransomware has 70.5%. RAM scrapper attack occurs for 7%. Capturing of the
application data takes place for 3.9% of the total malware attacking process.
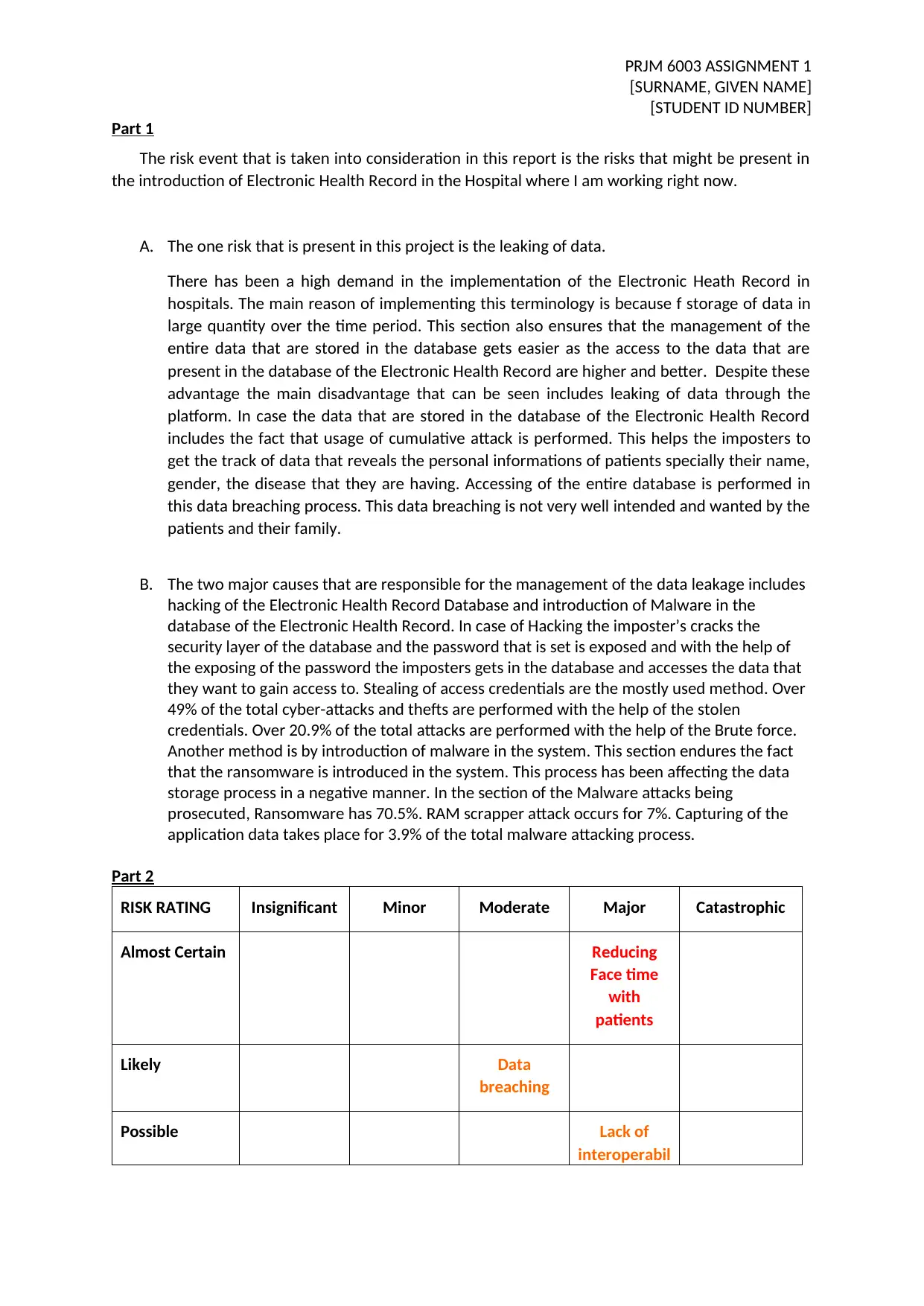
Part 2
RISK RATING Insignificant Minor Moderate Major Catastrophic
Almost Certain Reducing
Face time
with
patients
Likely Data
breaching
Possible Lack of
interoperabil
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Part 1
The risk event that is taken into consideration in this report is the risks that might be present in
the introduction of Electronic Health Record in the Hospital where I am working right now.
A. The one risk that is present in this project is the leaking of data.
There has been a high demand in the implementation of the Electronic Heath Record in
hospitals. The main reason of implementing this terminology is because f storage of data in
large quantity over the time period. This section also ensures that the management of the
entire data that are stored in the database gets easier as the access to the data that are
present in the database of the Electronic Health Record are higher and better. Despite these
advantage the main disadvantage that can be seen includes leaking of data through the
platform. In case the data that are stored in the database of the Electronic Health Record
includes the fact that usage of cumulative attack is performed. This helps the imposters to
get the track of data that reveals the personal informations of patients specially their name,
gender, the disease that they are having. Accessing of the entire database is performed in
this data breaching process. This data breaching is not very well intended and wanted by the
patients and their family.
B. The two major causes that are responsible for the management of the data leakage includes
hacking of the Electronic Health Record Database and introduction of Malware in the
database of the Electronic Health Record. In case of Hacking the imposter’s cracks the
security layer of the database and the password that is set is exposed and with the help of
the exposing of the password the imposters gets in the database and accesses the data that
they want to gain access to. Stealing of access credentials are the mostly used method. Over
49% of the total cyber-attacks and thefts are performed with the help of the stolen
credentials. Over 20.9% of the total attacks are performed with the help of the Brute force.
Another method is by introduction of malware in the system. This section endures the fact
that the ransomware is introduced in the system. This process has been affecting the data
storage process in a negative manner. In the section of the Malware attacks being
prosecuted, Ransomware has 70.5%. RAM scrapper attack occurs for 7%. Capturing of the
application data takes place for 3.9% of the total malware attacking process.
Part 2
RISK RATING Insignificant Minor Moderate Major Catastrophic
Almost Certain Reducing
Face time
with
patients
Likely Data
breaching
Possible Lack of
interoperabil
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
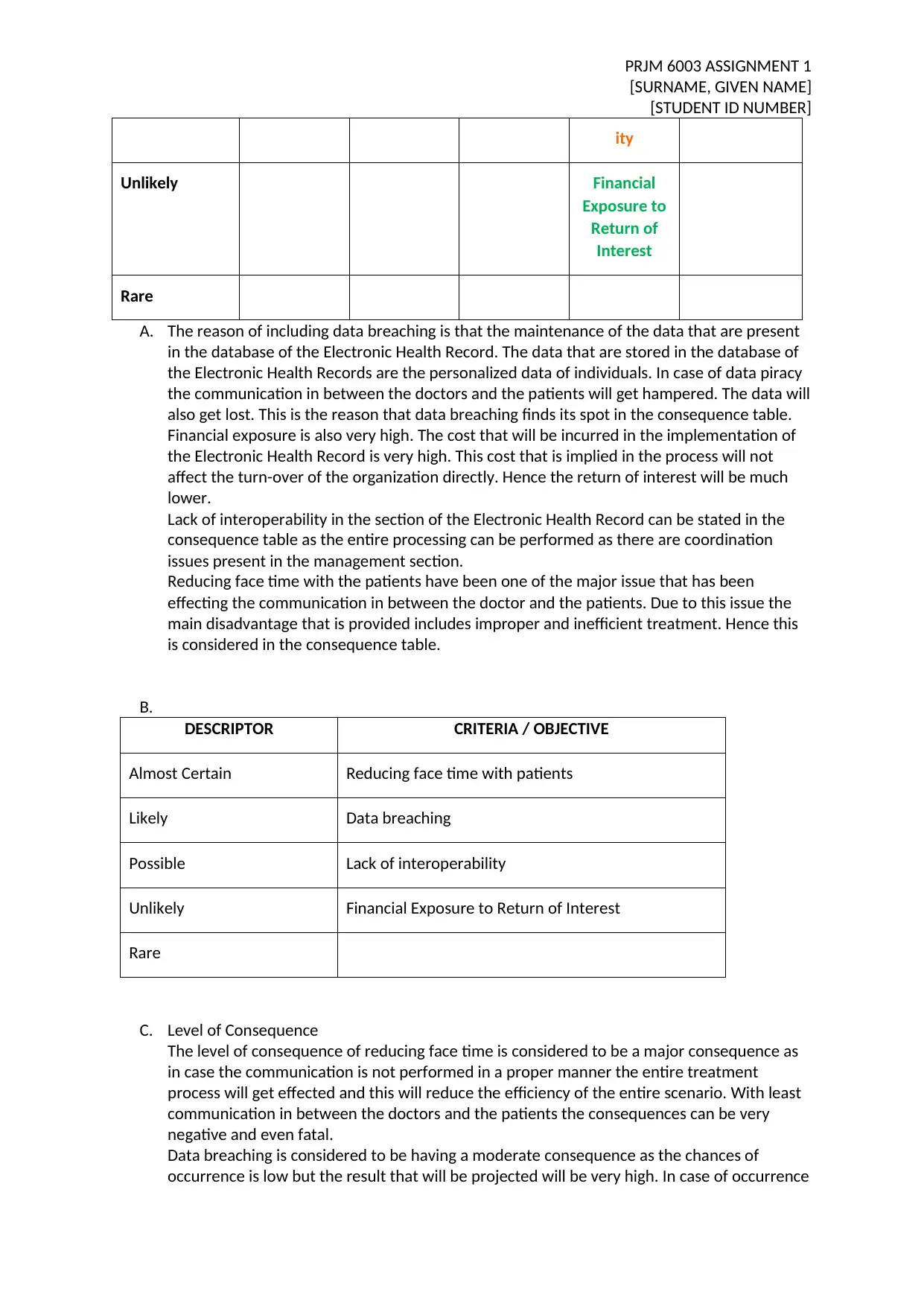
ity
Unlikely Financial
Exposure to
Return of
Interest
Rare
A. The reason of including data breaching is that the maintenance of the data that are present
in the database of the Electronic Health Record. The data that are stored in the database of
the Electronic Health Records are the personalized data of individuals. In case of data piracy
the communication in between the doctors and the patients will get hampered. The data will
also get lost. This is the reason that data breaching finds its spot in the consequence table.
Financial exposure is also very high. The cost that will be incurred in the implementation of
the Electronic Health Record is very high. This cost that is implied in the process will not
affect the turn-over of the organization directly. Hence the return of interest will be much
lower.
Lack of interoperability in the section of the Electronic Health Record can be stated in the
consequence table as the entire processing can be performed as there are coordination
issues present in the management section.
Reducing face time with the patients have been one of the major issue that has been
effecting the communication in between the doctor and the patients. Due to this issue the
main disadvantage that is provided includes improper and inefficient treatment. Hence this
is considered in the consequence table.
B.
DESCRIPTOR CRITERIA / OBJECTIVE
Almost Certain Reducing face time with patients
Likely Data breaching
Possible Lack of interoperability
Unlikely Financial Exposure to Return of Interest
Rare
C. Level of Consequence
The level of consequence of reducing face time is considered to be a major consequence as
in case the communication is not performed in a proper manner the entire treatment
process will get effected and this will reduce the efficiency of the entire scenario. With least
communication in between the doctors and the patients the consequences can be very
negative and even fatal.
Data breaching is considered to be having a moderate consequence as the chances of
occurrence is low but the result that will be projected will be very high. In case of occurrence
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
ity
Unlikely Financial
Exposure to
Return of
Interest
Rare
A. The reason of including data breaching is that the maintenance of the data that are present
in the database of the Electronic Health Record. The data that are stored in the database of
the Electronic Health Records are the personalized data of individuals. In case of data piracy
the communication in between the doctors and the patients will get hampered. The data will
also get lost. This is the reason that data breaching finds its spot in the consequence table.
Financial exposure is also very high. The cost that will be incurred in the implementation of
the Electronic Health Record is very high. This cost that is implied in the process will not
affect the turn-over of the organization directly. Hence the return of interest will be much
lower.
Lack of interoperability in the section of the Electronic Health Record can be stated in the
consequence table as the entire processing can be performed as there are coordination
issues present in the management section.
Reducing face time with the patients have been one of the major issue that has been
effecting the communication in between the doctor and the patients. Due to this issue the
main disadvantage that is provided includes improper and inefficient treatment. Hence this
is considered in the consequence table.
B.
DESCRIPTOR CRITERIA / OBJECTIVE
Almost Certain Reducing face time with patients
Likely Data breaching
Possible Lack of interoperability
Unlikely Financial Exposure to Return of Interest
Rare
C. Level of Consequence
The level of consequence of reducing face time is considered to be a major consequence as
in case the communication is not performed in a proper manner the entire treatment
process will get effected and this will reduce the efficiency of the entire scenario. With least
communication in between the doctors and the patients the consequences can be very
negative and even fatal.
Data breaching is considered to be having a moderate consequence as the chances of
occurrence is low but the result that will be projected will be very high. In case of occurrence

PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
of this issue the data that will be stored will get stolen and privacy of the personal data will
get deleted.
In case of lack of interoperability the complexity in the processing increases and hence
functional process gets hampered. This is the main reason that this risk has a major
consequence
In case of the return of interest, despite the fact that the investment that will be made will
help in data protection. Hence the consequence will be low. The issue will arise only if the
hospital do not receive any benefit. Benefit will be received and hence the consequence is
low.
Level of Likeliness
Reducing face time interaction in between the doctors will be almost certain. The reason of
this certainness is high because with the help of the Electronic health record,
telecommunication can be used and communication process can be performed. Due to this
reason direct communication decreases and this is the main reason that the processing of
the entire project gets performed in a negative manner.
Data breaching is likely to happen as the electronic platform that is used in the Electronic
Health Record does not have a robust data frame. Hence hacking of the data base gets easy.
Lack of interoperability is possible to occur as the entire functioning will be having a system f
complexity.
Lack of Return of Investment is least likely occur as the benefits that are gained after the
implementation of the Electronic data breach is high. Hence the return of Investment is
probably high.
Part 3
A. 3 possible risk mitigation process includes conduction of HIPAA security risk analysis,
Encryption of data and implementation of firewall and antivirus.
With the help of the periodic risk analysis the main advantage that will be gained includes
the terminology of fostering of the culture as per the as per the common understanding of
the right way to handle the patient data. This aspect ensures the fact that the management
of the entire scenario gets processed as per the creation of the human firewall. With the
help of the proposing of the patient protection, PHI is another aspect. This ensures the fact
that promotion of careful handling of the PHI of patients will also be checked. This also helps
in better prosecuting of the HCAHPS. Hospital Consumer Assessment of Healthcare Providers
and Systems are scored in this process of HIPAA. With the help of the HIPAA analysis a better
understanding of the methods will be increasing the robustness in data storage of the
patients.
Encryption of data is one of the most important methodology that can be used in increasing
the security of the data that are being stored in the database of the Electronic Health
Record. In case encryption of the data is performed the main advantage that will be enjoyed
includes the fact that despite the imposters cracks the security password they cannot gain
access to the information that are stored in the database of the organization. After
encryption of the data that are stored in the database of the Electronic health record, the
only way to gain access to the data is to decrypt the data that are stored. This decryption of
data is only possible if the decryption key is available to the imposters. Hence the data will
stay protected.
With the implementation of the firewall in the system the main advantage that will be
provided includes the fact that the management of the entire data section will get effected
as introduction of malware will not affect the security of the database of the Electronic
Health Record. The imposters fails to introduce the virus in the system. Hence data blockage
aspect will get mitigated.
B. The residual risk level of implementation of the HIPAA security is medium in nature. The
main residual issue that is present in the inclusion of the restriction and misinterpretation of
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
of this issue the data that will be stored will get stolen and privacy of the personal data will
get deleted.
In case of lack of interoperability the complexity in the processing increases and hence
functional process gets hampered. This is the main reason that this risk has a major
consequence
In case of the return of interest, despite the fact that the investment that will be made will
help in data protection. Hence the consequence will be low. The issue will arise only if the
hospital do not receive any benefit. Benefit will be received and hence the consequence is
low.
Level of Likeliness
Reducing face time interaction in between the doctors will be almost certain. The reason of
this certainness is high because with the help of the Electronic health record,
telecommunication can be used and communication process can be performed. Due to this
reason direct communication decreases and this is the main reason that the processing of
the entire project gets performed in a negative manner.
Data breaching is likely to happen as the electronic platform that is used in the Electronic
Health Record does not have a robust data frame. Hence hacking of the data base gets easy.
Lack of interoperability is possible to occur as the entire functioning will be having a system f
complexity.
Lack of Return of Investment is least likely occur as the benefits that are gained after the
implementation of the Electronic data breach is high. Hence the return of Investment is
probably high.
Part 3
A. 3 possible risk mitigation process includes conduction of HIPAA security risk analysis,
Encryption of data and implementation of firewall and antivirus.
With the help of the periodic risk analysis the main advantage that will be gained includes
the terminology of fostering of the culture as per the as per the common understanding of
the right way to handle the patient data. This aspect ensures the fact that the management
of the entire scenario gets processed as per the creation of the human firewall. With the
help of the proposing of the patient protection, PHI is another aspect. This ensures the fact
that promotion of careful handling of the PHI of patients will also be checked. This also helps
in better prosecuting of the HCAHPS. Hospital Consumer Assessment of Healthcare Providers
and Systems are scored in this process of HIPAA. With the help of the HIPAA analysis a better
understanding of the methods will be increasing the robustness in data storage of the
patients.
Encryption of data is one of the most important methodology that can be used in increasing
the security of the data that are being stored in the database of the Electronic Health
Record. In case encryption of the data is performed the main advantage that will be enjoyed
includes the fact that despite the imposters cracks the security password they cannot gain
access to the information that are stored in the database of the organization. After
encryption of the data that are stored in the database of the Electronic health record, the
only way to gain access to the data is to decrypt the data that are stored. This decryption of
data is only possible if the decryption key is available to the imposters. Hence the data will
stay protected.
With the implementation of the firewall in the system the main advantage that will be
provided includes the fact that the management of the entire data section will get effected
as introduction of malware will not affect the security of the database of the Electronic
Health Record. The imposters fails to introduce the virus in the system. Hence data blockage
aspect will get mitigated.
B. The residual risk level of implementation of the HIPAA security is medium in nature. The
main residual issue that is present in the inclusion of the restriction and misinterpretation of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
the data during the emergency situations. Due to this issue the main disadvantage that is
present includes slowing of the information passaging. The usage of HIPAA requires
processing of the usage of the electronic platforms which are supposedly vulnerable in
nature and the robustness of the platform stays low. Risk avoidance must be done in this
case.
After performing the encryption of data, the level of residual risk is low in nature. The only
risk that is present is that validation of decryption key will affect the functioning of the
project. In case the decryption key is lost the major disadvantage that is present is that the
genuine clients of the projects will not gain access to the data that are stored in the
Electronic Health Record. Risk Retention must be performed in this case.
After implementation of the firewall the residual risk will be low. This is due to the fact that
after the implementation of the firewall the risks that are very limited. Risk retention can be
made.
C. The secondary risk that is present in this process is that the usage of encryption of data has
been increasing in a very fast rate. The imposters have been using this encryption related
issue as their strength. Malicious activities are attached in this encrypted code. This affect
the functioning of the entire data set. With the malicious virus and Trojan horses imbibed in
the encrypted code the main disadvantage that will be present includes the fact that the
data that are to be transacted will get overloaded with excess and unnecessary data. Hence
the data that will be required will get lost among the unnecessary data that are imbibed by
the imposters. With the Trojan horses and the virus that are imbibed in the encrypted data
set the platform of Electronic health record that will get corrupted.
The main method of protecting data from this issue is by using the cryptographic protocols.
Usage of machine learning in order to detect the problem that might be happening. With the
help of data transformation the robustness of the entire platform can be increased.
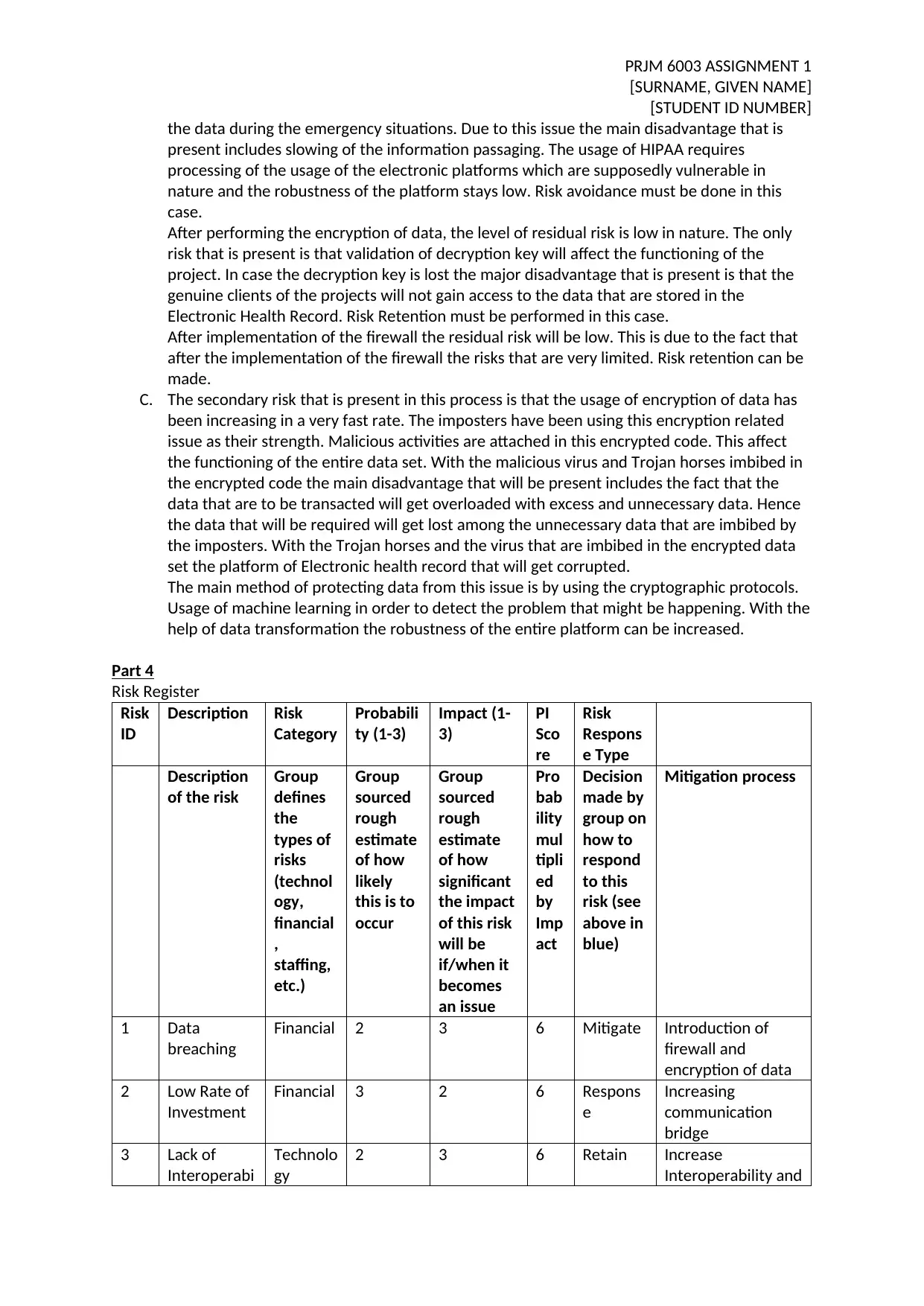
Part 4
Risk Register
Risk
ID
Description Risk
Category
Probabili
ty (1-3)
Impact (1-
3)
PI
Sco
re
Risk
Respons
e Type
Description
of the risk
Group
defines
the
types of
risks
(technol
ogy,
financial
,
staffing,
etc.)
Group
sourced
rough
estimate
of how
likely
this is to
occur
Group
sourced
rough
estimate
of how
significant
the impact
of this risk
will be
if/when it
becomes
an issue
Pro
bab
ility
mul
tipli
ed
by
Imp
act
Decision
made by
group on
how to
respond
to this
risk (see
above in
blue)
Mitigation process
1 Data
breaching
Financial 2 3 6 Mitigate Introduction of
firewall and
encryption of data
2 Low Rate of
Investment
Financial 3 2 6 Respons
e
Increasing
communication
bridge
3 Lack of
Interoperabi
Technolo
gy
2 3 6 Retain Increase
Interoperability and
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
the data during the emergency situations. Due to this issue the main disadvantage that is
present includes slowing of the information passaging. The usage of HIPAA requires
processing of the usage of the electronic platforms which are supposedly vulnerable in
nature and the robustness of the platform stays low. Risk avoidance must be done in this
case.
After performing the encryption of data, the level of residual risk is low in nature. The only
risk that is present is that validation of decryption key will affect the functioning of the
project. In case the decryption key is lost the major disadvantage that is present is that the
genuine clients of the projects will not gain access to the data that are stored in the
Electronic Health Record. Risk Retention must be performed in this case.
After implementation of the firewall the residual risk will be low. This is due to the fact that
after the implementation of the firewall the risks that are very limited. Risk retention can be
made.
C. The secondary risk that is present in this process is that the usage of encryption of data has
been increasing in a very fast rate. The imposters have been using this encryption related
issue as their strength. Malicious activities are attached in this encrypted code. This affect
the functioning of the entire data set. With the malicious virus and Trojan horses imbibed in
the encrypted code the main disadvantage that will be present includes the fact that the
data that are to be transacted will get overloaded with excess and unnecessary data. Hence
the data that will be required will get lost among the unnecessary data that are imbibed by
the imposters. With the Trojan horses and the virus that are imbibed in the encrypted data
set the platform of Electronic health record that will get corrupted.
The main method of protecting data from this issue is by using the cryptographic protocols.
Usage of machine learning in order to detect the problem that might be happening. With the
help of data transformation the robustness of the entire platform can be increased.
Part 4
Risk Register
Risk
ID
Description Risk
Category
Probabili
ty (1-3)
Impact (1-
3)
PI
Sco
re
Risk
Respons
e Type
Description
of the risk
Group
defines
the
types of
risks
(technol
ogy,
financial
,
staffing,
etc.)
Group
sourced
rough
estimate
of how
likely
this is to
occur
Group
sourced
rough
estimate
of how
significant
the impact
of this risk
will be
if/when it
becomes
an issue
Pro
bab
ility
mul
tipli
ed
by
Imp
act
Decision
made by
group on
how to
respond
to this
risk (see
above in
blue)
Mitigation process
1 Data
breaching
Financial 2 3 6 Mitigate Introduction of
firewall and
encryption of data
2 Low Rate of
Investment
Financial 3 2 6 Respons
e
Increasing
communication
bridge
3 Lack of
Interoperabi
Technolo
gy
2 3 6 Retain Increase
Interoperability and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
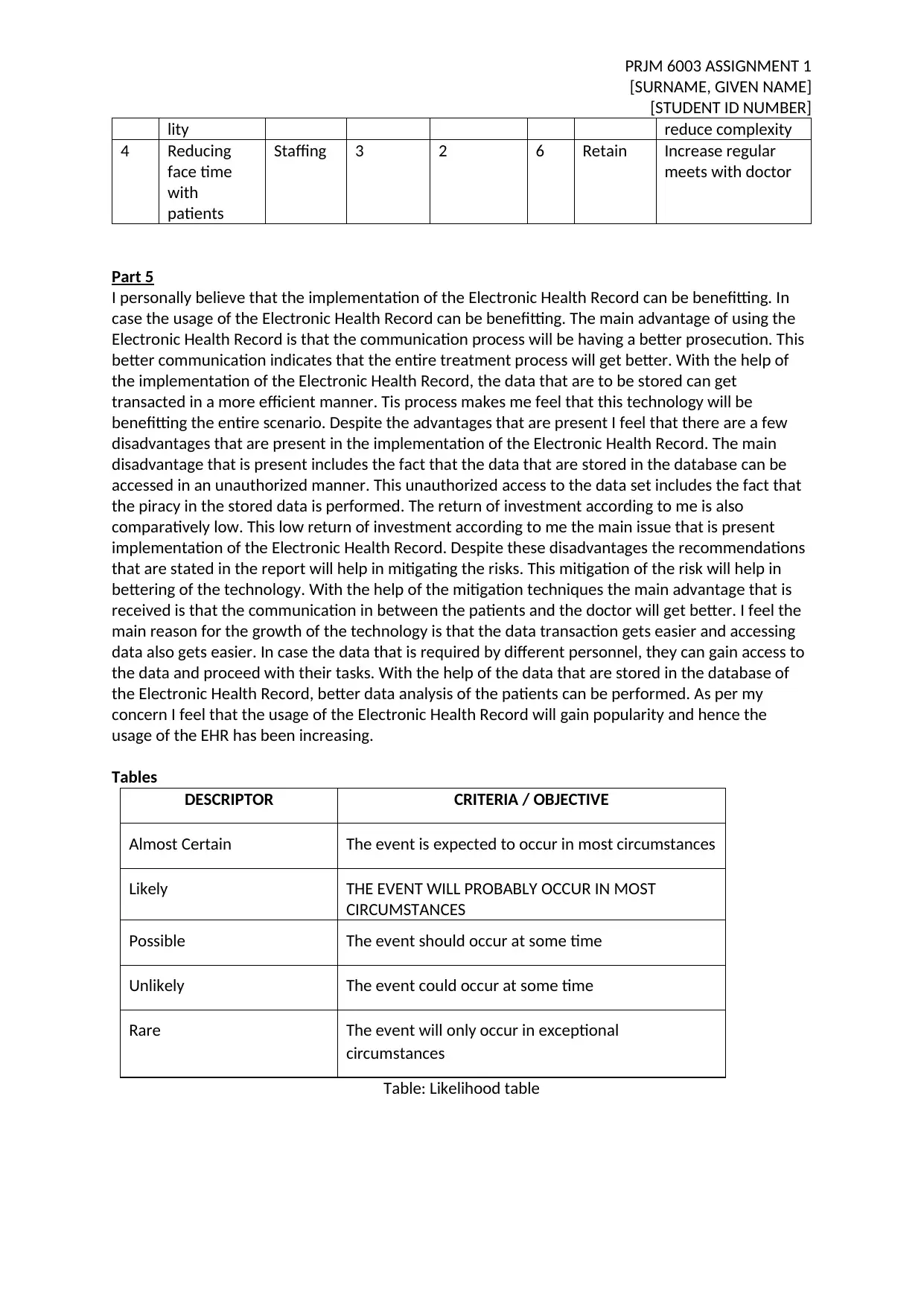
lity reduce complexity
4 Reducing
face time
with
patients
Staffing 3 2 6 Retain Increase regular
meets with doctor
Part 5
I personally believe that the implementation of the Electronic Health Record can be benefitting. In
case the usage of the Electronic Health Record can be benefitting. The main advantage of using the
Electronic Health Record is that the communication process will be having a better prosecution. This
better communication indicates that the entire treatment process will get better. With the help of
the implementation of the Electronic Health Record, the data that are to be stored can get
transacted in a more efficient manner. Tis process makes me feel that this technology will be
benefitting the entire scenario. Despite the advantages that are present I feel that there are a few
disadvantages that are present in the implementation of the Electronic Health Record. The main
disadvantage that is present includes the fact that the data that are stored in the database can be
accessed in an unauthorized manner. This unauthorized access to the data set includes the fact that
the piracy in the stored data is performed. The return of investment according to me is also
comparatively low. This low return of investment according to me the main issue that is present
implementation of the Electronic Health Record. Despite these disadvantages the recommendations
that are stated in the report will help in mitigating the risks. This mitigation of the risk will help in
bettering of the technology. With the help of the mitigation techniques the main advantage that is
received is that the communication in between the patients and the doctor will get better. I feel the
main reason for the growth of the technology is that the data transaction gets easier and accessing
data also gets easier. In case the data that is required by different personnel, they can gain access to
the data and proceed with their tasks. With the help of the data that are stored in the database of
the Electronic Health Record, better data analysis of the patients can be performed. As per my
concern I feel that the usage of the Electronic Health Record will gain popularity and hence the
usage of the EHR has been increasing.
Tables
DESCRIPTOR CRITERIA / OBJECTIVE
Almost Certain The event is expected to occur in most circumstances
Likely THE EVENT WILL PROBABLY OCCUR IN MOST
CIRCUMSTANCES
Possible The event should occur at some time
Unlikely The event could occur at some time
Rare The event will only occur in exceptional
circumstances
Table: Likelihood table
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
lity reduce complexity
4 Reducing
face time
with
patients
Staffing 3 2 6 Retain Increase regular
meets with doctor
Part 5
I personally believe that the implementation of the Electronic Health Record can be benefitting. In
case the usage of the Electronic Health Record can be benefitting. The main advantage of using the
Electronic Health Record is that the communication process will be having a better prosecution. This
better communication indicates that the entire treatment process will get better. With the help of
the implementation of the Electronic Health Record, the data that are to be stored can get
transacted in a more efficient manner. Tis process makes me feel that this technology will be
benefitting the entire scenario. Despite the advantages that are present I feel that there are a few
disadvantages that are present in the implementation of the Electronic Health Record. The main
disadvantage that is present includes the fact that the data that are stored in the database can be
accessed in an unauthorized manner. This unauthorized access to the data set includes the fact that
the piracy in the stored data is performed. The return of investment according to me is also
comparatively low. This low return of investment according to me the main issue that is present
implementation of the Electronic Health Record. Despite these disadvantages the recommendations
that are stated in the report will help in mitigating the risks. This mitigation of the risk will help in
bettering of the technology. With the help of the mitigation techniques the main advantage that is
received is that the communication in between the patients and the doctor will get better. I feel the
main reason for the growth of the technology is that the data transaction gets easier and accessing
data also gets easier. In case the data that is required by different personnel, they can gain access to
the data and proceed with their tasks. With the help of the data that are stored in the database of
the Electronic Health Record, better data analysis of the patients can be performed. As per my
concern I feel that the usage of the Electronic Health Record will gain popularity and hence the
usage of the EHR has been increasing.
Tables
DESCRIPTOR CRITERIA / OBJECTIVE
Almost Certain The event is expected to occur in most circumstances
Likely THE EVENT WILL PROBABLY OCCUR IN MOST
CIRCUMSTANCES
Possible The event should occur at some time
Unlikely The event could occur at some time
Rare The event will only occur in exceptional
circumstances
Table: Likelihood table
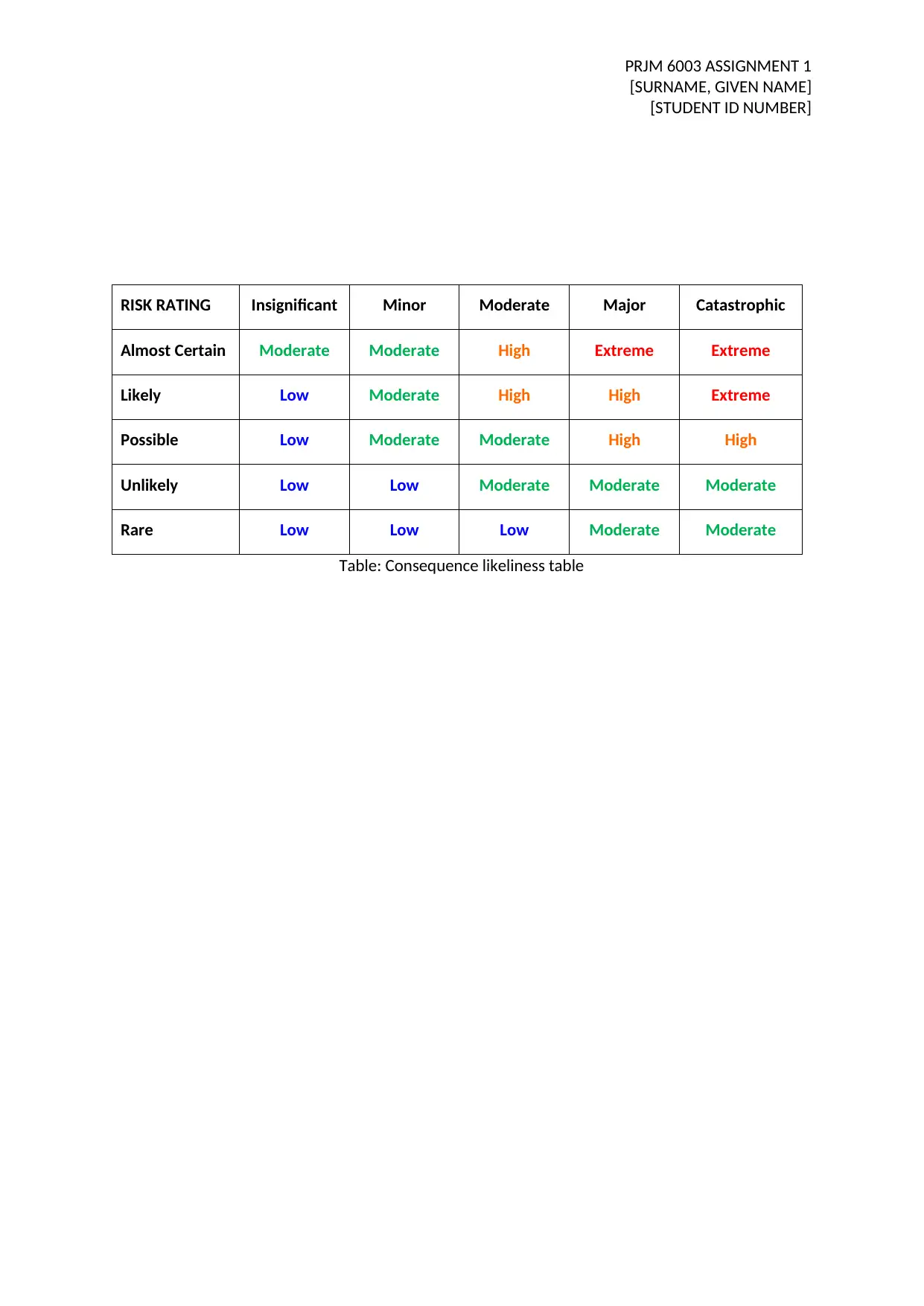
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
RISK RATING Insignificant Minor Moderate Major Catastrophic
Almost Certain Moderate Moderate High Extreme Extreme
Likely Low Moderate High High Extreme
Possible Low Moderate Moderate High High
Unlikely Low Low Moderate Moderate Moderate
Rare Low Low Low Moderate Moderate
Table: Consequence likeliness table
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
RISK RATING Insignificant Minor Moderate Major Catastrophic
Almost Certain Moderate Moderate High Extreme Extreme
Likely Low Moderate High High Extreme
Possible Low Moderate Moderate High High
Unlikely Low Low Moderate Moderate Moderate
Rare Low Low Low Moderate Moderate
Table: Consequence likeliness table
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Bibliography
Goldstein, Benjamin A., Ann Marie Navar, Michael J. Pencina, and John Ioannidis. "Opportunities and
challenges in developing risk prediction models with electronic health records data: a systematic
review." Journal of the American Medical Informatics Association 24, no. 1 (2017): 198-208.
Cheng, Yu, Fei Wang, Ping Zhang, and Jianying Hu. "Risk prediction with electronic health records: A
deep learning approach." In Proceedings of the 2016 SIAM International Conference on Data Mining,
pp. 432-440. Society for Industrial and Applied Mathematics, 2016.
Perotte, Adler, Rajesh Ranganath, Jamie S. Hirsch, David Blei, and Noémie Elhadad. "Risk prediction
for chronic kidney disease progression using heterogeneous electronic health record data and time
series analysis." Journal of the American Medical Informatics Association 22, no. 4 (2015): 872-880.
Ozair, Fouzia F., Nayer Jamshed, Amit Sharma, and Praveen Aggarwal. "Ethical issues in electronic
health records: A general overview." Perspectives in clinical research 6, no. 2 (2015): 73.
Casey, Joan A., Brian S. Schwartz, Walter F. Stewart, and Nancy E. Adler. "Using electronic health
records for population health research: a review of methods and applications." Annual review of
public health 37 (2016): 61-81.
Gellert, George A., Ricardo Ramirez, and S. Luke Webster. "The rise of the medical scribe industry:
implications for the advancement of electronic health records." Jama 313, no. 13 (2015): 1315-1316.
Birkhead, Guthrie S., Michael Klompas, and Nirav R. Shah. "Uses of electronic health records for
public health surveillance to advance public health." Annual review of public health 36 (2015): 345-
359.
Rajkomar, Alvin, Eyal Oren, Kai Chen, Andrew M. Dai, Nissan Hajaj, Michaela Hardt, Peter J. Liu et al.
"Scalable and accurate deep learning with electronic health records." NPJ Digital Medicine 1, no. 1
(2018): 18.
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Bibliography
Goldstein, Benjamin A., Ann Marie Navar, Michael J. Pencina, and John Ioannidis. "Opportunities and
challenges in developing risk prediction models with electronic health records data: a systematic
review." Journal of the American Medical Informatics Association 24, no. 1 (2017): 198-208.
Cheng, Yu, Fei Wang, Ping Zhang, and Jianying Hu. "Risk prediction with electronic health records: A
deep learning approach." In Proceedings of the 2016 SIAM International Conference on Data Mining,
pp. 432-440. Society for Industrial and Applied Mathematics, 2016.
Perotte, Adler, Rajesh Ranganath, Jamie S. Hirsch, David Blei, and Noémie Elhadad. "Risk prediction
for chronic kidney disease progression using heterogeneous electronic health record data and time
series analysis." Journal of the American Medical Informatics Association 22, no. 4 (2015): 872-880.
Ozair, Fouzia F., Nayer Jamshed, Amit Sharma, and Praveen Aggarwal. "Ethical issues in electronic
health records: A general overview." Perspectives in clinical research 6, no. 2 (2015): 73.
Casey, Joan A., Brian S. Schwartz, Walter F. Stewart, and Nancy E. Adler. "Using electronic health
records for population health research: a review of methods and applications." Annual review of
public health 37 (2016): 61-81.
Gellert, George A., Ricardo Ramirez, and S. Luke Webster. "The rise of the medical scribe industry:
implications for the advancement of electronic health records." Jama 313, no. 13 (2015): 1315-1316.
Birkhead, Guthrie S., Michael Klompas, and Nirav R. Shah. "Uses of electronic health records for
public health surveillance to advance public health." Annual review of public health 36 (2015): 345-
359.
Rajkomar, Alvin, Eyal Oren, Kai Chen, Andrew M. Dai, Nissan Hajaj, Michaela Hardt, Peter J. Liu et al.
"Scalable and accurate deep learning with electronic health records." NPJ Digital Medicine 1, no. 1
(2018): 18.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





