Comprehensive Risk Management Audit Report: Logistics Service Provider
VerifiedAdded on 2020/03/16
|7
|2134
|277
Report
AI Summary
This report presents a comprehensive audit of the risk management practices employed by a global logistics service provider, offering customized solutions worldwide. The audit investigates the organization's risk management structures, assessing their effectiveness through the exploration of tools and techniques used for risk identification, analysis, and mapping. It delves into the company's disaster recovery planning processes, contingency planning, control measures, and organizational structure. The report outlines the steps involved in risk management, including identification, analysis, ranking, and response. It identifies various risk scenarios across social, technical, political, financial, and environmental domains. The assessment includes risk ranking based on impact and probability, leading to the creation of a risk matrix. The report also details disaster recovery plans and business continuity plans, providing insights into handling various operational disruptions, including employee strikes and technology adoption. Furthermore, the report discusses control measures for establishing security across different layers of the OSI model, ensuring a robust approach to risk mitigation.
Introduction
This report involves an audit of the risk management practices used in an organization that is a
logistics service provider. The logistics organization provides customized logistics solutions to
companies worldwide and has global expertise into land transport, ocean and air freight services. It
has an international network of 5000 offices working with over 72,000 vehicles and 425 aircraft
carriers in 220 countries including 120,000 destinations. The organization has over 300,000
employees working for them. The aim of this report is to investigate the risk management structures
used in the organization to understand their effectiveness through exploration of tools and
techniques used for investigation, analysis and mapping of risks, disaster recovery planning process,
contingency planning, control, and organizational structure.
Risk Management Audit
Risk Management
For risk management, standard steps can be followed including risk identification, risk analysis, risk
ranking, and risk response.
Risk Identification: For identification of risks, macro ad microscopic aspects related to different
perspectives have to be considered including social, technical, political, managerial, temporal,
environmental, financial, geographical, financial, and legal and outreach (Anderson, 2010). Based on
these topics, sub-topics and risk scenarios can be identified for the logistics company as shown in the
table below:
Risk Topic Risk Sub-topics Risk Scenarios
Social Education
Competition
If staff is not trained properly, they would not perform
Market share will drop with stiff competition faced
Technical System System failure can cause data loss resulting into
interruptions in business
Political Security Loss of transported goods can negatively affect company
reputation
Financial Delays Delays in fund release or salary disbursement would
damage company reputation
Infrastructure Transportation
modes
Delays in deliveries
Environmental Pollution Vehicles used in transportation cause emission of harmful
gases
Outreach Marketing Incorrect customer segmentation
(APM Group Ltd, 2017)
Risk Assessment: The strategic objectives of the organization have to be defined such that the risks
identified can be explored to understand how they would be affected. The strategic objectives can
be identified from the four categories including delivering highest quality through utilization of local
expertise as well as global network, creation of global environment using multi-cultural heritage,
This report involves an audit of the risk management practices used in an organization that is a
logistics service provider. The logistics organization provides customized logistics solutions to
companies worldwide and has global expertise into land transport, ocean and air freight services. It
has an international network of 5000 offices working with over 72,000 vehicles and 425 aircraft
carriers in 220 countries including 120,000 destinations. The organization has over 300,000
employees working for them. The aim of this report is to investigate the risk management structures
used in the organization to understand their effectiveness through exploration of tools and
techniques used for investigation, analysis and mapping of risks, disaster recovery planning process,
contingency planning, control, and organizational structure.
Risk Management Audit
Risk Management
For risk management, standard steps can be followed including risk identification, risk analysis, risk
ranking, and risk response.
Risk Identification: For identification of risks, macro ad microscopic aspects related to different
perspectives have to be considered including social, technical, political, managerial, temporal,
environmental, financial, geographical, financial, and legal and outreach (Anderson, 2010). Based on
these topics, sub-topics and risk scenarios can be identified for the logistics company as shown in the
table below:
Risk Topic Risk Sub-topics Risk Scenarios
Social Education
Competition
If staff is not trained properly, they would not perform
Market share will drop with stiff competition faced
Technical System System failure can cause data loss resulting into
interruptions in business
Political Security Loss of transported goods can negatively affect company
reputation
Financial Delays Delays in fund release or salary disbursement would
damage company reputation
Infrastructure Transportation
modes
Delays in deliveries
Environmental Pollution Vehicles used in transportation cause emission of harmful
gases
Outreach Marketing Incorrect customer segmentation
(APM Group Ltd, 2017)
Risk Assessment: The strategic objectives of the organization have to be defined such that the risks
identified can be explored to understand how they would be affected. The strategic objectives can
be identified from the four categories including delivering highest quality through utilization of local
expertise as well as global network, creation of global environment using multi-cultural heritage,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
providing superior quality solution using efficient processes, and creating cooperation between
citizens by considering social and environmental needs of local communities, employees, and the
public. Risk assessment involves identification of severity of risk and probability of it occurrence
(Armour, 2017). This value can be used for giving rank to the respective risks
Table A: Risk Impacts
Impact
Level
Descriptor Description
0 Negligible No monetary loss
1 Minor Some loss of dignity and finance
2 Moderate Moderate financial loss and reputation loss
3 Serious Serious loss causing interruption in business
4 Severe Major loss and interruption
5 Catastrophic Failure that can lead to shut down of the company (Avdoshin &
Pesotskaya, 2011)
Table B: Risk Probabilities
Probability
Level
Descriptor Description
0 Impossible Event would not happen
1 Rare Event can occur in exceptional circumstances
2 Unlikely Event can occur at times
3 Moderate Event should occur some time
4 likely Event can occur in most circumstances
5 Most certain Event is expected to happen (Bayne, 2002)
Risk Ranking: Based on the level of impact and the risk probabilities, risk ranking can be provided to
each risk from acceptable, moderate, significant, and severe to high risk categories.
Risk Probability
Impact
Level
0 1 2 3 4 5
0 0 0 0 0 0 0
1 0 1 2 3 4 5
2 0 2 4 6 8 10
3 0 3 6 9 12 15
4 0 4 8 12 16 20
5 0 5 10 15 20 25
Risk
Categor
y
No Risk 1-2: Acceptable 3-5:
Moderate
6-12:
Significant
13-18:
Severe
19-25:
High Risk
(Bodicha,
2005)
Risk Matrix: Each identified risk can be given ranking based on its likelihood of occurrence and
impact on the project to form the risk matrix as shown below:
citizens by considering social and environmental needs of local communities, employees, and the
public. Risk assessment involves identification of severity of risk and probability of it occurrence
(Armour, 2017). This value can be used for giving rank to the respective risks
Table A: Risk Impacts
Impact
Level
Descriptor Description
0 Negligible No monetary loss
1 Minor Some loss of dignity and finance
2 Moderate Moderate financial loss and reputation loss
3 Serious Serious loss causing interruption in business
4 Severe Major loss and interruption
5 Catastrophic Failure that can lead to shut down of the company (Avdoshin &
Pesotskaya, 2011)
Table B: Risk Probabilities
Probability
Level
Descriptor Description
0 Impossible Event would not happen
1 Rare Event can occur in exceptional circumstances
2 Unlikely Event can occur at times
3 Moderate Event should occur some time
4 likely Event can occur in most circumstances
5 Most certain Event is expected to happen (Bayne, 2002)
Risk Ranking: Based on the level of impact and the risk probabilities, risk ranking can be provided to
each risk from acceptable, moderate, significant, and severe to high risk categories.
Risk Probability
Impact
Level
0 1 2 3 4 5
0 0 0 0 0 0 0
1 0 1 2 3 4 5
2 0 2 4 6 8 10
3 0 3 6 9 12 15
4 0 4 8 12 16 20
5 0 5 10 15 20 25
Risk
Categor
y
No Risk 1-2: Acceptable 3-5:
Moderate
6-12:
Significant
13-18:
Severe
19-25:
High Risk
(Bodicha,
2005)
Risk Matrix: Each identified risk can be given ranking based on its likelihood of occurrence and
impact on the project to form the risk matrix as shown below:
Risk Impact Probability Ranking
If staff is not trained properly, they would not perform 4 3 12
Market share will drop with stiff competition faced 4 2 8
System failure can cause data loss resulting into interruptions in
business
5 1 5
Loss of transported goods can negatively affect company
reputation
4 2 8
Delays in fund release or salary disbursement would damage
company reputation (Health and Safety Authority, 2006)
3 3 9
Delays in deliveries 4 4 16
Vehicles used in transportation cause emission of harmful gases 4 2 8
Incorrect customer segmentation 5 1 5
(Cooper,
2004)
Risk Response: Based on the level of severity of the risk, an appropriate response can be planned
from acceptance, avoiding, transfer and mitigation. Acceptable risks are not worked upon while high
and sever risks are avoided. Moderate level risks can be mitigated and significant risks can either be
avoided to transfer to another party or mitigated in case both are not possible (Curtis & Carey, 2012)
Risk Ranking Descriptor Response
If staff is not trained properly,
they would not perform
12 Significant Avoid by identifying training needs
and making provisions for training
Market share will drop with stiff
competition faced
8 Significant Transfer by negotiating with suppliers
or mitigate by cost cutting
System failure can cause data
loss resulting into interruptions
in business
5 Moderate Mitigate by recovering the lost data
Loss of transported goods can
negatively affect company
reputation
8 Significant Transfer the risk to transporter or
insurance company for damaged
goods (Solomon Island Government,
2009)
Delays in fund release or salary
disbursement would damage
company reputation
9 Significant Mitigate risk by releasing funds as
soon as possible
Delays in deliveries 16 Severe Avoid by taking appropriate steps for
controlling delivery schedules
Vehicles used in transportation
cause emission of harmful gases
8 Significant Mitigate by using low emission fuels
and vehicles
Incorrect customer segmentation 5 Moderate Mitigate by correcting customer
targeting and modify marketing plan
(Engine Yard, Inc., 2014)
Disaster Recovery Plan
Disaster recovery is the process by which the access to a company data is regained after the critical
operations have been devastated by natural calamities or other human induced damages. Specific
procedures and directions are needed to provide instructions to enable system infrastructure for
resuming services in the case. Some of the cases where disaster recovery plan would be required
If staff is not trained properly, they would not perform 4 3 12
Market share will drop with stiff competition faced 4 2 8
System failure can cause data loss resulting into interruptions in
business
5 1 5
Loss of transported goods can negatively affect company
reputation
4 2 8
Delays in fund release or salary disbursement would damage
company reputation (Health and Safety Authority, 2006)
3 3 9
Delays in deliveries 4 4 16
Vehicles used in transportation cause emission of harmful gases 4 2 8
Incorrect customer segmentation 5 1 5
(Cooper,
2004)
Risk Response: Based on the level of severity of the risk, an appropriate response can be planned
from acceptance, avoiding, transfer and mitigation. Acceptable risks are not worked upon while high
and sever risks are avoided. Moderate level risks can be mitigated and significant risks can either be
avoided to transfer to another party or mitigated in case both are not possible (Curtis & Carey, 2012)
Risk Ranking Descriptor Response
If staff is not trained properly,
they would not perform
12 Significant Avoid by identifying training needs
and making provisions for training
Market share will drop with stiff
competition faced
8 Significant Transfer by negotiating with suppliers
or mitigate by cost cutting
System failure can cause data
loss resulting into interruptions
in business
5 Moderate Mitigate by recovering the lost data
Loss of transported goods can
negatively affect company
reputation
8 Significant Transfer the risk to transporter or
insurance company for damaged
goods (Solomon Island Government,
2009)
Delays in fund release or salary
disbursement would damage
company reputation
9 Significant Mitigate risk by releasing funds as
soon as possible
Delays in deliveries 16 Severe Avoid by taking appropriate steps for
controlling delivery schedules
Vehicles used in transportation
cause emission of harmful gases
8 Significant Mitigate by using low emission fuels
and vehicles
Incorrect customer segmentation 5 Moderate Mitigate by correcting customer
targeting and modify marketing plan
(Engine Yard, Inc., 2014)
Disaster Recovery Plan
Disaster recovery is the process by which the access to a company data is regained after the critical
operations have been devastated by natural calamities or other human induced damages. Specific
procedures and directions are needed to provide instructions to enable system infrastructure for
resuming services in the case. Some of the cases where disaster recovery plan would be required
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
include relocation of the work site, data replication between two sites, crisis management, and
establishment of secondary work sites for communication.
The recovery plan would also follow steps based on specific situations (JIRA Security and Privacy
Committee (SPC) , 2007).
For example, the recovery plan for the logistics company would follow the following steps in case
the company headquarter gets destroyed:
Setting up a temporary headquarter to be used in the cases of emergency
Allocate local staff to keep the operations going
Transfer the data from the backup to this temporary site
Transport the management team to the temporary facility
Repair the main office that is destroyed meanwhile
Make the public announcement of changes (Delhi Government, 2014)
Business Contingency Plan
Business Continuity planning involves identification of data systems and functions that are critical o
an organization, analysis of the risks that can disrupt them, determination of the probability of risk
occurrence and development of a recovery plan to enable restart of the services after disruption
(Ting, et al., 2009).
Based on the situation, a business continuity plan can be developed in following steps:
Step 1: Initiation of a BCP project
Step 2: Assessment of risks and their impacts on business processes
Step 3: Identification of recovery strategies to respond to emergencies
Step 4: Disaster recovery
Step 5: Testing recovery process
Step 6: Training of staff on recovery steps
Step 7: Update the BCP plan (OECD, 2014)
IN different situations faced by the logistics service provided, different BCP steps may be followed as
illustrated below:
Situation: Dissatisfied employees going on strike Competitors having advantage because of
faster adoption of new technologies
Step 1 Inform the situation to the top
management
Assess the marketability of technology
Step 2 Form an emergency team for dealing
with the situation
Negotiate with the technology owner for the
purchase
Step 3 Start negotiating with the labour
union or representative to arrive at
Implement technology and do piloting of the
same
establishment of secondary work sites for communication.
The recovery plan would also follow steps based on specific situations (JIRA Security and Privacy
Committee (SPC) , 2007).
For example, the recovery plan for the logistics company would follow the following steps in case
the company headquarter gets destroyed:
Setting up a temporary headquarter to be used in the cases of emergency
Allocate local staff to keep the operations going
Transfer the data from the backup to this temporary site
Transport the management team to the temporary facility
Repair the main office that is destroyed meanwhile
Make the public announcement of changes (Delhi Government, 2014)
Business Contingency Plan
Business Continuity planning involves identification of data systems and functions that are critical o
an organization, analysis of the risks that can disrupt them, determination of the probability of risk
occurrence and development of a recovery plan to enable restart of the services after disruption
(Ting, et al., 2009).
Based on the situation, a business continuity plan can be developed in following steps:
Step 1: Initiation of a BCP project
Step 2: Assessment of risks and their impacts on business processes
Step 3: Identification of recovery strategies to respond to emergencies
Step 4: Disaster recovery
Step 5: Testing recovery process
Step 6: Training of staff on recovery steps
Step 7: Update the BCP plan (OECD, 2014)
IN different situations faced by the logistics service provided, different BCP steps may be followed as
illustrated below:
Situation: Dissatisfied employees going on strike Competitors having advantage because of
faster adoption of new technologies
Step 1 Inform the situation to the top
management
Assess the marketability of technology
Step 2 Form an emergency team for dealing
with the situation
Negotiate with the technology owner for the
purchase
Step 3 Start negotiating with the labour
union or representative to arrive at
Implement technology and do piloting of the
same
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
the most acceptable resolution
Step 4 Resume limited operations with
available staff
Retain the limited services and operations in
the pilot run so that business is least affected
in the case of technology failure
Step 5 Inform public about the resolution and
resumption of services
Make announcement to public about adoption
Step 6 Retain all normal business activities Retain all activities in the normal business
Step 7 Re-employ people in case the
negotiation fails
Re-employ new staff or company in case
negotiation fails (Ting, et al., 2009)
Controls
For establishing control over the security related risks in the company, the vulnerabilities at each
level of the OSI model would be assessed and control measures would be taken.
Level of Layer OSI Layer Risk Control
1 Physical Use IEEE defined standards for wireless Ethernet
Use UPS for handling situations of power failure such that
disruptions are not caused
2 Data link Use address resolution protocol for correct routing of messages
3 Network Use network security protocols for taking routing decisions
Provide restricted access to employees on network (SLAC, 2009)
4 Transport Use TCP for checking errors in transmission
Use UDP for a reliable transmission
5 Session Use security systems like password authentication for identification
6 Presentation Use universal standards for coding and data transfers
7 Application Install anti-virus ad anti-malware for protection (Armour, 2017)
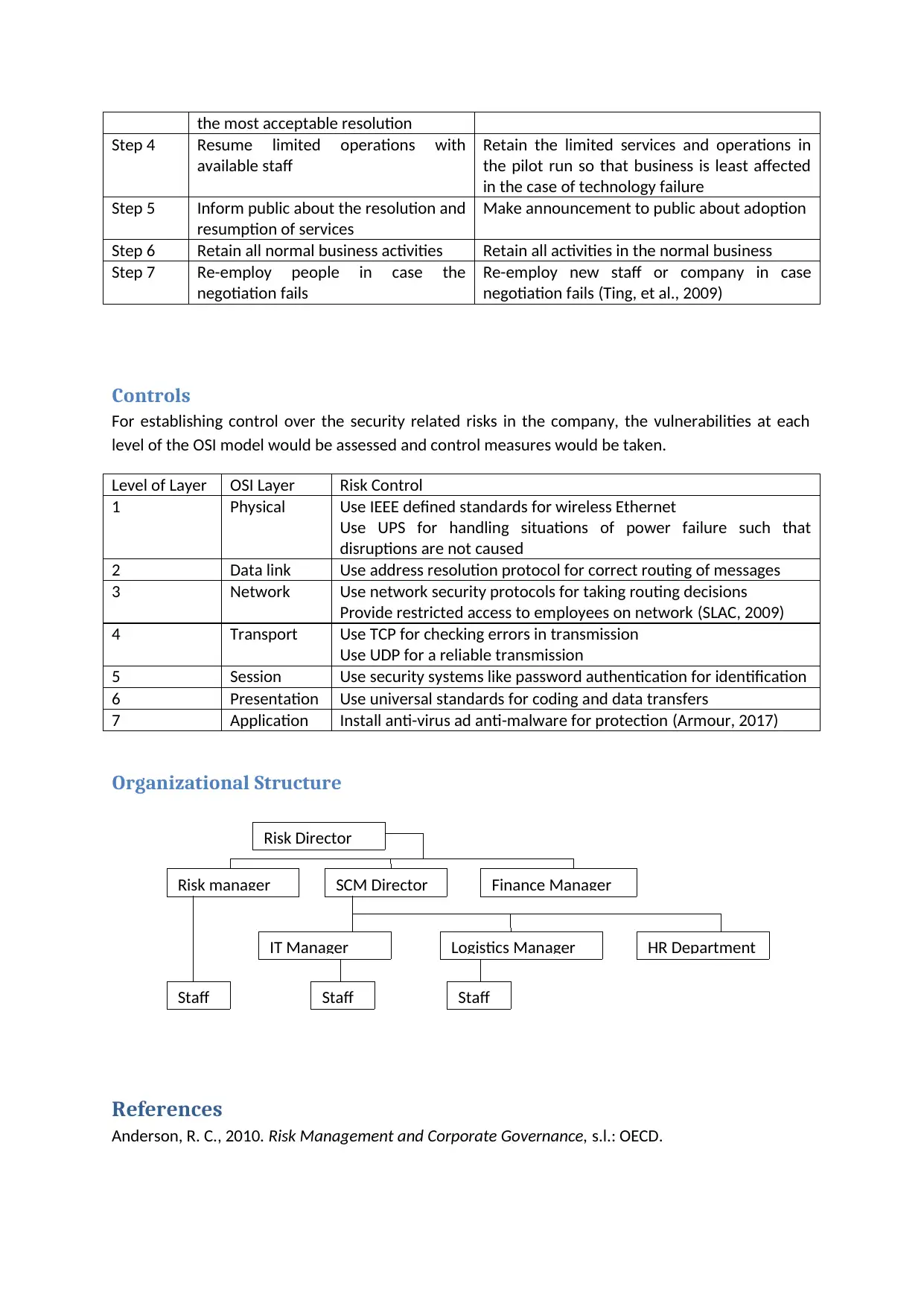
Organizational Structure
References
Anderson, R. C., 2010. Risk Management and Corporate Governance, s.l.: OECD.
Risk Director
Risk manager Finance ManagerSCM Director
IT Manager Logistics Manager HR Department
StaffStaffStaff
Step 4 Resume limited operations with
available staff
Retain the limited services and operations in
the pilot run so that business is least affected
in the case of technology failure
Step 5 Inform public about the resolution and
resumption of services
Make announcement to public about adoption
Step 6 Retain all normal business activities Retain all activities in the normal business
Step 7 Re-employ people in case the
negotiation fails
Re-employ new staff or company in case
negotiation fails (Ting, et al., 2009)
Controls
For establishing control over the security related risks in the company, the vulnerabilities at each
level of the OSI model would be assessed and control measures would be taken.
Level of Layer OSI Layer Risk Control
1 Physical Use IEEE defined standards for wireless Ethernet
Use UPS for handling situations of power failure such that
disruptions are not caused
2 Data link Use address resolution protocol for correct routing of messages
3 Network Use network security protocols for taking routing decisions
Provide restricted access to employees on network (SLAC, 2009)
4 Transport Use TCP for checking errors in transmission
Use UDP for a reliable transmission
5 Session Use security systems like password authentication for identification
6 Presentation Use universal standards for coding and data transfers
7 Application Install anti-virus ad anti-malware for protection (Armour, 2017)
Organizational Structure
References
Anderson, R. C., 2010. Risk Management and Corporate Governance, s.l.: OECD.
Risk Director
Risk manager Finance ManagerSCM Director
IT Manager Logistics Manager HR Department
StaffStaffStaff

APM Group Ltd, 2017. DEFINING RISK: THE RISK MANAGEMENT CYCLE. [Online]
Available at: https://ppp-certification.com/ppp-certification-guide/52-defining-risk-risk-
management-cycle36
[Accessed 14 September 2017].
Armour, D., 2017. Understanding Security Using the OSI Model, s.l.: SANS Institute.
Avdoshin, S. M. & Pesotskaya, E. Y., 2011. Software Risk Management: Using the Automated Tools,
s.l.: Russian Federation.
Bayne, J., 2002. An Overview of Threat and Risk Assessment, s.l.: SANS Institute .
Bodicha, H. H., 2005. How to Measure the Effect of Project Risk Management Process on the Success
of Construction Projects: A Critical Literature Review. The International Journal Of Business &
Management, 3(12), pp. 99-112.
Cooper, R., 2004. Risk Analysis and Preventing Information Systems Project Failures, s.l.: School of
Computing and Mathematical Sciences.
Curtis, P. & Carey, M., 2012. Risk Assessment in Practice, s.l.: COSO.
Delhi Government, 2014. HAZARD, RISK AND VULNERABILITY ANALYSIS, New Delhi: Delhi
Government.
Engine Yard, Inc., 2014. Security, Risk, and Compliance, s.l.: Engine Yard.
Health and Safety Authority, 2006. Guidelines on Risk Assessments and Safety Statements , Dublin:
Health and Safety Authority.
JIRA Security and Privacy Committee (SPC) , 2007. Information Security Risk Management for
Healthcare Systems , s.l.: MITA (Medical Imaging & Technology Alliance) .
OECD, 2014. Risk Management and Corporate Governance, s.l.: OECD.
SLAC, 2009. Research Support Building and Infrastructure Modernization: Risk Management Plan,
s.l.: SLAC.
Solomon Island Government, 2009. National Disaster Risk Management Plan, s.l.: SOLOMON
ISLANDS GOVER NMENT.
Ting, J. S.-L., Kwok, S.-K. & Tsang, A. H.-C., 2009. Hybrid Risk Management Methodology: A Case
Study. International Journal of Engineering Business Management, 1(1), pp. 25-32.
Available at: https://ppp-certification.com/ppp-certification-guide/52-defining-risk-risk-
management-cycle36
[Accessed 14 September 2017].
Armour, D., 2017. Understanding Security Using the OSI Model, s.l.: SANS Institute.
Avdoshin, S. M. & Pesotskaya, E. Y., 2011. Software Risk Management: Using the Automated Tools,
s.l.: Russian Federation.
Bayne, J., 2002. An Overview of Threat and Risk Assessment, s.l.: SANS Institute .
Bodicha, H. H., 2005. How to Measure the Effect of Project Risk Management Process on the Success
of Construction Projects: A Critical Literature Review. The International Journal Of Business &
Management, 3(12), pp. 99-112.
Cooper, R., 2004. Risk Analysis and Preventing Information Systems Project Failures, s.l.: School of
Computing and Mathematical Sciences.
Curtis, P. & Carey, M., 2012. Risk Assessment in Practice, s.l.: COSO.
Delhi Government, 2014. HAZARD, RISK AND VULNERABILITY ANALYSIS, New Delhi: Delhi
Government.
Engine Yard, Inc., 2014. Security, Risk, and Compliance, s.l.: Engine Yard.
Health and Safety Authority, 2006. Guidelines on Risk Assessments and Safety Statements , Dublin:
Health and Safety Authority.
JIRA Security and Privacy Committee (SPC) , 2007. Information Security Risk Management for
Healthcare Systems , s.l.: MITA (Medical Imaging & Technology Alliance) .
OECD, 2014. Risk Management and Corporate Governance, s.l.: OECD.
SLAC, 2009. Research Support Building and Infrastructure Modernization: Risk Management Plan,
s.l.: SLAC.
Solomon Island Government, 2009. National Disaster Risk Management Plan, s.l.: SOLOMON
ISLANDS GOVER NMENT.
Ting, J. S.-L., Kwok, S.-K. & Tsang, A. H.-C., 2009. Hybrid Risk Management Methodology: A Case
Study. International Journal of Engineering Business Management, 1(1), pp. 25-32.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1 out of 7