Cloud Security Project: Proposal, Plan, and Development Strategy
VerifiedAdded on 2020/03/07
|12
|2096
|1387
Project
AI Summary
This project proposal outlines a comprehensive plan to address the challenges of cloud security. It begins by identifying the increasing security risks associated with cloud adoption, including threats to data integrity, privacy, and availability. The research questions focus on identifying security threats, available solutions, latest protective technologies, and best practices. The conceptual framework introduces cloud computing concepts and highlights innovations in security systems, including XML encryption, SAML, and Kerberos. The methodology involves qualitative research, collecting data from journals, security websites, and academic reports. The project includes a detailed work breakdown structure, risk analysis, and Gantt chart for project management. The deliverables encompass an exploration of risks, security attacks, and the analysis of various solutions to enhance the security of cloud computing systems. The project aims to develop a security enhancement plan based on the analysis of case studies, which includes recommendations for strengthening cloud security.

Project proposal and plan - Cloud Security
[Student Name]
[Student Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project proposal and plan - Cloud Security
Table of Contents
Introduction......................................................................................................................3
Rationale...........................................................................................................................3
Problem domain........................................................................................................................3
Purpose and justification..........................................................................................................3
Sponsor or Supervisor recommendation..........................................................................3
Research Questions...........................................................................................................3
Conceptual or Theoretical Framework.............................................................................4
Introduction to Cloud Computing............................................................................................4
Innovation in Security Systems.................................................................................................4
Cloud Computing Security Framework....................................................................................5
Methodology.....................................................................................................................6
Research and Systems Development method............................................................................6
Data collection...........................................................................................................................6
Ethical Issues............................................................................................................................6
Compliance Requirements........................................................................................................6
Analysis of data.........................................................................................................................6
Project Plan Deliverables.........................................................................................................7
Work breakdown structure (WBS)...........................................................................................7
Risk Analysis.............................................................................................................................8
Duration....................................................................................................................................9
Gantt chart......................................................................................................................10
References.......................................................................................................................11
2
Table of Contents
Introduction......................................................................................................................3
Rationale...........................................................................................................................3
Problem domain........................................................................................................................3
Purpose and justification..........................................................................................................3
Sponsor or Supervisor recommendation..........................................................................3
Research Questions...........................................................................................................3
Conceptual or Theoretical Framework.............................................................................4
Introduction to Cloud Computing............................................................................................4
Innovation in Security Systems.................................................................................................4
Cloud Computing Security Framework....................................................................................5
Methodology.....................................................................................................................6
Research and Systems Development method............................................................................6
Data collection...........................................................................................................................6
Ethical Issues............................................................................................................................6
Compliance Requirements........................................................................................................6
Analysis of data.........................................................................................................................6
Project Plan Deliverables.........................................................................................................7
Work breakdown structure (WBS)...........................................................................................7
Risk Analysis.............................................................................................................................8
Duration....................................................................................................................................9
Gantt chart......................................................................................................................10
References.......................................................................................................................11
2

Project proposal and plan - Cloud Security
Introduction
This paper explores the challenges in the cloud security so that a plan for the enhancement of
security can be formulated. The report explains the key security issues and challenges faced
in cloud based systems, explore the theoretical framework for development of a methodology
for exploration, methods used for data collection, and work break down structure highlighting
key tasks in the research.
Rationale
Problem domain
Adoption of cloud solutions for business management and other personal uses is increasing
day by day and on the other side, there also exposed to increasing number of security risks
that are raising concern. While security professionals have come up with several security
measures, attacks are also becoming sophisticated in their approaches and have developed
new strategies to attack data on cloud. There are a number of dimensions on which security
of the cloud can be compromised including integrity, privacy, availability, confidentiality,
authenticity and non-repudiation. With these challenges, it has become essential to keep
enhancing the security systems so that cloud users can be better protected (Ma, 2008).
Purpose and justification
The aim of this research is to explore the problem of cloud security and the innovations in
cloud security space to overcome these problems. As the cloud adoption is increasing day by
day with many companies also using cloud for their critical infrastructure management, it has
become a precursor to explore and mitigate the security risks these platforms are faced with.
A range of security risks are faced by cloud platforms such as intellectual property theft,
compliance violation, contractual breaches, data breaches, and so on(OECD, 2008).
Sponsor or Supervisor recommendation
Supervisor has recommended exploring the security threats to cloud security as well as the
solutions used for protection.
3
Introduction
This paper explores the challenges in the cloud security so that a plan for the enhancement of
security can be formulated. The report explains the key security issues and challenges faced
in cloud based systems, explore the theoretical framework for development of a methodology
for exploration, methods used for data collection, and work break down structure highlighting
key tasks in the research.
Rationale
Problem domain
Adoption of cloud solutions for business management and other personal uses is increasing
day by day and on the other side, there also exposed to increasing number of security risks
that are raising concern. While security professionals have come up with several security
measures, attacks are also becoming sophisticated in their approaches and have developed
new strategies to attack data on cloud. There are a number of dimensions on which security
of the cloud can be compromised including integrity, privacy, availability, confidentiality,
authenticity and non-repudiation. With these challenges, it has become essential to keep
enhancing the security systems so that cloud users can be better protected (Ma, 2008).
Purpose and justification
The aim of this research is to explore the problem of cloud security and the innovations in
cloud security space to overcome these problems. As the cloud adoption is increasing day by
day with many companies also using cloud for their critical infrastructure management, it has
become a precursor to explore and mitigate the security risks these platforms are faced with.
A range of security risks are faced by cloud platforms such as intellectual property theft,
compliance violation, contractual breaches, data breaches, and so on(OECD, 2008).
Sponsor or Supervisor recommendation
Supervisor has recommended exploring the security threats to cloud security as well as the
solutions used for protection.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Project proposal and plan - Cloud Security
Research Questions
What security threats are faced by cloud computing technologies?
What cloud security solutions are available and how do they work?
What latest technologies are used for protection of cloud platforms?
What are the best practices in cloud security enhancement?(Optus, 2016)
Conceptual or Theoretical Framework
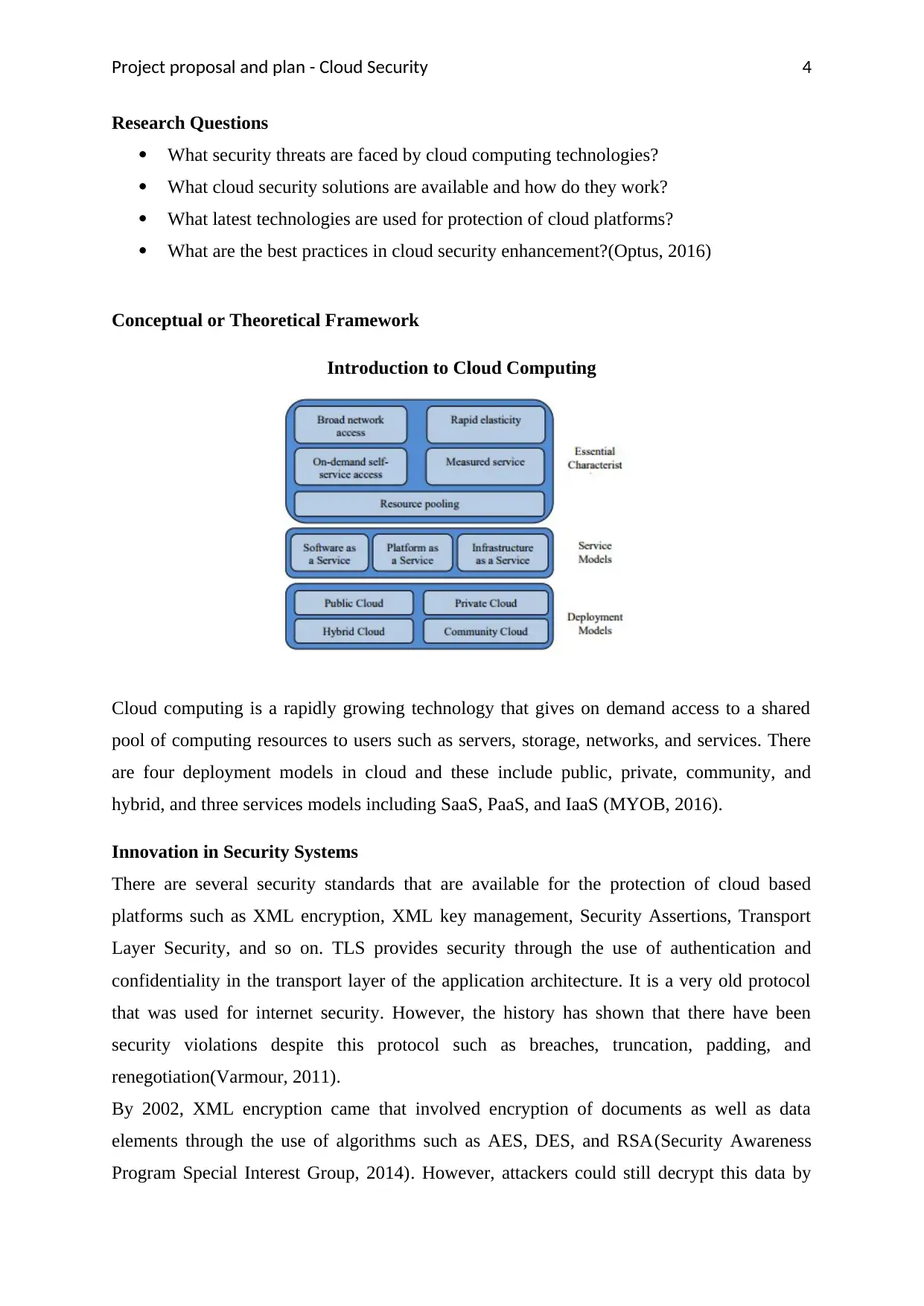
Introduction to Cloud Computing
Cloud computing is a rapidly growing technology that gives on demand access to a shared
pool of computing resources to users such as servers, storage, networks, and services. There
are four deployment models in cloud and these include public, private, community, and
hybrid, and three services models including SaaS, PaaS, and IaaS (MYOB, 2016).
Innovation in Security Systems
There are several security standards that are available for the protection of cloud based
platforms such as XML encryption, XML key management, Security Assertions, Transport
Layer Security, and so on. TLS provides security through the use of authentication and
confidentiality in the transport layer of the application architecture. It is a very old protocol
that was used for internet security. However, the history has shown that there have been
security violations despite this protocol such as breaches, truncation, padding, and
renegotiation(Varmour, 2011).
By 2002, XML encryption came that involved encryption of documents as well as data
elements through the use of algorithms such as AES, DES, and RSA(Security Awareness
Program Special Interest Group, 2014). However, attackers could still decrypt this data by
4
Research Questions
What security threats are faced by cloud computing technologies?
What cloud security solutions are available and how do they work?
What latest technologies are used for protection of cloud platforms?
What are the best practices in cloud security enhancement?(Optus, 2016)
Conceptual or Theoretical Framework
Introduction to Cloud Computing
Cloud computing is a rapidly growing technology that gives on demand access to a shared
pool of computing resources to users such as servers, storage, networks, and services. There
are four deployment models in cloud and these include public, private, community, and
hybrid, and three services models including SaaS, PaaS, and IaaS (MYOB, 2016).
Innovation in Security Systems
There are several security standards that are available for the protection of cloud based
platforms such as XML encryption, XML key management, Security Assertions, Transport
Layer Security, and so on. TLS provides security through the use of authentication and
confidentiality in the transport layer of the application architecture. It is a very old protocol
that was used for internet security. However, the history has shown that there have been
security violations despite this protocol such as breaches, truncation, padding, and
renegotiation(Varmour, 2011).
By 2002, XML encryption came that involved encryption of documents as well as data
elements through the use of algorithms such as AES, DES, and RSA(Security Awareness
Program Special Interest Group, 2014). However, attackers could still decrypt this data by
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project proposal and plan - Cloud Security
sending modified ciphers. To prevent this from happening, XML signature was added to the
security layer (Luhach, Dwivedi, & Jha, 2014). It reduced the vulnerabilities but added more
issues due to complexities involved. XKMS was the next innovation in the security space that
created an interface between the XML code and the web space KPI. The attacks upgraded
themselves with newer attacks in response such as reply attacks and Denial of Service attacks
that failed even XKMS security (Youseef & Liu, 2012)
A variety of other attempts to secure systems exposed to internet included SAML and
Kerberos for authentication and authorization to enhance protection against the reply attacks
and other attacks like eavesdropping (TrustSphere, 2012).
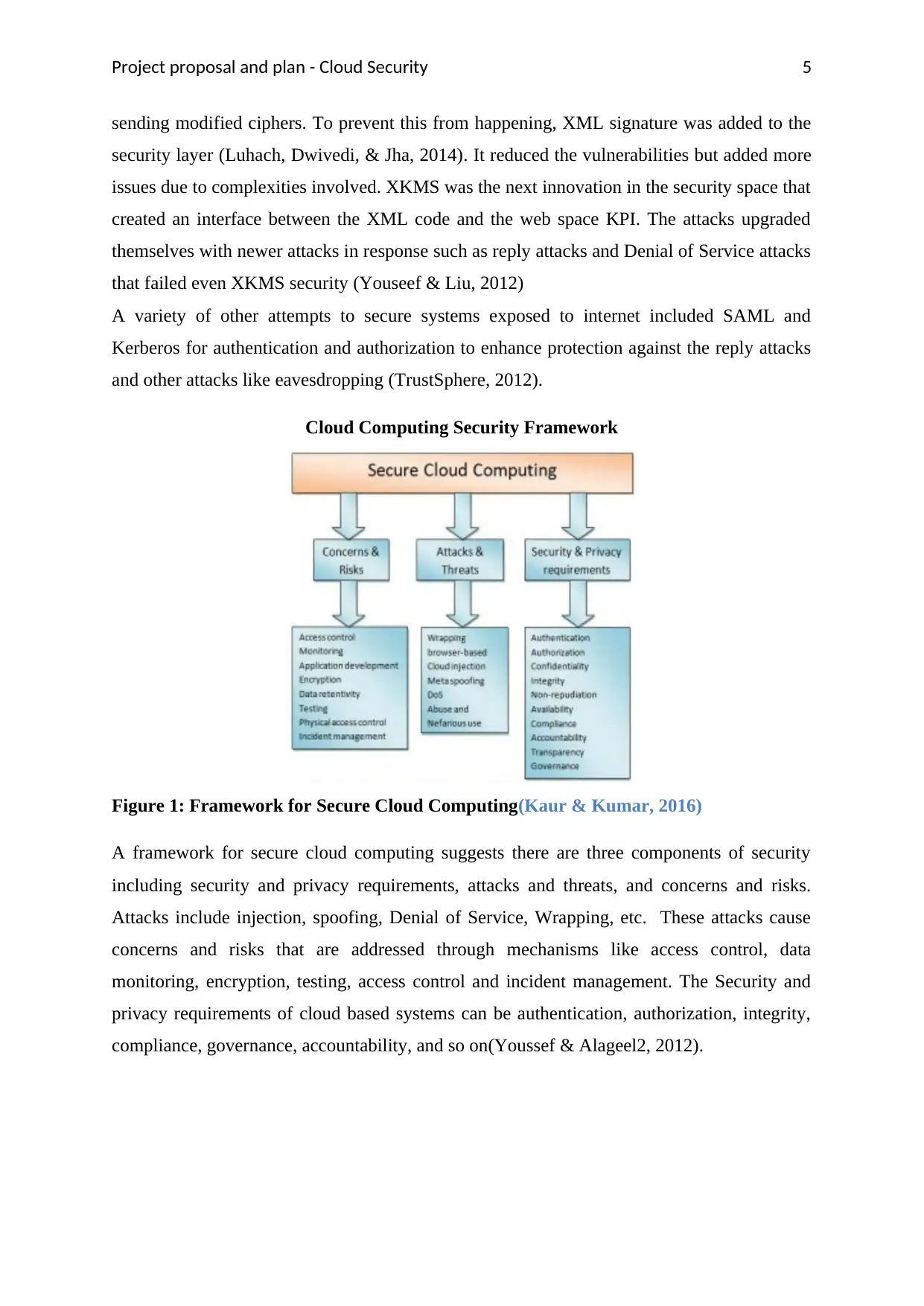
Cloud Computing Security Framework
Figure 1: Framework for Secure Cloud Computing(Kaur & Kumar, 2016)
A framework for secure cloud computing suggests there are three components of security
including security and privacy requirements, attacks and threats, and concerns and risks.
Attacks include injection, spoofing, Denial of Service, Wrapping, etc. These attacks cause
concerns and risks that are addressed through mechanisms like access control, data
monitoring, encryption, testing, access control and incident management. The Security and
privacy requirements of cloud based systems can be authentication, authorization, integrity,
compliance, governance, accountability, and so on(Youssef & Alageel2, 2012).
5
sending modified ciphers. To prevent this from happening, XML signature was added to the
security layer (Luhach, Dwivedi, & Jha, 2014). It reduced the vulnerabilities but added more
issues due to complexities involved. XKMS was the next innovation in the security space that
created an interface between the XML code and the web space KPI. The attacks upgraded
themselves with newer attacks in response such as reply attacks and Denial of Service attacks
that failed even XKMS security (Youseef & Liu, 2012)
A variety of other attempts to secure systems exposed to internet included SAML and
Kerberos for authentication and authorization to enhance protection against the reply attacks
and other attacks like eavesdropping (TrustSphere, 2012).
Cloud Computing Security Framework
Figure 1: Framework for Secure Cloud Computing(Kaur & Kumar, 2016)
A framework for secure cloud computing suggests there are three components of security
including security and privacy requirements, attacks and threats, and concerns and risks.
Attacks include injection, spoofing, Denial of Service, Wrapping, etc. These attacks cause
concerns and risks that are addressed through mechanisms like access control, data
monitoring, encryption, testing, access control and incident management. The Security and
privacy requirements of cloud based systems can be authentication, authorization, integrity,
compliance, governance, accountability, and so on(Youssef & Alageel2, 2012).
5

Project proposal and plan - Cloud Security
Methodology
Research and Systems Development method
The research would utilize the cloud security framework as the base to determine different
types of threats, risks and the innovations in the security systems used for protection of cloud
computing. As per this framework, the study on cloud computing security can explore threats,
risks, and security requirements. Each of the areas would be explored in the case studies
taking threats or attacks as the key problem causing threats such that the innovations done for
combating them would be identified.
Data collection
For exploring the challenges and solutions to the security issues in cloud computing, a
qualitative research would be conducted where the data on risks, threats and security
technologies would be collected journals, security websites, and academic research reports.
Specific cases of cloud security solutions would be studied for which the data would be taken
from past journals and research reports (Optus, 2016).
Ethical Issues
The secondary data would only be collected from the authentic sources that have verifiable
data. To ensure that the research maintains the ethical code, the data obtained would not be
modified by would be used in the case study analysis as it is(MYOB, 2016).
Compliance Requirements
This project would present solutions based on the defined security framework for cloud
computing.
Analysis of data
A multiple case study analysis would be conducted on the secondary cases data to extract the
data on risks, threats and security solutions. The case studies would include the exploration of
some of the security threats like DDOS, cloud injection, and Meta spoofing. In each case, the
risks and possible solutions would be explored to identify innovative solutions that were able
to secure the cloud against these risks. Further, upon getting the analysis of all cases, a
combined case study analysis would be performed on the results obtained to come up with
the final recommendations for the enhancement of the security of a cloud system.
6
Methodology
Research and Systems Development method
The research would utilize the cloud security framework as the base to determine different
types of threats, risks and the innovations in the security systems used for protection of cloud
computing. As per this framework, the study on cloud computing security can explore threats,
risks, and security requirements. Each of the areas would be explored in the case studies
taking threats or attacks as the key problem causing threats such that the innovations done for
combating them would be identified.
Data collection
For exploring the challenges and solutions to the security issues in cloud computing, a
qualitative research would be conducted where the data on risks, threats and security
technologies would be collected journals, security websites, and academic research reports.
Specific cases of cloud security solutions would be studied for which the data would be taken
from past journals and research reports (Optus, 2016).
Ethical Issues
The secondary data would only be collected from the authentic sources that have verifiable
data. To ensure that the research maintains the ethical code, the data obtained would not be
modified by would be used in the case study analysis as it is(MYOB, 2016).
Compliance Requirements
This project would present solutions based on the defined security framework for cloud
computing.
Analysis of data
A multiple case study analysis would be conducted on the secondary cases data to extract the
data on risks, threats and security solutions. The case studies would include the exploration of
some of the security threats like DDOS, cloud injection, and Meta spoofing. In each case, the
risks and possible solutions would be explored to identify innovative solutions that were able
to secure the cloud against these risks. Further, upon getting the analysis of all cases, a
combined case study analysis would be performed on the results obtained to come up with
the final recommendations for the enhancement of the security of a cloud system.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project proposal and plan - Cloud Security
Project Plan
Deliverables
The deliverables of this research project are:
Exploration of various types of risks and concerned in the security of cloud
computing
Study of various types of security attacks such as spoofing, DDOS and injection
attacks
Exploration of cases of types of attacks and the solutions used for protection
Analysis of different case to identify best security solutions
Recommendations on enhancing the security of the cloud computing system based on
case study analysis
Development of a security enhancement plan based on the security solutions
identified in the data analysis as efficient.
Work breakdown structure (WBS)
1.0 Explore Literature
1.1 Cloud Computing system
1.2 Security Concerns and Risks
1.3 Security Threats and Attacks
1.4 Security Solutions
2.0 System development framework
2.1 Cloud Security Framework
2.2 Study of Security components
2.2.1 Risks and Concerns
2.2.2 Threats and attacks
2.2.2.1 Spoofing
2.2.2.2 DDOS
2.2.2.3 Cloud Injection
2.2.3 Security Technologies
3.0 data collection
3.1 Case Studies
3.1.1 Journals
7
Project Plan
Deliverables
The deliverables of this research project are:
Exploration of various types of risks and concerned in the security of cloud
computing
Study of various types of security attacks such as spoofing, DDOS and injection
attacks
Exploration of cases of types of attacks and the solutions used for protection
Analysis of different case to identify best security solutions
Recommendations on enhancing the security of the cloud computing system based on
case study analysis
Development of a security enhancement plan based on the security solutions
identified in the data analysis as efficient.
Work breakdown structure (WBS)
1.0 Explore Literature
1.1 Cloud Computing system
1.2 Security Concerns and Risks
1.3 Security Threats and Attacks
1.4 Security Solutions
2.0 System development framework
2.1 Cloud Security Framework
2.2 Study of Security components
2.2.1 Risks and Concerns
2.2.2 Threats and attacks
2.2.2.1 Spoofing
2.2.2.2 DDOS
2.2.2.3 Cloud Injection
2.2.3 Security Technologies
3.0 data collection
3.1 Case Studies
3.1.1 Journals
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project proposal and plan - Cloud Security
3.1.2 Research reports
3.1.3 Security companies websites
4.0 Case Study analysis
4.1 Case Study analysis
4.2 Multiple case study analysis
4.3 Security solutions
5.0 Cloud Security System development
5.1 Security components
5.2 development methodology
5.3 Security Solutions
6.0 project closure
Risk Analysis
The table below shows various types of risks that can occur on the research project and
presents a response plan to deal with them/
Risk Probability Impact Response plan
Sufficient literature
may not be found for
collection of case
data
Medium High The scope of research
cases would be
limited to only few
threats that have the
data available
Delays can happen in
completion of
research tasks
Medium Medium The researcher would
create a timeline for
milestones and would
keep monitoring the
work against it to
ensure that the
research steps are
conducted as per the
timeline
The results of the
research may not
sufficient to add
value to the field of
Low High The researcher would
do an exhaustive
study of literature,
identify gaps and
8
3.1.2 Research reports
3.1.3 Security companies websites
4.0 Case Study analysis
4.1 Case Study analysis
4.2 Multiple case study analysis
4.3 Security solutions
5.0 Cloud Security System development
5.1 Security components
5.2 development methodology
5.3 Security Solutions
6.0 project closure
Risk Analysis
The table below shows various types of risks that can occur on the research project and
presents a response plan to deal with them/
Risk Probability Impact Response plan
Sufficient literature
may not be found for
collection of case
data
Medium High The scope of research
cases would be
limited to only few
threats that have the
data available
Delays can happen in
completion of
research tasks
Medium Medium The researcher would
create a timeline for
milestones and would
keep monitoring the
work against it to
ensure that the
research steps are
conducted as per the
timeline
The results of the
research may not
sufficient to add
value to the field of
Low High The researcher would
do an exhaustive
study of literature,
identify gaps and
8
Project proposal and plan - Cloud Security
research would work on those
gaps to ensure that
the research findings
add value to the field
of research
The researcher may
not be able to make
any usable
recommendations on
the cloud security
Low High Before making
recommendations for
strengthening of the
cloud security, the
researcher would get
the probable solutions
discussed with the
tutor and peers to
ensure that the
selected solutions are
appropriate.
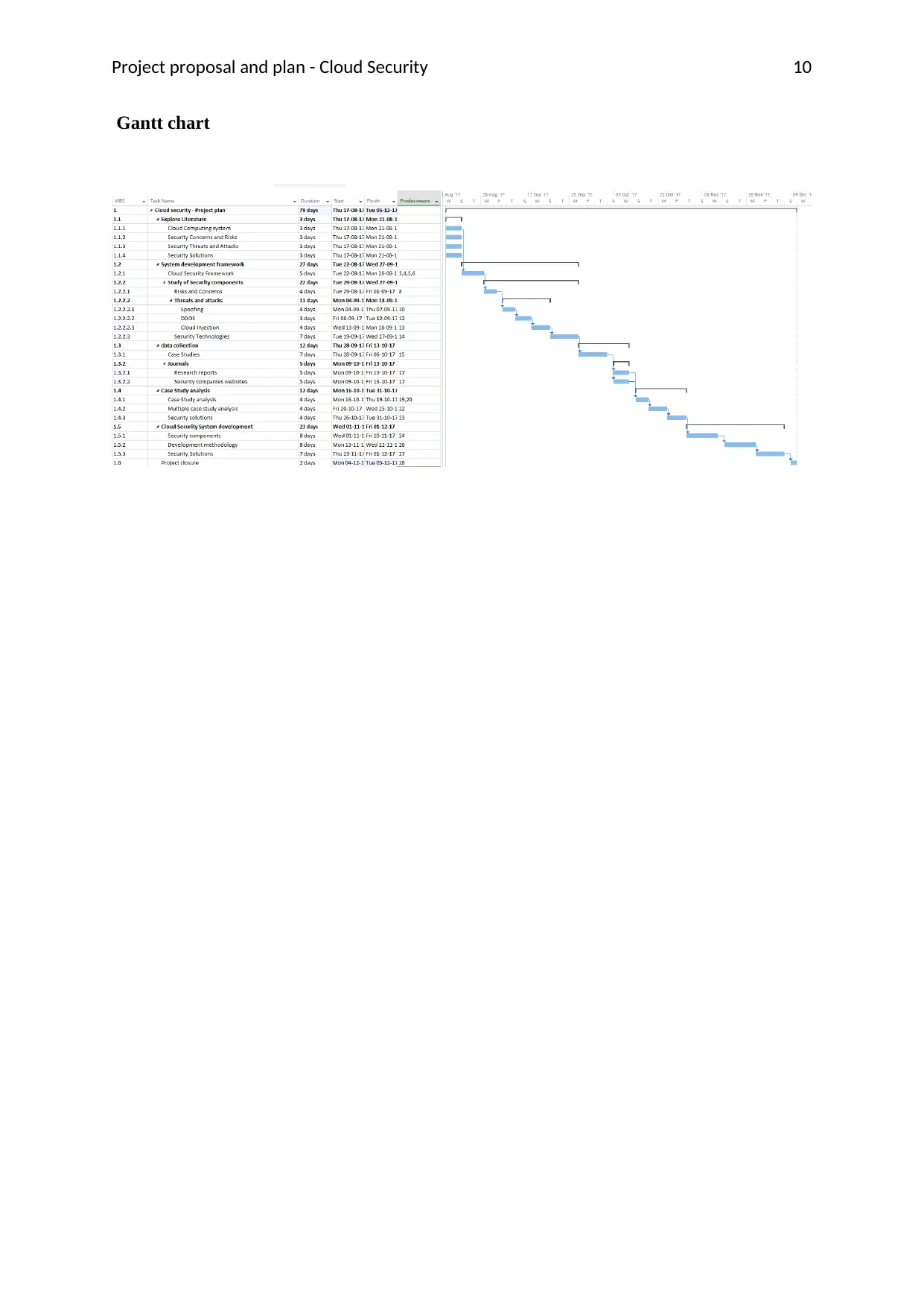
Duration
This research project would be completed in 3 months. The initial literature study would take
3 days and the data collection for case studies would take another 15 days. The case study
analysis would be finished in 20 days and the remaining days would be utilized for making
interpretations of data, making recommendations, and preparing the research report.
9
research would work on those
gaps to ensure that
the research findings
add value to the field
of research
The researcher may
not be able to make
any usable
recommendations on
the cloud security
Low High Before making
recommendations for
strengthening of the
cloud security, the
researcher would get
the probable solutions
discussed with the
tutor and peers to
ensure that the
selected solutions are
appropriate.
Duration
This research project would be completed in 3 months. The initial literature study would take
3 days and the data collection for case studies would take another 15 days. The case study
analysis would be finished in 20 days and the remaining days would be utilized for making
interpretations of data, making recommendations, and preparing the research report.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Project proposal and plan - Cloud Security
Gantt chart
10
Gantt chart
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project proposal and plan - Cloud Security
References
Kaur, S., & Kumar, D. (2016). Analysis of Cloud COmputing Security Framework in E-
governance. IJCST , 7 (1), 99-102.
Luhach, A. K., Dwivedi, D. S., & Jha, D. C. (2014). DESIGNING A LOGICAL SECURITY
FRAMEWORK FOR E-COMMERCE SYSTEM BASED ON SOA. International Journal
on Soft Computing (IJSC) , 5 (2), 1-10.
Ma, D. Q. (2008). A Review of Emerging Technology Trends in E-Commerce. International
Technology Management Review , 1 (2), 2-15.
MYOB. (2016, September 13). Company file security. Retrieved from MYOB:
http://help.myob.com/wiki/display/ar/Company+file+security
MYOB. (2016, September 13). Protecting your confidential information. Retrieved from
MYOB: http://myob.com.au/myob/australia/myob-security-recommendations-
1257829253909
OECD. (2008). Malicious Software (Malware): A security Threat to Internet Economy.
OECD.
Optus. (2016). Security in the cloud. Optus.
Security Awareness Program Special Interest Group. (2014). Best Practices for Implementing
a Security Awareness Program. PCI.
TrustSphere. (2012). Advanced Security Methods for eFraud and Messaging. TrustSphere.
Varmour. (2011). Pathway to Multi-Cloud Security Architecture. Varmour.
Youseef, A., & Liu, F. (2012). A new Framework to Model a Secure E-commerce System.
International Journal of Social, Behavioral, Educational, Economic, Business and Industrial
Engineering , 6 (2), 159-164.
Youssef, A. E., & Alageel2, M. (2012). A Framework for Secure Cloud Computing . IJCSI
International Journal of Computer Science Issues , 9 (4), 487-500.
11
References
Kaur, S., & Kumar, D. (2016). Analysis of Cloud COmputing Security Framework in E-
governance. IJCST , 7 (1), 99-102.
Luhach, A. K., Dwivedi, D. S., & Jha, D. C. (2014). DESIGNING A LOGICAL SECURITY
FRAMEWORK FOR E-COMMERCE SYSTEM BASED ON SOA. International Journal
on Soft Computing (IJSC) , 5 (2), 1-10.
Ma, D. Q. (2008). A Review of Emerging Technology Trends in E-Commerce. International
Technology Management Review , 1 (2), 2-15.
MYOB. (2016, September 13). Company file security. Retrieved from MYOB:
http://help.myob.com/wiki/display/ar/Company+file+security
MYOB. (2016, September 13). Protecting your confidential information. Retrieved from
MYOB: http://myob.com.au/myob/australia/myob-security-recommendations-
1257829253909
OECD. (2008). Malicious Software (Malware): A security Threat to Internet Economy.
OECD.
Optus. (2016). Security in the cloud. Optus.
Security Awareness Program Special Interest Group. (2014). Best Practices for Implementing
a Security Awareness Program. PCI.
TrustSphere. (2012). Advanced Security Methods for eFraud and Messaging. TrustSphere.
Varmour. (2011). Pathway to Multi-Cloud Security Architecture. Varmour.
Youseef, A., & Liu, F. (2012). A new Framework to Model a Secure E-commerce System.
International Journal of Social, Behavioral, Educational, Economic, Business and Industrial
Engineering , 6 (2), 159-164.
Youssef, A. E., & Alageel2, M. (2012). A Framework for Secure Cloud Computing . IJCSI
International Journal of Computer Science Issues , 9 (4), 487-500.
11

Project proposal and plan - Cloud Security 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





