Exploring BATMAN and SPEED: Routing Protocols for Ad-hoc Networks
VerifiedAdded on 2023/06/12
|27
|2239
|314
Report
AI Summary
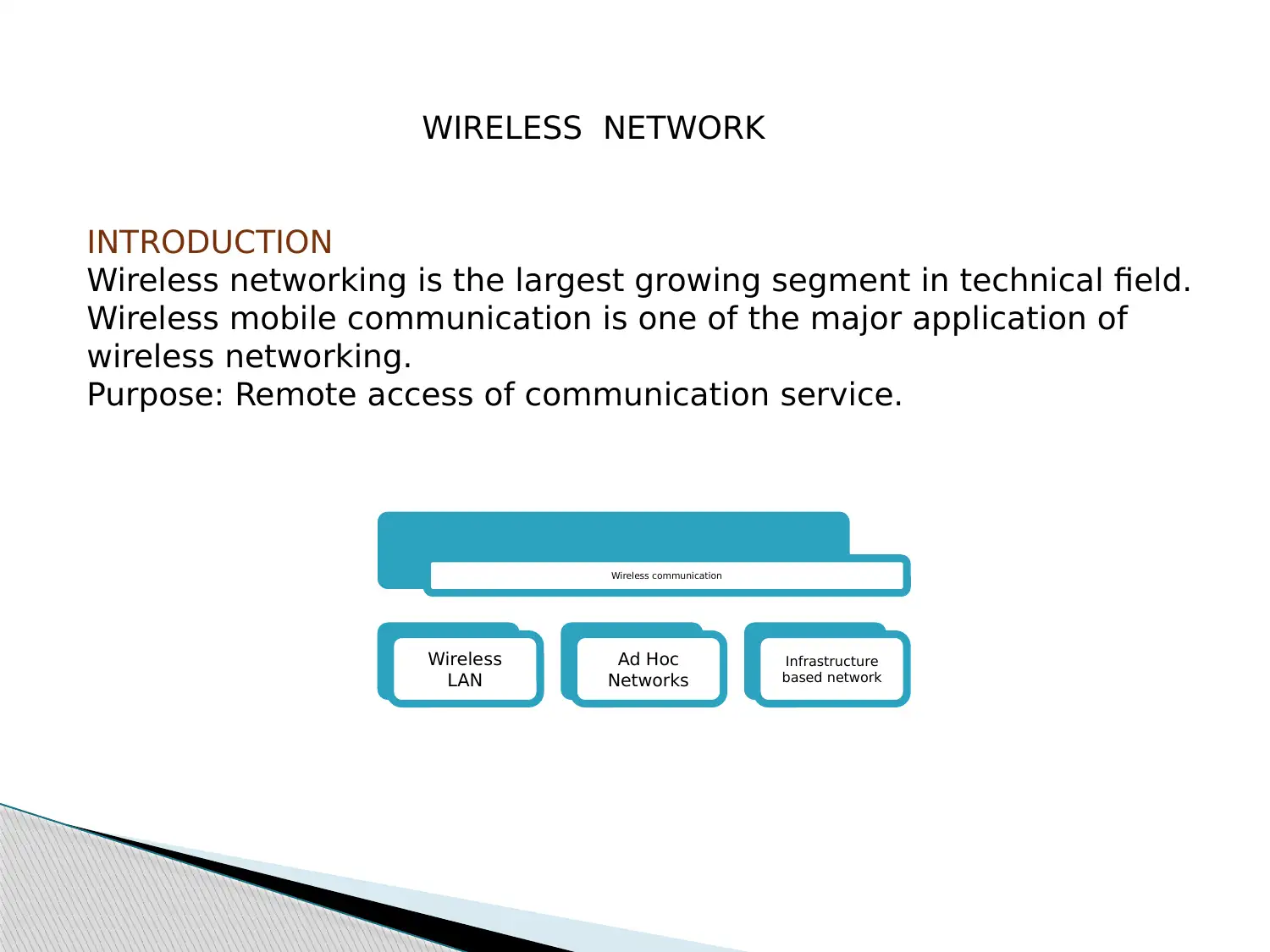
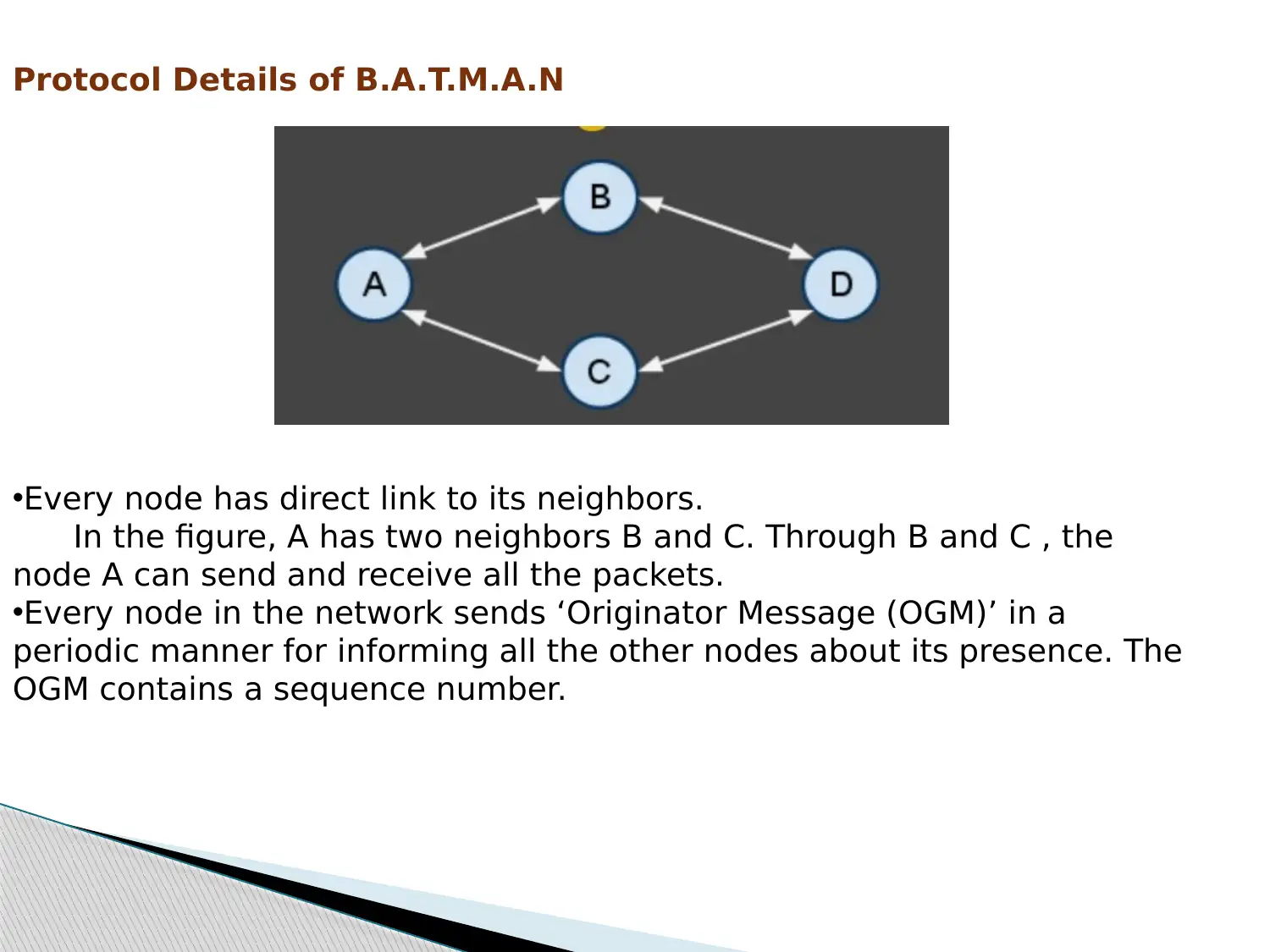
This report provides an overview of mobile ad-hoc networks (MANETs) and delves into two prominent routing protocols: Better Approach To Mobile Ad-Hoc Networking (B.A.T.M.A.N.) and SPEED, a real-time routing protocol for wireless sensor networks. It begins by introducing wireless networking concepts, highlighting the characteristics and advantages of ad-hoc networks, and then focuses on the MESH topology. The report details the B.A.T.M.A.N protocol, its algorithm, and its advantages over Optimized Link State Protocol (OLSR). Furthermore, it explores real-time sensor networks, their applications, constraints, and the importance of MAC and routing protocols. The SPEED protocol and its variations (MM SPEED, FT SPEED, EE SPEED) are discussed in detail, along with their evaluation and comparison. The report concludes by emphasizing the suitability of B.A.T.M.A.N for ad-hoc networks and SPEED (particularly MMSPEED) for real-time wireless networking.
1 out of 27





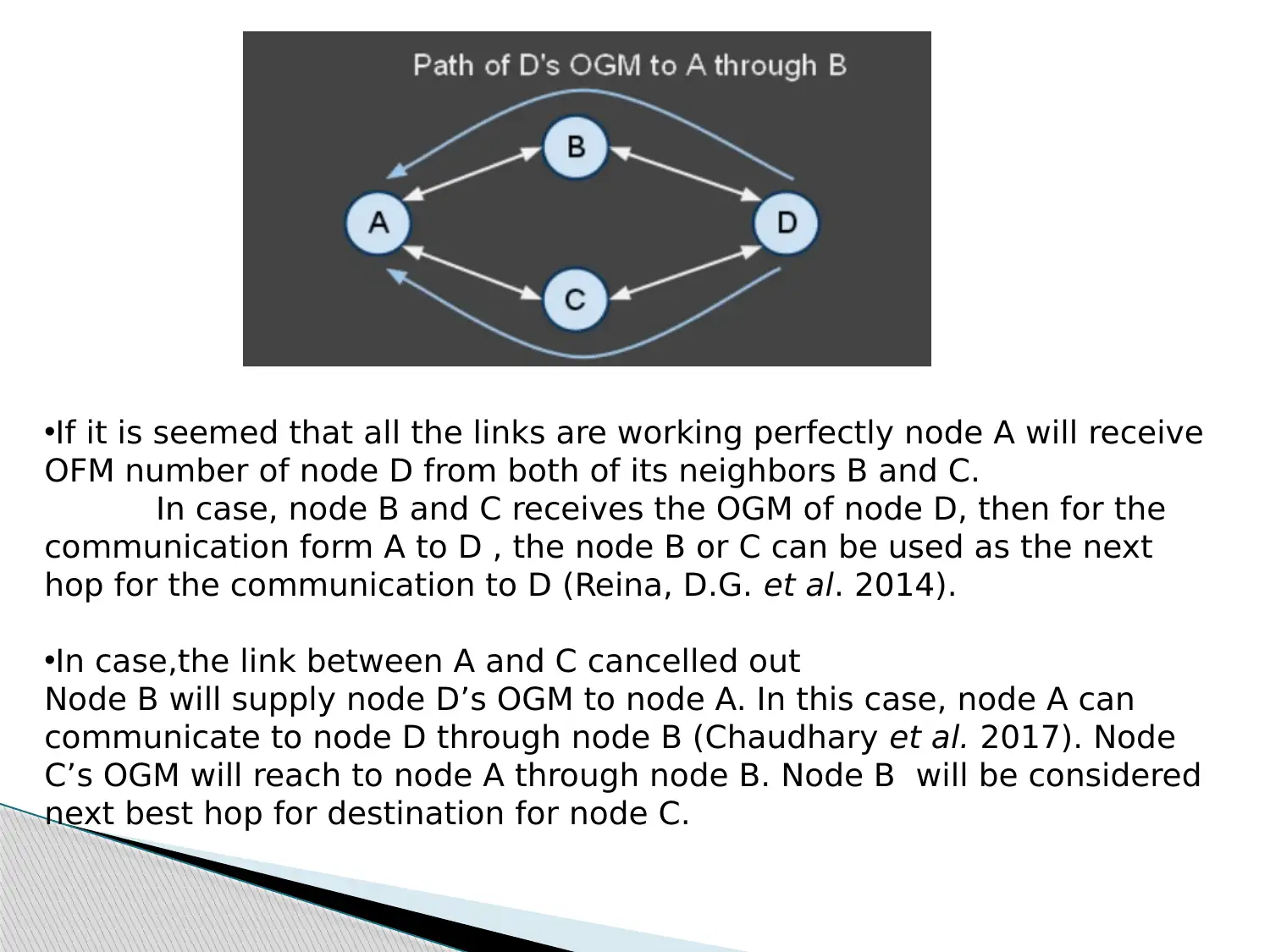
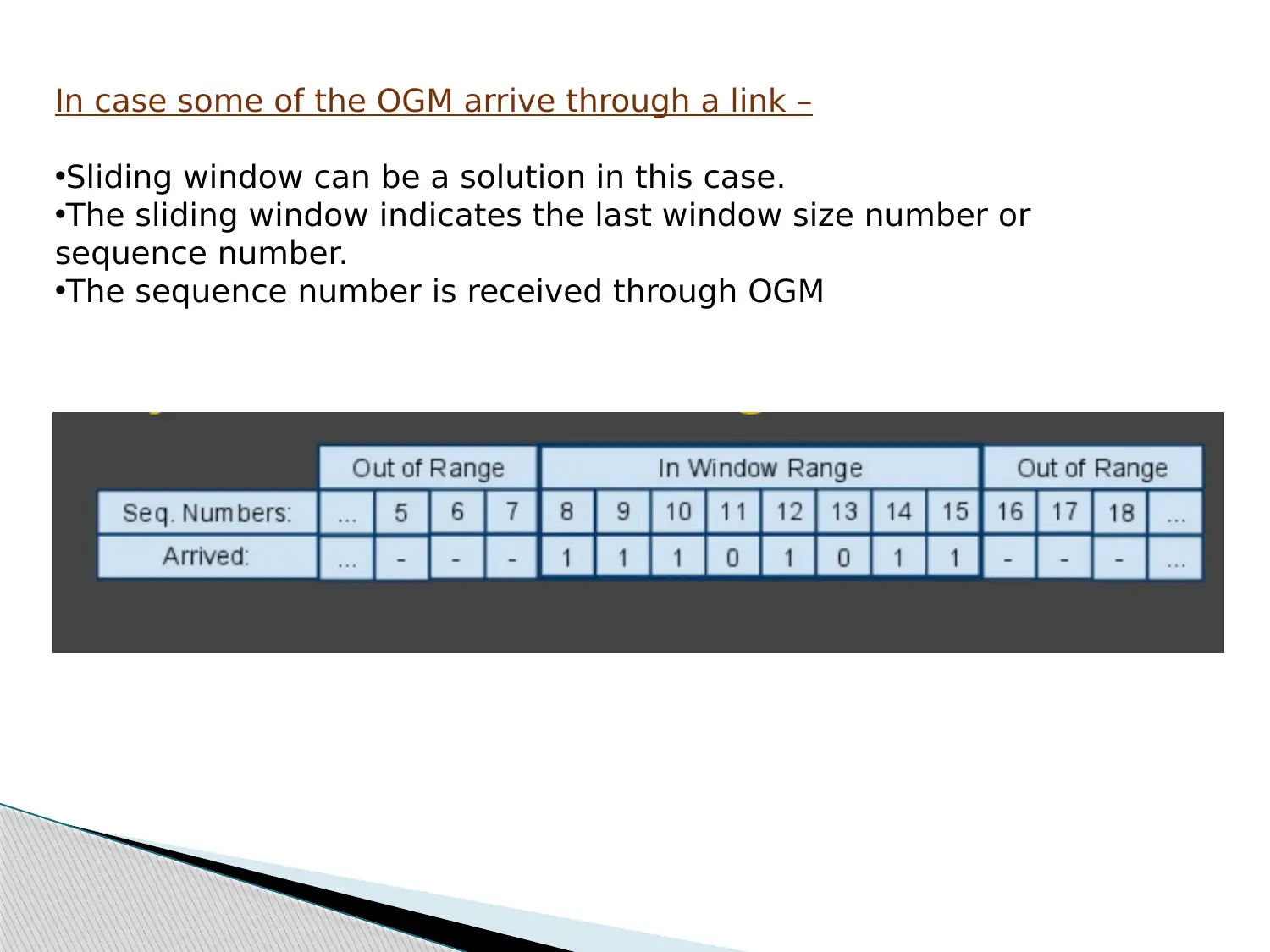








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)