Analysis of UX, Sensors, IoT, and Privacy in Modern Technology
VerifiedAdded on 2020/02/24
|8
|1804
|70
Report
AI Summary
This report delves into various aspects of modern technology, focusing on user experience (UX), sensors, and the Internet of Things (IoT). It examines the complexities of interfaces, the paradox of choice, and the efforts of companies like Google and Facebook in relation to user experience. The report analyzes different cable types, including UTP and STP, and discusses the role of sensors in IoT, along with applications like RFID and video tracking. It also highlights the privacy issues associated with IoT, including data communication, unique identifiers, and business process considerations. Furthermore, the report explores bandwidth considerations and the impact of Nielsen's Law, which provides a framework for understanding the growth of user bandwidth and its implications for technology design and user experience. The report also provides references to support the arguments made within the report.
report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1:
The interfaces are generally found to be making a life of an individual complicated when there
are convoluted applications on the mobile phone for even unlocking the door of the car. With
this, there are interfaces like the sign up and then using all the mandatory signs for surfing on
any website. The screen based thinking with the good designing also helps in solving the issues
but they are not limited to the wireframe GUI. The options set for this are paradox of choice
which directs towards the procrastinated level. The companies like Google and Facebook are
working hard for keeping their hold on the shareholders rather than the GUI. (Cheng et al, 2017).
Some of the examples which could be seen are the sensors and the automation which could lead
to some of the seamless UX, where the hospital example with the sensors of the patient and the
automatic alerts are given to the doctors, car air bags and the detection of the athletes injuries,
the automatic door sliding is also seen to be a seamless option where there is no need of the User
Interface.
The GUI can also be important for some of the places where there is a need of the smart lamp
example which is considered to have the GUI for a proper overriding and tune setting.
(Dastjerdiet al.,2016)
2:
Twister Pair Cable Coaxial optic Fibre
Bandwidth 0-4Khz 0 to 500 Mhz 186-350 Thz
Distance 3km 10km 40 km
The interfaces are generally found to be making a life of an individual complicated when there
are convoluted applications on the mobile phone for even unlocking the door of the car. With
this, there are interfaces like the sign up and then using all the mandatory signs for surfing on
any website. The screen based thinking with the good designing also helps in solving the issues
but they are not limited to the wireframe GUI. The options set for this are paradox of choice
which directs towards the procrastinated level. The companies like Google and Facebook are
working hard for keeping their hold on the shareholders rather than the GUI. (Cheng et al, 2017).
Some of the examples which could be seen are the sensors and the automation which could lead
to some of the seamless UX, where the hospital example with the sensors of the patient and the
automatic alerts are given to the doctors, car air bags and the detection of the athletes injuries,
the automatic door sliding is also seen to be a seamless option where there is no need of the User
Interface.
The GUI can also be important for some of the places where there is a need of the smart lamp
example which is considered to have the GUI for a proper overriding and tune setting.
(Dastjerdiet al.,2016)
2:
Twister Pair Cable Coaxial optic Fibre
Bandwidth 0-4Khz 0 to 500 Mhz 186-350 Thz
Distance 3km 10km 40 km
Interference rating Medium level Medium level Lower level
Cost Less than coaxial Medium High
Security Medium Medium High
There are some of the other cables which are included:
1. The UTP includes the connections with the settings that are for the proper connections
setup with the connector. With this, there are costs related to the UTP which seems to be
working on the different ranges that are for the varying speed from 1 to 10000 Mbps. The
use is to handle the attenuation setup with the ranges to determine the system security.
2. The STP is the Shielded Twisted Pair which is for the handling of interference which is
medium and then the cost that is seen to be medium to afford. It requires a safety and
distance is medium more than UTP (Hinckley, 2017).
3. The radio range cost from low to medium and there are setups based on the standardized
power of attenuation. It works for the processing which includes the signal depending
upon the response with the feasibility that is for the interferences that amounts to a lesser
security.
3:
Sensors
The sensors are for the IoT
with the growth of the smart
RFID
It includes the Radio-
Frequency Identification
Video Tracking
The video tracking is
considered to involve the
Cost Less than coaxial Medium High
Security Medium Medium High
There are some of the other cables which are included:
1. The UTP includes the connections with the settings that are for the proper connections
setup with the connector. With this, there are costs related to the UTP which seems to be
working on the different ranges that are for the varying speed from 1 to 10000 Mbps. The
use is to handle the attenuation setup with the ranges to determine the system security.
2. The STP is the Shielded Twisted Pair which is for the handling of interference which is
medium and then the cost that is seen to be medium to afford. It requires a safety and
distance is medium more than UTP (Hinckley, 2017).
3. The radio range cost from low to medium and there are setups based on the standardized
power of attenuation. It works for the processing which includes the signal depending
upon the response with the feasibility that is for the interferences that amounts to a lesser
security.
3:
Sensors
The sensors are for the IoT
with the growth of the smart
RFID
It includes the Radio-
Frequency Identification
Video Tracking
The video tracking is
considered to involve the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
technology that helps in
bringing the connectivity in
the system and handling the
supply chain. It works with
the smart sensors which
includes the RFID with the
tags, and then serve the
different purposes. The
identification of the items,
location and then determining
the environmental conditions
is based on the supply chain
management and the
manufacturing. The
applications are the
healthcare, measuring
temperature etc.
The major disadvantage to
this is the loss of the jobs of
the people due to the
increased technology use.
where the reference to the
small electronic devices is
considered to be handling the
information. The RFID is
important for the ATM cards
and the credit cards for the
transactions of data. Here, the
RFID devices are set for the
high frequency devices which
includes the technology
handling the different tags.
(Roca et al.,2016).
The major disadvantage to
this is the reader collision
with the tagging issues. For
this, it is important to check
on how the readers are able to
receive the signals and then
work on the systems which
will be to avoid any problems
with the tag collision that
occurs when the tags are in
the small area. The issue is
different analytics where the
technology is based on how
the learning algorithms are
able to work on allowing the
cameras for recognizing the
people, objects and the
different situations. For this,
the IoT applications are for
the propelling growth and
then examining the
opportunities with the use
case, settings and the
technology. The applications
they are used in are the
cameras or the vision sensors
which are used with the video
capability and the visual data
complex feeds. The advanced
pattern recognition and the
multidimensional decisions
are important to work on the
multiple variables as well.
bringing the connectivity in
the system and handling the
supply chain. It works with
the smart sensors which
includes the RFID with the
tags, and then serve the
different purposes. The
identification of the items,
location and then determining
the environmental conditions
is based on the supply chain
management and the
manufacturing. The
applications are the
healthcare, measuring
temperature etc.
The major disadvantage to
this is the loss of the jobs of
the people due to the
increased technology use.
where the reference to the
small electronic devices is
considered to be handling the
information. The RFID is
important for the ATM cards
and the credit cards for the
transactions of data. Here, the
RFID devices are set for the
high frequency devices which
includes the technology
handling the different tags.
(Roca et al.,2016).
The major disadvantage to
this is the reader collision
with the tagging issues. For
this, it is important to check
on how the readers are able to
receive the signals and then
work on the systems which
will be to avoid any problems
with the tag collision that
occurs when the tags are in
the small area. The issue is
different analytics where the
technology is based on how
the learning algorithms are
able to work on allowing the
cameras for recognizing the
people, objects and the
different situations. For this,
the IoT applications are for
the propelling growth and
then examining the
opportunities with the use
case, settings and the
technology. The applications
they are used in are the
cameras or the vision sensors
which are used with the video
capability and the visual data
complex feeds. The advanced
pattern recognition and the
multidimensional decisions
are important to work on the
multiple variables as well.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
also related to the reading
time with the easy vendors
working on the development
of the systems and then
responding to the tags at a
time (Romero et al., 2016).
The issues are the privacy
issues where some of the
users are uneasy and then
they try to monitor the
different situations with the
production line workers. The
technology is based on how
the demographic information
like the genders and the ages
of the shoppers could be
tracked.
4:
The issues and the privacy is based on how the individuals are set from the exposure in IoT and
work towards the protection of the environment with the physical and logical entities. The
unique identifier is for handling the communication and work on the transmission of the data
which works on conjunction to the other end points. Hence, for this, the communication is based
on the networked elements where the fragmented data needs to be analyzed and worked upon.
The networking is based on the globalized connectivity and the transfer of the data where the
product designing is set with allowing to request the Wi-Fi credentials for proper access to the
network. Here, the privacy and the security issues are evaluated based on the patterns where
there is a need to check the authentication of the data with the retrieval of the address and the
time with the easy vendors
working on the development
of the systems and then
responding to the tags at a
time (Romero et al., 2016).
The issues are the privacy
issues where some of the
users are uneasy and then
they try to monitor the
different situations with the
production line workers. The
technology is based on how
the demographic information
like the genders and the ages
of the shoppers could be
tracked.
4:
The issues and the privacy is based on how the individuals are set from the exposure in IoT and
work towards the protection of the environment with the physical and logical entities. The
unique identifier is for handling the communication and work on the transmission of the data
which works on conjunction to the other end points. Hence, for this, the communication is based
on the networked elements where the fragmented data needs to be analyzed and worked upon.
The networking is based on the globalized connectivity and the transfer of the data where the
product designing is set with allowing to request the Wi-Fi credentials for proper access to the
network. Here, the privacy and the security issues are evaluated based on the patterns where
there is a need to check the authentication of the data with the retrieval of the address and the

other points of information. The client privacy is important to measure about the information
provide which is able to infer from the different points with the use of the lookup systems that
are important for the specific customers. The attribution of the tags to the objects are also
considered to be under drawing the attention of the traces with the aggravating the problems. The
business processes are mainly to address the data with the privacy requirements that are based on
major concern of the risk management and the concepts of the governing business activities.
5:
The trigger is requested every 1sec
Round trip propagation is 12ms
Process request 3ms
And the applications handle 2ms.
Applications block then the time budget saved is 1.015sec.
Processing for the round-trip time would be 6ms+2ms= 8ms.
6:
The Nielsen law is based on working for the user bandwidth which tend to grow every year by
50%. Here, here are specifications for the updates about how the exponential curve for the
annualized growth is stated. (Sun et al., 2016)
provide which is able to infer from the different points with the use of the lookup systems that
are important for the specific customers. The attribution of the tags to the objects are also
considered to be under drawing the attention of the traces with the aggravating the problems. The
business processes are mainly to address the data with the privacy requirements that are based on
major concern of the risk management and the concepts of the governing business activities.
5:
The trigger is requested every 1sec
Round trip propagation is 12ms
Process request 3ms
And the applications handle 2ms.
Applications block then the time budget saved is 1.015sec.
Processing for the round-trip time would be 6ms+2ms= 8ms.
6:
The Nielsen law is based on working for the user bandwidth which tend to grow every year by
50%. Here, here are specifications for the updates about how the exponential curve for the
annualized growth is stated. (Sun et al., 2016)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
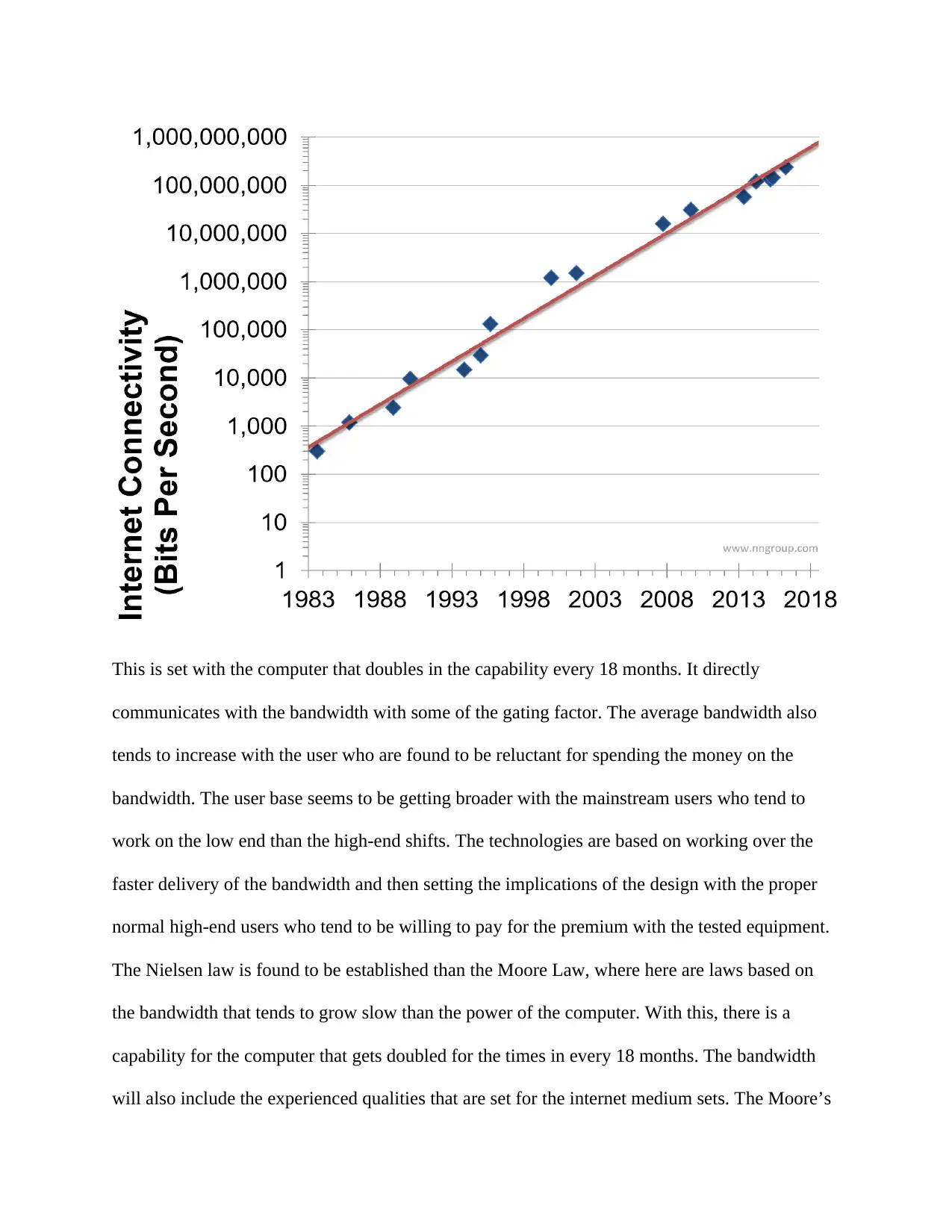
This is set with the computer that doubles in the capability every 18 months. It directly
communicates with the bandwidth with some of the gating factor. The average bandwidth also
tends to increase with the user who are found to be reluctant for spending the money on the
bandwidth. The user base seems to be getting broader with the mainstream users who tend to
work on the low end than the high-end shifts. The technologies are based on working over the
faster delivery of the bandwidth and then setting the implications of the design with the proper
normal high-end users who tend to be willing to pay for the premium with the tested equipment.
The Nielsen law is found to be established than the Moore Law, where here are laws based on
the bandwidth that tends to grow slow than the power of the computer. With this, there is a
capability for the computer that gets doubled for the times in every 18 months. The bandwidth
will also include the experienced qualities that are set for the internet medium sets. The Moore’s
communicates with the bandwidth with some of the gating factor. The average bandwidth also
tends to increase with the user who are found to be reluctant for spending the money on the
bandwidth. The user base seems to be getting broader with the mainstream users who tend to
work on the low end than the high-end shifts. The technologies are based on working over the
faster delivery of the bandwidth and then setting the implications of the design with the proper
normal high-end users who tend to be willing to pay for the premium with the tested equipment.
The Nielsen law is found to be established than the Moore Law, where here are laws based on
the bandwidth that tends to grow slow than the power of the computer. With this, there is a
capability for the computer that gets doubled for the times in every 18 months. The bandwidth
will also include the experienced qualities that are set for the internet medium sets. The Moore’s
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

law is found for the processing power with the remaining bandwidth that is bound. The
learnability, efficiency and the memorability is tracked with the proper hierarchy and the visual
clues of the system. The idea for the Internet of Things is based on working over the wide scale
proliferation of the mobile and the miniaturized computing, which includes the telemetry
applications and the facilitations based on the data processing and handling the content
management as well.
learnability, efficiency and the memorability is tracked with the proper hierarchy and the visual
clues of the system. The idea for the Internet of Things is based on working over the wide scale
proliferation of the mobile and the miniaturized computing, which includes the telemetry
applications and the facilitations based on the data processing and handling the content
management as well.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





