Year 1 Data Communication Report: Bluetooth Networking Overview
VerifiedAdded on 2023/04/17
|9
|1841
|350
Report
AI Summary
This report provides a comprehensive overview of Bluetooth networking, a short-range wireless communication technology. It begins with an introduction to Bluetooth, followed by an explanation of its technology architecture, including the roles of master and slave radios, piconets, and scatter-nets. The report then delves into the security aspects of Bluetooth, discussing various security modes and vulnerabilities such as Blueborne, Bluebugging, Bluejacking, and Bluesnarfing. Application areas of Bluetooth, including data and voice access points, cable replacement, and ad-hoc networking, are also covered. Furthermore, the report outlines the pros and cons of Bluetooth networking, highlighting its ease of use and energy efficiency alongside its limited range and slower transmission rate compared to other technologies. The report concludes by summarizing the key aspects of Bluetooth networking, emphasizing its significance in modern data communication and the ongoing challenges related to security.
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Bluetooth Networking
Data Communication & Network Routing
3/25/2019
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Bluetooth Networking
Data Communication & Network Routing
3/25/2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Bluetooth Networking
Table of Contents
Bluetooth Networking - Introduction.....................................................................................................2
Technology Architecture.......................................................................................................................2
Bluetooth Networking Security.............................................................................................................4
Application Areas..................................................................................................................................5
Pros & Cons..........................................................................................................................................6
Conclusion.............................................................................................................................................6
References.............................................................................................................................................8
1
Table of Contents
Bluetooth Networking - Introduction.....................................................................................................2
Technology Architecture.......................................................................................................................2
Bluetooth Networking Security.............................................................................................................4
Application Areas..................................................................................................................................5
Pros & Cons..........................................................................................................................................6
Conclusion.............................................................................................................................................6
References.............................................................................................................................................8
1

Bluetooth Networking
Bluetooth Networking - Introduction
Communication and networking has become an essential requirement for the business firms
and the individuals in the present times. There are various technologies that have been
developed that provide the ability to carry out short-range and wide-range communications &
networking.
Bluetooth Networking is one such technology which comes under the category of radio
communication technology. The technology provides the ability to carry out low-power and
short distance wireless networking. It can be conducted using phones, computer systems, and
several other networking devices (Kaur, 2016). The details about the architecture and
working mechanism of the technology, application areas, security aspect, and pros & cons are
covered in the further sections.
Technology Architecture
The communication and networking activities in Bluetooth Networking take place between a
master radio and a slave radio. These radios involved in the Bluetooth communication
architecture are symmetric in nature. As per the architecture, same device may be used to act
as a master radio and the same device can act as a slave radio. The recognition of the devices
is done using a 48-bit unique device address. The address for the device is fixed and cannot
be changed. The inter-connection of two or more such devices leads to the development of an
ad-hoc network which is termed as piconets. The units involved in a piconet share the same
channel. The total number of slaves that may remain active at one instance shall not be more
than seven. The devices active in a piconet are recognized using a three-bit device address.
There may also be inactive slaves that may also remain within the piconet. Master radio is the
one that initiates the communication link. As soon as a link is established, the slaves are
provided with the capability to request the master/slave switch to make it the master. Direct
communication between the slaves in the Bluetooth communication is not allowed. In the
piconet, it is also necessary that all the slaves synchronize their internal clocks and frequency
hops as per the master. The hopping sequence followed by one piconet shall differ from the
other (Pandya, Desai and Merchant, 2013). The radio devices involved make use of Time
Division Multiplexing (TDM). The transmission by the master device is done on even
number slots and the odd-numbered slots are used by the slaves.
2
Bluetooth Networking - Introduction
Communication and networking has become an essential requirement for the business firms
and the individuals in the present times. There are various technologies that have been
developed that provide the ability to carry out short-range and wide-range communications &
networking.
Bluetooth Networking is one such technology which comes under the category of radio
communication technology. The technology provides the ability to carry out low-power and
short distance wireless networking. It can be conducted using phones, computer systems, and
several other networking devices (Kaur, 2016). The details about the architecture and
working mechanism of the technology, application areas, security aspect, and pros & cons are
covered in the further sections.
Technology Architecture
The communication and networking activities in Bluetooth Networking take place between a
master radio and a slave radio. These radios involved in the Bluetooth communication
architecture are symmetric in nature. As per the architecture, same device may be used to act
as a master radio and the same device can act as a slave radio. The recognition of the devices
is done using a 48-bit unique device address. The address for the device is fixed and cannot
be changed. The inter-connection of two or more such devices leads to the development of an
ad-hoc network which is termed as piconets. The units involved in a piconet share the same
channel. The total number of slaves that may remain active at one instance shall not be more
than seven. The devices active in a piconet are recognized using a three-bit device address.
There may also be inactive slaves that may also remain within the piconet. Master radio is the
one that initiates the communication link. As soon as a link is established, the slaves are
provided with the capability to request the master/slave switch to make it the master. Direct
communication between the slaves in the Bluetooth communication is not allowed. In the
piconet, it is also necessary that all the slaves synchronize their internal clocks and frequency
hops as per the master. The hopping sequence followed by one piconet shall differ from the
other (Pandya, Desai and Merchant, 2013). The radio devices involved make use of Time
Division Multiplexing (TDM). The transmission by the master device is done on even
number slots and the odd-numbered slots are used by the slaves.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Bluetooth Networking
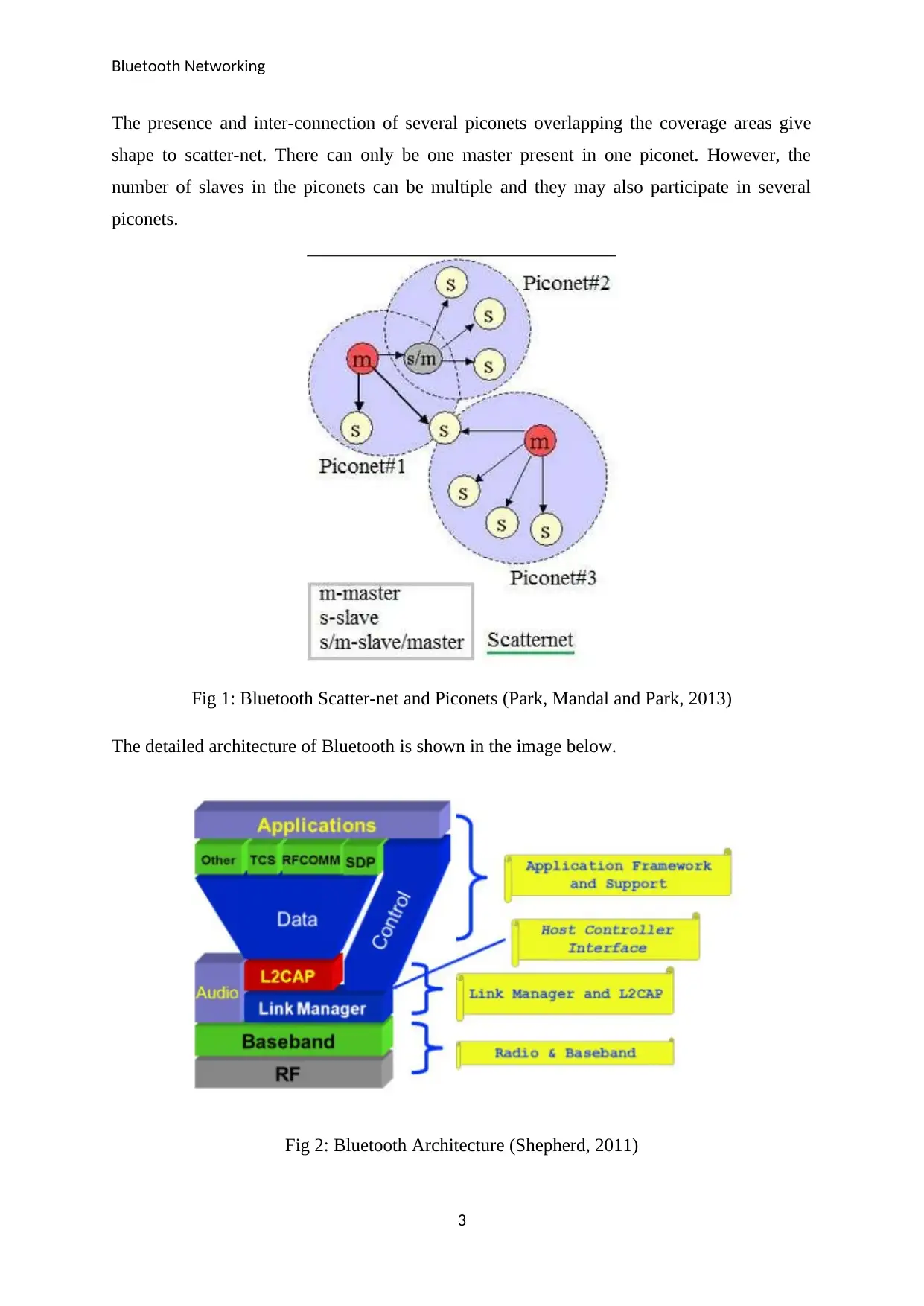
The presence and inter-connection of several piconets overlapping the coverage areas give
shape to scatter-net. There can only be one master present in one piconet. However, the
number of slaves in the piconets can be multiple and they may also participate in several
piconets.
Fig 1: Bluetooth Scatter-net and Piconets (Park, Mandal and Park, 2013)
The detailed architecture of Bluetooth is shown in the image below.
Fig 2: Bluetooth Architecture (Shepherd, 2011)
3
The presence and inter-connection of several piconets overlapping the coverage areas give
shape to scatter-net. There can only be one master present in one piconet. However, the
number of slaves in the piconets can be multiple and they may also participate in several
piconets.
Fig 1: Bluetooth Scatter-net and Piconets (Park, Mandal and Park, 2013)
The detailed architecture of Bluetooth is shown in the image below.
Fig 2: Bluetooth Architecture (Shepherd, 2011)
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Bluetooth Networking
There are several layers and protocols that are present in the Bluetooth architecture as shown
in the image above. The radio transmission is conducted at the radio layer and it is equivalent
to the physical layer in the OSI model. The layer above is the baseband layer in which the
master and slave slots communicate with each other (Cordeiro, Abhyankar and Agrawal,
2012). The logic control and link layer is then included and the quality of services is ensured
by the control layer.
Fig 3: Bluetooth Frame Format (Mohamed et al., 2008)
There are various fields that are involved in the Bluetooth frame which is as shown in the
image above.
Bluetooth Networking Security
There are different security modes offered by Bluetooth networking. Also, there are
Bluetooth-enabled devices that are developed and the security mode to be implemented in
these gadgets is the decision of the manufacturer. The Bluetooth users are provided with the
ability to establish trusted devices that have the ability to exchange the data sets without
acquiring permissions. The request from the other Bluetooth-enabled device requesting to
form a connection with other device is also handled by the device owner. The acceptance or
rejection of this request can be done.
4
There are several layers and protocols that are present in the Bluetooth architecture as shown
in the image above. The radio transmission is conducted at the radio layer and it is equivalent
to the physical layer in the OSI model. The layer above is the baseband layer in which the
master and slave slots communicate with each other (Cordeiro, Abhyankar and Agrawal,
2012). The logic control and link layer is then included and the quality of services is ensured
by the control layer.
Fig 3: Bluetooth Frame Format (Mohamed et al., 2008)
There are various fields that are involved in the Bluetooth frame which is as shown in the
image above.
Bluetooth Networking Security
There are different security modes offered by Bluetooth networking. Also, there are
Bluetooth-enabled devices that are developed and the security mode to be implemented in
these gadgets is the decision of the manufacturer. The Bluetooth users are provided with the
ability to establish trusted devices that have the ability to exchange the data sets without
acquiring permissions. The request from the other Bluetooth-enabled device requesting to
form a connection with other device is also handled by the device owner. The acceptance or
rejection of this request can be done.
4

Bluetooth Networking
There is service-level and device-level security integrated in Bluetooth networking to make
sure that the unauthorized data transmissions are prevented. Some of the security methods
that are included comprise of authorization and access control mechanisms that put
restrictions on the utilization of the Bluetooth services for the registered users. The users are
required to make conscious decisions in such cases to entertain the request from the other
user or not. The user also has the option to switch the discovery mode to on or off as per the
need. If the user selects the non-discoverable mode, then the other users in the proximity will
not be able to connect with the device and services.
There are; however, some of the security vulnerabilities that the Bluetooth networks and
devices are exposed to. Blueborne is one of the attack vectors that were identified in the year
2017. The attackers could launch man in the middle attacks or take control of the device
using this attack mechanism and it did not ask for pairing as well. Bluebugging is a similar
form of the attack in which the control is taken without the user’s knowledge (Hassan et al.,
2018). Once the malicious entities succeed in gaining access to the device, they may gain
control over the device and access sensitive information of the user. Bluejacking and
Bluesnarfing are also the two forms of security attacks that may provide unauthorized access
to the attackers.
Application Areas
Bluetooth networking is a technology that can be used in a number of different areas. There
are essentially three such application areas that have been developed.
The first application area is data and voice access points. The technology facilitates
real-time transmission of data and voice and makes sure that the portable connection
of the devices is enabled.
Cable replacement is the second area of application that is associated with the
technology. The technology eliminates the requirement of several cables for
establishing the communication connections. Thus, the technology is used in the
workplaces and at homes for the transmission of the data.
Ad-hoc networking is another application area that comes with the technology. There
is no requirement of any infrastructure or implementations to be done in advance to
make use of the technology. The users can establish ad-hoc networking connections
5
There is service-level and device-level security integrated in Bluetooth networking to make
sure that the unauthorized data transmissions are prevented. Some of the security methods
that are included comprise of authorization and access control mechanisms that put
restrictions on the utilization of the Bluetooth services for the registered users. The users are
required to make conscious decisions in such cases to entertain the request from the other
user or not. The user also has the option to switch the discovery mode to on or off as per the
need. If the user selects the non-discoverable mode, then the other users in the proximity will
not be able to connect with the device and services.
There are; however, some of the security vulnerabilities that the Bluetooth networks and
devices are exposed to. Blueborne is one of the attack vectors that were identified in the year
2017. The attackers could launch man in the middle attacks or take control of the device
using this attack mechanism and it did not ask for pairing as well. Bluebugging is a similar
form of the attack in which the control is taken without the user’s knowledge (Hassan et al.,
2018). Once the malicious entities succeed in gaining access to the device, they may gain
control over the device and access sensitive information of the user. Bluejacking and
Bluesnarfing are also the two forms of security attacks that may provide unauthorized access
to the attackers.
Application Areas
Bluetooth networking is a technology that can be used in a number of different areas. There
are essentially three such application areas that have been developed.
The first application area is data and voice access points. The technology facilitates
real-time transmission of data and voice and makes sure that the portable connection
of the devices is enabled.
Cable replacement is the second area of application that is associated with the
technology. The technology eliminates the requirement of several cables for
establishing the communication connections. Thus, the technology is used in the
workplaces and at homes for the transmission of the data.
Ad-hoc networking is another application area that comes with the technology. There
is no requirement of any infrastructure or implementations to be done in advance to
make use of the technology. The users can establish ad-hoc networking connections
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Bluetooth Networking
using the Bluetooth-enabled gadgets and can utilize the same for data exchange and
communication purposes (Vergetis et al., 2014).
Pros & Cons
There are various advantages and disadvantages of Bluetooth networking that are present.
Some of these advantages include:
The wireless transmission of data is possible with the aid of the technology. There is a
wireless personal area network developed with the aid of the technology that can
allow the transmission of the data and files from one device to the other. There are no
connections required and the technology is mobile in nature. Therefore, the users get
the flexibility to use the technology on the move.
The pairing of the devices to make use of the Bluetooth networking and data
communication services is very easy. The users can pair the devices and share
information with just one click (Deb and Sinha, 2014).
The technology is also energy efficient in nature and therefore, the further benefits of
wireless data transmission are provided by the technology.
There are also a few disadvantages that are associated with the Bluetooth networking.
There is only a limited range that is supported by the Bluetooth networks and
services. The technology does not offer long-distance communication and sharing.
This may lead to the limited preference of the technology by the users.
The transmission rate offered by the technology is slower than the other hardware
interfacing technologies. For example, average transmission rate offered by Bluetooth
4.0 is 24 Mbps while the transmission rate provided by Wi-Fi Direct is 250 Mbps.
There is a huge difference in the transmission rate.
There are certain security vulnerabilities associated with the Bluetooth networks and
services. The utilization of these vulnerabilities by the malicious entities may give rise
to the security threats and attacks (Musale and Apte, 2012).
Conclusion
Bluetooth Networking comes under the category of radio communication technology. The
technology provides the ability to carry out low-power and short distance wireless
networking. It can be conducted using phones, computer systems, and several other
6
using the Bluetooth-enabled gadgets and can utilize the same for data exchange and
communication purposes (Vergetis et al., 2014).
Pros & Cons
There are various advantages and disadvantages of Bluetooth networking that are present.
Some of these advantages include:
The wireless transmission of data is possible with the aid of the technology. There is a
wireless personal area network developed with the aid of the technology that can
allow the transmission of the data and files from one device to the other. There are no
connections required and the technology is mobile in nature. Therefore, the users get
the flexibility to use the technology on the move.
The pairing of the devices to make use of the Bluetooth networking and data
communication services is very easy. The users can pair the devices and share
information with just one click (Deb and Sinha, 2014).
The technology is also energy efficient in nature and therefore, the further benefits of
wireless data transmission are provided by the technology.
There are also a few disadvantages that are associated with the Bluetooth networking.
There is only a limited range that is supported by the Bluetooth networks and
services. The technology does not offer long-distance communication and sharing.
This may lead to the limited preference of the technology by the users.
The transmission rate offered by the technology is slower than the other hardware
interfacing technologies. For example, average transmission rate offered by Bluetooth
4.0 is 24 Mbps while the transmission rate provided by Wi-Fi Direct is 250 Mbps.
There is a huge difference in the transmission rate.
There are certain security vulnerabilities associated with the Bluetooth networks and
services. The utilization of these vulnerabilities by the malicious entities may give rise
to the security threats and attacks (Musale and Apte, 2012).
Conclusion
Bluetooth Networking comes under the category of radio communication technology. The
technology provides the ability to carry out low-power and short distance wireless
networking. It can be conducted using phones, computer systems, and several other
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Bluetooth Networking
networking devices. The communication and networking activities in Bluetooth Networking
take place between a master radio and a slave radio. These radios involved in the Bluetooth
communication architecture are symmetric in nature. There are; however, some of the
security vulnerabilities that the Bluetooth networks and devices are exposed to. Blueborne is
one of the attack vectors that were identified in the year 2017. The attackers could launch
man in the middle attacks or take control of the device using this attack mechanism and it did
not ask for pairing as well. Bluebugging, Bluesnarfing, and Bluejacking are the other security
attacks that may occur. The pairing of the devices to make use of the Bluetooth networking
and data communication services is very easy. The users can pair the devices and share
information with just one click. There is only a limited range that is supported by the
Bluetooth networks and services. The technology does not offer long-distance
communication and sharing. This may lead to the limited preference of the technology by the
users.
7
networking devices. The communication and networking activities in Bluetooth Networking
take place between a master radio and a slave radio. These radios involved in the Bluetooth
communication architecture are symmetric in nature. There are; however, some of the
security vulnerabilities that the Bluetooth networks and devices are exposed to. Blueborne is
one of the attack vectors that were identified in the year 2017. The attackers could launch
man in the middle attacks or take control of the device using this attack mechanism and it did
not ask for pairing as well. Bluebugging, Bluesnarfing, and Bluejacking are the other security
attacks that may occur. The pairing of the devices to make use of the Bluetooth networking
and data communication services is very easy. The users can pair the devices and share
information with just one click. There is only a limited range that is supported by the
Bluetooth networks and services. The technology does not offer long-distance
communication and sharing. This may lead to the limited preference of the technology by the
users.
7

Bluetooth Networking
References
Cordeiro, C., Abhyankar, S. and Agrawal, D. (2012). An enhanced and energy efficient
communication architecture for Bluetooth wireless PANs. Ad Hoc Networks, 3(2), pp.119-
140.
Deb, A. and Sinha, S. (2014). Bluetooth Messenger: an Android Messenger app based on
Bluetooth Connectivity. IOSR Journal of Computer Engineering, 16(3), pp.61-66.
Hassan, S., Bibon, S., Hossain, M. and Atiquzzaman, M. (2018). Security threats in Bluetooth
technology. Computers & Security, 74, pp.308-322.
Kaur, J. (2016). Bluetooth Technology. International Journal Of Engineering And Computer
Science.
Mohamed, M., Abu El-Azm, A., El-Fishawy, N., El-Tokhy, M. and Abd El-Samie, F. (2008).
Optimization of Bluetooth Frame Format for Efficient Performance. Progress In
Electromagnetics Research M, 1, pp.101-110.
Musale, V. and Apte, S. (2012). Security Risks in Bluetooth Devices. International Journal
of Computer Applications, 51(1), pp.1-6.
Pandya, U., Desai, U. and Merchant, S. (2013). Realization of Bluetooth piconet for real time
monitoring of multiple parameters. Biomedical Engineering Letters, 3(2), pp.95-101.
Park, N., Mandal, B. and Park, Y. (2013). Sensor Protocol for Roaming Bluetooth Multiagent
Systems. International Journal of Distributed Sensor Networks, 9(4), p.963508.
Shepherd, R. (2011). Bluetooth wireless technology in the home. Electronics &
Communication Engineering Journal, 13(5), pp.195-203.
Vergetis, E., Guerin, R., Sarkar, S. and Rank, J. (2014). Can Bluetooth succeed as a large-
scale ad hoc networking technology?. IEEE Journal on Selected Areas in Communications,
23(3), pp.644-656.
8
References
Cordeiro, C., Abhyankar, S. and Agrawal, D. (2012). An enhanced and energy efficient
communication architecture for Bluetooth wireless PANs. Ad Hoc Networks, 3(2), pp.119-
140.
Deb, A. and Sinha, S. (2014). Bluetooth Messenger: an Android Messenger app based on
Bluetooth Connectivity. IOSR Journal of Computer Engineering, 16(3), pp.61-66.
Hassan, S., Bibon, S., Hossain, M. and Atiquzzaman, M. (2018). Security threats in Bluetooth
technology. Computers & Security, 74, pp.308-322.
Kaur, J. (2016). Bluetooth Technology. International Journal Of Engineering And Computer
Science.
Mohamed, M., Abu El-Azm, A., El-Fishawy, N., El-Tokhy, M. and Abd El-Samie, F. (2008).
Optimization of Bluetooth Frame Format for Efficient Performance. Progress In
Electromagnetics Research M, 1, pp.101-110.
Musale, V. and Apte, S. (2012). Security Risks in Bluetooth Devices. International Journal
of Computer Applications, 51(1), pp.1-6.
Pandya, U., Desai, U. and Merchant, S. (2013). Realization of Bluetooth piconet for real time
monitoring of multiple parameters. Biomedical Engineering Letters, 3(2), pp.95-101.
Park, N., Mandal, B. and Park, Y. (2013). Sensor Protocol for Roaming Bluetooth Multiagent
Systems. International Journal of Distributed Sensor Networks, 9(4), p.963508.
Shepherd, R. (2011). Bluetooth wireless technology in the home. Electronics &
Communication Engineering Journal, 13(5), pp.195-203.
Vergetis, E., Guerin, R., Sarkar, S. and Rank, J. (2014). Can Bluetooth succeed as a large-
scale ad hoc networking technology?. IEEE Journal on Selected Areas in Communications,
23(3), pp.644-656.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
