Online Shopping System Project Report
VerifiedAdded on 2023/04/23
|22
|3826
|322
AI Summary
This project report is about the development of an online shopping system on Android platform. It includes feasibility study, work breakdown structure, project milestone statement, and more.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: Mobile Application
A project Report
On
ONLINE MOBILE APPLICATION
Name of the Student
Name of the University
Name of the Author
A project Report
On
ONLINE MOBILE APPLICATION
Name of the Student
Name of the University
Name of the Author
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1Online shopping system
Table of Contents
Introduction:...............................................................................................................................3
Project Objectives:.....................................................................................................................3
Project Opportunity:...................................................................................................................4
Feasibility Study:.......................................................................................................................4
Operational Feasibility:..........................................................................................................5
Financial Feasibility:..............................................................................................................5
Technical Feasibility:.............................................................................................................6
Project Risk Management:.........................................................................................................7
Identification Project Threats...............................................................................................8
Threat Influence.....................................................................................................................8
Threat Management Technique..............................................................................................8
Work Break-Down Structure:..................................................................................................10
1. Implementation and Establishment of Project management.........................................10
2. Business Necessity........................................................................................................10
3. System Architecture......................................................................................................11
4. Technical Essentiality...................................................................................................11
5. Implementation of the System......................................................................................12
6. System Testing..............................................................................................................12
Table of Contents
Introduction:...............................................................................................................................3
Project Objectives:.....................................................................................................................3
Project Opportunity:...................................................................................................................4
Feasibility Study:.......................................................................................................................4
Operational Feasibility:..........................................................................................................5
Financial Feasibility:..............................................................................................................5
Technical Feasibility:.............................................................................................................6
Project Risk Management:.........................................................................................................7
Identification Project Threats...............................................................................................8
Threat Influence.....................................................................................................................8
Threat Management Technique..............................................................................................8
Work Break-Down Structure:..................................................................................................10
1. Implementation and Establishment of Project management.........................................10
2. Business Necessity........................................................................................................10
3. System Architecture......................................................................................................11
4. Technical Essentiality...................................................................................................11
5. Implementation of the System......................................................................................12
6. System Testing..............................................................................................................12

2Online shopping system
7. System Utilization Development..................................................................................12
8. Grounding.....................................................................................................................13
Project milestone statement:................................................................................................13
Influence of Work Breakdown Structure in the system:......................................................14
Accumulations of the Proposed System:..................................................................................15
Work breakdown structure with its Resource relation:........................................................16
Assumption of the Project Outcome:...................................................................................16
Conclusion:..............................................................................................................................17
Reference List..........................................................................................................................19
7. System Utilization Development..................................................................................12
8. Grounding.....................................................................................................................13
Project milestone statement:................................................................................................13
Influence of Work Breakdown Structure in the system:......................................................14
Accumulations of the Proposed System:..................................................................................15
Work breakdown structure with its Resource relation:........................................................16
Assumption of the Project Outcome:...................................................................................16
Conclusion:..............................................................................................................................17
Reference List..........................................................................................................................19

3Online shopping system
Introduction:
The purpose of this project is to implement an application on mobile platform which
will portray an application of Product Purchasing through internet. The central aim of the
approached application is to develop a specific Product purchasing System through internet
into Android Platform.
The approached application will offer several functionalities which includes the
method to access the desired products and buy them directly from the vendor via internet,
thus no negotiators interruption is needed. The approached application is an e-commerce
application. Proposed electronic commerce system is developed to facilitate the user with the
functionalities of product purchasing directly from the vendor through internet (Schafer et al.,
2017). It will provide a benefits of buying products via internet from anywhere any time to
the Android user. Therefore, the user facilitate with the advantage of purchasing goods from
their preferable vendors as well as will get a home delivery service (Einav et al., 2014).
Project Objectives:
This project is proposed in order to develop an Android based online application to
purchase goods online from the existing vendor. In order to implement this e-commerce
application, it needs a strong support from web service provider. Primary aim of this
approached system is to implement an efficient and a comprehensive web application. This
system will be developed on an Android platform along with the website view. It will also
provide the users a shopping facility from independent locations. This application is an
android based mobile application thus, it offers the customer the facility to buy product from
anytime anywhere.
Introduction:
The purpose of this project is to implement an application on mobile platform which
will portray an application of Product Purchasing through internet. The central aim of the
approached application is to develop a specific Product purchasing System through internet
into Android Platform.
The approached application will offer several functionalities which includes the
method to access the desired products and buy them directly from the vendor via internet,
thus no negotiators interruption is needed. The approached application is an e-commerce
application. Proposed electronic commerce system is developed to facilitate the user with the
functionalities of product purchasing directly from the vendor through internet (Schafer et al.,
2017). It will provide a benefits of buying products via internet from anywhere any time to
the Android user. Therefore, the user facilitate with the advantage of purchasing goods from
their preferable vendors as well as will get a home delivery service (Einav et al., 2014).
Project Objectives:
This project is proposed in order to develop an Android based online application to
purchase goods online from the existing vendor. In order to implement this e-commerce
application, it needs a strong support from web service provider. Primary aim of this
approached system is to implement an efficient and a comprehensive web application. This
system will be developed on an Android platform along with the website view. It will also
provide the users a shopping facility from independent locations. This application is an
android based mobile application thus, it offers the customer the facility to buy product from
anytime anywhere.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4Online shopping system
Project Opportunity:
The online purchasing application is entirely concerning with buying and saleing the
products as well as desired services through internet from customer preferable shop without
any physically movement. The approached online purchasing application will provide various
beneficial operations such as accessing of goods via internet, goods shopping, payment
through internet as well as a facility of home delivery. Accompanying these beneficial
operations, the shopping Cart also offers several beneficial functionalities like a user can pick
any preferable item and then drop it to the shopping cart and resume product accessing until
the final selection of user. The customer can also modify goods quantity from the shopping
cart any time before placing the order and user can remove the item too.
In this proposed online shopping application, the cash on delivery facility is not
present thus, the customer must familiar with the process of online payment.
Feasibility Study:
Based on the study of Cheng et al., (2015) the feasibility analysis is conduct to
determine the usefulness of the approached system. This approached system has accounted
three probable factors to determine feasibility of the approached system such as Operational
Feasibility, Financial Feasibility and Technical Feasibility.
Project Opportunity:
The online purchasing application is entirely concerning with buying and saleing the
products as well as desired services through internet from customer preferable shop without
any physically movement. The approached online purchasing application will provide various
beneficial operations such as accessing of goods via internet, goods shopping, payment
through internet as well as a facility of home delivery. Accompanying these beneficial
operations, the shopping Cart also offers several beneficial functionalities like a user can pick
any preferable item and then drop it to the shopping cart and resume product accessing until
the final selection of user. The customer can also modify goods quantity from the shopping
cart any time before placing the order and user can remove the item too.
In this proposed online shopping application, the cash on delivery facility is not
present thus, the customer must familiar with the process of online payment.
Feasibility Study:
Based on the study of Cheng et al., (2015) the feasibility analysis is conduct to
determine the usefulness of the approached system. This approached system has accounted
three probable factors to determine feasibility of the approached system such as Operational
Feasibility, Financial Feasibility and Technical Feasibility.

5Online shopping system
Operational Feasibility:
The inspection procedure is basically focused on how the proposed application is
meeting all the desired needs of the administrator as well as the customer. This approached
application will considered as the probable operational system if it able to addressed all its
necessities of admin after the installation of the application ( Rezzouk et al., 2015).
Following the study of Kebede et al., (2015) the study of Operational feasible inspection is
performed based on the following factors:
Proposed application will improve the comprehensive performance.
To address these aspects, the application will give enough value to the customer, and
will provide them various operational activities.
The proposed system will provide an enhanced market value to the vendor.
The proposed system will allow the user a worldwide accessing facility.
Following this study of operational feasibility factors of the approached application, it is
considered that the application has surely met all the mentioned factors. Hence, the system is
operationally feasible.
Financial Feasibility:
Mostly utilized process to analysing the usefulness of the approached application is
the Financial Feasibility inspection. When the profit of the system crosses overall cost of the
approached system, then only the application will proceed further for development process.
Operational Feasibility:
The inspection procedure is basically focused on how the proposed application is
meeting all the desired needs of the administrator as well as the customer. This approached
application will considered as the probable operational system if it able to addressed all its
necessities of admin after the installation of the application ( Rezzouk et al., 2015).
Following the study of Kebede et al., (2015) the study of Operational feasible inspection is
performed based on the following factors:
Proposed application will improve the comprehensive performance.
To address these aspects, the application will give enough value to the customer, and
will provide them various operational activities.
The proposed system will provide an enhanced market value to the vendor.
The proposed system will allow the user a worldwide accessing facility.
Following this study of operational feasibility factors of the approached application, it is
considered that the application has surely met all the mentioned factors. Hence, the system is
operationally feasible.
Financial Feasibility:
Mostly utilized process to analysing the usefulness of the approached application is
the Financial Feasibility inspection. When the profit of the system crosses overall cost of the
approached system, then only the application will proceed further for development process.

6Online shopping system
Based on the study of Gao et al., (2016) the economical feasibility inspection will be
performed on the basis of the mentioned factors below:
The application should consist inexpensive Hardware as well as Software
specifications.
The entire cost will be less expensive while representing it in global platforms.
It must be highly profitable while performing in the global platform.
Low cost maintenance of the developed system.
Following this study of financial feasibility factors of the approached application, it is
considered that the approached application has surely met all the mentioned factors. Hence,
the system is economically feasible.
In order to provide the system application more efficiency, the system should offers
various ways to contact the admin, and it should also enhance its web page structure. The
application must offer cash on delivery procedure for product buying.
Technical Feasibility:
This inspection is basically focused on the hardware as well as the software
equipment. Accompanying those specifications furthermore it involves few essential
technical influence that are the software reliability, access of the accurate product, data
security, future extension of the gadget and technical validity ( Lui et al., 2017).
Based on the study of Gao et al., (2016) the economical feasibility inspection will be
performed on the basis of the mentioned factors below:
The application should consist inexpensive Hardware as well as Software
specifications.
The entire cost will be less expensive while representing it in global platforms.
It must be highly profitable while performing in the global platform.
Low cost maintenance of the developed system.
Following this study of financial feasibility factors of the approached application, it is
considered that the approached application has surely met all the mentioned factors. Hence,
the system is economically feasible.
In order to provide the system application more efficiency, the system should offers
various ways to contact the admin, and it should also enhance its web page structure. The
application must offer cash on delivery procedure for product buying.
Technical Feasibility:
This inspection is basically focused on the hardware as well as the software
equipment. Accompanying those specifications furthermore it involves few essential
technical influence that are the software reliability, access of the accurate product, data
security, future extension of the gadget and technical validity ( Lui et al., 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7Online shopping system
Technical feasibility inspection will be accomplished based on these following factors:
Existence technology for the system installation.
Proposed application must be modified by the administrator. The admin should be
permitted to modify the system.
Hardware as well as the software specification of the approached system must be
liable with accurate privacy, back up and security.
Proposed application is enough efficient to store the information for further use.
Proposed application is enough efficient to dispense the customer a correct reply and
should permit the number of the customer regardless to access the system.
Followed by the analysis of the technical feasibility factors of the approached application,
it can be expressed that the approached application has addressed all the mentioned factors
perfectly. Therefore, the approached application is technically feasible.
Project Risk Management:
Although, there are various advantages of product purchasing via internet, it also
contains of several major threat factors. After, studying the threat aspects of the proposed
shopping system, it can be stated that these threats have significant influence on the
approached application. However, various threats are there in the proposed shopping system,
these threats can be handled if the administrator and the customer obey some risk
Technical feasibility inspection will be accomplished based on these following factors:
Existence technology for the system installation.
Proposed application must be modified by the administrator. The admin should be
permitted to modify the system.
Hardware as well as the software specification of the approached system must be
liable with accurate privacy, back up and security.
Proposed application is enough efficient to store the information for further use.
Proposed application is enough efficient to dispense the customer a correct reply and
should permit the number of the customer regardless to access the system.
Followed by the analysis of the technical feasibility factors of the approached application,
it can be expressed that the approached application has addressed all the mentioned factors
perfectly. Therefore, the approached application is technically feasible.
Project Risk Management:
Although, there are various advantages of product purchasing via internet, it also
contains of several major threat factors. After, studying the threat aspects of the proposed
shopping system, it can be stated that these threats have significant influence on the
approached application. However, various threats are there in the proposed shopping system,
these threats can be handled if the administrator and the customer obey some risk

8Online shopping system
management technique. The following table contains the entire detail about the proposed
system threat identification, its influence and management technique.
management technique. The following table contains the entire detail about the proposed
system threat identification, its influence and management technique.
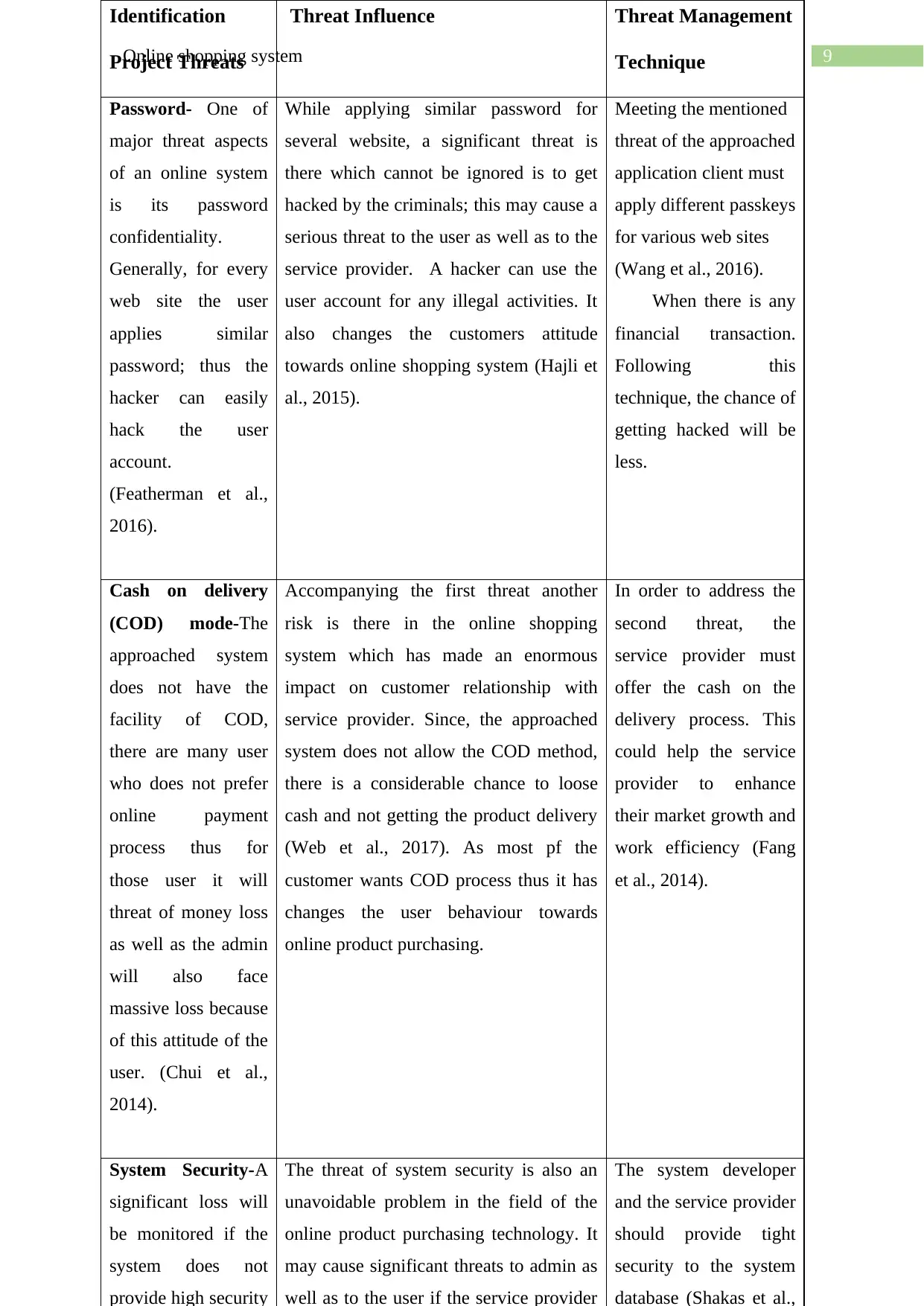
9Online shopping system
Identification
Project Threats
Threat Influence Threat Management
Technique
Password- One of
major threat aspects
of an online system
is its password
confidentiality.
Generally, for every
web site the user
applies similar
password; thus the
hacker can easily
hack the user
account.
(Featherman et al.,
2016).
While applying similar password for
several website, a significant threat is
there which cannot be ignored is to get
hacked by the criminals; this may cause a
serious threat to the user as well as to the
service provider. A hacker can use the
user account for any illegal activities. It
also changes the customers attitude
towards online shopping system (Hajli et
al., 2015).
Meeting the mentioned
threat of the approached
application client must
apply different passkeys
for various web sites
(Wang et al., 2016).
When there is any
financial transaction.
Following this
technique, the chance of
getting hacked will be
less.
Cash on delivery
(COD) mode-The
approached system
does not have the
facility of COD,
there are many user
who does not prefer
online payment
process thus for
those user it will
threat of money loss
as well as the admin
will also face
massive loss because
of this attitude of the
user. (Chui et al.,
2014).
Accompanying the first threat another
risk is there in the online shopping
system which has made an enormous
impact on customer relationship with
service provider. Since, the approached
system does not allow the COD method,
there is a considerable chance to loose
cash and not getting the product delivery
(Web et al., 2017). As most pf the
customer wants COD process thus it has
changes the user behaviour towards
online product purchasing.
In order to address the
second threat, the
service provider must
offer the cash on the
delivery process. This
could help the service
provider to enhance
their market growth and
work efficiency (Fang
et al., 2014).
System Security-A
significant loss will
be monitored if the
system does not
provide high security
The threat of system security is also an
unavoidable problem in the field of the
online product purchasing technology. It
may cause significant threats to admin as
well as to the user if the service provider
The system developer
and the service provider
should provide tight
security to the system
database (Shakas et al.,
Identification
Project Threats
Threat Influence Threat Management
Technique
Password- One of
major threat aspects
of an online system
is its password
confidentiality.
Generally, for every
web site the user
applies similar
password; thus the
hacker can easily
hack the user
account.
(Featherman et al.,
2016).
While applying similar password for
several website, a significant threat is
there which cannot be ignored is to get
hacked by the criminals; this may cause a
serious threat to the user as well as to the
service provider. A hacker can use the
user account for any illegal activities. It
also changes the customers attitude
towards online shopping system (Hajli et
al., 2015).
Meeting the mentioned
threat of the approached
application client must
apply different passkeys
for various web sites
(Wang et al., 2016).
When there is any
financial transaction.
Following this
technique, the chance of
getting hacked will be
less.
Cash on delivery
(COD) mode-The
approached system
does not have the
facility of COD,
there are many user
who does not prefer
online payment
process thus for
those user it will
threat of money loss
as well as the admin
will also face
massive loss because
of this attitude of the
user. (Chui et al.,
2014).
Accompanying the first threat another
risk is there in the online shopping
system which has made an enormous
impact on customer relationship with
service provider. Since, the approached
system does not allow the COD method,
there is a considerable chance to loose
cash and not getting the product delivery
(Web et al., 2017). As most pf the
customer wants COD process thus it has
changes the user behaviour towards
online product purchasing.
In order to address the
second threat, the
service provider must
offer the cash on the
delivery process. This
could help the service
provider to enhance
their market growth and
work efficiency (Fang
et al., 2014).
System Security-A
significant loss will
be monitored if the
system does not
provide high security
The threat of system security is also an
unavoidable problem in the field of the
online product purchasing technology. It
may cause significant threats to admin as
well as to the user if the service provider
The system developer
and the service provider
should provide tight
security to the system
database (Shakas et al.,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10Online shopping system
Work Break-Down Structure:
Work breakdown structure helps to give an outline of any system that defines all the pivotal
attributes and operations of that specific system.
1. Implementation and Establishment of Project management
1.1. Partnership Management Plan.
1.2. Service procurement and management Plan.
1.3. Project opportunity improvement.
1.4. Threat Management Strategy.
1.5. Superiority management Strategy.
1.6. Economics management.
1.7. Strategy of structuring the work flow.
1.8. File management Procedure.
2. Business Necessity
2.1. Investigation of existing application.
2.2. Investigation of existing systems documentation and human resources.
2.3. Contract Regulator.
2.4. Inspection management.
2.5. Reporting.
i. User end.
ii. User management.
Work Break-Down Structure:
Work breakdown structure helps to give an outline of any system that defines all the pivotal
attributes and operations of that specific system.
1. Implementation and Establishment of Project management
1.1. Partnership Management Plan.
1.2. Service procurement and management Plan.
1.3. Project opportunity improvement.
1.4. Threat Management Strategy.
1.5. Superiority management Strategy.
1.6. Economics management.
1.7. Strategy of structuring the work flow.
1.8. File management Procedure.
2. Business Necessity
2.1. Investigation of existing application.
2.2. Investigation of existing systems documentation and human resources.
2.3. Contract Regulator.
2.4. Inspection management.
2.5. Reporting.
i. User end.
ii. User management.

11Online shopping system
iii. Technical system management.
iv. Third party interruption.
2.6. Repercussion estimation of the application
i. Third party interruption.
ii. Estimation of provision data.
2.7. Definition of the proposed business strategy.
2.8. Work flow structure of the proposed system.
2.9. UI essentiality.
2.10. Technical Necessity.
2.11. Essential Documentation.
3. System Architecture
3.1. Description of system activities.
3.2. Progress Report.
3.3. N-tier logic.
3.4. Database Structure.
4. Technical Essentiality
4.1. Specification of selected platform.
4.2. Language Description.
4.3. User Signup procedure.
iii. Technical system management.
iv. Third party interruption.
2.6. Repercussion estimation of the application
i. Third party interruption.
ii. Estimation of provision data.
2.7. Definition of the proposed business strategy.
2.8. Work flow structure of the proposed system.
2.9. UI essentiality.
2.10. Technical Necessity.
2.11. Essential Documentation.
3. System Architecture
3.1. Description of system activities.
3.2. Progress Report.
3.3. N-tier logic.
3.4. Database Structure.
4. Technical Essentiality
4.1. Specification of selected platform.
4.2. Language Description.
4.3. User Signup procedure.

12Online shopping system
5. Implementation of the System
5.1. Document representation of Code.
5.1.1. Specification of beneficial operations.
5.2. Code control procedure.
5.3. Platform evaluation procedure.
5.4. UI. Implementation
5.5. Development of Code.
5.5.1. Code testing
5.5.2. Bug fixing.
6. System Testing
6.1. Testing the selected platform setting.
6.2. Testing strategies.
6.3. Each unit testing.
6.4. UAT.
6.5. Result reporting.
7. System Utilization Development
7.1. Documentation
7.1.1. Documentation of Data backup.
7.1.2. System administration documentation.
7.1.3. Documentation of user interface.
5. Implementation of the System
5.1. Document representation of Code.
5.1.1. Specification of beneficial operations.
5.2. Code control procedure.
5.3. Platform evaluation procedure.
5.4. UI. Implementation
5.5. Development of Code.
5.5.1. Code testing
5.5.2. Bug fixing.
6. System Testing
6.1. Testing the selected platform setting.
6.2. Testing strategies.
6.3. Each unit testing.
6.4. UAT.
6.5. Result reporting.
7. System Utilization Development
7.1. Documentation
7.1.1. Documentation of Data backup.
7.1.2. System administration documentation.
7.1.3. Documentation of user interface.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13Online shopping system
7.1.4. Documentation of the application.
8. Grounding
8.1. The grounding of user interface.
8.2. System administration grounding.
Project milestone statement:
The below table represents the achievement of the project and their time duration.
Progress Activities Expected Start Date
Structure of the system Development and
Application of the system management have
completed in time.
2nd of May, 2017
Completed professional Necessity in time. 15th of June, 2017
Completed the Structure of application
development in time.
20th July, 2017
Gathering the Technical equipment is
completed in time.
2nd August,2017
System Development process is completed in
time.
10th September, 2017
7.1.4. Documentation of the application.
8. Grounding
8.1. The grounding of user interface.
8.2. System administration grounding.
Project milestone statement:
The below table represents the achievement of the project and their time duration.
Progress Activities Expected Start Date
Structure of the system Development and
Application of the system management have
completed in time.
2nd of May, 2017
Completed professional Necessity in time. 15th of June, 2017
Completed the Structure of application
development in time.
20th July, 2017
Gathering the Technical equipment is
completed in time.
2nd August,2017
System Development process is completed in
time.
10th September, 2017

14Online shopping system
System Testing is finished in time. 1st October, 2017
System installation is completed. 2nd November, 2017
Grounding completed. 1st December, 2017
Influence of Work Breakdown Structure in the system:
Work breakdown structure allows the application manager to strategies their
operations to improve the system work regulation. While developing a system, initially it
helps to segregate the entire task into some sub-tasks with specific time and cost. It always
satisfies all the requirements of the stakeholder in order to implement the entire system (lock
et al., 2017). It offers the project organiser to structure their flow of work to develop the
system in an organised way. The system administrator must plan for the related work
structure, fix specific amount of money is provided to complete each divided part and
allocate the all the accountabilities among the labours (Pateli et al., 2014). There are various
justification of work breakdown structure in development of any system which are specified
below:
System Testing is finished in time. 1st October, 2017
System installation is completed. 2nd November, 2017
Grounding completed. 1st December, 2017
Influence of Work Breakdown Structure in the system:
Work breakdown structure allows the application manager to strategies their
operations to improve the system work regulation. While developing a system, initially it
helps to segregate the entire task into some sub-tasks with specific time and cost. It always
satisfies all the requirements of the stakeholder in order to implement the entire system (lock
et al., 2017). It offers the project organiser to structure their flow of work to develop the
system in an organised way. The system administrator must plan for the related work
structure, fix specific amount of money is provided to complete each divided part and
allocate the all the accountabilities among the labours (Pateli et al., 2014). There are various
justification of work breakdown structure in development of any system which are specified
below:
15Online shopping system
One of the major remarkable benefits of work breakdown structure is, it offers to simplify
complex jobs into some simple jobs. Which helps to enhance the working efficiency of the
system.
Utilising the conception of WBS, the system manager will allocate particular
amount of money for each divided task. It also offers to enhance the high cost
efficiency of the system.
It also offers to monitor each progress indvisually as the complete task is
segregated in several small sections.
Additional beneficial aspect of the WBS which helps to meet all the desired
outcome at the time of the system installation.
Accumulations of the Proposed System:
Several types of accumulations were utilized to develop the offered system, which is
specified in the below table:
Human Accumulation Software Equipment Hardware Equipment
User, Administrator, System
Manager, Developer,
Analyst, Sponsor, Testing
Android Oreo (8.0-8.1) and
updated version.
JSP, java script, CSS
HTML, Android, MySql.
16 GB of memory.
Dual-core 64-bit processor,
One of the major remarkable benefits of work breakdown structure is, it offers to simplify
complex jobs into some simple jobs. Which helps to enhance the working efficiency of the
system.
Utilising the conception of WBS, the system manager will allocate particular
amount of money for each divided task. It also offers to enhance the high cost
efficiency of the system.
It also offers to monitor each progress indvisually as the complete task is
segregated in several small sections.
Additional beneficial aspect of the WBS which helps to meet all the desired
outcome at the time of the system installation.
Accumulations of the Proposed System:
Several types of accumulations were utilized to develop the offered system, which is
specified in the below table:
Human Accumulation Software Equipment Hardware Equipment
User, Administrator, System
Manager, Developer,
Analyst, Sponsor, Testing
Android Oreo (8.0-8.1) and
updated version.
JSP, java script, CSS
HTML, Android, MySql.
16 GB of memory.
Dual-core 64-bit processor,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
16Online shopping system
Work breakdown structure with its Resource relation:
Resource Activities
Project manager
Analyst
Administrator
Developer
Testing Team
Training Team
Controls accomplishment of the proposed project.
Investigates the professional necessity.
establish the structure of the proposed system.
Accomplished the proposed system.
Investigates the usefulness and work reliability of this.
Provides training.
Assumption of the Project Outcome:
To implement the proposed android application, it is imagined that the application has
addressed all the required equipment. At the time of developing the proposed system the
accumulations were well utilised to embellish the approached application as well as the
assumed expenses was prolonged. The benefactresses were very supportive and pleasant. We
have finished this project in anticipated time duration, and the software and hardware
techniques worked well to complete the system implementation. Finally, the system outcome
has satisfied all the expectation of the developer.
Conclusion:
This can be accomplished that the project entitled Online Shopping System was
implemented efficiently. This system has been developed carefully. It’s a work efficient
Work breakdown structure with its Resource relation:
Resource Activities
Project manager
Analyst
Administrator
Developer
Testing Team
Training Team
Controls accomplishment of the proposed project.
Investigates the professional necessity.
establish the structure of the proposed system.
Accomplished the proposed system.
Investigates the usefulness and work reliability of this.
Provides training.
Assumption of the Project Outcome:
To implement the proposed android application, it is imagined that the application has
addressed all the required equipment. At the time of developing the proposed system the
accumulations were well utilised to embellish the approached application as well as the
assumed expenses was prolonged. The benefactresses were very supportive and pleasant. We
have finished this project in anticipated time duration, and the software and hardware
techniques worked well to complete the system implementation. Finally, the system outcome
has satisfied all the expectation of the developer.
Conclusion:
This can be accomplished that the project entitled Online Shopping System was
implemented efficiently. This system has been developed carefully. It’s a work efficient

17Online shopping system
system, as well as it is an error free and well time manageable system. The aim of this new
project was developed for android mobile platform for purchasing goods directly from the
vendors.
At the time of the implementation of this project, it has helped me to gain various
knowledge related to android application and practical knowledge in various fields like
DBMS, web site structuring and practical experience in the platform of android system
development. Whole system is highly secured, furthermore several feasible investigations has
done on this system. While developing this project it has provided me the practical grounding
of system testing. Afterwards, finishing the installation of this system, I have earned a brief
knowledge on the software implementation cycle.
Considering all the beneficial functionalities of the system it can be announced that it
has significant future scope, the application should adopt some new operations for the better
scope towards its professional growth.
system, as well as it is an error free and well time manageable system. The aim of this new
project was developed for android mobile platform for purchasing goods directly from the
vendors.
At the time of the implementation of this project, it has helped me to gain various
knowledge related to android application and practical knowledge in various fields like
DBMS, web site structuring and practical experience in the platform of android system
development. Whole system is highly secured, furthermore several feasible investigations has
done on this system. While developing this project it has provided me the practical grounding
of system testing. Afterwards, finishing the installation of this system, I have earned a brief
knowledge on the software implementation cycle.
Considering all the beneficial functionalities of the system it can be announced that it
has significant future scope, the application should adopt some new operations for the better
scope towards its professional growth.

18Online shopping system
Reference List
Cheng, X., Yang, L., & Shen, X. (2015). D2D for intelligent transportation systems: A
feasibility study. IEEE Transactions on Intelligent Transportation Systems, 16(4),
1784-1793.
Chiu, C. M., Wang, E. T., Fang, Y. H., & Huang, H. Y. (2014). Understanding customers'
repeat purchase intentions in B2C e‐commerce: the roles of practical value, hedonic
value and perceived risk. Information Systems Journal, 24(1), 85-114.
Einav, L., Levin, J., Popov, I., & Sundaresan, N. (2014). Growth, adoption, and use of mobile
E-commerce. American Economic Review, 104(5), 489-94.
Fang, Y., Qureshi, I., Sun, H., McCole, P., Ramsey, E., & Lim, K. H. (2014). Trust,
satisfaction, and online repurchase intention: The moderating role of perceived
effectiveness of e-commerce institutional mechanisms. Mis Quarterly, 38(2).
Featherman, M. S., & Hajli, N. (2016). Self-service technologies and e-services risks in social
commerce era. Journal of Business Ethics, 139(2), 251-269.
Gao, F., & Su, X. (2016). Omnichannel retail operations with buy-online-and-pick-up-in-
store. Management Science, 63(8), 2478-2492.
Glendon, A. I., & Clarke, S. (2015). Human safety and risk management: A psychological
perspective. Crc Press.
Hajli, N. (2015). Social commerce constructs and consumer's intention to buy. International
Journal of Information Management, 35(2), 183-191.
Hopkin, P. (2018). Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Reference List
Cheng, X., Yang, L., & Shen, X. (2015). D2D for intelligent transportation systems: A
feasibility study. IEEE Transactions on Intelligent Transportation Systems, 16(4),
1784-1793.
Chiu, C. M., Wang, E. T., Fang, Y. H., & Huang, H. Y. (2014). Understanding customers'
repeat purchase intentions in B2C e‐commerce: the roles of practical value, hedonic
value and perceived risk. Information Systems Journal, 24(1), 85-114.
Einav, L., Levin, J., Popov, I., & Sundaresan, N. (2014). Growth, adoption, and use of mobile
E-commerce. American Economic Review, 104(5), 489-94.
Fang, Y., Qureshi, I., Sun, H., McCole, P., Ramsey, E., & Lim, K. H. (2014). Trust,
satisfaction, and online repurchase intention: The moderating role of perceived
effectiveness of e-commerce institutional mechanisms. Mis Quarterly, 38(2).
Featherman, M. S., & Hajli, N. (2016). Self-service technologies and e-services risks in social
commerce era. Journal of Business Ethics, 139(2), 251-269.
Gao, F., & Su, X. (2016). Omnichannel retail operations with buy-online-and-pick-up-in-
store. Management Science, 63(8), 2478-2492.
Glendon, A. I., & Clarke, S. (2015). Human safety and risk management: A psychological
perspective. Crc Press.
Hajli, N. (2015). Social commerce constructs and consumer's intention to buy. International
Journal of Information Management, 35(2), 183-191.
Hopkin, P. (2018). Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19Online shopping system
Kebede, K. Y. (2015). Viability study of grid-connected solar PV system in
Ethiopia. Sustainable Energy Technologies and Assessments, 10, 63-70.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
Liu, Z., Xu, W., Zhai, X., Qian, C., & Chen, X. (2017). Feasibility and performance study of
the hybrid ground-source heat pump system for one office building in Chinese heating
dominated areas. Renewable energy, 101, 1131-1140.
Lock, D. (2017). The essentials of project management. Routledge.
O. Pappas, I., G. Pateli, A., N. Giannakos, M., & Chrissikopoulos, V. (2014). Moderating
effects of online shopping experience on customer satisfaction and repurchase
intentions. International Journal of Retail & Distribution Management, 42(3), 187-
204.
Pritchard, C. L., & PMP, P. R. (2014). Risk management: concepts and guidance. Auerbach
Publications.
Rezzouk, H., & Mellit, A. (2015). Feasibility study and sensitivity analysis of a stand-alone
photovoltaic–diesel–battery hybrid energy system in the north of Algeria. Renewable
and Sustainable Energy Reviews, 43, 1134-1150.
Sakas, D., Vlachos, D., & Nasiopoulos, D. (2014). Modelling strategic management for the
development of competitive advantage, based on technology. Journal of Systems and
Information Technology, 16(3), 187-209.
Schafer, J. B., Konstan, J., & Riedl, J. (2017 November). Recommender systems in e-
commerce. In Proceedings of the 1st ACM conference on Electronic commerce (pp.
158-166). ACM.
Kebede, K. Y. (2015). Viability study of grid-connected solar PV system in
Ethiopia. Sustainable Energy Technologies and Assessments, 10, 63-70.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
Liu, Z., Xu, W., Zhai, X., Qian, C., & Chen, X. (2017). Feasibility and performance study of
the hybrid ground-source heat pump system for one office building in Chinese heating
dominated areas. Renewable energy, 101, 1131-1140.
Lock, D. (2017). The essentials of project management. Routledge.
O. Pappas, I., G. Pateli, A., N. Giannakos, M., & Chrissikopoulos, V. (2014). Moderating
effects of online shopping experience on customer satisfaction and repurchase
intentions. International Journal of Retail & Distribution Management, 42(3), 187-
204.
Pritchard, C. L., & PMP, P. R. (2014). Risk management: concepts and guidance. Auerbach
Publications.
Rezzouk, H., & Mellit, A. (2015). Feasibility study and sensitivity analysis of a stand-alone
photovoltaic–diesel–battery hybrid energy system in the north of Algeria. Renewable
and Sustainable Energy Reviews, 43, 1134-1150.
Sakas, D., Vlachos, D., & Nasiopoulos, D. (2014). Modelling strategic management for the
development of competitive advantage, based on technology. Journal of Systems and
Information Technology, 16(3), 187-209.
Schafer, J. B., Konstan, J., & Riedl, J. (2017 November). Recommender systems in e-
commerce. In Proceedings of the 1st ACM conference on Electronic commerce (pp.
158-166). ACM.

20Online shopping system
Wang, Y., Min, Q., & Han, S. (2016). Understanding the effects of trust and risk on
individual behaviour toward social media platforms: A meta-analysis of the empirical
evidence. Computers in Human Behavior, 56, 34-44.
Webb, A. (2017). Using earned value: a project manager's guide. Routledge.
Wolke, T. (2017). Risk Management. Walter de Gruyter GmbH & Co KG.
Wang, Y., Min, Q., & Han, S. (2016). Understanding the effects of trust and risk on
individual behaviour toward social media platforms: A meta-analysis of the empirical
evidence. Computers in Human Behavior, 56, 34-44.
Webb, A. (2017). Using earned value: a project manager's guide. Routledge.
Wolke, T. (2017). Risk Management. Walter de Gruyter GmbH & Co KG.

21Online shopping system
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





