Public-Key Infrastructure (PKI) - Importance, Working, and Benefits
VerifiedAdded on 2022/12/15
|10
|2275
|404
AI Summary
This document provides an overview of Public-Key Infrastructure (PKI) and its importance in ensuring secure communication and data protection. It discusses the concepts of cryptography, replay attacks, obtaining digital certificates, and digital signatures. The document also explores the working of asymmetric cryptography and the benefits it offers over symmetric cryptography. It concludes with a discussion on the risks associated with PKI and recommendations to address them.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Public-Key
Infrastructure (PKI)
Part-A
Infrastructure (PKI)
Part-A
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................3
Replay attacks.........................................................................................................................3
Obtaining a digital certificate.................................................................................................3
Digital signatures....................................................................................................................4
CONCLUSION................................................................................................................................6
References:.......................................................................................................................................8
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................3
Replay attacks.........................................................................................................................3
Obtaining a digital certificate.................................................................................................3
Digital signatures....................................................................................................................4
CONCLUSION................................................................................................................................6
References:.......................................................................................................................................8

INTRODUCTION
Objectives
The following discussion is made on the cryptography and its importance, working of
asymmetric cryptography and its benefits over symmetric cryptography, concept of replay
attacks against PKI, obtaining a digital certificate and digital signatures.
Cryptography
It is defined as a technique through which information or data can be protected while
communicating or transferring it with help of private codes so that confidential data can be saved
from losing or breaches (Höglund, Lindemer, Furuhed and Raza, 2020). This is done so that only
those people could be able to access the particular information and can read and write the same
in a similar manner for the feedback. Cryptography is divided by its meaning such as crypt
means hidden or vault and graphy means writing. It is also the field of study or practice of
methods for safe and secure communication of information from place to another with full
security in the presence of adversaries also known as third parties either they are involved in an
intentional or an unintentional manner. There are three types of cryptography are available such
as secret key, public key and hash function. Secret key is also known as the private key or
symmetric cryptography used to encrypt and decrypt the personal messages which contain
private information. Public key is also known as the asymmetric cryptography which uses the
keys in pairs of public and private keys, these are dependent on the mathematical problems
which are termed as one way functions. Hash function is a mathematical algorithm that maps
information of arbitrary size to a bit array of a fixed size used to encrypt or decrypt messages to
secure the information.
Importance of cryptography
Confidentiality is one of the importance of cryptography which means that it holds back
the privacy of data and information by maintaining the confidentiality of it for better transfer of
data. Identification and authentication is an another importance of cryptography which means
that it recognises and authenticates the data and information to be put in how much security and
encoding requirements of it so that most important data can be more secure and vice versa.
Integrity is also the one of the importance of cryptography which means that it supports the data
to be integrated with the safety and security so that information cannot get leaked. Assurance of
right sender or receiver is also an another importance of cryptography which means that it aids in
1
Objectives
The following discussion is made on the cryptography and its importance, working of
asymmetric cryptography and its benefits over symmetric cryptography, concept of replay
attacks against PKI, obtaining a digital certificate and digital signatures.
Cryptography
It is defined as a technique through which information or data can be protected while
communicating or transferring it with help of private codes so that confidential data can be saved
from losing or breaches (Höglund, Lindemer, Furuhed and Raza, 2020). This is done so that only
those people could be able to access the particular information and can read and write the same
in a similar manner for the feedback. Cryptography is divided by its meaning such as crypt
means hidden or vault and graphy means writing. It is also the field of study or practice of
methods for safe and secure communication of information from place to another with full
security in the presence of adversaries also known as third parties either they are involved in an
intentional or an unintentional manner. There are three types of cryptography are available such
as secret key, public key and hash function. Secret key is also known as the private key or
symmetric cryptography used to encrypt and decrypt the personal messages which contain
private information. Public key is also known as the asymmetric cryptography which uses the
keys in pairs of public and private keys, these are dependent on the mathematical problems
which are termed as one way functions. Hash function is a mathematical algorithm that maps
information of arbitrary size to a bit array of a fixed size used to encrypt or decrypt messages to
secure the information.
Importance of cryptography
Confidentiality is one of the importance of cryptography which means that it holds back
the privacy of data and information by maintaining the confidentiality of it for better transfer of
data. Identification and authentication is an another importance of cryptography which means
that it recognises and authenticates the data and information to be put in how much security and
encoding requirements of it so that most important data can be more secure and vice versa.
Integrity is also the one of the importance of cryptography which means that it supports the data
to be integrated with the safety and security so that information cannot get leaked. Assurance of
right sender or receiver is also an another importance of cryptography which means that it aids in
1

identifying the right receiver and sender so that wrong person cannot receive the information
from the wrong sender to maintain its security. Ensures the availability of data is one of the
importance of cryptography which means that it also helps in gathering the useful data and
information as per the relevancy to the transfer context so that accuracy can be maintained in
communicating via data and information along with the security of it.
Working of asymmetric cryptography
(Isirova and Potii, 2018).
Benefits of asymmetric cryptography over symmetric
More security is one of the benefit of asymmetric cryptography which means that it is
considered as the more safer type of cryptography as it forms with the help of combination of
public and private keys, which means they are not required to switch the keys on a frequent basis
and that is why it is more secure but symmetric cryptography uses only one type of a key that is
the private key which switches itself to public key whenever required and switching part is not
safe so that is why it cannot be considered as safe data or information management. Better
management of keys is an another benefit of asymmetric cryptography which means that it uses
the combination of public and private keys which switch their working as per the needs and
requirements of the transfer of data and its communication over the network that is why this type
of cryptography is considered as the better management as compared to the symmetric
cryptography because it uses the single key for both the functions of public and private in which
management can be complex which is not good and safe for the security of data and information.
2
from the wrong sender to maintain its security. Ensures the availability of data is one of the
importance of cryptography which means that it also helps in gathering the useful data and
information as per the relevancy to the transfer context so that accuracy can be maintained in
communicating via data and information along with the security of it.
Working of asymmetric cryptography
(Isirova and Potii, 2018).
Benefits of asymmetric cryptography over symmetric
More security is one of the benefit of asymmetric cryptography which means that it is
considered as the more safer type of cryptography as it forms with the help of combination of
public and private keys, which means they are not required to switch the keys on a frequent basis
and that is why it is more secure but symmetric cryptography uses only one type of a key that is
the private key which switches itself to public key whenever required and switching part is not
safe so that is why it cannot be considered as safe data or information management. Better
management of keys is an another benefit of asymmetric cryptography which means that it uses
the combination of public and private keys which switch their working as per the needs and
requirements of the transfer of data and its communication over the network that is why this type
of cryptography is considered as the better management as compared to the symmetric
cryptography because it uses the single key for both the functions of public and private in which
management can be complex which is not good and safe for the security of data and information.
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
MAIN BODY
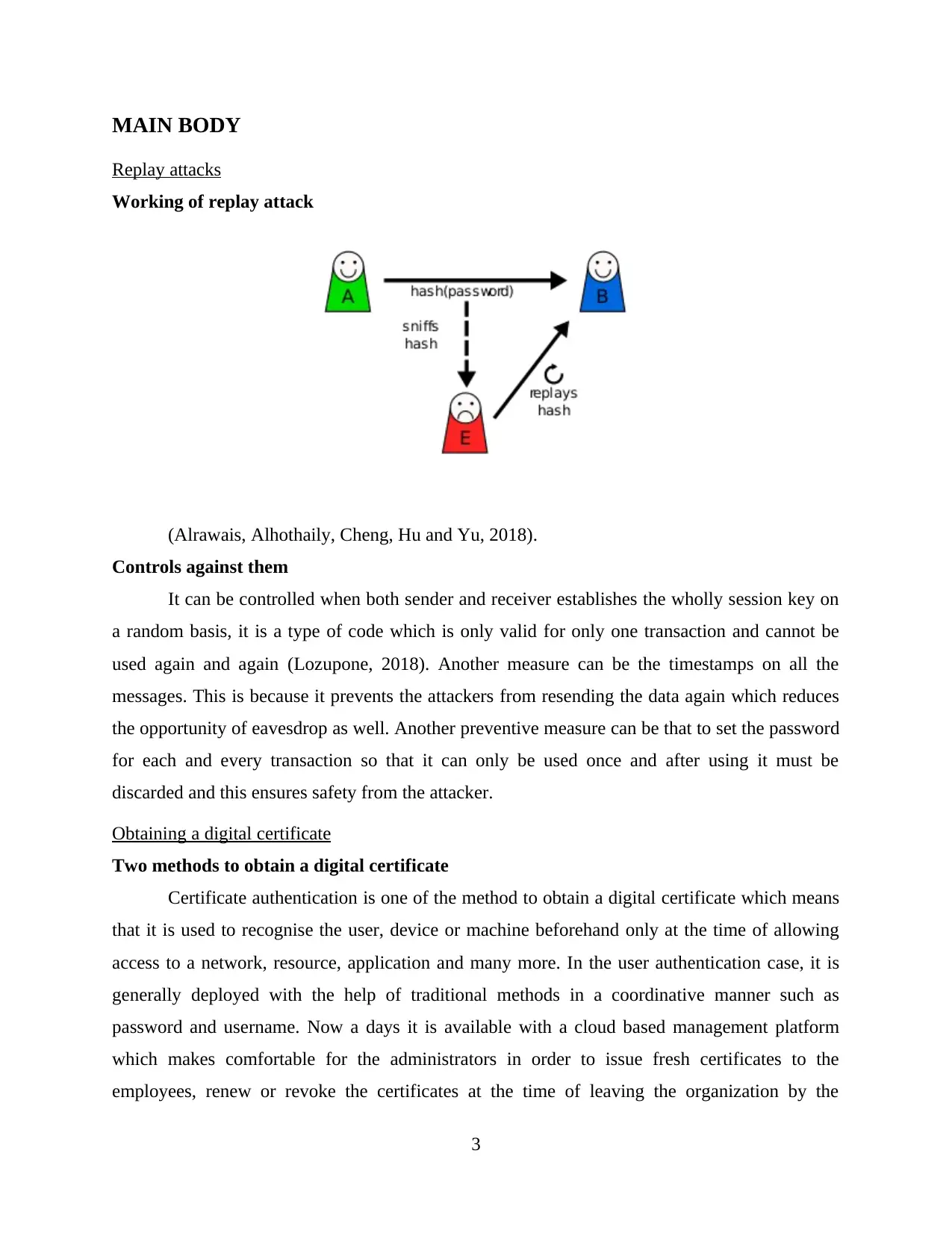
Replay attacks
Working of replay attack
(Alrawais, Alhothaily, Cheng, Hu and Yu, 2018).
Controls against them
It can be controlled when both sender and receiver establishes the wholly session key on
a random basis, it is a type of code which is only valid for only one transaction and cannot be
used again and again (Lozupone, 2018). Another measure can be the timestamps on all the
messages. This is because it prevents the attackers from resending the data again which reduces
the opportunity of eavesdrop as well. Another preventive measure can be that to set the password
for each and every transaction so that it can only be used once and after using it must be
discarded and this ensures safety from the attacker.
Obtaining a digital certificate
Two methods to obtain a digital certificate
Certificate authentication is one of the method to obtain a digital certificate which means
that it is used to recognise the user, device or machine beforehand only at the time of allowing
access to a network, resource, application and many more. In the user authentication case, it is
generally deployed with the help of traditional methods in a coordinative manner such as
password and username. Now a days it is available with a cloud based management platform
which makes comfortable for the administrators in order to issue fresh certificates to the
employees, renew or revoke the certificates at the time of leaving the organization by the
3
Replay attacks
Working of replay attack
(Alrawais, Alhothaily, Cheng, Hu and Yu, 2018).
Controls against them
It can be controlled when both sender and receiver establishes the wholly session key on
a random basis, it is a type of code which is only valid for only one transaction and cannot be
used again and again (Lozupone, 2018). Another measure can be the timestamps on all the
messages. This is because it prevents the attackers from resending the data again which reduces
the opportunity of eavesdrop as well. Another preventive measure can be that to set the password
for each and every transaction so that it can only be used once and after using it must be
discarded and this ensures safety from the attacker.
Obtaining a digital certificate
Two methods to obtain a digital certificate
Certificate authentication is one of the method to obtain a digital certificate which means
that it is used to recognise the user, device or machine beforehand only at the time of allowing
access to a network, resource, application and many more. In the user authentication case, it is
generally deployed with the help of traditional methods in a coordinative manner such as
password and username. Now a days it is available with a cloud based management platform
which makes comfortable for the administrators in order to issue fresh certificates to the
employees, renew or revoke the certificates at the time of leaving the organization by the
3

employees. Self-signed certificate is an another method to obtain a digital certificate which
means that it is not signed by the certificate authority which includes SSL and TLS certificates, S
and MIME certificates and code signing certificate. Reason behind that they are different from
traditional method is that they are generated, issued and signed by the firm or developer and they
are accountable for the signing of the software or a website and that it is considered as the unsafe
as compared to the certificate authentication method (Dykcik, Chuat, Szalachowski and Perrig,
2018).
Advantages and disadvantages of each method
Advantages of Certificate authentication are there is no requirements to distribute the
public or validate fingerprints at the time of creating or upgrading the pair of keys. Credentials
which are authenticated are able to revoked centrally. It is highly scalable in nature. It can easily
be compared the same and higher level of security to the public key authentication. It renders the
facility of identity verification with the help of secret private keys. There is a possibility of non
interactive login with the help of authentication agent. Such certificates can be used for many
purposes for example, log in, access to file servers and security of e-mail. Disadvantages of
certificate authentication are that it highly needs the public key infrastructure (PKI) which
increases the initial cost of deployment in some environments as compared to the public key
authentication. Advantages of Self-signed certificate are that they are free to incorporate. They
are compatible to the internal or intranet testing environments or sites. They helps in encrypting
the data which is incoming and outgoing with the same ciphers as compared to the any other paid
certificate. Disadvantages of self-signed certificate are that they are not trustable by the browsers
or operating systems. It negatively affects the traffic on the websites. People feel insecure while
using such method because man in the middle attacks are frequent in type of the the digital
certificate therefore it is highly risky in nature (Won, Singla, Bertino and Bollella, 2018).
Digital signatures
Overview
It is defined as the electronic fingerprints which safely relates a signer along with the
document inside the transaction which are recorded in the form of coded language. They use
standards which is an accepted format known as the public key infrastructure in order to render
biggest level of safety and acceptance universally (Neish, Walter and Powell, 2019). It is a
mathematical method for depicting the authenticity of documents or messages which are digital
4
means that it is not signed by the certificate authority which includes SSL and TLS certificates, S
and MIME certificates and code signing certificate. Reason behind that they are different from
traditional method is that they are generated, issued and signed by the firm or developer and they
are accountable for the signing of the software or a website and that it is considered as the unsafe
as compared to the certificate authentication method (Dykcik, Chuat, Szalachowski and Perrig,
2018).
Advantages and disadvantages of each method
Advantages of Certificate authentication are there is no requirements to distribute the
public or validate fingerprints at the time of creating or upgrading the pair of keys. Credentials
which are authenticated are able to revoked centrally. It is highly scalable in nature. It can easily
be compared the same and higher level of security to the public key authentication. It renders the
facility of identity verification with the help of secret private keys. There is a possibility of non
interactive login with the help of authentication agent. Such certificates can be used for many
purposes for example, log in, access to file servers and security of e-mail. Disadvantages of
certificate authentication are that it highly needs the public key infrastructure (PKI) which
increases the initial cost of deployment in some environments as compared to the public key
authentication. Advantages of Self-signed certificate are that they are free to incorporate. They
are compatible to the internal or intranet testing environments or sites. They helps in encrypting
the data which is incoming and outgoing with the same ciphers as compared to the any other paid
certificate. Disadvantages of self-signed certificate are that they are not trustable by the browsers
or operating systems. It negatively affects the traffic on the websites. People feel insecure while
using such method because man in the middle attacks are frequent in type of the the digital
certificate therefore it is highly risky in nature (Won, Singla, Bertino and Bollella, 2018).
Digital signatures
Overview
It is defined as the electronic fingerprints which safely relates a signer along with the
document inside the transaction which are recorded in the form of coded language. They use
standards which is an accepted format known as the public key infrastructure in order to render
biggest level of safety and acceptance universally (Neish, Walter and Powell, 2019). It is a
mathematical method for depicting the authenticity of documents or messages which are digital
4
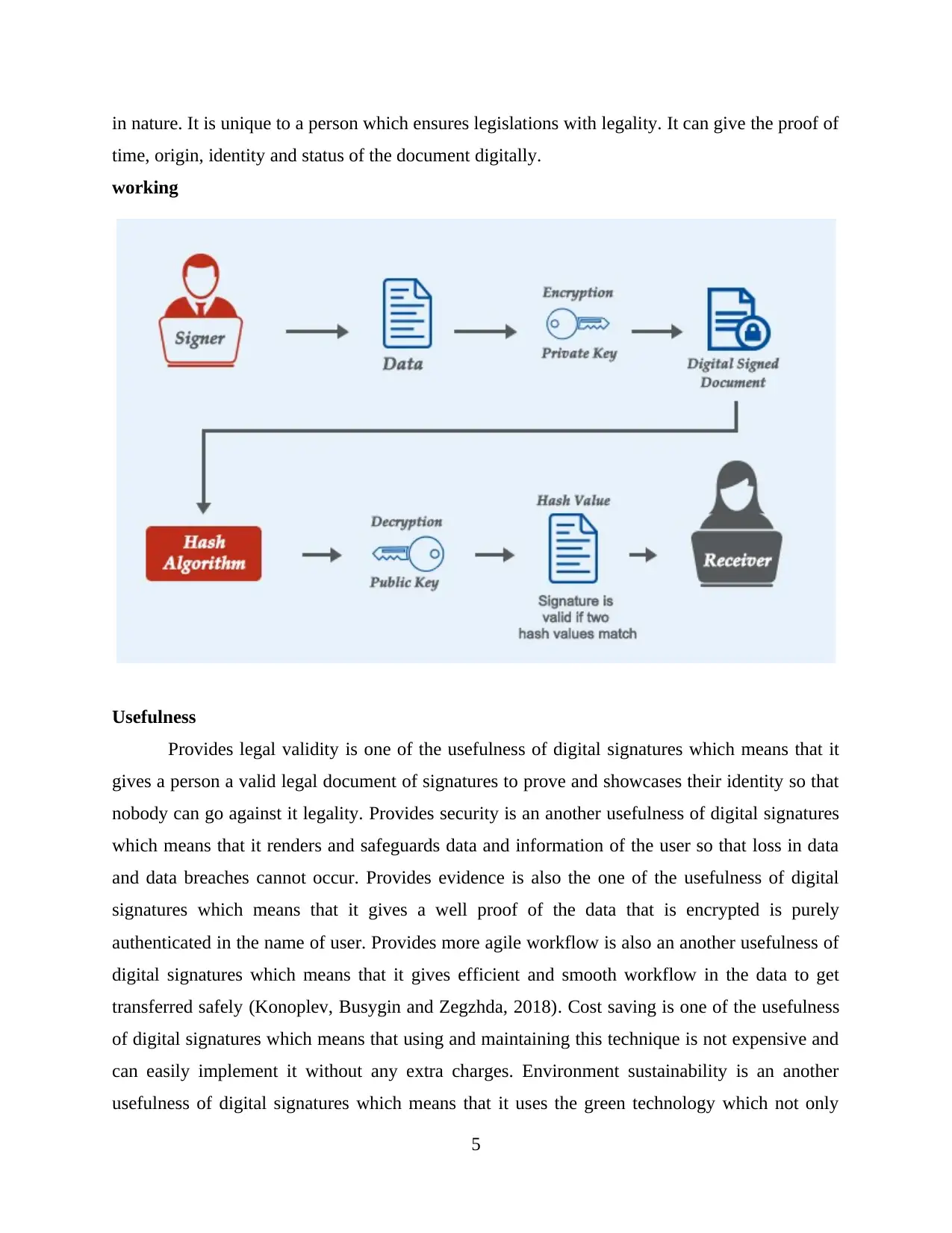
in nature. It is unique to a person which ensures legislations with legality. It can give the proof of
time, origin, identity and status of the document digitally.
working
Usefulness
Provides legal validity is one of the usefulness of digital signatures which means that it
gives a person a valid legal document of signatures to prove and showcases their identity so that
nobody can go against it legality. Provides security is an another usefulness of digital signatures
which means that it renders and safeguards data and information of the user so that loss in data
and data breaches cannot occur. Provides evidence is also the one of the usefulness of digital
signatures which means that it gives a well proof of the data that is encrypted is purely
authenticated in the name of user. Provides more agile workflow is also an another usefulness of
digital signatures which means that it gives efficient and smooth workflow in the data to get
transferred safely (Konoplev, Busygin and Zegzhda, 2018). Cost saving is one of the usefulness
of digital signatures which means that using and maintaining this technique is not expensive and
can easily implement it without any extra charges. Environment sustainability is an another
usefulness of digital signatures which means that it uses the green technology which not only
5
time, origin, identity and status of the document digitally.
working
Usefulness
Provides legal validity is one of the usefulness of digital signatures which means that it
gives a person a valid legal document of signatures to prove and showcases their identity so that
nobody can go against it legality. Provides security is an another usefulness of digital signatures
which means that it renders and safeguards data and information of the user so that loss in data
and data breaches cannot occur. Provides evidence is also the one of the usefulness of digital
signatures which means that it gives a well proof of the data that is encrypted is purely
authenticated in the name of user. Provides more agile workflow is also an another usefulness of
digital signatures which means that it gives efficient and smooth workflow in the data to get
transferred safely (Konoplev, Busygin and Zegzhda, 2018). Cost saving is one of the usefulness
of digital signatures which means that using and maintaining this technique is not expensive and
can easily implement it without any extra charges. Environment sustainability is an another
usefulness of digital signatures which means that it uses the green technology which not only
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
saves cost but also the time and energy as well. Better time management is also the one of the
usefulness of digital signatures which means that it saves time and fear from being breached and
maintains trust to carry out the activities. Access from anywhere and at any time is also an
another usefulness of digital signatures which means that it can get used at the time of mobility
of a person at any time they want. Business efficiency is one of the usefulness of digital
signatures which means that it helps the business in its operations and management in a safe
manner with better data and information storage and security.
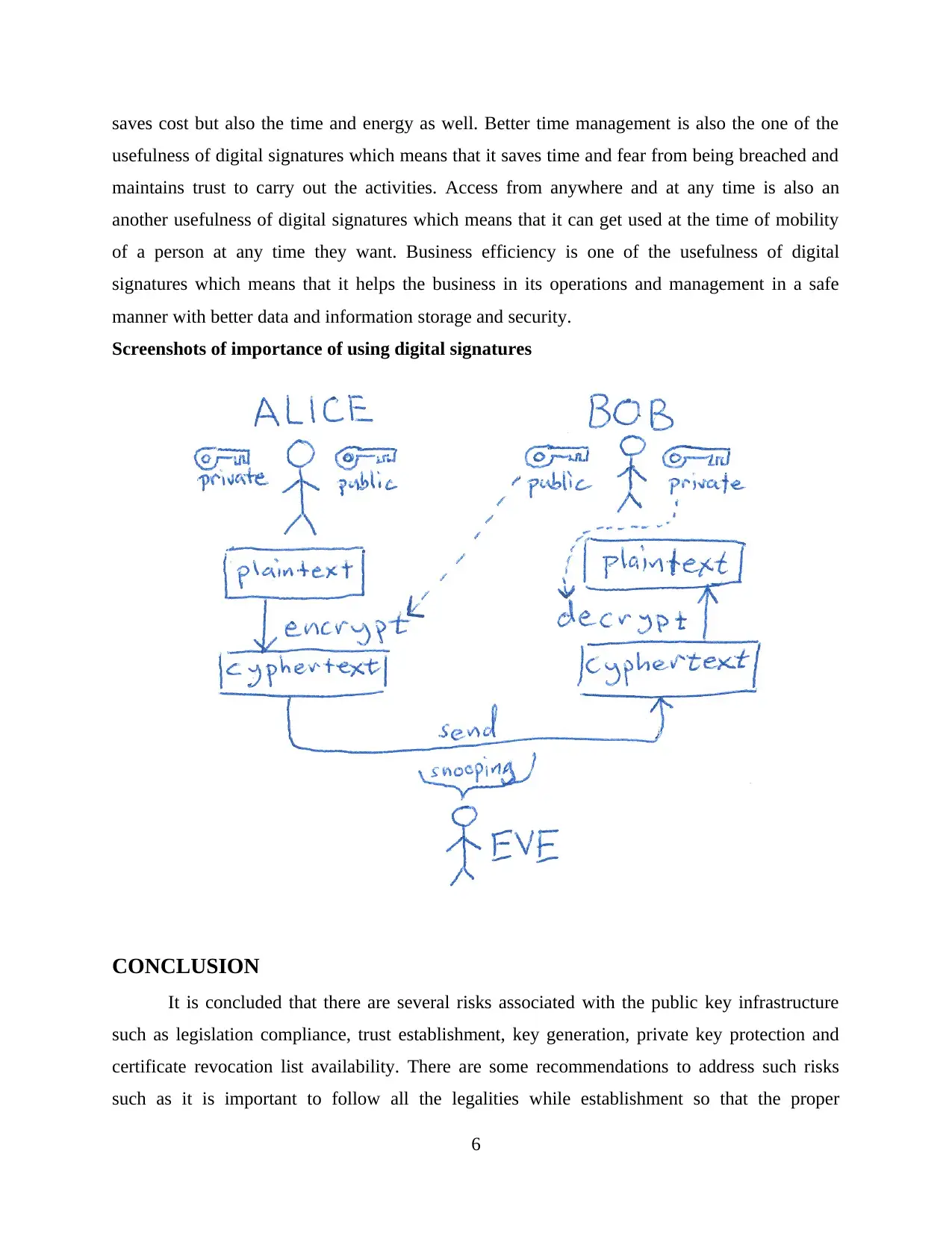
Screenshots of importance of using digital signatures
CONCLUSION
It is concluded that there are several risks associated with the public key infrastructure
such as legislation compliance, trust establishment, key generation, private key protection and
certificate revocation list availability. There are some recommendations to address such risks
such as it is important to follow all the legalities while establishment so that the proper
6
usefulness of digital signatures which means that it saves time and fear from being breached and
maintains trust to carry out the activities. Access from anywhere and at any time is also an
another usefulness of digital signatures which means that it can get used at the time of mobility
of a person at any time they want. Business efficiency is one of the usefulness of digital
signatures which means that it helps the business in its operations and management in a safe
manner with better data and information storage and security.
Screenshots of importance of using digital signatures
CONCLUSION
It is concluded that there are several risks associated with the public key infrastructure
such as legislation compliance, trust establishment, key generation, private key protection and
certificate revocation list availability. There are some recommendations to address such risks
such as it is important to follow all the legalities while establishment so that the proper
6

authentication and authorization can be performed while using. All the mathematical algorithms
must be used in an appropriate manner so that it can be accurate in nature without any bugs and
errors.
7
must be used in an appropriate manner so that it can be accurate in nature without any bugs and
errors.
7

References:
Books and Journals
Alrawais, A., Alhothaily, A., Cheng, X., Hu, C. and Yu, J., 2018. SecureGuard: A certificate
validation system in public key infrastructure. IEEE Transactions on Vehicular
Technology. 67(6). pp.5399-5408.
Dykcik, L., Chuat, L., Szalachowski, P. and Perrig, A., 2018, November. BlockPKI: an
automated, resilient, and transparent public-key infrastructure. In 2018 IEEE
International Conference on Data Mining Workshops (ICDMW) (pp. 105-114). IEEE.
Höglund, J., Lindemer, S., Furuhed, M. and Raza, S., 2020. PKI4IoT: Towards public key
infrastructure for the Internet of Things. Computers & Security, 89, p.101658.
Isirova, K. and Potii, O., 2018, May. Decentralized public key infrastructure development
principles. In 2018 IEEE 9th International Conference on Dependable Systems, Services
and Technologies (DESSERT) (pp. 305-310). IEEE.
Konoplev, A.S., Busygin, A.G. and Zegzhda, D.P., 2018. A blockchain decentralized public key
infrastructure model. Automatic Control and Computer Sciences. 52(8). pp.1017-1021.
Lozupone, V., 2018. Analyze encryption and public key infrastructure (PKI). International
Journal of Information Management. 38(1). pp.42-44.
Neish, A., Walter, T. and Powell, J.D., 2019, April. Design and analysis of a public key
infrastructure for SBAS data authentication. In Proceedings of the ION 2019 Pacific
PNT Meeting (pp. 964-988).
Won, J., Singla, A., Bertino, E. and Bollella, G., 2018, October. Decentralized public key
infrastructure for internet-of-things. In MILCOM 2018-2018 IEEE Military
Communications Conference (MILCOM) (pp. 907-913). IEEE.
8
Books and Journals
Alrawais, A., Alhothaily, A., Cheng, X., Hu, C. and Yu, J., 2018. SecureGuard: A certificate
validation system in public key infrastructure. IEEE Transactions on Vehicular
Technology. 67(6). pp.5399-5408.
Dykcik, L., Chuat, L., Szalachowski, P. and Perrig, A., 2018, November. BlockPKI: an
automated, resilient, and transparent public-key infrastructure. In 2018 IEEE
International Conference on Data Mining Workshops (ICDMW) (pp. 105-114). IEEE.
Höglund, J., Lindemer, S., Furuhed, M. and Raza, S., 2020. PKI4IoT: Towards public key
infrastructure for the Internet of Things. Computers & Security, 89, p.101658.
Isirova, K. and Potii, O., 2018, May. Decentralized public key infrastructure development
principles. In 2018 IEEE 9th International Conference on Dependable Systems, Services
and Technologies (DESSERT) (pp. 305-310). IEEE.
Konoplev, A.S., Busygin, A.G. and Zegzhda, D.P., 2018. A blockchain decentralized public key
infrastructure model. Automatic Control and Computer Sciences. 52(8). pp.1017-1021.
Lozupone, V., 2018. Analyze encryption and public key infrastructure (PKI). International
Journal of Information Management. 38(1). pp.42-44.
Neish, A., Walter, T. and Powell, J.D., 2019, April. Design and analysis of a public key
infrastructure for SBAS data authentication. In Proceedings of the ION 2019 Pacific
PNT Meeting (pp. 964-988).
Won, J., Singla, A., Bertino, E. and Bollella, G., 2018, October. Decentralized public key
infrastructure for internet-of-things. In MILCOM 2018-2018 IEEE Military
Communications Conference (MILCOM) (pp. 907-913). IEEE.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





