SBM4304 IS Security and Risk Management: Blockchain Analysis Report
VerifiedAdded on 2023/01/11
|10
|2687
|82
Report
AI Summary
This report provides a comprehensive analysis of blockchain technology, focusing on its security and risk management aspects. It begins with an introduction to blockchain, explaining its underlying mechanisms, including how it works and its various applications. The report then delves into how the principles of Confidentiality, Integrity, and Availability (CIA) are achieved within blockchain systems, supporting the discussion with practical examples. It also examines the role of hashing techniques in securing blockchain and the capabilities and limitations of the technology. Furthermore, the report explores the future of blockchain technology, particularly in the banking industry, highlighting its potential impact and applications. The report concludes by summarizing the key findings and implications of blockchain technology in various contexts.

Security And Risk
Management
Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction......................................................................................................................................1
Blockchain technology................................................................................................................1
Working of blockchain................................................................................................................1
Applications of blockchain..........................................................................................................1
Illustrate ways in which CIA can be attained in blockchain.......................................................1
Describe ways in which hashing technique furnishes execution of blocks in blockchain..........1
Capabilities as well as restrictions of blockchain technology.....................................................1
Future of blockchain technology in banking industry.................................................................1
Conclusion.......................................................................................................................................1
REREFENCES................................................................................................................................2
Introduction......................................................................................................................................1
Blockchain technology................................................................................................................1
Working of blockchain................................................................................................................1
Applications of blockchain..........................................................................................................1
Illustrate ways in which CIA can be attained in blockchain.......................................................1
Describe ways in which hashing technique furnishes execution of blocks in blockchain..........1
Capabilities as well as restrictions of blockchain technology.....................................................1
Future of blockchain technology in banking industry.................................................................1
Conclusion.......................................................................................................................................1
REREFENCES................................................................................................................................2

Introduction
Information security is defined as set of practices that are projected for keeping
information protected from any kind of unauthenticated access or modification is defined as
information security (Bai and Sarkis, 2020). It comprises of processes and methods that are
formulated as well as implemented for protection of confidential data. The decentralised and
distributed ledger technology that is responsible to record attribution of digital entities. This
report provides an overview of distinct perspectives associated with blockchain technology and
many other associated components related with this like working, hashing techniques,
capabilities,, restrictions and future analysis.
Blockchain technology
The structure that is accountable to store transactional records of various databases of
individuals within a network that are connected through peer to peer nodes is defined as
blockchain. This implies publicly accessible as well as transparent ledger that allow transferring
ownership securely to units of values by utilisation of public key encryption. Usually, this
implies distributed database which is responsible to record digital transactions as well as events
that have been implemented along with shared between distinct parties which are involved in
these perspectives (Chong and et. al, 2020). In addition to this, by taking into account security
concerns each transaction needs to be verified via distinct parties associated with system. This
denotes promising and revolutionary technology that assists in minimisation of threats and brings
in transparency in operations.
Working of blockchain
Blockchain refers to system of network that involves various nodes or computers which
acts like a distributed network. Along with this, each node encompasses of distinct copies of
database as well as ledger (Di Vaio and Varriale, 2020). The transaction history is liable for
accessing needs as well as updates it each time node is being update new transactions that are
present within chain. The working of blockchain has been illustrated below:
It can be considered that there are two nodes in blockchain network node A and B that
are liable for carrying out new transactions among them. This operation occurs when all the
nodes verify legitimate transactions, each node will have request for processing transactions
which takes place in between A and B.
1
Information security is defined as set of practices that are projected for keeping
information protected from any kind of unauthenticated access or modification is defined as
information security (Bai and Sarkis, 2020). It comprises of processes and methods that are
formulated as well as implemented for protection of confidential data. The decentralised and
distributed ledger technology that is responsible to record attribution of digital entities. This
report provides an overview of distinct perspectives associated with blockchain technology and
many other associated components related with this like working, hashing techniques,
capabilities,, restrictions and future analysis.
Blockchain technology
The structure that is accountable to store transactional records of various databases of
individuals within a network that are connected through peer to peer nodes is defined as
blockchain. This implies publicly accessible as well as transparent ledger that allow transferring
ownership securely to units of values by utilisation of public key encryption. Usually, this
implies distributed database which is responsible to record digital transactions as well as events
that have been implemented along with shared between distinct parties which are involved in
these perspectives (Chong and et. al, 2020). In addition to this, by taking into account security
concerns each transaction needs to be verified via distinct parties associated with system. This
denotes promising and revolutionary technology that assists in minimisation of threats and brings
in transparency in operations.
Working of blockchain
Blockchain refers to system of network that involves various nodes or computers which
acts like a distributed network. Along with this, each node encompasses of distinct copies of
database as well as ledger (Di Vaio and Varriale, 2020). The transaction history is liable for
accessing needs as well as updates it each time node is being update new transactions that are
present within chain. The working of blockchain has been illustrated below:
It can be considered that there are two nodes in blockchain network node A and B that
are liable for carrying out new transactions among them. This operation occurs when all the
nodes verify legitimate transactions, each node will have request for processing transactions
which takes place in between A and B.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
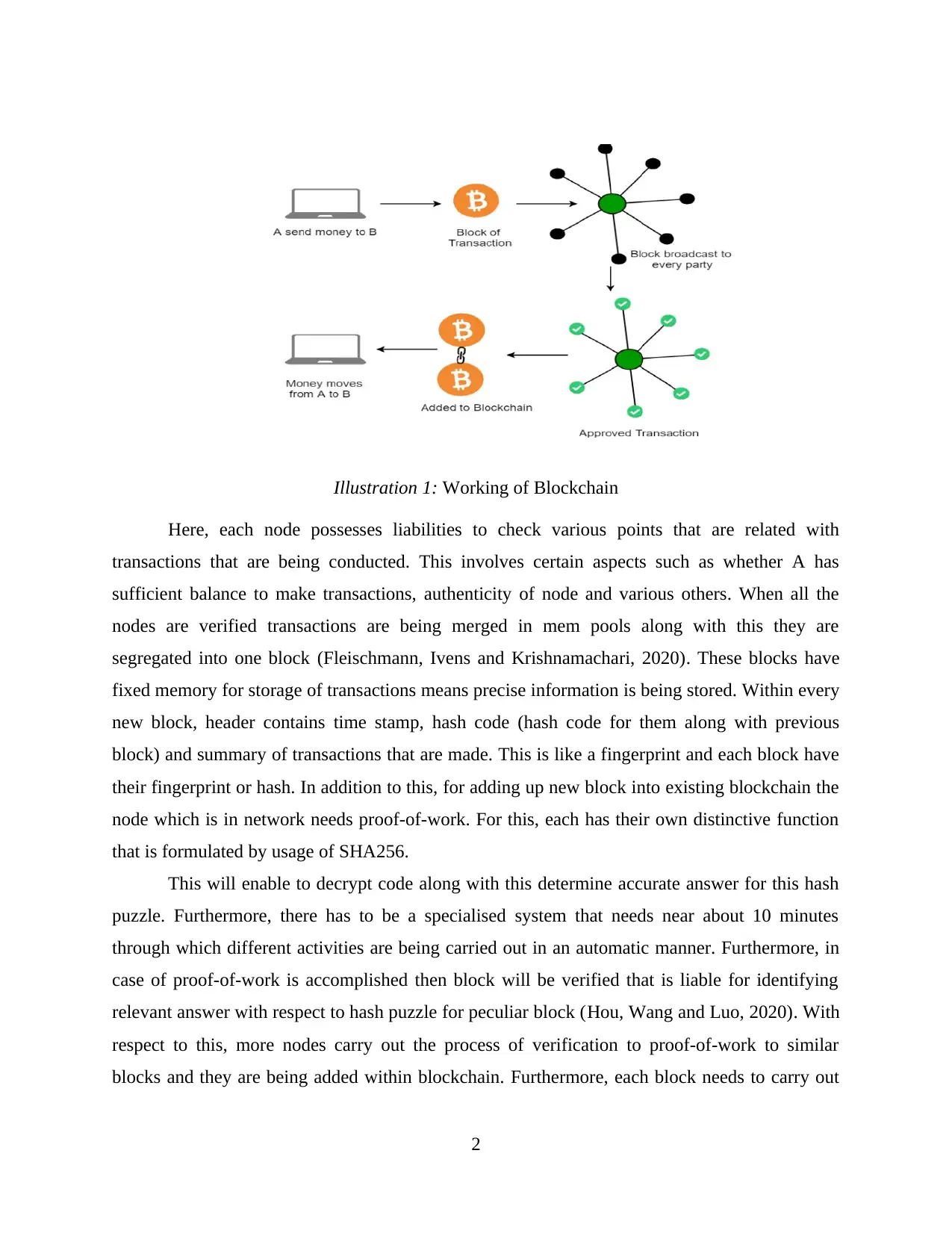
Illustration 1: Working of Blockchain
Here, each node possesses liabilities to check various points that are related with
transactions that are being conducted. This involves certain aspects such as whether A has
sufficient balance to make transactions, authenticity of node and various others. When all the
nodes are verified transactions are being merged in mem pools along with this they are
segregated into one block (Fleischmann, Ivens and Krishnamachari, 2020). These blocks have
fixed memory for storage of transactions means precise information is being stored. Within every
new block, header contains time stamp, hash code (hash code for them along with previous
block) and summary of transactions that are made. This is like a fingerprint and each block have
their fingerprint or hash. In addition to this, for adding up new block into existing blockchain the
node which is in network needs proof-of-work. For this, each has their own distinctive function
that is formulated by usage of SHA256.
This will enable to decrypt code along with this determine accurate answer for this hash
puzzle. Furthermore, there has to be a specialised system that needs near about 10 minutes
through which different activities are being carried out in an automatic manner. Furthermore, in
case of proof-of-work is accomplished then block will be verified that is liable for identifying
relevant answer with respect to hash puzzle for peculiar block (Hou, Wang and Luo, 2020). With
respect to this, more nodes carry out the process of verification to proof-of-work to similar
blocks and they are being added within blockchain. Furthermore, each block needs to carry out
2
Here, each node possesses liabilities to check various points that are related with
transactions that are being conducted. This involves certain aspects such as whether A has
sufficient balance to make transactions, authenticity of node and various others. When all the
nodes are verified transactions are being merged in mem pools along with this they are
segregated into one block (Fleischmann, Ivens and Krishnamachari, 2020). These blocks have
fixed memory for storage of transactions means precise information is being stored. Within every
new block, header contains time stamp, hash code (hash code for them along with previous
block) and summary of transactions that are made. This is like a fingerprint and each block have
their fingerprint or hash. In addition to this, for adding up new block into existing blockchain the
node which is in network needs proof-of-work. For this, each has their own distinctive function
that is formulated by usage of SHA256.
This will enable to decrypt code along with this determine accurate answer for this hash
puzzle. Furthermore, there has to be a specialised system that needs near about 10 minutes
through which different activities are being carried out in an automatic manner. Furthermore, in
case of proof-of-work is accomplished then block will be verified that is liable for identifying
relevant answer with respect to hash puzzle for peculiar block (Hou, Wang and Luo, 2020). With
respect to this, more nodes carry out the process of verification to proof-of-work to similar
blocks and they are being added within blockchain. Furthermore, each block needs to carry out
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

transaction for records and block is being added that aids within implementation of transaction
which exist between A as well as B.
Applications associated with blockchain
Blockchain acts as substitute for transaction method, centralised methods and transaction
methods that are liable for altering ways through which transaction will be conducted. In
reference to this, applications have been specified below:
Data Sharing: Cryptocurrency IOTA furnishes beta version for data in marketplace that
demonstrate blockchain will be used in marketplace to sell or share data that is not used.
This occurs as a reason because maximum of data of organisation is not being used as
only processed information is utilised (Nagasubramanian and et. al, 2020). Here,
blockchain will be like an intermediary along with storage and moving data to enhance
host of sectors.
Copyright & royalty protection: Access for internet is increasing continuously, so there
has to be adequate laws with respect to ownership along with copyright in context to
music or journals and other aspects. By making use of blockchain, copyright law will
beef in context of digital content download by making sure that artist or content writer
have fair share. It denotes that real time as well as transparent royalty distribution of
information for creators.
Payment processing & money transfers: The logical use of blockchain demonstrates
means for accelerating transfer of funds between distinct individuals. Within banks, the
validation process takes near about 24 hours and weeks to carry out transactions but by
making use of blockchain same transaction will take few seconds (Tozanlı, Kongar and
Gupta, 2020).
Weapon tracking: Through implementing blockchain transparent along with unchanging
registry network will be formulated that assist law enforcement bodies as well as federal
government to track ownership by maintaining record of each weapon that is privately
sold.
Exemplify methods by which CIA can be accomplished within blockchain
Bitcoin is a protocol that is being utilised in Blockchain and have acquired huge attention
in few years. With respect to security aspects, there are three important perspectives which have
to be ensured while delivering any kind of services to users (Valeri, 2020). This involves
3
which exist between A as well as B.
Applications associated with blockchain
Blockchain acts as substitute for transaction method, centralised methods and transaction
methods that are liable for altering ways through which transaction will be conducted. In
reference to this, applications have been specified below:
Data Sharing: Cryptocurrency IOTA furnishes beta version for data in marketplace that
demonstrate blockchain will be used in marketplace to sell or share data that is not used.
This occurs as a reason because maximum of data of organisation is not being used as
only processed information is utilised (Nagasubramanian and et. al, 2020). Here,
blockchain will be like an intermediary along with storage and moving data to enhance
host of sectors.
Copyright & royalty protection: Access for internet is increasing continuously, so there
has to be adequate laws with respect to ownership along with copyright in context to
music or journals and other aspects. By making use of blockchain, copyright law will
beef in context of digital content download by making sure that artist or content writer
have fair share. It denotes that real time as well as transparent royalty distribution of
information for creators.
Payment processing & money transfers: The logical use of blockchain demonstrates
means for accelerating transfer of funds between distinct individuals. Within banks, the
validation process takes near about 24 hours and weeks to carry out transactions but by
making use of blockchain same transaction will take few seconds (Tozanlı, Kongar and
Gupta, 2020).
Weapon tracking: Through implementing blockchain transparent along with unchanging
registry network will be formulated that assist law enforcement bodies as well as federal
government to track ownership by maintaining record of each weapon that is privately
sold.
Exemplify methods by which CIA can be accomplished within blockchain
Bitcoin is a protocol that is being utilised in Blockchain and have acquired huge attention
in few years. With respect to security aspects, there are three important perspectives which have
to be ensured while delivering any kind of services to users (Valeri, 2020). This involves
3

integrity, availability and confidentiality. These are essential aspects which have to be
considered, in reference to integrity there are uncertainty issues like alteration within information
when it is being transmitted among users via usage of internet. There are probabilities that third
person can have access to network and can modify message that is being transmitted or to have
an access to confidential information as per their requirements. With respect to availability, this
comprises of abrupt shutdown, server crash and many other aspects (Bai and Sarkis, 2020). In
context of confidentiality, unauthorised access is taken into consideration, where vulnerabilities,
exploits or any kind of loopholes are being utilised for having access to the system. Blockchain
assists in enhancing all these three perspectives, CIA to ensure that transactions carried out are
secured.
Blockchain comprises of distributed database that is maintained along with this shared
through distinct nodes that aids to attain CIA. Transactions that are being made with reference to
blockchain are being grouped and stored within chain of blocks that are connected with one other
in sequence as per hash contained with them. Each block involves their hash and of previous
block that is liable for furnishing details related with transactions that are being carried out
(Chong and et. al, 2020). Each node is accountable for verifying these groups so that CIA can be
attained.
Illustrate manner in which hashing technique executes blocks in blockchain
The process that is related with having adequate input of distinct lengths but is liabel for
rendering output of fixed length is defined as hashing. For an examle different transactiosn are
bieng made by users with reference to cryptocurrency hwich implies that input given is different
but outcome attained is of definite outcome. Blockchain can be referred to as linked taht
comprises of address to next node or a hash pointer that points toward next block. In context of
blockchain, hash function not only contains hash function for previous block but also containt
unique hash for itself which acts as a identifier to particular block. This will also lead to ensure
sequence for next hash when transaction is being carried out (Di Vaio and Varriale, 2020). For
an example, by taking into consideration last transaction which have been made, further
alterations or transactions can eb conducted by making use of previous one. For this reason
address of previous block is contained for verifying that transactions arebieng carried out
precisely. In this hash function executes in blockchain technology.
4
considered, in reference to integrity there are uncertainty issues like alteration within information
when it is being transmitted among users via usage of internet. There are probabilities that third
person can have access to network and can modify message that is being transmitted or to have
an access to confidential information as per their requirements. With respect to availability, this
comprises of abrupt shutdown, server crash and many other aspects (Bai and Sarkis, 2020). In
context of confidentiality, unauthorised access is taken into consideration, where vulnerabilities,
exploits or any kind of loopholes are being utilised for having access to the system. Blockchain
assists in enhancing all these three perspectives, CIA to ensure that transactions carried out are
secured.
Blockchain comprises of distributed database that is maintained along with this shared
through distinct nodes that aids to attain CIA. Transactions that are being made with reference to
blockchain are being grouped and stored within chain of blocks that are connected with one other
in sequence as per hash contained with them. Each block involves their hash and of previous
block that is liable for furnishing details related with transactions that are being carried out
(Chong and et. al, 2020). Each node is accountable for verifying these groups so that CIA can be
attained.
Illustrate manner in which hashing technique executes blocks in blockchain
The process that is related with having adequate input of distinct lengths but is liabel for
rendering output of fixed length is defined as hashing. For an examle different transactiosn are
bieng made by users with reference to cryptocurrency hwich implies that input given is different
but outcome attained is of definite outcome. Blockchain can be referred to as linked taht
comprises of address to next node or a hash pointer that points toward next block. In context of
blockchain, hash function not only contains hash function for previous block but also containt
unique hash for itself which acts as a identifier to particular block. This will also lead to ensure
sequence for next hash when transaction is being carried out (Di Vaio and Varriale, 2020). For
an example, by taking into consideration last transaction which have been made, further
alterations or transactions can eb conducted by making use of previous one. For this reason
address of previous block is contained for verifying that transactions arebieng carried out
precisely. In this hash function executes in blockchain technology.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
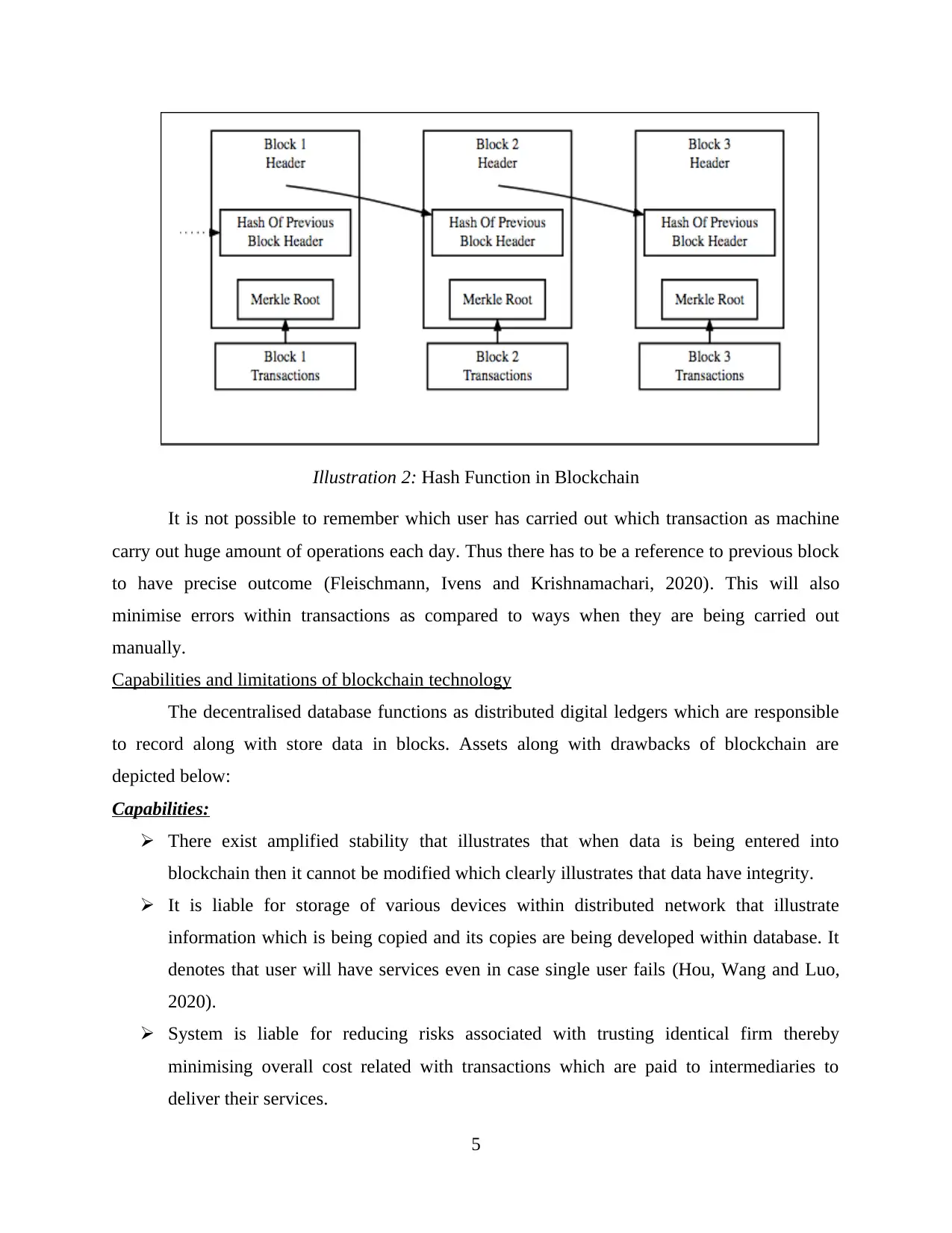
Illustration 2: Hash Function in Blockchain
It is not possible to remember which user has carried out which transaction as machine
carry out huge amount of operations each day. Thus there has to be a reference to previous block
to have precise outcome (Fleischmann, Ivens and Krishnamachari, 2020). This will also
minimise errors within transactions as compared to ways when they are being carried out
manually.
Capabilities and limitations of blockchain technology
The decentralised database functions as distributed digital ledgers which are responsible
to record along with store data in blocks. Assets along with drawbacks of blockchain are
depicted below:
Capabilities:
There exist amplified stability that illustrates that when data is being entered into
blockchain then it cannot be modified which clearly illustrates that data have integrity.
It is liable for storage of various devices within distributed network that illustrate
information which is being copied and its copies are being developed within database. It
denotes that user will have services even in case single user fails (Hou, Wang and Luo,
2020).
System is liable for reducing risks associated with trusting identical firm thereby
minimising overall cost related with transactions which are paid to intermediaries to
deliver their services.
5
It is not possible to remember which user has carried out which transaction as machine
carry out huge amount of operations each day. Thus there has to be a reference to previous block
to have precise outcome (Fleischmann, Ivens and Krishnamachari, 2020). This will also
minimise errors within transactions as compared to ways when they are being carried out
manually.
Capabilities and limitations of blockchain technology
The decentralised database functions as distributed digital ledgers which are responsible
to record along with store data in blocks. Assets along with drawbacks of blockchain are
depicted below:
Capabilities:
There exist amplified stability that illustrates that when data is being entered into
blockchain then it cannot be modified which clearly illustrates that data have integrity.
It is liable for storage of various devices within distributed network that illustrate
information which is being copied and its copies are being developed within database. It
denotes that user will have services even in case single user fails (Hou, Wang and Luo,
2020).
System is liable for reducing risks associated with trusting identical firm thereby
minimising overall cost related with transactions which are paid to intermediaries to
deliver their services.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Limitations
For giving ownership asymmetric cryptography is used but in case user lose their private
key then there is high probability that they may lose entire information or amount
whatever is being stored within this.
Hard fork can be utilised for altering data that is being stored within code of blockchain
along with this one chain is being abandoned then other is considered (Nagasubramanian
and et. al, 2020).
If adequate space is not available then there is high probability that ledgers will not be
downloaded or stored within device of individuals.
Future of blockchain technology
Each sector can make use of blockchain as per their requirements but banking sector has
huge applications with respect to this, some applications are specified below:
Beyond Payments: This can be used for setting up smart contracts which have capability
to automate execution according to formulated predetermined criteria. Because of
derivative nature, parties involved within transaction need to track conditions which
prevails within the market along with barriers. This will lead to creation of affirmative
impact on processes as they are automated by making use of smart contracts like cash
flows are being provided according to situations that prevails within the market. This will
provide transparency within operations carried out by banking industry.
Know your customer: It implies regulatory process which is being related with
authentication profile of users as this leads to creation if huge influence on ways in which
industry render their services. Through blockchain data can be shared and encrypted for
KYC obligations. This cannot be attained without sharing confidential information of ser
but there is probability that while sending information network might be attacked which
denotes that information will be compromised (Tozanlı, Kongar and Gupta, 2020). In this
context, if user have KYC process done with other bank then they can exchange the
information as there system are being secured as compared to users. This clearly
illustrates that by making sue of blockchain user need to worry about security of their
issue and verification will also not be an issue.
6
For giving ownership asymmetric cryptography is used but in case user lose their private
key then there is high probability that they may lose entire information or amount
whatever is being stored within this.
Hard fork can be utilised for altering data that is being stored within code of blockchain
along with this one chain is being abandoned then other is considered (Nagasubramanian
and et. al, 2020).
If adequate space is not available then there is high probability that ledgers will not be
downloaded or stored within device of individuals.
Future of blockchain technology
Each sector can make use of blockchain as per their requirements but banking sector has
huge applications with respect to this, some applications are specified below:
Beyond Payments: This can be used for setting up smart contracts which have capability
to automate execution according to formulated predetermined criteria. Because of
derivative nature, parties involved within transaction need to track conditions which
prevails within the market along with barriers. This will lead to creation of affirmative
impact on processes as they are automated by making use of smart contracts like cash
flows are being provided according to situations that prevails within the market. This will
provide transparency within operations carried out by banking industry.
Know your customer: It implies regulatory process which is being related with
authentication profile of users as this leads to creation if huge influence on ways in which
industry render their services. Through blockchain data can be shared and encrypted for
KYC obligations. This cannot be attained without sharing confidential information of ser
but there is probability that while sending information network might be attacked which
denotes that information will be compromised (Tozanlı, Kongar and Gupta, 2020). In this
context, if user have KYC process done with other bank then they can exchange the
information as there system are being secured as compared to users. This clearly
illustrates that by making sue of blockchain user need to worry about security of their
issue and verification will also not be an issue.
6

They illustrates the major applications within banking sector as it is necessary to verify
user before providing them with services and to have transparency within operations carried out
by them. But there are many other assets which can be utilised by organisations (Valeri, 2020).
Conclusion
From above it can be concluded that, security of operations that are being carried out is
essential as it leads to creation of trust among user with respect to services that are being carried
out by firms. Blockchain refers to aggregation of blocks in a sequence in such a way that they
formulate chain. Hash function is utilised as a pointer to previous block to have information
about that and accordingly carry out transactions. It provides wide range of assets through which
firms can ensure that they are able to deliver enhanced services. Furthermore, blockchain have
their application within different segment of industry by which all the transactions either it is
form of money or information can be carried out with high security as different nodes are
accountable for verification of user.
7
user before providing them with services and to have transparency within operations carried out
by them. But there are many other assets which can be utilised by organisations (Valeri, 2020).
Conclusion
From above it can be concluded that, security of operations that are being carried out is
essential as it leads to creation of trust among user with respect to services that are being carried
out by firms. Blockchain refers to aggregation of blocks in a sequence in such a way that they
formulate chain. Hash function is utilised as a pointer to previous block to have information
about that and accordingly carry out transactions. It provides wide range of assets through which
firms can ensure that they are able to deliver enhanced services. Furthermore, blockchain have
their application within different segment of industry by which all the transactions either it is
form of money or information can be carried out with high security as different nodes are
accountable for verification of user.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REREFENCES
Books and Journals
Bai, C. and Sarkis, J., 2020. A supply chain transparency and sustainability technology appraisal
model for blockchain technology. International Journal of Production Research, pp.1-21.
Chong, M.and et. al, 2020. Blockchain Technology Applied to the Cocoa Export Supply Chain:
A Latin America Case. In Handbook of Research on Emerging Technologies for Effective
Project Management (pp. 323-339). IGI Global.
Di Vaio, A. and Varriale, L., 2020. Blockchain technology in supply chain management for
sustainable performance: Evidence from the airport industry. International Journal of
Information Management, 52, p.102014.
Fleischmann, M., Ivens, B.S. and Krishnamachari, B., 2020, January. Blockchain Technology as
a Means for Brand Trust Repair–Empirical Evidence from a Digital Transgression.
In Proceedings of the 53rd Hawaii International Conference on System Sciences.
Hou, J., Wang, C. and Luo, S., 2020. How to improve the competiveness of distributed energy
resources in China with blockchain technology. Technological Forecasting and Social
Change, 151, p.119744.
Nagasubramanian, G. and et. al, 2020. Securing e-health records using keyless signature
infrastructure Blockchain technology in the cloud. Neural Computing and
Applications, 32(3), pp.639-647.
Tozanlı, Ö., Kongar, E. and Gupta, S.M., 2020. Trade-in-to-upgrade as a marketing strategy in
disassembly-to-order systems at the edge of blockchain technology. International Journal
of Production Research, pp.1-18.
Valeri, M., 2020. Blockchain Technology: Adoption Perspectives in Tourism.
In Entrepreneurship and Organizational Change (pp. 27-35). Springer, Cham.
8
Books and Journals
Bai, C. and Sarkis, J., 2020. A supply chain transparency and sustainability technology appraisal
model for blockchain technology. International Journal of Production Research, pp.1-21.
Chong, M.and et. al, 2020. Blockchain Technology Applied to the Cocoa Export Supply Chain:
A Latin America Case. In Handbook of Research on Emerging Technologies for Effective
Project Management (pp. 323-339). IGI Global.
Di Vaio, A. and Varriale, L., 2020. Blockchain technology in supply chain management for
sustainable performance: Evidence from the airport industry. International Journal of
Information Management, 52, p.102014.
Fleischmann, M., Ivens, B.S. and Krishnamachari, B., 2020, January. Blockchain Technology as
a Means for Brand Trust Repair–Empirical Evidence from a Digital Transgression.
In Proceedings of the 53rd Hawaii International Conference on System Sciences.
Hou, J., Wang, C. and Luo, S., 2020. How to improve the competiveness of distributed energy
resources in China with blockchain technology. Technological Forecasting and Social
Change, 151, p.119744.
Nagasubramanian, G. and et. al, 2020. Securing e-health records using keyless signature
infrastructure Blockchain technology in the cloud. Neural Computing and
Applications, 32(3), pp.639-647.
Tozanlı, Ö., Kongar, E. and Gupta, S.M., 2020. Trade-in-to-upgrade as a marketing strategy in
disassembly-to-order systems at the edge of blockchain technology. International Journal
of Production Research, pp.1-18.
Valeri, M., 2020. Blockchain Technology: Adoption Perspectives in Tourism.
In Entrepreneurship and Organizational Change (pp. 27-35). Springer, Cham.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




