Mobile App Comparison and Recommendation Report - AI Module
VerifiedAdded on 2022/08/29
|10
|2023
|17
Report
AI Summary
This report analyzes and compares three mobile applications: Find My iPhone, Wickr Me, and Lookout, focusing on their features, security aspects, and overall user experience. The methodology involves evaluating each app based on supportive systems, security measures, and enhancing features. The report recommends Lookout as the preferred application due to its strong security capabilities in preventing phishing, data breaches, and malicious URLs, and its applicability across both iOS and Android platforms. An implementation plan is proposed, including small-scale testing, government involvement, nationwide deployment, and ongoing result analysis, along with cost-benefit considerations. The conclusion highlights the increasing need for security applications to combat data insecurity and unethical practices, reinforcing the recommendation of Lookout for improving ethical standards and safeguarding the future. The report also includes an executive summary and cited sources.

Recommendation Report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

App Introduction:
Is already done please see the attached file called App Intro for your reference.
Background:
- https://www.techworld.com/security/uks-most-infamous-data-breaches-3604586/
- https://haveibeenpwned.com/
- https://privacyrights.org/data-breaches
The first site includes almost more than 10 years of data on data breach but with brief
description. This makes it a bit confusing for the non-technical readers to understand the
content and the issue. The second website carries an issue of including all companies’ data
beaches under one roof. The third website is confusing as it marks each breach with its type
which is confusing for normal people to understand.
The three websites provides authentic and authorized information and facts and figures. Each
website is accurate in its approach. The facts and figures are specifically stated in each
website.
The negative consequence of the three sites is that it reveals the darker side of technology and
it can create a mess over the ones who carry ethical views.
Methodology:
1. Purpose of comparison:
Through companring the three apps, the best and the worst features of the
each app could be identified through which the future developments could be designed in
a manner which would fill up those gaps. The comparison of Find My App, Wickr App
Is already done please see the attached file called App Intro for your reference.
Background:
- https://www.techworld.com/security/uks-most-infamous-data-breaches-3604586/
- https://haveibeenpwned.com/
- https://privacyrights.org/data-breaches
The first site includes almost more than 10 years of data on data breach but with brief
description. This makes it a bit confusing for the non-technical readers to understand the
content and the issue. The second website carries an issue of including all companies’ data
beaches under one roof. The third website is confusing as it marks each breach with its type
which is confusing for normal people to understand.
The three websites provides authentic and authorized information and facts and figures. Each
website is accurate in its approach. The facts and figures are specifically stated in each
website.
The negative consequence of the three sites is that it reveals the darker side of technology and
it can create a mess over the ones who carry ethical views.
Methodology:
1. Purpose of comparison:
Through companring the three apps, the best and the worst features of the
each app could be identified through which the future developments could be designed in
a manner which would fill up those gaps. The comparison of Find My App, Wickr App

and Lookout App would provide the justification for the popularity of the one over the
other and thus this would help in identifying the consumer’s preferences and choices.
2. Description: Application A is (Find My iPhone) paraphrase / add details to your
previous description!!
The Application A is the Find My iPhone App and this helps the Apple Ios devices like
iPhone, iPad, and iPod to get located on being stolen or lost. This application helps in
restricting the usage of the device after being lost r stolen. The app helps in locking the
device and thus no other person could access the data. The app was established by Apple Inc.
for serving its customer’s with an additional feature.
Description: Application B is (Wickr Me) paraphrase / add details to your
previous description!!
The Application B is the Wicker Me App formulated by an American IT company. The app
is a chatting app which provides an encryption conversations be it within two people or a
group of people. The application is supported in both the Apple iOs as well as in the Android
phones.
Description: Application C is (Lookout) paraphrase / add details to your
previous description!!
The Application C is Lookout which is a cloud based security software for the mobile
phones. The security application helps in preventing phishing, data breaches, malicious URL
and other insignificant or unethical internet practices.
3. Criteria: find three caritas to compare the app
other and thus this would help in identifying the consumer’s preferences and choices.
2. Description: Application A is (Find My iPhone) paraphrase / add details to your
previous description!!
The Application A is the Find My iPhone App and this helps the Apple Ios devices like
iPhone, iPad, and iPod to get located on being stolen or lost. This application helps in
restricting the usage of the device after being lost r stolen. The app helps in locking the
device and thus no other person could access the data. The app was established by Apple Inc.
for serving its customer’s with an additional feature.
Description: Application B is (Wickr Me) paraphrase / add details to your
previous description!!
The Application B is the Wicker Me App formulated by an American IT company. The app
is a chatting app which provides an encryption conversations be it within two people or a
group of people. The application is supported in both the Apple iOs as well as in the Android
phones.
Description: Application C is (Lookout) paraphrase / add details to your
previous description!!
The Application C is Lookout which is a cloud based security software for the mobile
phones. The security application helps in preventing phishing, data breaches, malicious URL
and other insignificant or unethical internet practices.
3. Criteria: find three caritas to compare the app
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Supportive System
Security Based
Enhancing feature
4. Comparison: (a) each application one paragraph
Application A
Criteria A: The first application that is Find My iPhone is supportive only to the Apple iOs
software which restricts its applications
Criteria B: The application is security based as it provides a security and restriction on usage
of data available in the phone by any other user.
Criteria C: It helped Apple Inc. in attracting new customers and business people with a
secured feature. The application enhanced the company’s sales.
Application B
Criteria A: The application is supportive to Android as well as the Ios software which makes
it widely applicable.
Criteria B: The application is not security based but is a chatting application which connects
people.
Criteria C: The application helps in enhancing the communication skills and reduces gap in
communicating on wide scale.
Application C
Security Based
Enhancing feature
4. Comparison: (a) each application one paragraph
Application A
Criteria A: The first application that is Find My iPhone is supportive only to the Apple iOs
software which restricts its applications
Criteria B: The application is security based as it provides a security and restriction on usage
of data available in the phone by any other user.
Criteria C: It helped Apple Inc. in attracting new customers and business people with a
secured feature. The application enhanced the company’s sales.
Application B
Criteria A: The application is supportive to Android as well as the Ios software which makes
it widely applicable.
Criteria B: The application is not security based but is a chatting application which connects
people.
Criteria C: The application helps in enhancing the communication skills and reduces gap in
communicating on wide scale.
Application C
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Criteria A: The third application also supports Android as well as iOs software.
Criteria B: The application is a security application which protects from phishing and other
data breaches.
Criteria C: The application helps the company in enhancing its sales and profits through its
effective services.
Recommendation:
The comparison of the three applications helped in identifying the main features of each
application and thus the productivity and results which could be gained through each of it has
been acknowledged. The three criteria set for acknowledging the three applications provided
with an identification of each applications strengths and weaknesses.
The application which is recommended is the Application C that is Lookout which is a
security application. The app helps in restricting phishing, data breaches and other unethical
practices in the IT industry. The application is recommended because of its applicability in
the two domains that is in iOs as well as in Android. The wide applicability and the
restriction of unethical practices makes it quite productive and fruitful application.
Implementation plan:
Which app do you recommend?
Application C: Lookout App developed by Lookout Inc.
In brief, what do you envision will happen?
The application would help in reducing unethical practices in the IT world. As phishing, data
stealing, malicious URLs all would be under control through the application of this app.
Criteria B: The application is a security application which protects from phishing and other
data breaches.
Criteria C: The application helps the company in enhancing its sales and profits through its
effective services.
Recommendation:
The comparison of the three applications helped in identifying the main features of each
application and thus the productivity and results which could be gained through each of it has
been acknowledged. The three criteria set for acknowledging the three applications provided
with an identification of each applications strengths and weaknesses.
The application which is recommended is the Application C that is Lookout which is a
security application. The app helps in restricting phishing, data breaches and other unethical
practices in the IT industry. The application is recommended because of its applicability in
the two domains that is in iOs as well as in Android. The wide applicability and the
restriction of unethical practices makes it quite productive and fruitful application.
Implementation plan:
Which app do you recommend?
Application C: Lookout App developed by Lookout Inc.
In brief, what do you envision will happen?
The application would help in reducing unethical practices in the IT world. As phishing, data
stealing, malicious URLs all would be under control through the application of this app.

How does this improve upon the previous situation?
Technology has provided with acceleration in all sectors which has been accompanied by
some unethical practices. These unethical practices could be restricted and controlled through
this app. It has been experienced that in the last few years, phishing has been impacting the
word at large and a control over this could help in improving the ethical practices.
Implementation Steps
One: Check its benefits and results on small scale.
Rationale: Checking on small scale would help in reducing risk on large scale and thus the
applicability would be beneficial and productive.
How to Implement: Some minor along with the major companies and financial banks would
be approached for utilizing the app. This would help in acknowledging the results on small
scale but in effective area.
Two: Government insight into the application
Rationale: Through government insight and authorization the application would be identified
on nationwide scale. This would authorize the applicability.
How to Implement: The government officials would be required for acknowledging the
results of the app and thus through various tests the final decision would be taken.
Three: Apply on nationwide scale
Technology has provided with acceleration in all sectors which has been accompanied by
some unethical practices. These unethical practices could be restricted and controlled through
this app. It has been experienced that in the last few years, phishing has been impacting the
word at large and a control over this could help in improving the ethical practices.
Implementation Steps
One: Check its benefits and results on small scale.
Rationale: Checking on small scale would help in reducing risk on large scale and thus the
applicability would be beneficial and productive.
How to Implement: Some minor along with the major companies and financial banks would
be approached for utilizing the app. This would help in acknowledging the results on small
scale but in effective area.
Two: Government insight into the application
Rationale: Through government insight and authorization the application would be identified
on nationwide scale. This would authorize the applicability.
How to Implement: The government officials would be required for acknowledging the
results of the app and thus through various tests the final decision would be taken.
Three: Apply on nationwide scale
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Rationale: The application on nationwide scale would reduce phishing which has been
increasing on a high rate. Data malfunctioning and malicious URLs would be checked which
would improvise the social and ethical conditions.
How to Implement: Government applications should be sent to the 20 major companies of the
country to use and apply the application with proper marketing and advertisement.
Four: Cross check the results of the application implied
Rationale: This would help in gaining an insight into the productivity of the app and the
benefits which has been gained. Benefit would be checked through reduction on unethical
practices by the app.
How to Implement: Report from each company would be taken and this would be assessed
through some special tea.
Five: Make it a law to imply Application C on all companies
Rationale: This would help in implying the app on wide scale and thus ethics would be
prioritized.
How to Implement: Making it a law to imply the Lookout App on every financial and IT
company would help in gaining a grip over its application.
COSTS and BENEFITS
Benefit One : Reduction in Phishing, data breaches and malicious URLs
Explanation: The reduction in such practices would enhance the implementation of ethical
practices.
Benefit Two : Improvise the decision making ability
Explanation: Through understating the acceleration in unethical practices, people would be
more accurate in their decisions which would be productive and effective.
increasing on a high rate. Data malfunctioning and malicious URLs would be checked which
would improvise the social and ethical conditions.
How to Implement: Government applications should be sent to the 20 major companies of the
country to use and apply the application with proper marketing and advertisement.
Four: Cross check the results of the application implied
Rationale: This would help in gaining an insight into the productivity of the app and the
benefits which has been gained. Benefit would be checked through reduction on unethical
practices by the app.
How to Implement: Report from each company would be taken and this would be assessed
through some special tea.
Five: Make it a law to imply Application C on all companies
Rationale: This would help in implying the app on wide scale and thus ethics would be
prioritized.
How to Implement: Making it a law to imply the Lookout App on every financial and IT
company would help in gaining a grip over its application.
COSTS and BENEFITS
Benefit One : Reduction in Phishing, data breaches and malicious URLs
Explanation: The reduction in such practices would enhance the implementation of ethical
practices.
Benefit Two : Improvise the decision making ability
Explanation: Through understating the acceleration in unethical practices, people would be
more accurate in their decisions which would be productive and effective.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
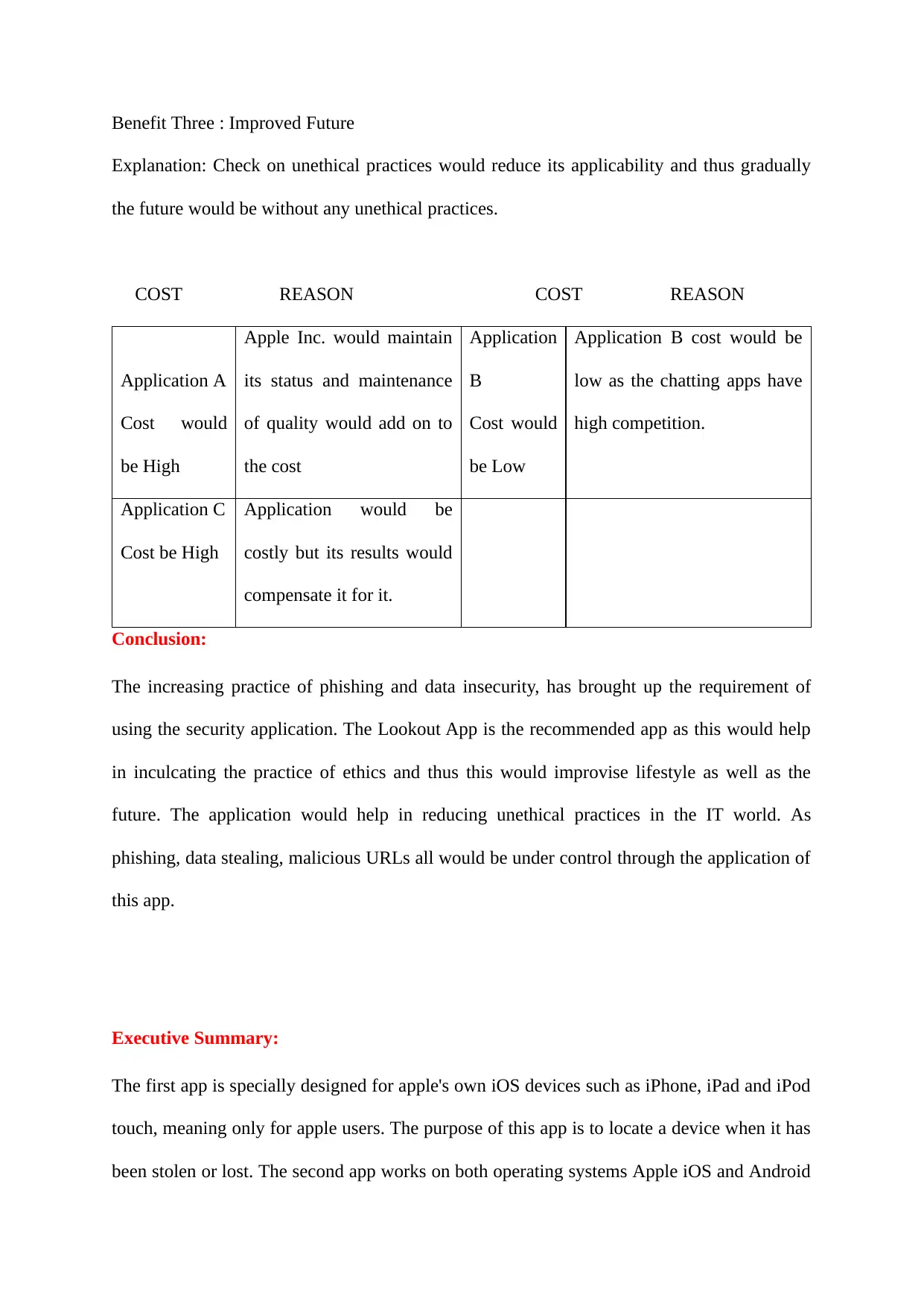
Benefit Three : Improved Future
Explanation: Check on unethical practices would reduce its applicability and thus gradually
the future would be without any unethical practices.
COST REASON COST REASON
Application A
Cost would
be High
Apple Inc. would maintain
its status and maintenance
of quality would add on to
the cost
Application
B
Cost would
be Low
Application B cost would be
low as the chatting apps have
high competition.
Application C
Cost be High
Application would be
costly but its results would
compensate it for it.
Conclusion:
The increasing practice of phishing and data insecurity, has brought up the requirement of
using the security application. The Lookout App is the recommended app as this would help
in inculcating the practice of ethics and thus this would improvise lifestyle as well as the
future. The application would help in reducing unethical practices in the IT world. As
phishing, data stealing, malicious URLs all would be under control through the application of
this app.
Executive Summary:
The first app is specially designed for apple's own iOS devices such as iPhone, iPad and iPod
touch, meaning only for apple users. The purpose of this app is to locate a device when it has
been stolen or lost. The second app works on both operating systems Apple iOS and Android
Explanation: Check on unethical practices would reduce its applicability and thus gradually
the future would be without any unethical practices.
COST REASON COST REASON
Application A
Cost would
be High
Apple Inc. would maintain
its status and maintenance
of quality would add on to
the cost
Application
B
Cost would
be Low
Application B cost would be
low as the chatting apps have
high competition.
Application C
Cost be High
Application would be
costly but its results would
compensate it for it.
Conclusion:
The increasing practice of phishing and data insecurity, has brought up the requirement of
using the security application. The Lookout App is the recommended app as this would help
in inculcating the practice of ethics and thus this would improvise lifestyle as well as the
future. The application would help in reducing unethical practices in the IT world. As
phishing, data stealing, malicious URLs all would be under control through the application of
this app.
Executive Summary:
The first app is specially designed for apple's own iOS devices such as iPhone, iPad and iPod
touch, meaning only for apple users. The purpose of this app is to locate a device when it has
been stolen or lost. The second app works on both operating systems Apple iOS and Android

OS. Wickr is designed to allow users to create an end-to-end encryption conversation, it can
be between two people or more as there is a group enabled chat option. Lockout is an IT
security company that was founded in 2007 by John Hering, their main focuses are on
developing cloud-based security software for mobile devices. This app also works on both
operating systems Apple iOS and Android OS. Through companring the three apps, the best
and the worst features of the each app could be identified through which the future
developments could be designed in a manner which would fill up those gaps. The application
which is recommended is the Application C that is Lookout which is a security application.
The app helps in restricting phishing, data breaches and other unethical practices in the IT
industry. The application would help in reducing unethical practices in the IT world. As
phishing, data stealing, malicious URLs all would be under control through the application of
this app. Checking on small scale would help in reducing risk on large scale and thus the
applicability would be beneficial and productive. Technology has provided with acceleration
in all sectors which has been accompanied by some unethical practices. These unethical
practices could be restricted and controlled through this app. It has been experienced that in
the last few years, phishing has been impacting the word at large and a control over this could
help in improving the ethical practices. Through government insight and authorization the
application would be identified on nationwide scale. This would authorize the applicability.
The increasing practice of phishing and data insecurity, has brought up the requirement of
using the security application. The Lookout App is the recommended app as this would help
in inculcating the practice of ethics and thus this would improvise lifestyle as well as the
future.
Works Cited:
be between two people or more as there is a group enabled chat option. Lockout is an IT
security company that was founded in 2007 by John Hering, their main focuses are on
developing cloud-based security software for mobile devices. This app also works on both
operating systems Apple iOS and Android OS. Through companring the three apps, the best
and the worst features of the each app could be identified through which the future
developments could be designed in a manner which would fill up those gaps. The application
which is recommended is the Application C that is Lookout which is a security application.
The app helps in restricting phishing, data breaches and other unethical practices in the IT
industry. The application would help in reducing unethical practices in the IT world. As
phishing, data stealing, malicious URLs all would be under control through the application of
this app. Checking on small scale would help in reducing risk on large scale and thus the
applicability would be beneficial and productive. Technology has provided with acceleration
in all sectors which has been accompanied by some unethical practices. These unethical
practices could be restricted and controlled through this app. It has been experienced that in
the last few years, phishing has been impacting the word at large and a control over this could
help in improving the ethical practices. Through government insight and authorization the
application would be identified on nationwide scale. This would authorize the applicability.
The increasing practice of phishing and data insecurity, has brought up the requirement of
using the security application. The Lookout App is the recommended app as this would help
in inculcating the practice of ethics and thus this would improvise lifestyle as well as the
future.
Works Cited:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

- [1]T. Staff, "The Most Infamous Data Breaches", Techworld, 2020. [Online].
Available: https://www.techworld.com/security/uks-most-infamous-data-breaches-
3604586/. [Accessed: 24- Mar- 2020]
- [2] Haveibeenpwned.com 2020. [Online]. Available: https://haveibeenpwned.com/.
[Accessed: 24- Mar- 2020]
- [3]"Data Breaches | Privacy Rights Clearinghouse", Privacyrights.org, 2020.
[Online]. Available: https://privacyrights.org/data-breaches. [Accessed: 24- Mar-
2020]
Available: https://www.techworld.com/security/uks-most-infamous-data-breaches-
3604586/. [Accessed: 24- Mar- 2020]
- [2] Haveibeenpwned.com 2020. [Online]. Available: https://haveibeenpwned.com/.
[Accessed: 24- Mar- 2020]
- [3]"Data Breaches | Privacy Rights Clearinghouse", Privacyrights.org, 2020.
[Online]. Available: https://privacyrights.org/data-breaches. [Accessed: 24- Mar-
2020]
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

