Secure Virtual Private Network (VPN) Setup
VerifiedAdded on 2019/09/18
|13
|3497
|643
Report
AI Summary
The assignment involves generating certificates and keys using the OpenSSL tool 'easy-rsa'. The steps include generating a Certificate Authority (CA) certificate and key, generating server and client certificates and private keys, and generating Diffie-Hellman parameters. The generated files are then copied to their respective machines and used to configure OpenVPN servers on both machines. The assignment also involves modifying configuration files for the server and client, and testing the VPN by pinging across it. Additionally, the setup is tested using Wireshark to verify that packets are encrypted.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Project 1: Public Key, Root CA, Certificates, Hash, MAC and SSL
VPNs
1 Lab Preparation...................................................................................................................................2
2 Performance Comparison: RSA versus AES..........................................................................................2
3 Become a root CA and sign a Certificate..............................................................................................3
3.1 Create a new CA..........................................................................................................................3
3.2 Generate a new certificate request.............................................................................................4
3.3 Sign the certificate request..........................................................................................................4
4 Configure SSL certificates on the Apache server..................................................................................5
4.1 Modify the Apache server configuration.....................................................................................5
4.2 Test an SSL/TLS connection.........................................................................................................5
5 Install the CA root certificate as a Trusted Root Certificate.................................................................6
5.1 Install the root CA for Firefox on the Linux server.......................................................................6
5.2 Install the root CA for Firefox on a Linux client............................................................................7
5.3 Install the root CA for IE on Windows..........................................................................................7
5.4 Install the root CA for Firefox on Windows..................................................................................7
6 One-Way Hash Function and MAC......................................................................................................7
6.1 One-way Hash Functions.............................................................................................................7
6.2 Keyed Hash and HMAC................................................................................................................8
7 Setting SSL based VPNs for Linux.........................................................................................................8
7.1 Build Certificate Authority (CA)....................................................................................................8
7.2 Certificate and key generation.....................................................................................................9
7.3 Server configuration..................................................................................................................10
7.4 Client configuration...................................................................................................................11
8 Configure client certificates for authentication (optional).................................................................11
Goal: In this lab we will exercise the idea that digital certificates are verified using a chain of
trust. The trust anchor for the digital certificates is the Root Certificate Authority (CA). In
addition, we will practice using command-line procedures for setting up SSL/TLS certificates.
First, we will generate a root certificate (to become the root CA) and other certificates. Then, we
will sign the certificates with the root certificate. Next, we will place these certificates on an
Apache web server. When the web server is visited by a client’s browser with the root CA
installed, the server will be trusted automatically due the chain of trust.
Page | 1
VPNs
1 Lab Preparation...................................................................................................................................2
2 Performance Comparison: RSA versus AES..........................................................................................2
3 Become a root CA and sign a Certificate..............................................................................................3
3.1 Create a new CA..........................................................................................................................3
3.2 Generate a new certificate request.............................................................................................4
3.3 Sign the certificate request..........................................................................................................4
4 Configure SSL certificates on the Apache server..................................................................................5
4.1 Modify the Apache server configuration.....................................................................................5
4.2 Test an SSL/TLS connection.........................................................................................................5
5 Install the CA root certificate as a Trusted Root Certificate.................................................................6
5.1 Install the root CA for Firefox on the Linux server.......................................................................6
5.2 Install the root CA for Firefox on a Linux client............................................................................7
5.3 Install the root CA for IE on Windows..........................................................................................7
5.4 Install the root CA for Firefox on Windows..................................................................................7
6 One-Way Hash Function and MAC......................................................................................................7
6.1 One-way Hash Functions.............................................................................................................7
6.2 Keyed Hash and HMAC................................................................................................................8
7 Setting SSL based VPNs for Linux.........................................................................................................8
7.1 Build Certificate Authority (CA)....................................................................................................8
7.2 Certificate and key generation.....................................................................................................9
7.3 Server configuration..................................................................................................................10
7.4 Client configuration...................................................................................................................11
8 Configure client certificates for authentication (optional).................................................................11
Goal: In this lab we will exercise the idea that digital certificates are verified using a chain of
trust. The trust anchor for the digital certificates is the Root Certificate Authority (CA). In
addition, we will practice using command-line procedures for setting up SSL/TLS certificates.
First, we will generate a root certificate (to become the root CA) and other certificates. Then, we
will sign the certificates with the root certificate. Next, we will place these certificates on an
Apache web server. When the web server is visited by a client’s browser with the root CA
installed, the server will be trusted automatically due the chain of trust.
Page | 1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Major Reference for this lab:
http://www.reppep.com/~pepper/writing/tidbits/ssl-article/ssl2.text
How to use virtualbox:
http://www.makeuseof.com/tag/how-to-use-virtualbox/
How to use vmware:
https://www.vmware.com/pdf/ws80-using.pdf
Fedora live image:
I used Fedora-18-x86_64-Live-Desktop.iso.
http://archives.fedoraproject.org/pub/archive/fedora/linux/releases/18/Live/
x86_64/
You also can download the new version.
https://getfedora.org/en/workstation/download/
Windows:
I used IE8 on Win7 virtual machines. You can download free virtual machines from this
webpage:
https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/
1 Lab Preparation (2 points)
On your FC Linux server, as root, type the following command to update your openssl and httpd
utilities: (needs Internet access)
yum –y install openssl
yum –y install openssl-*
yum –y install httpd-*
yum –y install mod_ssl
2 Performance Comparison: RSA versus AES
In this task, we will study the performance of public-key algorithms. Please prepare a file
(message.txt) that contains a 16-byte message. Please also generate a 1024-bit RSA
public/private key pair by using the following commands:
openssl genrsa -out private.pem 1024
This command creates a key file called private.pem that uses 1024 bits. This file actually has
both the private and public keys, so you should extract the public one from this file:
openssl rsa -in private.pem -out public.pem -outform PEM –pubout
The commands of encryption and decryption using public key look like the following:
openssl rsautl -encrypt -inkey public.pem -pubin -in file.txt -out file.ssl
openssl rsautl -decrypt -inkey private.pem -in file.ssl -out decrypted.txt
Page | 2
http://www.reppep.com/~pepper/writing/tidbits/ssl-article/ssl2.text
How to use virtualbox:
http://www.makeuseof.com/tag/how-to-use-virtualbox/
How to use vmware:
https://www.vmware.com/pdf/ws80-using.pdf
Fedora live image:
I used Fedora-18-x86_64-Live-Desktop.iso.
http://archives.fedoraproject.org/pub/archive/fedora/linux/releases/18/Live/
x86_64/
You also can download the new version.
https://getfedora.org/en/workstation/download/
Windows:
I used IE8 on Win7 virtual machines. You can download free virtual machines from this
webpage:
https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/
1 Lab Preparation (2 points)
On your FC Linux server, as root, type the following command to update your openssl and httpd
utilities: (needs Internet access)
yum –y install openssl
yum –y install openssl-*
yum –y install httpd-*
yum –y install mod_ssl
2 Performance Comparison: RSA versus AES
In this task, we will study the performance of public-key algorithms. Please prepare a file
(message.txt) that contains a 16-byte message. Please also generate a 1024-bit RSA
public/private key pair by using the following commands:
openssl genrsa -out private.pem 1024
This command creates a key file called private.pem that uses 1024 bits. This file actually has
both the private and public keys, so you should extract the public one from this file:
openssl rsa -in private.pem -out public.pem -outform PEM –pubout
The commands of encryption and decryption using public key look like the following:
openssl rsautl -encrypt -inkey public.pem -pubin -in file.txt -out file.ssl
openssl rsautl -decrypt -inkey private.pem -in file.ssl -out decrypted.txt
Page | 2

The commands of encryption and decryption using AES like the following:
openssl enc –aes-128-cbc -in file.txt -out file.enc
openssl enc –d –aes-128-cbc -in file.enc -out file.txt
Next, do the following:
1. Encrypt message.txt using the public key; save the output in message enc.ssl. (2 points)
2. Decrypt message enc.ssl using the private key. (2 points)
3. Encrypt message.txt using a 128-bit AES key. (2 points)
2.1.1 Compare the time spent on each of the above operations, and describe
your observations. If an operation is too fast, you may want to repeat it for
many times, and then take an average. (5 points)
After you finish the above exercise, you can now use the openssl speed commands to do such a
benchmarking. The following command shows examples of using speed to benchmark RSA and
AES:
openssl speed rsa
openssl speed aes
2.1.2 Please describe whether your observations are similar to those from the
outputs of the speed command. (2 points)
3 Become a root CA and sign a Certificate
Go to the /etc/pki/tls/misc/ directory. There is a file named CA.pl. We will use this file to
create a root certificate and other certificates.
3.1 Create a new CA
./CA.pl -newca
A certificate filename (or enter to create) <enter>
Making CA certificate ...
Using configuration from openssl.cnf
Generating a 1024 bit RSA private key
............++++++
......................++++++
writing new private key to '/etc/pki/CA/private/cakey.pem'
Enter PEM pass phrase: <secret passphrase here> write it down for future
reference, mine is CMSC622y
Verifying password - Enter PEM pass phrase: <secret passphrase again>
-----
Page | 3
openssl enc –aes-128-cbc -in file.txt -out file.enc
openssl enc –d –aes-128-cbc -in file.enc -out file.txt
Next, do the following:
1. Encrypt message.txt using the public key; save the output in message enc.ssl. (2 points)
2. Decrypt message enc.ssl using the private key. (2 points)
3. Encrypt message.txt using a 128-bit AES key. (2 points)
2.1.1 Compare the time spent on each of the above operations, and describe
your observations. If an operation is too fast, you may want to repeat it for
many times, and then take an average. (5 points)
After you finish the above exercise, you can now use the openssl speed commands to do such a
benchmarking. The following command shows examples of using speed to benchmark RSA and
AES:
openssl speed rsa
openssl speed aes
2.1.2 Please describe whether your observations are similar to those from the
outputs of the speed command. (2 points)
3 Become a root CA and sign a Certificate
Go to the /etc/pki/tls/misc/ directory. There is a file named CA.pl. We will use this file to
create a root certificate and other certificates.
3.1 Create a new CA
./CA.pl -newca
A certificate filename (or enter to create) <enter>
Making CA certificate ...
Using configuration from openssl.cnf
Generating a 1024 bit RSA private key
............++++++
......................++++++
writing new private key to '/etc/pki/CA/private/cakey.pem'
Enter PEM pass phrase: <secret passphrase here> write it down for future
reference, mine is CMSC622y
Verifying password - Enter PEM pass phrase: <secret passphrase again>
-----
Page | 3

You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a
DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:VA
Locality Name (eg, city) []:Richmond
Organization Name (eg, company) []:VCU
Organizational Unit Name (eg, section) []:CS
Common Name (eg, YOUR name) []: WeiCheng # I put WeiCheng here as the
example common name. A more general practice is to put your sever’s DNS name.
Email Address []:yourname@vcu.edu
No need to add a challenge password
You will be asked to input your PEM key again in the end (before the
accomplish of the certificate creation)
This creates a new root certificate in the directory /etc/pki/CA. The new root certificate file is
named as cacert.pem. (3 points)
3.2 Generate a new certificate request
./CA.pl -newreq
Using configuration from openssl.cnf
Generating a 1024 bit RSA private key
..........++++++
..............++++++
writing new private key to 'newreq.pem'
Enter PEM pass phrase: <another secret passphrase here> mine is 622req
Verifying password - Enter PEM pass phrase: <another secret passphrase
again>
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a
DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:VA
Locality Name (eg, city) []:Richmond
Organization Name (eg, company) [Internet Widgits Pty Ltd]:VCU
Organizational Unit Name (eg, section) []:CStest
Common Name (eg, YOUR name) []:192.168.56.101, which is the http server’s
IP address. You can use your FC Linux server’s IP (i.e., the IP of the virtual
machine). If the http server has a DNS name, please use the DNS name.
Email Address []:yourname@vcu.edu
Page | 4
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a
DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:VA
Locality Name (eg, city) []:Richmond
Organization Name (eg, company) []:VCU
Organizational Unit Name (eg, section) []:CS
Common Name (eg, YOUR name) []: WeiCheng # I put WeiCheng here as the
example common name. A more general practice is to put your sever’s DNS name.
Email Address []:yourname@vcu.edu
No need to add a challenge password
You will be asked to input your PEM key again in the end (before the
accomplish of the certificate creation)
This creates a new root certificate in the directory /etc/pki/CA. The new root certificate file is
named as cacert.pem. (3 points)
3.2 Generate a new certificate request
./CA.pl -newreq
Using configuration from openssl.cnf
Generating a 1024 bit RSA private key
..........++++++
..............++++++
writing new private key to 'newreq.pem'
Enter PEM pass phrase: <another secret passphrase here> mine is 622req
Verifying password - Enter PEM pass phrase: <another secret passphrase
again>
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a
DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:VA
Locality Name (eg, city) []:Richmond
Organization Name (eg, company) [Internet Widgits Pty Ltd]:VCU
Organizational Unit Name (eg, section) []:CStest
Common Name (eg, YOUR name) []:192.168.56.101, which is the http server’s
IP address. You can use your FC Linux server’s IP (i.e., the IP of the virtual
machine). If the http server has a DNS name, please use the DNS name.
Email Address []:yourname@vcu.edu
Page | 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
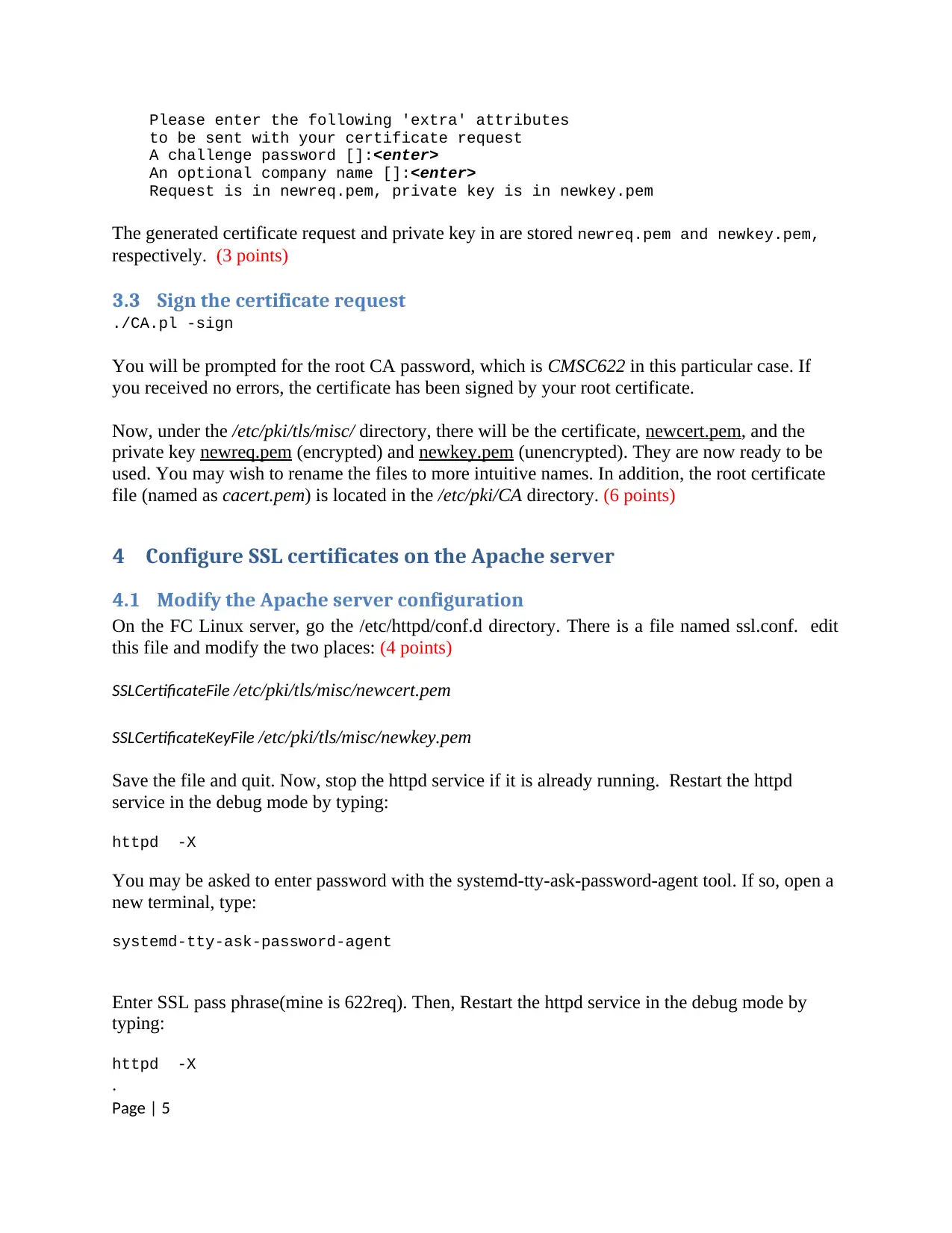
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:<enter>
An optional company name []:<enter>
Request is in newreq.pem, private key is in newkey.pem
The generated certificate request and private key in are stored newreq.pem and newkey.pem,
respectively. (3 points)
3.3 Sign the certificate request
./CA.pl -sign
You will be prompted for the root CA password, which is CMSC622 in this particular case. If
you received no errors, the certificate has been signed by your root certificate.
Now, under the /etc/pki/tls/misc/ directory, there will be the certificate, newcert.pem, and the
private key newreq.pem (encrypted) and newkey.pem (unencrypted). They are now ready to be
used. You may wish to rename the files to more intuitive names. In addition, the root certificate
file (named as cacert.pem) is located in the /etc/pki/CA directory. (6 points)
4 Configure SSL certificates on the Apache server
4.1 Modify the Apache server configuration
On the FC Linux server, go the /etc/httpd/conf.d directory. There is a file named ssl.conf. edit
this file and modify the two places: (4 points)
SSLCertificateFile /etc/pki/tls/misc/newcert.pem
SSLCertificateKeyFile /etc/pki/tls/misc/newkey.pem
Save the file and quit. Now, stop the httpd service if it is already running. Restart the httpd
service in the debug mode by typing:
httpd -X
You may be asked to enter password with the systemd-tty-ask-password-agent tool. If so, open a
new terminal, type:
systemd-tty-ask-password-agent
Enter SSL pass phrase(mine is 622req). Then, Restart the httpd service in the debug mode by
typing:
httpd -X
.
Page | 5
to be sent with your certificate request
A challenge password []:<enter>
An optional company name []:<enter>
Request is in newreq.pem, private key is in newkey.pem
The generated certificate request and private key in are stored newreq.pem and newkey.pem,
respectively. (3 points)
3.3 Sign the certificate request
./CA.pl -sign
You will be prompted for the root CA password, which is CMSC622 in this particular case. If
you received no errors, the certificate has been signed by your root certificate.
Now, under the /etc/pki/tls/misc/ directory, there will be the certificate, newcert.pem, and the
private key newreq.pem (encrypted) and newkey.pem (unencrypted). They are now ready to be
used. You may wish to rename the files to more intuitive names. In addition, the root certificate
file (named as cacert.pem) is located in the /etc/pki/CA directory. (6 points)
4 Configure SSL certificates on the Apache server
4.1 Modify the Apache server configuration
On the FC Linux server, go the /etc/httpd/conf.d directory. There is a file named ssl.conf. edit
this file and modify the two places: (4 points)
SSLCertificateFile /etc/pki/tls/misc/newcert.pem
SSLCertificateKeyFile /etc/pki/tls/misc/newkey.pem
Save the file and quit. Now, stop the httpd service if it is already running. Restart the httpd
service in the debug mode by typing:
httpd -X
You may be asked to enter password with the systemd-tty-ask-password-agent tool. If so, open a
new terminal, type:
systemd-tty-ask-password-agent
Enter SSL pass phrase(mine is 622req). Then, Restart the httpd service in the debug mode by
typing:
httpd -X
.
Page | 5

4.1.1 Were asked to provide a key? Which key should you provide? (4 points)
4.2 Test an SSL/TLS connection
Open a browser, type the https://server_IP.
4.2.1 Did you receive a warning message? (2 points)
You may notice that you are required to enter the key when the http restarts. There is way to start
the Apache server without requiring inputting the key. Here are the steps:
cd /etc/pki/tls/misc
cp newkey.pem newkey.pem.org
openssl rsa -in newkey.pem.org -out newkey.pem
You will be asked to enter pass phrase for newkey.pem.org. For me, it is 622req.
Now, issue service httpd restart command to verify the setting is okay.
5 Install the CA root certificate as a Trusted Root Certificate
Next, we will verify the chain of trust.
5.1 Install the root CA for Firefox on the Linux server (5 points)
Open the Firefox. Go to Edit -> Preferences -> Advanced -> Encryption ->View Certificates:
Next, import our Authorities (the cacert.pem in /etc/pki/CA):
Page | 6
4.2 Test an SSL/TLS connection
Open a browser, type the https://server_IP.
4.2.1 Did you receive a warning message? (2 points)
You may notice that you are required to enter the key when the http restarts. There is way to start
the Apache server without requiring inputting the key. Here are the steps:
cd /etc/pki/tls/misc
cp newkey.pem newkey.pem.org
openssl rsa -in newkey.pem.org -out newkey.pem
You will be asked to enter pass phrase for newkey.pem.org. For me, it is 622req.
Now, issue service httpd restart command to verify the setting is okay.
5 Install the CA root certificate as a Trusted Root Certificate
Next, we will verify the chain of trust.
5.1 Install the root CA for Firefox on the Linux server (5 points)
Open the Firefox. Go to Edit -> Preferences -> Advanced -> Encryption ->View Certificates:
Next, import our Authorities (the cacert.pem in /etc/pki/CA):
Page | 6

Test an SSL/TLS connection. If you aren't warned about the site certificate, the root certificate
has been successfully installed.
5.1.1 Explain why you did not receive the warning message? (2 points)
5.2 Install the root CA for Firefox on a Linux client (5 points)
Go a FC Linux client virtual machine; repeat the same procedures to install the root CA.
Test an SSL/TLS connection
If you aren't warned about the site certificate, the root certificate has been successfully installed.
5.3 Install the root CA for IE on Windows
On your FC Linux server, convert the Root Certificate from PEM to DER format (for Windows
client use):
cd /etc/pki/CA
openssl x509 -in cacert.pem -inform PEM -out my-rootCA.der -outform DER
Page | 7
has been successfully installed.
5.1.1 Explain why you did not receive the warning message? (2 points)
5.2 Install the root CA for Firefox on a Linux client (5 points)
Go a FC Linux client virtual machine; repeat the same procedures to install the root CA.
Test an SSL/TLS connection
If you aren't warned about the site certificate, the root certificate has been successfully installed.
5.3 Install the root CA for IE on Windows
On your FC Linux server, convert the Root Certificate from PEM to DER format (for Windows
client use):
cd /etc/pki/CA
openssl x509 -in cacert.pem -inform PEM -out my-rootCA.der -outform DER
Page | 7
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

This will create a DER format certificate that can be easily installed on Windows XP.
Transfer the DER format certificate to a Windows machine. An easy way to transfer the
certificate is to place the certificate on the Linux web server and download it from the Windows
machine. Copy the certificate to /var/www/html.
Once you have downloaded the certificate to the Windows machine, double click the certificate
to install it. Follow the default option should be okay. (5 points)
Test an SSL/TLS connection using IE.
If you aren't warned about the site certificate, the root certificate has been successfully installed.
Test an SSL/TLS connection using Firefox.
5.3.1 Explain what happened. Why? (2 points)
5.4 Install the root CA for Firefox on Windows (3 points)
The procedure to install the root CA for Firefox on Windows is similar to that of Linux.
6 One-Way Hash Function and MAC
6.1 One-way Hash Functions
In this task, we will play with various one-way hash algorithms. You can use the following
commands to generate the hash value for a file. You can create the file by typing echo “whatever
contend in here” > filename
md5sum filename
sha256sum filename
sha512sum filename
Output the hash values to a file for future reference.
Alternatively, you can use openssl dgst command to achieve the same goals. The command
prototype looks like: openssl dgst dgsttype filename, where the dgsttype refers to a specific
one-way hash algorithm, such as -md5, -sha256, etc.
To understand the randomness of the one-way function, we will do the following exercise for
MD5, SHA256, and SHA512. Modify one letter of the original input file and regenerate the hash
values for three one-way functions.
6.1.1 Please observe whether the results are similar or not. Please describe your
observations in the project report. (4 points)
Page | 8
Transfer the DER format certificate to a Windows machine. An easy way to transfer the
certificate is to place the certificate on the Linux web server and download it from the Windows
machine. Copy the certificate to /var/www/html.
Once you have downloaded the certificate to the Windows machine, double click the certificate
to install it. Follow the default option should be okay. (5 points)
Test an SSL/TLS connection using IE.
If you aren't warned about the site certificate, the root certificate has been successfully installed.
Test an SSL/TLS connection using Firefox.
5.3.1 Explain what happened. Why? (2 points)
5.4 Install the root CA for Firefox on Windows (3 points)
The procedure to install the root CA for Firefox on Windows is similar to that of Linux.
6 One-Way Hash Function and MAC
6.1 One-way Hash Functions
In this task, we will play with various one-way hash algorithms. You can use the following
commands to generate the hash value for a file. You can create the file by typing echo “whatever
contend in here” > filename
md5sum filename
sha256sum filename
sha512sum filename
Output the hash values to a file for future reference.
Alternatively, you can use openssl dgst command to achieve the same goals. The command
prototype looks like: openssl dgst dgsttype filename, where the dgsttype refers to a specific
one-way hash algorithm, such as -md5, -sha256, etc.
To understand the randomness of the one-way function, we will do the following exercise for
MD5, SHA256, and SHA512. Modify one letter of the original input file and regenerate the hash
values for three one-way functions.
6.1.1 Please observe whether the results are similar or not. Please describe your
observations in the project report. (4 points)
Page | 8

6.2 Keyed Hash and HMAC
In this task, we would like to generate a keyed hash (i.e. MAC) for a file. We can use the -hmac
option. The following example generates a keyed hash for a file using the HMAC-MD5
algorithm. The string following the -hmac option is the key.
openssl dgst -md5 -hmac "abcdefg" filename
Please generate a keyed hash using HMAC-MD5 and HMC-SHA512 for any file that you
choose. Please try several keys with different length. (3 points)
6.2.1 Do we have to use a key with a fixed size in HMAC? If so, what is the key
size? If not, why? (2 points)
7 Setting SSL based VPNs for Linux
The instructions below are adopted from the following source with some modifications:
http://openvpn.net/index.php/open-source/documentation/howto.html
Determine your VPN server and client machines. On both FC server and FC client: (2 points)
yum –y install openssl openvpn
yum –y install openpn easy-rsa
systemctl disable firewalld
7.1 Build Certificate Authority (CA) (2 points)
On your FC server:
cp –r /usr/share/easy-rsa/ /etc/openvpn/
cd /etc/openvpn/easy-rsa/2.0
. ./vars
./clean-all
./build-ca
The final command (build-ca) will build the certificate authority (CA) certificate and key by
invoking the interactive openssl command:
ai:easy-rsa # ./build-ca
Generating a 1024 bit RSA private key
............++++++
...........++++++
writing new private key to 'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
Page | 9
In this task, we would like to generate a keyed hash (i.e. MAC) for a file. We can use the -hmac
option. The following example generates a keyed hash for a file using the HMAC-MD5
algorithm. The string following the -hmac option is the key.
openssl dgst -md5 -hmac "abcdefg" filename
Please generate a keyed hash using HMAC-MD5 and HMC-SHA512 for any file that you
choose. Please try several keys with different length. (3 points)
6.2.1 Do we have to use a key with a fixed size in HMAC? If so, what is the key
size? If not, why? (2 points)
7 Setting SSL based VPNs for Linux
The instructions below are adopted from the following source with some modifications:
http://openvpn.net/index.php/open-source/documentation/howto.html
Determine your VPN server and client machines. On both FC server and FC client: (2 points)
yum –y install openssl openvpn
yum –y install openpn easy-rsa
systemctl disable firewalld
7.1 Build Certificate Authority (CA) (2 points)
On your FC server:
cp –r /usr/share/easy-rsa/ /etc/openvpn/
cd /etc/openvpn/easy-rsa/2.0
. ./vars
./clean-all
./build-ca
The final command (build-ca) will build the certificate authority (CA) certificate and key by
invoking the interactive openssl command:
ai:easy-rsa # ./build-ca
Generating a 1024 bit RSA private key
............++++++
...........++++++
writing new private key to 'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
Page | 9
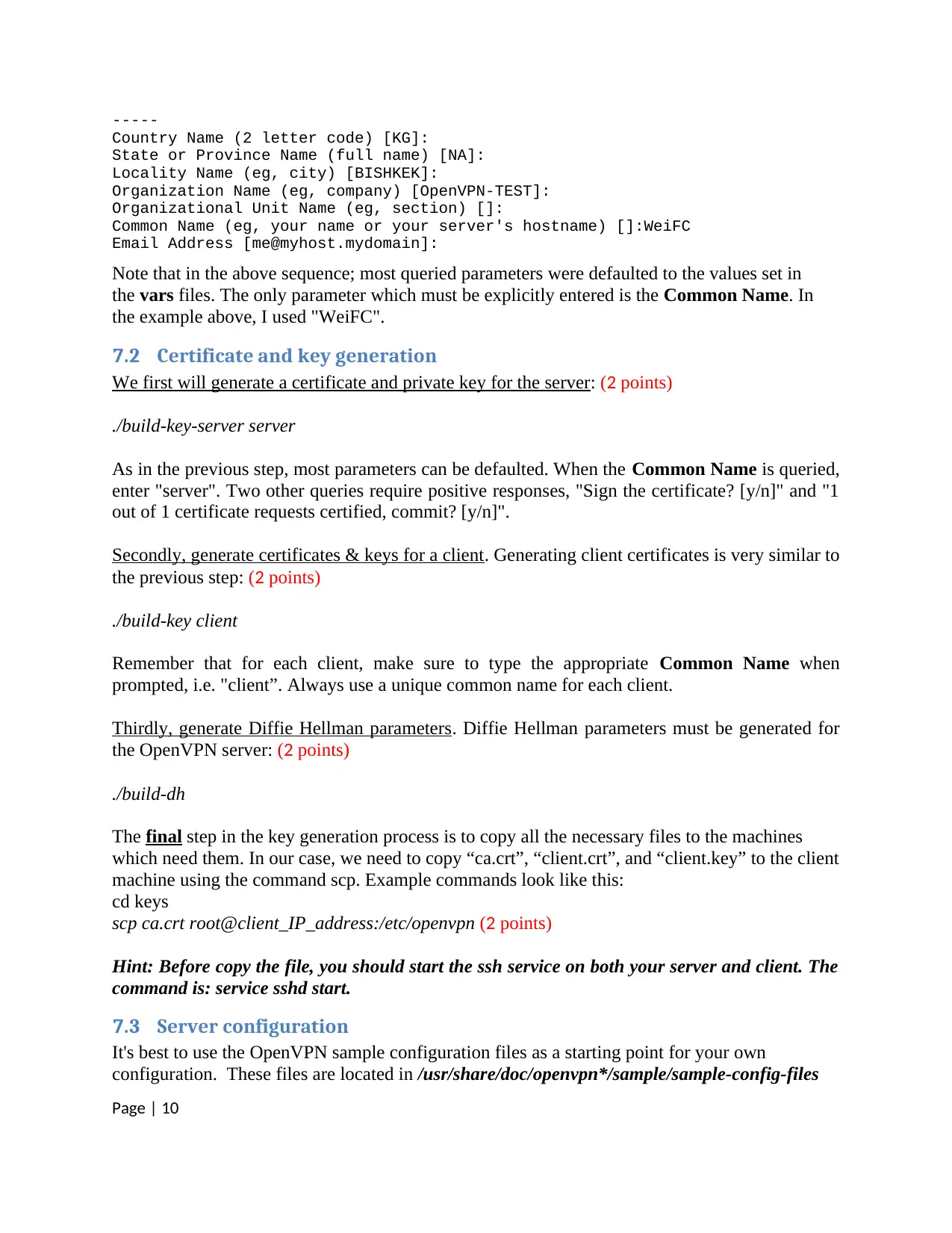
-----
Country Name (2 letter code) [KG]:
State or Province Name (full name) [NA]:
Locality Name (eg, city) [BISHKEK]:
Organization Name (eg, company) [OpenVPN-TEST]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:WeiFC
Email Address [me@myhost.mydomain]:
Note that in the above sequence; most queried parameters were defaulted to the values set in
the vars files. The only parameter which must be explicitly entered is the Common Name. In
the example above, I used "WeiFC".
7.2 Certificate and key generation
We first will generate a certificate and private key for the server: (2 points)
./build-key-server server
As in the previous step, most parameters can be defaulted. When the Common Name is queried,
enter "server". Two other queries require positive responses, "Sign the certificate? [y/n]" and "1
out of 1 certificate requests certified, commit? [y/n]".
Secondly, generate certificates & keys for a client. Generating client certificates is very similar to
the previous step: (2 points)
./build-key client
Remember that for each client, make sure to type the appropriate Common Name when
prompted, i.e. "client”. Always use a unique common name for each client.
Thirdly, generate Diffie Hellman parameters. Diffie Hellman parameters must be generated for
the OpenVPN server: (2 points)
./build-dh
The final step in the key generation process is to copy all the necessary files to the machines
which need them. In our case, we need to copy “ca.crt”, “client.crt”, and “client.key” to the client
machine using the command scp. Example commands look like this:
cd keys
scp ca.crt root@client_IP_address:/etc/openvpn (2 points)
Hint: Before copy the file, you should start the ssh service on both your server and client. The
command is: service sshd start.
7.3 Server configuration
It's best to use the OpenVPN sample configuration files as a starting point for your own
configuration. These files are located in /usr/share/doc/openvpn*/sample/sample-config-files
Page | 10
Country Name (2 letter code) [KG]:
State or Province Name (full name) [NA]:
Locality Name (eg, city) [BISHKEK]:
Organization Name (eg, company) [OpenVPN-TEST]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:WeiFC
Email Address [me@myhost.mydomain]:
Note that in the above sequence; most queried parameters were defaulted to the values set in
the vars files. The only parameter which must be explicitly entered is the Common Name. In
the example above, I used "WeiFC".
7.2 Certificate and key generation
We first will generate a certificate and private key for the server: (2 points)
./build-key-server server
As in the previous step, most parameters can be defaulted. When the Common Name is queried,
enter "server". Two other queries require positive responses, "Sign the certificate? [y/n]" and "1
out of 1 certificate requests certified, commit? [y/n]".
Secondly, generate certificates & keys for a client. Generating client certificates is very similar to
the previous step: (2 points)
./build-key client
Remember that for each client, make sure to type the appropriate Common Name when
prompted, i.e. "client”. Always use a unique common name for each client.
Thirdly, generate Diffie Hellman parameters. Diffie Hellman parameters must be generated for
the OpenVPN server: (2 points)
./build-dh
The final step in the key generation process is to copy all the necessary files to the machines
which need them. In our case, we need to copy “ca.crt”, “client.crt”, and “client.key” to the client
machine using the command scp. Example commands look like this:
cd keys
scp ca.crt root@client_IP_address:/etc/openvpn (2 points)
Hint: Before copy the file, you should start the ssh service on both your server and client. The
command is: service sshd start.
7.3 Server configuration
It's best to use the OpenVPN sample configuration files as a starting point for your own
configuration. These files are located in /usr/share/doc/openvpn*/sample/sample-config-files
Page | 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
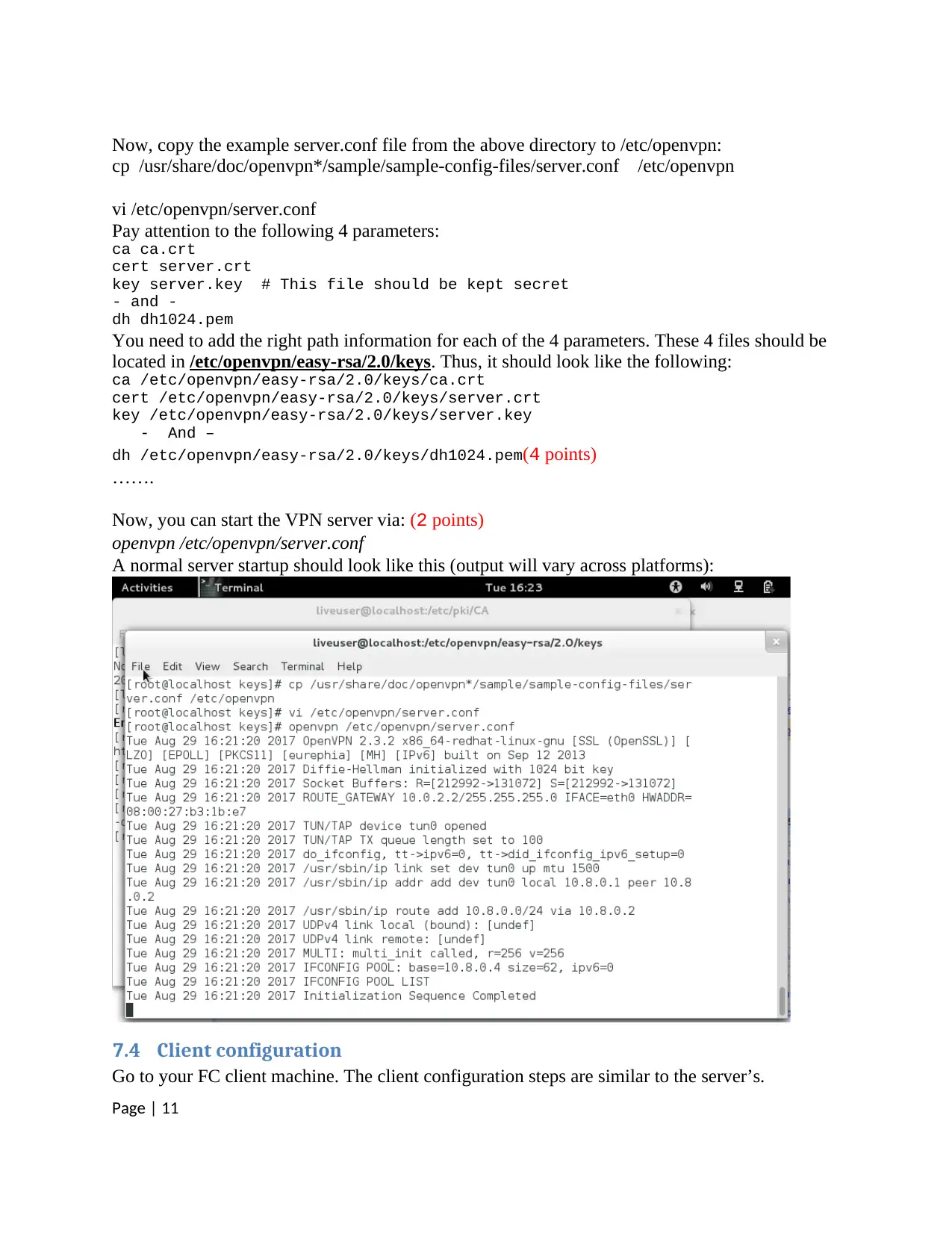
Now, copy the example server.conf file from the above directory to /etc/openvpn:
cp /usr/share/doc/openvpn*/sample/sample-config-files/server.conf /etc/openvpn
vi /etc/openvpn/server.conf
Pay attention to the following 4 parameters:
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
- and -
dh dh1024.pem
You need to add the right path information for each of the 4 parameters. These 4 files should be
located in /etc/openvpn/easy-rsa/2.0/keys. Thus, it should look like the following:
ca /etc/openvpn/easy-rsa/2.0/keys/ca.crt
cert /etc/openvpn/easy-rsa/2.0/keys/server.crt
key /etc/openvpn/easy-rsa/2.0/keys/server.key
- And –
dh /etc/openvpn/easy-rsa/2.0/keys/dh1024.pem(4 points)
…….
Now, you can start the VPN server via: (2 points)
openvpn /etc/openvpn/server.conf
A normal server startup should look like this (output will vary across platforms):
7.4 Client configuration
Go to your FC client machine. The client configuration steps are similar to the server’s.
Page | 11
cp /usr/share/doc/openvpn*/sample/sample-config-files/server.conf /etc/openvpn
vi /etc/openvpn/server.conf
Pay attention to the following 4 parameters:
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
- and -
dh dh1024.pem
You need to add the right path information for each of the 4 parameters. These 4 files should be
located in /etc/openvpn/easy-rsa/2.0/keys. Thus, it should look like the following:
ca /etc/openvpn/easy-rsa/2.0/keys/ca.crt
cert /etc/openvpn/easy-rsa/2.0/keys/server.crt
key /etc/openvpn/easy-rsa/2.0/keys/server.key
- And –
dh /etc/openvpn/easy-rsa/2.0/keys/dh1024.pem(4 points)
…….
Now, you can start the VPN server via: (2 points)
openvpn /etc/openvpn/server.conf
A normal server startup should look like this (output will vary across platforms):
7.4 Client configuration
Go to your FC client machine. The client configuration steps are similar to the server’s.
Page | 11
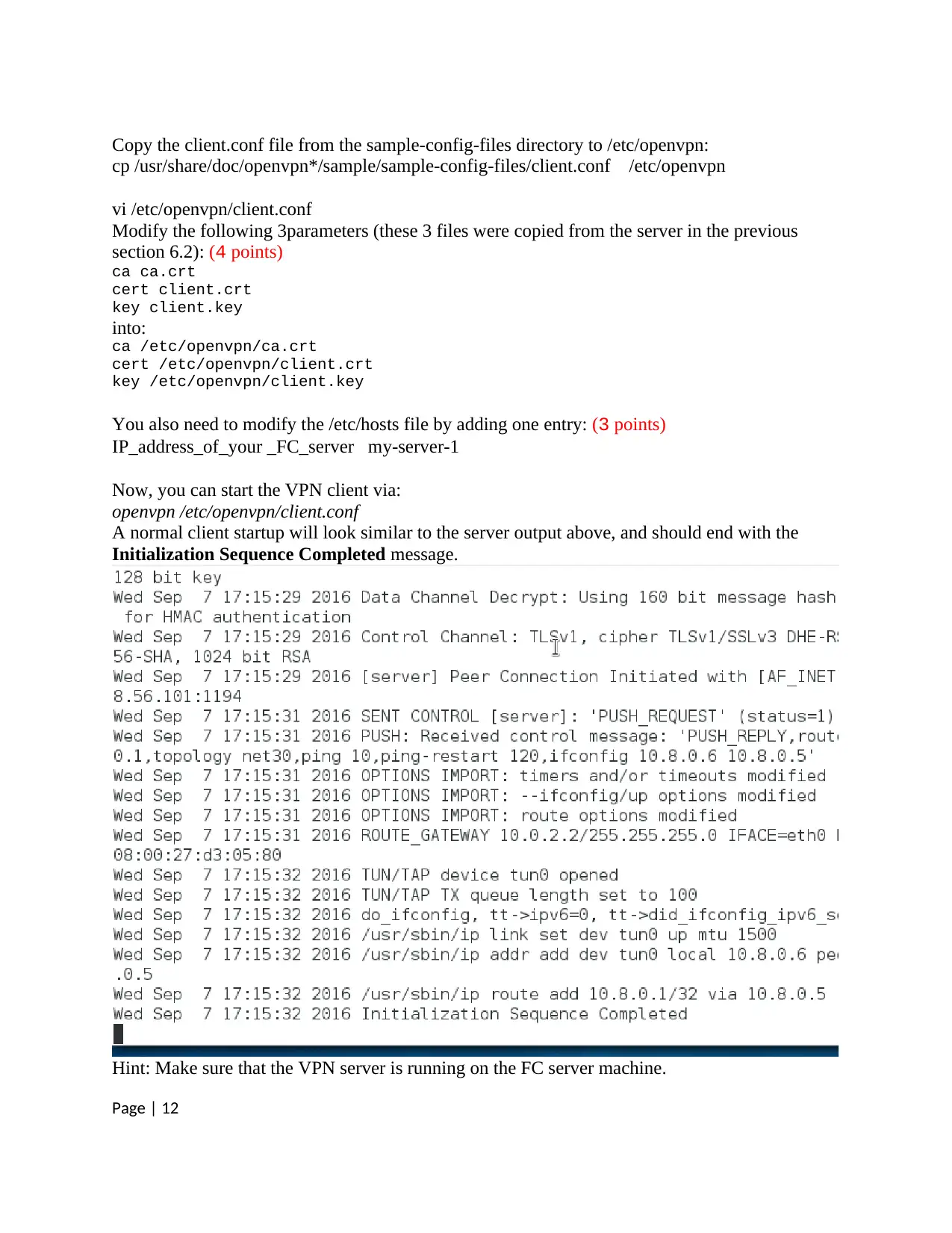
Copy the client.conf file from the sample-config-files directory to /etc/openvpn:
cp /usr/share/doc/openvpn*/sample/sample-config-files/client.conf /etc/openvpn
vi /etc/openvpn/client.conf
Modify the following 3parameters (these 3 files were copied from the server in the previous
section 6.2): (4 points)
ca ca.crt
cert client.crt
key client.key
into:
ca /etc/openvpn/ca.crt
cert /etc/openvpn/client.crt
key /etc/openvpn/client.key
You also need to modify the /etc/hosts file by adding one entry: (3 points)
IP_address_of_your _FC_server my-server-1
Now, you can start the VPN client via:
openvpn /etc/openvpn/client.conf
A normal client startup will look similar to the server output above, and should end with the
Initialization Sequence Completed message.
Hint: Make sure that the VPN server is running on the FC server machine.
Page | 12
cp /usr/share/doc/openvpn*/sample/sample-config-files/client.conf /etc/openvpn
vi /etc/openvpn/client.conf
Modify the following 3parameters (these 3 files were copied from the server in the previous
section 6.2): (4 points)
ca ca.crt
cert client.crt
key client.key
into:
ca /etc/openvpn/ca.crt
cert /etc/openvpn/client.crt
key /etc/openvpn/client.key
You also need to modify the /etc/hosts file by adding one entry: (3 points)
IP_address_of_your _FC_server my-server-1
Now, you can start the VPN client via:
openvpn /etc/openvpn/client.conf
A normal client startup will look similar to the server output above, and should end with the
Initialization Sequence Completed message.
Hint: Make sure that the VPN server is running on the FC server machine.
Page | 12

Now, try a ping across the VPN from the client:
ping 10.8.0.1
If the ping succeeds, congratulations! You now have a functioning SSL based VPN. (3 points)
Start the Wireshark to capture the ongoing ping packets.
7.4.1 Check whether the ping packets are encrypted. (2 points)
7.4.2 In your words, explain what does this setup do? (2 points)
8 Configure client certificates for authentication (optional) (10 points)
Sometime, you may want to limit the access to certain content on a web site. One common
approach is to set up user name and password pairs for access control. Another stronger approach
is to deploy client certificates for authentication.
If you have some time, please try to set up client certificates for authentication.
Page | 13
ping 10.8.0.1
If the ping succeeds, congratulations! You now have a functioning SSL based VPN. (3 points)
Start the Wireshark to capture the ongoing ping packets.
7.4.1 Check whether the ping packets are encrypted. (2 points)
7.4.2 In your words, explain what does this setup do? (2 points)
8 Configure client certificates for authentication (optional) (10 points)
Sometime, you may want to limit the access to certain content on a web site. One common
approach is to set up user name and password pairs for access control. Another stronger approach
is to deploy client certificates for authentication.
If you have some time, please try to set up client certificates for authentication.
Page | 13
1 out of 13
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)