Network Architecture and Technologies Overview
VerifiedAdded on 2020/02/24
|14
|2600
|67
AI Summary
This assignment delves into the realm of network architecture and technology. It encompasses a wide range of topics, including the OSI model, TCP/IP protocols, Local Area Networks (LANs), Metropolitan Area Networks (MANs), Wide Area Networks (WANs), Software-Defined Networking (SDN), Named Data Networking (NDN), and Multipath TCP. The provided papers offer insights into network implementation, management, maintenance, Quality of Experience (QoE) fairness, consensus in hardware, high-speed railway communication systems, multipath TCP performance in VANETs, disaster-resilient WANs, the challenges of IoT networking via TCP/IP architecture, underwater acoustic networking platforms, and low-latency networking with dedicated NICs.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: TCP/IP NETWORKING
TCP/IP Networking
Name of the Student
Name of the University
Author’s Note
TCP/IP Networking
Name of the Student
Name of the University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
TCP/IP NETWORKING
Table of Contents
TASK 1................................................................................................................................2
a. Designing the network solution for M2M solutions....................................................2
b. Explanation of the design for increased number of workstations................................7
TASK 2................................................................................................................................7
a. Explanation and comparison of the communication network and network protocol
analyzer role.................................................................................................................................7
b. Detailed analysis of the available network analysis tools...........................................8
i. Benefits, associated costs and Ease of usability.......................................................8
ii. Recommendations.................................................................................................10
Bibliography......................................................................................................................11
TCP/IP NETWORKING
Table of Contents
TASK 1................................................................................................................................2
a. Designing the network solution for M2M solutions....................................................2
b. Explanation of the design for increased number of workstations................................7
TASK 2................................................................................................................................7
a. Explanation and comparison of the communication network and network protocol
analyzer role.................................................................................................................................7
b. Detailed analysis of the available network analysis tools...........................................8
i. Benefits, associated costs and Ease of usability.......................................................8
ii. Recommendations.................................................................................................10
Bibliography......................................................................................................................11
2
TCP/IP NETWORKING
TASK 1
a. Designing the network solution for M2M solutions
For formation of the system outline for M2M arrangement an investigation is required to
be performed on the available network topology and apply the best suited topology in the
network. For the advancement of the system the IP address 10.3.0.0 is used and the host
connected in the network is required to be accommodated for and also support the future growth
of the company. The routers installed in the network are configured following the created simple
addressing solution and border gateway protocol is used for communicating with the hosts
installed outside the network.
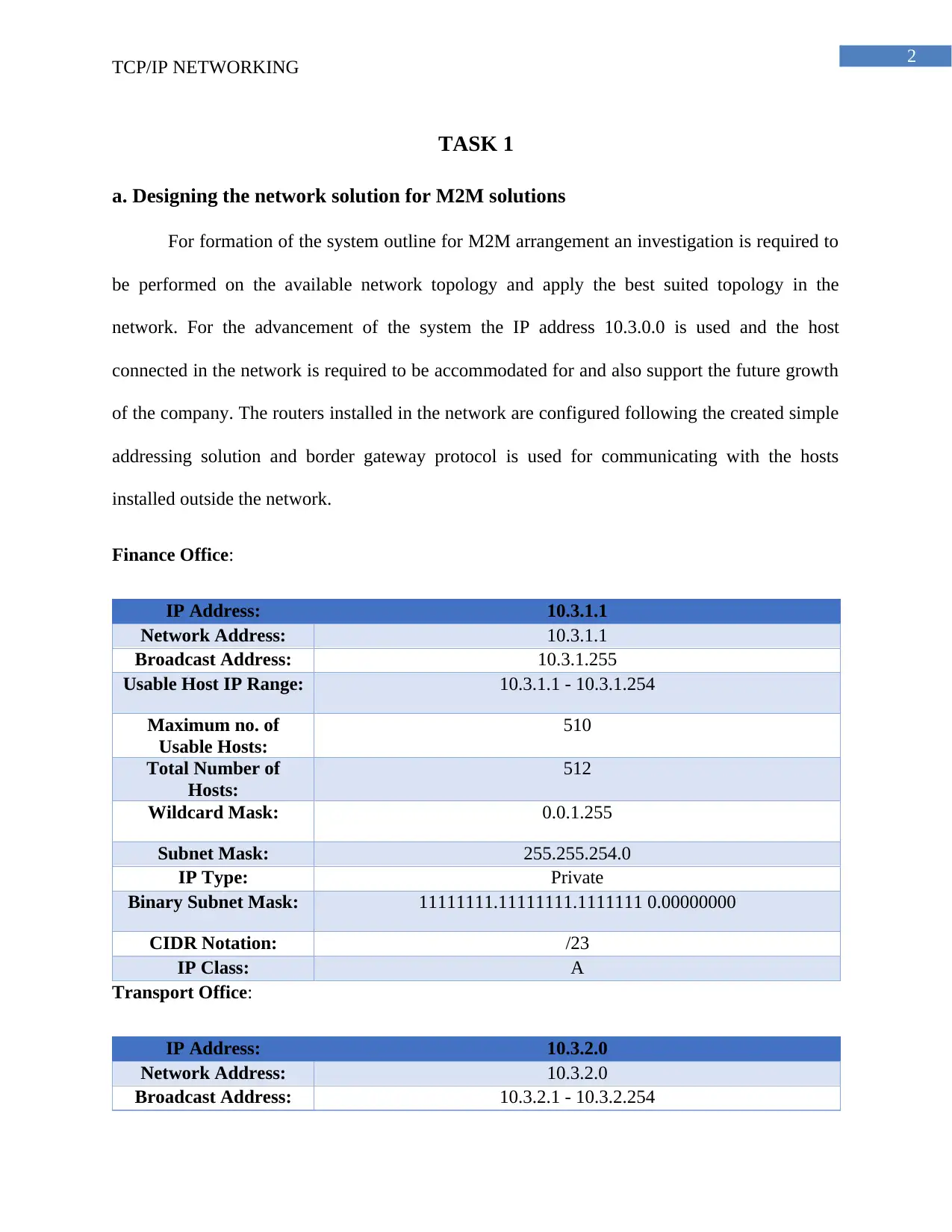
Finance Office:
IP Address: 10.3.1.1
Network Address: 10.3.1.1
Broadcast Address: 10.3.1.255
Usable Host IP Range: 10.3.1.1 - 10.3.1.254
Maximum no. of
Usable Hosts:
510
Total Number of
Hosts:
512
Wildcard Mask: 0.0.1.255
Subnet Mask: 255.255.254.0
IP Type: Private
Binary Subnet Mask: 11111111.11111111.1111111 0.00000000
CIDR Notation: /23
IP Class: A
Transport Office:
IP Address: 10.3.2.0
Network Address: 10.3.2.0
Broadcast Address: 10.3.2.1 - 10.3.2.254
TCP/IP NETWORKING
TASK 1
a. Designing the network solution for M2M solutions
For formation of the system outline for M2M arrangement an investigation is required to
be performed on the available network topology and apply the best suited topology in the
network. For the advancement of the system the IP address 10.3.0.0 is used and the host
connected in the network is required to be accommodated for and also support the future growth
of the company. The routers installed in the network are configured following the created simple
addressing solution and border gateway protocol is used for communicating with the hosts
installed outside the network.
Finance Office:
IP Address: 10.3.1.1
Network Address: 10.3.1.1
Broadcast Address: 10.3.1.255
Usable Host IP Range: 10.3.1.1 - 10.3.1.254
Maximum no. of
Usable Hosts:
510
Total Number of
Hosts:
512
Wildcard Mask: 0.0.1.255
Subnet Mask: 255.255.254.0
IP Type: Private
Binary Subnet Mask: 11111111.11111111.1111111 0.00000000
CIDR Notation: /23
IP Class: A
Transport Office:
IP Address: 10.3.2.0
Network Address: 10.3.2.0
Broadcast Address: 10.3.2.1 - 10.3.2.254
3
TCP/IP NETWORKING
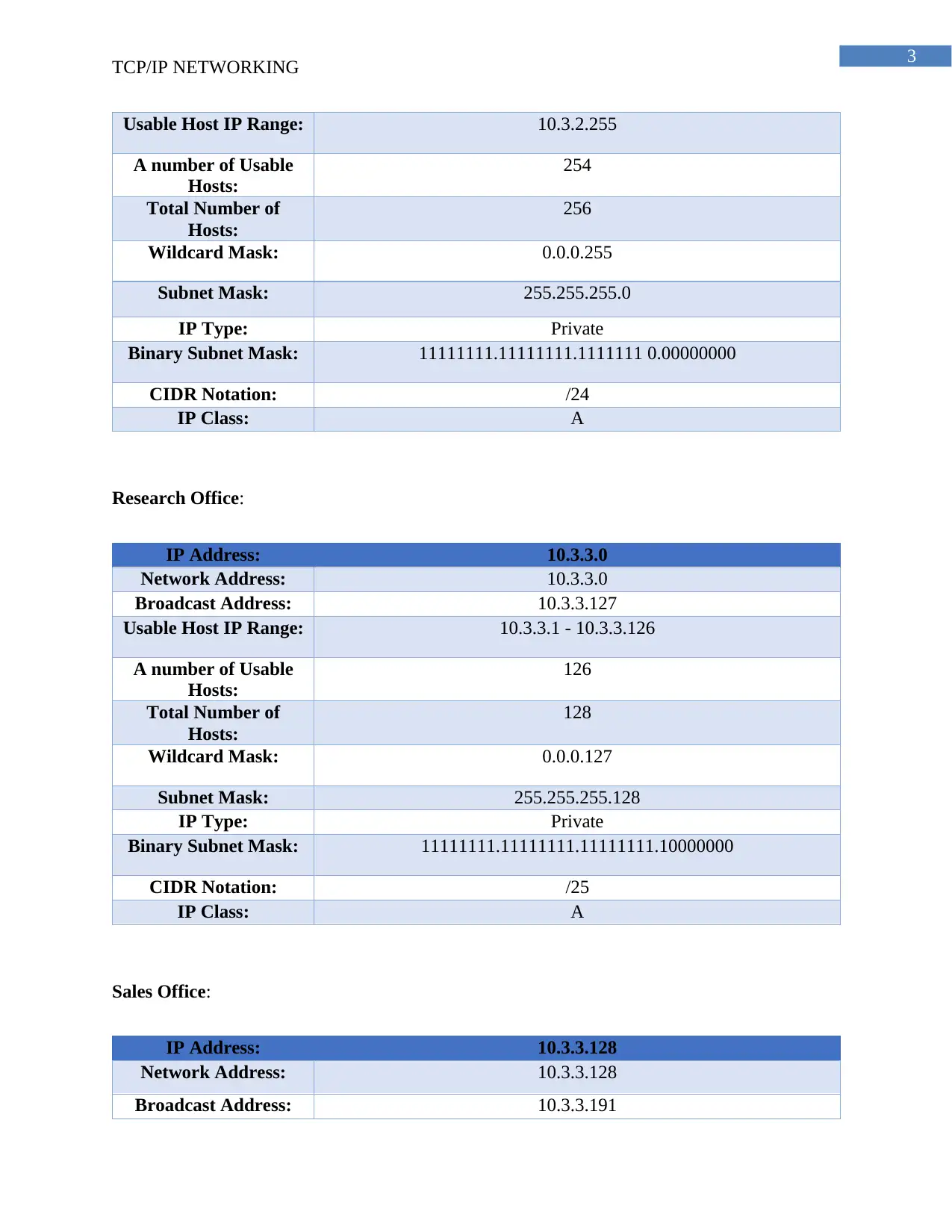
Usable Host IP Range: 10.3.2.255
A number of Usable
Hosts:
254
Total Number of
Hosts:
256
Wildcard Mask: 0.0.0.255
Subnet Mask: 255.255.255.0
IP Type: Private
Binary Subnet Mask: 11111111.11111111.1111111 0.00000000
CIDR Notation: /24
IP Class: A
Research Office:
IP Address: 10.3.3.0
Network Address: 10.3.3.0
Broadcast Address: 10.3.3.127
Usable Host IP Range: 10.3.3.1 - 10.3.3.126
A number of Usable
Hosts:
126
Total Number of
Hosts:
128
Wildcard Mask: 0.0.0.127
Subnet Mask: 255.255.255.128
IP Type: Private
Binary Subnet Mask: 11111111.11111111.11111111.10000000
CIDR Notation: /25
IP Class: A
Sales Office:
IP Address: 10.3.3.128
Network Address: 10.3.3.128
Broadcast Address: 10.3.3.191
TCP/IP NETWORKING
Usable Host IP Range: 10.3.2.255
A number of Usable
Hosts:
254
Total Number of
Hosts:
256
Wildcard Mask: 0.0.0.255
Subnet Mask: 255.255.255.0
IP Type: Private
Binary Subnet Mask: 11111111.11111111.1111111 0.00000000
CIDR Notation: /24
IP Class: A
Research Office:
IP Address: 10.3.3.0
Network Address: 10.3.3.0
Broadcast Address: 10.3.3.127
Usable Host IP Range: 10.3.3.1 - 10.3.3.126
A number of Usable
Hosts:
126
Total Number of
Hosts:
128
Wildcard Mask: 0.0.0.127
Subnet Mask: 255.255.255.128
IP Type: Private
Binary Subnet Mask: 11111111.11111111.11111111.10000000
CIDR Notation: /25
IP Class: A
Sales Office:
IP Address: 10.3.3.128
Network Address: 10.3.3.128
Broadcast Address: 10.3.3.191
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
TCP/IP NETWORKING
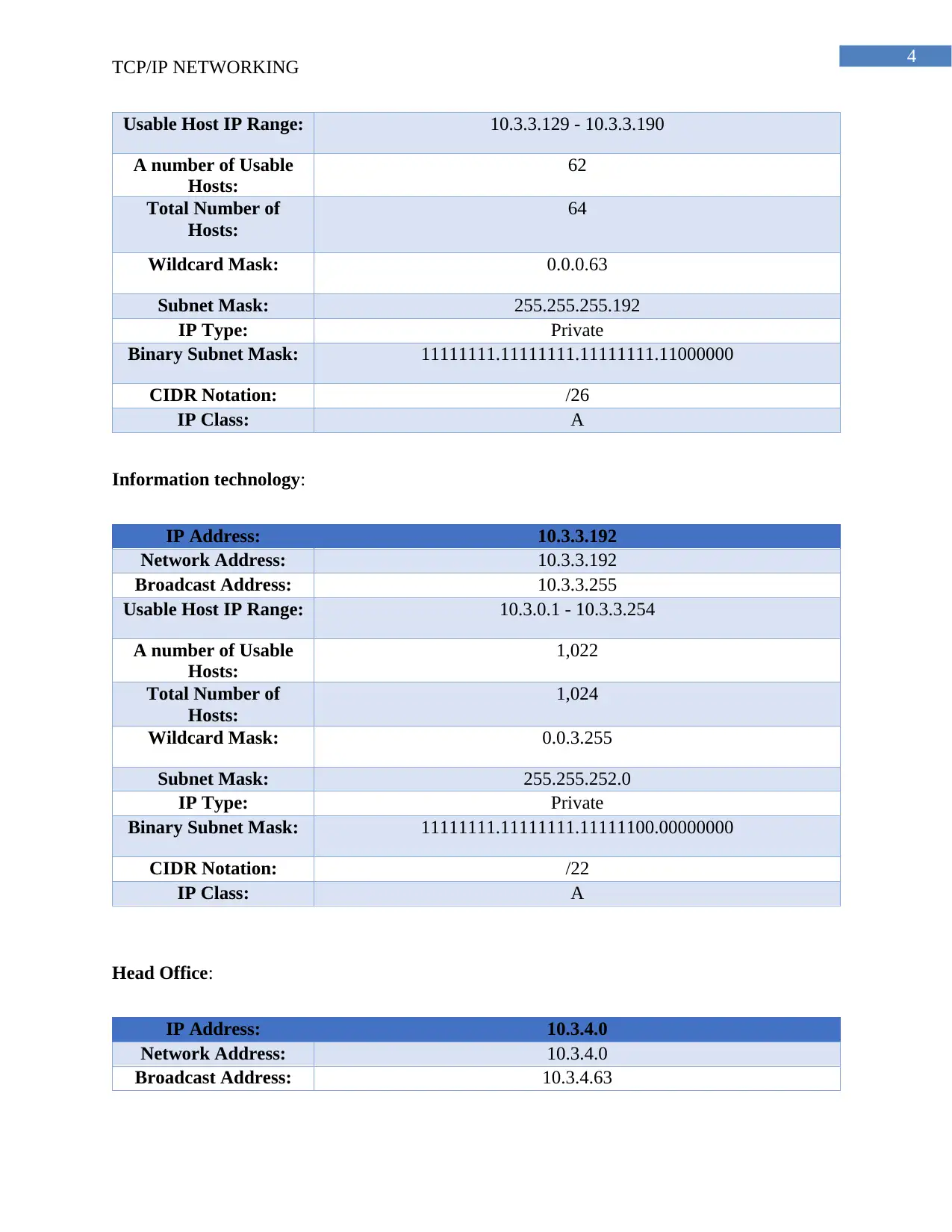
Usable Host IP Range: 10.3.3.129 - 10.3.3.190
A number of Usable
Hosts:
62
Total Number of
Hosts:
64
Wildcard Mask: 0.0.0.63
Subnet Mask: 255.255.255.192
IP Type: Private
Binary Subnet Mask: 11111111.11111111.11111111.11000000
CIDR Notation: /26
IP Class: A
Information technology:
IP Address: 10.3.3.192
Network Address: 10.3.3.192
Broadcast Address: 10.3.3.255
Usable Host IP Range: 10.3.0.1 - 10.3.3.254
A number of Usable
Hosts:
1,022
Total Number of
Hosts:
1,024
Wildcard Mask: 0.0.3.255
Subnet Mask: 255.255.252.0
IP Type: Private
Binary Subnet Mask: 11111111.11111111.11111100.00000000
CIDR Notation: /22
IP Class: A
Head Office:
IP Address: 10.3.4.0
Network Address: 10.3.4.0
Broadcast Address: 10.3.4.63
TCP/IP NETWORKING
Usable Host IP Range: 10.3.3.129 - 10.3.3.190
A number of Usable
Hosts:
62
Total Number of
Hosts:
64
Wildcard Mask: 0.0.0.63
Subnet Mask: 255.255.255.192
IP Type: Private
Binary Subnet Mask: 11111111.11111111.11111111.11000000
CIDR Notation: /26
IP Class: A
Information technology:
IP Address: 10.3.3.192
Network Address: 10.3.3.192
Broadcast Address: 10.3.3.255
Usable Host IP Range: 10.3.0.1 - 10.3.3.254
A number of Usable
Hosts:
1,022
Total Number of
Hosts:
1,024
Wildcard Mask: 0.0.3.255
Subnet Mask: 255.255.252.0
IP Type: Private
Binary Subnet Mask: 11111111.11111111.11111100.00000000
CIDR Notation: /22
IP Class: A
Head Office:
IP Address: 10.3.4.0
Network Address: 10.3.4.0
Broadcast Address: 10.3.4.63
5
TCP/IP NETWORKING
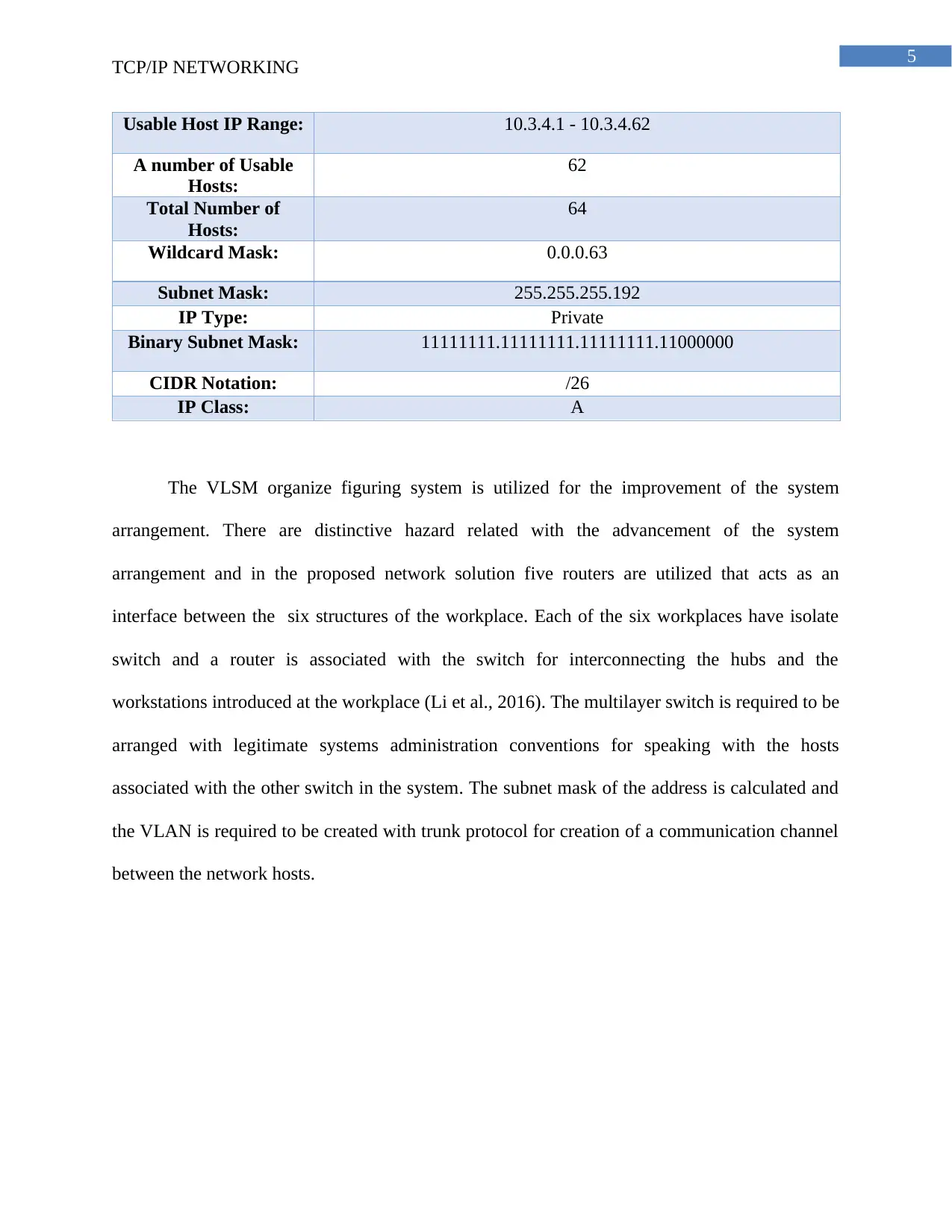
Usable Host IP Range: 10.3.4.1 - 10.3.4.62
A number of Usable
Hosts:
62
Total Number of
Hosts:
64
Wildcard Mask: 0.0.0.63
Subnet Mask: 255.255.255.192
IP Type: Private
Binary Subnet Mask: 11111111.11111111.11111111.11000000
CIDR Notation: /26
IP Class: A
The VLSM organize figuring system is utilized for the improvement of the system
arrangement. There are distinctive hazard related with the advancement of the system
arrangement and in the proposed network solution five routers are utilized that acts as an
interface between the six structures of the workplace. Each of the six workplaces have isolate
switch and a router is associated with the switch for interconnecting the hubs and the
workstations introduced at the workplace (Li et al., 2016). The multilayer switch is required to be
arranged with legitimate systems administration conventions for speaking with the hosts
associated with the other switch in the system. The subnet mask of the address is calculated and
the VLAN is required to be created with trunk protocol for creation of a communication channel
between the network hosts.
TCP/IP NETWORKING
Usable Host IP Range: 10.3.4.1 - 10.3.4.62
A number of Usable
Hosts:
62
Total Number of
Hosts:
64
Wildcard Mask: 0.0.0.63
Subnet Mask: 255.255.255.192
IP Type: Private
Binary Subnet Mask: 11111111.11111111.11111111.11000000
CIDR Notation: /26
IP Class: A
The VLSM organize figuring system is utilized for the improvement of the system
arrangement. There are distinctive hazard related with the advancement of the system
arrangement and in the proposed network solution five routers are utilized that acts as an
interface between the six structures of the workplace. Each of the six workplaces have isolate
switch and a router is associated with the switch for interconnecting the hubs and the
workstations introduced at the workplace (Li et al., 2016). The multilayer switch is required to be
arranged with legitimate systems administration conventions for speaking with the hosts
associated with the other switch in the system. The subnet mask of the address is calculated and
the VLAN is required to be created with trunk protocol for creation of a communication channel
between the network hosts.
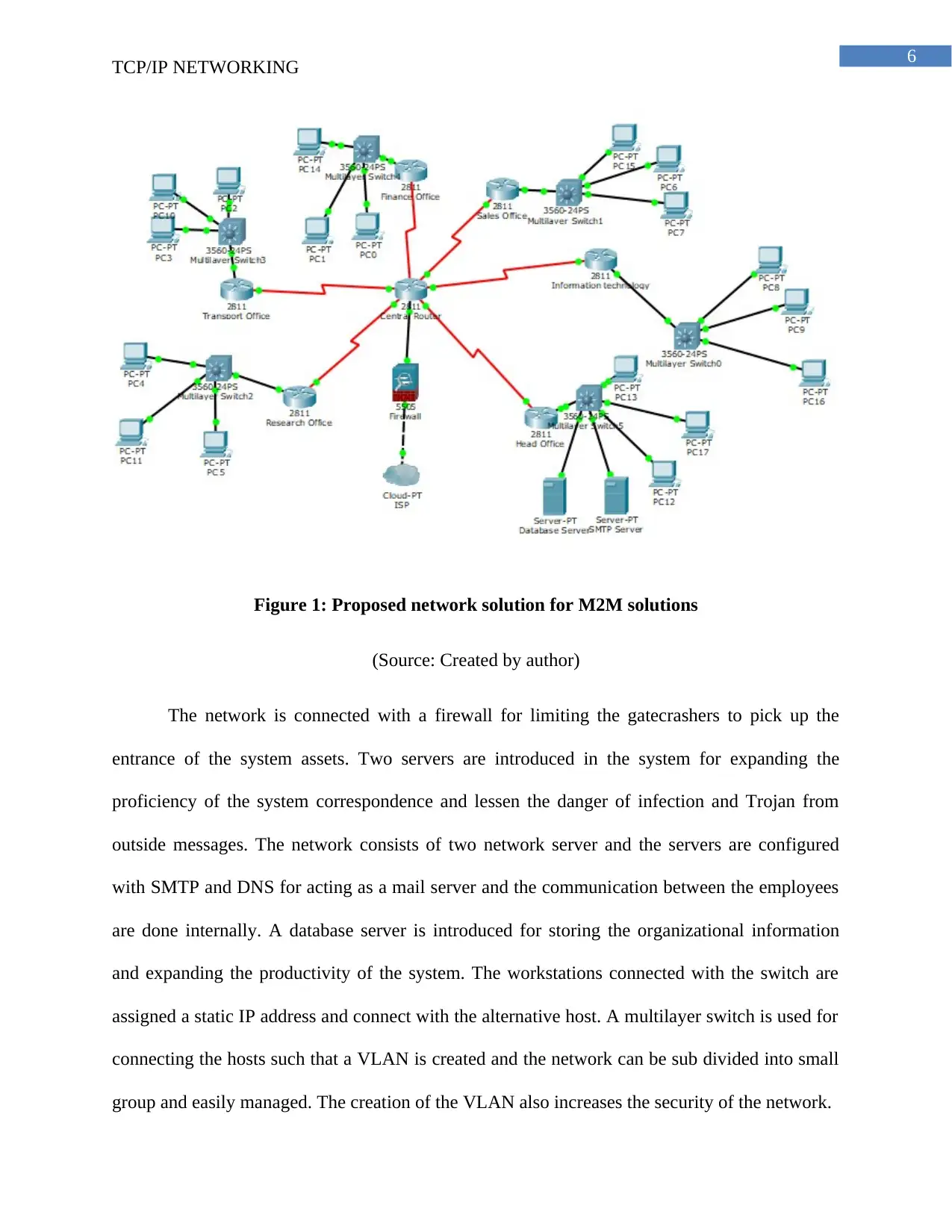
6
TCP/IP NETWORKING
Figure 1: Proposed network solution for M2M solutions
(Source: Created by author)
The network is connected with a firewall for limiting the gatecrashers to pick up the
entrance of the system assets. Two servers are introduced in the system for expanding the
proficiency of the system correspondence and lessen the danger of infection and Trojan from
outside messages. The network consists of two network server and the servers are configured
with SMTP and DNS for acting as a mail server and the communication between the employees
are done internally. A database server is introduced for storing the organizational information
and expanding the productivity of the system. The workstations connected with the switch are
assigned a static IP address and connect with the alternative host. A multilayer switch is used for
connecting the hosts such that a VLAN is created and the network can be sub divided into small
group and easily managed. The creation of the VLAN also increases the security of the network.
TCP/IP NETWORKING
Figure 1: Proposed network solution for M2M solutions
(Source: Created by author)
The network is connected with a firewall for limiting the gatecrashers to pick up the
entrance of the system assets. Two servers are introduced in the system for expanding the
proficiency of the system correspondence and lessen the danger of infection and Trojan from
outside messages. The network consists of two network server and the servers are configured
with SMTP and DNS for acting as a mail server and the communication between the employees
are done internally. A database server is introduced for storing the organizational information
and expanding the productivity of the system. The workstations connected with the switch are
assigned a static IP address and connect with the alternative host. A multilayer switch is used for
connecting the hosts such that a VLAN is created and the network can be sub divided into small
group and easily managed. The creation of the VLAN also increases the security of the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
TCP/IP NETWORKING
b. Explanation of the design for increased number of workstations
In future there is a possibility of increase in the users in the network and the host size can
be increased to 1024 numbers. The subnet mask of the network is required to be calculated and
the new hosts connected in the network is required to be assigned with a new IP address for
communication with the other workstations in the same or other network. The recalculation of
the subnet mask does not adds any extra cost in the expansion of the network and thus are
calculated below:
Head Office 10.0.20.0 /22 255.255.252.0 10.0.20.1 - 10.0.23.254
Finance Office 10.0.0.0 /22 255.255.252.0 10.0.0.1 - 10.0.3.254
Transport Office 10.0.4.0 /22 255.255.252.0 10.0.4.1 - 10.0.7.254
Research Office 10.0.8.0 /22 255.255.252.0 10.0.8.1 - 10.0.11.254
Sales Office 10.0.12.0 /22 255.255.252.0 10.0.12.1 - 10.0.15.254
Information Technology 10.0.16.0 /22 255.255.252.0 10.0.16.1 - 10.0.19.254
TASK 2
a. Explanation and comparison of the communication network and network
protocol analyzer role
Many distinctive system resolution analyzer are available and are utilized for
distinguishing evidence of the breach of the information of the system. The workstations
associated in the system are dissected and it is utilized for arrangement of the disclosure and
investigation of the system. The information loss, retries and timeouts occurred during running
the information system are controlled for expansion of the proficiency of the information system.
TCP/IP NETWORKING
b. Explanation of the design for increased number of workstations
In future there is a possibility of increase in the users in the network and the host size can
be increased to 1024 numbers. The subnet mask of the network is required to be calculated and
the new hosts connected in the network is required to be assigned with a new IP address for
communication with the other workstations in the same or other network. The recalculation of
the subnet mask does not adds any extra cost in the expansion of the network and thus are
calculated below:
Head Office 10.0.20.0 /22 255.255.252.0 10.0.20.1 - 10.0.23.254
Finance Office 10.0.0.0 /22 255.255.252.0 10.0.0.1 - 10.0.3.254
Transport Office 10.0.4.0 /22 255.255.252.0 10.0.4.1 - 10.0.7.254
Research Office 10.0.8.0 /22 255.255.252.0 10.0.8.1 - 10.0.11.254
Sales Office 10.0.12.0 /22 255.255.252.0 10.0.12.1 - 10.0.15.254
Information Technology 10.0.16.0 /22 255.255.252.0 10.0.16.1 - 10.0.19.254
TASK 2
a. Explanation and comparison of the communication network and network
protocol analyzer role
Many distinctive system resolution analyzer are available and are utilized for
distinguishing evidence of the breach of the information of the system. The workstations
associated in the system are dissected and it is utilized for arrangement of the disclosure and
investigation of the system. The information loss, retries and timeouts occurred during running
the information system are controlled for expansion of the proficiency of the information system.

8
TCP/IP NETWORKING
The congestion in the network can be removed with the proper identification of the loss of the
organizational information.
The planning of the system outlining for M2M solution the IP address 10.3.0.0 is utilized
and execution of the Network Instruments is used for the examination of the activity of the
system. The Network Instruments is used for analyzing different types of network environment
such as LAN, WAN and wireless network. The user interface of the packet analyzer software is
simple and there is an ability to replay the network packet components. There are diverse
programming that can likewise be utilized for investigation of the movement, for example nmap,
wireshark and so forth and these are accessible free of cost. The Network Instruments are
introduced for social affair evidence from the system if there should arise an occurrence of
network attack and the evidence are collected for future use. The expansion of the network are
required to be considered and the nic cards installed in the network can be identified for finding
the source of the handle the crisis of the network..
b. Detailed analysis of the available network analysis tools
i. Benefits, associated costs and Ease of usability
With the application of the Network Instruments the network packets can be decoded
easily and it is an excellent tool for the analysis of the distributed environment. The packets
captured during the analysis the network can be stored in the database of the organization and
replayed in future for analyzing. The packets can be analyzed for finding evidence of an attack of
the network. A report can be generated demonstrating the current condition of the network with
the inclusion of histograms and traffic matrixes (Demmer, Ott & Perreault, 2014). An alarm can
be set using the Network Instruments for alerting the network administrator during an emergency
condition. The packet summary can be observed at a glance and it is easy to use with improved
TCP/IP NETWORKING
The congestion in the network can be removed with the proper identification of the loss of the
organizational information.
The planning of the system outlining for M2M solution the IP address 10.3.0.0 is utilized
and execution of the Network Instruments is used for the examination of the activity of the
system. The Network Instruments is used for analyzing different types of network environment
such as LAN, WAN and wireless network. The user interface of the packet analyzer software is
simple and there is an ability to replay the network packet components. There are diverse
programming that can likewise be utilized for investigation of the movement, for example nmap,
wireshark and so forth and these are accessible free of cost. The Network Instruments are
introduced for social affair evidence from the system if there should arise an occurrence of
network attack and the evidence are collected for future use. The expansion of the network are
required to be considered and the nic cards installed in the network can be identified for finding
the source of the handle the crisis of the network..
b. Detailed analysis of the available network analysis tools
i. Benefits, associated costs and Ease of usability
With the application of the Network Instruments the network packets can be decoded
easily and it is an excellent tool for the analysis of the distributed environment. The packets
captured during the analysis the network can be stored in the database of the organization and
replayed in future for analyzing. The packets can be analyzed for finding evidence of an attack of
the network. A report can be generated demonstrating the current condition of the network with
the inclusion of histograms and traffic matrixes (Demmer, Ott & Perreault, 2014). An alarm can
be set using the Network Instruments for alerting the network administrator during an emergency
condition. The packet summary can be observed at a glance and it is easy to use with improved
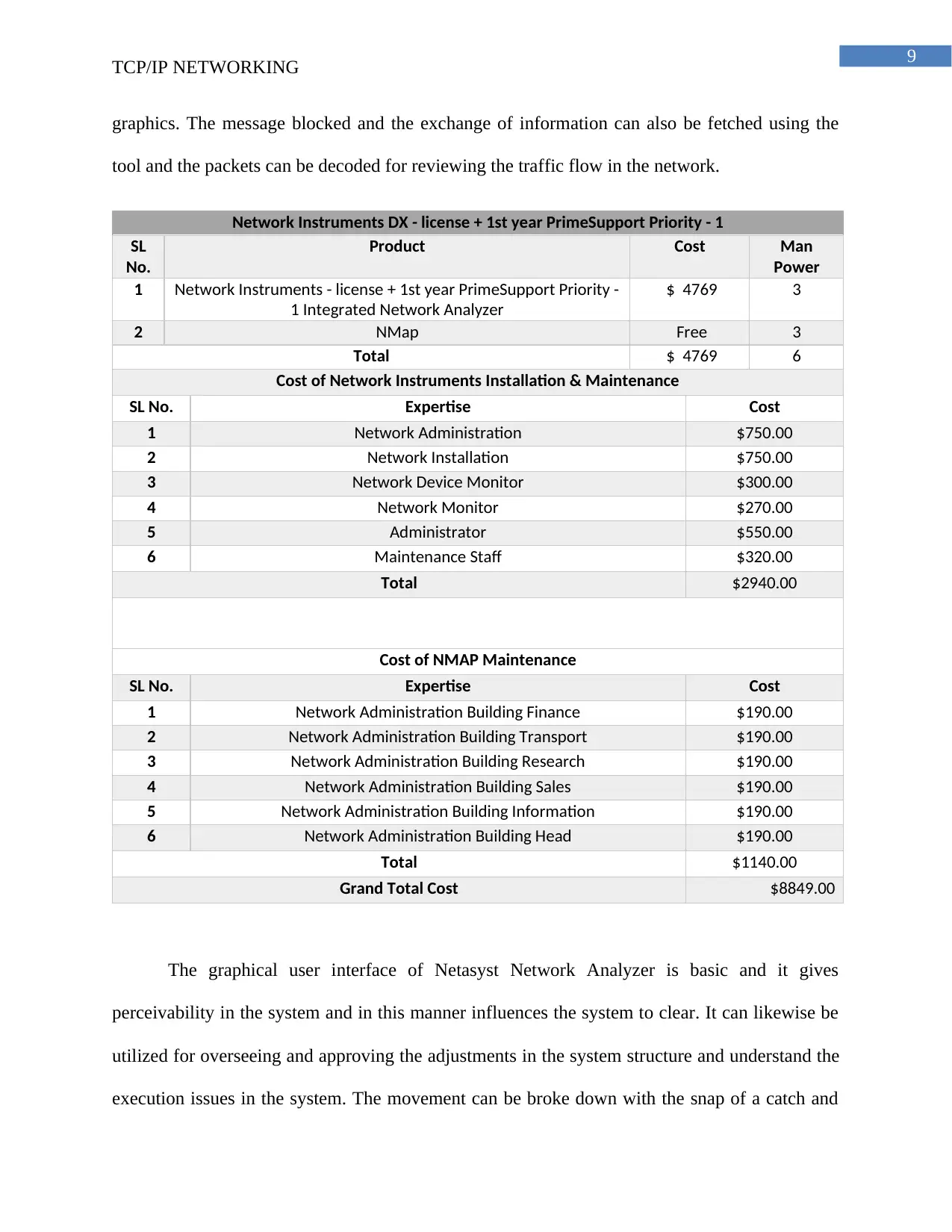
9
TCP/IP NETWORKING
graphics. The message blocked and the exchange of information can also be fetched using the
tool and the packets can be decoded for reviewing the traffic flow in the network.
Network Instruments DX - license + 1st year PrimeSupport Priority - 1
SL
No.
Product Cost Man
Power
1 Network Instruments - license + 1st year PrimeSupport Priority -
1 Integrated Network Analyzer
$ 4769 3
2 NMap Free 3
Total $ 4769 6
Cost of Network Instruments Installation & Maintenance
SL No. Expertise Cost
1 Network Administration $750.00
2 Network Installation $750.00
3 Network Device Monitor $300.00
4 Network Monitor $270.00
5 Administrator $550.00
6 Maintenance Staff $320.00
Total $2940.00
Cost of NMAP Maintenance
SL No. Expertise Cost
1 Network Administration Building Finance $190.00
2 Network Administration Building Transport $190.00
3 Network Administration Building Research $190.00
4 Network Administration Building Sales $190.00
5 Network Administration Building Information $190.00
6 Network Administration Building Head $190.00
Total $1140.00
Grand Total Cost $8849.00
The graphical user interface of Netasyst Network Analyzer is basic and it gives
perceivability in the system and in this manner influences the system to clear. It can likewise be
utilized for overseeing and approving the adjustments in the system structure and understand the
execution issues in the system. The movement can be broke down with the snap of a catch and
TCP/IP NETWORKING
graphics. The message blocked and the exchange of information can also be fetched using the
tool and the packets can be decoded for reviewing the traffic flow in the network.
Network Instruments DX - license + 1st year PrimeSupport Priority - 1
SL
No.
Product Cost Man
Power
1 Network Instruments - license + 1st year PrimeSupport Priority -
1 Integrated Network Analyzer
$ 4769 3
2 NMap Free 3
Total $ 4769 6
Cost of Network Instruments Installation & Maintenance
SL No. Expertise Cost
1 Network Administration $750.00
2 Network Installation $750.00
3 Network Device Monitor $300.00
4 Network Monitor $270.00
5 Administrator $550.00
6 Maintenance Staff $320.00
Total $2940.00
Cost of NMAP Maintenance
SL No. Expertise Cost
1 Network Administration Building Finance $190.00
2 Network Administration Building Transport $190.00
3 Network Administration Building Research $190.00
4 Network Administration Building Sales $190.00
5 Network Administration Building Information $190.00
6 Network Administration Building Head $190.00
Total $1140.00
Grand Total Cost $8849.00
The graphical user interface of Netasyst Network Analyzer is basic and it gives
perceivability in the system and in this manner influences the system to clear. It can likewise be
utilized for overseeing and approving the adjustments in the system structure and understand the
execution issues in the system. The movement can be broke down with the snap of a catch and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
TCP/IP NETWORKING
causes the system overseer to screen the system at an ongoing (István et al., 2016). The
measurements of the gadget associated in the system can likewise be brought on a tick and aides
in examination of the VLAN and switch course associated in the system. A record is made for
the system overseer for dealing with the system application and the assets productively.
ii. Recommendations
For the improvement of the current network infrastructure some recommendations are
made and a detailed analysis is made on the recent technologies that can be applied for reducing
the congestion in the network and increase the security. A separate subnet can be used for each
of the floors or office in the building and isolate it from external access. The Network
Instruments can be used for the capturing of the remote packets and it also supports the wireless
network. The future expansion of the network can also be supported for adaptation of the new
network solution. There are different features such as alarms, capture filtering, triggers and name
filtering for dealing with the network solution and help to deal with the remote management
system. The configuration of the firewall with the business rules of the organization is also
important for supporting the hardware and network devices installed in the network.
TCP/IP NETWORKING
causes the system overseer to screen the system at an ongoing (István et al., 2016). The
measurements of the gadget associated in the system can likewise be brought on a tick and aides
in examination of the VLAN and switch course associated in the system. A record is made for
the system overseer for dealing with the system application and the assets productively.
ii. Recommendations
For the improvement of the current network infrastructure some recommendations are
made and a detailed analysis is made on the recent technologies that can be applied for reducing
the congestion in the network and increase the security. A separate subnet can be used for each
of the floors or office in the building and isolate it from external access. The Network
Instruments can be used for the capturing of the remote packets and it also supports the wireless
network. The future expansion of the network can also be supported for adaptation of the new
network solution. There are different features such as alarms, capture filtering, triggers and name
filtering for dealing with the network solution and help to deal with the remote management
system. The configuration of the firewall with the business rules of the organization is also
important for supporting the hardware and network devices installed in the network.

11
TCP/IP NETWORKING
Bibliography
Chen, S., Yuan, Z., & Muntean, G. M. (2013, April). An energy-aware multipath-TCP-based
content delivery scheme in heterogeneous wireless networks. In Wireless
Communications and Networking Conference (WCNC), 2013 IEEE (pp. 1291-1296).
IEEE.
Demmer, M., Ott, J., & Perreault, S. (2014). Delay-Tolerant Networking TCP Convergence-
Layer Protocol (No. RFC 7242).
Edwards, J., & Bramante, R. (2015). Networking self-teaching guide: OSI, TCP/IP, LANs,
MANs, WANs, implementation, management, and maintenance. John Wiley & Sons.
Georgopoulos, P., Elkhatib, Y., Broadbent, M., Mu, M., & Race, N. (2013, August). Towards
network-wide QoE fairness using openflow-assisted adaptive video streaming. In
Proceedings of the 2013 ACM SIGCOMM workshop on Future human-centric
multimedia networking (pp. 15-20). ACM.
István, Z., Sidler, D., Alonso, G., & Vukolic, M. (2016, March). Consensus in a Box:
Inexpensive Coordination in Hardware. In NSDI (pp. 425-438).
Li, Z., Chen, Y., Shi, H., & Liu, K. (2016). NDN-GSM-R: a novel high-speed railway
communication system via named data networking. EURASIP Journal on Wireless
Communications and Networking, 2016(1), 48.
Mena, J., Bankole, P., & Gerla, M. (2017, June). Multipath TCP on a VANET: A Performance
Study. In Proceedings of the 2017 ACM SIGMETRICS/International Conference on
Measurement and Modeling of Computer Systems (pp. 39-40). ACM.
TCP/IP NETWORKING
Bibliography
Chen, S., Yuan, Z., & Muntean, G. M. (2013, April). An energy-aware multipath-TCP-based
content delivery scheme in heterogeneous wireless networks. In Wireless
Communications and Networking Conference (WCNC), 2013 IEEE (pp. 1291-1296).
IEEE.
Demmer, M., Ott, J., & Perreault, S. (2014). Delay-Tolerant Networking TCP Convergence-
Layer Protocol (No. RFC 7242).
Edwards, J., & Bramante, R. (2015). Networking self-teaching guide: OSI, TCP/IP, LANs,
MANs, WANs, implementation, management, and maintenance. John Wiley & Sons.
Georgopoulos, P., Elkhatib, Y., Broadbent, M., Mu, M., & Race, N. (2013, August). Towards
network-wide QoE fairness using openflow-assisted adaptive video streaming. In
Proceedings of the 2013 ACM SIGCOMM workshop on Future human-centric
multimedia networking (pp. 15-20). ACM.
István, Z., Sidler, D., Alonso, G., & Vukolic, M. (2016, March). Consensus in a Box:
Inexpensive Coordination in Hardware. In NSDI (pp. 425-438).
Li, Z., Chen, Y., Shi, H., & Liu, K. (2016). NDN-GSM-R: a novel high-speed railway
communication system via named data networking. EURASIP Journal on Wireless
Communications and Networking, 2016(1), 48.
Mena, J., Bankole, P., & Gerla, M. (2017, June). Multipath TCP on a VANET: A Performance
Study. In Proceedings of the 2017 ACM SIGMETRICS/International Conference on
Measurement and Modeling of Computer Systems (pp. 39-40). ACM.

12
TCP/IP NETWORKING
Nguyen, K., Minh, Q. T., & Yamada, S. (2013, July). A software-defined networking approach
for disaster-resilient WANs. In Computer Communications and Networks (ICCCN),
2013 22nd International Conference on (pp. 1-5). IEEE.
Peng, Q., Walid, A., Hwang, J., & Low, S. H. (2016). Multipath TCP: Analysis, design, and
implementation. IEEE/ACM Transactions on Networking, 24(1), 596-609.
Shang, W., Bannis, A., Liang, T., Wang, Z., Yu, Y., Afanasyev, A., ... & Zhang, L. (2016,
April). Named data networking of things. In Internet-of-Things Design and
Implementation (IoTDI), 2016 IEEE First International Conference on (pp. 117-128).
IEEE.
Shang, W., Yu, Y., Droms, R., & Zhang, L. (2016). Challenges in IoT networking via TCP/IP
architecture. NDN Project, Tech. Rep. NDN-0038.
Torres, D., Friedman, J., Schmid, T., Srivastava, M. B., Noh, Y., & Gerla, M. (2015). Software-
defined underwater acoustic networking platform and its applications. Ad Hoc Networks,
34, 252-264.
Yasukata, K., Honda, M., Santry, D., & Eggert, L. (2016, June). StackMap: Low-Latency
Networking with the OS Stack and Dedicated NICs. In USENIX Annual Technical
Conference (pp. 43-56).
Zinner, T., Jarschel, M., Blenk, A., Wamser, F., & Kellerer, W. (2014, May). Dynamic
application-aware resource management using Software-Defined Networking:
Implementation prospects and challenges. In Network Operations and Management
Symposium (NOMS), 2014 IEEE (pp. 1-6). IEEE.
TCP/IP NETWORKING
Nguyen, K., Minh, Q. T., & Yamada, S. (2013, July). A software-defined networking approach
for disaster-resilient WANs. In Computer Communications and Networks (ICCCN),
2013 22nd International Conference on (pp. 1-5). IEEE.
Peng, Q., Walid, A., Hwang, J., & Low, S. H. (2016). Multipath TCP: Analysis, design, and
implementation. IEEE/ACM Transactions on Networking, 24(1), 596-609.
Shang, W., Bannis, A., Liang, T., Wang, Z., Yu, Y., Afanasyev, A., ... & Zhang, L. (2016,
April). Named data networking of things. In Internet-of-Things Design and
Implementation (IoTDI), 2016 IEEE First International Conference on (pp. 117-128).
IEEE.
Shang, W., Yu, Y., Droms, R., & Zhang, L. (2016). Challenges in IoT networking via TCP/IP
architecture. NDN Project, Tech. Rep. NDN-0038.
Torres, D., Friedman, J., Schmid, T., Srivastava, M. B., Noh, Y., & Gerla, M. (2015). Software-
defined underwater acoustic networking platform and its applications. Ad Hoc Networks,
34, 252-264.
Yasukata, K., Honda, M., Santry, D., & Eggert, L. (2016, June). StackMap: Low-Latency
Networking with the OS Stack and Dedicated NICs. In USENIX Annual Technical
Conference (pp. 43-56).
Zinner, T., Jarschel, M., Blenk, A., Wamser, F., & Kellerer, W. (2014, May). Dynamic
application-aware resource management using Software-Defined Networking:
Implementation prospects and challenges. In Network Operations and Management
Symposium (NOMS), 2014 IEEE (pp. 1-6). IEEE.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
TCP/IP NETWORKING
TCP/IP NETWORKING
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





