Risk Management Report: National Archives of Australia Website Project
VerifiedAdded on 2023/06/08
|16
|4270
|78
Report
AI Summary
This report presents a comprehensive risk management plan for the upgrade of the National Archives of Australia's Destination Australia website. The project involves transferring the website to a commonly available content management system to enhance functionality and user experience, including features for user-contributed data. The report details the internal and external risk contexts, including people, technology, resources, regulatory requirements, stakeholders, and financial aspects. It outlines the risk attitude, appetite, and tolerance levels. The report describes the approaches to identifying risks through brainstorming and interviews, culminating in a detailed risk register that includes risk descriptions, mitigation strategies, and rating. The report also includes risk action plans for security and budget/schedule overruns, detailing proposed actions, resource requirements, and monitoring procedures. Furthermore, it discusses activities to monitor and control project risks, including incident report analysis and regulatory environment analysis, and concludes with an assessment of risk management outcomes and areas for improvement.
qwertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasdfg
hjklzxcvbnmqwertyuiopasdfghjklzx
cvbnmqwertyuiopasdfghjklzxcvbn
mqwertyuiopasdfghjklzxcvbnmqwe
rtyuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnmq
wertyuiopasdfghjklzxcvbnmqwerty
uiopasdfghjklzxcvbnmqwertyuiopa
sdfghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjklzxc
vbnmrtyuiopasdfghjklzxcvbnmqwe
rtyuiopasdfghjklzxcvbnmqwertyui
ational Archives of AustraliaN
Managing roject RisksP
7/30/2018
yuiopasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasdfg
hjklzxcvbnmqwertyuiopasdfghjklzx
cvbnmqwertyuiopasdfghjklzxcvbn
mqwertyuiopasdfghjklzxcvbnmqwe
rtyuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnmq
wertyuiopasdfghjklzxcvbnmqwerty
uiopasdfghjklzxcvbnmqwertyuiopa
sdfghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjklzxc
vbnmrtyuiopasdfghjklzxcvbnmqwe
rtyuiopasdfghjklzxcvbnmqwertyui
ational Archives of AustraliaN
Managing roject RisksP
7/30/2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Managing roject RisksP
Table of Contents
Introduction...........................................................................................................................................2
Risk Context..........................................................................................................................................2
Internal Risk Context.........................................................................................................................2
External Risk Context........................................................................................................................2
Risk Attitude......................................................................................................................................3
Risk Appetite.....................................................................................................................................3
Risk Tolerance...................................................................................................................................3
Approach to Identifying Risks...............................................................................................................3
Risk Register.........................................................................................................................................4
Risk Action Plan 1.............................................................................................................................7
Risk Action Plan 2.............................................................................................................................8
Monitor & Control Project Risks.........................................................................................................10
Activities to Monitor Risk Environment..........................................................................................10
Outcome of the Review...................................................................................................................11
Areas of Improvement.................................................................................................................11
Points to be considered................................................................................................................11
Management of Changed Risk Responses.......................................................................................12
Assess Risk Management Outcomes...................................................................................................12
Project Performance in terms of Risk Management.........................................................................12
Risk Management Issues.................................................................................................................12
Case Study...........................................................................................................................................13
Risk Review Process.......................................................................................................................13
Change in Risks over the period of time..........................................................................................13
Activities to Update the Risk Register.............................................................................................14
References...........................................................................................................................................15
1
Table of Contents
Introduction...........................................................................................................................................2
Risk Context..........................................................................................................................................2
Internal Risk Context.........................................................................................................................2
External Risk Context........................................................................................................................2
Risk Attitude......................................................................................................................................3
Risk Appetite.....................................................................................................................................3
Risk Tolerance...................................................................................................................................3
Approach to Identifying Risks...............................................................................................................3
Risk Register.........................................................................................................................................4
Risk Action Plan 1.............................................................................................................................7
Risk Action Plan 2.............................................................................................................................8
Monitor & Control Project Risks.........................................................................................................10
Activities to Monitor Risk Environment..........................................................................................10
Outcome of the Review...................................................................................................................11
Areas of Improvement.................................................................................................................11
Points to be considered................................................................................................................11
Management of Changed Risk Responses.......................................................................................12
Assess Risk Management Outcomes...................................................................................................12
Project Performance in terms of Risk Management.........................................................................12
Risk Management Issues.................................................................................................................12
Case Study...........................................................................................................................................13
Risk Review Process.......................................................................................................................13
Change in Risks over the period of time..........................................................................................13
Activities to Update the Risk Register.............................................................................................14
References...........................................................................................................................................15
1

Managing roject RisksP
Introduction
Destination Australia is the website of National Archives of Australia. It is essential to
upgrade the website and bring it to a commonly available content management system. There
are numerous functionalities that need to be added and modified. The report is a risk
management report for the project that lists out the measures to identify, analyse, evaluate,
treat, monitor, and control the risks.
Risk Context
Internal Risk Context
People: There are people resources that will be assigned to the project and will have
the responsibility for different modules of the web site in the areas as development,
design, testing, deployment, and maintenance. The conflicts and disputes among the
resources may bring in project risks. Also, there may be communication issues among
the management resources, technical resources, and operational resources.
Technology: There will be technical tools and platforms that will be used in the
project. Some of these will include Content Management System (CMS),
development tools, testing tools, communication tools, project management tools, etc.
These may bring in technical risks of faults and failures for the project1.
Resources: The resources involved in the project will include people resources,
hardware, technological tools, and facilities. The availability of the resources and their
performance may lead to the presence or absence of project risks.
Accessibility: There will be access to the database and project environments that will
be necessary for the resources to meet the project goals. This may bring in a set of
issues.
1 oao alter Saunders acheco do Vale and Marly Monteiro de Carvalho "Risk And ncertainty n rojectsJ W P , U I P
Management iterature Review And Conceptual ramework": L F , evista Gest o a Produ o pera es ER ã D çã O çõ
istemasS no doi gepros v i12, . 2 (2017): 93-120, :10.15675/ . 12 2.1637.
2
Introduction
Destination Australia is the website of National Archives of Australia. It is essential to
upgrade the website and bring it to a commonly available content management system. There
are numerous functionalities that need to be added and modified. The report is a risk
management report for the project that lists out the measures to identify, analyse, evaluate,
treat, monitor, and control the risks.
Risk Context
Internal Risk Context
People: There are people resources that will be assigned to the project and will have
the responsibility for different modules of the web site in the areas as development,
design, testing, deployment, and maintenance. The conflicts and disputes among the
resources may bring in project risks. Also, there may be communication issues among
the management resources, technical resources, and operational resources.
Technology: There will be technical tools and platforms that will be used in the
project. Some of these will include Content Management System (CMS),
development tools, testing tools, communication tools, project management tools, etc.
These may bring in technical risks of faults and failures for the project1.
Resources: The resources involved in the project will include people resources,
hardware, technological tools, and facilities. The availability of the resources and their
performance may lead to the presence or absence of project risks.
Accessibility: There will be access to the database and project environments that will
be necessary for the resources to meet the project goals. This may bring in a set of
issues.
1 oao alter Saunders acheco do Vale and Marly Monteiro de Carvalho "Risk And ncertainty n rojectsJ W P , U I P
Management iterature Review And Conceptual ramework": L F , evista Gest o a Produ o pera es ER ã D çã O çõ
istemasS no doi gepros v i12, . 2 (2017): 93-120, :10.15675/ . 12 2.1637.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Managing roject RisksP
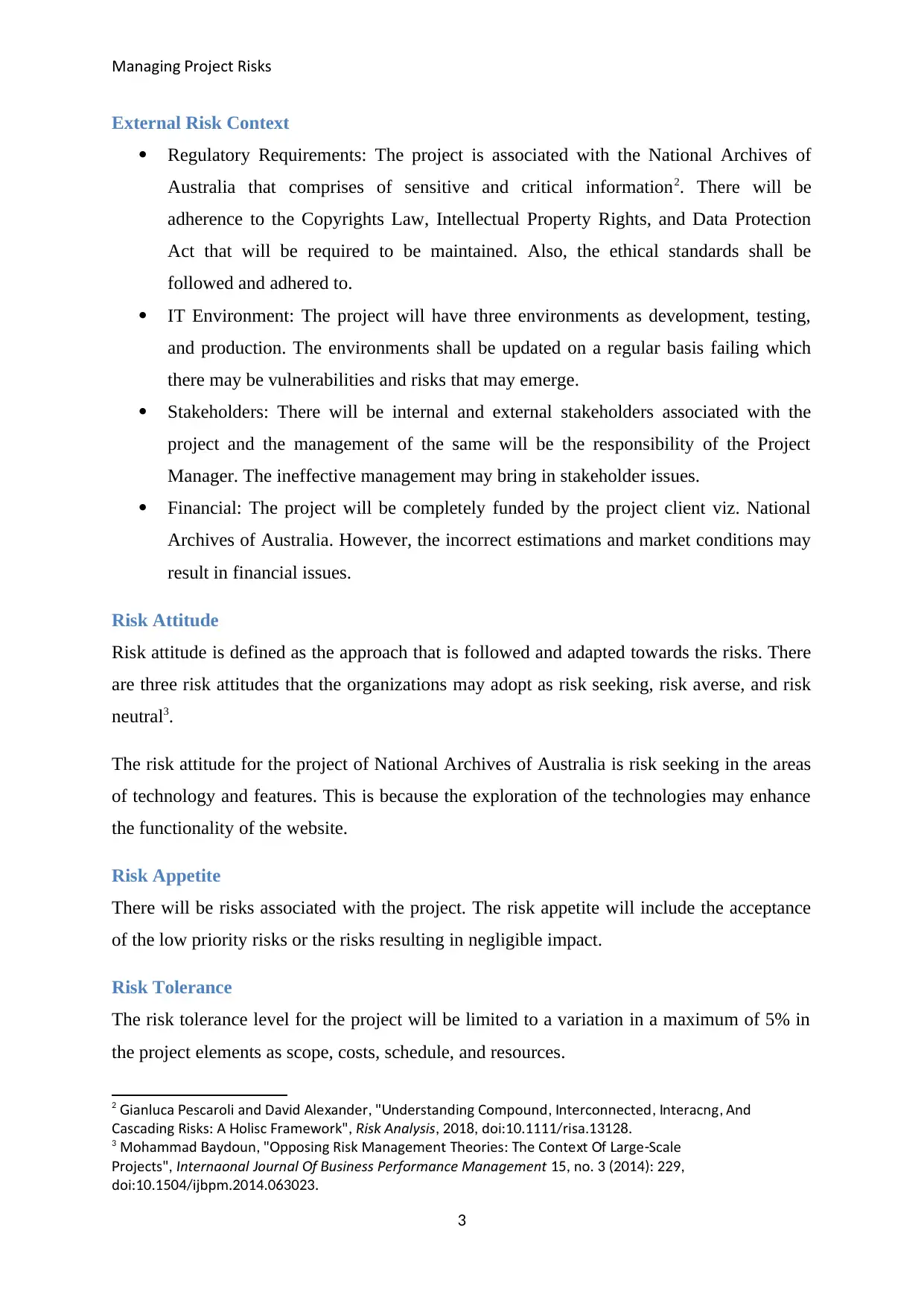
External Risk Context
Regulatory Requirements: The project is associated with the National Archives of
Australia that comprises of sensitive and critical information2. There will be
adherence to the Copyrights Law, Intellectual Property Rights, and Data Protection
Act that will be required to be maintained. Also, the ethical standards shall be
followed and adhered to.
IT Environment: The project will have three environments as development, testing,
and production. The environments shall be updated on a regular basis failing which
there may be vulnerabilities and risks that may emerge.
Stakeholders: There will be internal and external stakeholders associated with the
project and the management of the same will be the responsibility of the Project
Manager. The ineffective management may bring in stakeholder issues.
Financial: The project will be completely funded by the project client viz. National
Archives of Australia. However, the incorrect estimations and market conditions may
result in financial issues.
Risk Attitude
Risk attitude is defined as the approach that is followed and adapted towards the risks. There
are three risk attitudes that the organizations may adopt as risk seeking, risk averse, and risk
neutral3.
The risk attitude for the project of National Archives of Australia is risk seeking in the areas
of technology and features. This is because the exploration of the technologies may enhance
the functionality of the website.
Risk Appetite
There will be risks associated with the project. The risk appetite will include the acceptance
of the low priority risks or the risks resulting in negligible impact.
Risk Tolerance
The risk tolerance level for the project will be limited to a variation in a maximum of 5% in
the project elements as scope, costs, schedule, and resources.
2 ianluca escaroli and David Ale ander " nderstanding Compound nterconnected nteracting AndG P x , U , I , I ,
Cascading Risks A olistic ramework": H F , is nalysisR k A doi risa, 2018, :10.1111/ .13128.
3 Mohammad aydoun " pposing Risk Management heories he Conte t f arge ScaleB , O T : T x O L -
rojects"P , nternational ournal f usiness Performance ManagementI J O B no15, . 3 (2014): 229,
doi ijbpm:10.1504/ .2014.063023.
3
External Risk Context
Regulatory Requirements: The project is associated with the National Archives of
Australia that comprises of sensitive and critical information2. There will be
adherence to the Copyrights Law, Intellectual Property Rights, and Data Protection
Act that will be required to be maintained. Also, the ethical standards shall be
followed and adhered to.
IT Environment: The project will have three environments as development, testing,
and production. The environments shall be updated on a regular basis failing which
there may be vulnerabilities and risks that may emerge.
Stakeholders: There will be internal and external stakeholders associated with the
project and the management of the same will be the responsibility of the Project
Manager. The ineffective management may bring in stakeholder issues.
Financial: The project will be completely funded by the project client viz. National
Archives of Australia. However, the incorrect estimations and market conditions may
result in financial issues.
Risk Attitude
Risk attitude is defined as the approach that is followed and adapted towards the risks. There
are three risk attitudes that the organizations may adopt as risk seeking, risk averse, and risk
neutral3.
The risk attitude for the project of National Archives of Australia is risk seeking in the areas
of technology and features. This is because the exploration of the technologies may enhance
the functionality of the website.
Risk Appetite
There will be risks associated with the project. The risk appetite will include the acceptance
of the low priority risks or the risks resulting in negligible impact.
Risk Tolerance
The risk tolerance level for the project will be limited to a variation in a maximum of 5% in
the project elements as scope, costs, schedule, and resources.
2 ianluca escaroli and David Ale ander " nderstanding Compound nterconnected nteracting AndG P x , U , I , I ,
Cascading Risks A olistic ramework": H F , is nalysisR k A doi risa, 2018, :10.1111/ .13128.
3 Mohammad aydoun " pposing Risk Management heories he Conte t f arge ScaleB , O T : T x O L -
rojects"P , nternational ournal f usiness Performance ManagementI J O B no15, . 3 (2014): 229,
doi ijbpm:10.1504/ .2014.063023.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Managing roject RisksP
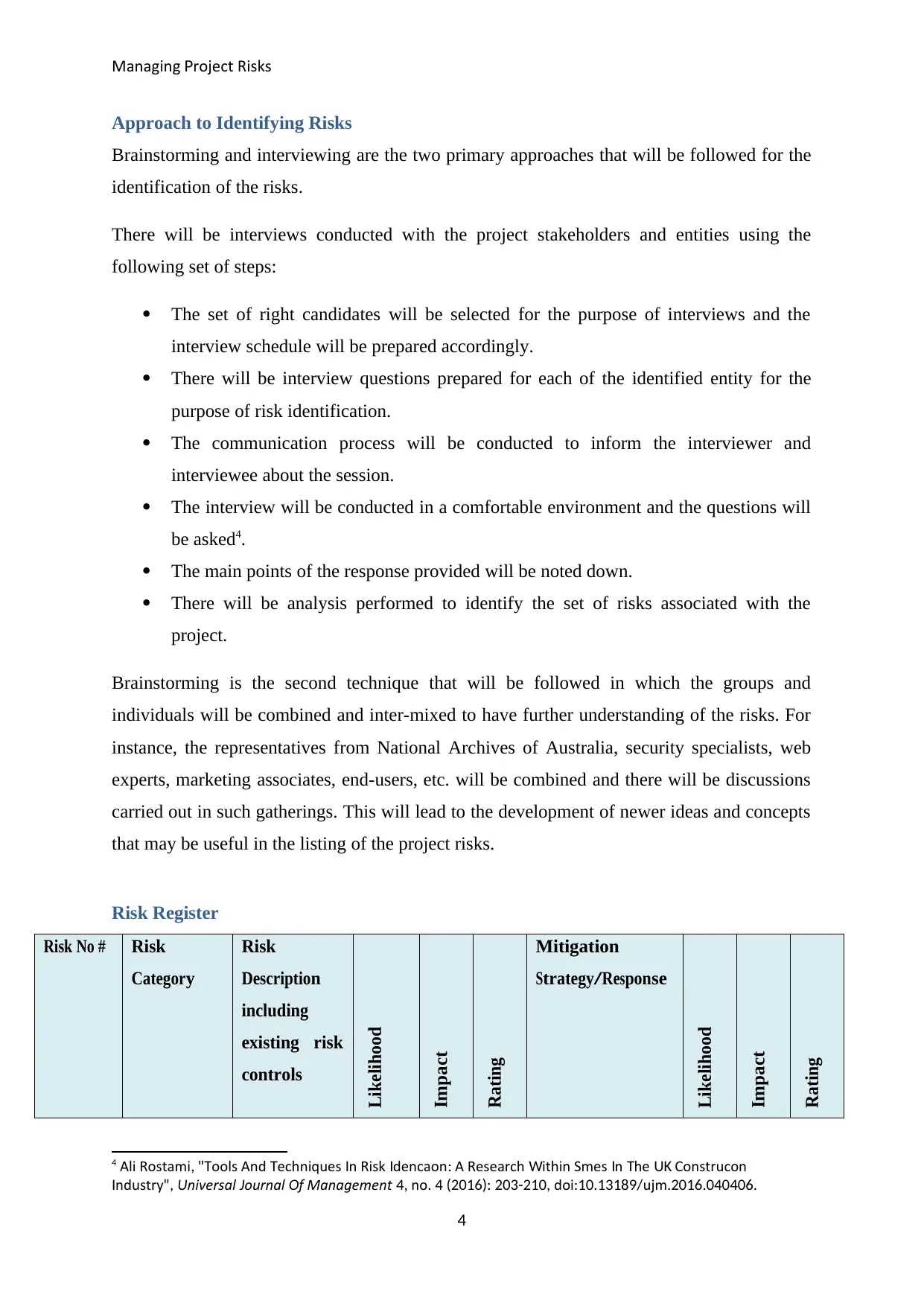
Approach to Identifying Risks
Brainstorming and interviewing are the two primary approaches that will be followed for the
identification of the risks.
There will be interviews conducted with the project stakeholders and entities using the
following set of steps:
The set of right candidates will be selected for the purpose of interviews and the
interview schedule will be prepared accordingly.
There will be interview questions prepared for each of the identified entity for the
purpose of risk identification.
The communication process will be conducted to inform the interviewer and
interviewee about the session.
The interview will be conducted in a comfortable environment and the questions will
be asked4.
The main points of the response provided will be noted down.
There will be analysis performed to identify the set of risks associated with the
project.
Brainstorming is the second technique that will be followed in which the groups and
individuals will be combined and inter-mixed to have further understanding of the risks. For
instance, the representatives from National Archives of Australia, security specialists, web
experts, marketing associates, end-users, etc. will be combined and there will be discussions
carried out in such gatherings. This will lead to the development of newer ideas and concepts
that may be useful in the listing of the project risks.
Risk Register
Risk No # Risk
Categor y
Risk
Descriptio n
including
existing risk
controls
Likelihood
Impact
Rating
Mitigation
Stra tegy/Response
Likelihood
Impact
Rating
4 Ali Rostami " ools And echniques n Risk dentification A Research ithin Smes n he Construction, T T I I : W I T UK
ndustry"I , niversal ournal f ManagementU J O no doi ujm4, . 4 (2016): 203-210, :10.13189/ .2016.040406.
4
Approach to Identifying Risks
Brainstorming and interviewing are the two primary approaches that will be followed for the
identification of the risks.
There will be interviews conducted with the project stakeholders and entities using the
following set of steps:
The set of right candidates will be selected for the purpose of interviews and the
interview schedule will be prepared accordingly.
There will be interview questions prepared for each of the identified entity for the
purpose of risk identification.
The communication process will be conducted to inform the interviewer and
interviewee about the session.
The interview will be conducted in a comfortable environment and the questions will
be asked4.
The main points of the response provided will be noted down.
There will be analysis performed to identify the set of risks associated with the
project.
Brainstorming is the second technique that will be followed in which the groups and
individuals will be combined and inter-mixed to have further understanding of the risks. For
instance, the representatives from National Archives of Australia, security specialists, web
experts, marketing associates, end-users, etc. will be combined and there will be discussions
carried out in such gatherings. This will lead to the development of newer ideas and concepts
that may be useful in the listing of the project risks.
Risk Register
Risk No # Risk
Categor y
Risk
Descriptio n
including
existing risk
controls
Likelihood
Impact
Rating
Mitigation
Stra tegy/Response
Likelihood
Impact
Rating
4 Ali Rostami " ools And echniques n Risk dentification A Research ithin Smes n he Construction, T T I I : W I T UK
ndustry"I , niversal ournal f ManagementU J O no doi ujm4, . 4 (2016): 203-210, :10.13189/ .2016.040406.
4
Managing roject RisksP
Initial Residual
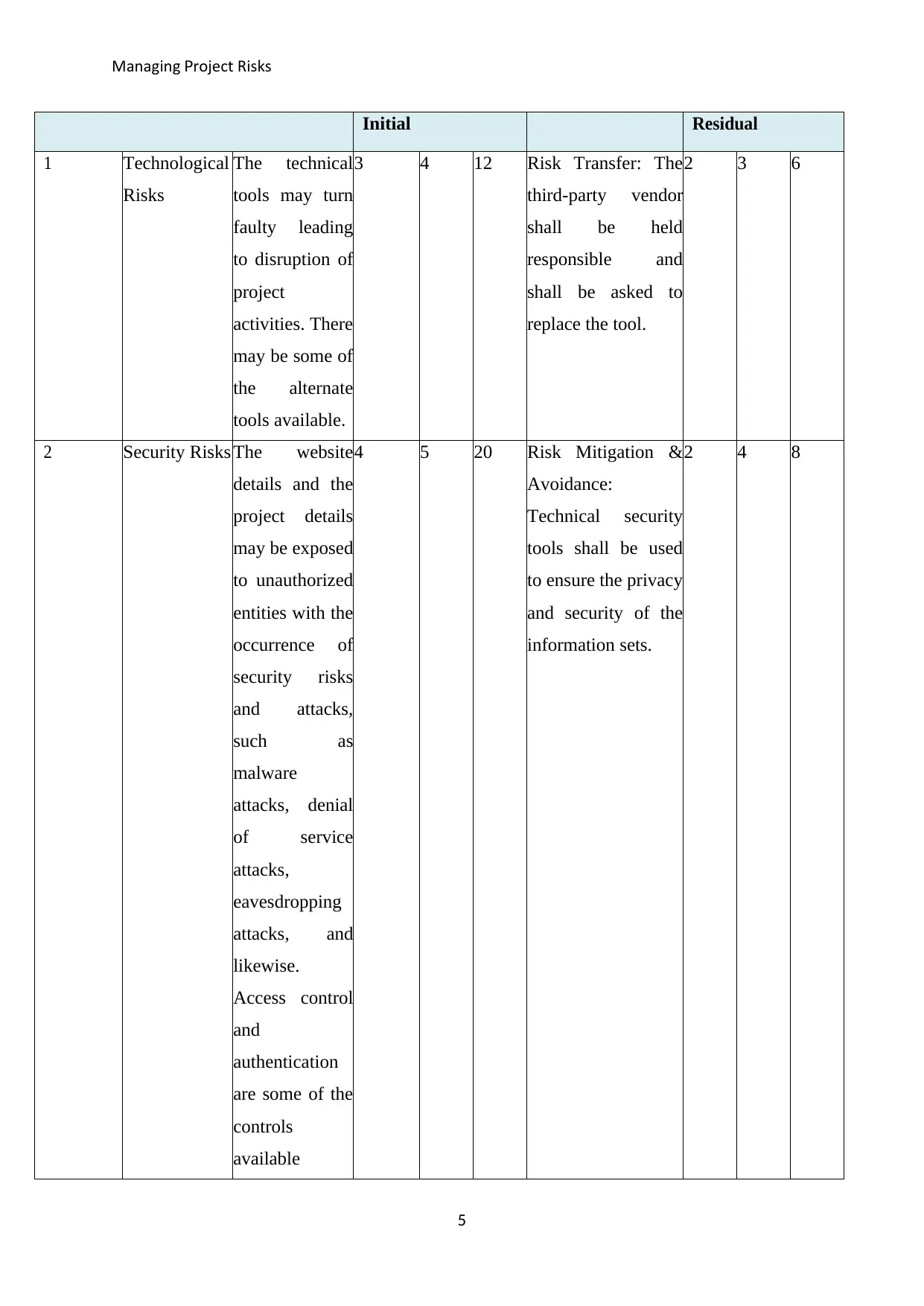
1 Technological
Risks
The technical
tools may turn
faulty leading
to disruption of
project
activities. There
may be some of
the alternate
tools available.
3 4 12 Risk Transfer: The
third-party vendor
shall be held
responsible and
shall be asked to
replace the tool.
2 3 6
2 Security Risks The website
details and the
project details
may be exposed
to unauthorized
entities with the
occurrence of
security risks
and attacks,
such as
malware
attacks, denial
of service
attacks,
eavesdropping
attacks, and
likewise.
Access control
and
authentication
are some of the
controls
available
4 5 20 Risk Mitigation &
Avoidance:
Technical security
tools shall be used
to ensure the privacy
and security of the
information sets.
2 4 8
5
Initial Residual
1 Technological
Risks
The technical
tools may turn
faulty leading
to disruption of
project
activities. There
may be some of
the alternate
tools available.
3 4 12 Risk Transfer: The
third-party vendor
shall be held
responsible and
shall be asked to
replace the tool.
2 3 6
2 Security Risks The website
details and the
project details
may be exposed
to unauthorized
entities with the
occurrence of
security risks
and attacks,
such as
malware
attacks, denial
of service
attacks,
eavesdropping
attacks, and
likewise.
Access control
and
authentication
are some of the
controls
available
4 5 20 Risk Mitigation &
Avoidance:
Technical security
tools shall be used
to ensure the privacy
and security of the
information sets.
2 4 8
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Managing roject RisksP
3 Schedule/
Budget
Overrun
The estimated
budget or
schedule may
not be correct
which may lead
to significant
delays and
overrun of the
costs. There
may be reviews
carried out by
the
management to
handle the
issue.
3 5 15 Risk Avoidance &
Mitigation: There
must be reviews
carried out by the
management to
make sure that the
situation of overrun
does not come up.
1 4 4
4 Market Risks It is a positive
risk as the
market
scenarios may
determine the
cost of tools
which may
come down as
per the
conditions.
2 4 8 Risk Acceptance:
The market analysis
shall be regularly
conducted and the
purchase shall be
made at the time of
lowest costs.
1 3 3
5 Resource
Risks
It is a positive
risk as the
resources may
showcase
unexpected
productivity
and efficiency
levels.
1 4 4 Risk Acceptance:
The remaining
schedule and budget
shall be utilized to
improve the project
quality.
1 3 3
6 Quality Risks The quality of1 5 5 Risk Avoidance:1 5 5
6
3 Schedule/
Budget
Overrun
The estimated
budget or
schedule may
not be correct
which may lead
to significant
delays and
overrun of the
costs. There
may be reviews
carried out by
the
management to
handle the
issue.
3 5 15 Risk Avoidance &
Mitigation: There
must be reviews
carried out by the
management to
make sure that the
situation of overrun
does not come up.
1 4 4
4 Market Risks It is a positive
risk as the
market
scenarios may
determine the
cost of tools
which may
come down as
per the
conditions.
2 4 8 Risk Acceptance:
The market analysis
shall be regularly
conducted and the
purchase shall be
made at the time of
lowest costs.
1 3 3
5 Resource
Risks
It is a positive
risk as the
resources may
showcase
unexpected
productivity
and efficiency
levels.
1 4 4 Risk Acceptance:
The remaining
schedule and budget
shall be utilized to
improve the project
quality.
1 3 3
6 Quality Risks The quality of1 5 5 Risk Avoidance:1 5 5
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Managing roject RisksP
the project may
be negatively
impacted due to
the operational
errors or
increased
rework. Quality
assessments
may be carried
out for the
same.
There must be
quality reviews and
assessment
processes that must
be conducted to
maintain the quality
of the project
outcomes.
7 Legal Risks The occurrence
of security
attacks may
result in legal
obligations and
punishments.
2 5 10 Risk Avoidance:
There must be legal
reviews that shall be
conducted to ensure
that the risk does not
take place.
1 5 5
Risk Action Plan 1
Risk Action Plan #1
Item No: 2 Risk Description:
The website details and the project details may be exposed to
unauthorized entities with the occurrence of security risks and attacks,
such as malware attacks, denial of service attacks, eavesdropping
attacks, and likewise. Access control and authentication are some of the
controls available.
Risk Rating : 20 Category: Security Risks Risk Treatment:
Mitigation & Avoidance
Action Plan:
Proposed Actions:
7
the project may
be negatively
impacted due to
the operational
errors or
increased
rework. Quality
assessments
may be carried
out for the
same.
There must be
quality reviews and
assessment
processes that must
be conducted to
maintain the quality
of the project
outcomes.
7 Legal Risks The occurrence
of security
attacks may
result in legal
obligations and
punishments.
2 5 10 Risk Avoidance:
There must be legal
reviews that shall be
conducted to ensure
that the risk does not
take place.
1 5 5
Risk Action Plan 1
Risk Action Plan #1
Item No: 2 Risk Description:
The website details and the project details may be exposed to
unauthorized entities with the occurrence of security risks and attacks,
such as malware attacks, denial of service attacks, eavesdropping
attacks, and likewise. Access control and authentication are some of the
controls available.
Risk Rating : 20 Category: Security Risks Risk Treatment:
Mitigation & Avoidance
Action Plan:
Proposed Actions:
7
Managing roject RisksP
Technical security tools shall be used to ensure the privacy and security of the information
sets.
Resource Requirements:
Security Analyst, Security Expert
Responsibilities:
To procure the security tools necessary for the website and the project and integrate it with
the other technical components.
Scope Impact:
The scope of the project will not be altered as the security testing is already a part of the
project.
Time Impact:
A timeframe of 21 days will be needed to implement the risk response.
Cost Impact:
The cost of the tools will go up as a one-time cost that will include cost of anti-malware
tools, anti-denial tools, intrusion detection tools, encryption tools, and network monitoring
tools.
Reporting & Monitoring Required:
There will be weekly risk status report that shall be shared and the management must
conduct reviews to monitor the progress.
Prepared by:
Project
Manager
Date:
30th July 2018
Reviewed by:
Project Director
Date: 30th July 2018
Risk Action Plan 2
Risk Action Plan #2
Item No: 3 Risk Description:
8
Technical security tools shall be used to ensure the privacy and security of the information
sets.
Resource Requirements:
Security Analyst, Security Expert
Responsibilities:
To procure the security tools necessary for the website and the project and integrate it with
the other technical components.
Scope Impact:
The scope of the project will not be altered as the security testing is already a part of the
project.
Time Impact:
A timeframe of 21 days will be needed to implement the risk response.
Cost Impact:
The cost of the tools will go up as a one-time cost that will include cost of anti-malware
tools, anti-denial tools, intrusion detection tools, encryption tools, and network monitoring
tools.
Reporting & Monitoring Required:
There will be weekly risk status report that shall be shared and the management must
conduct reviews to monitor the progress.
Prepared by:
Project
Manager
Date:
30th July 2018
Reviewed by:
Project Director
Date: 30th July 2018
Risk Action Plan 2
Risk Action Plan #2
Item No: 3 Risk Description:
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Managing roject RisksP
The estimated budget or schedule may not be correct which may lead to
significant delays and overrun of the costs. There may be reviews
carried out by the management to handle the issue
Risk Rating : 15 Category: Schedule/Budget
Overrun
Risk Treatment:
Avoidance & Mitigation
Action Plan:
Proposed Actions:
There must be reviews carried out by the management to make sure that the situation of
overrun does not come up.
Resource Requirements:
Project Manager, Finance Officer
Responsibilities:
The Project Manager and Finance Office will be responsible to review the project timeline
and conduct cost benefit analysis.
Scope Impact:
The scope of the project will not be altered as the reviews and monitoring activities are
already a part of the project.
Time Impact:
A timeframe of 30 days will be needed to implement the risk response.
Cost Impact:
There may be rescheduling of the activities and redesign of the budget that may occur
having an impact on the cost of development and deployment tasks.
Reporting & Monitoring Required:
9
The estimated budget or schedule may not be correct which may lead to
significant delays and overrun of the costs. There may be reviews
carried out by the management to handle the issue
Risk Rating : 15 Category: Schedule/Budget
Overrun
Risk Treatment:
Avoidance & Mitigation
Action Plan:
Proposed Actions:
There must be reviews carried out by the management to make sure that the situation of
overrun does not come up.
Resource Requirements:
Project Manager, Finance Officer
Responsibilities:
The Project Manager and Finance Office will be responsible to review the project timeline
and conduct cost benefit analysis.
Scope Impact:
The scope of the project will not be altered as the reviews and monitoring activities are
already a part of the project.
Time Impact:
A timeframe of 30 days will be needed to implement the risk response.
Cost Impact:
There may be rescheduling of the activities and redesign of the budget that may occur
having an impact on the cost of development and deployment tasks.
Reporting & Monitoring Required:
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Managing roject RisksP
There will be weekly risk status report that shall be shared and the management must
conduct reviews to monitor the progress.
Prepared by:
Project
Manager
Date:
30th July 2018
Reviewed by:
Project Director
Date: 30th July 2018
Monitor & Control Project Risks
Activities to Monitor Risk Environment
Analysis of Incident Report & Security Events: There will be incidents that will be
reported and logs of the same will be maintained. For instance, the network activity
logs will be maintained and saved in the system. The incidents that are reported and
are in resolved/unresolved state shall be reviewed at a weekly interval to understand
the improvements that shall be made to make the project environments safer and
secure. There may be attempts made by the malicious entities to give shape to the
security issues5. Such events shall be handled using the log analysis tools and
intrusion detection systems. The list of deviations shall be prepared and the
corresponding actions shall be taken.
Regulatory Environment Analysis: There are several regulations and standards that
the project is required to adhere to. There must be an analysis of the regulatory
environment that shall be conducted on a weekly basis to understand the level of
adherence and the loopholes.
Interview Sessions: The project resources, resources in the IT control areas, and
project stakeholders shall be communicated regularly and there shall be interviews
conducted with these entities to understand the risk status, risk probability levels, and
the further steps of actions that may be taken6. There may be newer risks that may
come up that shall be discussed in these sessions.
Status Tracking & Analysis: It would be essential for the resources responsible for
handling the risks and all the other resources in the project team to submit the status
reports to the Project Manager. These will include the risk status reports and project
5 oana ei oto et al " roject Risk Management Methodology A Case Study f An lectric nergyJ P x ., P : O E E
rganization"O , Procedia echnologyT doi j protcy16 (2014): 1096-1105, :10.1016/ . .2014.10.124.
6 Mahmoud hraiwesh " roject Monitoring And Control Measures n CMM "K , P I I , nternational ournal f ComputerI J O
cience nd nformation echnologyS A I T no doi ijcsit5, . 5 (2013): 39-56, :10.5121/ .2013.5503.
10
There will be weekly risk status report that shall be shared and the management must
conduct reviews to monitor the progress.
Prepared by:
Project
Manager
Date:
30th July 2018
Reviewed by:
Project Director
Date: 30th July 2018
Monitor & Control Project Risks
Activities to Monitor Risk Environment
Analysis of Incident Report & Security Events: There will be incidents that will be
reported and logs of the same will be maintained. For instance, the network activity
logs will be maintained and saved in the system. The incidents that are reported and
are in resolved/unresolved state shall be reviewed at a weekly interval to understand
the improvements that shall be made to make the project environments safer and
secure. There may be attempts made by the malicious entities to give shape to the
security issues5. Such events shall be handled using the log analysis tools and
intrusion detection systems. The list of deviations shall be prepared and the
corresponding actions shall be taken.
Regulatory Environment Analysis: There are several regulations and standards that
the project is required to adhere to. There must be an analysis of the regulatory
environment that shall be conducted on a weekly basis to understand the level of
adherence and the loopholes.
Interview Sessions: The project resources, resources in the IT control areas, and
project stakeholders shall be communicated regularly and there shall be interviews
conducted with these entities to understand the risk status, risk probability levels, and
the further steps of actions that may be taken6. There may be newer risks that may
come up that shall be discussed in these sessions.
Status Tracking & Analysis: It would be essential for the resources responsible for
handling the risks and all the other resources in the project team to submit the status
reports to the Project Manager. These will include the risk status reports and project
5 oana ei oto et al " roject Risk Management Methodology A Case Study f An lectric nergyJ P x ., P : O E E
rganization"O , Procedia echnologyT doi j protcy16 (2014): 1096-1105, :10.1016/ . .2014.10.124.
6 Mahmoud hraiwesh " roject Monitoring And Control Measures n CMM "K , P I I , nternational ournal f ComputerI J O
cience nd nformation echnologyS A I T no doi ijcsit5, . 5 (2013): 39-56, :10.5121/ .2013.5503.
10

Managing roject RisksP
status reports. These reports shall be analysed to understand the gaps and areas of
improvements.
Audit & Reviews: The management and leadership shall carry out project reviews and
security audits to ensure that the project environment is always kept safe and the
newer set of risks and prevented and avoided7.
Evaluation Meetings: The Project Manager must conduct a weekly meeting with the
project client, external stakeholders, and the internal project team to evaluate the
project status, risk status, risk environment, and project environment to come up with
the changes that shall be made. The strengths and weaknesses along with the
opportunities will be identified through such meetings and discussions.
Outcome of the Review
Areas of Improvement
Network Security: There shall be network scanners installed to keep a track of the
network activity at all times.
Change Management Plan: There are updates that need to be made in the format of
the change request that is currently followed.
Access Control Mechanisms: There shall be role-based access control implemented
for the web site for the user roles.
Technical Reviews: An external auditor shall carry out the technical and security
review twice a month.
Points to be considered
Team Meetings: The frequency of team meetings shall be changed from weekly to
twice a week so that the issues may be resolved quickly.
Conflict Management: Conflict management report shall be prepared and shared with
the project client by the Project Manager.
Management of Changed Risk Responses
The outcomes that are listed above provided certain areas that may be improved. An action
and change management plan has been prepared for the management of the risk responses
that have been upgraded.
7 ean C edard et al "Risk Monitoring And Control n Audit irms A Research Synthesis"J . B ., I F : , GAUDITIN : A
ournal f Practice heoryJ O & T no doi aud27, . 1 (2008): 187-218, :10.2308/ .2008.27.1.187.
11
status reports. These reports shall be analysed to understand the gaps and areas of
improvements.
Audit & Reviews: The management and leadership shall carry out project reviews and
security audits to ensure that the project environment is always kept safe and the
newer set of risks and prevented and avoided7.
Evaluation Meetings: The Project Manager must conduct a weekly meeting with the
project client, external stakeholders, and the internal project team to evaluate the
project status, risk status, risk environment, and project environment to come up with
the changes that shall be made. The strengths and weaknesses along with the
opportunities will be identified through such meetings and discussions.
Outcome of the Review
Areas of Improvement
Network Security: There shall be network scanners installed to keep a track of the
network activity at all times.
Change Management Plan: There are updates that need to be made in the format of
the change request that is currently followed.
Access Control Mechanisms: There shall be role-based access control implemented
for the web site for the user roles.
Technical Reviews: An external auditor shall carry out the technical and security
review twice a month.
Points to be considered
Team Meetings: The frequency of team meetings shall be changed from weekly to
twice a week so that the issues may be resolved quickly.
Conflict Management: Conflict management report shall be prepared and shared with
the project client by the Project Manager.
Management of Changed Risk Responses
The outcomes that are listed above provided certain areas that may be improved. An action
and change management plan has been prepared for the management of the risk responses
that have been upgraded.
7 ean C edard et al "Risk Monitoring And Control n Audit irms A Research Synthesis"J . B ., I F : , GAUDITIN : A
ournal f Practice heoryJ O & T no doi aud27, . 1 (2008): 187-218, :10.2308/ .2008.27.1.187.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16