Report on Operating System Concepts and Virtualization
VerifiedAdded on 2022/09/02
|29
|4801
|13
Report
AI Summary
This report delves into the complexities of operating systems, emphasizing the evolution of virtualization techniques. It begins by introducing the concept of Exokernel operating systems and the utilization of ontologies to enhance information sharing and reusability within the system. The report explores the architecture of virtual machines, detailing their role in emulating hardware and enabling the execution of multiple operating systems on a single physical machine. It reviews different virtualization types, including process-based and system-level virtualization, and explains the virtualization process. The core of the report focuses on KVM (Kernel Virtual Machine) operation, providing insights into its implementation and the steps involved in setting up and managing virtual machines. Furthermore, the report addresses security considerations related to virtual machines and provides an evaluation of the discussed concepts. The report concludes by summarizing the key findings and implications of virtualization in operating systems.

Running head: REPORT ON OPERATING SYSTEM
By
Academic Year: 2019-20
Module: Operating System
By
Academic Year: 2019-20
Module: Operating System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The Operating system is extremely muddled programming and its size is enormous. The
difficulties overseeing operating systems administrations have a gigantic number of
administrations and operating systems refresh programming. In this paper, we worried about
the Exokernel operating system structure for more speculation and reusability. To encourage
information sharing and reusability the metaphysics based has been created in man-made
consciousness(MP, Kumar, Pai, and Gopal, 2016, July). Likewise, a semantic character in
cosmology based will diminish the number of administrations rather than keep every one of
them. In this paper, metaphysics alludes to a layer of interfaces and administrations that lives
between the application and the operating system is proposed. The proposed administration's
cosmology based encourages the advancement, organization and the executives of the
implanted system. Additionally, The proposed metaphysics based appropriate for any
operating system. This paper will utilize Service-Oriented cosmology design to the
executives the operating system administration improvement.
The Operating system is extremely muddled programming and its size is enormous. The
difficulties overseeing operating systems administrations have a gigantic number of
administrations and operating systems refresh programming. In this paper, we worried about
the Exokernel operating system structure for more speculation and reusability. To encourage
information sharing and reusability the metaphysics based has been created in man-made
consciousness(MP, Kumar, Pai, and Gopal, 2016, July). Likewise, a semantic character in
cosmology based will diminish the number of administrations rather than keep every one of
them. In this paper, metaphysics alludes to a layer of interfaces and administrations that lives
between the application and the operating system is proposed. The proposed administration's
cosmology based encourages the advancement, organization and the executives of the
implanted system. Additionally, The proposed metaphysics based appropriate for any
operating system. This paper will utilize Service-Oriented cosmology design to the
executives the operating system administration improvement.

Table of Contents
Introduction ………………………………………………………………………...... 2
Background information...…………………………………………………………… 3
Virtual Machines ….……………………………………………………………........ 4
Literature Review..……………………………………………................................... 5
Virtualization Types ..…………………………………….......................................... 6
Virtualization Process ……………………………………………………………… 7
Scope and limitations…………................................................................................. 8
KVM (Kernel Virtual Machine) operation…………………………………............ 8
Concepts and Implementation of…………………………………………………....... 9
Setting up ….………………………………………………………………………..10
Management of Virtual Machine ..……………………………………………..….. 17
VM Security Issues ....................................................................................................18
Evaluation ……………………………………………………................................. 20
Conclusion ………………………………………………….................................... 22
References …………………………………………………………..…………….. 23
Introduction ………………………………………………………………………...... 2
Background information...…………………………………………………………… 3
Virtual Machines ….……………………………………………………………........ 4
Literature Review..……………………………………………................................... 5
Virtualization Types ..…………………………………….......................................... 6
Virtualization Process ……………………………………………………………… 7
Scope and limitations…………................................................................................. 8
KVM (Kernel Virtual Machine) operation…………………………………............ 8
Concepts and Implementation of…………………………………………………....... 9
Setting up ….………………………………………………………………………..10
Management of Virtual Machine ..……………………………………………..….. 17
VM Security Issues ....................................................................................................18
Evaluation ……………………………………………………................................. 20
Conclusion ………………………………………………….................................... 22
References …………………………………………………………..…………….. 23
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
An operating system (OS) is a lot of projects that control the execution of utilization projects
and go about as a delegate between a client of a PC and the PC equipment. The operating
system is programming that deals with the PC equipment just as giving a domain to
application projects to run. Ontologies become normal in more applications and as those
applications become bigger and longer-lived, it is getting progressively regular for ontologies
to be created in appropriated conditions by creators with divergent foundations. Ontologies
that are relied upon to be cooperatively made and kept up after some time by creators in
numerous areas present extraordinary difficulties to the issue of calculated demonstrating.
This paper worried about improving the operating system by utilizing metaphysics based.
The Operating system is extremely convoluted programming and its size is huge. Because of
the constrained size of the memory, we can't keep the full OS on the memory. Along these
lines, the OS contains two sections: First-Called KERNEL and it contains the basic schedules
which utilized regularly, it is the core of the operating system. The second part contains
schedules which are required some of the time yet not generally and they are not essential.
Virtualization is a strategy that imitates a genuine framework into a virtual framework that
physically isolated reliance(AbdelSalam, Clad, Filsfils, Salsano, Siracusano, and Veltri, 2017,
July). As such, something that has been virtualized can never again be seen with the eye or
held, however, it has a similar capacity as the first framework. The reason for virtualization is
to make reserve funds from all perspectives. Virtualization is an idea that was first created
during the 1960s to oversee centralized computer equipment. Furthermore in 1960-based PC
x86 design are looked with a similar issue, to be specific unbending nature and
underutilization. Virtualization is constantly utilized above all else just to test the creation or
new framework over a current framework. It expects to get results or to test whether the new
An operating system (OS) is a lot of projects that control the execution of utilization projects
and go about as a delegate between a client of a PC and the PC equipment. The operating
system is programming that deals with the PC equipment just as giving a domain to
application projects to run. Ontologies become normal in more applications and as those
applications become bigger and longer-lived, it is getting progressively regular for ontologies
to be created in appropriated conditions by creators with divergent foundations. Ontologies
that are relied upon to be cooperatively made and kept up after some time by creators in
numerous areas present extraordinary difficulties to the issue of calculated demonstrating.
This paper worried about improving the operating system by utilizing metaphysics based.
The Operating system is extremely convoluted programming and its size is huge. Because of
the constrained size of the memory, we can't keep the full OS on the memory. Along these
lines, the OS contains two sections: First-Called KERNEL and it contains the basic schedules
which utilized regularly, it is the core of the operating system. The second part contains
schedules which are required some of the time yet not generally and they are not essential.
Virtualization is a strategy that imitates a genuine framework into a virtual framework that
physically isolated reliance(AbdelSalam, Clad, Filsfils, Salsano, Siracusano, and Veltri, 2017,
July). As such, something that has been virtualized can never again be seen with the eye or
held, however, it has a similar capacity as the first framework. The reason for virtualization is
to make reserve funds from all perspectives. Virtualization is an idea that was first created
during the 1960s to oversee centralized computer equipment. Furthermore in 1960-based PC
x86 design are looked with a similar issue, to be specific unbending nature and
underutilization. Virtualization is constantly utilized above all else just to test the creation or
new framework over a current framework. It expects to get results or to test whether the new
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

framework has still to be perfect or required further improvement. At that point, some
consequent period virtualization can remain solitary in a parent (have) system. This
understanding attempts to depict the virtualization procedure. It portrays the fundamental
standard of the virtuality(Abeni, Balsini, and Cucinotta, 2016, October).
Background information
This area presents different endeavors to improve the operating system by metaphysics based.
Numerous thoughts do that inside the bit of the operating system. Reference [6] planned
cosmology based document framework yet they can't pass numerous difficulties in their
proposition. Additionally, There are searchers utilizing cosmology based to build up the
operating system in various manners as TELOS and VRTOS In July 2009 Software
innovation inquire about research center, Demontfort college, England proposed virtual
continuous operating system VRTOS with RTOS philosophy center. The RTOS cosmology
characterizes a lot of normal framework benefits as investigate, semaphore, holding up the
line, string, booking. The RTOS philosophy administrations are utilized as a standard for
versatile programming advancement. In The VRTOS guessed that the memory the executives
and the clock are two of pivotal highlights for the application layer likewise knead line,
mutex and semaphore administrations are created as framework autonomous part(Beserra,
Moreno, Endo, Barreto, Fernandes, and Sadok, 2017).
Virtual Machines
Virtual machine (VM) is a gadget that regularly is a product or working framework, which
can not be seen physically however can be run in a situation other. For this situation, the VM
is alluded to as a "visitor" because the gadget just rides, while the earth is running purported
consequent period virtualization can remain solitary in a parent (have) system. This
understanding attempts to depict the virtualization procedure. It portrays the fundamental
standard of the virtuality(Abeni, Balsini, and Cucinotta, 2016, October).
Background information
This area presents different endeavors to improve the operating system by metaphysics based.
Numerous thoughts do that inside the bit of the operating system. Reference [6] planned
cosmology based document framework yet they can't pass numerous difficulties in their
proposition. Additionally, There are searchers utilizing cosmology based to build up the
operating system in various manners as TELOS and VRTOS In July 2009 Software
innovation inquire about research center, Demontfort college, England proposed virtual
continuous operating system VRTOS with RTOS philosophy center. The RTOS cosmology
characterizes a lot of normal framework benefits as investigate, semaphore, holding up the
line, string, booking. The RTOS philosophy administrations are utilized as a standard for
versatile programming advancement. In The VRTOS guessed that the memory the executives
and the clock are two of pivotal highlights for the application layer likewise knead line,
mutex and semaphore administrations are created as framework autonomous part(Beserra,
Moreno, Endo, Barreto, Fernandes, and Sadok, 2017).
Virtual Machines
Virtual machine (VM) is a gadget that regularly is a product or working framework, which
can not be seen physically however can be run in a situation other. For this situation, the VM
is alluded to as a "visitor" because the gadget just rides, while the earth is running purported

"have." The essential idea of the virtual machine is that it imitates the equipment of a PC
comprising of a CPU, memory, HDD into numerous execution conditions, so that appears to
have the physical gadget on every virtualization. VM to show up for their preliminary to run
various working frameworks on a solitary PC.
Figure 1 shows the virtual machine engineering. The server can covers a few virtual
machines all the while. Virtual machine innovation has numerous capacities, for example,
equipment union, encourage the salvage framework, and run the product before. One of the
most significant utilization of virtual machine innovation is cross-stage joining. Some other
significant applications are:
1. Server Consolidation. On the off chance that few servers run applications that solitary
takes up almost no assets, VM can be utilized to fuse the applications that sudden spike in
comprising of a CPU, memory, HDD into numerous execution conditions, so that appears to
have the physical gadget on every virtualization. VM to show up for their preliminary to run
various working frameworks on a solitary PC.
Figure 1 shows the virtual machine engineering. The server can covers a few virtual
machines all the while. Virtual machine innovation has numerous capacities, for example,
equipment union, encourage the salvage framework, and run the product before. One of the
most significant utilization of virtual machine innovation is cross-stage joining. Some other
significant applications are:
1. Server Consolidation. On the off chance that few servers run applications that solitary
takes up almost no assets, VM can be utilized to fuse the applications that sudden spike in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

demand for just a single server, regardless of whether the application necessitates that the
working framework is unique(Karpov, Fedotova, Kachan, Kirova, and Siemens, 2017, July).
2. Mechanization and union. Each VM can go about various situations; this enables engineers
so no compelling reason to give condition physically.
3. Simple System Recovery. Virtualization can be utilized for framework recuperation that
requires convenience and adaptability crosswise over stages.
4. Exhibit programming. With VM innovation, clean working framework, and its design can
be given rapidly.
Literature review
Our perspective on metaphysics based semantic customized search is that Ontology-based
may improve the usefulness of the web crawlers on the framework by adding semantics to the
data substance of the framework. Metaphysics is utilized to characterize the importance of the
terms rising on the information records and these can be utilized to make surmisings to get
more data identified with the objects of intrigue. Cosmology based can be utilized to depict
areas and to construe on relations of records(Kon, Mizusawa, Umezawa, Yamaguchi, and
Tao, 2017, December). The errand of a grouping, in this unique circumstance, is to dole out
working framework is unique(Karpov, Fedotova, Kachan, Kirova, and Siemens, 2017, July).
2. Mechanization and union. Each VM can go about various situations; this enables engineers
so no compelling reason to give condition physically.
3. Simple System Recovery. Virtualization can be utilized for framework recuperation that
requires convenience and adaptability crosswise over stages.
4. Exhibit programming. With VM innovation, clean working framework, and its design can
be given rapidly.
Literature review
Our perspective on metaphysics based semantic customized search is that Ontology-based
may improve the usefulness of the web crawlers on the framework by adding semantics to the
data substance of the framework. Metaphysics is utilized to characterize the importance of the
terms rising on the information records and these can be utilized to make surmisings to get
more data identified with the objects of intrigue. Cosmology based can be utilized to depict
areas and to construe on relations of records(Kon, Mizusawa, Umezawa, Yamaguchi, and
Tao, 2017, December). The errand of a grouping, in this unique circumstance, is to dole out
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

each record to a class of a given arrangement of classes. Assume a file of a progressive record
framework, for example, the record framework converted into a cosmology store and
metadata is added to each document. In the customized search which includes demonstrating,
the client setting as "ontological profiles" by appointing certainly inferred intrigue scores to
existing ideas in area metaphysics. Each ontological client profile is at first an occasion of the
reference metaphysics. Every idea in the client profile is commented on with an intriguing
score which has an underlying estimation of one. As the client associates with the framework
by choosing or review new records, the ontological client profile is refreshed and the
explanations for existing ideas are altered by spreading initiation. Hence, the client setting is
kept up and refreshed gradually dependent on the client's progressing conduct(Callegati,
Cerroni, and Contoli, 2016).
Virtualization Types
Virtual Machine gives comfort concerning the conveyance of equipment assets that exist in
every visitor framework, each running a visitor working framework itself. The product gives
the virtualization is known as a virtual machine screen or hypervisor. A hypervisor can run on
equipment or a working framework. The primary points of interest and VM framework are:
1. Different working framework condition can be run on a similar PC, in solid seclusion
between situations
framework, for example, the record framework converted into a cosmology store and
metadata is added to each document. In the customized search which includes demonstrating,
the client setting as "ontological profiles" by appointing certainly inferred intrigue scores to
existing ideas in area metaphysics. Each ontological client profile is at first an occasion of the
reference metaphysics. Every idea in the client profile is commented on with an intriguing
score which has an underlying estimation of one. As the client associates with the framework
by choosing or review new records, the ontological client profile is refreshed and the
explanations for existing ideas are altered by spreading initiation. Hence, the client setting is
kept up and refreshed gradually dependent on the client's progressing conduct(Callegati,
Cerroni, and Contoli, 2016).
Virtualization Types
Virtual Machine gives comfort concerning the conveyance of equipment assets that exist in
every visitor framework, each running a visitor working framework itself. The product gives
the virtualization is known as a virtual machine screen or hypervisor. A hypervisor can run on
equipment or a working framework. The primary points of interest and VM framework are:
1. Different working framework condition can be run on a similar PC, in solid seclusion
between situations

2. VM can give the guidance set engineering (ISA) that is distinctive to that of the equipment.
The working framework on the visitor doesn't have the equivalent working framework. The
utilization of the VM to help a wide range of working frameworks turned out to be so
mainstream in installed frameworks, where the continuous working framework is utilized
related to a significant level working framework, for example, Linux or Windows. Another
capacity is to sandbox that disengages changes in the codes that doubt emerges from the OS
that can not be trusted because it is still in the advancement arrange. VM has different
advantages in the improvement of working frameworks, for example, get to preferred
investigating and reboots quicker over the first machine(Celesti, Mulfari, Fazio, Villari, and
Puliafito, 2016, May).
Virtualization Process
A virtual machine process here and there called an application virtual machine runs as a
typical application inside a working framework and supports the procedure. VM process was
made at the time the procedure was started and is obliterated when the procedure exits. The
point is to give a programming situation that is stage free which abstracts the subtleties of the
product or working framework and permits a program executed similarly on any stage. The
procedure VM gives an elevated level reflection process is executed clicking VM-use
translators. VM-type got mainstream with the Java programming language, which is executed
by the Java Virtual Machine. Another model is the .NET Framework, which runs on a VM
called the Common Language Runtime. An extraordinary instance of the VM procedure is a
framework that modified works of the correspondence system of group PCs. Vanya is
anything but a solitary procedure, but instead one procedure for each physical machine in the
bunch. VM is intended to rearrange the work program an application in parallel with letting
The working framework on the visitor doesn't have the equivalent working framework. The
utilization of the VM to help a wide range of working frameworks turned out to be so
mainstream in installed frameworks, where the continuous working framework is utilized
related to a significant level working framework, for example, Linux or Windows. Another
capacity is to sandbox that disengages changes in the codes that doubt emerges from the OS
that can not be trusted because it is still in the advancement arrange. VM has different
advantages in the improvement of working frameworks, for example, get to preferred
investigating and reboots quicker over the first machine(Celesti, Mulfari, Fazio, Villari, and
Puliafito, 2016, May).
Virtualization Process
A virtual machine process here and there called an application virtual machine runs as a
typical application inside a working framework and supports the procedure. VM process was
made at the time the procedure was started and is obliterated when the procedure exits. The
point is to give a programming situation that is stage free which abstracts the subtleties of the
product or working framework and permits a program executed similarly on any stage. The
procedure VM gives an elevated level reflection process is executed clicking VM-use
translators. VM-type got mainstream with the Java programming language, which is executed
by the Java Virtual Machine. Another model is the .NET Framework, which runs on a VM
called the Common Language Runtime. An extraordinary instance of the VM procedure is a
framework that modified works of the correspondence system of group PCs. Vanya is
anything but a solitary procedure, but instead one procedure for each physical machine in the
bunch. VM is intended to rearrange the work program an application in parallel with letting
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the software engineer center around calculations instead of the correspondence instruments
gave by the interconnect and working frameworks. The way that correspondence was not
covered up and the group isn't developed spoken to as a solitary machine(Claassen, Koning,
and Grosso, 2016, April).
Scope and limitations
The goals of OS are:
(1) To make the PC framework advantageous and simple to use for the client.
(2) To utilize the PC equipment proficiently.
(3) To execute client projects and make taking care of client issues simpler.
Experimental work and analysis
Linux Virtualisation
KVM (Kernel Virtual Machine) operation
KVM or Kernel-Based Virtual Machine gives a virtual situation used to running at least one
extra working framework other than the essential framework without meddling with its
capacities. In KVM, the Linux Kernel utilizes the virtualization innovation by using your
current framework and equipment assets. The new virtual condition made by KVM can be
utilized for giving additional workspace to programming analyzers, engineers, planners and
even home clients(Eiras, Couto, and Rubinstein, 2016, November).
gave by the interconnect and working frameworks. The way that correspondence was not
covered up and the group isn't developed spoken to as a solitary machine(Claassen, Koning,
and Grosso, 2016, April).
Scope and limitations
The goals of OS are:
(1) To make the PC framework advantageous and simple to use for the client.
(2) To utilize the PC equipment proficiently.
(3) To execute client projects and make taking care of client issues simpler.
Experimental work and analysis
Linux Virtualisation
KVM (Kernel Virtual Machine) operation
KVM or Kernel-Based Virtual Machine gives a virtual situation used to running at least one
extra working framework other than the essential framework without meddling with its
capacities. In KVM, the Linux Kernel utilizes the virtualization innovation by using your
current framework and equipment assets. The new virtual condition made by KVM can be
utilized for giving additional workspace to programming analyzers, engineers, planners and
even home clients(Eiras, Couto, and Rubinstein, 2016, November).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

0
In this instructional exercise, we will portray how to introduce and utilize a virtual machine
utilizing the open-source virtualization stage KVM. The directions and methods depicted in
this instructional exercise have been run on a Ubuntu 18 framework on an x86 processor.
Kernel virtualization is any of the various techniques where an operating system (OS) part is
adjusted to help various clients running applications at the same time on a solitary machine.
The portion is the basic center of an operating system that gives essential administrations to
every single other kernel of the OS. Virtualization is a method for making various virtual
frameworks that offer physical register assets, for example, processor cycles, memory space,
arrange transmission capacity, etc. In the regular virtualization model, a hypervisor
segregates operating systems and applications from the fundamental PC equipment,
permitting the host machine to work numerous, free virtual machines (VMs) as visitors,
which share the host assets. kernel virtualization might be founded on either hypervisors or
compartments.
Concepts and implementations
A virtual machine gives a completely ensured and disengaged reproduction of the
fundamental physical framework. It adopts a layered strategy to accomplish this objective.
We need another layer over the first exposed frameworks to digest the physical assets and
give an interface to working frameworks running on it. This layer is called the Virtual
Machine Monitor (VMM). The VMM is the fundamental piece of the virtual machine
execution since it plays out the interpretation between the exposed equipment and virtualized
basic stage: giving virtual processors, memory, and virtualized I/O gadgets. Since all the
virtual machines share the same exposed equipment, the Virtual Machine Monitor ought to
In this instructional exercise, we will portray how to introduce and utilize a virtual machine
utilizing the open-source virtualization stage KVM. The directions and methods depicted in
this instructional exercise have been run on a Ubuntu 18 framework on an x86 processor.
Kernel virtualization is any of the various techniques where an operating system (OS) part is
adjusted to help various clients running applications at the same time on a solitary machine.
The portion is the basic center of an operating system that gives essential administrations to
every single other kernel of the OS. Virtualization is a method for making various virtual
frameworks that offer physical register assets, for example, processor cycles, memory space,
arrange transmission capacity, etc. In the regular virtualization model, a hypervisor
segregates operating systems and applications from the fundamental PC equipment,
permitting the host machine to work numerous, free virtual machines (VMs) as visitors,
which share the host assets. kernel virtualization might be founded on either hypervisors or
compartments.
Concepts and implementations
A virtual machine gives a completely ensured and disengaged reproduction of the
fundamental physical framework. It adopts a layered strategy to accomplish this objective.
We need another layer over the first exposed frameworks to digest the physical assets and
give an interface to working frameworks running on it. This layer is called the Virtual
Machine Monitor (VMM). The VMM is the fundamental piece of the virtual machine
execution since it plays out the interpretation between the exposed equipment and virtualized
basic stage: giving virtual processors, memory, and virtualized I/O gadgets. Since all the
virtual machines share the same exposed equipment, the Virtual Machine Monitor ought to
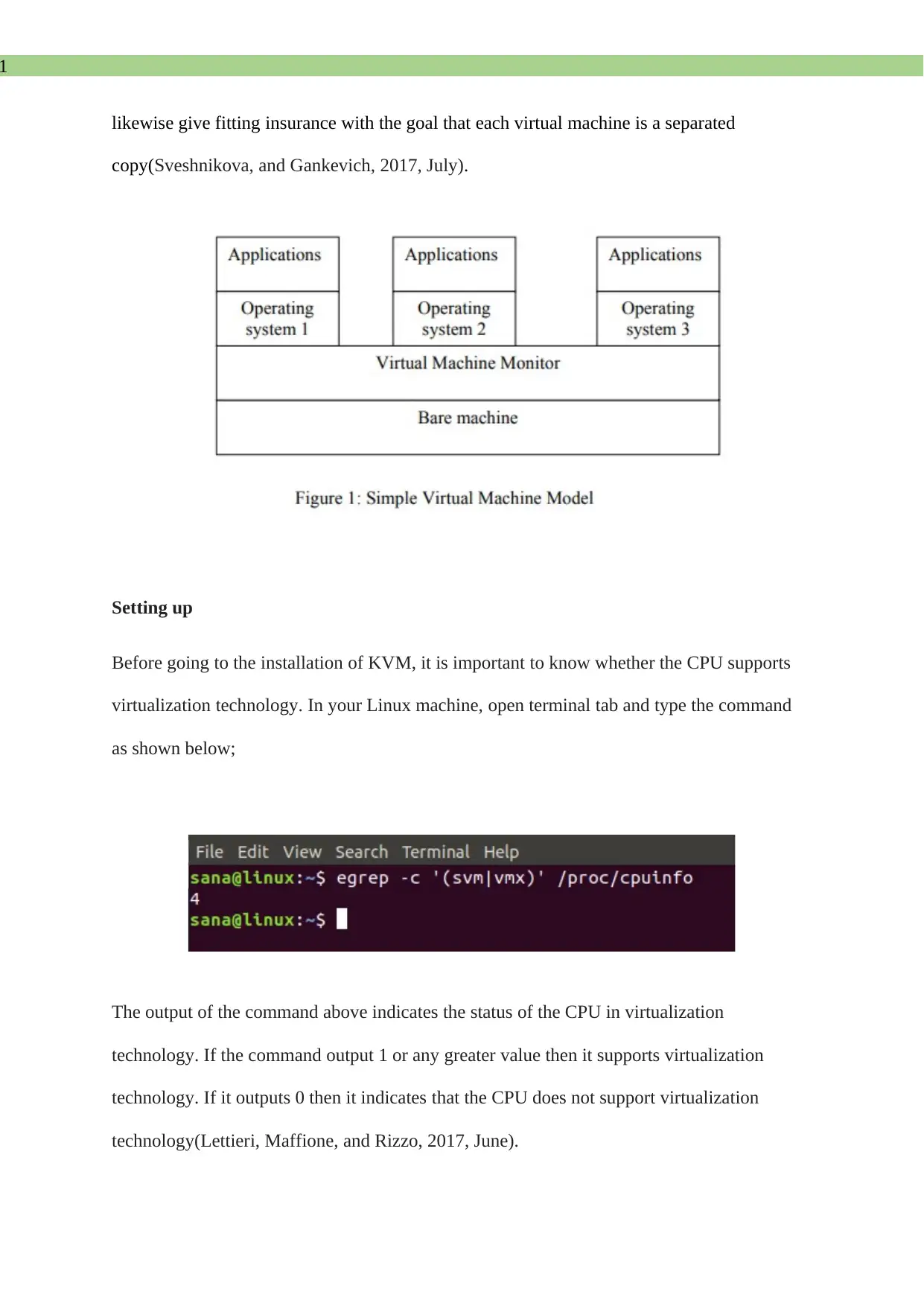
1
likewise give fitting insurance with the goal that each virtual machine is a separated
copy(Sveshnikova, and Gankevich, 2017, July).
Setting up
Before going to the installation of KVM, it is important to know whether the CPU supports
virtualization technology. In your Linux machine, open terminal tab and type the command
as shown below;
The output of the command above indicates the status of the CPU in virtualization
technology. If the command output 1 or any greater value then it supports virtualization
technology. If it outputs 0 then it indicates that the CPU does not support virtualization
technology(Lettieri, Maffione, and Rizzo, 2017, June).
likewise give fitting insurance with the goal that each virtual machine is a separated
copy(Sveshnikova, and Gankevich, 2017, July).
Setting up
Before going to the installation of KVM, it is important to know whether the CPU supports
virtualization technology. In your Linux machine, open terminal tab and type the command
as shown below;
The output of the command above indicates the status of the CPU in virtualization
technology. If the command output 1 or any greater value then it supports virtualization
technology. If it outputs 0 then it indicates that the CPU does not support virtualization
technology(Lettieri, Maffione, and Rizzo, 2017, June).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 29
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


