PROJ6000: Project Management in Reserve Bank of Australia
VerifiedAdded on 2022/09/18
|15
|1257
|25
Presentation
AI Summary
This presentation analyzes project management practices within the Reserve Bank of Australia (RBA), focusing on a cyber security implementation project. It outlines the project management processes, including initiation, planning, execution, validation, and closure. The PMBOK methodology is used to guide the project, emphasizing its strategic alignment, security goals, and cost control. The presentation details the importance of PMBOK, project selection methods like benefit measurement, and the project management knowledge areas such as integration, scope, schedule, cost, quality, communication, resource, risk, procurement, and stakeholder management. It also explores the role of a project manager, project success factors (technical expertise, detailed planning, experienced leadership, flexible communication, issue resolution, risk assessment, and strong project closure), and project failure factors (lack of cooperation, poor technical implementation, unrealistic demands). The consequences of project failures, including financial crisis and loss of reputation, are also discussed. References to relevant literature are included.

PROJECT
MANAGEMENT
IN
RESERVE BANK
OF
AUSTRALIA
MANAGEMENT
IN
RESERVE BANK
OF
AUSTRALIA
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Management
■ A project is the accomplishment of a goal
with a desired outcome.
■ Project Management is the set of
activities that is carried out accurately in
order to accomplish the project
successfully.
■ Project Management activities are not
routine operations, but a combination of
specific tasks relevant to the project
(Kerzner, 2017).
■ Efficient management of a project is done
by a competent project manager to make
it successful.
■ A project is the accomplishment of a goal
with a desired outcome.
■ Project Management is the set of
activities that is carried out accurately in
order to accomplish the project
successfully.
■ Project Management activities are not
routine operations, but a combination of
specific tasks relevant to the project
(Kerzner, 2017).
■ Efficient management of a project is done
by a competent project manager to make
it successful.

Reserve Bank of Australia
■ It is the central bank of Australia, since 14th
January, 1960 (Rees, Smith & Hall, 2016)
■ The bank has its headquarters at Sydney of
New South Wales in Australia.
■ Philip Lowe is the current governor of the
bank.
■ Have the authority to issue notes of the
nation.
■ Provides employment to the responsible
citizens of Australia.
■ Maintains the economic growth and
prosperity of the country.
■ It is the central bank of Australia, since 14th
January, 1960 (Rees, Smith & Hall, 2016)
■ The bank has its headquarters at Sydney of
New South Wales in Australia.
■ Philip Lowe is the current governor of the
bank.
■ Have the authority to issue notes of the
nation.
■ Provides employment to the responsible
citizens of Australia.
■ Maintains the economic growth and
prosperity of the country.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cyber Security at RBA
■ Gain an insight about the network
traffic of the bank and implement data
security technologies.
■ Extension in layers of Security by multi-
factor authentication.
■ Optimum protection of data by
encrypting devices.
■ Incorporate Advanced Threat Protection
(ATP) to combat hacking of data.
■ Train employees at RBA after
completion of the cyber security
project.
■ Gain an insight about the network
traffic of the bank and implement data
security technologies.
■ Extension in layers of Security by multi-
factor authentication.
■ Optimum protection of data by
encrypting devices.
■ Incorporate Advanced Threat Protection
(ATP) to combat hacking of data.
■ Train employees at RBA after
completion of the cyber security
project.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project Management Processes
■ Initiation- Determine the requirements of cyber
security in bank and conduct a feasibility study.
■ Planning- Determine the steps of implementing
firewalls and encryption algorithms.
■ Execution- Implement strong encryption on
devices and networks, apply firewalls in
different layers of network, enhance security
(Lientz & Rea, 2016).
■ Validation- Test the systems after the
implementation of cyber security measure and
detect authentication.
■ Closure- If everything works well, close project
and deploy for commercial use.
■ Initiation- Determine the requirements of cyber
security in bank and conduct a feasibility study.
■ Planning- Determine the steps of implementing
firewalls and encryption algorithms.
■ Execution- Implement strong encryption on
devices and networks, apply firewalls in
different layers of network, enhance security
(Lientz & Rea, 2016).
■ Validation- Test the systems after the
implementation of cyber security measure and
detect authentication.
■ Closure- If everything works well, close project
and deploy for commercial use.

PMBOK Project Management
MethodologyPMBOK methodology of project management
is used to implement cyber security
protection in the Reserve Bank of Australia.
The PMBOK guide provides for a standard set
of “Comprehensive Security Policy” that will
help the engineers and the technical experts
to provide optimum quality of work with
regard to privacy of data, integrity in
systems, developing architectures and many
other aspects (Chavez, 2018).
Following the PMBOK methods, the cyber
security project in RBA will help to instill
confidence amongst the stakeholders that
quality is maintained at every firewall
implementation and network security.
MethodologyPMBOK methodology of project management
is used to implement cyber security
protection in the Reserve Bank of Australia.
The PMBOK guide provides for a standard set
of “Comprehensive Security Policy” that will
help the engineers and the technical experts
to provide optimum quality of work with
regard to privacy of data, integrity in
systems, developing architectures and many
other aspects (Chavez, 2018).
Following the PMBOK methods, the cyber
security project in RBA will help to instill
confidence amongst the stakeholders that
quality is maintained at every firewall
implementation and network security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Importance of PMBOK
■ Strategic alignment is obtained in the
implementation of cyber security.
■ Ensures security goals of the work
processes in the money transaction
departments of RBA.
■ Accounts for a good technical expert
personnel to guide in the processes of
security implementation.
■ Ensures security standards in online
transactions and effective utilization of
resources.
■ Reduces costs and controls quality in
the system development process.
■ Strategic alignment is obtained in the
implementation of cyber security.
■ Ensures security goals of the work
processes in the money transaction
departments of RBA.
■ Accounts for a good technical expert
personnel to guide in the processes of
security implementation.
■ Ensures security standards in online
transactions and effective utilization of
resources.
■ Reduces costs and controls quality in
the system development process.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
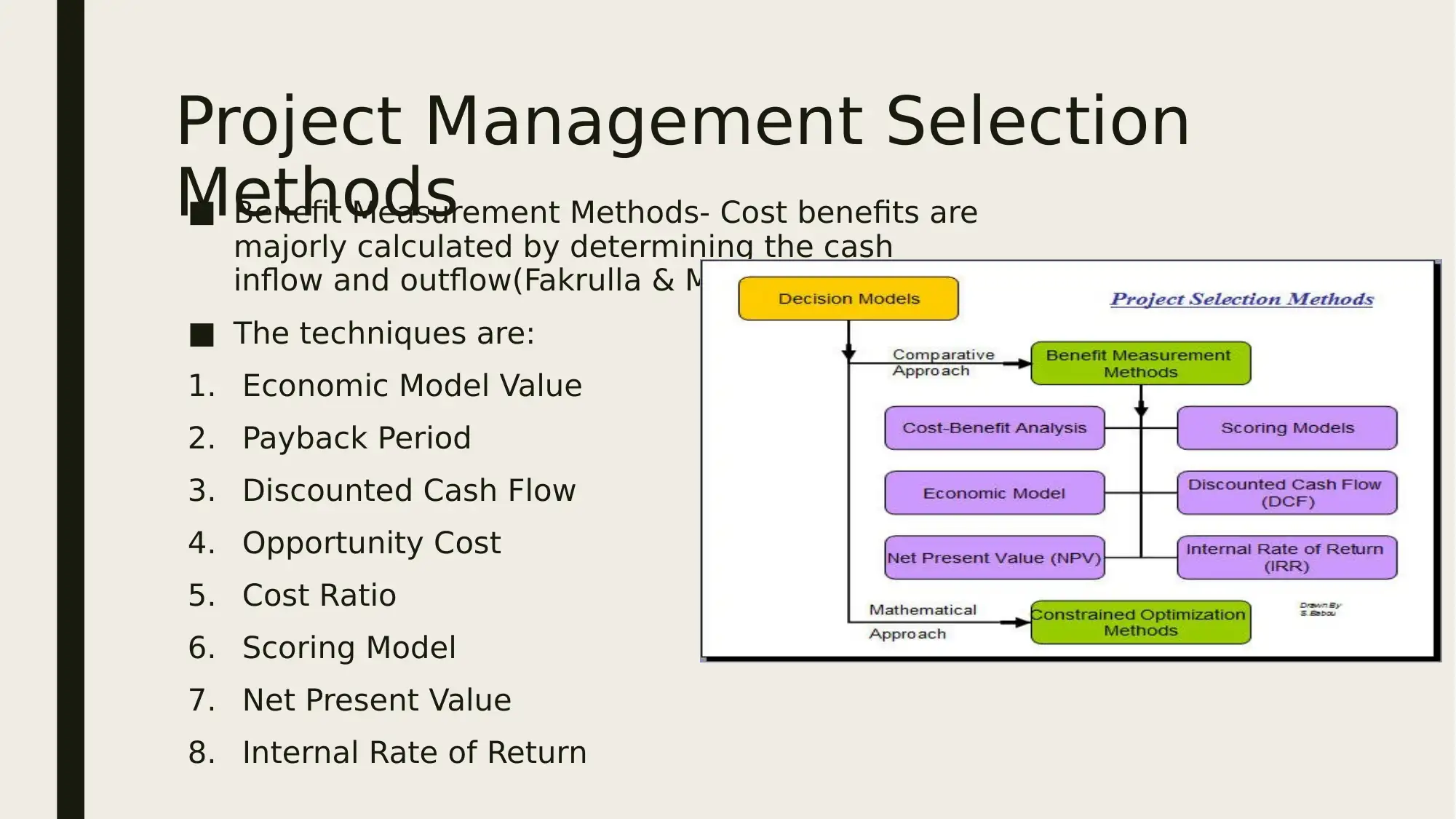
Project Management Selection
Methods■ Benefit Measurement Methods- Cost benefits are
majorly calculated by determining the cash
inflow and outflow(Fakrulla & Mouli, 2019).
■ The techniques are:
1. Economic Model Value
2. Payback Period
3. Discounted Cash Flow
4. Opportunity Cost
5. Cost Ratio
6. Scoring Model
7. Net Present Value
8. Internal Rate of Return
Methods■ Benefit Measurement Methods- Cost benefits are
majorly calculated by determining the cash
inflow and outflow(Fakrulla & Mouli, 2019).
■ The techniques are:
1. Economic Model Value
2. Payback Period
3. Discounted Cash Flow
4. Opportunity Cost
5. Cost Ratio
6. Scoring Model
7. Net Present Value
8. Internal Rate of Return
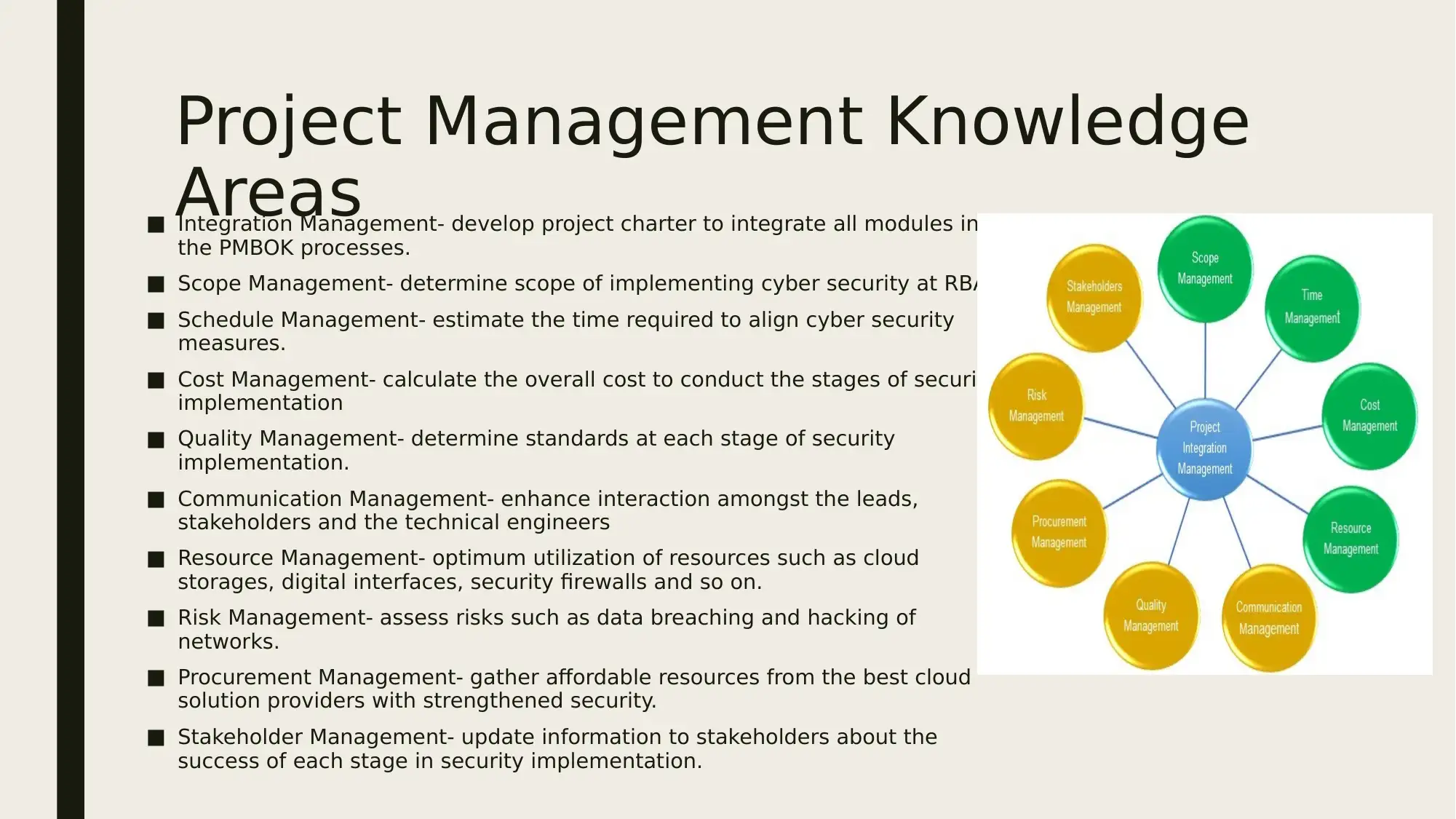
Project Management Knowledge
Areas■ Integration Management- develop project charter to integrate all modules in
the PMBOK processes.
■ Scope Management- determine scope of implementing cyber security at RBA.
■ Schedule Management- estimate the time required to align cyber security
measures.
■ Cost Management- calculate the overall cost to conduct the stages of security
implementation
■ Quality Management- determine standards at each stage of security
implementation.
■ Communication Management- enhance interaction amongst the leads,
stakeholders and the technical engineers
■ Resource Management- optimum utilization of resources such as cloud
storages, digital interfaces, security firewalls and so on.
■ Risk Management- assess risks such as data breaching and hacking of
networks.
■ Procurement Management- gather affordable resources from the best cloud
solution providers with strengthened security.
■ Stakeholder Management- update information to stakeholders about the
success of each stage in security implementation.
Areas■ Integration Management- develop project charter to integrate all modules in
the PMBOK processes.
■ Scope Management- determine scope of implementing cyber security at RBA.
■ Schedule Management- estimate the time required to align cyber security
measures.
■ Cost Management- calculate the overall cost to conduct the stages of security
implementation
■ Quality Management- determine standards at each stage of security
implementation.
■ Communication Management- enhance interaction amongst the leads,
stakeholders and the technical engineers
■ Resource Management- optimum utilization of resources such as cloud
storages, digital interfaces, security firewalls and so on.
■ Risk Management- assess risks such as data breaching and hacking of
networks.
■ Procurement Management- gather affordable resources from the best cloud
solution providers with strengthened security.
■ Stakeholder Management- update information to stakeholders about the
success of each stage in security implementation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Role of a Project Manager
■ Conduct requirement gathering and analysis for
the cyber security implementation at RBA
■ Plan the schedule, cost, stages and technical
expertise.
■ Execute the operations for implementing
security in all devices of the bank step wise.
■ Determine risks of data hacking and mitigation
measures of security algorithms.
■ Determine quality control in firewalls, password
authentication and other encryption algorithms.
■ Enhance communication amongst technical
engineers and non-technical experts.
■ Involve stakeholders of the bank and the
government sponsors at every stage.
■ Conduct requirement gathering and analysis for
the cyber security implementation at RBA
■ Plan the schedule, cost, stages and technical
expertise.
■ Execute the operations for implementing
security in all devices of the bank step wise.
■ Determine risks of data hacking and mitigation
measures of security algorithms.
■ Determine quality control in firewalls, password
authentication and other encryption algorithms.
■ Enhance communication amongst technical
engineers and non-technical experts.
■ Involve stakeholders of the bank and the
government sponsors at every stage.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Success Factors
■ Involvement of technical engineers who will have
sound knowledge on cyber security.
■ Comprehensive and detailed planning of
requirements, budget and schedule (Rogers, 2019).
■ Leadership of a good and experienced project
leader and co-operation of the bank members.
■ Flexible communication amongst the project
members and stakeholders such as RBA executive
personnel and cloud service providers.
■ Immediate resolve of issues in the ongoing
activities of security implantation.
■ Assessment of risks such as hacking or malicious
activities in advance.
■ Incorporating strong closure of project by live
functioning of the bank operations aligned with
security measures.
■ Involvement of technical engineers who will have
sound knowledge on cyber security.
■ Comprehensive and detailed planning of
requirements, budget and schedule (Rogers, 2019).
■ Leadership of a good and experienced project
leader and co-operation of the bank members.
■ Flexible communication amongst the project
members and stakeholders such as RBA executive
personnel and cloud service providers.
■ Immediate resolve of issues in the ongoing
activities of security implantation.
■ Assessment of risks such as hacking or malicious
activities in advance.
■ Incorporating strong closure of project by live
functioning of the bank operations aligned with
security measures.
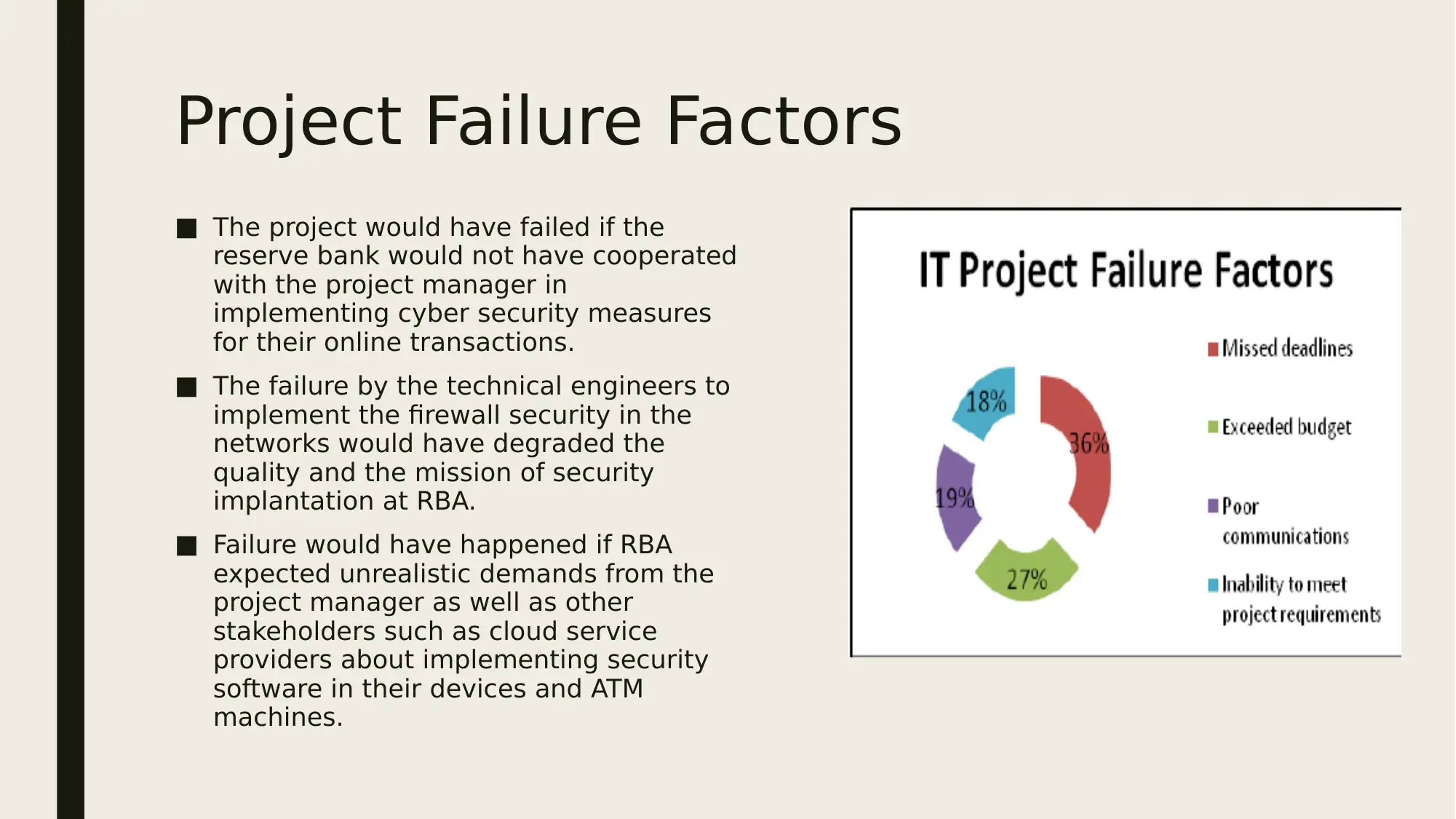
Project Failure Factors
■ The project would have failed if the
reserve bank would not have cooperated
with the project manager in
implementing cyber security measures
for their online transactions.
■ The failure by the technical engineers to
implement the firewall security in the
networks would have degraded the
quality and the mission of security
implantation at RBA.
■ Failure would have happened if RBA
expected unrealistic demands from the
project manager as well as other
stakeholders such as cloud service
providers about implementing security
software in their devices and ATM
machines.
■ The project would have failed if the
reserve bank would not have cooperated
with the project manager in
implementing cyber security measures
for their online transactions.
■ The failure by the technical engineers to
implement the firewall security in the
networks would have degraded the
quality and the mission of security
implantation at RBA.
■ Failure would have happened if RBA
expected unrealistic demands from the
project manager as well as other
stakeholders such as cloud service
providers about implementing security
software in their devices and ATM
machines.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

![Cyber Security Research Paper Abstract - [University] - [Course Name]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fbd%2F04151bc652ee49f480e5594ea23a69c7.jpg&w=256&q=75)



