Biometric Security: Concepts and Applications
VerifiedAdded on 2020/02/05
|11
|2339
|140
Essay
AI Summary
This assignment delves into the concept of biometric security, a technology that utilizes an individual's unique biological traits for identification and verification purposes. It outlines the various stages involved in the biometric process, from capturing biometric data to matching it against a database. The report also analyzes the advantages and disadvantages of biometric security, considering its effectiveness, reliability, and potential privacy concerns.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

INFORMATION TECHNOLOGY
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

ABSTRACT
The present report is based on biometric-security. This security feature is based on the
identification of biological traits. This technique is considered as a solution for remembering
passwords and codes for unlocking. This approach is adapted in various places such as ATM
voice recognition, finger print testing and eye scanning. It is considered as one of the best safety
method. But it is also not 100% accurate because system failure can occur in any device. Due to
which may affect its functioning affect.
The present report is based on biometric-security. This security feature is based on the
identification of biological traits. This technique is considered as a solution for remembering
passwords and codes for unlocking. This approach is adapted in various places such as ATM
voice recognition, finger print testing and eye scanning. It is considered as one of the best safety
method. But it is also not 100% accurate because system failure can occur in any device. Due to
which may affect its functioning affect.

Table of Contents
ABSTRACT.....................................................................................................................................2
INTRODUCTION...........................................................................................................................4
DISCUSSION..................................................................................................................................4
CONCLUSION................................................................................................................................6
References........................................................................................................................................7
ABSTRACT.....................................................................................................................................2
INTRODUCTION...........................................................................................................................4
DISCUSSION..................................................................................................................................4
CONCLUSION................................................................................................................................6
References........................................................................................................................................7

INTRODUCTION
Biometric technology is related to verification or authentication of individual from
security concern in which persons face, eyes and hand are used for identification. This report
consists of implementation of biometrics security, along with this steps involved for the
implementation and investigation of this problem. All advantages and disadvantage of biometrics
are also considered (Bagga, Hans, and Sharma, 2017). The biometric security are considered as
one of advance safety feature through this one cannot access others property without making him
known. Through this chances of theft will be automatically get reduce or become negligible.
DISCUSSION
Information and Communication technology(ICT ) plays an important role in providing
reliable, safe and secure IT services. This concept is developed with the objective of providing
security to clients by using their face or hand as unique identification key.
Implementation of biometric security technology: This method involves biometric
components in order to provide security due to which risk of safety break automatically get
reduced. This security device is use to identify or verify an individual on the basis of biological
traits of an individual. This security method is considered as one of strongest identification
process because if the result is positive then only lock can be opened, but in case of negative
result individual will be provided with limited count of chances in order to open it (Beerling,
2017).
Steps involved in fingerprint identification process: The process of figure print recognition
takes place in three steps such as image enhancement, minutiae extraction and minutiae
matching. That are described below: Image Enhancement: Under this methodology image of biological trait is captured such
as figure on the basis of that image algorithm works by using certain set of steps such as:1. Normalization: In this input image is normalized in order to generate mean ad variance
of image.2. Local orientation estimation: The orientation of image is estimated on the basis of input.3. Local frequency estimation: The frequency of image is estimated on the basis ad the
basis of that orientation is decided (Miko, and et., 2015).
Biometric technology is related to verification or authentication of individual from
security concern in which persons face, eyes and hand are used for identification. This report
consists of implementation of biometrics security, along with this steps involved for the
implementation and investigation of this problem. All advantages and disadvantage of biometrics
are also considered (Bagga, Hans, and Sharma, 2017). The biometric security are considered as
one of advance safety feature through this one cannot access others property without making him
known. Through this chances of theft will be automatically get reduce or become negligible.
DISCUSSION
Information and Communication technology(ICT ) plays an important role in providing
reliable, safe and secure IT services. This concept is developed with the objective of providing
security to clients by using their face or hand as unique identification key.
Implementation of biometric security technology: This method involves biometric
components in order to provide security due to which risk of safety break automatically get
reduced. This security device is use to identify or verify an individual on the basis of biological
traits of an individual. This security method is considered as one of strongest identification
process because if the result is positive then only lock can be opened, but in case of negative
result individual will be provided with limited count of chances in order to open it (Beerling,
2017).
Steps involved in fingerprint identification process: The process of figure print recognition
takes place in three steps such as image enhancement, minutiae extraction and minutiae
matching. That are described below: Image Enhancement: Under this methodology image of biological trait is captured such
as figure on the basis of that image algorithm works by using certain set of steps such as:1. Normalization: In this input image is normalized in order to generate mean ad variance
of image.2. Local orientation estimation: The orientation of image is estimated on the basis of input.3. Local frequency estimation: The frequency of image is estimated on the basis ad the
basis of that orientation is decided (Miko, and et., 2015).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4. Region mask identification: The identification process is based on result generated by
classification of each block involved in normalization process.5. Filtering: On the basis of above process identified image is filtered by certain filters in
order to generate enhanced image. Minutiae Extraction: The process of minutiae extraction involve five stages such as
input image, orientation field, extracted ridges, thinned ridges and minutiae points.
During this process image is converted into binary form and on the basis of that reduced
ridge ethicalness is created . The popular method for this process is Crossing number,
under this skeleton of image is considered where it is divided into eight segment of
pattern. And by comparing with neighbours result is generated. By addition and
subtraction of adjacent pixels considerable output is generated.
Minutiae Matching: under this process matching takes place between the image in
database and input one.
Types of fingerprint scanning devices: There are various types of fingerprint devices are
available on the basis of their technologies, size and operation are describe below:
USB Fingerprint Device: This is one of the popularly known fingerprint device which
provide ride of remembering complex text code password to customers. They are
composed of CMOS sensor technologies which is considered as best service provider
among its peer. They are available under 77.77 Pound and can easily convert simplest
PC into high tech device. On the basis of users review. This device is useful for
individual as well as businesses for security purpose. As they are provided with USB so
they provide easy installation interface to users. And also provided at considerable price
(Dranove, Forman, Goldfarb, and Greenstein, 2014).
Keyboard Fingerprint Device: Now considering security as major issues PC are also
available with fingerprint scanner. Along with this additional text code passwords are
also provided with that to provide backup option. As no two person can have same print
so this is considered as lowest risk provider. They are available under 124.40 pound. On
the basis of users review. This reduces the chances of data lost and stole from individuals
device.
Fingerprint Scanner and card reader: These types of scanners are available in the
combination of USB scanner and card reader together. Through this way it provide two
classification of each block involved in normalization process.5. Filtering: On the basis of above process identified image is filtered by certain filters in
order to generate enhanced image. Minutiae Extraction: The process of minutiae extraction involve five stages such as
input image, orientation field, extracted ridges, thinned ridges and minutiae points.
During this process image is converted into binary form and on the basis of that reduced
ridge ethicalness is created . The popular method for this process is Crossing number,
under this skeleton of image is considered where it is divided into eight segment of
pattern. And by comparing with neighbours result is generated. By addition and
subtraction of adjacent pixels considerable output is generated.
Minutiae Matching: under this process matching takes place between the image in
database and input one.
Types of fingerprint scanning devices: There are various types of fingerprint devices are
available on the basis of their technologies, size and operation are describe below:
USB Fingerprint Device: This is one of the popularly known fingerprint device which
provide ride of remembering complex text code password to customers. They are
composed of CMOS sensor technologies which is considered as best service provider
among its peer. They are available under 77.77 Pound and can easily convert simplest
PC into high tech device. On the basis of users review. This device is useful for
individual as well as businesses for security purpose. As they are provided with USB so
they provide easy installation interface to users. And also provided at considerable price
(Dranove, Forman, Goldfarb, and Greenstein, 2014).
Keyboard Fingerprint Device: Now considering security as major issues PC are also
available with fingerprint scanner. Along with this additional text code passwords are
also provided with that to provide backup option. As no two person can have same print
so this is considered as lowest risk provider. They are available under 124.40 pound. On
the basis of users review. This reduces the chances of data lost and stole from individuals
device.
Fingerprint Scanner and card reader: These types of scanners are available in the
combination of USB scanner and card reader together. Through this way it provide two

levels of security. This devices are commonly used for commercial users. Such as large
networks and enterprises use this techniques for encryption. They are available under
31.03 pound. On the basis of users review the price of product is affordable along with
this it is portable and mobile.
Car Fingerprint Scanner: This is newly used feature of auto mobiles. Through this
facility in case if driver forget key in that ca he can open the door and start engine by
scanning. Along with this it reduces the chances of theft of vehicles. They are available at
the price of 27686120.00 pound. On the basis of users review this decreases the chances
of car stolen and also give ride of carrying keys (Kautz, and Pries-Heje, eds., 2013).
On the basis of research done by industrial experts, this kinds of devices are installed at
every places such as hospitals, educational institutes and offices for identification of students and
staff, tracking patients in hospitals. These devices are considered as a major safety provider and
along with this it is unbreakable security layer. So on the basis of above description this can be
considered as efficient devices and also help to maintain record digitally. Through this user can
be ensure of safety because through this risk level of devices automatically become negligible.
Along with this is can be used to track the entry and exit time of staff ad students and track
patient count at hospital. It is recommended to install fingerprint devices in order to improve
security.
Steps involved in face recognition system identification process:
(Source: Kautz, and Pries-Heje, eds., 2013)
In order to recognition face using biometric-security devices following process. Under
this input is provided in the form of image which is being capture by any scanner that is present
into device through this image is stored for face detection. After this step pre-processing of
image takes place. On the basis of per-processing result feature extraction of image takes place.
On the basis of that training and evaluation of image take place. If result generated by detection
Illustration 1: Face recognition system
networks and enterprises use this techniques for encryption. They are available under
31.03 pound. On the basis of users review the price of product is affordable along with
this it is portable and mobile.
Car Fingerprint Scanner: This is newly used feature of auto mobiles. Through this
facility in case if driver forget key in that ca he can open the door and start engine by
scanning. Along with this it reduces the chances of theft of vehicles. They are available at
the price of 27686120.00 pound. On the basis of users review this decreases the chances
of car stolen and also give ride of carrying keys (Kautz, and Pries-Heje, eds., 2013).
On the basis of research done by industrial experts, this kinds of devices are installed at
every places such as hospitals, educational institutes and offices for identification of students and
staff, tracking patients in hospitals. These devices are considered as a major safety provider and
along with this it is unbreakable security layer. So on the basis of above description this can be
considered as efficient devices and also help to maintain record digitally. Through this user can
be ensure of safety because through this risk level of devices automatically become negligible.
Along with this is can be used to track the entry and exit time of staff ad students and track
patient count at hospital. It is recommended to install fingerprint devices in order to improve
security.
Steps involved in face recognition system identification process:
(Source: Kautz, and Pries-Heje, eds., 2013)
In order to recognition face using biometric-security devices following process. Under
this input is provided in the form of image which is being capture by any scanner that is present
into device through this image is stored for face detection. After this step pre-processing of
image takes place. On the basis of per-processing result feature extraction of image takes place.
On the basis of that training and evaluation of image take place. If result generated by detection
Illustration 1: Face recognition system
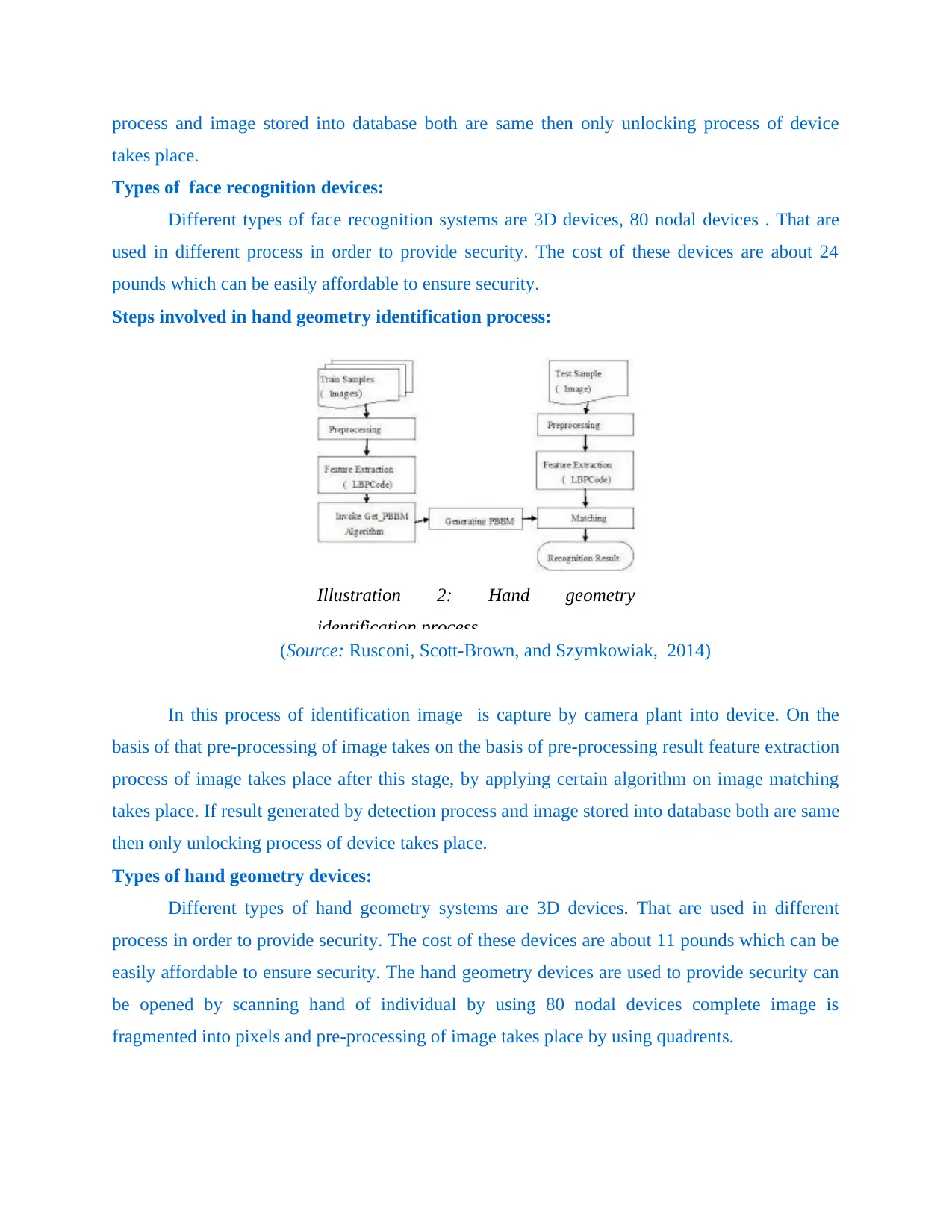
process and image stored into database both are same then only unlocking process of device
takes place.
Types of face recognition devices:
Different types of face recognition systems are 3D devices, 80 nodal devices . That are
used in different process in order to provide security. The cost of these devices are about 24
pounds which can be easily affordable to ensure security.
Steps involved in hand geometry identification process:
(Source: Rusconi, Scott-Brown, and Szymkowiak, 2014)
In this process of identification image is capture by camera plant into device. On the
basis of that pre-processing of image takes on the basis of pre-processing result feature extraction
process of image takes place after this stage, by applying certain algorithm on image matching
takes place. If result generated by detection process and image stored into database both are same
then only unlocking process of device takes place.
Types of hand geometry devices:
Different types of hand geometry systems are 3D devices. That are used in different
process in order to provide security. The cost of these devices are about 11 pounds which can be
easily affordable to ensure security. The hand geometry devices are used to provide security can
be opened by scanning hand of individual by using 80 nodal devices complete image is
fragmented into pixels and pre-processing of image takes place by using quadrents.
Illustration 2: Hand geometry
identification process
takes place.
Types of face recognition devices:
Different types of face recognition systems are 3D devices, 80 nodal devices . That are
used in different process in order to provide security. The cost of these devices are about 24
pounds which can be easily affordable to ensure security.
Steps involved in hand geometry identification process:
(Source: Rusconi, Scott-Brown, and Szymkowiak, 2014)
In this process of identification image is capture by camera plant into device. On the
basis of that pre-processing of image takes on the basis of pre-processing result feature extraction
process of image takes place after this stage, by applying certain algorithm on image matching
takes place. If result generated by detection process and image stored into database both are same
then only unlocking process of device takes place.
Types of hand geometry devices:
Different types of hand geometry systems are 3D devices. That are used in different
process in order to provide security. The cost of these devices are about 11 pounds which can be
easily affordable to ensure security. The hand geometry devices are used to provide security can
be opened by scanning hand of individual by using 80 nodal devices complete image is
fragmented into pixels and pre-processing of image takes place by using quadrents.
Illustration 2: Hand geometry
identification process
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RECOMMENDATIONS
On the basis of security features that are provided by these devices, biometric-security
can be considered for security purpose. I would like to recommend these devices in order to
ensure safety and security of home, office or any other place. This can reduce risk at make the
property safe from any kind of theft and stolen of thing. By using various devices such as
fingerprint, face recognisance and hand geometry security different layers of security can be
created. Along with this there are some drawback of these as no machine can provide 100%
accuracy. Due to this user should always consider certain backups.
Advantages and disadvantage of biometrics security
Advantages Disadvantages
Improves security: As it requires biological
traits for verification purpose in that case level
of security automatically get improved because
chances of hacking become negligible.
Environment and usage can affect
measurement: As the process take place by
scanning traits under this process certain rays
may release which may affect enviroment.
Improve customer experience: As customers
are not required to remember due to this load
of remembering password get reduced so
experience get improved.
System are not 100% accurate: Throughput
of this process is not !00% therefore chances
of mistakes always remain as other systems.
Cannot be forgotten or lost: As not need of
password or access card is required and whole
process is dependent on biological traits. In
that case no chance of lost and forgotten will
occur (Rusconi, Scott-Brown, and
Szymkowiak, 2014).
Requirement of additional hardware: in
order to complete this process additional hard
wares are required such as scanner, camera etc.
Reduce operational cost: As process is
dependent on scanner due to which operational
cost of other process automatically get
reduced.
Cannot be reset once compromised: As the
device only be altered at the time installation in
that case reset of the system cannot takes place.
On the basis of security features that are provided by these devices, biometric-security
can be considered for security purpose. I would like to recommend these devices in order to
ensure safety and security of home, office or any other place. This can reduce risk at make the
property safe from any kind of theft and stolen of thing. By using various devices such as
fingerprint, face recognisance and hand geometry security different layers of security can be
created. Along with this there are some drawback of these as no machine can provide 100%
accuracy. Due to this user should always consider certain backups.
Advantages and disadvantage of biometrics security
Advantages Disadvantages
Improves security: As it requires biological
traits for verification purpose in that case level
of security automatically get improved because
chances of hacking become negligible.
Environment and usage can affect
measurement: As the process take place by
scanning traits under this process certain rays
may release which may affect enviroment.
Improve customer experience: As customers
are not required to remember due to this load
of remembering password get reduced so
experience get improved.
System are not 100% accurate: Throughput
of this process is not !00% therefore chances
of mistakes always remain as other systems.
Cannot be forgotten or lost: As not need of
password or access card is required and whole
process is dependent on biological traits. In
that case no chance of lost and forgotten will
occur (Rusconi, Scott-Brown, and
Szymkowiak, 2014).
Requirement of additional hardware: in
order to complete this process additional hard
wares are required such as scanner, camera etc.
Reduce operational cost: As process is
dependent on scanner due to which operational
cost of other process automatically get
reduced.
Cannot be reset once compromised: As the
device only be altered at the time installation in
that case reset of the system cannot takes place.

CONCLUSION
On the basis of above report the following conclusion is drawn. ICT is used to provide
reliable and safe services to businesses and industries in the form of various devices. Biometrics
security is one of the concept. Through this identification and verification of individual takes
place by comparing its biological traits. For this process various stages are involved that are
mentioned above along with this advantages and disadvantages are also considered.
On the basis of above report the following conclusion is drawn. ICT is used to provide
reliable and safe services to businesses and industries in the form of various devices. Biometrics
security is one of the concept. Through this identification and verification of individual takes
place by comparing its biological traits. For this process various stages are involved that are
mentioned above along with this advantages and disadvantages are also considered.

References
Books and journals
Bagga, Hans, and Sharma, 2017. A Biological Immune System (BIS) inspired Mobile Agent
Platform (MAP) security architecture. Expert Systems with Applications, 72, pp.269-282.
Beerling, 2017. Enhanced rock weathering: biological climate change mitigation with co-benefits
for food security?.
Dranove, Forman, Goldfarb, and Greenstein, 2014. The trillion dollar conundrum:
Complementarities and health information technology. American Economic Journal:
Economic Policy, 6(4), pp.239-270.
Kautz, and Pries-Heje, eds., 2013. Diffusion and Adoption of Information Technology:
Proceedings of the first IFIP WG 8.6 working conference on the diffusion and adoption of
information technology, Oslo, Norway, October 1995. Springer.
Miko, and et., 2015. Epidemiological and Biological Determinants of Staphylococcus aureus
Clinical Infection in New York State Maximum Security Prisons. Clinical Infectious
Diseases, 61(2), pp.203-210.
Rusconi, Scott-Brown, and Szymkowiak, 2014. Neuroscience perspectives on
security. Frontiers in human neuroscience, 8.
Singleton, Jacob, Krebs, and Monadjem, 2015. A meeting of mice and men: rodent impacts on
food security, human diseases and wildlife conservation; ecosystem benefits; fascinating
biological models. Wildlife Research, 42(2), pp.83-85.
Smith, and Daniel‐Allegro, 2016, July. Architectural parallels between biological and
engineered solutions in defence and security. In INCOSE International Symposium (Vol.
26, No. 1, pp. 1566-1583).
Watson, Watson, Ackerman, and Gronvall,2017. Expert Views on Biological Threat
Characterization for the US Government: A Delphi Study. Risk Analysis.
Online
Biometric security. Available
through:<https://www.techopedia.com/definition/6203/biometric-security>
[Accessed on 29th May 2017].
Books and journals
Bagga, Hans, and Sharma, 2017. A Biological Immune System (BIS) inspired Mobile Agent
Platform (MAP) security architecture. Expert Systems with Applications, 72, pp.269-282.
Beerling, 2017. Enhanced rock weathering: biological climate change mitigation with co-benefits
for food security?.
Dranove, Forman, Goldfarb, and Greenstein, 2014. The trillion dollar conundrum:
Complementarities and health information technology. American Economic Journal:
Economic Policy, 6(4), pp.239-270.
Kautz, and Pries-Heje, eds., 2013. Diffusion and Adoption of Information Technology:
Proceedings of the first IFIP WG 8.6 working conference on the diffusion and adoption of
information technology, Oslo, Norway, October 1995. Springer.
Miko, and et., 2015. Epidemiological and Biological Determinants of Staphylococcus aureus
Clinical Infection in New York State Maximum Security Prisons. Clinical Infectious
Diseases, 61(2), pp.203-210.
Rusconi, Scott-Brown, and Szymkowiak, 2014. Neuroscience perspectives on
security. Frontiers in human neuroscience, 8.
Singleton, Jacob, Krebs, and Monadjem, 2015. A meeting of mice and men: rodent impacts on
food security, human diseases and wildlife conservation; ecosystem benefits; fascinating
biological models. Wildlife Research, 42(2), pp.83-85.
Smith, and Daniel‐Allegro, 2016, July. Architectural parallels between biological and
engineered solutions in defence and security. In INCOSE International Symposium (Vol.
26, No. 1, pp. 1566-1583).
Watson, Watson, Ackerman, and Gronvall,2017. Expert Views on Biological Threat
Characterization for the US Government: A Delphi Study. Risk Analysis.
Online
Biometric security. Available
through:<https://www.techopedia.com/definition/6203/biometric-security>
[Accessed on 29th May 2017].
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1 out of 11
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


