Advanced Network Security Report - University Name, Semester 1
VerifiedAdded on 2020/05/08
|15
|1894
|53
Report
AI Summary
This report on advanced network security provides a comprehensive overview of various critical aspects of network protection. It begins with a detailed examination of firewalls, including the creation of network diagrams using Cisco Packet Tracer, the implementation of access control lists (ACLs) based on business rules, and the configuration of firewall policies using iptables. The report then delves into WiFi security, discussing WPA and WPA2 encryption, the role of antennas, transmit power, and AP positioning in controlling radio range, the importance of RADIUS authentication, and methods for manual detection of rogue access points. Further, the report discusses access control, including password storage and security. It also covers HTTPS and certificates, explaining certificate acquisition, SSL/TLS usage, and the role of signature methods. Finally, the report addresses internet privacy, exploring the use of web proxies, VPNs, and Tor networks to enhance user anonymity and data protection. The report provides a solid foundation for understanding and implementing robust network security measures.

Ruining head: ADVANCED NETWORK SECURITY
Advanced network Security
Name of the Student
Name of the University
Author’s Note
Advanced network Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ADVANCED NETWORK SECURITY
Table of Contents
1. Firewalls..........................................................................................................................2
2. WiFi Security...................................................................................................................3
3. Access Control.................................................................................................................5
4. HTTPS and Certificates...................................................................................................8
5. Internet Privacy..............................................................................................................11
Bibliography......................................................................................................................13
ADVANCED NETWORK SECURITY
Table of Contents
1. Firewalls..........................................................................................................................2
2. WiFi Security...................................................................................................................3
3. Access Control.................................................................................................................5
4. HTTPS and Certificates...................................................................................................8
5. Internet Privacy..............................................................................................................11
Bibliography......................................................................................................................13
2
ADVANCED NETWORK SECURITY
1. Firewalls
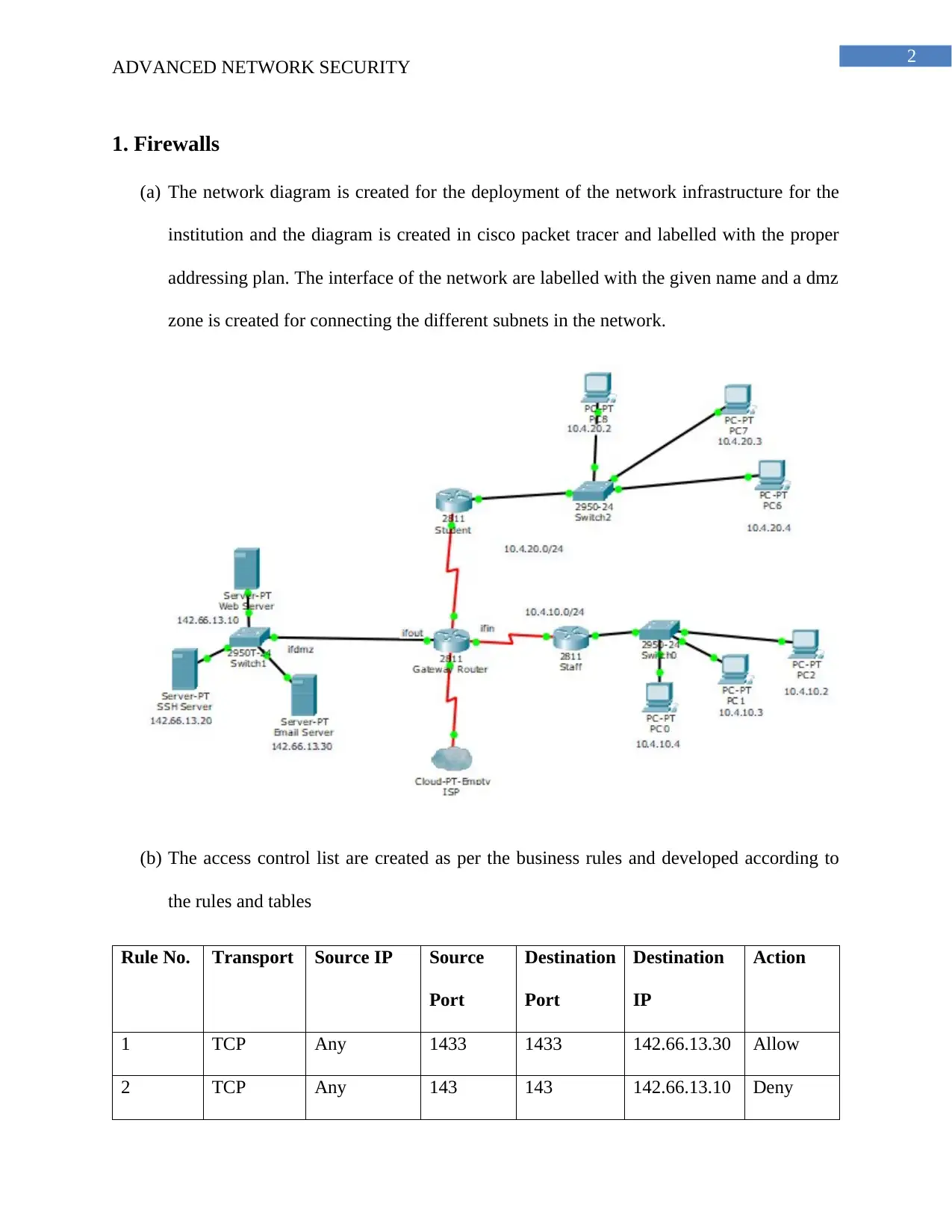
(a) The network diagram is created for the deployment of the network infrastructure for the
institution and the diagram is created in cisco packet tracer and labelled with the proper
addressing plan. The interface of the network are labelled with the given name and a dmz
zone is created for connecting the different subnets in the network.
(b) The access control list are created as per the business rules and developed according to
the rules and tables
Rule No. Transport Source IP Source
Port
Destination
Port
Destination
IP
Action
1 TCP Any 1433 1433 142.66.13.30 Allow
2 TCP Any 143 143 142.66.13.10 Deny
ADVANCED NETWORK SECURITY
1. Firewalls
(a) The network diagram is created for the deployment of the network infrastructure for the
institution and the diagram is created in cisco packet tracer and labelled with the proper
addressing plan. The interface of the network are labelled with the given name and a dmz
zone is created for connecting the different subnets in the network.
(b) The access control list are created as per the business rules and developed according to
the rules and tables
Rule No. Transport Source IP Source
Port
Destination
Port
Destination
IP
Action
1 TCP Any 1433 1433 142.66.13.30 Allow
2 TCP Any 143 143 142.66.13.10 Deny
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
ADVANCED NETWORK SECURITY
5 TCP 142.66.13.10 1023 Any 142.66.13.30 Allow
3 TCP Any 1023 Any 142.66.13.20 Deny
4 TCP 10.4.10.0 –
10.4.10.255
143 143 142.66.13.10 Allow
6 TCP 142.66.13.30 1023 Any 142.66.13.20 Allow
7 TCP 10.40.10.2 1234 1234 10.4.10.4 Allow
9 TCP 10.40.10.3 1234 1234 Any Deny
8 TCP 10.40.20.2 1234 1234 10.40.10.3 Allow
(c) Firewall policy is developed using the iptables from the routers and the default routing
policy can be changed using different commands such as –P, –L or –A. The two
examples of the common default policies used for the configuration of the access control
list are as follow:
Dropping of the data packets from unknown hosts outside the dmz zone and allowing
access of the web server for the student subnet with IP address 10.4.20.0/24.
2. WiFi Security
(a) The WPA also known as the Wifi protected Passwords are used in the in the
wireless networks so that the security of the network can be enhanced to a great level. This
would help in restricting the unauthorized access to the network. The other version of the
WPA are also available such as the WPA2. The WPA2 was introduced in the year 2003 and
it was thought to be a suitable replacement for the WEP at that point of time. The encryption
algorithm used for WPA is TKIP. It is basically a 128-bit key generated for the prevention of
different type of attack on the network.
ADVANCED NETWORK SECURITY
5 TCP 142.66.13.10 1023 Any 142.66.13.30 Allow
3 TCP Any 1023 Any 142.66.13.20 Deny
4 TCP 10.4.10.0 –
10.4.10.255
143 143 142.66.13.10 Allow
6 TCP 142.66.13.30 1023 Any 142.66.13.20 Allow
7 TCP 10.40.10.2 1234 1234 10.4.10.4 Allow
9 TCP 10.40.10.3 1234 1234 Any Deny
8 TCP 10.40.20.2 1234 1234 10.40.10.3 Allow
(c) Firewall policy is developed using the iptables from the routers and the default routing
policy can be changed using different commands such as –P, –L or –A. The two
examples of the common default policies used for the configuration of the access control
list are as follow:
Dropping of the data packets from unknown hosts outside the dmz zone and allowing
access of the web server for the student subnet with IP address 10.4.20.0/24.
2. WiFi Security
(a) The WPA also known as the Wifi protected Passwords are used in the in the
wireless networks so that the security of the network can be enhanced to a great level. This
would help in restricting the unauthorized access to the network. The other version of the
WPA are also available such as the WPA2. The WPA2 was introduced in the year 2003 and
it was thought to be a suitable replacement for the WEP at that point of time. The encryption
algorithm used for WPA is TKIP. It is basically a 128-bit key generated for the prevention of
different type of attack on the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ADVANCED NETWORK SECURITY
(b) Antennas, transmit power and AP positioning for controlling the radio range
Antennas are very useful in the wireless networks. They are used for the generation of
wireless signals across the whole network. They perform the basic task of extending the network
to a greater range this helps in the extensions of the radios used in the wireless networks. The
range of the antennas depend on the amount of energy that is passing through it. The more
amount of energy entering into the antenna would cause the antenna to increase its range. The
radio energy passes through the network and the transmit power is used for controlling this
energy. The increased control of the network increases the efficiency of the network.
There are a number of factors on which the transmission power depends. The
polarization, gain of antenna and attenuation are the different type of factors in which the
transmission power depends on. In to this, the different types of antenna available to us are Omni
directional antennas, point to point and directional antennas. With increased amount of
attenuation, the transmit power required to meet the loss of signal also increase to a great extent.
The access points within the network have the requirement for placement in the proper
locations so the whole area within the network are covered. The selection of an antenna for the
network is also very important as the security of the network depends on the antenna to a great
extent. Hence, implementation of proper encryption process is required by the network so that
the access points can be prevented from unauthorized access to the network.
(c) RADIUS authentication
The radius authentication is very important for the centralized authentication function
within the wireless network. The AAA protocol within the network is used for the authentication
in the servers. The RADIUS protocol is very important for the network and this is used by the
ADVANCED NETWORK SECURITY
(b) Antennas, transmit power and AP positioning for controlling the radio range
Antennas are very useful in the wireless networks. They are used for the generation of
wireless signals across the whole network. They perform the basic task of extending the network
to a greater range this helps in the extensions of the radios used in the wireless networks. The
range of the antennas depend on the amount of energy that is passing through it. The more
amount of energy entering into the antenna would cause the antenna to increase its range. The
radio energy passes through the network and the transmit power is used for controlling this
energy. The increased control of the network increases the efficiency of the network.
There are a number of factors on which the transmission power depends. The
polarization, gain of antenna and attenuation are the different type of factors in which the
transmission power depends on. In to this, the different types of antenna available to us are Omni
directional antennas, point to point and directional antennas. With increased amount of
attenuation, the transmit power required to meet the loss of signal also increase to a great extent.
The access points within the network have the requirement for placement in the proper
locations so the whole area within the network are covered. The selection of an antenna for the
network is also very important as the security of the network depends on the antenna to a great
extent. Hence, implementation of proper encryption process is required by the network so that
the access points can be prevented from unauthorized access to the network.
(c) RADIUS authentication
The radius authentication is very important for the centralized authentication function
within the wireless network. The AAA protocol within the network is used for the authentication
in the servers. The RADIUS protocol is very important for the network and this is used by the
5
ADVANCED NETWORK SECURITY
ISP so the external and the internal networks can be managed accurately. Two types of packets
are used by the protocol that can manage the authentication, accounting and the access within the
network.
(d) Manual detection of the rogue Aps
For the detection of the rogue access points the risks associated with the wireless network
is are analyzed and the determination of the vulnerability within the network are performed. The
vulnerabilities within the network are also recorded so that it can be avoided in the future. The
evaluation of the security measures implemented within the network are to be done repeatedly as
thee evaluation would help in increasing the flexibility of the network. the access points of the
network are required to be guarded safely so that external interference in the network can be
avoided. This would reduce the risk of attacks on the systems.
3. Access Control
ADVANCED NETWORK SECURITY
ISP so the external and the internal networks can be managed accurately. Two types of packets
are used by the protocol that can manage the authentication, accounting and the access within the
network.
(d) Manual detection of the rogue Aps
For the detection of the rogue access points the risks associated with the wireless network
is are analyzed and the determination of the vulnerability within the network are performed. The
vulnerabilities within the network are also recorded so that it can be avoided in the future. The
evaluation of the security measures implemented within the network are to be done repeatedly as
thee evaluation would help in increasing the flexibility of the network. the access points of the
network are required to be guarded safely so that external interference in the network can be
avoided. This would reduce the risk of attacks on the systems.
3. Access Control
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
ADVANCED NETWORK SECURITY
ADVANCED NETWORK SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
ADVANCED NETWORK SECURITY
ADVANCED NETWORK SECURITY
8
ADVANCED NETWORK SECURITY
ADVANCED NETWORK SECURITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
ADVANCED NETWORK SECURITY
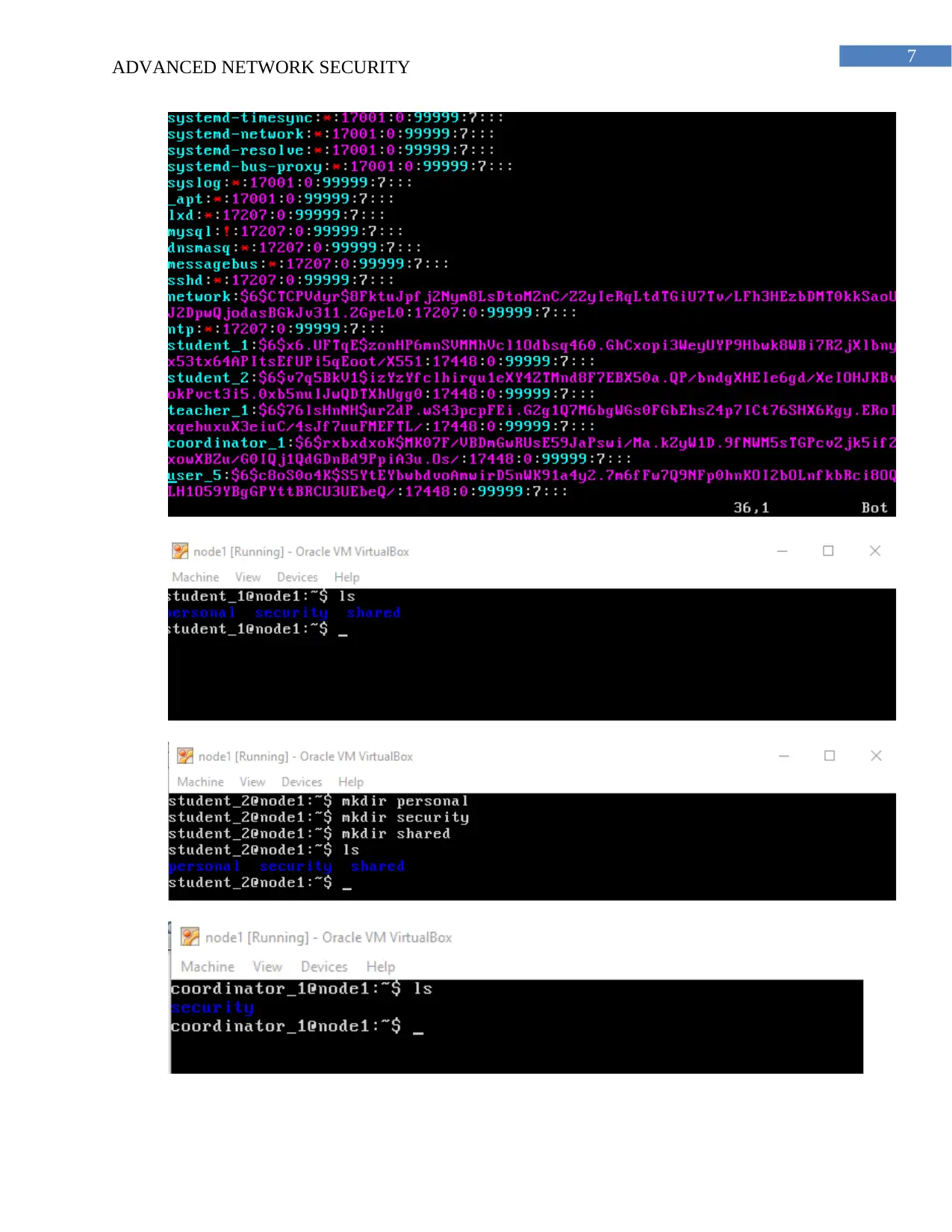
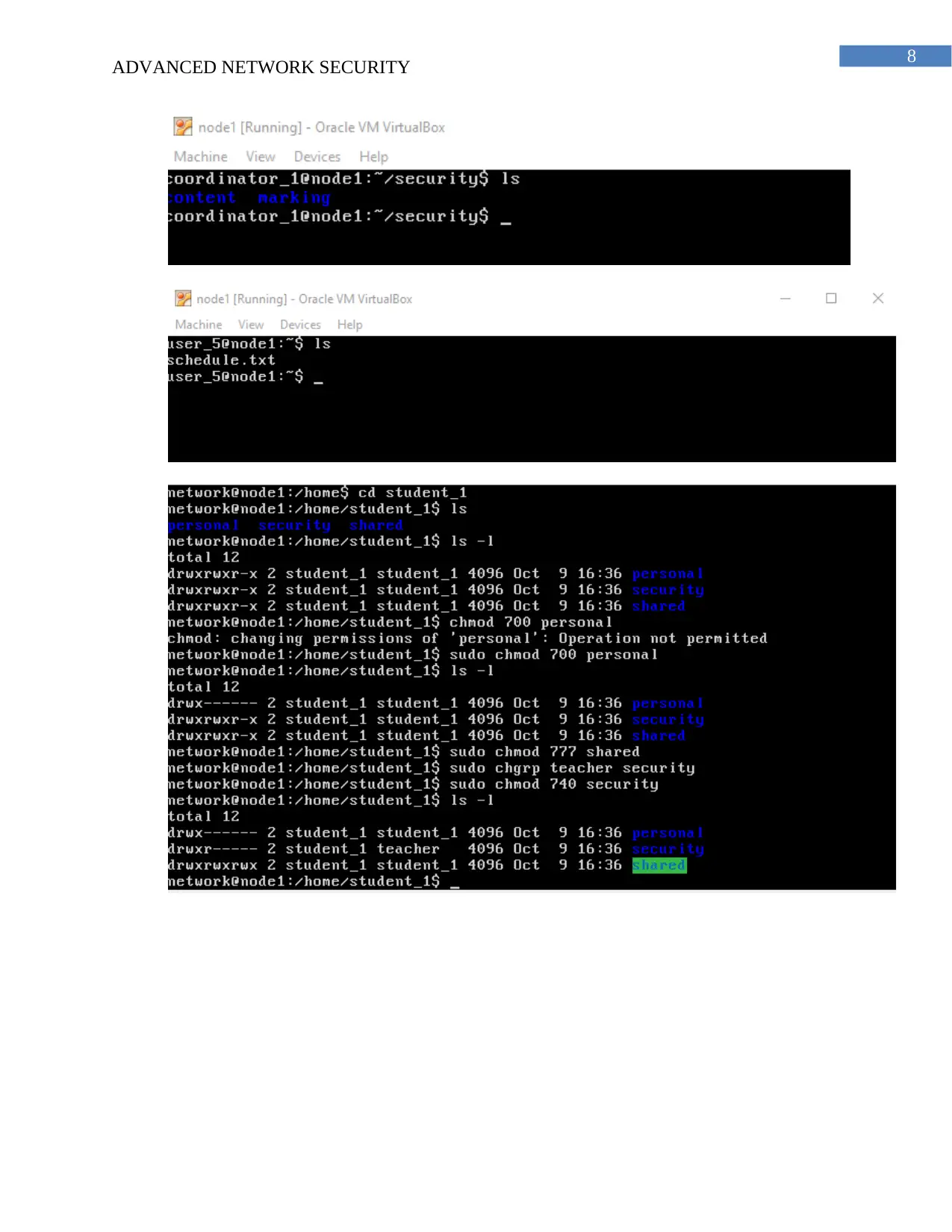
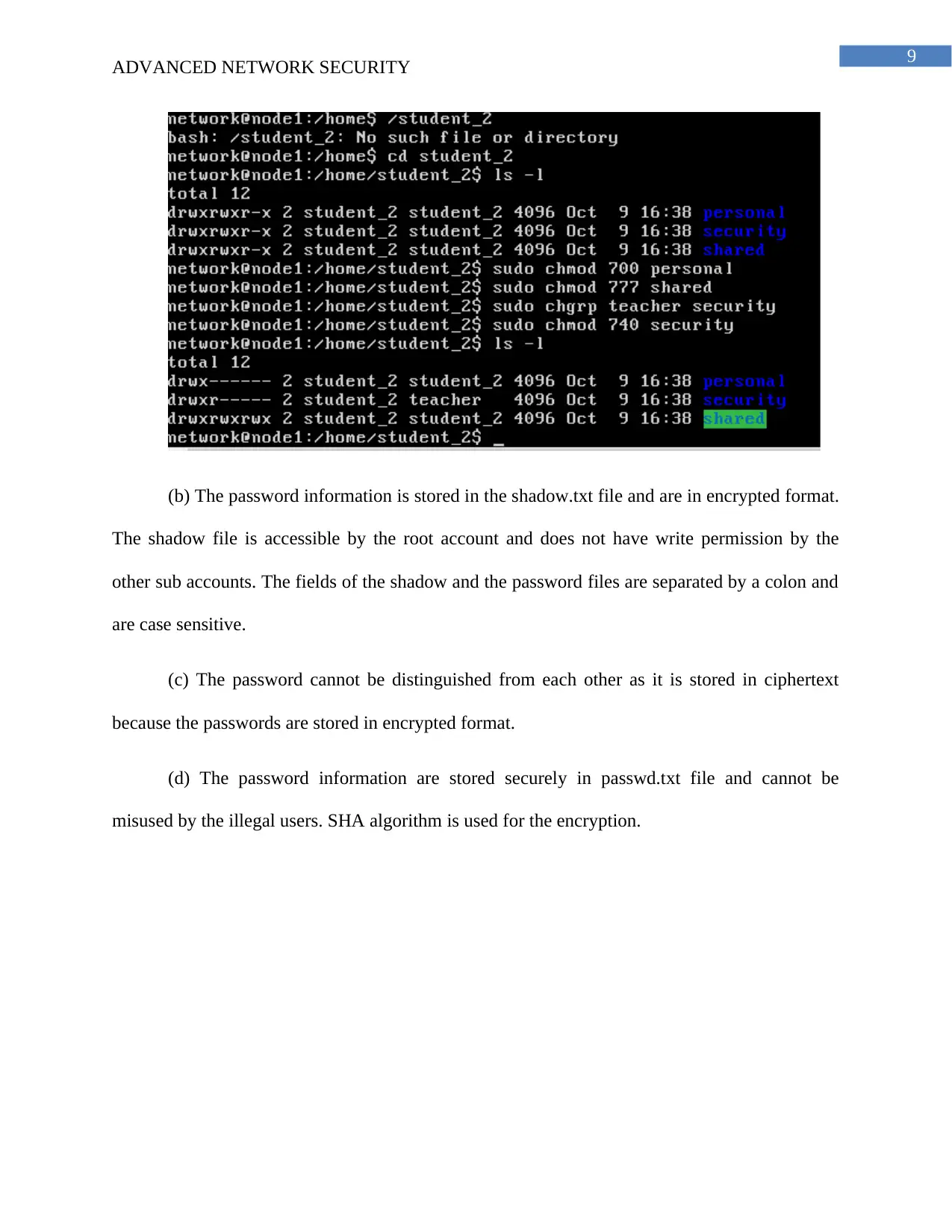
(b) The password information is stored in the shadow.txt file and are in encrypted format.
The shadow file is accessible by the root account and does not have write permission by the
other sub accounts. The fields of the shadow and the password files are separated by a colon and
are case sensitive.
(c) The password cannot be distinguished from each other as it is stored in ciphertext
because the passwords are stored in encrypted format.
(d) The password information are stored securely in passwd.txt file and cannot be
misused by the illegal users. SHA algorithm is used for the encryption.
ADVANCED NETWORK SECURITY
(b) The password information is stored in the shadow.txt file and are in encrypted format.
The shadow file is accessible by the root account and does not have write permission by the
other sub accounts. The fields of the shadow and the password files are separated by a colon and
are case sensitive.
(c) The password cannot be distinguished from each other as it is stored in ciphertext
because the passwords are stored in encrypted format.
(d) The password information are stored securely in passwd.txt file and cannot be
misused by the illegal users. SHA algorithm is used for the encryption.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
ADVANCED NETWORK SECURITY
4. HTTPS and Certificates
ADVANCED NETWORK SECURITY
4. HTTPS and Certificates
11
ADVANCED NETWORK SECURITY
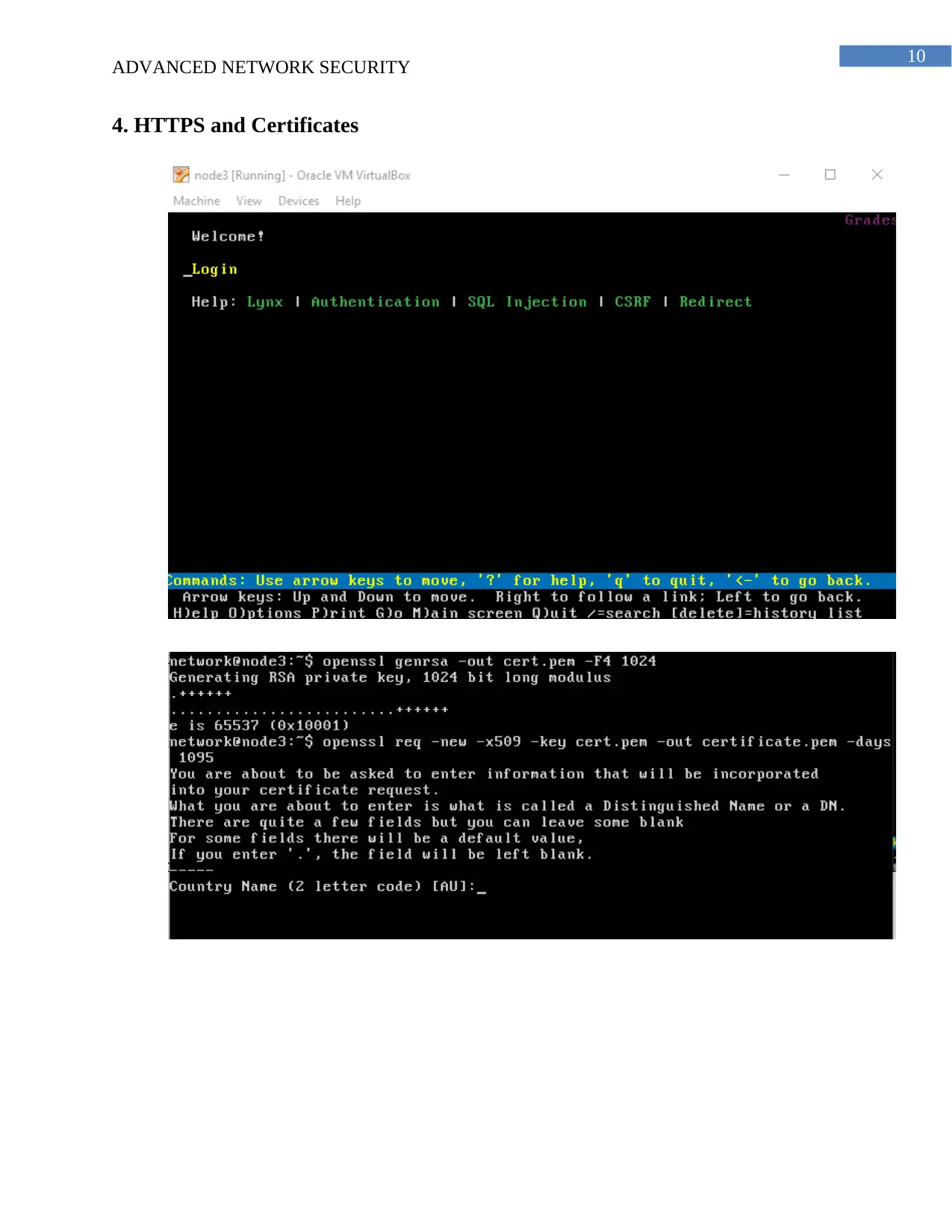
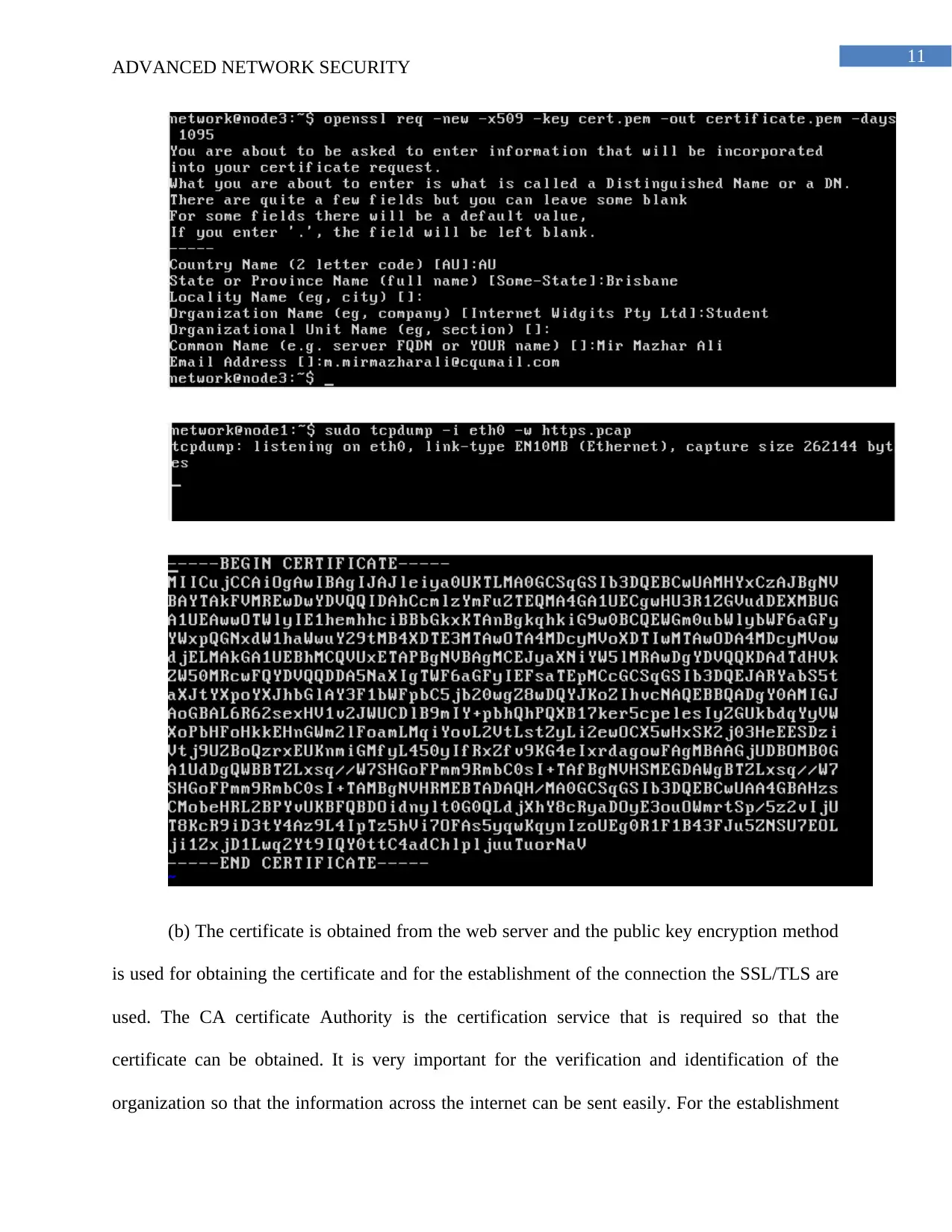
(b) The certificate is obtained from the web server and the public key encryption method
is used for obtaining the certificate and for the establishment of the connection the SSL/TLS are
used. The CA certificate Authority is the certification service that is required so that the
certificate can be obtained. It is very important for the verification and identification of the
organization so that the information across the internet can be sent easily. For the establishment
ADVANCED NETWORK SECURITY
(b) The certificate is obtained from the web server and the public key encryption method
is used for obtaining the certificate and for the establishment of the connection the SSL/TLS are
used. The CA certificate Authority is the certification service that is required so that the
certificate can be obtained. It is very important for the verification and identification of the
organization so that the information across the internet can be sent easily. For the establishment
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





