Risk Management in Healthcare Application Project: Analysis
VerifiedAdded on 2023/04/07
|15
|3514
|419
Report
AI Summary
This report provides a detailed analysis of project risk management within the context of a healthcare mobile application development project. It begins by identifying potential risk events, focusing on information security threats in the production environment, including malware attacks, insider threats, data breaches, data loss, and denial-of-service attacks. The report then explores the key causes of these risks, emphasizing the lack of technical security controls and potential user errors. A qualitative risk analysis is conducted using consequence and likelihood tables to assess the severity and probability of each risk. Subsequently, the report proposes various risk treatment strategies, such as implementing technical security controls, encryption, and access control mechanisms. The residual risks and potential secondary risks, like cryptanalysis attacks, are also discussed. The report concludes with a risk register summarizing the identified risks, their likelihood, consequence, and risk ratings, along with a reflection and critical analysis of the risk management process. This assignment is available on Desklib, where students can access a wealth of academic resources, including past papers and solved assignments.
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Project Risk Management
Healthcare Application
3/18/2019
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Project Risk Management
Healthcare Application
3/18/2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Risk Management
Table of Contents
Introduction...........................................................................................................................................2
Project Background...........................................................................................................................2
Risk Identification.................................................................................................................................2
Risk Event.........................................................................................................................................2
Key Causes........................................................................................................................................3
Qualitative Risk Analysis......................................................................................................................4
Consequence Table............................................................................................................................4
Likelihood Table...............................................................................................................................4
Likelihood Consequence Table.........................................................................................................5
Consequence & Probability Explanation & Justification...................................................................5
Risk Treatment......................................................................................................................................6
Possible Treatments...........................................................................................................................6
Residual Risk.....................................................................................................................................7
Secondary Risk..................................................................................................................................8
Risk Register.........................................................................................................................................8
Reflection............................................................................................................................................11
Critical Analysis..............................................................................................................................11
References...........................................................................................................................................13
1
Table of Contents
Introduction...........................................................................................................................................2
Project Background...........................................................................................................................2
Risk Identification.................................................................................................................................2
Risk Event.........................................................................................................................................2
Key Causes........................................................................................................................................3
Qualitative Risk Analysis......................................................................................................................4
Consequence Table............................................................................................................................4
Likelihood Table...............................................................................................................................4
Likelihood Consequence Table.........................................................................................................5
Consequence & Probability Explanation & Justification...................................................................5
Risk Treatment......................................................................................................................................6
Possible Treatments...........................................................................................................................6
Residual Risk.....................................................................................................................................7
Secondary Risk..................................................................................................................................8
Risk Register.........................................................................................................................................8
Reflection............................................................................................................................................11
Critical Analysis..............................................................................................................................11
References...........................................................................................................................................13
1

Project Risk Management
Introduction
The risk management is one of the significant areas under project management. A risk is
defined as an event that may have an impact on the project progress, operations, and its
elements and the nature of the impacts may be positive or negative. The occurrence of the
risks during the project timeline may alter the determined levels of scope, costs, and schedule
that may impact the client satisfaction levels as well. There are also various other possible
implications of these risks and it is, therefore, essential that the management of the risks is
done adequately. The risk management is also included as one of the significant areas under a
majority of the project management methodologies. The report covers the risk management
for one of the projects.
Project Background
The project is an ongoing project which involves the development of a mobile application for
the employees of the healthcare firm. The mobile application is to be developed for the
Android and iOS platforms and it will include the main modules as user login, patient data
records, data analysis, medical reports, and information sharing. It will allow the doctors and
nursing staff to keep a track of the patient data and analyse the same to determine patterns for
enhanced medical diagnosis and reporting. Information sharing will also be possible between
the medical professionals and the patients through the application.
Risk Identification
Risk Event
There will be various risks that may be involved in the project. One such risk event that may
appear during the project timeline is the emergence of information security threats and
attacks. The mobile application that is being developed for the healthcare care will be done in
three major environments as development environment, test environment, and production
environment. The application developers and the testing team members will perform the
development and testing activities in the first two environments. The production environment
will include user acceptance testing processes along with the deployment activities. The risk
event that is included may take place in the production environment of the project. This is
because the development and test environments will involve the dummy data sets; however,
the real data and information will be used in the production environment of the project. These
2
Introduction
The risk management is one of the significant areas under project management. A risk is
defined as an event that may have an impact on the project progress, operations, and its
elements and the nature of the impacts may be positive or negative. The occurrence of the
risks during the project timeline may alter the determined levels of scope, costs, and schedule
that may impact the client satisfaction levels as well. There are also various other possible
implications of these risks and it is, therefore, essential that the management of the risks is
done adequately. The risk management is also included as one of the significant areas under a
majority of the project management methodologies. The report covers the risk management
for one of the projects.
Project Background
The project is an ongoing project which involves the development of a mobile application for
the employees of the healthcare firm. The mobile application is to be developed for the
Android and iOS platforms and it will include the main modules as user login, patient data
records, data analysis, medical reports, and information sharing. It will allow the doctors and
nursing staff to keep a track of the patient data and analyse the same to determine patterns for
enhanced medical diagnosis and reporting. Information sharing will also be possible between
the medical professionals and the patients through the application.
Risk Identification
Risk Event
There will be various risks that may be involved in the project. One such risk event that may
appear during the project timeline is the emergence of information security threats and
attacks. The mobile application that is being developed for the healthcare care will be done in
three major environments as development environment, test environment, and production
environment. The application developers and the testing team members will perform the
development and testing activities in the first two environments. The production environment
will include user acceptance testing processes along with the deployment activities. The risk
event that is included may take place in the production environment of the project. This is
because the development and test environments will involve the dummy data sets; however,
the real data and information will be used in the production environment of the project. These
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Risk Management
data sets will be exposed to the information security risks and attacks (Deursen, Buchanan
and Duff 2013).
The healthcare information is one of the most critical pieces of data and the security attacks
on these data sets can have severe implications. The data in the production environment will
have an enhanced attack surface and attack window. This is because the application will not
be fully implemented and the exposure of the data sets to the unauthorized entities may be
done with ease. The first form of information security attack that may occur in this risk event
is malware threats and attacks (Bahtiyar 2016). These are the attacks in which the malicious
codes and software may be used to impact the information privacy, confidentiality, and
availability. These may be carried out on the production data sets through files and the
application modules. The employees developing the mobile application will also be provided
with the grants and permissions of the production data. The competitors of the healthcare
firm may influence these employees and gain access to these data sets. These will be the
insider threats and may have severe implications on the data properties (Probst 2011).
The primary users of the mobile application will be the patients and the medical
professionals. Some of these users will be provided with the beta version of the mobile
application. The users may not be aware of the functionalities initially and may carry out the
operations resulting in improper handling of the data sets. The networks will be the important
element in the mobile application and the network testing will also be necessary. The use of
the production data over the networks during the testing phase may result in the breaching
and loss of the data sets. There may also be issues of the denial of services attacks conducted
by the malicious entities (Bertino 2015).
Key Causes
The primary cause behind the occurrence of the risk event described above is the lack of
technical and logical security controls before the final implementation of the mobile
application. This may result in the enhanced attack surface and attack window providing the
malicious entities with the opportunity to easily carry out the risk. The security threat agents
in this case may involve the users, application modules, or the networks being used in the
application for the purpose of testing and implementation (Green 2015).
The second cause that may be involved may be the users carrying out the user acceptance
testing processes. Some of these users may be provided with the production data sets. The
users may not be aware of the security practices and measures and may carry out certain
3
data sets will be exposed to the information security risks and attacks (Deursen, Buchanan
and Duff 2013).
The healthcare information is one of the most critical pieces of data and the security attacks
on these data sets can have severe implications. The data in the production environment will
have an enhanced attack surface and attack window. This is because the application will not
be fully implemented and the exposure of the data sets to the unauthorized entities may be
done with ease. The first form of information security attack that may occur in this risk event
is malware threats and attacks (Bahtiyar 2016). These are the attacks in which the malicious
codes and software may be used to impact the information privacy, confidentiality, and
availability. These may be carried out on the production data sets through files and the
application modules. The employees developing the mobile application will also be provided
with the grants and permissions of the production data. The competitors of the healthcare
firm may influence these employees and gain access to these data sets. These will be the
insider threats and may have severe implications on the data properties (Probst 2011).
The primary users of the mobile application will be the patients and the medical
professionals. Some of these users will be provided with the beta version of the mobile
application. The users may not be aware of the functionalities initially and may carry out the
operations resulting in improper handling of the data sets. The networks will be the important
element in the mobile application and the network testing will also be necessary. The use of
the production data over the networks during the testing phase may result in the breaching
and loss of the data sets. There may also be issues of the denial of services attacks conducted
by the malicious entities (Bertino 2015).
Key Causes
The primary cause behind the occurrence of the risk event described above is the lack of
technical and logical security controls before the final implementation of the mobile
application. This may result in the enhanced attack surface and attack window providing the
malicious entities with the opportunity to easily carry out the risk. The security threat agents
in this case may involve the users, application modules, or the networks being used in the
application for the purpose of testing and implementation (Green 2015).
The second cause that may be involved may be the users carrying out the user acceptance
testing processes. Some of these users may be provided with the production data sets. The
users may not be aware of the security practices and measures and may carry out certain
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project Risk Management
activities that may lead to the exposure of the data sets. The employees of the organization
may also get involved in the process and may deliberately transfer the data sets to the
competitors.
Qualitative Risk Analysis
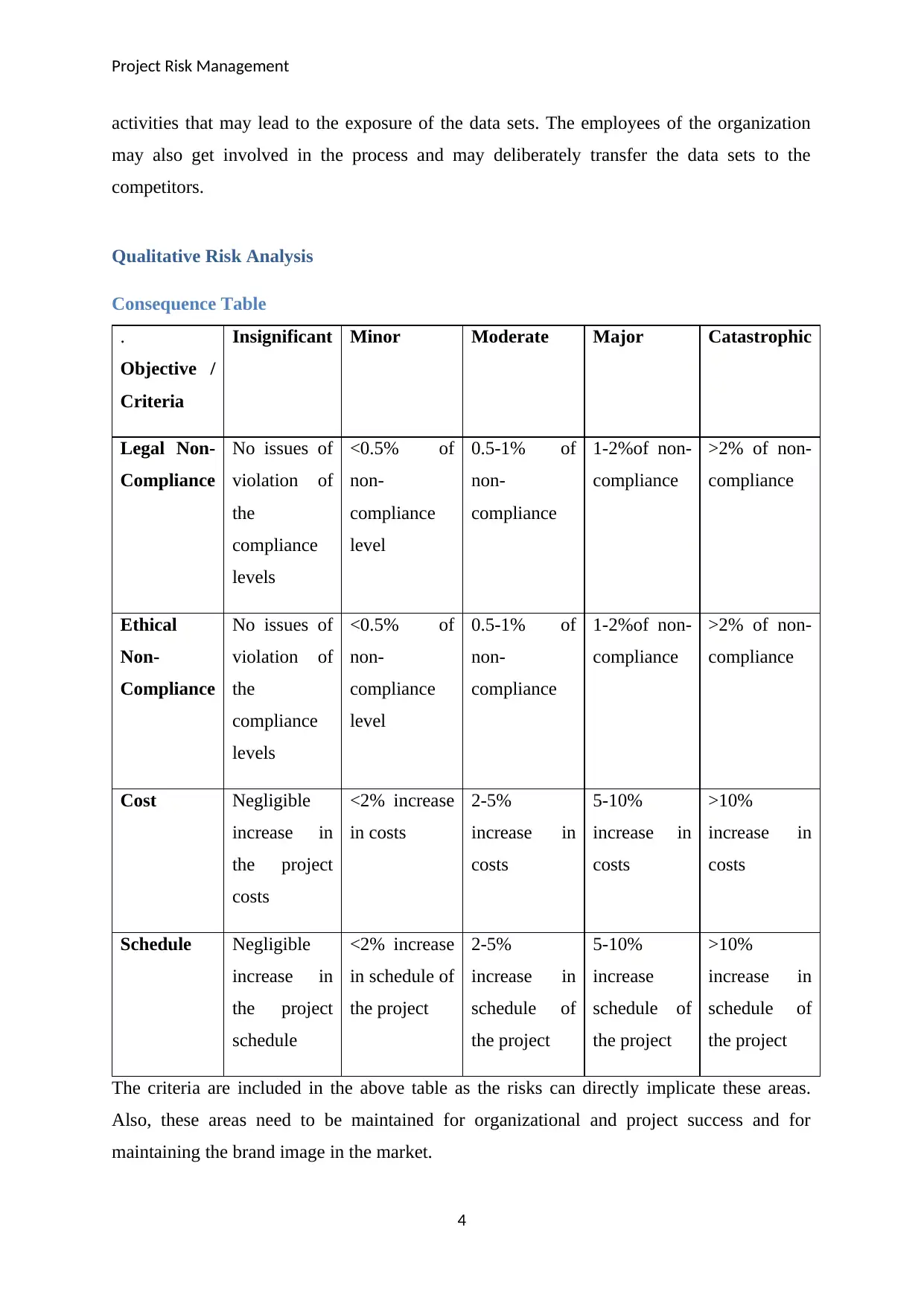
Consequence Table
.
Objective /
Criteria
Insignificant Minor Moderate Major Catastrophic
Legal Non-
Compliance
No issues of
violation of
the
compliance
levels
<0.5% of
non-
compliance
level
0.5-1% of
non-
compliance
1-2%of non-
compliance
>2% of non-
compliance
Ethical
Non-
Compliance
No issues of
violation of
the
compliance
levels
<0.5% of
non-
compliance
level
0.5-1% of
non-
compliance
1-2%of non-
compliance
>2% of non-
compliance
Cost Negligible
increase in
the project
costs
<2% increase
in costs
2-5%
increase in
costs
5-10%
increase in
costs
>10%
increase in
costs
Schedule Negligible
increase in
the project
schedule
<2% increase
in schedule of
the project
2-5%
increase in
schedule of
the project
5-10%
increase
schedule of
the project
>10%
increase in
schedule of
the project
The criteria are included in the above table as the risks can directly implicate these areas.
Also, these areas need to be maintained for organizational and project success and for
maintaining the brand image in the market.
4
activities that may lead to the exposure of the data sets. The employees of the organization
may also get involved in the process and may deliberately transfer the data sets to the
competitors.
Qualitative Risk Analysis
Consequence Table
.
Objective /
Criteria
Insignificant Minor Moderate Major Catastrophic
Legal Non-
Compliance
No issues of
violation of
the
compliance
levels
<0.5% of
non-
compliance
level
0.5-1% of
non-
compliance
1-2%of non-
compliance
>2% of non-
compliance
Ethical
Non-
Compliance
No issues of
violation of
the
compliance
levels
<0.5% of
non-
compliance
level
0.5-1% of
non-
compliance
1-2%of non-
compliance
>2% of non-
compliance
Cost Negligible
increase in
the project
costs
<2% increase
in costs
2-5%
increase in
costs
5-10%
increase in
costs
>10%
increase in
costs
Schedule Negligible
increase in
the project
schedule
<2% increase
in schedule of
the project
2-5%
increase in
schedule of
the project
5-10%
increase
schedule of
the project
>10%
increase in
schedule of
the project
The criteria are included in the above table as the risks can directly implicate these areas.
Also, these areas need to be maintained for organizational and project success and for
maintaining the brand image in the market.
4
Project Risk Management
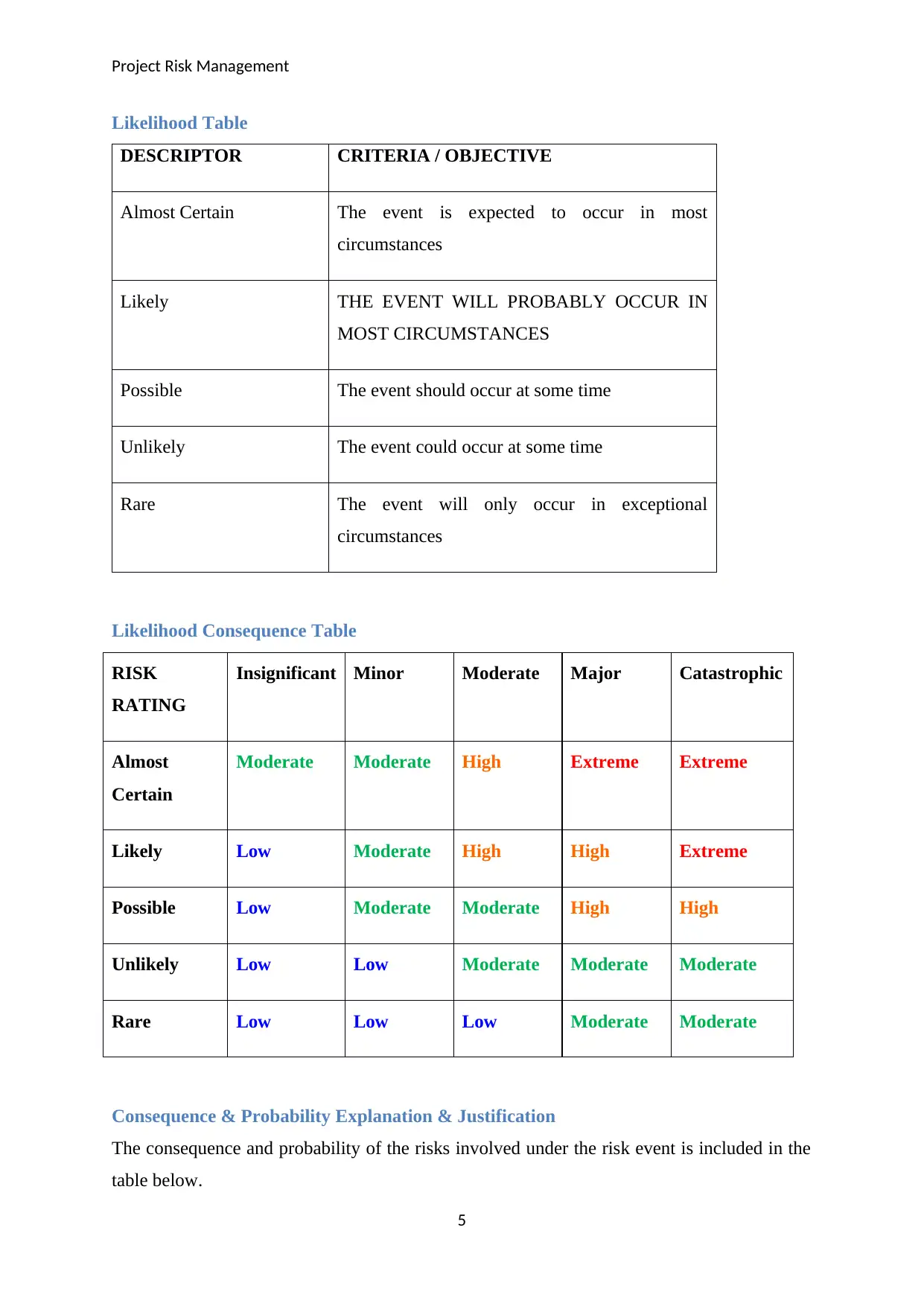
Likelihood Table
DESCRIPTOR CRITERIA / OBJECTIVE
Almost Certain The event is expected to occur in most
circumstances
Likely THE EVENT WILL PROBABLY OCCUR IN
MOST CIRCUMSTANCES
Possible The event should occur at some time
Unlikely The event could occur at some time
Rare The event will only occur in exceptional
circumstances
Likelihood Consequence Table
RISK
RATING
Insignificant Minor Moderate Major Catastrophic
Almost
Certain
Moderate Moderate High Extreme Extreme
Likely Low Moderate High High Extreme
Possible Low Moderate Moderate High High
Unlikely Low Low Moderate Moderate Moderate
Rare Low Low Low Moderate Moderate
Consequence & Probability Explanation & Justification
The consequence and probability of the risks involved under the risk event is included in the
table below.
5
Likelihood Table
DESCRIPTOR CRITERIA / OBJECTIVE
Almost Certain The event is expected to occur in most
circumstances
Likely THE EVENT WILL PROBABLY OCCUR IN
MOST CIRCUMSTANCES
Possible The event should occur at some time
Unlikely The event could occur at some time
Rare The event will only occur in exceptional
circumstances
Likelihood Consequence Table
RISK
RATING
Insignificant Minor Moderate Major Catastrophic
Almost
Certain
Moderate Moderate High Extreme Extreme
Likely Low Moderate High High Extreme
Possible Low Moderate Moderate High High
Unlikely Low Low Moderate Moderate Moderate
Rare Low Low Low Moderate Moderate
Consequence & Probability Explanation & Justification
The consequence and probability of the risks involved under the risk event is included in the
table below.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Project Risk Management
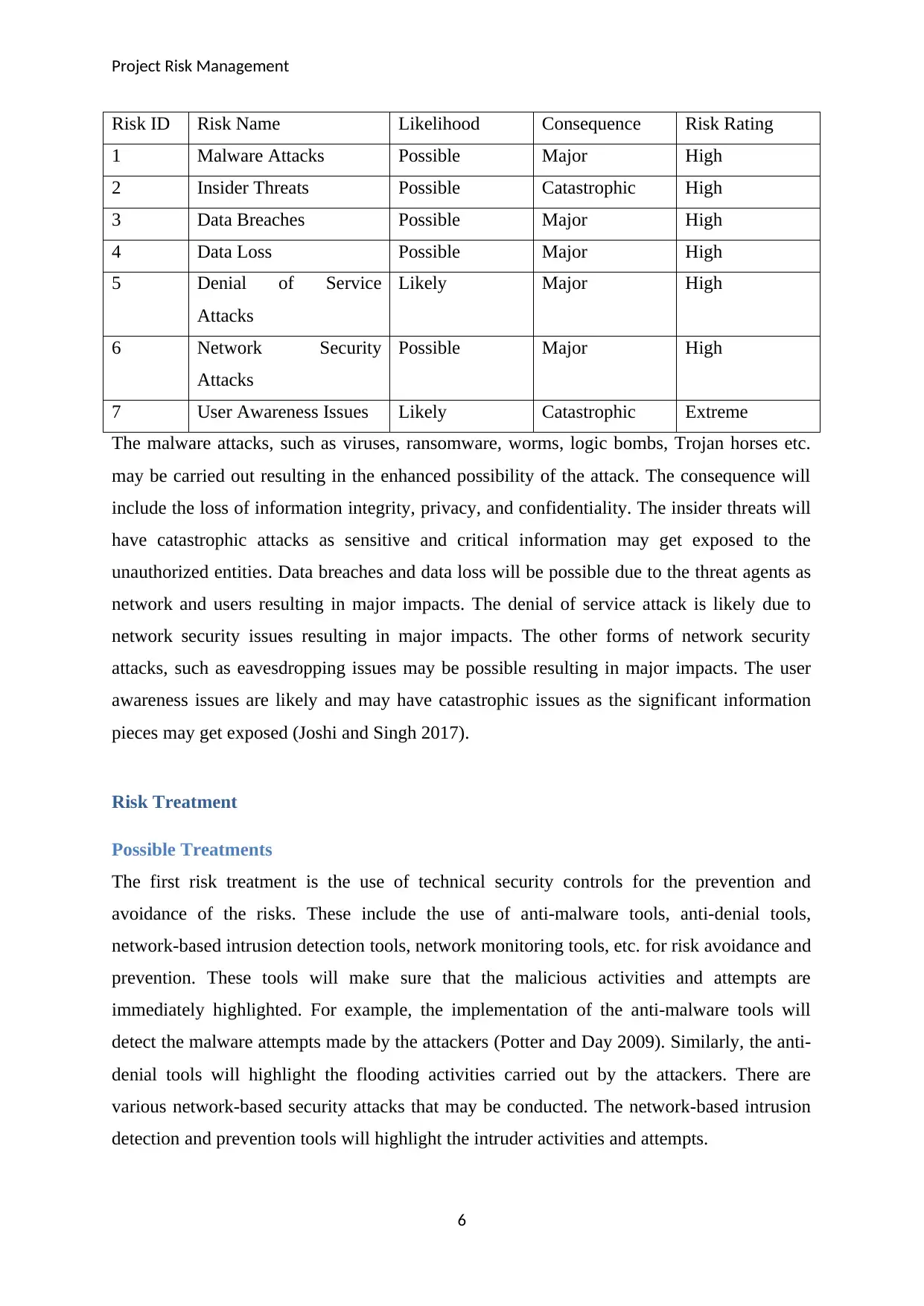
Risk ID Risk Name Likelihood Consequence Risk Rating
1 Malware Attacks Possible Major High
2 Insider Threats Possible Catastrophic High
3 Data Breaches Possible Major High
4 Data Loss Possible Major High
5 Denial of Service
Attacks
Likely Major High
6 Network Security
Attacks
Possible Major High
7 User Awareness Issues Likely Catastrophic Extreme
The malware attacks, such as viruses, ransomware, worms, logic bombs, Trojan horses etc.
may be carried out resulting in the enhanced possibility of the attack. The consequence will
include the loss of information integrity, privacy, and confidentiality. The insider threats will
have catastrophic attacks as sensitive and critical information may get exposed to the
unauthorized entities. Data breaches and data loss will be possible due to the threat agents as
network and users resulting in major impacts. The denial of service attack is likely due to
network security issues resulting in major impacts. The other forms of network security
attacks, such as eavesdropping issues may be possible resulting in major impacts. The user
awareness issues are likely and may have catastrophic issues as the significant information
pieces may get exposed (Joshi and Singh 2017).
Risk Treatment
Possible Treatments
The first risk treatment is the use of technical security controls for the prevention and
avoidance of the risks. These include the use of anti-malware tools, anti-denial tools,
network-based intrusion detection tools, network monitoring tools, etc. for risk avoidance and
prevention. These tools will make sure that the malicious activities and attempts are
immediately highlighted. For example, the implementation of the anti-malware tools will
detect the malware attempts made by the attackers (Potter and Day 2009). Similarly, the anti-
denial tools will highlight the flooding activities carried out by the attackers. There are
various network-based security attacks that may be conducted. The network-based intrusion
detection and prevention tools will highlight the intruder activities and attempts.
6
Risk ID Risk Name Likelihood Consequence Risk Rating
1 Malware Attacks Possible Major High
2 Insider Threats Possible Catastrophic High
3 Data Breaches Possible Major High
4 Data Loss Possible Major High
5 Denial of Service
Attacks
Likely Major High
6 Network Security
Attacks
Possible Major High
7 User Awareness Issues Likely Catastrophic Extreme
The malware attacks, such as viruses, ransomware, worms, logic bombs, Trojan horses etc.
may be carried out resulting in the enhanced possibility of the attack. The consequence will
include the loss of information integrity, privacy, and confidentiality. The insider threats will
have catastrophic attacks as sensitive and critical information may get exposed to the
unauthorized entities. Data breaches and data loss will be possible due to the threat agents as
network and users resulting in major impacts. The denial of service attack is likely due to
network security issues resulting in major impacts. The other forms of network security
attacks, such as eavesdropping issues may be possible resulting in major impacts. The user
awareness issues are likely and may have catastrophic issues as the significant information
pieces may get exposed (Joshi and Singh 2017).
Risk Treatment
Possible Treatments
The first risk treatment is the use of technical security controls for the prevention and
avoidance of the risks. These include the use of anti-malware tools, anti-denial tools,
network-based intrusion detection tools, network monitoring tools, etc. for risk avoidance and
prevention. These tools will make sure that the malicious activities and attempts are
immediately highlighted. For example, the implementation of the anti-malware tools will
detect the malware attempts made by the attackers (Potter and Day 2009). Similarly, the anti-
denial tools will highlight the flooding activities carried out by the attackers. There are
various network-based security attacks that may be conducted. The network-based intrusion
detection and prevention tools will highlight the intruder activities and attempts.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project Risk Management
Encryption is another method that shall be used for the purpose of risk treatment. All of the
data and information in the mobile application shall be encrypted using the data encryption
algorithms. Some of these algorithms shall include advanced data encryption standard, triple
data encryption standard, and likewise. The encryption of the data sets will convert the
application data in its cipher form and the attackers will not be able to decrypt the data
without the secret key. The attackers will not be able to decrypt these data sets and the data
loss and breaching of the data sets will be avoided (Neelima and Brinda 2018).
Access control is the third mechanism that shall be used. The risk treatment involved the use
of role-based access control along with access control lists for preventing the risks. The users
shall be provided with the data permissions on the basis of their role. For example, the
employees of the organization will be provided with the data access on the basis of their roles
(Franqueira and Wieringa 2012). The permissions provided to the Database Administrator
will be different from that of the analyst and likewise. There shall also be use of access
control lists that shall be used to avoid the attacks.
All of these three treatment methods will be acceptable as they will be able to control and
mitigate the risks.
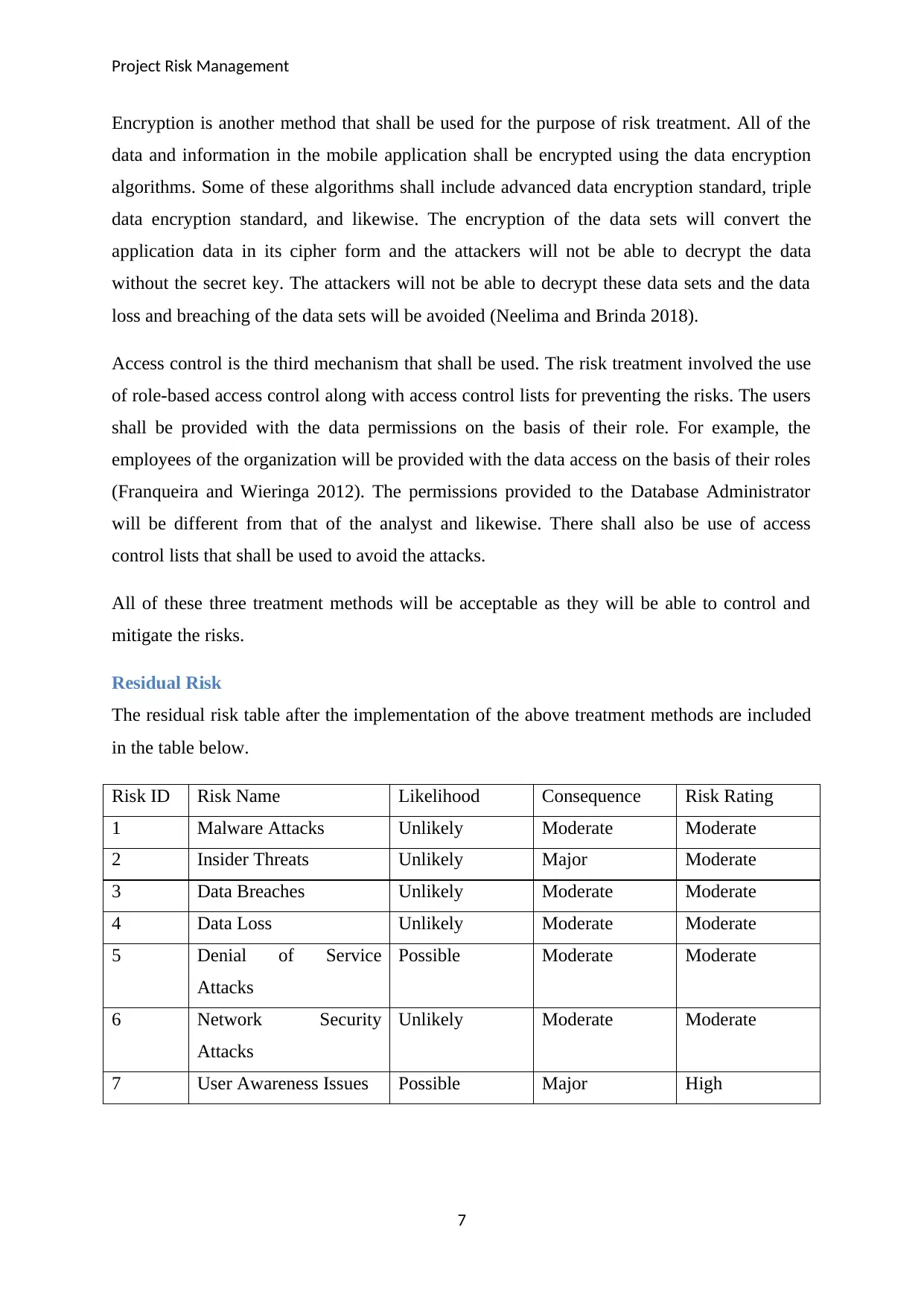
Residual Risk
The residual risk table after the implementation of the above treatment methods are included
in the table below.
Risk ID Risk Name Likelihood Consequence Risk Rating
1 Malware Attacks Unlikely Moderate Moderate
2 Insider Threats Unlikely Major Moderate
3 Data Breaches Unlikely Moderate Moderate
4 Data Loss Unlikely Moderate Moderate
5 Denial of Service
Attacks
Possible Moderate Moderate
6 Network Security
Attacks
Unlikely Moderate Moderate
7 User Awareness Issues Possible Major High
7
Encryption is another method that shall be used for the purpose of risk treatment. All of the
data and information in the mobile application shall be encrypted using the data encryption
algorithms. Some of these algorithms shall include advanced data encryption standard, triple
data encryption standard, and likewise. The encryption of the data sets will convert the
application data in its cipher form and the attackers will not be able to decrypt the data
without the secret key. The attackers will not be able to decrypt these data sets and the data
loss and breaching of the data sets will be avoided (Neelima and Brinda 2018).
Access control is the third mechanism that shall be used. The risk treatment involved the use
of role-based access control along with access control lists for preventing the risks. The users
shall be provided with the data permissions on the basis of their role. For example, the
employees of the organization will be provided with the data access on the basis of their roles
(Franqueira and Wieringa 2012). The permissions provided to the Database Administrator
will be different from that of the analyst and likewise. There shall also be use of access
control lists that shall be used to avoid the attacks.
All of these three treatment methods will be acceptable as they will be able to control and
mitigate the risks.
Residual Risk
The residual risk table after the implementation of the above treatment methods are included
in the table below.
Risk ID Risk Name Likelihood Consequence Risk Rating
1 Malware Attacks Unlikely Moderate Moderate
2 Insider Threats Unlikely Major Moderate
3 Data Breaches Unlikely Moderate Moderate
4 Data Loss Unlikely Moderate Moderate
5 Denial of Service
Attacks
Possible Moderate Moderate
6 Network Security
Attacks
Unlikely Moderate Moderate
7 User Awareness Issues Possible Major High
7
Project Risk Management
The likelihood and consequence levels of all the risks will reduce after the implementation of
the treatment methods. However, there are residual risks that may remain after the
implementation of the treatment measures. This is because there will be changes in
technology that will occur and may be utilized by the attackers even after the implementation
of the treatment methods. Therefore, the possibility of these risks cannot be completely
eliminated from the project.
Secondary Risk
One secondary risk that may occur after the treatment of the risk may be cryptanalysis
attacks. These are the forms of information security attacks in which the attackers analyse
and identify the encryption algorithms being applied. These algorithms and the codes
implemented are identified by the attackers to violate the same (Xu et al. 2014).
The prolonged use of the same encryption algorithms by the attackers may provide the
attackers with the ability to analyse the algorithms and the patterns used. This may lead to the
inability to protect the data sets using encryption as the method.
The risk can be treated using multi-path encryption protocols which will reduce the attack
window and attack surface.
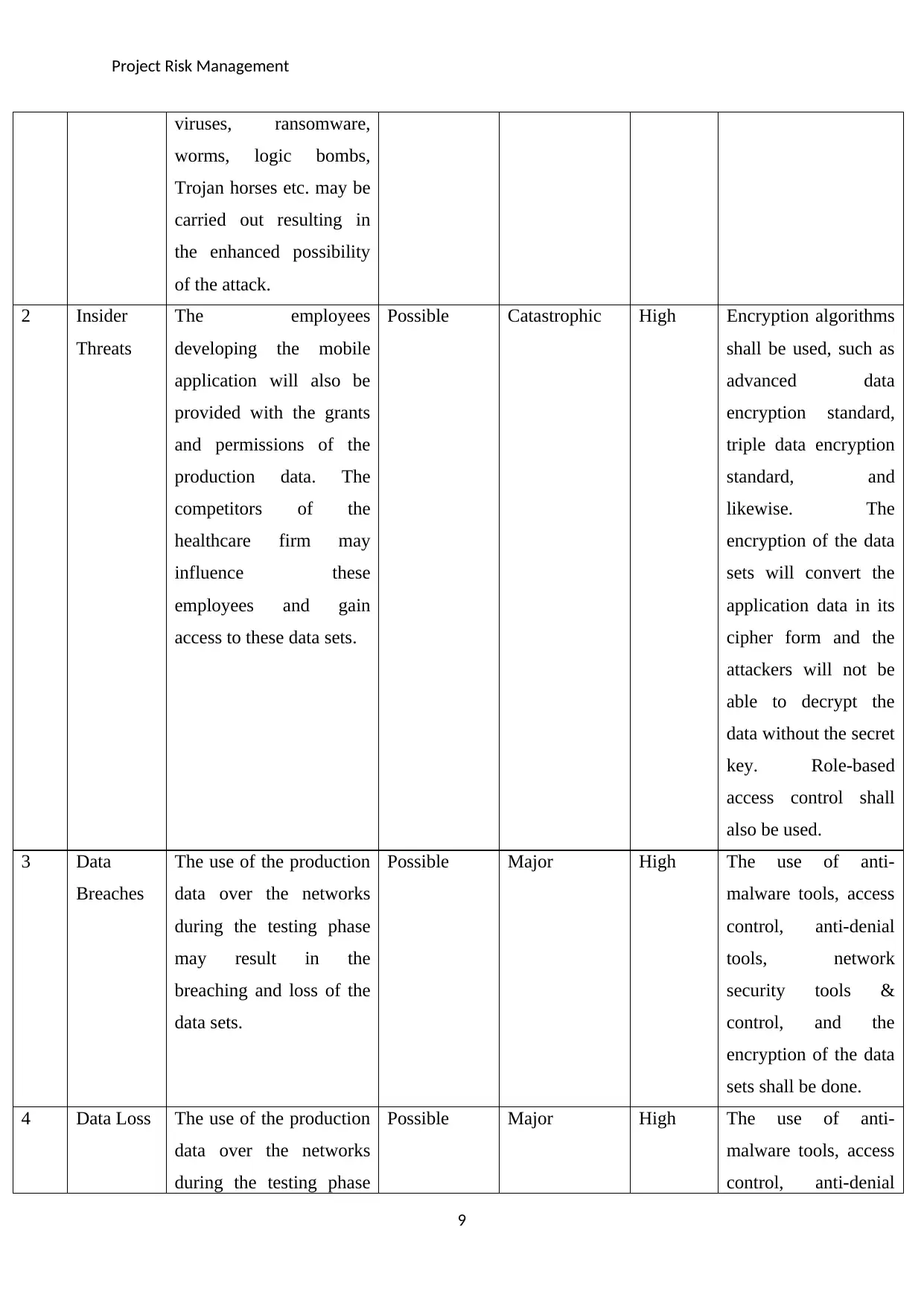
Risk Register
Risk
ID
Risk
Name
Description Likelihood Consequence Risk
Rating
Risk Treatment
Strategy
1 Malware
Attacks
The first form of
information security
attack that may occur in
this risk event is malware
threats and attacks. These
are the attacks in which
the malicious codes and
software may be used to
impact the information
privacy, confidentiality,
and availability. The
malware attacks, such as
Possible Major High Risk avoidance and
mitigation shall be
done with the
implementation of the
anti-malware tools
that will detect the
malware attempts
made by the attackers.
8
The likelihood and consequence levels of all the risks will reduce after the implementation of
the treatment methods. However, there are residual risks that may remain after the
implementation of the treatment measures. This is because there will be changes in
technology that will occur and may be utilized by the attackers even after the implementation
of the treatment methods. Therefore, the possibility of these risks cannot be completely
eliminated from the project.
Secondary Risk
One secondary risk that may occur after the treatment of the risk may be cryptanalysis
attacks. These are the forms of information security attacks in which the attackers analyse
and identify the encryption algorithms being applied. These algorithms and the codes
implemented are identified by the attackers to violate the same (Xu et al. 2014).
The prolonged use of the same encryption algorithms by the attackers may provide the
attackers with the ability to analyse the algorithms and the patterns used. This may lead to the
inability to protect the data sets using encryption as the method.
The risk can be treated using multi-path encryption protocols which will reduce the attack
window and attack surface.
Risk Register
Risk
ID
Risk
Name
Description Likelihood Consequence Risk
Rating
Risk Treatment
Strategy
1 Malware
Attacks
The first form of
information security
attack that may occur in
this risk event is malware
threats and attacks. These
are the attacks in which
the malicious codes and
software may be used to
impact the information
privacy, confidentiality,
and availability. The
malware attacks, such as
Possible Major High Risk avoidance and
mitigation shall be
done with the
implementation of the
anti-malware tools
that will detect the
malware attempts
made by the attackers.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
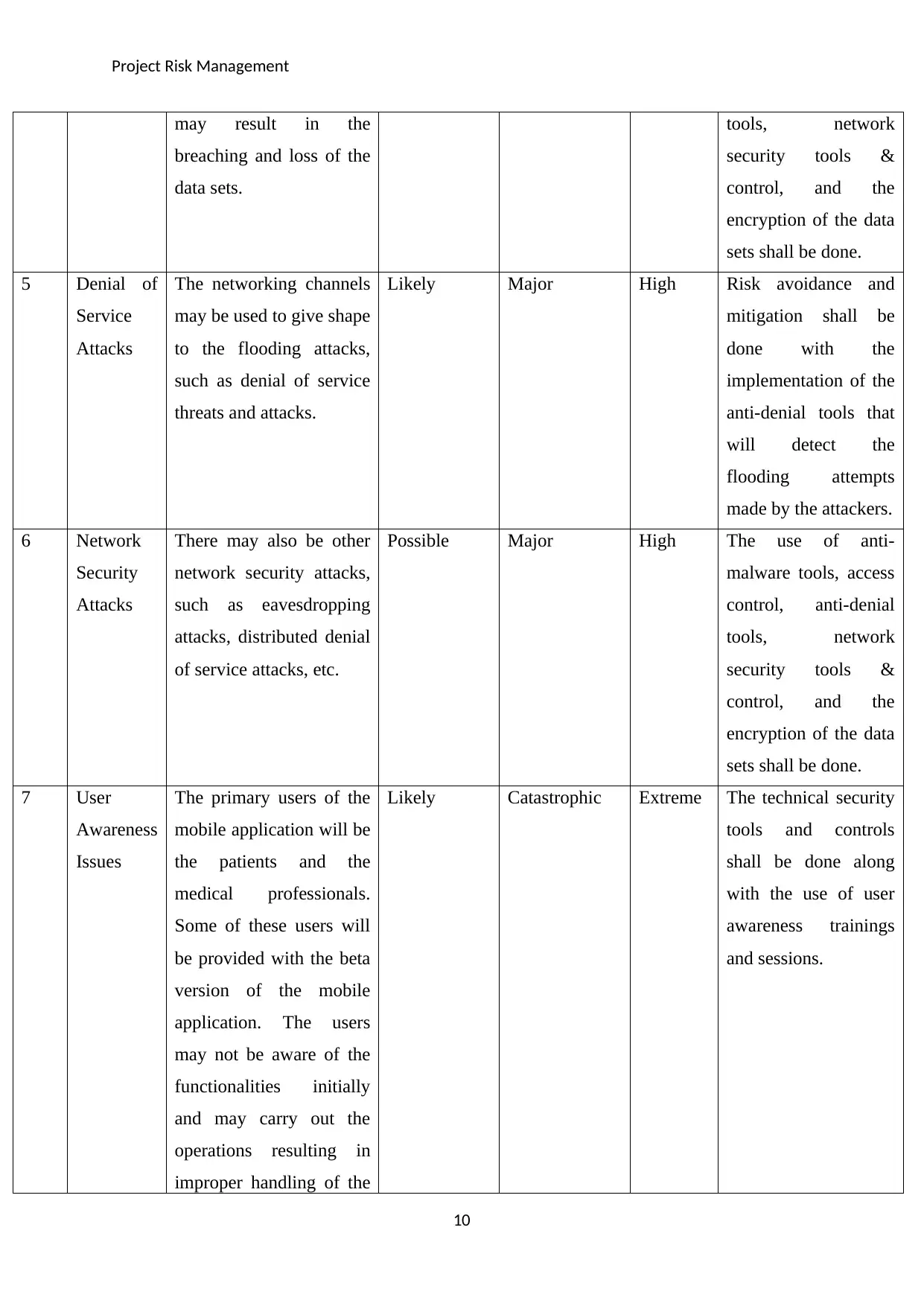
Project Risk Management
viruses, ransomware,
worms, logic bombs,
Trojan horses etc. may be
carried out resulting in
the enhanced possibility
of the attack.
2 Insider
Threats
The employees
developing the mobile
application will also be
provided with the grants
and permissions of the
production data. The
competitors of the
healthcare firm may
influence these
employees and gain
access to these data sets.
Possible Catastrophic High Encryption algorithms
shall be used, such as
advanced data
encryption standard,
triple data encryption
standard, and
likewise. The
encryption of the data
sets will convert the
application data in its
cipher form and the
attackers will not be
able to decrypt the
data without the secret
key. Role-based
access control shall
also be used.
3 Data
Breaches
The use of the production
data over the networks
during the testing phase
may result in the
breaching and loss of the
data sets.
Possible Major High The use of anti-
malware tools, access
control, anti-denial
tools, network
security tools &
control, and the
encryption of the data
sets shall be done.
4 Data Loss The use of the production
data over the networks
during the testing phase
Possible Major High The use of anti-
malware tools, access
control, anti-denial
9
viruses, ransomware,
worms, logic bombs,
Trojan horses etc. may be
carried out resulting in
the enhanced possibility
of the attack.
2 Insider
Threats
The employees
developing the mobile
application will also be
provided with the grants
and permissions of the
production data. The
competitors of the
healthcare firm may
influence these
employees and gain
access to these data sets.
Possible Catastrophic High Encryption algorithms
shall be used, such as
advanced data
encryption standard,
triple data encryption
standard, and
likewise. The
encryption of the data
sets will convert the
application data in its
cipher form and the
attackers will not be
able to decrypt the
data without the secret
key. Role-based
access control shall
also be used.
3 Data
Breaches
The use of the production
data over the networks
during the testing phase
may result in the
breaching and loss of the
data sets.
Possible Major High The use of anti-
malware tools, access
control, anti-denial
tools, network
security tools &
control, and the
encryption of the data
sets shall be done.
4 Data Loss The use of the production
data over the networks
during the testing phase
Possible Major High The use of anti-
malware tools, access
control, anti-denial
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project Risk Management
may result in the
breaching and loss of the
data sets.
tools, network
security tools &
control, and the
encryption of the data
sets shall be done.
5 Denial of
Service
Attacks
The networking channels
may be used to give shape
to the flooding attacks,
such as denial of service
threats and attacks.
Likely Major High Risk avoidance and
mitigation shall be
done with the
implementation of the
anti-denial tools that
will detect the
flooding attempts
made by the attackers.
6 Network
Security
Attacks
There may also be other
network security attacks,
such as eavesdropping
attacks, distributed denial
of service attacks, etc.
Possible Major High The use of anti-
malware tools, access
control, anti-denial
tools, network
security tools &
control, and the
encryption of the data
sets shall be done.
7 User
Awareness
Issues
The primary users of the
mobile application will be
the patients and the
medical professionals.
Some of these users will
be provided with the beta
version of the mobile
application. The users
may not be aware of the
functionalities initially
and may carry out the
operations resulting in
improper handling of the
Likely Catastrophic Extreme The technical security
tools and controls
shall be done along
with the use of user
awareness trainings
and sessions.
10
may result in the
breaching and loss of the
data sets.
tools, network
security tools &
control, and the
encryption of the data
sets shall be done.
5 Denial of
Service
Attacks
The networking channels
may be used to give shape
to the flooding attacks,
such as denial of service
threats and attacks.
Likely Major High Risk avoidance and
mitigation shall be
done with the
implementation of the
anti-denial tools that
will detect the
flooding attempts
made by the attackers.
6 Network
Security
Attacks
There may also be other
network security attacks,
such as eavesdropping
attacks, distributed denial
of service attacks, etc.
Possible Major High The use of anti-
malware tools, access
control, anti-denial
tools, network
security tools &
control, and the
encryption of the data
sets shall be done.
7 User
Awareness
Issues
The primary users of the
mobile application will be
the patients and the
medical professionals.
Some of these users will
be provided with the beta
version of the mobile
application. The users
may not be aware of the
functionalities initially
and may carry out the
operations resulting in
improper handling of the
Likely Catastrophic Extreme The technical security
tools and controls
shall be done along
with the use of user
awareness trainings
and sessions.
10

Project Risk Management
data sets.
Reflection
Critical Analysis
Risk management is one of the critical territories under project management. A risk is
characterized as an occasion that may affect the undertaking advancement, activities, and its
components and the idea of the effects might be positive or negative. The event of the risks
amid the venture course of events may adjust the decided dimensions of extension, expenses,
and calendar that may affect the customer fulfilment levels too. There are additionally
different conceivable ramifications of these risks and it is, in this way, fundamental that the
management of the risks is done satisfactorily. The risk management is likewise, included as
one of the critical regions under a larger part of the venture management strategies. The
report covers the risk management for one of the tasks. The undertaking is a progressing
venture which includes the advancement of a versatile application for the representatives of
the healthcare firm. The versatile application is to be created for the Android and iOS stages
and it will incorporate the primary modules as client login, patient information records,
information investigation, medical reports, and information sharing. It will enable the doctors
and nursing staff to monitor the patient information and dissect the equivalent to decide
designs for improved medical analysis and detailing. Information sharing will likewise be
conceivable between the medical experts and the patients through the application (Dey and
Kinch 2008).
One of the risks that occurred in this project was schedule overrun. It was because there were
various changes that were requested by the project sponsor during the entire timeline of the
project. The requirements and scope of the project was defined and estimated in the initial
project phases. The project sponsor and client requested the changes in the application
modules, user interface, and specifications during the entire timeline of the project. This
resulted in the delay in the delivery of the project deliverables and resulted in the overrun of
the schedule during the execution phase (Javaid 2013).
The risk control and treatment process that was used in this phase was risk avoidance and
mitigation. The use of change control and management was used as the treatment strategy.
The process included the change handling process as change identification, approval of the
11
data sets.
Reflection
Critical Analysis
Risk management is one of the critical territories under project management. A risk is
characterized as an occasion that may affect the undertaking advancement, activities, and its
components and the idea of the effects might be positive or negative. The event of the risks
amid the venture course of events may adjust the decided dimensions of extension, expenses,
and calendar that may affect the customer fulfilment levels too. There are additionally
different conceivable ramifications of these risks and it is, in this way, fundamental that the
management of the risks is done satisfactorily. The risk management is likewise, included as
one of the critical regions under a larger part of the venture management strategies. The
report covers the risk management for one of the tasks. The undertaking is a progressing
venture which includes the advancement of a versatile application for the representatives of
the healthcare firm. The versatile application is to be created for the Android and iOS stages
and it will incorporate the primary modules as client login, patient information records,
information investigation, medical reports, and information sharing. It will enable the doctors
and nursing staff to monitor the patient information and dissect the equivalent to decide
designs for improved medical analysis and detailing. Information sharing will likewise be
conceivable between the medical experts and the patients through the application (Dey and
Kinch 2008).
One of the risks that occurred in this project was schedule overrun. It was because there were
various changes that were requested by the project sponsor during the entire timeline of the
project. The requirements and scope of the project was defined and estimated in the initial
project phases. The project sponsor and client requested the changes in the application
modules, user interface, and specifications during the entire timeline of the project. This
resulted in the delay in the delivery of the project deliverables and resulted in the overrun of
the schedule during the execution phase (Javaid 2013).
The risk control and treatment process that was used in this phase was risk avoidance and
mitigation. The use of change control and management was used as the treatment strategy.
The process included the change handling process as change identification, approval of the
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





