Cloud Computing Security and Privacy Report
VerifiedAdded on 2019/11/25
|22
|5610
|356
Report
AI Summary
This report analyzes the security and privacy risks associated with implementing Software-as-a-Service (SaaS) in the Department of Administrative Service (DAS). It identifies existing and new threats to employee data, including cloud computing vulnerabilities, poor configurations, and identity theft. The report presents severity matrices to assess the likelihood and impact of these risks. It also addresses privacy concerns related to surveillance and data breaches, offering preventive and contingency plans. The document further explores digital identity issues, provider solution challenges, and data sensitivity, concluding with recommendations for a secure and private SaaS implementation. The report includes a solution architecture diagram and references to support its findings.

Cloud Computing in DAS
Name of the Student
Name of the University
Author Note
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
4033 Introduction..................................................................................................................................3
Security of Employee Data....................................................................................................................3
Existing security threats to Employee data........................................................................................3
Explaining issues...............................................................................................................................5
New Security Threat to Employee data (after moving to SaaS).........................................................6
Explain issues....................................................................................................................................8
Severity Matrix......................................................................................................................................9
Privacy of Employee Data...................................................................................................................10
Existing privacy threats and risks to the privacy of employee data..................................................10
New Security Threat to Employee data (after moving to SaaS).......................................................12
Severity Matrix................................................................................................................................13
Digital Identity Issues..........................................................................................................................14
Explanation briefly..........................................................................................................................14
Provider Solution Issues and why?..................................................................................................15
Solution Architecture Including Security and Privacy.........................................................................16
Data Sensitivity...................................................................................................................................16
Appendix.............................................................................................................................................20
Group Communication....................................................................................................................20
4033 Introduction..................................................................................................................................3
Security of Employee Data....................................................................................................................3
Existing security threats to Employee data........................................................................................3
Explaining issues...............................................................................................................................5
New Security Threat to Employee data (after moving to SaaS).........................................................6
Explain issues....................................................................................................................................8
Severity Matrix......................................................................................................................................9
Privacy of Employee Data...................................................................................................................10
Existing privacy threats and risks to the privacy of employee data..................................................10
New Security Threat to Employee data (after moving to SaaS).......................................................12
Severity Matrix................................................................................................................................13
Digital Identity Issues..........................................................................................................................14
Explanation briefly..........................................................................................................................14
Provider Solution Issues and why?..................................................................................................15
Solution Architecture Including Security and Privacy.........................................................................16
Data Sensitivity...................................................................................................................................16
Appendix.............................................................................................................................................20
Group Communication....................................................................................................................20
4033 Introduction
The DAS (Department of the Administrative Service) is responsible for delivering many
services for the various departments of the state government in Australia. The data centre of
the DAS is the one who is accountable for delivering the services for the department. A new
service provider has been introduced to DAS in order to upgrade the existing system named
‘SaaS’ (Software-as-a-Service), which is a centrally hosting licensed model and software
delivery services. A team of two members is being introduced to the management for the
delivery of a risk management program, which will be helpful in identifying the threats and
risks to the privacy and security of employee’s data, who are employed in DAS. Following
report presents a severity matrix in order to show the likelihood, priority and the impact of
the identified risks and threats. They are rated based on the consideration.
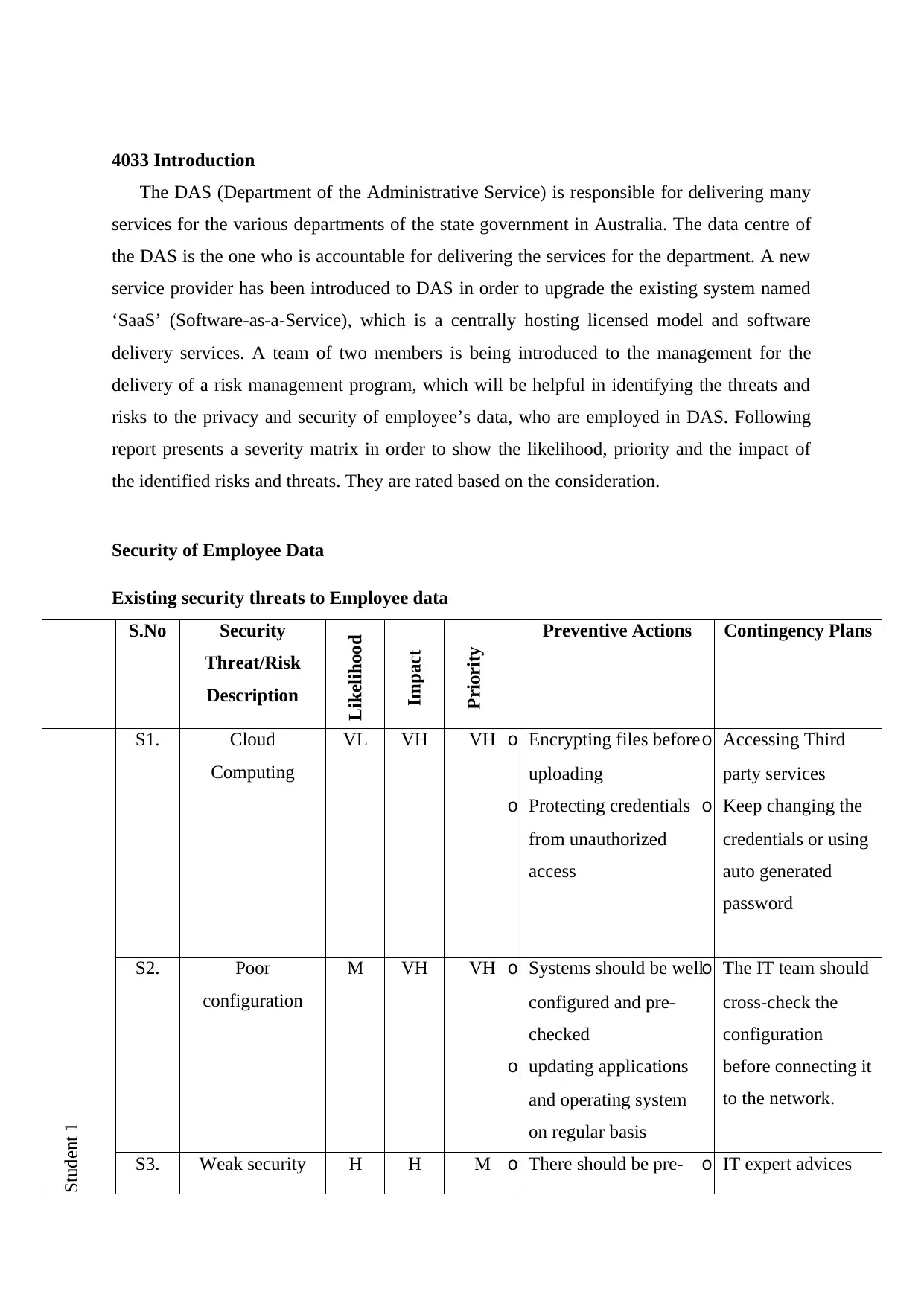
Security of Employee Data
Existing security threats to Employee data
S.No Security
Threat/Risk
Description
Likelihood
Impact
Priority Preventive Actions Contingency Plans
Student 1
S1. Cloud
Computing
VL VH VH o Encrypting files before
uploading
o Protecting credentials
from unauthorized
access
o Accessing Third
party services
o Keep changing the
credentials or using
auto generated
password
S2. Poor
configuration
M VH VH o Systems should be well
configured and pre-
checked
o updating applications
and operating system
on regular basis
o The IT team should
cross-check the
configuration
before connecting it
to the network.
S3. Weak security H H M o There should be pre- o IT expert advices
The DAS (Department of the Administrative Service) is responsible for delivering many
services for the various departments of the state government in Australia. The data centre of
the DAS is the one who is accountable for delivering the services for the department. A new
service provider has been introduced to DAS in order to upgrade the existing system named
‘SaaS’ (Software-as-a-Service), which is a centrally hosting licensed model and software
delivery services. A team of two members is being introduced to the management for the
delivery of a risk management program, which will be helpful in identifying the threats and
risks to the privacy and security of employee’s data, who are employed in DAS. Following
report presents a severity matrix in order to show the likelihood, priority and the impact of
the identified risks and threats. They are rated based on the consideration.
Security of Employee Data
Existing security threats to Employee data
S.No Security
Threat/Risk
Description
Likelihood
Impact
Priority Preventive Actions Contingency Plans
Student 1
S1. Cloud
Computing
VL VH VH o Encrypting files before
uploading
o Protecting credentials
from unauthorized
access
o Accessing Third
party services
o Keep changing the
credentials or using
auto generated
password
S2. Poor
configuration
M VH VH o Systems should be well
configured and pre-
checked
o updating applications
and operating system
on regular basis
o The IT team should
cross-check the
configuration
before connecting it
to the network.
S3. Weak security H H M o There should be pre- o IT expert advices
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
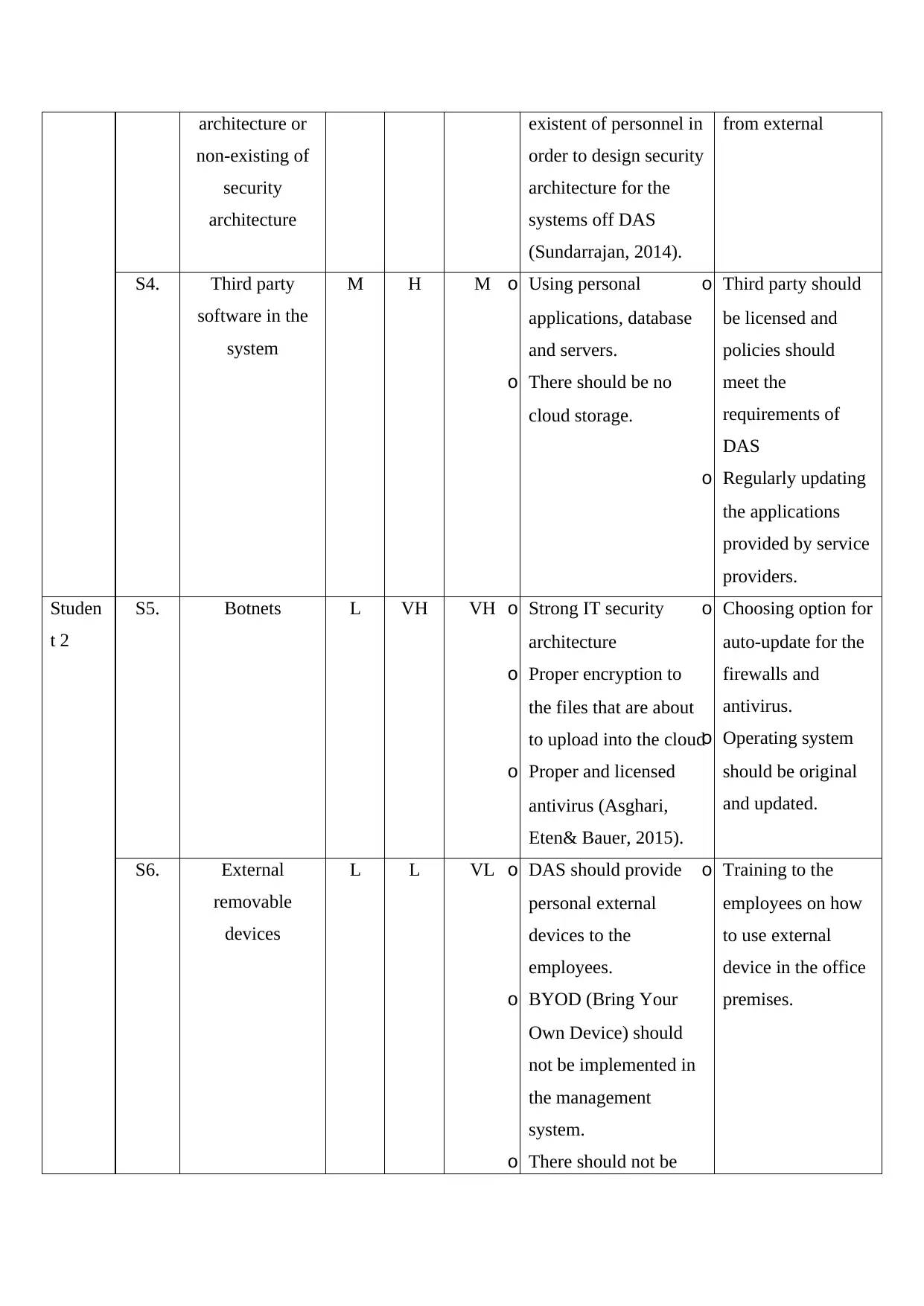
architecture or
non-existing of
security
architecture
existent of personnel in
order to design security
architecture for the
systems off DAS
(Sundarrajan, 2014).
from external
S4. Third party
software in the
system
M H M o Using personal
applications, database
and servers.
o There should be no
cloud storage.
o Third party should
be licensed and
policies should
meet the
requirements of
DAS
o Regularly updating
the applications
provided by service
providers.
Studen
t 2
S5. Botnets L VH VH o Strong IT security
architecture
o Proper encryption to
the files that are about
to upload into the cloud
o Proper and licensed
antivirus (Asghari,
Eten& Bauer, 2015).
o Choosing option for
auto-update for the
firewalls and
antivirus.
o Operating system
should be original
and updated.
S6. External
removable
devices
L L VL o DAS should provide
personal external
devices to the
employees.
o BYOD (Bring Your
Own Device) should
not be implemented in
the management
system.
o There should not be
o Training to the
employees on how
to use external
device in the office
premises.
non-existing of
security
architecture
existent of personnel in
order to design security
architecture for the
systems off DAS
(Sundarrajan, 2014).
from external
S4. Third party
software in the
system
M H M o Using personal
applications, database
and servers.
o There should be no
cloud storage.
o Third party should
be licensed and
policies should
meet the
requirements of
DAS
o Regularly updating
the applications
provided by service
providers.
Studen
t 2
S5. Botnets L VH VH o Strong IT security
architecture
o Proper encryption to
the files that are about
to upload into the cloud
o Proper and licensed
antivirus (Asghari,
Eten& Bauer, 2015).
o Choosing option for
auto-update for the
firewalls and
antivirus.
o Operating system
should be original
and updated.
S6. External
removable
devices
L L VL o DAS should provide
personal external
devices to the
employees.
o BYOD (Bring Your
Own Device) should
not be implemented in
the management
system.
o There should not be
o Training to the
employees on how
to use external
device in the office
premises.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
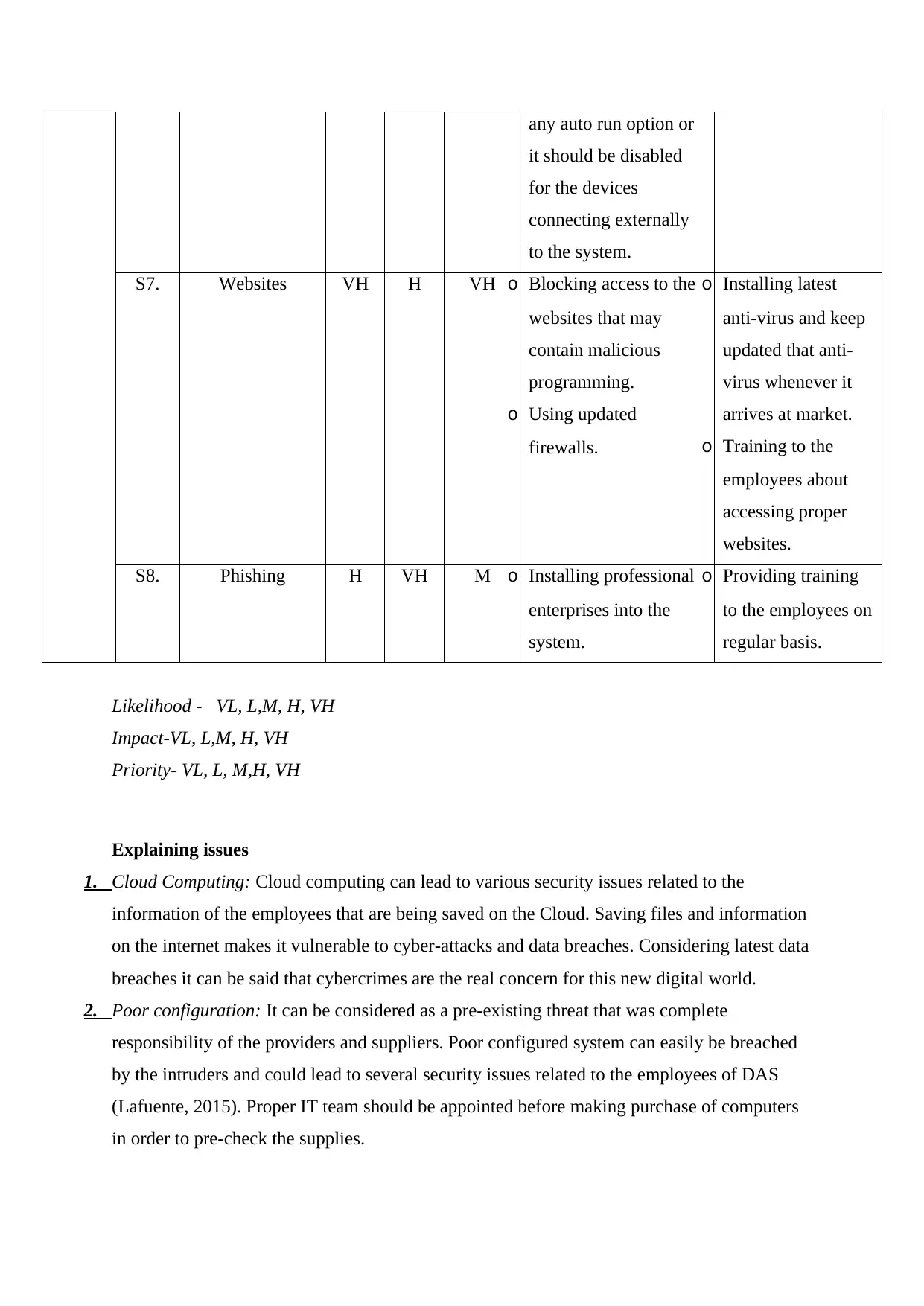
any auto run option or
it should be disabled
for the devices
connecting externally
to the system.
S7. Websites VH H VH o Blocking access to the
websites that may
contain malicious
programming.
o Using updated
firewalls.
o Installing latest
anti-virus and keep
updated that anti-
virus whenever it
arrives at market.
o Training to the
employees about
accessing proper
websites.
S8. Phishing H VH M o Installing professional
enterprises into the
system.
o Providing training
to the employees on
regular basis.
Likelihood - VL, L,M, H, VH
Impact-VL, L,M, H, VH
Priority- VL, L, M,H, VH
Explaining issues
1. Cloud Computing: Cloud computing can lead to various security issues related to the
information of the employees that are being saved on the Cloud. Saving files and information
on the internet makes it vulnerable to cyber-attacks and data breaches. Considering latest data
breaches it can be said that cybercrimes are the real concern for this new digital world.
2. Poor configuration: It can be considered as a pre-existing threat that was complete
responsibility of the providers and suppliers. Poor configured system can easily be breached
by the intruders and could lead to several security issues related to the employees of DAS
(Lafuente, 2015). Proper IT team should be appointed before making purchase of computers
in order to pre-check the supplies.
it should be disabled
for the devices
connecting externally
to the system.
S7. Websites VH H VH o Blocking access to the
websites that may
contain malicious
programming.
o Using updated
firewalls.
o Installing latest
anti-virus and keep
updated that anti-
virus whenever it
arrives at market.
o Training to the
employees about
accessing proper
websites.
S8. Phishing H VH M o Installing professional
enterprises into the
system.
o Providing training
to the employees on
regular basis.
Likelihood - VL, L,M, H, VH
Impact-VL, L,M, H, VH
Priority- VL, L, M,H, VH
Explaining issues
1. Cloud Computing: Cloud computing can lead to various security issues related to the
information of the employees that are being saved on the Cloud. Saving files and information
on the internet makes it vulnerable to cyber-attacks and data breaches. Considering latest data
breaches it can be said that cybercrimes are the real concern for this new digital world.
2. Poor configuration: It can be considered as a pre-existing threat that was complete
responsibility of the providers and suppliers. Poor configured system can easily be breached
by the intruders and could lead to several security issues related to the employees of DAS
(Lafuente, 2015). Proper IT team should be appointed before making purchase of computers
in order to pre-check the supplies.

3. Weak security architecture or non-existing of security architecture: Weak security
architecture of the network is another important aspect that can lead expose of personal and
sensitive information and alternatively affect the security of the employees and the
organization too. There should be updated and always presence of a security architecture for
the network that is being used within the organization.
4. Third party software in the system: Using third party software makes the organization
completely reliable on that organization, which makes them dependent to those third party on
“what, when and how” that data should be used. Nothing is stable in this digital world
specially, with respect to the information system. Breaches that affect the third party will
automatically affect the information and data of the organization, which was relied on those
third parties.
5. Botnets:Botnets are not a new concept in the cybercrime. They are being used in order to get
access to the systems whose access is highly secured. These could be spread into the system
by mails, files or several other means and allow unauthorized users to access the system.
6. External removable devices: Many malware coding can be transferred to the systems in
which those devices had been used(Felbermayr, Hauptmann &Schmerer, 2014). Not all the
computers are safe and using external devices could lead towards transferring of those
malicious viruses from one system to another.
7. Websites: Generally using untrusted websites leads toward download of malicious coding
that could harm the system. These websites often asks to download applications that are not
certified or licensed. Using secured, certified and safe websites should be the first step in
order to keep the data secured into the system.
8. Phishing: It is term used in computer science generally related to transfer of malicious
programs via emails or messages.
New Security Threat to Employee data(after moving to SaaS)
S.No New Security
Threat/Risk of
employee data
Description
(after moving to
Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
architecture of the network is another important aspect that can lead expose of personal and
sensitive information and alternatively affect the security of the employees and the
organization too. There should be updated and always presence of a security architecture for
the network that is being used within the organization.
4. Third party software in the system: Using third party software makes the organization
completely reliable on that organization, which makes them dependent to those third party on
“what, when and how” that data should be used. Nothing is stable in this digital world
specially, with respect to the information system. Breaches that affect the third party will
automatically affect the information and data of the organization, which was relied on those
third parties.
5. Botnets:Botnets are not a new concept in the cybercrime. They are being used in order to get
access to the systems whose access is highly secured. These could be spread into the system
by mails, files or several other means and allow unauthorized users to access the system.
6. External removable devices: Many malware coding can be transferred to the systems in
which those devices had been used(Felbermayr, Hauptmann &Schmerer, 2014). Not all the
computers are safe and using external devices could lead towards transferring of those
malicious viruses from one system to another.
7. Websites: Generally using untrusted websites leads toward download of malicious coding
that could harm the system. These websites often asks to download applications that are not
certified or licensed. Using secured, certified and safe websites should be the first step in
order to keep the data secured into the system.
8. Phishing: It is term used in computer science generally related to transfer of malicious
programs via emails or messages.
New Security Threat to Employee data(after moving to SaaS)
S.No New Security
Threat/Risk of
employee data
Description
(after moving to
Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
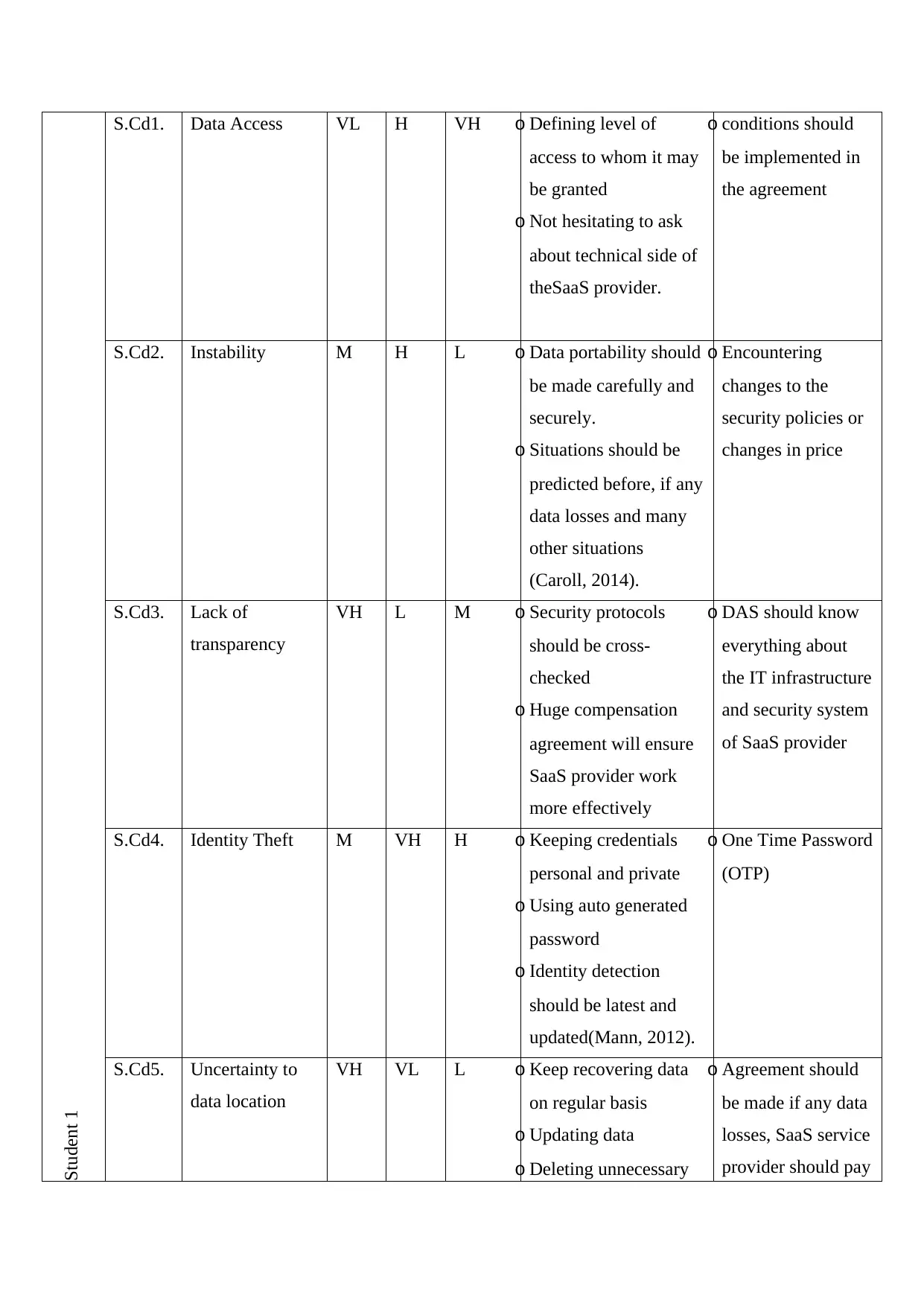
Student 1
S.Cd1. Data Access VL H VH o Defining level of
access to whom it may
be granted
o Not hesitating to ask
about technical side of
theSaaS provider.
o conditions should
be implemented in
the agreement
S.Cd2. Instability M H L o Data portability should
be made carefully and
securely.
o Situations should be
predicted before, if any
data losses and many
other situations
(Caroll, 2014).
o Encountering
changes to the
security policies or
changes in price
S.Cd3. Lack of
transparency
VH L M o Security protocols
should be cross-
checked
o Huge compensation
agreement will ensure
SaaS provider work
more effectively
o DAS should know
everything about
the IT infrastructure
and security system
of SaaS provider
S.Cd4. Identity Theft M VH H o Keeping credentials
personal and private
o Using auto generated
password
o Identity detection
should be latest and
updated(Mann, 2012).
o One Time Password
(OTP)
S.Cd5. Uncertainty to
data location
VH VL L o Keep recovering data
on regular basis
o Updating data
o Deleting unnecessary
o Agreement should
be made if any data
losses, SaaS service
provider should pay
S.Cd1. Data Access VL H VH o Defining level of
access to whom it may
be granted
o Not hesitating to ask
about technical side of
theSaaS provider.
o conditions should
be implemented in
the agreement
S.Cd2. Instability M H L o Data portability should
be made carefully and
securely.
o Situations should be
predicted before, if any
data losses and many
other situations
(Caroll, 2014).
o Encountering
changes to the
security policies or
changes in price
S.Cd3. Lack of
transparency
VH L M o Security protocols
should be cross-
checked
o Huge compensation
agreement will ensure
SaaS provider work
more effectively
o DAS should know
everything about
the IT infrastructure
and security system
of SaaS provider
S.Cd4. Identity Theft M VH H o Keeping credentials
personal and private
o Using auto generated
password
o Identity detection
should be latest and
updated(Mann, 2012).
o One Time Password
(OTP)
S.Cd5. Uncertainty to
data location
VH VL L o Keep recovering data
on regular basis
o Updating data
o Deleting unnecessary
o Agreement should
be made if any data
losses, SaaS service
provider should pay
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
data the compensation
Student 2
S.Cd6. Paying Long-
term and upfront
VH VL VL o DAS should chose
smallest service time
o Post-paid service
can be helpful
S.Cd7. Agreement made
is unsure
VH M L o DAS should check all
the conditions apply
and policies of the
service provider and
check either it meets
with the policies of
DAS or not
o Agreement should
made by the DAS.
S.Cd8. How data is
actually being
secured
L H VH o DAS should use
encryption to the data
before sending it to the
SaaS service providers.
o Regular audit on the
data that are being
saved
S.Cd9. No direct control
over the data
H VL M o The management
should decide which
data should be
uploaded to the cloud
or which should not
o Only not important
data should be
uploaded over the
Cloud.
S.Cd10. Do not update
with modern
security
standards
VH VH VH o Service provider
should provide updated
security measures
o The service
provider should be
reminded again and
again to update the
security
Likelihood - VL, L,M, H, VH
Impact- - VL, L,M, H, VH
Priority- - VL, L, M,H, VH
Explain issues
Student 2
S.Cd6. Paying Long-
term and upfront
VH VL VL o DAS should chose
smallest service time
o Post-paid service
can be helpful
S.Cd7. Agreement made
is unsure
VH M L o DAS should check all
the conditions apply
and policies of the
service provider and
check either it meets
with the policies of
DAS or not
o Agreement should
made by the DAS.
S.Cd8. How data is
actually being
secured
L H VH o DAS should use
encryption to the data
before sending it to the
SaaS service providers.
o Regular audit on the
data that are being
saved
S.Cd9. No direct control
over the data
H VL M o The management
should decide which
data should be
uploaded to the cloud
or which should not
o Only not important
data should be
uploaded over the
Cloud.
S.Cd10. Do not update
with modern
security
standards
VH VH VH o Service provider
should provide updated
security measures
o The service
provider should be
reminded again and
again to update the
security
Likelihood - VL, L,M, H, VH
Impact- - VL, L,M, H, VH
Priority- - VL, L, M,H, VH
Explain issues

1. Data Access:Employees if not trained well, might access to the websites that can upload or
download malicious coding into the system. This coding has capability to corrupt, manipulate
and delete the data and information that are being saved to the database system.
2. Instability:SaaS (Software as a service) does not show stability of data. Uploading or porting
data into the Cloud could be a hassle for the organization and management of the
organization, who is responsible for data management. Proper policies should be introduced
related to the issue that might affect the security of DAS’s employees (Pfeifer, 2016).
3. Lack of transparency:SaaS cannot provide transparency of its working to the customers,
which raises a concern of distrust on the service provider. Several security questions are
being unanswerable to the clients like DAS. This creates an empty space and speculation
about the services that are being offered by the SaaS.
4. Identity Theft: Making payment to this service provider through credit cards is a matter of
risk and raise concern towards potential risk it may arises. Identity management can be within
the LDAP directions of the company, inside the firewall of the firm, or on the SaaSwebsite of
providers in order to make system more secure (Kristal, 2017).
5. Uncertainty to data location: The data is being stored in the cloud, which is a virtual space to
save data and information raises concern about the uncertainty to the location, where the data
is being saved. In this case even the headquarters are separated and situated far away from the
location of the firm.
6. Paying Long-term and upfront:SaaS does not provide any short-term services, which can be
irrespective to the changes made in policies or if an organization does not need any services.
After the payment, service is being offered. However, that is matter of security concern for
the customers or the clients.
7. Agreement made is unsure: agreement papers are generally big documented agreements,
which in general no one bothers to read or if read properly individual customers might have
many problems regarding the security of the information, which is being shared with the third
party(Müller & Neumann, 2015).
8. How data is actually being secured: As stated above SaaS is not agree to expose the security
architecture for its services led individuals concerns regarding, whether the data moving to
cloud by SaaS will be safe or not safe.
9. No direct control over the data: Data will be helpless in controlling the data after uploading
them into Cloud. After moving to SaaS, DAS will have to completely rely on them for any
data or information related to the employee or any operational or transactional details (Smith
& Ross, 2014).
download malicious coding into the system. This coding has capability to corrupt, manipulate
and delete the data and information that are being saved to the database system.
2. Instability:SaaS (Software as a service) does not show stability of data. Uploading or porting
data into the Cloud could be a hassle for the organization and management of the
organization, who is responsible for data management. Proper policies should be introduced
related to the issue that might affect the security of DAS’s employees (Pfeifer, 2016).
3. Lack of transparency:SaaS cannot provide transparency of its working to the customers,
which raises a concern of distrust on the service provider. Several security questions are
being unanswerable to the clients like DAS. This creates an empty space and speculation
about the services that are being offered by the SaaS.
4. Identity Theft: Making payment to this service provider through credit cards is a matter of
risk and raise concern towards potential risk it may arises. Identity management can be within
the LDAP directions of the company, inside the firewall of the firm, or on the SaaSwebsite of
providers in order to make system more secure (Kristal, 2017).
5. Uncertainty to data location: The data is being stored in the cloud, which is a virtual space to
save data and information raises concern about the uncertainty to the location, where the data
is being saved. In this case even the headquarters are separated and situated far away from the
location of the firm.
6. Paying Long-term and upfront:SaaS does not provide any short-term services, which can be
irrespective to the changes made in policies or if an organization does not need any services.
After the payment, service is being offered. However, that is matter of security concern for
the customers or the clients.
7. Agreement made is unsure: agreement papers are generally big documented agreements,
which in general no one bothers to read or if read properly individual customers might have
many problems regarding the security of the information, which is being shared with the third
party(Müller & Neumann, 2015).
8. How data is actually being secured: As stated above SaaS is not agree to expose the security
architecture for its services led individuals concerns regarding, whether the data moving to
cloud by SaaS will be safe or not safe.
9. No direct control over the data: Data will be helpless in controlling the data after uploading
them into Cloud. After moving to SaaS, DAS will have to completely rely on them for any
data or information related to the employee or any operational or transactional details (Smith
& Ross, 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
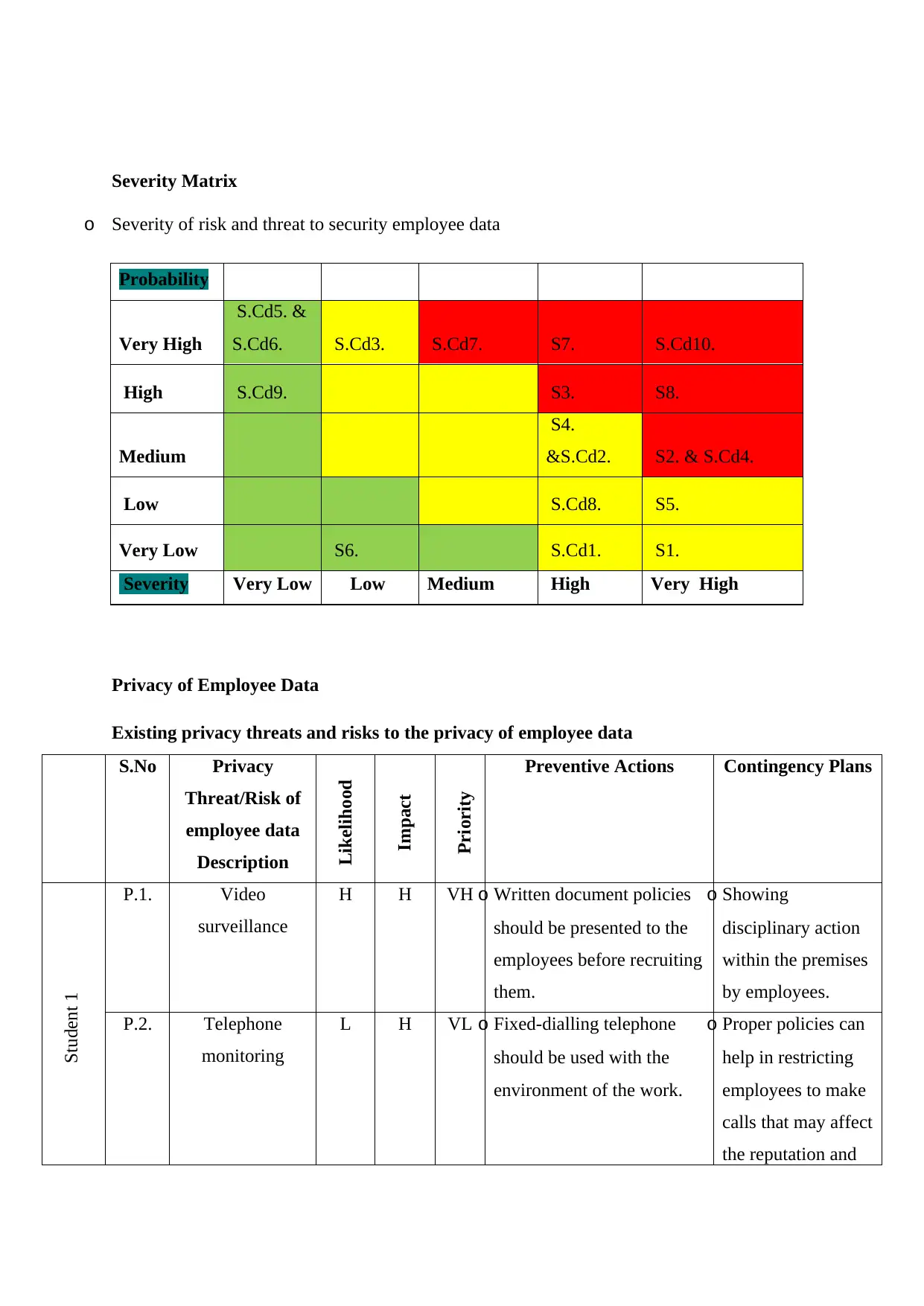
Severity Matrix
o Severity of risk and threat to security employee data
Probability
Very High
S.Cd5. &
S.Cd6. S.Cd3. S.Cd7. S7. S.Cd10.
High S.Cd9. S3. S8.
Medium
S4.
&S.Cd2. S2. & S.Cd4.
Low S.Cd8. S5.
Very Low S6. S.Cd1. S1.
Severity Very Low Low Medium High Very High
Privacy of Employee Data
Existing privacy threats and risks to the privacy of employee data
S.No Privacy
Threat/Risk of
employee data
Description
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
P.1. Video
surveillance
H H VH o Written document policies
should be presented to the
employees before recruiting
them.
o Showing
disciplinary action
within the premises
by employees.
P.2. Telephone
monitoring
L H VL o Fixed-dialling telephone
should be used with the
environment of the work.
o Proper policies can
help in restricting
employees to make
calls that may affect
the reputation and
o Severity of risk and threat to security employee data
Probability
Very High
S.Cd5. &
S.Cd6. S.Cd3. S.Cd7. S7. S.Cd10.
High S.Cd9. S3. S8.
Medium
S4.
&S.Cd2. S2. & S.Cd4.
Low S.Cd8. S5.
Very Low S6. S.Cd1. S1.
Severity Very Low Low Medium High Very High
Privacy of Employee Data
Existing privacy threats and risks to the privacy of employee data
S.No Privacy
Threat/Risk of
employee data
Description
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
P.1. Video
surveillance
H H VH o Written document policies
should be presented to the
employees before recruiting
them.
o Showing
disciplinary action
within the premises
by employees.
P.2. Telephone
monitoring
L H VL o Fixed-dialling telephone
should be used with the
environment of the work.
o Proper policies can
help in restricting
employees to make
calls that may affect
the reputation and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
performance of the
organization.
P.3. Internet usage
monitoring
L VH VH o Updated and original
firewalls, operating system
and secured network(Miller,
2012).
o Training to the
employees on how
to surf and what to
surf on the internet.
Student 2
P.4. Computer
monitoring
VH L H o Original softwares,
applications and hardware
as per the need should be
provided by DAS(Miller,
2012).
o Blocking domains
and restricting
usage
P.5. Email
monitoring
M H VH o Private messaging websites
(portal) for organization’s
daily operational activities.
o Agreement should
be made in order to
compromising both
employees and the
organization.
P.6. Mobile device
monitoring
VL M L o Bring-your-own-device
(BYOD) should be
restricted in the office
premises or work
environments.
o Training programs
and better policies.
Explain issues
1. Video surveillance: video surveillance will be beneficial, only with the perspective of the
organization but it can affect the privacy of the employees at work places. Video surveillance
can help in protecting organizational personal assets but it will also raise privacy concern to
the employees working in that environment(Kristal, 2017).
2. Telephone monitoring:It is another issue related to the privacy of the employees, it could
expose the privacy to whom and what an individual is talking. Those conversations may be
very personal for the individual, which he or she does not wanted to expose to anyone.
3. Internet usage monitoring: Organization generally monitors the internet usage of the
employee, especially those whose operational activities are connected to the internet (Finkin,
organization.
P.3. Internet usage
monitoring
L VH VH o Updated and original
firewalls, operating system
and secured network(Miller,
2012).
o Training to the
employees on how
to surf and what to
surf on the internet.
Student 2
P.4. Computer
monitoring
VH L H o Original softwares,
applications and hardware
as per the need should be
provided by DAS(Miller,
2012).
o Blocking domains
and restricting
usage
P.5. Email
monitoring
M H VH o Private messaging websites
(portal) for organization’s
daily operational activities.
o Agreement should
be made in order to
compromising both
employees and the
organization.
P.6. Mobile device
monitoring
VL M L o Bring-your-own-device
(BYOD) should be
restricted in the office
premises or work
environments.
o Training programs
and better policies.
Explain issues
1. Video surveillance: video surveillance will be beneficial, only with the perspective of the
organization but it can affect the privacy of the employees at work places. Video surveillance
can help in protecting organizational personal assets but it will also raise privacy concern to
the employees working in that environment(Kristal, 2017).
2. Telephone monitoring:It is another issue related to the privacy of the employees, it could
expose the privacy to whom and what an individual is talking. Those conversations may be
very personal for the individual, which he or she does not wanted to expose to anyone.
3. Internet usage monitoring: Organization generally monitors the internet usage of the
employee, especially those whose operational activities are connected to the internet (Finkin,
2015). This could lead proper internet usage by the employees at workplaces but will, no-
doubt affect the privacy of the individual.
4. Computer monitoring: Computer monitoring is another general likelihood of several
organizations that might affect the privacy of the individuals, as there may be personal media
files, which an individual is unwilling to expose to others without his or her permission.
5. Email monitoring: Email is generally used for personal messages and contains very personal
information related to the personal life of the individual, which no one would ever like to
expose to an unwanted individual. Accessing this information without the will of the
employees exposes their privacy into real world.
6. Mobile device monitoring: Mobile devices of individual information that can be considered
as personal and private information and monitoring this will be against the policies of FERPA
and will violate those policies.
New Security Threat to Employee data(after moving to SaaS)
S.No New Privacy
Threat/Risk of
employee data
Description
(after moving to
Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
P.Cd1. Data and
information may
be compromised
H VH VH o Encrypting all the files
before uploading to the
Cloud
o Tokenization of files
o Using protected server
o Involving third
party for the
system.
P.Cd2. Types of
information
saved
VL L L o Categorizing data into
different groups
o Very personal information
should not be uploaded
(Humphreys, 2016).
o Suggestions or
permission of the
employees on
which data they
want to upload.
doubt affect the privacy of the individual.
4. Computer monitoring: Computer monitoring is another general likelihood of several
organizations that might affect the privacy of the individuals, as there may be personal media
files, which an individual is unwilling to expose to others without his or her permission.
5. Email monitoring: Email is generally used for personal messages and contains very personal
information related to the personal life of the individual, which no one would ever like to
expose to an unwanted individual. Accessing this information without the will of the
employees exposes their privacy into real world.
6. Mobile device monitoring: Mobile devices of individual information that can be considered
as personal and private information and monitoring this will be against the policies of FERPA
and will violate those policies.
New Security Threat to Employee data(after moving to SaaS)
S.No New Privacy
Threat/Risk of
employee data
Description
(after moving to
Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
P.Cd1. Data and
information may
be compromised
H VH VH o Encrypting all the files
before uploading to the
Cloud
o Tokenization of files
o Using protected server
o Involving third
party for the
system.
P.Cd2. Types of
information
saved
VL L L o Categorizing data into
different groups
o Very personal information
should not be uploaded
(Humphreys, 2016).
o Suggestions or
permission of the
employees on
which data they
want to upload.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





