Ransomware: An Analysis of Mitigation Strategies and Consequences
VerifiedAdded on 2020/04/29
|18
|4239
|77
Report
AI Summary
This report delves into the multifaceted world of ransomware, a critical threat in the digital age. It begins with an introduction to ransomware, defining it as a form of malware that restricts user access to their systems or files, demanding a ransom for their release. The report then reviews the existing literature, explaining how ransomware operates, including the use of encryption techniques like AES and RSA, and the methods attackers employ to infiltrate systems, such as phishing and RaaS. It examines the increasing prevalence of ransomware attacks, citing statistics on their frequency and the sectors most affected. The report highlights the WannaCry ransomware attack, detailing its impact and the demand for Bitcoin. Furthermore, it analyzes the consequences of both paying and not paying the ransom, discussing mitigation strategies to prevent and respond to these attacks. The report concludes by emphasizing the importance of staying updated with the latest versions of operating systems and adopting proactive security measures to safeguard against ransomware threats.

Running head: RANSOMWARE: TO BE PAY OR NOT
Ransomware: To be pay or not
Name of the Student
Name of the University
Author Note
Ransomware: To be pay or not
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RANSOMWARE: TO BE PAY OR NOT
Table of Contents
Abstract............................................................................................................................................3
1) Introduction.................................................................................................................................3
2) Literature review.........................................................................................................................4
2.1) What is Ransomware............................................................................................................4
2.2) How it works........................................................................................................................5
2.3) What happens.......................................................................................................................5
2.4) Increasing Problems.............................................................................................................6
3) The Scam...................................................................................................................................10
3.1) The profit............................................................................................................................11
4) Impact of Paying Ransomware..................................................................................................11
5) Impact of not Paying Ransomware...........................................................................................12
6) Mitigation Strategies.................................................................................................................13
7) Conclusion.................................................................................................................................14
8) References.................................................................................................................................15
Table of Contents
Abstract............................................................................................................................................3
1) Introduction.................................................................................................................................3
2) Literature review.........................................................................................................................4
2.1) What is Ransomware............................................................................................................4
2.2) How it works........................................................................................................................5
2.3) What happens.......................................................................................................................5
2.4) Increasing Problems.............................................................................................................6
3) The Scam...................................................................................................................................10
3.1) The profit............................................................................................................................11
4) Impact of Paying Ransomware..................................................................................................11
5) Impact of not Paying Ransomware...........................................................................................12
6) Mitigation Strategies.................................................................................................................13
7) Conclusion.................................................................................................................................14
8) References.................................................................................................................................15

RANSOMWARE: TO BE PAY OR NOT
Abstract
In this new world of technology, everything is being automated and data and information are being saved
over the internet for easy accessibility and availability. Ransomware has become one of the most concerning topics
for this digital world as the world is changing and digitization has become a pillar for the enhancement of life living
for human beings. Ransomware is an illegal activity made by certain highly trained programmers or by the support
of such programmers. Such unwanted incident opposes the user from getting access to the personal files and
information of the user and money is demanded in exchange of the cryptographic keys that is a necessary coding for
again gaining access to those files. The purpose of this report is to present a thorough research on the ransomware
attacks and present all the objectives related to the ransom and ransomware malicious coding. This report presents
a literature review on the aspects related to the ransomware attacks that will be helpful in understanding what is it,
what how it works, and what happens in the ransomware attack. This report also presents the technical aspects
related to the ransomware attack, which highlights on how this attack keep on through malicious coding. This report
also highlights on the WannaCry ransomware attack that was represented as the most dangerous and mass
destructive ransomware attack and explains how the attack was made and how much destruction could be such
attacks. This report also highlights on the objectives related to the consequences of paying and not paying the
ransomware attack.
1) Introduction
Ransomware is a malware, which prevents the system or limits the user to access get access to
their systems. This can be done by locking the screen of the system or can also be done by
locking the files of the user unless a ransom is paid (Mohurle and Patil, 2017). The data that are
present in the system of the user is locked by the malware ransomware that is mainly done by
encryption and an amount of money is demanded by the attacker and only after the payment, the
files are decrypted (Smith, 2016). There have arrived modern families of Ransomware. They are
mainly categorized as crypto-ransomware that only encrypts certain types of files only on the
Abstract
In this new world of technology, everything is being automated and data and information are being saved
over the internet for easy accessibility and availability. Ransomware has become one of the most concerning topics
for this digital world as the world is changing and digitization has become a pillar for the enhancement of life living
for human beings. Ransomware is an illegal activity made by certain highly trained programmers or by the support
of such programmers. Such unwanted incident opposes the user from getting access to the personal files and
information of the user and money is demanded in exchange of the cryptographic keys that is a necessary coding for
again gaining access to those files. The purpose of this report is to present a thorough research on the ransomware
attacks and present all the objectives related to the ransom and ransomware malicious coding. This report presents
a literature review on the aspects related to the ransomware attacks that will be helpful in understanding what is it,
what how it works, and what happens in the ransomware attack. This report also presents the technical aspects
related to the ransomware attack, which highlights on how this attack keep on through malicious coding. This report
also highlights on the WannaCry ransomware attack that was represented as the most dangerous and mass
destructive ransomware attack and explains how the attack was made and how much destruction could be such
attacks. This report also highlights on the objectives related to the consequences of paying and not paying the
ransomware attack.
1) Introduction
Ransomware is a malware, which prevents the system or limits the user to access get access to
their systems. This can be done by locking the screen of the system or can also be done by
locking the files of the user unless a ransom is paid (Mohurle and Patil, 2017). The data that are
present in the system of the user is locked by the malware ransomware that is mainly done by
encryption and an amount of money is demanded by the attacker and only after the payment, the
files are decrypted (Smith, 2016). There have arrived modern families of Ransomware. They are
mainly categorized as crypto-ransomware that only encrypts certain types of files only on the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RANSOMWARE: TO BE PAY OR NOT
encrypted systems. They enforce the user to pay a certain amount of money through online
payment so that they can get the key for decryption.
The aim of this report is to present a thorough research on the working and consequences of the
ransomware attack and put the focus on the mitigation that could be applied in a manner to
prevent such attacks. The literature review presents a thorough explanation on the related topic
and presents the thought presented by several researchers in different articles. This report also
presents how an individual and organization could prevent such attacks and be safe from getting
looted by an intruder.
2) Literature review
2.1) What is Ransomware
It can be categorized into the cyberattacks in which the victim becomes the prey of a high profile
programmer and pushed away from accessing own personal information and data saved in the
database. After this, the programmer used to claim money in exchange for providing the access
to the same data or information. Ransomware predominantly encrypts the files through using
AES algorithm by using some good methods in a manner to encrypt those files with unique
coding. Earlier it was reported that the average payment made for the ransom was $500 per
incident but it is being expected for now that the price is being doubled or tripled as the
organizations are continuously paying the demand (Ali, 2017). When the system is hacked by the
intruder the user gets a pop-up on the screen with written information that the system is hacked
or the files are encrypted and the user can only get the access to the data if he or she is ready to
pay the ransom. Most common ransomware includes crypto-ransomware and Crypto-Locker;
those have been evolved during 2013 and are capable of encrypting the files once entered the
encrypted systems. They enforce the user to pay a certain amount of money through online
payment so that they can get the key for decryption.
The aim of this report is to present a thorough research on the working and consequences of the
ransomware attack and put the focus on the mitigation that could be applied in a manner to
prevent such attacks. The literature review presents a thorough explanation on the related topic
and presents the thought presented by several researchers in different articles. This report also
presents how an individual and organization could prevent such attacks and be safe from getting
looted by an intruder.
2) Literature review
2.1) What is Ransomware
It can be categorized into the cyberattacks in which the victim becomes the prey of a high profile
programmer and pushed away from accessing own personal information and data saved in the
database. After this, the programmer used to claim money in exchange for providing the access
to the same data or information. Ransomware predominantly encrypts the files through using
AES algorithm by using some good methods in a manner to encrypt those files with unique
coding. Earlier it was reported that the average payment made for the ransom was $500 per
incident but it is being expected for now that the price is being doubled or tripled as the
organizations are continuously paying the demand (Ali, 2017). When the system is hacked by the
intruder the user gets a pop-up on the screen with written information that the system is hacked
or the files are encrypted and the user can only get the access to the data if he or she is ready to
pay the ransom. Most common ransomware includes crypto-ransomware and Crypto-Locker;
those have been evolved during 2013 and are capable of encrypting the files once entered the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RANSOMWARE: TO BE PAY OR NOT
system of the computers. Ali Murthy and Kohun (2016) stated that as the evolution is on pace for
all the technologies, such attacks are also getting advanced and RSA encryption are also being
used along with the AES encryption technology that results in, decryption needs two
cryptographic keys for again gaining access to the files.
2.2) How it works
The malicious coding uses AES and RSA encryption key for encrypting the files, AES
decryption key has been written over the files saved into the system by the malware itself. In
addition to the AES, the RSA decryption key is executed over the AES decryption key that uses
public key and it has been embedded in the malware itself as stated earlier that results in the need
of private key in a manner to decrypt the files (Yaqoob et al., 2017). It was found after some
researchers that crypto-locker infections are being spread by the spam campaign. The malicious
attachments have been attached to the message belonging to the TROJ_UPATRE that has been a
simple coding for smoothly downloads into the system and of very small. In this new digital
world, an individual with no technical background is also capable of ordering less expensive
RaaS (Ransomware as a Service) with little or not any effort. In this service, the coding providers
enable the intruder to get the ransom and take the percentage of that ransom (Lonidm, Scarlat
and Militaru, 2017). There are various ways to inject the malicious coding to encrypt the files,
such as phishing is one of the common attack strategies. The user might get a mail with the same
logo as the organization is using with attached files that includes the malicious program. A pop-
up with a deadline and if the ransom is not paid within that deadline the files are supposed to be
deleted and for this private cryptographic is needed in a manner to get the access of the files
again.
system of the computers. Ali Murthy and Kohun (2016) stated that as the evolution is on pace for
all the technologies, such attacks are also getting advanced and RSA encryption are also being
used along with the AES encryption technology that results in, decryption needs two
cryptographic keys for again gaining access to the files.
2.2) How it works
The malicious coding uses AES and RSA encryption key for encrypting the files, AES
decryption key has been written over the files saved into the system by the malware itself. In
addition to the AES, the RSA decryption key is executed over the AES decryption key that uses
public key and it has been embedded in the malware itself as stated earlier that results in the need
of private key in a manner to decrypt the files (Yaqoob et al., 2017). It was found after some
researchers that crypto-locker infections are being spread by the spam campaign. The malicious
attachments have been attached to the message belonging to the TROJ_UPATRE that has been a
simple coding for smoothly downloads into the system and of very small. In this new digital
world, an individual with no technical background is also capable of ordering less expensive
RaaS (Ransomware as a Service) with little or not any effort. In this service, the coding providers
enable the intruder to get the ransom and take the percentage of that ransom (Lonidm, Scarlat
and Militaru, 2017). There are various ways to inject the malicious coding to encrypt the files,
such as phishing is one of the common attack strategies. The user might get a mail with the same
logo as the organization is using with attached files that includes the malicious program. A pop-
up with a deadline and if the ransom is not paid within that deadline the files are supposed to be
deleted and for this private cryptographic is needed in a manner to get the access of the files
again.

RANSOMWARE: TO BE PAY OR NOT
2.3) What happens
The main motive for the attack of ransomware is that to collect money from the users. Other
cyber attacks notify the user about the attack and there are instructions available about how to get
rid of those attacks. However, the ransomware does not allow such processes (Sitting and Singh,
2016). The payment that is to be done after the attack is that they mainly demand Bitcoins so the
identity of the attack is not known by the cybercrime investigators. The spread of ransomware is
done mainly by email attachments, which infect the application software in the system,
compromised websites, and attacks the external storage device of the system. Remote access
protocols are used by the attackers and they do not use any other forms of user interaction
(Smith, 2017). Highly knowledgeable scammers in system programming use the ransomware
attack in a cyber attack. Email attachments are sent to users. If the user opens the files that are
attached in the mail, their system gets corrupted and they lose the access to the files in their own
system. This is the most common type of cyber attack in the modern world.
2.4) Increasing Problems
The rate of ransomware is seemed to be increasing with very high speed in the current
digital world and it is being estimated that every organization is facing such attack in every forty
seconds ("Kasperskycontenthub", 2017). Businesses around the world are facing ransomware
attacks, more often and in every two minutes it is being estimated that one ransomware attack is
making prey a business.
2.3) What happens
The main motive for the attack of ransomware is that to collect money from the users. Other
cyber attacks notify the user about the attack and there are instructions available about how to get
rid of those attacks. However, the ransomware does not allow such processes (Sitting and Singh,
2016). The payment that is to be done after the attack is that they mainly demand Bitcoins so the
identity of the attack is not known by the cybercrime investigators. The spread of ransomware is
done mainly by email attachments, which infect the application software in the system,
compromised websites, and attacks the external storage device of the system. Remote access
protocols are used by the attackers and they do not use any other forms of user interaction
(Smith, 2017). Highly knowledgeable scammers in system programming use the ransomware
attack in a cyber attack. Email attachments are sent to users. If the user opens the files that are
attached in the mail, their system gets corrupted and they lose the access to the files in their own
system. This is the most common type of cyber attack in the modern world.
2.4) Increasing Problems
The rate of ransomware is seemed to be increasing with very high speed in the current
digital world and it is being estimated that every organization is facing such attack in every forty
seconds ("Kasperskycontenthub", 2017). Businesses around the world are facing ransomware
attacks, more often and in every two minutes it is being estimated that one ransomware attack is
making prey a business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
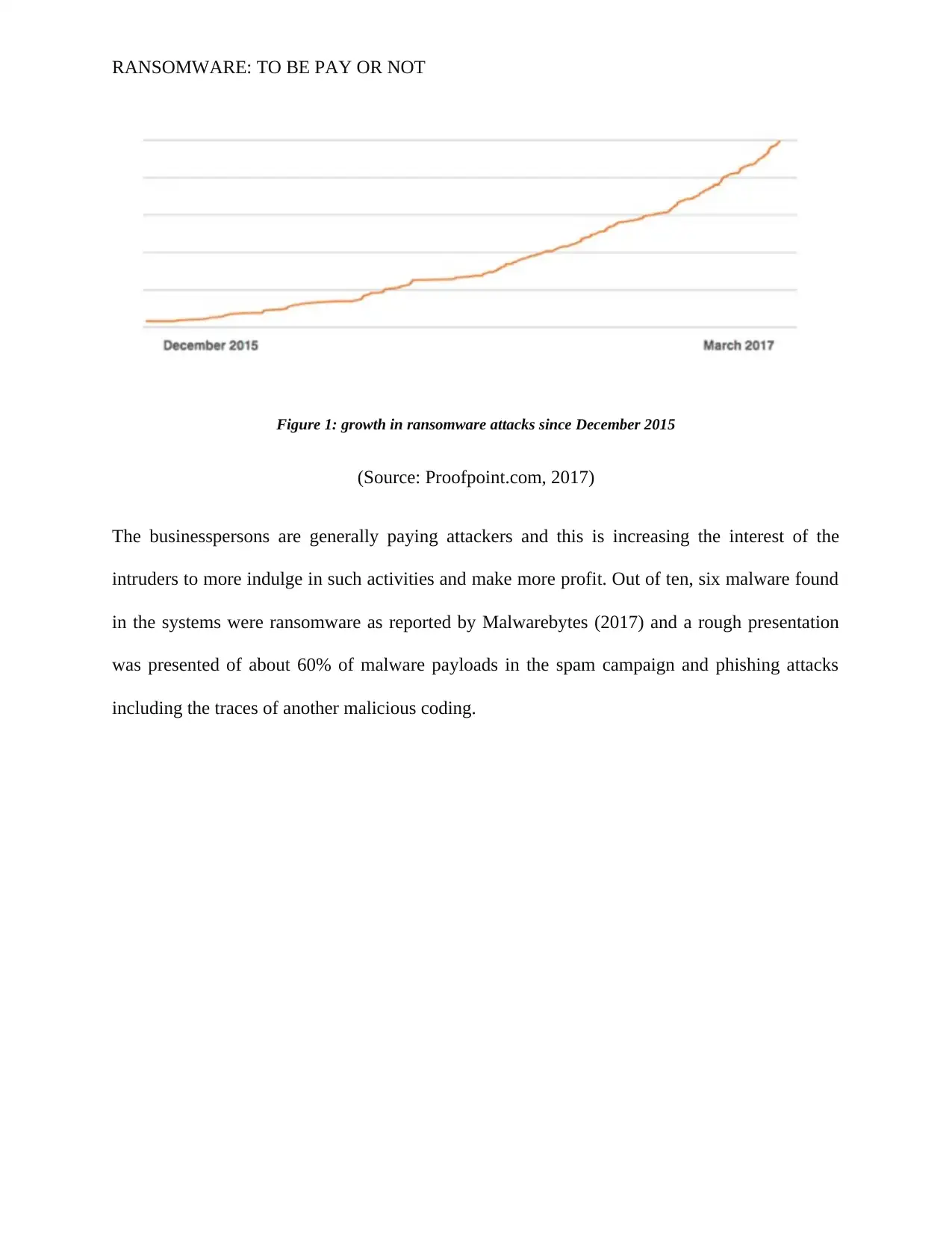
RANSOMWARE: TO BE PAY OR NOT
Figure 1: growth in ransomware attacks since December 2015
(Source: Proofpoint.com, 2017)
The businesspersons are generally paying attackers and this is increasing the interest of the
intruders to more indulge in such activities and make more profit. Out of ten, six malware found
in the systems were ransomware as reported by Malwarebytes (2017) and a rough presentation
was presented of about 60% of malware payloads in the spam campaign and phishing attacks
including the traces of another malicious coding.
Figure 1: growth in ransomware attacks since December 2015
(Source: Proofpoint.com, 2017)
The businesspersons are generally paying attackers and this is increasing the interest of the
intruders to more indulge in such activities and make more profit. Out of ten, six malware found
in the systems were ransomware as reported by Malwarebytes (2017) and a rough presentation
was presented of about 60% of malware payloads in the spam campaign and phishing attacks
including the traces of another malicious coding.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
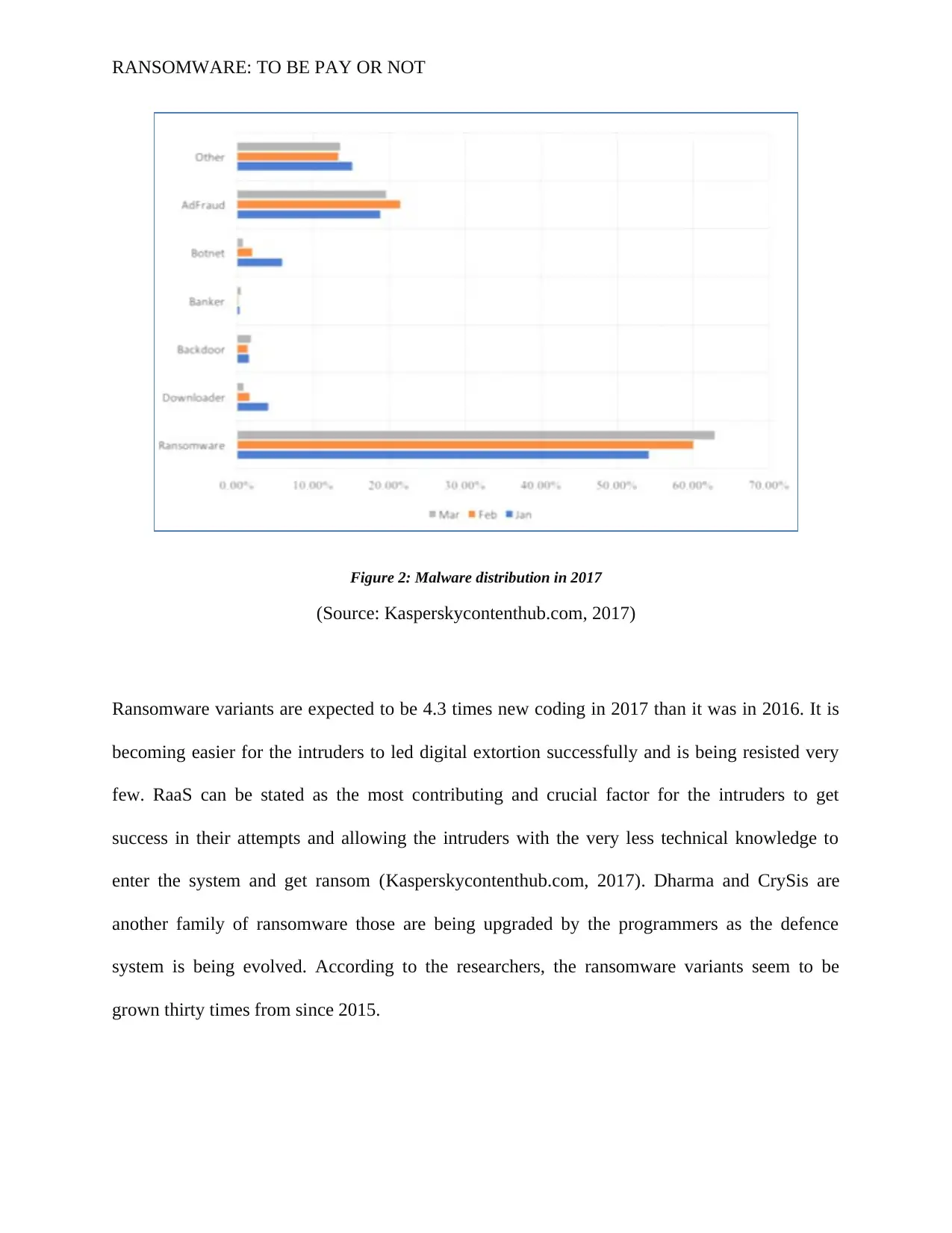
RANSOMWARE: TO BE PAY OR NOT
Figure 2: Malware distribution in 2017
(Source: Kasperskycontenthub.com, 2017)
Ransomware variants are expected to be 4.3 times new coding in 2017 than it was in 2016. It is
becoming easier for the intruders to led digital extortion successfully and is being resisted very
few. RaaS can be stated as the most contributing and crucial factor for the intruders to get
success in their attempts and allowing the intruders with the very less technical knowledge to
enter the system and get ransom (Kasperskycontenthub.com, 2017). Dharma and CrySis are
another family of ransomware those are being upgraded by the programmers as the defence
system is being evolved. According to the researchers, the ransomware variants seem to be
grown thirty times from since 2015.
Figure 2: Malware distribution in 2017
(Source: Kasperskycontenthub.com, 2017)
Ransomware variants are expected to be 4.3 times new coding in 2017 than it was in 2016. It is
becoming easier for the intruders to led digital extortion successfully and is being resisted very
few. RaaS can be stated as the most contributing and crucial factor for the intruders to get
success in their attempts and allowing the intruders with the very less technical knowledge to
enter the system and get ransom (Kasperskycontenthub.com, 2017). Dharma and CrySis are
another family of ransomware those are being upgraded by the programmers as the defence
system is being evolved. According to the researchers, the ransomware variants seem to be
grown thirty times from since 2015.

RANSOMWARE: TO BE PAY OR NOT
There is not any sector, which is untouchable of such intrusion and had to pay the ransom in a
manner to get the access to their personal data and the information (Crowe, 2017). Following is a
table that shows the quantity of sectors facing ransomware attack and had to pay the
circumstances.
Figure 3: Top 10 business facing ransomware attack.
(Source: Kasperskycontenthub.com, 2017)
One in four businesses is being hit by the ransomware attack those have more than 100
employees working in the organization. It was being reported by Barkly (2017) that among them
71% of the organization had to pay a large amount of ransom and 29% were only which, are
escaped safely.
There is not any sector, which is untouchable of such intrusion and had to pay the ransom in a
manner to get the access to their personal data and the information (Crowe, 2017). Following is a
table that shows the quantity of sectors facing ransomware attack and had to pay the
circumstances.
Figure 3: Top 10 business facing ransomware attack.
(Source: Kasperskycontenthub.com, 2017)
One in four businesses is being hit by the ransomware attack those have more than 100
employees working in the organization. It was being reported by Barkly (2017) that among them
71% of the organization had to pay a large amount of ransom and 29% were only which, are
escaped safely.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RANSOMWARE: TO BE PAY OR NOT
Figure 4: Infection rate by ransomware attack
(Source: Crowe, 2017)
3) The Scam
WannaCry Ransomware Attack
This was one of the most popular attack of this decade those was responsible for the mass
destruction. The properties of this attack were same as stated in the above report, but an
additional software was used in this attack called ‘EthernetBlue' that allows the intruder to get
access to the storage drives of the systems. This software was developed by a U.S. agency and
was stolen by an intruder and sold to the black market (Mohurle and Patil, 2017). This was a
much-planned attack in which intruder had implemented coding to execute the virus on the same
network and spread on all over the internet. Malicious injection principle was used to inject the
virus into the network that was reported to be started in a European organization. The main target
of the intruders was the multinational companies, big hospitals, institutions, federals and much
more (Chen and Brodges, 2017). Most of the organizations had to pay the ransom, however, very
few of them were able to shut down the network before it is spread to all systems in the
organization. It was reported that the virus was mostly affected the latest operating systems,
Figure 4: Infection rate by ransomware attack
(Source: Crowe, 2017)
3) The Scam
WannaCry Ransomware Attack
This was one of the most popular attack of this decade those was responsible for the mass
destruction. The properties of this attack were same as stated in the above report, but an
additional software was used in this attack called ‘EthernetBlue' that allows the intruder to get
access to the storage drives of the systems. This software was developed by a U.S. agency and
was stolen by an intruder and sold to the black market (Mohurle and Patil, 2017). This was a
much-planned attack in which intruder had implemented coding to execute the virus on the same
network and spread on all over the internet. Malicious injection principle was used to inject the
virus into the network that was reported to be started in a European organization. The main target
of the intruders was the multinational companies, big hospitals, institutions, federals and much
more (Chen and Brodges, 2017). Most of the organizations had to pay the ransom, however, very
few of them were able to shut down the network before it is spread to all systems in the
organization. It was reported that the virus was mostly affected the latest operating systems,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RANSOMWARE: TO BE PAY OR NOT
Windows XP, Windows 7, and Windows 8 and among them, the most destroyed systems were
the one with the pirated operating system. Thousands of systems were destroyed by this
malicious virus and the most affected region was the Chinese Institutions as, most of the
individuals over there were using services from the black market (Collier, 2017). The intruders
were demanding Bitcoins currencies in the exchange of the cryptographic key for the encryption
made by the virus over the files.
3.1) The profit
WannaCry incident helps in understanding that it is very important to keep the operating systems
updated with the latest version in a manner to stop any such intrusion. This is not limited to the
latest version of the operating system, but it should be original too and protected by proper anti-
virus and antimalware software. Mass destruction was made to the systems with the pirated
operating system, so using latest and original is very crucial in a manner to keep the system from
getting compromised (Batcheller et al., 2017). Most of the victims were not able to get the access
to their files even after paying the ransom money; this led to the statement that ‘it is not
important that the intruders will give the cryptographic key even after paying the ransom
amount.’ Even after getting access to those files, some of the organizations were not confident
that whether their data are compromised or not. This also states that no matter whether the access
is gained or not, data might be compromised even after getting access to the compromised files
(Martin, Kinross, and Hankin, 2017). There are ways to which we can turn the tables by
encoding encryption for the files before uploading to the database, whether it stays in the system
or transferred to the cloud. Whenever data is being compromised, it is not necessary that the files
have not been compromised. Microsoft should have launched the patches earlier and should have
estimated it earlier that such type of attack is coming. Providing update does not mean to provide
Windows XP, Windows 7, and Windows 8 and among them, the most destroyed systems were
the one with the pirated operating system. Thousands of systems were destroyed by this
malicious virus and the most affected region was the Chinese Institutions as, most of the
individuals over there were using services from the black market (Collier, 2017). The intruders
were demanding Bitcoins currencies in the exchange of the cryptographic key for the encryption
made by the virus over the files.
3.1) The profit
WannaCry incident helps in understanding that it is very important to keep the operating systems
updated with the latest version in a manner to stop any such intrusion. This is not limited to the
latest version of the operating system, but it should be original too and protected by proper anti-
virus and antimalware software. Mass destruction was made to the systems with the pirated
operating system, so using latest and original is very crucial in a manner to keep the system from
getting compromised (Batcheller et al., 2017). Most of the victims were not able to get the access
to their files even after paying the ransom money; this led to the statement that ‘it is not
important that the intruders will give the cryptographic key even after paying the ransom
amount.’ Even after getting access to those files, some of the organizations were not confident
that whether their data are compromised or not. This also states that no matter whether the access
is gained or not, data might be compromised even after getting access to the compromised files
(Martin, Kinross, and Hankin, 2017). There are ways to which we can turn the tables by
encoding encryption for the files before uploading to the database, whether it stays in the system
or transferred to the cloud. Whenever data is being compromised, it is not necessary that the files
have not been compromised. Microsoft should have launched the patches earlier and should have
estimated it earlier that such type of attack is coming. Providing update does not mean to provide

RANSOMWARE: TO BE PAY OR NOT
patches for the past threats rather it should have a measure that could prevent the estimated
threats and this estimation should be highly forward thinking.
4) Impact of Paying Ransomware
Ransomware is capable of affecting the mass impact on the financial condition of the
organization because of improper and insecure precautions taken against the malicious attacks.
Following are the impacts of ransomware attacks that could potentially affect the financial
condition of the organization:
Ransom cost paid: The amount that is being invested for gaining the access to the personal data
and information to the intruder through Bitcoins is also a certain big amount of the money
(Kshetri and Voas, 2017). On the other hand, it is being reported that the ransom amount has
been doubled from last year. This is also promoting the intruders to be more indulging in such
activities because of making money in less effort. Paying ransom never ensures the victim the
data that is about to be restored, will be restored or not or whether the data is already
compromised or not.
Downtime Cost: This is an impact the organization might face whether it pays the ransom or not
as the organization will have to face a loss that could be more affecting the business than paying
the ransom value. A ransomware targeting the organization will lead to the loss of the reputation
of the organization; it will have to face financial loss and reduced the satisfaction of the
customers.
Encourage the attackers for next attempt: Paying the ransom amount will encourage the intruders
to attempt to the different organization (Simmonds, 2017).
patches for the past threats rather it should have a measure that could prevent the estimated
threats and this estimation should be highly forward thinking.
4) Impact of Paying Ransomware
Ransomware is capable of affecting the mass impact on the financial condition of the
organization because of improper and insecure precautions taken against the malicious attacks.
Following are the impacts of ransomware attacks that could potentially affect the financial
condition of the organization:
Ransom cost paid: The amount that is being invested for gaining the access to the personal data
and information to the intruder through Bitcoins is also a certain big amount of the money
(Kshetri and Voas, 2017). On the other hand, it is being reported that the ransom amount has
been doubled from last year. This is also promoting the intruders to be more indulging in such
activities because of making money in less effort. Paying ransom never ensures the victim the
data that is about to be restored, will be restored or not or whether the data is already
compromised or not.
Downtime Cost: This is an impact the organization might face whether it pays the ransom or not
as the organization will have to face a loss that could be more affecting the business than paying
the ransom value. A ransomware targeting the organization will lead to the loss of the reputation
of the organization; it will have to face financial loss and reduced the satisfaction of the
customers.
Encourage the attackers for next attempt: Paying the ransom amount will encourage the intruders
to attempt to the different organization (Simmonds, 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




