Ransomware Attack: Operation, Impact, WannaCry Case, and Mitigation
VerifiedAdded on 2022/12/30
|13
|2416
|74
Report
AI Summary
This report provides a comprehensive analysis of ransomware attacks, detailing their operational mechanisms, real-world impact, and effective mitigation strategies. It begins with an introduction to cybersecurity and malware, defining ransomware as a type of malware that causes cyber extortion. The report then walks through the operation of ransomware, including installation, communication, handshake, encryption, and extortion phases. A case study of the WannaCry ransomware attack is presented, examining its mode of operation, the security breach, its impact on various sectors, and the actions that should be taken to address the issue. The report emphasizes the importance of updating systems, closing exploited ports, backing up data, and patching vulnerabilities to prevent ransomware attacks. The conclusion stresses the need for organizations to proactively enhance their security measures to combat the evolving landscape of cyber threats.

Running head: RANSOMWARE ATTACK AND ITS IMPACT
Ransomware Attack and its Impact
Name of the student:
Name of the university:
Author note:
Ransomware Attack and its Impact
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RANSOMWARE ATTACK AND ITS IMPACT
Table of Contents
Introduction:....................................................................................................................................2
Discussion:.......................................................................................................................................2
Walkthrough on the operation of Ransomware Attack:..............................................................3
Behind the scene of Ransomware Attack:...................................................................................5
Mode of operation of Ransomware in the real world:.................................................................6
Outcome and Impact of the WannaCry Ransomware:................................................................7
Aim of Security that was breached and it is resulting consequences:.........................................7
Victim responsible for the attack:................................................................................................8
Action that should be taken to address the issue:........................................................................8
Conclusion:..................................................................................................................................8
References:....................................................................................................................................10
Bibliography:.................................................................................................................................11
Table of Contents
Introduction:....................................................................................................................................2
Discussion:.......................................................................................................................................2
Walkthrough on the operation of Ransomware Attack:..............................................................3
Behind the scene of Ransomware Attack:...................................................................................5
Mode of operation of Ransomware in the real world:.................................................................6
Outcome and Impact of the WannaCry Ransomware:................................................................7
Aim of Security that was breached and it is resulting consequences:.........................................7
Victim responsible for the attack:................................................................................................8
Action that should be taken to address the issue:........................................................................8
Conclusion:..................................................................................................................................8
References:....................................................................................................................................10
Bibliography:.................................................................................................................................11

2RANSOMWARE ATTACK AND ITS IMPACT
Introduction:
Cybersecurity is often denoted to as the grouping of technologies and practices associated
to it to protect network, devices, information and plans from the attack of unauthorized accesses.
With the gradual advancement of information technology, the rise of cyber-attacks is gradually
increasing, causing a breach of information of organization’s personal as well as sensitive data of
users in the course of dealing with business operations. Among the various types of cyber issues,
malware attacks are one of the significant kind responsible for all the types of cyber-attacks
taking place in the modern world. This report is hence prepared to reflect on the considerable
standards of malware attacks that are prevalent nowadays with special consideration to their
mode of operation and real-world case study based on the malware attack.
Discussion:
A malware attack is defined as the type of attack in the cyber world where malicious
activities are performed over software that is installed in the victim's computer without their
concern. Malware cyphers like Ransomware, spyware or adware are observed as impartial codes
or agendas that can be spread through other networks, producing them to implement on their
own. While injecting malware into the system, cybercriminals can access to any one's credential
account while stealing the victim’s data and causing damage to the entire system. Malware can
be of different types such as virus, worm, Trojan, Ransomware, Adware, Spyware and many
more. However, this report studies the major operation behind the particular kind of malware
attack that is the Ransomware Attack.
Introduction:
Cybersecurity is often denoted to as the grouping of technologies and practices associated
to it to protect network, devices, information and plans from the attack of unauthorized accesses.
With the gradual advancement of information technology, the rise of cyber-attacks is gradually
increasing, causing a breach of information of organization’s personal as well as sensitive data of
users in the course of dealing with business operations. Among the various types of cyber issues,
malware attacks are one of the significant kind responsible for all the types of cyber-attacks
taking place in the modern world. This report is hence prepared to reflect on the considerable
standards of malware attacks that are prevalent nowadays with special consideration to their
mode of operation and real-world case study based on the malware attack.
Discussion:
A malware attack is defined as the type of attack in the cyber world where malicious
activities are performed over software that is installed in the victim's computer without their
concern. Malware cyphers like Ransomware, spyware or adware are observed as impartial codes
or agendas that can be spread through other networks, producing them to implement on their
own. While injecting malware into the system, cybercriminals can access to any one's credential
account while stealing the victim’s data and causing damage to the entire system. Malware can
be of different types such as virus, worm, Trojan, Ransomware, Adware, Spyware and many
more. However, this report studies the major operation behind the particular kind of malware
attack that is the Ransomware Attack.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RANSOMWARE ATTACK AND ITS IMPACT
Walkthrough on the operation of Ransomware Attack:
Ransomware is defined as the type of malware that causes cyber extortion leading to
financial gain. Once Ransomware gets activated into the user’s system, it stops the operators
from opening their files or any type of application schemes until and unless a ransom is rewarded
in the form of Bitcoin (O'Gorman, Gavin and McDonald). Ransomware is mainly spread via
phishing emails comprising spiteful attachments that get activated when the user transfers that
link. When a user downloads a link containing malware unknowingly, the entire network gets
infected by the malware causing exploitation of the web servers that are connected to the system.
The entire operation of Ransomware attack takes place via five main stages, which includes:
1. Installation Phase: During the installation phase, the computer of the victim gets infected
at the initial stage where a ransomware gets installed within the system while setting up
the Windows Registry Key that gets automatically initiated each time when a user boots
up the computer system (Salvi, Harshada and Kerkar).
2. Communicating with the Headquarters: As soon as the Ransomware gets injected within
the system it starts its operation while contacting with the server of the headquarter via
the cyber criminals.
3. Handshake and Keys: In the next step, an authentication process known as handshake is
carried in between the ransomware client and the server of the system (Salvi, Harshada
and Kerkar). The entire process then generates two kinds of Cryptographic keys. One of
these cryptographic keys remains within the computer of the victim while another one
gets stored within the server owned by the cybercriminal.
Walkthrough on the operation of Ransomware Attack:
Ransomware is defined as the type of malware that causes cyber extortion leading to
financial gain. Once Ransomware gets activated into the user’s system, it stops the operators
from opening their files or any type of application schemes until and unless a ransom is rewarded
in the form of Bitcoin (O'Gorman, Gavin and McDonald). Ransomware is mainly spread via
phishing emails comprising spiteful attachments that get activated when the user transfers that
link. When a user downloads a link containing malware unknowingly, the entire network gets
infected by the malware causing exploitation of the web servers that are connected to the system.
The entire operation of Ransomware attack takes place via five main stages, which includes:
1. Installation Phase: During the installation phase, the computer of the victim gets infected
at the initial stage where a ransomware gets installed within the system while setting up
the Windows Registry Key that gets automatically initiated each time when a user boots
up the computer system (Salvi, Harshada and Kerkar).
2. Communicating with the Headquarters: As soon as the Ransomware gets injected within
the system it starts its operation while contacting with the server of the headquarter via
the cyber criminals.
3. Handshake and Keys: In the next step, an authentication process known as handshake is
carried in between the ransomware client and the server of the system (Salvi, Harshada
and Kerkar). The entire process then generates two kinds of Cryptographic keys. One of
these cryptographic keys remains within the computer of the victim while another one
gets stored within the server owned by the cybercriminal.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RANSOMWARE ATTACK AND ITS IMPACT
4. Encryption Phase: After the encryption key gets established the encryption phase gets
initiated where the ransomware starts its operation while encrypting the files that it
discovers within the system.
5. Extortion: In the final stage of its operation, that is in the Extortion stage, a statement
regarding ransomware gets displayed on the system’s screen asking to pay a ransom just
before the criminal starts decrypting the files in order to destroy them (Salvi, Harshada
and Kerkar). The limit of this ransom often ranges to about $300 to $500 and are often
asked to pay via Bitcoin or any other type of electronic payment method that are
generally anonymous.
4. Encryption Phase: After the encryption key gets established the encryption phase gets
initiated where the ransomware starts its operation while encrypting the files that it
discovers within the system.
5. Extortion: In the final stage of its operation, that is in the Extortion stage, a statement
regarding ransomware gets displayed on the system’s screen asking to pay a ransom just
before the criminal starts decrypting the files in order to destroy them (Salvi, Harshada
and Kerkar). The limit of this ransom often ranges to about $300 to $500 and are often
asked to pay via Bitcoin or any other type of electronic payment method that are
generally anonymous.
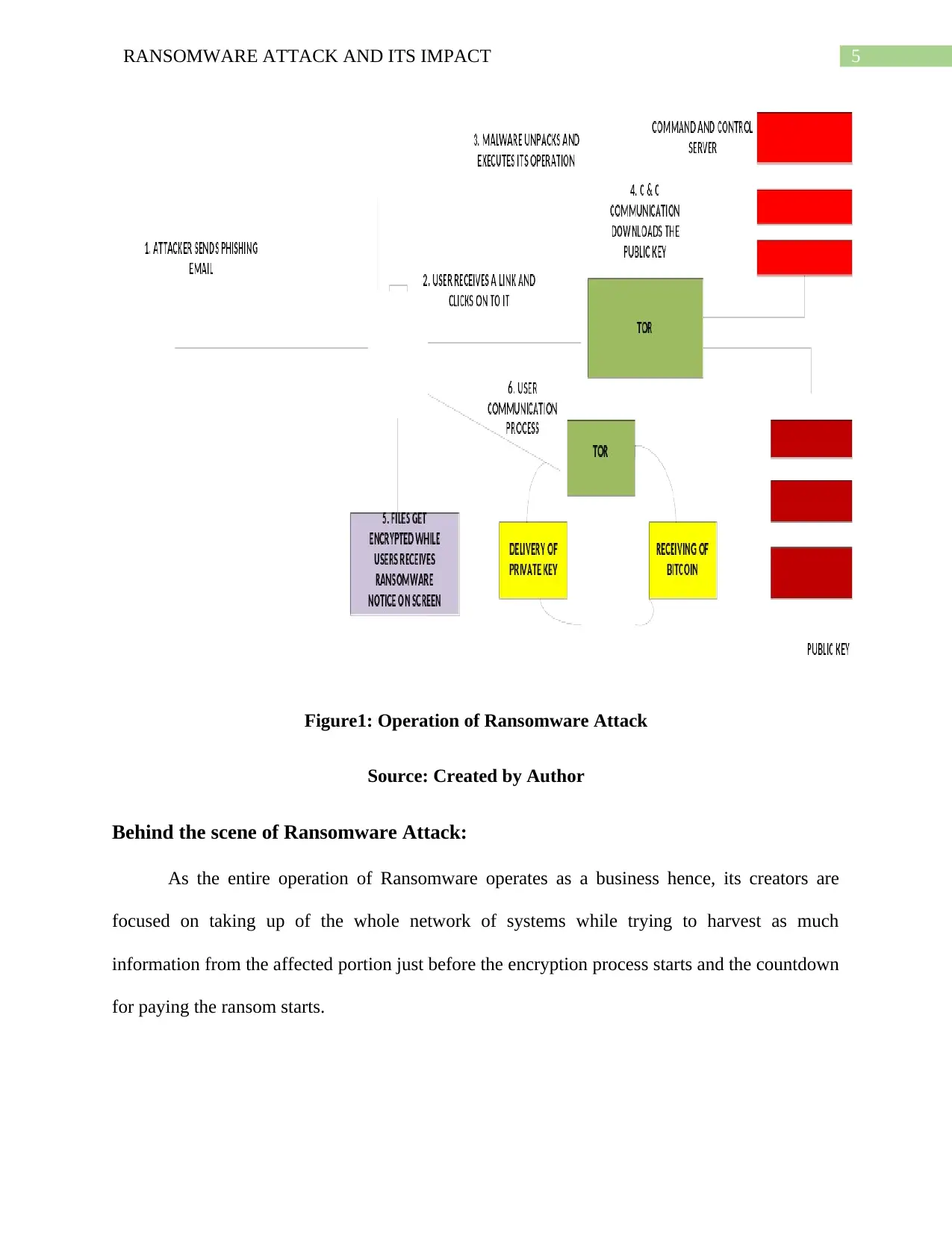
5RANSOMWARE ATTACK AND ITS IMPACT
Figure1: Operation of Ransomware Attack
Source: Created by Author
Behind the scene of Ransomware Attack:
As the entire operation of Ransomware operates as a business hence, its creators are
focused on taking up of the whole network of systems while trying to harvest as much
information from the affected portion just before the encryption process starts and the countdown
for paying the ransom starts.
Figure1: Operation of Ransomware Attack
Source: Created by Author
Behind the scene of Ransomware Attack:
As the entire operation of Ransomware operates as a business hence, its creators are
focused on taking up of the whole network of systems while trying to harvest as much
information from the affected portion just before the encryption process starts and the countdown
for paying the ransom starts.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RANSOMWARE ATTACK AND ITS IMPACT
Mode of operation of Ransomware in the real world:
Among the most recent case of a Ransomware attack, mention must be made of the
WannaCry Ransomware that struck the world across every corner of the globe in May 2017
(Chen, Qian, and Robert). The Ransomware was initially named as Wanna Cryptor and later was
appointed as Wanna Crypt. Due to the painful condition that was faced due to the attack, the
researchers then called it as the WannaCry Ransomware.
The Wannacry Ransomware contained of numerous components. The Ransomware
started its operation while infecting computers in the method of a dispenser which is a type of
self-bearable package that is used to extract details of other applications that are embedded
within the components of the system. The various parts of the system include an implementation
of the encrypted and decrypted data, files consisting of the encryption keys and a copy of the
Tor. Once the Wanna Cry ransomware got its access to the hard-coded URL, which is also
known as the kill-switch, it then started to proceed to hunt for other encrypted files while slewing
their compatible formats leaving them inaccessible for the users (Hsiao, Shou-Ching, and Da-Yu
Kao). It then started displaying a notice based on ransom while demanding to pay $300 in an
anonymous way of currency exchange that is via Bitcoin to decrypt the documents. The
attacking vector of the WannaCry Ransomware was much more interesting than that of the
Ransomware. The susceptibility that existed with the ransomware exploitation lied within the
implementation of the Windows of the SMB protocol (Mohurle, Savita, and Manisha Patil). The
SMB protocol helped the various bulges on the network to interconnect and also tricking the
application of Microsoft employing specially designed packets to execute arbitrary code.
Mode of operation of Ransomware in the real world:
Among the most recent case of a Ransomware attack, mention must be made of the
WannaCry Ransomware that struck the world across every corner of the globe in May 2017
(Chen, Qian, and Robert). The Ransomware was initially named as Wanna Cryptor and later was
appointed as Wanna Crypt. Due to the painful condition that was faced due to the attack, the
researchers then called it as the WannaCry Ransomware.
The Wannacry Ransomware contained of numerous components. The Ransomware
started its operation while infecting computers in the method of a dispenser which is a type of
self-bearable package that is used to extract details of other applications that are embedded
within the components of the system. The various parts of the system include an implementation
of the encrypted and decrypted data, files consisting of the encryption keys and a copy of the
Tor. Once the Wanna Cry ransomware got its access to the hard-coded URL, which is also
known as the kill-switch, it then started to proceed to hunt for other encrypted files while slewing
their compatible formats leaving them inaccessible for the users (Hsiao, Shou-Ching, and Da-Yu
Kao). It then started displaying a notice based on ransom while demanding to pay $300 in an
anonymous way of currency exchange that is via Bitcoin to decrypt the documents. The
attacking vector of the WannaCry Ransomware was much more interesting than that of the
Ransomware. The susceptibility that existed with the ransomware exploitation lied within the
implementation of the Windows of the SMB protocol (Mohurle, Savita, and Manisha Patil). The
SMB protocol helped the various bulges on the network to interconnect and also tricking the
application of Microsoft employing specially designed packets to execute arbitrary code.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RANSOMWARE ATTACK AND ITS IMPACT
Outcome and Impact of the WannaCry Ransomware:
As a result of the attack, the wannacry Ransomware spread across the world while
infecting about more than 230,000 computers in about 150countries incurring a cost of
approximately 4 billion dollars in terms of financial loss. It was regarded as the most virulent
type of malware that spread since the past centuries when the worm named Slammer worm
infected users within an hour. The operation of the WannaCry Ransomware disrupted the
facilities at Britain's National Health Services, causing cancellation of about 20,000
appointments at the clinics and hospitals while turning theme offline.
Aim of Security that was breached and it is resulting consequences:
The vulnerability that was discovered by the U.S. National Security Agency reported for
the presence of a developed code that was exploited and was known as the Eternal Blue. This
exploitation of the code was taken by a collection of hackers recognized as the Shadow Brokers
who released the code via medium political post on April 8, 2017 (Huang, Danny Yuxing, et al.).
Microsoft exposed this susceptibility a month before and as a measure to it released a patch. In
spite of that, several systems remained vulnerable to WannaCry (Richardson, Ronny, and North).
In the meantime, the Ransomware started spreading across networks making use of the Eternal
Blue and finally outbreak in May 2017. The security officers reported that the malware first tried
to access a long gibberish URL before starting its operation while attempting to access the
domain. The patch that was created to prevent the malware although was available before a
month when the attack took place, still many systems were left unpatched, and the malware
started spreading across them.
Outcome and Impact of the WannaCry Ransomware:
As a result of the attack, the wannacry Ransomware spread across the world while
infecting about more than 230,000 computers in about 150countries incurring a cost of
approximately 4 billion dollars in terms of financial loss. It was regarded as the most virulent
type of malware that spread since the past centuries when the worm named Slammer worm
infected users within an hour. The operation of the WannaCry Ransomware disrupted the
facilities at Britain's National Health Services, causing cancellation of about 20,000
appointments at the clinics and hospitals while turning theme offline.
Aim of Security that was breached and it is resulting consequences:
The vulnerability that was discovered by the U.S. National Security Agency reported for
the presence of a developed code that was exploited and was known as the Eternal Blue. This
exploitation of the code was taken by a collection of hackers recognized as the Shadow Brokers
who released the code via medium political post on April 8, 2017 (Huang, Danny Yuxing, et al.).
Microsoft exposed this susceptibility a month before and as a measure to it released a patch. In
spite of that, several systems remained vulnerable to WannaCry (Richardson, Ronny, and North).
In the meantime, the Ransomware started spreading across networks making use of the Eternal
Blue and finally outbreak in May 2017. The security officers reported that the malware first tried
to access a long gibberish URL before starting its operation while attempting to access the
domain. The patch that was created to prevent the malware although was available before a
month when the attack took place, still many systems were left unpatched, and the malware
started spreading across them.

8RANSOMWARE ATTACK AND ITS IMPACT
Victim responsible for the attack:
The Gibberish URL was discovered by Hutchins where he paid up to $10.96 to register
the domain to set up a site allowing the malware to spread. After being hailed as arrested for
developing another malware in the year 2014; however, after that, he was proclaimed of his
innocence.
Action that should be taken to address the issue:
Ransomware is popping out frequently and to prevent the effect such as in case of Wannacry
the necessary steps that need to be followed to mitigate the problems are as follows:
Maintaining security of the software used within an organization while keeping them up
to date.
Enabling automatic updating of the software whenever a device connects to a network
(Brewer).
The principal port that was exploited by the WannaCry Ransomware was port 445. Hence
it is needed to close the port that got exploited in the WannaCry attack (Furnell, Steven,
and David Emm).
Backing up relevant data and files and storing them via offline method to prevent them
from deletion by the attackers.
To patch the systems with the latest updates.
Conclusion:
Thus it can be concluded that every organization needs to advance their security
protections through regular updating the systems and the networks to prevent attacks of different
types of malware that are arising day by day. With the coming years, the number of malware and
Victim responsible for the attack:
The Gibberish URL was discovered by Hutchins where he paid up to $10.96 to register
the domain to set up a site allowing the malware to spread. After being hailed as arrested for
developing another malware in the year 2014; however, after that, he was proclaimed of his
innocence.
Action that should be taken to address the issue:
Ransomware is popping out frequently and to prevent the effect such as in case of Wannacry
the necessary steps that need to be followed to mitigate the problems are as follows:
Maintaining security of the software used within an organization while keeping them up
to date.
Enabling automatic updating of the software whenever a device connects to a network
(Brewer).
The principal port that was exploited by the WannaCry Ransomware was port 445. Hence
it is needed to close the port that got exploited in the WannaCry attack (Furnell, Steven,
and David Emm).
Backing up relevant data and files and storing them via offline method to prevent them
from deletion by the attackers.
To patch the systems with the latest updates.
Conclusion:
Thus it can be concluded that every organization needs to advance their security
protections through regular updating the systems and the networks to prevent attacks of different
types of malware that are arising day by day. With the coming years, the number of malware and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RANSOMWARE ATTACK AND ITS IMPACT
their malicious effects are yet to be discovered so to protect those effects, and companies need to
take up steps to protect their systems and stay updated on the new types of malicious codes
arising every day.
their malicious effects are yet to be discovered so to protect those effects, and companies need to
take up steps to protect their systems and stay updated on the new types of malicious codes
arising every day.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RANSOMWARE ATTACK AND ITS IMPACT
References:
Brewer, Ross. "Ransomware attacks: detection, prevention and cure." Network Security 2016.9
(2016): 5-9.
Chen, Qian, and Robert A. Bridges. "Automated behavioural analysis of malware: A case study
of wannacry ransomware." 2017 16th IEEE International Conference on Machine Learning and
Applications (ICMLA). IEEE, 2017.
Furnell, Steven, and David Emm. "The ABC of ransomware protection." Computer Fraud &
Security 2017.10 (2017): 5-11.
Hsiao, Shou-Ching, and Da-Yu Kao. "The static analysis of WannaCry ransomware." 2018 20th
International Conference on Advanced Communication Technology (ICACT). IEEE, 2018.
Huang, Danny Yuxing, et al. "Tracking ransomware end-to-end." 2018 IEEE Symposium on
Security and Privacy (SP). IEEE, 2018.
Module, Savita, and Manisha Patil. "A brief study of wannacry threat: Ransomware attack
2017." International Journal of Advanced Research in Computer Science 8.5 (2017).
O'Gorman, Gavin, and Geoff McDonald. Ransomware: A growing menace. Symantec
Corporation, 2015.
Richardson, Ronny, and Max M. North. "Ransomware: Evolution, mitigation and
prevention." International Management Review 13.1 (2017): 10.
Salvi, Miss Harshada U., and Mr Ravindra V. Kerkar. "Ransomware: A cyber extortion." Asian
Journal For Convergence In Technology (AJCT) 2 (2016).
References:
Brewer, Ross. "Ransomware attacks: detection, prevention and cure." Network Security 2016.9
(2016): 5-9.
Chen, Qian, and Robert A. Bridges. "Automated behavioural analysis of malware: A case study
of wannacry ransomware." 2017 16th IEEE International Conference on Machine Learning and
Applications (ICMLA). IEEE, 2017.
Furnell, Steven, and David Emm. "The ABC of ransomware protection." Computer Fraud &
Security 2017.10 (2017): 5-11.
Hsiao, Shou-Ching, and Da-Yu Kao. "The static analysis of WannaCry ransomware." 2018 20th
International Conference on Advanced Communication Technology (ICACT). IEEE, 2018.
Huang, Danny Yuxing, et al. "Tracking ransomware end-to-end." 2018 IEEE Symposium on
Security and Privacy (SP). IEEE, 2018.
Module, Savita, and Manisha Patil. "A brief study of wannacry threat: Ransomware attack
2017." International Journal of Advanced Research in Computer Science 8.5 (2017).
O'Gorman, Gavin, and Geoff McDonald. Ransomware: A growing menace. Symantec
Corporation, 2015.
Richardson, Ronny, and Max M. North. "Ransomware: Evolution, mitigation and
prevention." International Management Review 13.1 (2017): 10.
Salvi, Miss Harshada U., and Mr Ravindra V. Kerkar. "Ransomware: A cyber extortion." Asian
Journal For Convergence In Technology (AJCT) 2 (2016).

11RANSOMWARE ATTACK AND ITS IMPACT
Bibliography:
Richardson, Ronny, and Max M. North. "Ransomware: Evolution, mitigation and
prevention." International Management Review 13.1 (2017): 10.
O'Gorman, Gavin, and Geoff McDonald. Ransomware: A growing menace. Symantec
Corporation, 2015.
Module, Savita, and Manisha Patil. "A brief study of wannacry threat: Ransomware attack
2017." International Journal of Advanced Research in Computer Science 8.5 (2017).
Huang, Danny Yuxing, et al. "Tracking ransomware end-to-end." 2018 IEEE Symposium on
Security and Privacy (SP). IEEE, 2018.
Hsiao, Shou-Ching, and Da-Yu Kao. "The static analysis of WannaCry ransomware." 2018 20th
International Conference on Advanced Communication Technology (ICACT). IEEE, 2018.
Furnell, Steven, and David Emm. "The ABC of ransomware protection." Computer Fraud &
Security 2017.10 (2017): 5-11.
Chen, Qian, and Robert A. Bridges. "Automated behavioural analysis of malware: A case study
of wannacry ransomware." 2017 16th IEEE International Conference on Machine Learning and
Applications (ICMLA). IEEE, 2017.
Brewer, Ross. "Ransomware attacks: detection, prevention and cure." Network Security 2016.9
(2016): 5-9.
Bibliography:
Richardson, Ronny, and Max M. North. "Ransomware: Evolution, mitigation and
prevention." International Management Review 13.1 (2017): 10.
O'Gorman, Gavin, and Geoff McDonald. Ransomware: A growing menace. Symantec
Corporation, 2015.
Module, Savita, and Manisha Patil. "A brief study of wannacry threat: Ransomware attack
2017." International Journal of Advanced Research in Computer Science 8.5 (2017).
Huang, Danny Yuxing, et al. "Tracking ransomware end-to-end." 2018 IEEE Symposium on
Security and Privacy (SP). IEEE, 2018.
Hsiao, Shou-Ching, and Da-Yu Kao. "The static analysis of WannaCry ransomware." 2018 20th
International Conference on Advanced Communication Technology (ICACT). IEEE, 2018.
Furnell, Steven, and David Emm. "The ABC of ransomware protection." Computer Fraud &
Security 2017.10 (2017): 5-11.
Chen, Qian, and Robert A. Bridges. "Automated behavioural analysis of malware: A case study
of wannacry ransomware." 2017 16th IEEE International Conference on Machine Learning and
Applications (ICMLA). IEEE, 2017.
Brewer, Ross. "Ransomware attacks: detection, prevention and cure." Network Security 2016.9
(2016): 5-9.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





