Research Methods and Design: Misuse of Internet at Workplace
VerifiedAdded on 2022/11/25
|13
|3764
|465
AI Summary
This research study aims to assess the impact of internet misuse on the performance/productivity of employees and evaluate any significant difference in cyberslacking activities based on various factors.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: RESEARCH METHODS AND DESIGN 1
Research Methods and Design
Name of Student
Institution affiliation
Research Methods and Design
Name of Student
Institution affiliation
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESEARCH METHODS AND DESIGN 2
Research Methods and Design: Misuse of Internet at Workplace
Purpose of the Research
Since the integration of new strategic work process and the electronic environment in the
workplace, there has been a tremendous rise in implementation of information systems, computer
technologies, and internet technology as well as misuse of those technologies (Alharthi, 2018;
Farivar, 2016). The misuse of the internet at the workplace for other activities other than, also
known as cyberslacking or cyberloafing or cyberbludging, has been on the rising daily has been
associations with varying implications across the corporate world and other entities (Hernández
et al., 2016). The problem of misuse of internet at workplace involves using workplace’s internet
for work unrelated activities such accessing social networking sites for personal use, spending
hours to shop online, utilizing work internet to manage personal data, and using work internet to
visit pornographic websites, among other activities (James, 2010; Kamil, 2014). Managers,
employers, observers, and practitioners have noted a worrying trend of diminishing productivity
in the workplace in both public and private sectors attributed to cyberslacking (Jandaghi et al.,
2015). Therefore, the proliferation of internet misuse in the workplace, in both public and
private institutions, warrants a research study.
Today, employers have become gravely concerned about inappropriate internet usage.
According to America Management Association (AMA), 66% of employers monitor internet
connections, while 65% use software to block connections to inappropriate websites (Köleoğlu,
2017). Further, the study reveals that 30% of employers who have fired employees because of
inappropriate internet usage have cited their main reasons as viewing, downloading, or uploading
inappropriate content, breach of confidentiality rules, excessive personal use, and violation of
company policy. Moreover, another study report that on average, workers spend approximately
21 hours each month using the internet for personal reasons. The rising internet misuse has been
associated with major effects across various institutions.
One major cost of cyberslacking to institutions is lower productivity (Kuschnaroff &
Bayma, 2014). For instance, when workers utilize workplace internet and PCs for personal use,
evidently, the productivity of the organization will decrease. However, it is not satisfactory to
make a conclusion on the relationship between an organization’s productivity and cyberslacking
without providing sufficient statistical evidence. The main reason for conducting this research
study is to assess the impact of internet misuse on the performance/productivity of employees.
Research Methods and Design: Misuse of Internet at Workplace
Purpose of the Research
Since the integration of new strategic work process and the electronic environment in the
workplace, there has been a tremendous rise in implementation of information systems, computer
technologies, and internet technology as well as misuse of those technologies (Alharthi, 2018;
Farivar, 2016). The misuse of the internet at the workplace for other activities other than, also
known as cyberslacking or cyberloafing or cyberbludging, has been on the rising daily has been
associations with varying implications across the corporate world and other entities (Hernández
et al., 2016). The problem of misuse of internet at workplace involves using workplace’s internet
for work unrelated activities such accessing social networking sites for personal use, spending
hours to shop online, utilizing work internet to manage personal data, and using work internet to
visit pornographic websites, among other activities (James, 2010; Kamil, 2014). Managers,
employers, observers, and practitioners have noted a worrying trend of diminishing productivity
in the workplace in both public and private sectors attributed to cyberslacking (Jandaghi et al.,
2015). Therefore, the proliferation of internet misuse in the workplace, in both public and
private institutions, warrants a research study.
Today, employers have become gravely concerned about inappropriate internet usage.
According to America Management Association (AMA), 66% of employers monitor internet
connections, while 65% use software to block connections to inappropriate websites (Köleoğlu,
2017). Further, the study reveals that 30% of employers who have fired employees because of
inappropriate internet usage have cited their main reasons as viewing, downloading, or uploading
inappropriate content, breach of confidentiality rules, excessive personal use, and violation of
company policy. Moreover, another study report that on average, workers spend approximately
21 hours each month using the internet for personal reasons. The rising internet misuse has been
associated with major effects across various institutions.
One major cost of cyberslacking to institutions is lower productivity (Kuschnaroff &
Bayma, 2014). For instance, when workers utilize workplace internet and PCs for personal use,
evidently, the productivity of the organization will decrease. However, it is not satisfactory to
make a conclusion on the relationship between an organization’s productivity and cyberslacking
without providing sufficient statistical evidence. The main reason for conducting this research
study is to assess the impact of internet misuse on the performance/productivity of employees.

RESEARCH METHODS AND DESIGN 3
The research will assess the extent of worker’s report on their own internet misuse activities as
well as their co-workers, and the impact of these activities on the productivity or perceived
ethical severity of these activities. Another reason to perform this study is to assess any
significant difference in cyberslacking activities based on years of working at the institution, job
level, age, gender, and level of education.
It is crucial that an institution should be able to identify internet misuse problem and the
financial consequences of these activities. Internet misuse at the workplace is linked to three
main problems including the exhaustive use of company resources, productivity and financial
loss, and legal liability (ÖRÜCÜ & YILDIZ, 2014). Even though cyberslacking presents an
obvious challenge to organizations, the extent of its proliferation has not been fully studied.
Meanwhile, internet misuse is becoming a huge problem in the corporate world that many firms
are starting to crack down. Therefore, it is recommended that companies should support studies
of workers internet misuse of resources to minimize loss of productivity and legal liability (Ozler
& POLAT, 2012).
Variables
The main goal of this study is to examine the amount of time spent and frequency (self-
reported extent) to which employees and their co-workers engage in internet misuse at
workplace, to determine the relationship between internet misuse and diminishing productivity,
and to evaluate any statistical difference of these activities based on level of education, age, year
of experience, and gender. Therefore, there are two key variables in this study: the frequency of
cyberslacking activities and the perceived ethical severity of these cyberslacking activities. The
dependent variable is the perceived ethical severity of the cyberslacking activities because we are
investigating how it is influenced by the frequency of the cyberslacking activities. The frequency
of the cyberslacking activities is the dependent variable. The frequency of the internet misuse
variable is measured based on 20 items using a 7-point scale which ranges from 1-never to 77-
several times a day. The perceived ethical severity variable is also measured based on 20 items
using a 7-point scale which ranges from 1-Highly Unethical to 7-Highly Ethical. The control
variables are age, gender, education, and work experience.
Research Model
This research study will apply a regression model or XY model to ascertain the perceived
ethical severity of internet misuse activities. X is the independent/ explanatory variable which is
The research will assess the extent of worker’s report on their own internet misuse activities as
well as their co-workers, and the impact of these activities on the productivity or perceived
ethical severity of these activities. Another reason to perform this study is to assess any
significant difference in cyberslacking activities based on years of working at the institution, job
level, age, gender, and level of education.
It is crucial that an institution should be able to identify internet misuse problem and the
financial consequences of these activities. Internet misuse at the workplace is linked to three
main problems including the exhaustive use of company resources, productivity and financial
loss, and legal liability (ÖRÜCÜ & YILDIZ, 2014). Even though cyberslacking presents an
obvious challenge to organizations, the extent of its proliferation has not been fully studied.
Meanwhile, internet misuse is becoming a huge problem in the corporate world that many firms
are starting to crack down. Therefore, it is recommended that companies should support studies
of workers internet misuse of resources to minimize loss of productivity and legal liability (Ozler
& POLAT, 2012).
Variables
The main goal of this study is to examine the amount of time spent and frequency (self-
reported extent) to which employees and their co-workers engage in internet misuse at
workplace, to determine the relationship between internet misuse and diminishing productivity,
and to evaluate any statistical difference of these activities based on level of education, age, year
of experience, and gender. Therefore, there are two key variables in this study: the frequency of
cyberslacking activities and the perceived ethical severity of these cyberslacking activities. The
dependent variable is the perceived ethical severity of the cyberslacking activities because we are
investigating how it is influenced by the frequency of the cyberslacking activities. The frequency
of the cyberslacking activities is the dependent variable. The frequency of the internet misuse
variable is measured based on 20 items using a 7-point scale which ranges from 1-never to 77-
several times a day. The perceived ethical severity variable is also measured based on 20 items
using a 7-point scale which ranges from 1-Highly Unethical to 7-Highly Ethical. The control
variables are age, gender, education, and work experience.
Research Model
This research study will apply a regression model or XY model to ascertain the perceived
ethical severity of internet misuse activities. X is the independent/ explanatory variable which is

RESEARCH METHODS AND DESIGN 4
the frequency of engagement in internet misuse activities. Y is the dependent variable which is
been influenced by the independent variables, in this case, Y is the perceived ethical severity of
internet misuse activities (Christensen et al., 2011). The model can be represented in the form of
an equation as follows.
Y =mX +C
Where m is the coefficient of regression and C is a constant (Gliner, Morgan, & Leech,
(2011). A positive value of m means a high frequency of engagement in cyberslacking activities
is associated with an increase in ethical severity, while a negative value implies a diminishing
ethical severity. The model can be graphed as shown below.
0 2 4 6 8 10 12
0
2
4
6
8
10
12
Ethical Severity/Production(Y)
Ethical Severity/Production(Y)
Frequency of Internet Misuse Activities (X)
Ethical Severity/
Performance
Conceptual Model on the Impact of Frequency and Time Spent on Internet Misuse on Ethical
Severity
the frequency of engagement in internet misuse activities. Y is the dependent variable which is
been influenced by the independent variables, in this case, Y is the perceived ethical severity of
internet misuse activities (Christensen et al., 2011). The model can be represented in the form of
an equation as follows.
Y =mX +C
Where m is the coefficient of regression and C is a constant (Gliner, Morgan, & Leech,
(2011). A positive value of m means a high frequency of engagement in cyberslacking activities
is associated with an increase in ethical severity, while a negative value implies a diminishing
ethical severity. The model can be graphed as shown below.
0 2 4 6 8 10 12
0
2
4
6
8
10
12
Ethical Severity/Production(Y)
Ethical Severity/Production(Y)
Frequency of Internet Misuse Activities (X)
Ethical Severity/
Performance
Conceptual Model on the Impact of Frequency and Time Spent on Internet Misuse on Ethical
Severity
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESEARCH METHODS AND DESIGN 5
To obtain the regression equation, the SPSS data analysis tool is used to conduct multiple linear
regression analysis and ordinal logistic regression parameter estimates.
Measures of the Variables
A quantitative survey instrument is used in this research study for data collection. The
survey instrument contains six sections namely: (a) frequency of cyberslacking activity (self); (b)
frequency of cyberslacking activity (co-worker); (c) time spent on cyberslacking activity (self);
(d) time spend on cyberslacking activity (co-worker); (e) ethical severity; and (f) demographic
information. The survey utilizes a seven-point Likert scale to assess measured variables by
facilitating the participants identifying the activity and the perceived ethical severity. Time
spent, frequency and ethical severity are measured based on the twenty cyberslacking activities.
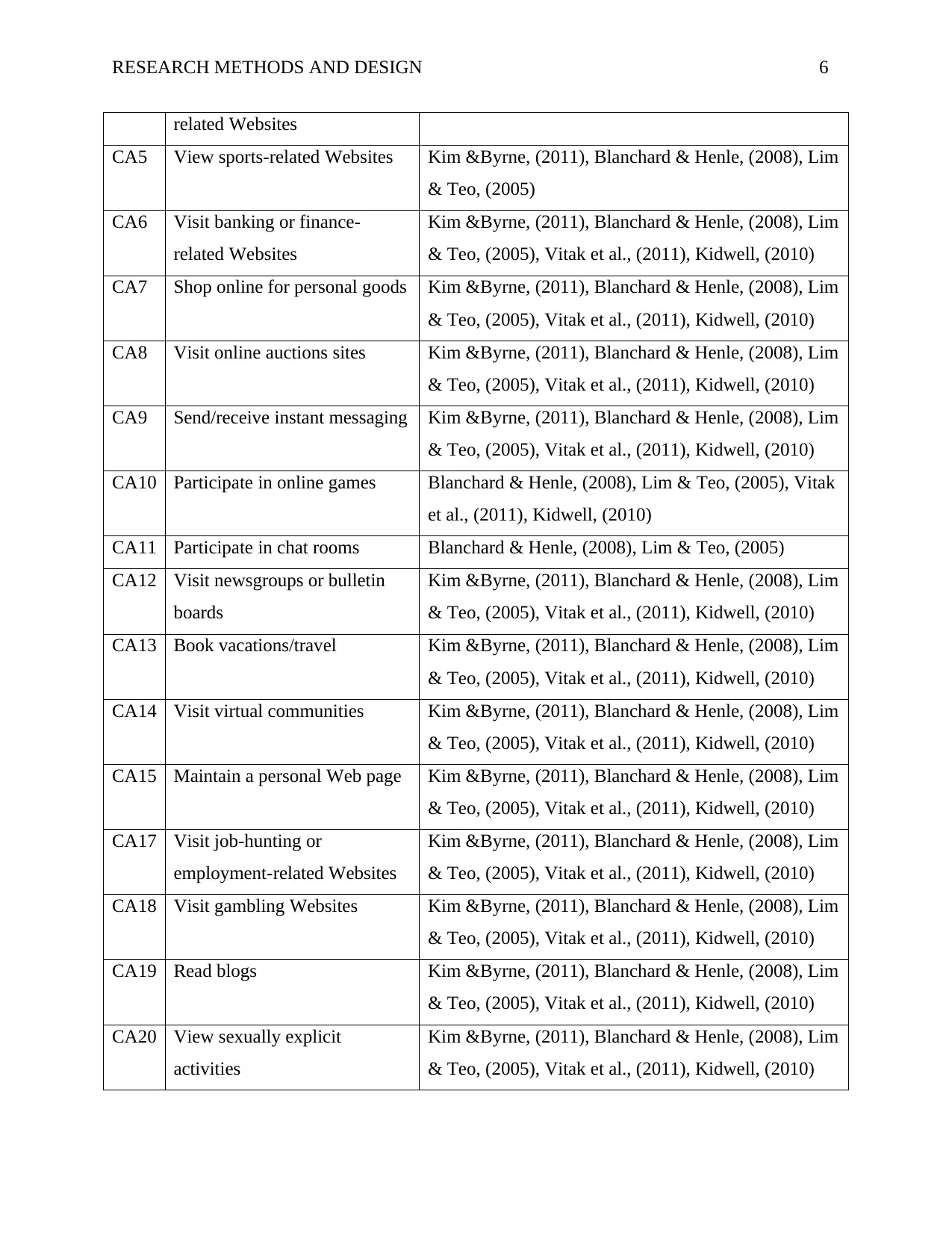
The following is a list of cyberslacking activities used in the survey.
Item Cyberslacking Activities Item Source
CA1 Check non-work related email Kim &Byrne, (2011)
CA2 Send non-work related email Vitak et al., (2011), Kim &Byrne, (2011)
CA3 Visit general news sites Kim &Byrne, (2011), Kidwell, (2010) Blanchard &
Henle, (2008)
CA4 Visit stock or investment- Kim &Byrne, (2011), Blanchard & Henle, (2008)
Cyberslacking
frequency(self
Cyberslacking
frequency(co-
Cyberslacking
time(self)
Cyberslacking
time(co-worker)
Ethical
Severity/Performan
ce
To obtain the regression equation, the SPSS data analysis tool is used to conduct multiple linear
regression analysis and ordinal logistic regression parameter estimates.
Measures of the Variables
A quantitative survey instrument is used in this research study for data collection. The
survey instrument contains six sections namely: (a) frequency of cyberslacking activity (self); (b)
frequency of cyberslacking activity (co-worker); (c) time spent on cyberslacking activity (self);
(d) time spend on cyberslacking activity (co-worker); (e) ethical severity; and (f) demographic
information. The survey utilizes a seven-point Likert scale to assess measured variables by
facilitating the participants identifying the activity and the perceived ethical severity. Time
spent, frequency and ethical severity are measured based on the twenty cyberslacking activities.
The following is a list of cyberslacking activities used in the survey.
Item Cyberslacking Activities Item Source
CA1 Check non-work related email Kim &Byrne, (2011)
CA2 Send non-work related email Vitak et al., (2011), Kim &Byrne, (2011)
CA3 Visit general news sites Kim &Byrne, (2011), Kidwell, (2010) Blanchard &
Henle, (2008)
CA4 Visit stock or investment- Kim &Byrne, (2011), Blanchard & Henle, (2008)
Cyberslacking
frequency(self
Cyberslacking
frequency(co-
Cyberslacking
time(self)
Cyberslacking
time(co-worker)
Ethical
Severity/Performan
ce
RESEARCH METHODS AND DESIGN 6
related Websites
CA5 View sports-related Websites Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005)
CA6 Visit banking or finance-
related Websites
Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA7 Shop online for personal goods Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA8 Visit online auctions sites Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA9 Send/receive instant messaging Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA10 Participate in online games Blanchard & Henle, (2008), Lim & Teo, (2005), Vitak
et al., (2011), Kidwell, (2010)
CA11 Participate in chat rooms Blanchard & Henle, (2008), Lim & Teo, (2005)
CA12 Visit newsgroups or bulletin
boards
Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA13 Book vacations/travel Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA14 Visit virtual communities Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA15 Maintain a personal Web page Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA17 Visit job-hunting or
employment-related Websites
Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA18 Visit gambling Websites Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA19 Read blogs Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA20 View sexually explicit
activities
Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
related Websites
CA5 View sports-related Websites Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005)
CA6 Visit banking or finance-
related Websites
Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA7 Shop online for personal goods Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA8 Visit online auctions sites Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA9 Send/receive instant messaging Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA10 Participate in online games Blanchard & Henle, (2008), Lim & Teo, (2005), Vitak
et al., (2011), Kidwell, (2010)
CA11 Participate in chat rooms Blanchard & Henle, (2008), Lim & Teo, (2005)
CA12 Visit newsgroups or bulletin
boards
Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA13 Book vacations/travel Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA14 Visit virtual communities Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA15 Maintain a personal Web page Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA17 Visit job-hunting or
employment-related Websites
Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA18 Visit gambling Websites Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA19 Read blogs Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)
CA20 View sexually explicit
activities
Kim &Byrne, (2011), Blanchard & Henle, (2008), Lim
& Teo, (2005), Vitak et al., (2011), Kidwell, (2010)

RESEARCH METHODS AND DESIGN 7
The frequency of the cyberslacking activities is measured using a seven-point Likert scale
which has the following:
1- never
2- once a month
3- every other week
4- one a week
5- several days a week
6- once a day
7- several times a day
The variable time spent on cyberslacking activities is also measured using a 7-point Likert
scale which ranges as follows:
1- never
2- on average about 15 minutes a day
3- on average about 30 minutes a day
4- on average about 1 hour a day
5- on average about 2-4 hours a day
6- on average about 5 to 7 hours a day
7- on average 8 or more hours a day
For the measure of ethical severity of cyberslacking activities, each of the 20 cyberslacking
activities was divided and participants asked how they ethically perceived each activity at the
worked place during working hours. A seven-point Likert scale was utilized to measure the
perceived severity of each activity as follows:
1- highly unethical
2- unethical
3- somewhat unethical
4- neither
5- somewhat ethical
6- ethical
7- highly ethical
Survey Questions
The frequency of the cyberslacking activities is measured using a seven-point Likert scale
which has the following:
1- never
2- once a month
3- every other week
4- one a week
5- several days a week
6- once a day
7- several times a day
The variable time spent on cyberslacking activities is also measured using a 7-point Likert
scale which ranges as follows:
1- never
2- on average about 15 minutes a day
3- on average about 30 minutes a day
4- on average about 1 hour a day
5- on average about 2-4 hours a day
6- on average about 5 to 7 hours a day
7- on average 8 or more hours a day
For the measure of ethical severity of cyberslacking activities, each of the 20 cyberslacking
activities was divided and participants asked how they ethically perceived each activity at the
worked place during working hours. A seven-point Likert scale was utilized to measure the
perceived severity of each activity as follows:
1- highly unethical
2- unethical
3- somewhat unethical
4- neither
5- somewhat ethical
6- ethical
7- highly ethical
Survey Questions
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH METHODS AND DESIGN 8
Data collection techniques are an integral part of the research design. In this study, data is
collected using a quantitative survey instrument which is distributed to the target audience
through emails. During the survey, Google Forms were will be used to collect data. The survey
instrument has got six sections: (1) Frequency of cyberslacking activity engagement (self); (2)
Frequency of cyberslacking activity engagement (co-worker); (3)time sent cyberslacking (self);
(4) time spent cyberslacking (co-worker); (5) ethical severity of cyberslacking activities; and (5)
demographic information. Sections 1, 2, 3, and 4 of the quantitative survey have got 20
cyberslacking activities. Each of the 20 items has got a seven-point Likert scale to help
participants measure the activity as well as the perceived severity of each activity.
Survey Questions for Self Cyberslacking Activity Frequency (SCAF)
How often do you estimate that you engage in the following cyberslacking activities during
working hours in a one-month period. Please mark the frequency using the following scale:
1- Never
2- Once a month
3- Every other week
4- Once a week
5- Several days a week
6- Once a day
7- Several times a day
Questions
1. I check non-work related emails
2. I send non-work related emails
3. I visit genera news Websites
4. I visit stock or investment Websites
5. I view sports-related Websites
6. I visit my banking or finance-related Websites
7. I shop online for personal goods
8. I visited online auction sites
9. I send or receive instant messaging
10. I participate in online games
11. I participate in online chat rooms
Data collection techniques are an integral part of the research design. In this study, data is
collected using a quantitative survey instrument which is distributed to the target audience
through emails. During the survey, Google Forms were will be used to collect data. The survey
instrument has got six sections: (1) Frequency of cyberslacking activity engagement (self); (2)
Frequency of cyberslacking activity engagement (co-worker); (3)time sent cyberslacking (self);
(4) time spent cyberslacking (co-worker); (5) ethical severity of cyberslacking activities; and (5)
demographic information. Sections 1, 2, 3, and 4 of the quantitative survey have got 20
cyberslacking activities. Each of the 20 items has got a seven-point Likert scale to help
participants measure the activity as well as the perceived severity of each activity.
Survey Questions for Self Cyberslacking Activity Frequency (SCAF)
How often do you estimate that you engage in the following cyberslacking activities during
working hours in a one-month period. Please mark the frequency using the following scale:
1- Never
2- Once a month
3- Every other week
4- Once a week
5- Several days a week
6- Once a day
7- Several times a day
Questions
1. I check non-work related emails
2. I send non-work related emails
3. I visit genera news Websites
4. I visit stock or investment Websites
5. I view sports-related Websites
6. I visit my banking or finance-related Websites
7. I shop online for personal goods
8. I visited online auction sites
9. I send or receive instant messaging
10. I participate in online games
11. I participate in online chat rooms

RESEARCH METHODS AND DESIGN 9
12. I visit newsgroups or bulletin boards
13. I book vacations/travel
14. I visit virtual communities
15. I work on maintaining my personal Web page or Website
16. I download music
17. I visit job-hunting or employment-related websites
18. I visit gambling websites
19. I read blogs
20. I view sexually explicit websites.
Section B of the survey instrument, Co-workers’ Cyberslacking Activity Frequency (CCAF)
will contain the same questions and the same seven-point Likert scale. However, for Self
Cyberslacking Activities Time (SCATx) and Co-Workers’ Cyberslacking Activities Time
(CCATx), the response will differ as follows:
1- never
2- on average about 15 minutes a day
3- on average about 30 minutes a day
4- on average about 1 hour a day
5- on average about 2-4 hours a day
6- on average about 5 to 7 hours a day
7- on average 8 or more hours a day
Validity and Reliability
Internal and External Validity
Internal Validity
Internal validity measures the accuracy of the study. It evaluates the extent to which the
study is free from errors and any variability in measurement is as a result of the independent
variable and nothing else (Sheriff, 2012). Internal validity is majorly concerned with the control
of the experiment and identifies how strong the research methods are. It describes the degree to
which the conclusion is warranted and eliminates alternative explanation for the result (Sheriff,
2012). In this research study, a panel of 8 experts had been invited to review the proposed
measures of variables. The panel constituted of professionals and practitioners in the field of
12. I visit newsgroups or bulletin boards
13. I book vacations/travel
14. I visit virtual communities
15. I work on maintaining my personal Web page or Website
16. I download music
17. I visit job-hunting or employment-related websites
18. I visit gambling websites
19. I read blogs
20. I view sexually explicit websites.
Section B of the survey instrument, Co-workers’ Cyberslacking Activity Frequency (CCAF)
will contain the same questions and the same seven-point Likert scale. However, for Self
Cyberslacking Activities Time (SCATx) and Co-Workers’ Cyberslacking Activities Time
(CCATx), the response will differ as follows:
1- never
2- on average about 15 minutes a day
3- on average about 30 minutes a day
4- on average about 1 hour a day
5- on average about 2-4 hours a day
6- on average about 5 to 7 hours a day
7- on average 8 or more hours a day
Validity and Reliability
Internal and External Validity
Internal Validity
Internal validity measures the accuracy of the study. It evaluates the extent to which the
study is free from errors and any variability in measurement is as a result of the independent
variable and nothing else (Sheriff, 2012). Internal validity is majorly concerned with the control
of the experiment and identifies how strong the research methods are. It describes the degree to
which the conclusion is warranted and eliminates alternative explanation for the result (Sheriff,
2012). In this research study, a panel of 8 experts had been invited to review the proposed
measures of variables. The panel constituted of professionals and practitioners in the field of

RESEARCH METHODS AND DESIGN 10
ethics, information systems, cybersecurity, and legal field. They validated the survey instruments
after making some minor changes according to their expertise and experience.
External Validity
External validity is the ability of the research results to be inferred to the world at large. It
assesses whether the relationship identified during the study can be generalized (Sheriff, 2012).
It is concerned with the naturalness of the study and identifies whether the outcome of the
research can be applied in the real world (Sheriff, 2012). Also, external validity describes the
degree to which the experiment is warrantied to generalize the result to another context. To
ensure the result of this study can be generalized in the real world, collection of gender, age,
education level, and job level must be collected from reliable sources such as government
agencies and other official sources.
Reliability
Reliability examines the quality of the measurement procedures used for data collection.
The results of a study can only be valid if the measurement procedure is reliable. A reliable
procedure must provide an accurate representation of the construct it measures. In quantitative
research, reliability represents the stability of the variables. One of the measures of the reliability
of a study is Cronbach’s Alpha which examines how well the items in a set correlate with each
other. A higher value of Cronbach’s Alpha implies higher reliability of the measurement
procedure. This research study applies the Cronbach’s Alpha to assess the reliability of the
measurement procedure. A recommended Cronbach’s alpha is a value greater than 0.7.
Analysis
In this section, analysis 5 constructs: (a) SCAF- a self cyberslacking activity frequency;
(b)CCAF- co-workers’ cyberslacking activity frequency; (c) SCATx- Self cyberslacking
activities time (SCATx); (d) CCATx- co-workers’ cyberslacking activities time; and ESCA-
ethical severity of cyberslacking activities is conducted. The key assumptions in this analysis are
that all the items are linearly distributed. Thus, all the constructs will be linearly aggregated as
follows:
Eq. 1: SCAF=SCA F1 +SCA F2+…+SCA F20
Eq. 2: CCAF=CCA F1 +CCA F2 +…+CCA F20
Eq. 3: SCAT=SCA T1 + SCA T2 +…+ SCA T 20
Eq. 4: CCAT =CCA T 1+CCA T 2+…+CCA T 20
ethics, information systems, cybersecurity, and legal field. They validated the survey instruments
after making some minor changes according to their expertise and experience.
External Validity
External validity is the ability of the research results to be inferred to the world at large. It
assesses whether the relationship identified during the study can be generalized (Sheriff, 2012).
It is concerned with the naturalness of the study and identifies whether the outcome of the
research can be applied in the real world (Sheriff, 2012). Also, external validity describes the
degree to which the experiment is warrantied to generalize the result to another context. To
ensure the result of this study can be generalized in the real world, collection of gender, age,
education level, and job level must be collected from reliable sources such as government
agencies and other official sources.
Reliability
Reliability examines the quality of the measurement procedures used for data collection.
The results of a study can only be valid if the measurement procedure is reliable. A reliable
procedure must provide an accurate representation of the construct it measures. In quantitative
research, reliability represents the stability of the variables. One of the measures of the reliability
of a study is Cronbach’s Alpha which examines how well the items in a set correlate with each
other. A higher value of Cronbach’s Alpha implies higher reliability of the measurement
procedure. This research study applies the Cronbach’s Alpha to assess the reliability of the
measurement procedure. A recommended Cronbach’s alpha is a value greater than 0.7.
Analysis
In this section, analysis 5 constructs: (a) SCAF- a self cyberslacking activity frequency;
(b)CCAF- co-workers’ cyberslacking activity frequency; (c) SCATx- Self cyberslacking
activities time (SCATx); (d) CCATx- co-workers’ cyberslacking activities time; and ESCA-
ethical severity of cyberslacking activities is conducted. The key assumptions in this analysis are
that all the items are linearly distributed. Thus, all the constructs will be linearly aggregated as
follows:
Eq. 1: SCAF=SCA F1 +SCA F2+…+SCA F20
Eq. 2: CCAF=CCA F1 +CCA F2 +…+CCA F20
Eq. 3: SCAT=SCA T1 + SCA T2 +…+ SCA T 20
Eq. 4: CCAT =CCA T 1+CCA T 2+…+CCA T 20
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESEARCH METHODS AND DESIGN 11
Eq. 5: ESCA=ESC A1+ESC A2 …+ ESC A20
After finding the aggregated constructs, the mean of the aggregated constructs scores and
standard deviation are calculated then plotted. The study will also perform analysis of covariance
(ANCOVA), multiple linear regression (MLR), and ordinal logistics regression (OLR) to
ascertain the perceived severity of the cyberslacking activities.
Eq. 5: ESCA=ESC A1+ESC A2 …+ ESC A20
After finding the aggregated constructs, the mean of the aggregated constructs scores and
standard deviation are calculated then plotted. The study will also perform analysis of covariance
(ANCOVA), multiple linear regression (MLR), and ordinal logistics regression (OLR) to
ascertain the perceived severity of the cyberslacking activities.

RESEARCH METHODS AND DESIGN 12
References
Alharthi, S. (2018). A Developmental Research of a Taxonomy for Employees’ Mobile Device
Cyberslacking and Commitment to the Organization in the Context of Productivity.
Blanchard, A. L., & Henle, C. A. (2008). Correlates of different forms of cyberloafing: The role
of norms and external locus of control. Computers in Human Behavior, 24(3), 1067-
1084.
Christensen, L. B., Johnson, B., Turner, L. A., & Christensen, L. B. (2011). Research methods,
design, and analysis.
Farivar, F. (2016). The effects of Cyberslacking through Social Media on Work-Life Conflict: A
fuzzy-set qualitative comparative analysis. 66).
Gliner, J. A., Morgan, G. A., & Leech, N. L. (2011). Research methods in applied settings: An
integrated approach to design and analysis. Routledge.
Hernández, W., Levy, Y., & Ramim, M. M. (2016). An empirical assessment of employee
cyberslacking in the public sector: The social engineering threat. Online Journal of
Applied Knowledge Management, 4(2), 93.
James, H. (2010). Cyberslacking, gold bricking and wasting time on the Internet. Retrieved on
January, 20, 2013.
Jandaghi, G., Alvani, S. M., Zarei Matin, H., & Fakheri Kozekanan, S. (2015). Cyberloafing
management in organizations. Iranian Journal of Management Studies, 8(3), 335-349.
Kamil, M. (2014). Factors influencing computer ethics at the workplace: A study of
professionals in South-East Asia. Kamil, NM (2014). Factors influencing computer ethics
at the workplace: A study of professionals in south-east Asia, Journal of Social Sciences
and Humanities, 9(2), 91-103.
Kasalak, M. A., Akar, H., & Kasalak, T. F. PERSONAL INTERNET USAGE OF
EMPLOYEES AND CYBERSLACKING TRENDS IN ANTALYA HOTEL
BUSINESSES.
Kim, S. J., & Byrne, S. (2011). Conceptualizing personal web usage in work contexts: A
preliminary framework. Computers in Human Behavior, 27(6), 2271-2283..
Köleoğlu, N. (2017). The Examination of Organizational Commitment and Interaction of
Cyberslacking for Employees in the Public Sector. European Journal of
Multidisciplinary Studies Articles, 5.
References
Alharthi, S. (2018). A Developmental Research of a Taxonomy for Employees’ Mobile Device
Cyberslacking and Commitment to the Organization in the Context of Productivity.
Blanchard, A. L., & Henle, C. A. (2008). Correlates of different forms of cyberloafing: The role
of norms and external locus of control. Computers in Human Behavior, 24(3), 1067-
1084.
Christensen, L. B., Johnson, B., Turner, L. A., & Christensen, L. B. (2011). Research methods,
design, and analysis.
Farivar, F. (2016). The effects of Cyberslacking through Social Media on Work-Life Conflict: A
fuzzy-set qualitative comparative analysis. 66).
Gliner, J. A., Morgan, G. A., & Leech, N. L. (2011). Research methods in applied settings: An
integrated approach to design and analysis. Routledge.
Hernández, W., Levy, Y., & Ramim, M. M. (2016). An empirical assessment of employee
cyberslacking in the public sector: The social engineering threat. Online Journal of
Applied Knowledge Management, 4(2), 93.
James, H. (2010). Cyberslacking, gold bricking and wasting time on the Internet. Retrieved on
January, 20, 2013.
Jandaghi, G., Alvani, S. M., Zarei Matin, H., & Fakheri Kozekanan, S. (2015). Cyberloafing
management in organizations. Iranian Journal of Management Studies, 8(3), 335-349.
Kamil, M. (2014). Factors influencing computer ethics at the workplace: A study of
professionals in South-East Asia. Kamil, NM (2014). Factors influencing computer ethics
at the workplace: A study of professionals in south-east Asia, Journal of Social Sciences
and Humanities, 9(2), 91-103.
Kasalak, M. A., Akar, H., & Kasalak, T. F. PERSONAL INTERNET USAGE OF
EMPLOYEES AND CYBERSLACKING TRENDS IN ANTALYA HOTEL
BUSINESSES.
Kim, S. J., & Byrne, S. (2011). Conceptualizing personal web usage in work contexts: A
preliminary framework. Computers in Human Behavior, 27(6), 2271-2283..
Köleoğlu, N. (2017). The Examination of Organizational Commitment and Interaction of
Cyberslacking for Employees in the Public Sector. European Journal of
Multidisciplinary Studies Articles, 5.

RESEARCH METHODS AND DESIGN 13
Kuschnaroff, F. C., & Bayma, F. O. (2014). Critical analysis of cyberslacking in organizational
structures. Journal of Human Resource and Sustainability Studies, 2(02), 70.
Lim, V. K., & Teo, T. S. (2005). Prevalence, perceived seriousness, justification and regulation
of cyberloafing in Singapore: An exploratory study. Information & Management, 42(8),
1081-1093.
ÖRÜCÜ, E., & YILDIZ, H. (2014). The Personal Internet and Technology Usage at the
Workplace: Cyberslacking. Ege Akademik Bakış Dergisi, 14(1), 99-114.
Ozler, D. E., & POLAT, G. (2012). Cyberloafing phenomenon in organizations: Determinants
and impacts. International Journal of eBusiness and eGovernment Studies, 4(2), 1-15.
Sheriff, A. M. (2012). The techniques and rationale of e-surveillance practices in organizations.
Vitak, J., Crouse, J., & LaRose, R. (2011). Personal Internet use at work: Understanding
cyberslacking. Computers in Human Behavior, 27(5), 1751-1759.
Kuschnaroff, F. C., & Bayma, F. O. (2014). Critical analysis of cyberslacking in organizational
structures. Journal of Human Resource and Sustainability Studies, 2(02), 70.
Lim, V. K., & Teo, T. S. (2005). Prevalence, perceived seriousness, justification and regulation
of cyberloafing in Singapore: An exploratory study. Information & Management, 42(8),
1081-1093.
ÖRÜCÜ, E., & YILDIZ, H. (2014). The Personal Internet and Technology Usage at the
Workplace: Cyberslacking. Ege Akademik Bakış Dergisi, 14(1), 99-114.
Ozler, D. E., & POLAT, G. (2012). Cyberloafing phenomenon in organizations: Determinants
and impacts. International Journal of eBusiness and eGovernment Studies, 4(2), 1-15.
Sheriff, A. M. (2012). The techniques and rationale of e-surveillance practices in organizations.
Vitak, J., Crouse, J., & LaRose, R. (2011). Personal Internet use at work: Understanding
cyberslacking. Computers in Human Behavior, 27(5), 1751-1759.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





