Impact of Blockchain on Cloud Computing in Business
VerifiedAdded on 2023/04/21
|64
|13659
|204
AI Summary
This research study focuses on the impact of Blockchain technology on cloud computing in business. It explores the implications of Blockchain on service, business operations, and regulations. The study aims to identify how Blockchain can improve efficiency, security, and cost-effectiveness in the business environment. The research objectives include understanding the impact of Blockchain on cloud computing, identifying security issues, and finding solutions to enhance the system for customer service. The literature review discusses the concept of Blockchain technology, its impact on service, business, and regulations, and the need for proper security measures. The study aims to provide insights into the implementation of Blockchain in cloud computing and its effects on business services.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: RESEARCH PAPER
Topic: Impact of Blockchain on Cloud Computing in Business
Name of the Student
Name of the University
Author Note
Topic: Impact of Blockchain on Cloud Computing in Business
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1RESEARCH PAPER
Table of Contents
Chapter 1: Introduction..............................................................................................................4
1.1 Background of the study..................................................................................................4
1.2 Research Aims and Objectives.........................................................................................6
1.3 Research Questions..........................................................................................................6
1.4 Problem Statement...........................................................................................................7
1.5 Rationale of the study.......................................................................................................7
1.6 Research Hypothesis........................................................................................................8
1.7 Summary..........................................................................................................................8
Chapter 2: Literature Review.....................................................................................................9
2.1 Introduction......................................................................................................................9
2.2 Concept of Blockchain Technology.................................................................................9
2.3 The impact of Blockchain Technology on Service, Business and Regulations.............11
2.4 Information symmetry through transparent record-keeping..........................................11
2.5 The impact of cloud technology on business.................................................................12
2.6 Security issues regarding cloud technology...................................................................13
2.7 Cloud ERP Blockchain solution to provide services to the customers..........................16
2.8 A gap in the Literature...................................................................................................17
Table of Contents
Chapter 1: Introduction..............................................................................................................4
1.1 Background of the study..................................................................................................4
1.2 Research Aims and Objectives.........................................................................................6
1.3 Research Questions..........................................................................................................6
1.4 Problem Statement...........................................................................................................7
1.5 Rationale of the study.......................................................................................................7
1.6 Research Hypothesis........................................................................................................8
1.7 Summary..........................................................................................................................8
Chapter 2: Literature Review.....................................................................................................9
2.1 Introduction......................................................................................................................9
2.2 Concept of Blockchain Technology.................................................................................9
2.3 The impact of Blockchain Technology on Service, Business and Regulations.............11
2.4 Information symmetry through transparent record-keeping..........................................11
2.5 The impact of cloud technology on business.................................................................12
2.6 Security issues regarding cloud technology...................................................................13
2.7 Cloud ERP Blockchain solution to provide services to the customers..........................16
2.8 A gap in the Literature...................................................................................................17

2RESEARCH PAPER
2.9 Summary........................................................................................................................18
Chapter 3: Proposed methodology...........................................................................................19
3.1 Introduction....................................................................................................................19
3.2 Research philosophy......................................................................................................19
3.3 Research approach.........................................................................................................20
3.4 Research design..............................................................................................................20
3.5 Data collection and analysis...........................................................................................21
3.5.1 Data collection methods..........................................................................................21
3.5.2 Data analysis methods.............................................................................................22
3.6 Population and sample...................................................................................................23
3.7 Ethical consideration......................................................................................................24
3.8 Research limitations.......................................................................................................24
3.9 Summary........................................................................................................................25
Chapter 4: Data Analysis and Findings....................................................................................26
4.1 Introduction....................................................................................................................26
4.2 Quantitative Data Analysis............................................................................................26
4.3 Regression Analysis.......................................................................................................49
4.4 Summary........................................................................................................................56
2.9 Summary........................................................................................................................18
Chapter 3: Proposed methodology...........................................................................................19
3.1 Introduction....................................................................................................................19
3.2 Research philosophy......................................................................................................19
3.3 Research approach.........................................................................................................20
3.4 Research design..............................................................................................................20
3.5 Data collection and analysis...........................................................................................21
3.5.1 Data collection methods..........................................................................................21
3.5.2 Data analysis methods.............................................................................................22
3.6 Population and sample...................................................................................................23
3.7 Ethical consideration......................................................................................................24
3.8 Research limitations.......................................................................................................24
3.9 Summary........................................................................................................................25
Chapter 4: Data Analysis and Findings....................................................................................26
4.1 Introduction....................................................................................................................26
4.2 Quantitative Data Analysis............................................................................................26
4.3 Regression Analysis.......................................................................................................49
4.4 Summary........................................................................................................................56
3RESEARCH PAPER
References................................................................................................................................57
Appendix..................................................................................................................................62
References................................................................................................................................57
Appendix..................................................................................................................................62
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4RESEARCH PAPER
Chapter 1: Introduction
1.1 Background of the study
The thesis paper is based on the impact of Blockchain on cloud computing in
business. Riasanow et al. (2018) defined that the Blockchain technology can share digital
ledger, which can record the transactions into the public and private peer-to-peer networks.
There is huge opportunity taking place to create the market for Blockchain based businesses
into the cloud. The cloud market is booming, and more applications, as well as businesses,
are moving to the cloud. It can benefit from greater accessibility, the effectiveness of the cost,
lower the risk as well as flexibility into the resource usages. Mostly, Blockchain helps in
finalising the transactional records, especially when it comes to securing the bitcoin and other
cryptocurrency (Yeniyurt et al. 2019). Treiblmaier and Beck (2019) argued that in the
business organisation, Blockchain technology could improve the business efficiency, secure
the business processes as well as cut the cost down by removal of unnecessary middlemen.
There are numerous organisations found to be implementing the Blockchain technology for
the business operations, and the implementation has not only been secluded to any specific
industry. It has been reported that various sectors have been making the use of Blockchain
technology in their business operation. These include the areas of healthcare, finance
industries, real estate agencies and even government organisations (Novais, Maqueira and
Ortiz-Bas 2019). Primarily the Blockchain technology is implemented along with cloud
technology.
In the research study, Blockchain technology is used to execute the business processes
in two ways, such as it can record the process execution status for the participants while
process exchange of messages. Liu and He (2019) discussed that smart contracts could check
those interactions can conform to the business model. The Blockchain technology can
Chapter 1: Introduction
1.1 Background of the study
The thesis paper is based on the impact of Blockchain on cloud computing in
business. Riasanow et al. (2018) defined that the Blockchain technology can share digital
ledger, which can record the transactions into the public and private peer-to-peer networks.
There is huge opportunity taking place to create the market for Blockchain based businesses
into the cloud. The cloud market is booming, and more applications, as well as businesses,
are moving to the cloud. It can benefit from greater accessibility, the effectiveness of the cost,
lower the risk as well as flexibility into the resource usages. Mostly, Blockchain helps in
finalising the transactional records, especially when it comes to securing the bitcoin and other
cryptocurrency (Yeniyurt et al. 2019). Treiblmaier and Beck (2019) argued that in the
business organisation, Blockchain technology could improve the business efficiency, secure
the business processes as well as cut the cost down by removal of unnecessary middlemen.
There are numerous organisations found to be implementing the Blockchain technology for
the business operations, and the implementation has not only been secluded to any specific
industry. It has been reported that various sectors have been making the use of Blockchain
technology in their business operation. These include the areas of healthcare, finance
industries, real estate agencies and even government organisations (Novais, Maqueira and
Ortiz-Bas 2019). Primarily the Blockchain technology is implemented along with cloud
technology.
In the research study, Blockchain technology is used to execute the business processes
in two ways, such as it can record the process execution status for the participants while
process exchange of messages. Liu and He (2019) discussed that smart contracts could check
those interactions can conform to the business model. The Blockchain technology can

5RESEARCH PAPER
coordinate collaborative processes executions. The smart contracts can drive the business
process as well as perform the data transformations. Novais, Maqueira and Ortiz-Bas (2019)
mentioned that the Blockchain is a new alternative to the traditional currency and centralized
banking along with traditional methods. It is not changing their ways as it can handle the
financial transactions. Into the business organisation, Blockchain is considered as a
distributed ledger which can maintain a continuous growing list of the transactions across the
network distributed over a various amount of computers. Davcev et al. (2018) summarized
that it makes it impossible to hack the data of the business organisation as it can provide
security to the payment methods. Cloud storage is an application that the business is taking
advantage of using the Blockchain technology. It is a way that the business is offered with
secure cloud storage while there is decreasing dependency.
Sharma, Moon and Park (2017) discussed that most of the business organisation, as
well as business activities, are felt to have an impact on the Blockchain technology and
applications based on it. The Blockchain technology is required no central node; and the
result is that the businesses are at risk to serve as intermediaries. Zhao and Duncan (2018)
illustrated that the Blockchain technology is expected to make functions of the problems of
middlemen. It is required to position the business organisation to capitalize on new
Blockchain applications as they are required to process the electronic transactions. It is done
to make sure that the system can meet with the industry's standards (Viriyasitavat et al.
2018). The research study is provided regarding changes into payments are done due to
progress in Blockchain and in what directions the business has thought to overhaul the
technology for their business benefits.
coordinate collaborative processes executions. The smart contracts can drive the business
process as well as perform the data transformations. Novais, Maqueira and Ortiz-Bas (2019)
mentioned that the Blockchain is a new alternative to the traditional currency and centralized
banking along with traditional methods. It is not changing their ways as it can handle the
financial transactions. Into the business organisation, Blockchain is considered as a
distributed ledger which can maintain a continuous growing list of the transactions across the
network distributed over a various amount of computers. Davcev et al. (2018) summarized
that it makes it impossible to hack the data of the business organisation as it can provide
security to the payment methods. Cloud storage is an application that the business is taking
advantage of using the Blockchain technology. It is a way that the business is offered with
secure cloud storage while there is decreasing dependency.
Sharma, Moon and Park (2017) discussed that most of the business organisation, as
well as business activities, are felt to have an impact on the Blockchain technology and
applications based on it. The Blockchain technology is required no central node; and the
result is that the businesses are at risk to serve as intermediaries. Zhao and Duncan (2018)
illustrated that the Blockchain technology is expected to make functions of the problems of
middlemen. It is required to position the business organisation to capitalize on new
Blockchain applications as they are required to process the electronic transactions. It is done
to make sure that the system can meet with the industry's standards (Viriyasitavat et al.
2018). The research study is provided regarding changes into payments are done due to
progress in Blockchain and in what directions the business has thought to overhaul the
technology for their business benefits.

6RESEARCH PAPER
1.2 Research Aims and Objectives
The aim of the research study is to find out the impact that Blockchain technology
assets on cloud computing technology. This is to be done so that it can be further utilised to
implement both the technologies for the betterment of the financial transaction system. The
impact would be upon the business organisations and other uses for the customers.
Following are the research objectives based on which this research study is being conducted,
such as:
To find out the impact of Blockchain technology on cloud computing technology
To identify the security issues of Blockchain on the cloud computing
To find out how the issues regarding the technology can be avoided to make the
system appropriate for service provided to the customers
1.3 Research Questions
The inclusion of proper research questions dependent upon the undertaken topic to
find out what problem is the research trying to answer that would identify and try to solve the
made item. According to the entire issue of the impact of Blockchain technology in the
technology of cloud computing, following are the research questions based on which the
study is carried out, such as:
1. What is the impact of Blockchain technology when implemented on cloud computing
in the business?
2. Is Blockchain technology appropriate for providing services to the customers when it
is adopted into business organisations?
1.2 Research Aims and Objectives
The aim of the research study is to find out the impact that Blockchain technology
assets on cloud computing technology. This is to be done so that it can be further utilised to
implement both the technologies for the betterment of the financial transaction system. The
impact would be upon the business organisations and other uses for the customers.
Following are the research objectives based on which this research study is being conducted,
such as:
To find out the impact of Blockchain technology on cloud computing technology
To identify the security issues of Blockchain on the cloud computing
To find out how the issues regarding the technology can be avoided to make the
system appropriate for service provided to the customers
1.3 Research Questions
The inclusion of proper research questions dependent upon the undertaken topic to
find out what problem is the research trying to answer that would identify and try to solve the
made item. According to the entire issue of the impact of Blockchain technology in the
technology of cloud computing, following are the research questions based on which the
study is carried out, such as:
1. What is the impact of Blockchain technology when implemented on cloud computing
in the business?
2. Is Blockchain technology appropriate for providing services to the customers when it
is adopted into business organisations?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RESEARCH PAPER
1.4 Problem Statement
Blockchain technology is used as cyber money by most of the business organisations
for daily transactions. When cloud computing is implemented with this technology, then it
becomes a huge risk for the business organisation to deliver secure transactions to the
customers. In this research study, it is a problem to find out the negative impacts of
Blockchain technology with cloud computing in the business so that it can provide better
services to their customers. The study is based on finding solutions to the problem regarding
the Blockchain technology. Thus, the research would be conducted to find a solution for
eliminating the problem regarding the technology of cloud computing. The technology is
amalgamated to Blockchain facilities to find out if they are harming the business
organisations and their services to the customers.
1.5 Rationale of the study
Blockchain technology mostly deals with the recording of the operations and the
transactions within the organisation. These are linked in peer-to-peer networks and trading
with cryptocurrency methods. This is understandable that the entire operation regarding the
Blockchain technology occurs online. Business operations would be much easier if the whole
of the transactional system is based upon cyber-based policies happening over networks.
Cloud implementation has also been regarded as a technological advancement where a
storage system is based upon the internet. There is no constraint regarding the storage space
in cloud computing technology. This is because; the entire system is based upon the virtual
storage area, and it does not have a specific limitation of the storage area. Technology, as the
whole of Blockchain into cloud computing, mostly deals with the financial and economic
aspects of the business. Therefore, it should be made sure that proper methods are applied to
technology as there is a constant risk of malicious hackers. They have been trying to steal the
1.4 Problem Statement
Blockchain technology is used as cyber money by most of the business organisations
for daily transactions. When cloud computing is implemented with this technology, then it
becomes a huge risk for the business organisation to deliver secure transactions to the
customers. In this research study, it is a problem to find out the negative impacts of
Blockchain technology with cloud computing in the business so that it can provide better
services to their customers. The study is based on finding solutions to the problem regarding
the Blockchain technology. Thus, the research would be conducted to find a solution for
eliminating the problem regarding the technology of cloud computing. The technology is
amalgamated to Blockchain facilities to find out if they are harming the business
organisations and their services to the customers.
1.5 Rationale of the study
Blockchain technology mostly deals with the recording of the operations and the
transactions within the organisation. These are linked in peer-to-peer networks and trading
with cryptocurrency methods. This is understandable that the entire operation regarding the
Blockchain technology occurs online. Business operations would be much easier if the whole
of the transactional system is based upon cyber-based policies happening over networks.
Cloud implementation has also been regarded as a technological advancement where a
storage system is based upon the internet. There is no constraint regarding the storage space
in cloud computing technology. This is because; the entire system is based upon the virtual
storage area, and it does not have a specific limitation of the storage area. Technology, as the
whole of Blockchain into cloud computing, mostly deals with the financial and economic
aspects of the business. Therefore, it should be made sure that proper methods are applied to
technology as there is a constant risk of malicious hackers. They have been trying to steal the

8RESEARCH PAPER
cryptocurrency at any vulnerability found. If this happens, the business organisations seeking
to implement this technology as a service to the customers will face problems. Therefore, the
study is necessary to find out the impact of the Blockchain technology on cloud computing
and if it creates any issues after implementation to the business services. In addition to that,
the further ways by which the services can be enhanced would be pointed out through the
research.
1.6 Research Hypothesis
The research hypothesis that would be considered for the research in this regard based
on the topic would be described as follows:
H0: Blockchain technology has no impact on cloud computing technology and business
services
H1: Blockchain technology has a definite effect on cloud computing technology and business
services
1.7 Summary
It is summarized that Blockchain technology is such a technology which is provided
with a huge impact on the business organisations by improving the mode of transactions. The
first application of it is bitcoin, which is raised into the financial services sector puts the
payment methods secured around the Blockchain technology. The study is focused on
gathering a higher number of experts to get a better understanding of the implications of
Blockchain technology into business organisations. The paper is also outlined changes which
are caused due to implementation of Blockchain in cloud computing. The research study is
contributed to literature study in the next chapter by analyzing the impact of Blockchain
technology in business.
cryptocurrency at any vulnerability found. If this happens, the business organisations seeking
to implement this technology as a service to the customers will face problems. Therefore, the
study is necessary to find out the impact of the Blockchain technology on cloud computing
and if it creates any issues after implementation to the business services. In addition to that,
the further ways by which the services can be enhanced would be pointed out through the
research.
1.6 Research Hypothesis
The research hypothesis that would be considered for the research in this regard based
on the topic would be described as follows:
H0: Blockchain technology has no impact on cloud computing technology and business
services
H1: Blockchain technology has a definite effect on cloud computing technology and business
services
1.7 Summary
It is summarized that Blockchain technology is such a technology which is provided
with a huge impact on the business organisations by improving the mode of transactions. The
first application of it is bitcoin, which is raised into the financial services sector puts the
payment methods secured around the Blockchain technology. The study is focused on
gathering a higher number of experts to get a better understanding of the implications of
Blockchain technology into business organisations. The paper is also outlined changes which
are caused due to implementation of Blockchain in cloud computing. The research study is
contributed to literature study in the next chapter by analyzing the impact of Blockchain
technology in business.

9RESEARCH PAPER
Chapter 2: Literature Review
2.1 Introduction
This research study is focused on the impact of Blockchain technology in cloud
computing into the business organisation. In this literature study, there is an investigation of
the definition of Blockchain technology as well as survey trends of this technology. The
trends are analysed in this study based on considering the environments of cloud computing.
Mainly, there is a review of the usage of Blockchain technology into the business
organisation, which helps to secure the electronic transactions and provides the business with
a secured mode of payments. There is a discussion of considerations of the Blockchain
security as well as secured solutions into the business environment. This literature studies the
Blockchain technology and its trends by analysing proposed technology. It is also discussing
the solutions using bitcoin in addition to future study areas. The researcher has fostered the
development of Blockchain technology by analysing the trends of Blockchain security. The
rest of the section is organized as discussing related works included basic concepts of the
Blockchain technology as well as bitcoin. There is a discussion of Blockchain included its
settlement and security of the transaction software. Finally, there is a summary in the final
section of the literature review.
2.2 Concept of Blockchain Technology
Aste, Tasca and Matteo (2017) stated that the Blockchain is such a technology which
can allow members to keep ledger contains transactional data. It is used to update the ledgers
for maintaining integrity where there are innovative transactions. Advancement of the
Blockchain technology can help to verify the reliability of the transactions. The authors
Miraz and Ali (2018), stated that the technology of Blockchain initiates a broker-free P2P
characteristic. Thus it is not necessary that authorisation of a third party is required in these
Chapter 2: Literature Review
2.1 Introduction
This research study is focused on the impact of Blockchain technology in cloud
computing into the business organisation. In this literature study, there is an investigation of
the definition of Blockchain technology as well as survey trends of this technology. The
trends are analysed in this study based on considering the environments of cloud computing.
Mainly, there is a review of the usage of Blockchain technology into the business
organisation, which helps to secure the electronic transactions and provides the business with
a secured mode of payments. There is a discussion of considerations of the Blockchain
security as well as secured solutions into the business environment. This literature studies the
Blockchain technology and its trends by analysing proposed technology. It is also discussing
the solutions using bitcoin in addition to future study areas. The researcher has fostered the
development of Blockchain technology by analysing the trends of Blockchain security. The
rest of the section is organized as discussing related works included basic concepts of the
Blockchain technology as well as bitcoin. There is a discussion of Blockchain included its
settlement and security of the transaction software. Finally, there is a summary in the final
section of the literature review.
2.2 Concept of Blockchain Technology
Aste, Tasca and Matteo (2017) stated that the Blockchain is such a technology which
can allow members to keep ledger contains transactional data. It is used to update the ledgers
for maintaining integrity where there are innovative transactions. Advancement of the
Blockchain technology can help to verify the reliability of the transactions. The authors
Miraz and Ali (2018), stated that the technology of Blockchain initiates a broker-free P2P
characteristic. Thus it is not necessary that authorisation of a third party is required in these
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10RESEARCH PAPER
kinds of transactions. This is a problem since it is tough for a hacker to handle into these
kinds of transactional information system if they are under the ownership of several people.
The security expense becomes saved, and transactions are automatically approved and
recorded by mass participation with assured promptness. The authors Li et al. (2017), stated
that various ongoing studies are trying to secure the vulnerabilities in this regard. While some
think that the security system would be even more vulnerable if the Blockchain technology is
utilised for the transactions involving bitcoin and taken to the cloud services. It is necessary
since understanding it from the aspect of a business perspective becomes much essential to
enhance the services.
Since cloud system has no limited and physical attributes of the storage areas, the
ERP implementation to track down the order would be difficult to maintain. It only happens
when the security vulnerabilities are not addressed before Blockchain technology is implied
upon. Thus, the authors Dorri, Kanhere and Jurdak (2016), suggests that the weaknesses of
the Blockchain transactional elements like bitcoin. These are incredibly vulnerable to falling
prey to malware should apply proper ways. The procedures are included to follow appropriate
security eradicating methodologies on the cloud computing technologies. In addition to that,
the necessary implementation process of Blockchain Technology in Cloud Computing and
their impact on the service provisions of the business organisation is also dependent on the
security system. If it is porous enough, customers would not like to invest their time and
online money to the business services. Following would be the findings of the literature
review that would bring possible effects of Blockchain and its implementation in a business
industry over cloud technology bring about in researches done previously.
kinds of transactions. This is a problem since it is tough for a hacker to handle into these
kinds of transactional information system if they are under the ownership of several people.
The security expense becomes saved, and transactions are automatically approved and
recorded by mass participation with assured promptness. The authors Li et al. (2017), stated
that various ongoing studies are trying to secure the vulnerabilities in this regard. While some
think that the security system would be even more vulnerable if the Blockchain technology is
utilised for the transactions involving bitcoin and taken to the cloud services. It is necessary
since understanding it from the aspect of a business perspective becomes much essential to
enhance the services.
Since cloud system has no limited and physical attributes of the storage areas, the
ERP implementation to track down the order would be difficult to maintain. It only happens
when the security vulnerabilities are not addressed before Blockchain technology is implied
upon. Thus, the authors Dorri, Kanhere and Jurdak (2016), suggests that the weaknesses of
the Blockchain transactional elements like bitcoin. These are incredibly vulnerable to falling
prey to malware should apply proper ways. The procedures are included to follow appropriate
security eradicating methodologies on the cloud computing technologies. In addition to that,
the necessary implementation process of Blockchain Technology in Cloud Computing and
their impact on the service provisions of the business organisation is also dependent on the
security system. If it is porous enough, customers would not like to invest their time and
online money to the business services. Following would be the findings of the literature
review that would bring possible effects of Blockchain and its implementation in a business
industry over cloud technology bring about in researches done previously.

11RESEARCH PAPER
2.3 The impact of Blockchain Technology on Service, Business and Regulations
Public and private sectors have been bringing about several expectations the
technology of Blockchain and its combination with the technology of cloud computing.
Taghavi et al. (2018) identified that the reason behind this combination is that this technology
sets for the development of a peer-to-peer platform, or a P2P platform. There is no
requirement of intermediary official social platform or official cyber platform for this
particular process, and only the exchange of information is needed. The author also identifies
that the utilisation of the technology of Blockchain has the potential of radically transforming
the face of the industry that is currently seen. There is no need of involving an intermediate
during the exchange of digitised goods, assets and information. The economic sectors are
prone to further improvements since they are radically enhancing the regulatory controls for
the organisation. The author Atlam et al. (2018), also characterises that it is one of the fourth
incoming industrial revolution. This is led by the combination and adoption of various
technologies. This has been increasingly narrowing the gap between the physical and the
virtual world. The transactions are occurred in various industries such as retail, IT,
manufacturing and banking in terms of the utilisation of cryptocurrency for business mode
transactions. Another author, Xiong et al. (2018), pointed out the fact that the Blockchain
technology has the potential for disrupting both the industry and the society at large.
2.4 Information symmetry through transparent record-keeping
At present, trades and negotiations are influenced by asymmetric information between
economic agents which give origin to problems like moral hazard and adverse selections.
Those problems have been historically solved by the introduction of central authorities with
function as a single point of control. It also has a potential point of failure when the
possibilities of attaining perfection are not given much priority. Lack of traceability and
2.3 The impact of Blockchain Technology on Service, Business and Regulations
Public and private sectors have been bringing about several expectations the
technology of Blockchain and its combination with the technology of cloud computing.
Taghavi et al. (2018) identified that the reason behind this combination is that this technology
sets for the development of a peer-to-peer platform, or a P2P platform. There is no
requirement of intermediary official social platform or official cyber platform for this
particular process, and only the exchange of information is needed. The author also identifies
that the utilisation of the technology of Blockchain has the potential of radically transforming
the face of the industry that is currently seen. There is no need of involving an intermediate
during the exchange of digitised goods, assets and information. The economic sectors are
prone to further improvements since they are radically enhancing the regulatory controls for
the organisation. The author Atlam et al. (2018), also characterises that it is one of the fourth
incoming industrial revolution. This is led by the combination and adoption of various
technologies. This has been increasingly narrowing the gap between the physical and the
virtual world. The transactions are occurred in various industries such as retail, IT,
manufacturing and banking in terms of the utilisation of cryptocurrency for business mode
transactions. Another author, Xiong et al. (2018), pointed out the fact that the Blockchain
technology has the potential for disrupting both the industry and the society at large.
2.4 Information symmetry through transparent record-keeping
At present, trades and negotiations are influenced by asymmetric information between
economic agents which give origin to problems like moral hazard and adverse selections.
Those problems have been historically solved by the introduction of central authorities with
function as a single point of control. It also has a potential point of failure when the
possibilities of attaining perfection are not given much priority. Lack of traceability and

12RESEARCH PAPER
transparent accounting are increasing regulatory oversight. Blockchain challenges are
reduced by eliminating the imbalance of information among agents. The author Samaniego
and Deters (2016) found out that the shared that the transparent ledger increases the
cooperation between regulators and regulated entities. Thus, Blockchain becomes a shared
data repository for them. It allows us to move from post-transaction monitoring to on-demand
and immediate tracking. It improves the capability of regulators to fulfil their mandate of
ensuring the legality, security and stability of the markets.
Indeed, employing Blockchain technology, it is possible to provide access to auditable
data which are verified, time-stamped and immutable, generating a transparent, inter-operable
environment where rules can be implemented, enforced and adapted. It is also pointed out the
reliability and reputation of clients and services providers can be verified and monitored by
analysing the historical record in the Blockchain. Rules can be encoded within the system
enabling automated review via audit software. Adoption of Blockchain technologies in the
services sector has the potential to be beneficial to both industry and regulators. This
convergence of industry and government interests is unique and opens great opportunities.
2.5 The impact of cloud technology on business
Cloud technology is the latest addition to the world of business that has been impacted
and transformed the way that marketing happens in the most recent times. The reports have
found out that mostly the companies have been running on the utilisation of cloud technology
instead of the traditional forms of running a business on a PC or with the help of LAN. The
implementation of the cloud has benefitted the organisation in various ways where the
employees have become more self-sufficient while performing a particular kind of job. They
are much more cost effective than the traditional forms of business operations. The author
Zhao and Duncan (2018), have also identified that it not includes the day to day operations of
transparent accounting are increasing regulatory oversight. Blockchain challenges are
reduced by eliminating the imbalance of information among agents. The author Samaniego
and Deters (2016) found out that the shared that the transparent ledger increases the
cooperation between regulators and regulated entities. Thus, Blockchain becomes a shared
data repository for them. It allows us to move from post-transaction monitoring to on-demand
and immediate tracking. It improves the capability of regulators to fulfil their mandate of
ensuring the legality, security and stability of the markets.
Indeed, employing Blockchain technology, it is possible to provide access to auditable
data which are verified, time-stamped and immutable, generating a transparent, inter-operable
environment where rules can be implemented, enforced and adapted. It is also pointed out the
reliability and reputation of clients and services providers can be verified and monitored by
analysing the historical record in the Blockchain. Rules can be encoded within the system
enabling automated review via audit software. Adoption of Blockchain technologies in the
services sector has the potential to be beneficial to both industry and regulators. This
convergence of industry and government interests is unique and opens great opportunities.
2.5 The impact of cloud technology on business
Cloud technology is the latest addition to the world of business that has been impacted
and transformed the way that marketing happens in the most recent times. The reports have
found out that mostly the companies have been running on the utilisation of cloud technology
instead of the traditional forms of running a business on a PC or with the help of LAN. The
implementation of the cloud has benefitted the organisation in various ways where the
employees have become more self-sufficient while performing a particular kind of job. They
are much more cost effective than the traditional forms of business operations. The author
Zhao and Duncan (2018), have also identified that it not includes the day to day operations of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13RESEARCH PAPER
a particular job but also encourages all kinds of applications in the cloud nowadays, like
CRM, accounting, HR, and custom-built applications. Over, upgrades are periodically
completed by cloud providers to facilitate new features, security, and performance
enhancements automatically. Cloud technology follows a pay-as-you-go model. Finally,
cloud applications and adaptation of Cloud technology, does not consume up the valuable IT
resources of any company. And adopting Cloud, allows the customer to focus on deploying
more applications, new projects, and innovation. Cloud computing is a modest idea, but it can
have a considerable impact on any business.
2.6 Security issues regarding cloud technology
However, there are various security constraints regarding the adoption of cloud
implementations in the business industries as well. The process of creating and managing a
secure cloud space is a more challenging task than creating a safe classical IT environment.
Given the immaturity of this technology, the new resources and the reallocation of traditional
ones are not thoroughly tested and come with new risks that are still under research. The
principal chances of adopting cloud computing identified by the authors Tosh et al. (2017)
are as follows:
Not understanding the responsibility of an individual: If in a traditional scenario, the
security of data is entirely the burden of the company owning data. In the cloud computing
scenario, the responsibilities are divided between the two actors: the cloud provider and the
client. There is a tremendous potential for misguided risk management decisions if cloud
providers do not disclose the extent to which the security controls are implemented. The
consumer knows which controls are further needed to be adopted into the Cloud environment.
Different kinds of cloud services utilized mean different responsibilities for the service
provider and the customer. If an Infrastructure as a service (IaaS) service model is approved,
a particular job but also encourages all kinds of applications in the cloud nowadays, like
CRM, accounting, HR, and custom-built applications. Over, upgrades are periodically
completed by cloud providers to facilitate new features, security, and performance
enhancements automatically. Cloud technology follows a pay-as-you-go model. Finally,
cloud applications and adaptation of Cloud technology, does not consume up the valuable IT
resources of any company. And adopting Cloud, allows the customer to focus on deploying
more applications, new projects, and innovation. Cloud computing is a modest idea, but it can
have a considerable impact on any business.
2.6 Security issues regarding cloud technology
However, there are various security constraints regarding the adoption of cloud
implementations in the business industries as well. The process of creating and managing a
secure cloud space is a more challenging task than creating a safe classical IT environment.
Given the immaturity of this technology, the new resources and the reallocation of traditional
ones are not thoroughly tested and come with new risks that are still under research. The
principal chances of adopting cloud computing identified by the authors Tosh et al. (2017)
are as follows:
Not understanding the responsibility of an individual: If in a traditional scenario, the
security of data is entirely the burden of the company owning data. In the cloud computing
scenario, the responsibilities are divided between the two actors: the cloud provider and the
client. There is a tremendous potential for misguided risk management decisions if cloud
providers do not disclose the extent to which the security controls are implemented. The
consumer knows which controls are further needed to be adopted into the Cloud environment.
Different kinds of cloud services utilized mean different responsibilities for the service
provider and the customer. If an Infrastructure as a service (IaaS) service model is approved,

14RESEARCH PAPER
then the provider is responsible for physical security, environment security and the
virtualisation software security. In this case, the consumer is responsible for securing
everything else above this layer including operating system, applications and data (Brundo
and Nicola 2018). However, in a SaaS cloud service model, the provider is responsible not
only for the physical and environmental security but also for all the software services he uses
to provide that particular software service to the client. In this case, the responsibilities of the
consumer in the field of security are much lowered.
Data security and confidentiality issues: One of the biggest security concerns people
have when moving to the cloud is related to the problem of keeping data. In this respect,
some particular issues arise who can create data, where the data is stored, who can access and
modify data, what happens when information is deleted, how the back-up is done, how the
data transfer occurs and others. This lifecycle also exists in the classic architecture, but in a
cloud environment, its stages are much more complex, posing higher security risks and
requiring more careful management (Liang et al. 2017). Worth reminding in this respect is
that it is much more difficult for the cloud customer to effectively check the data handling
practices of the cloud provider and thus be sure that the data is appropriately handled. To
counter such a risk, strategies like data encryption, particularly public key infrastructure, data
dispersion, standardisation of APIs and others are proposed to customers as security measures
to create a trusted and secure environment.
Not understanding the maturity of Standards: The immaturity of this technology
makes it challenging to develop a comprehensive and commonly accepted set of standards.
As a result, many standard development organisations were established to research and
develop the specifications. Organisations like Cloud Security Alliance, European Network
and Information Security Agency, Cloud Standards Customer Council, etc. have developed
then the provider is responsible for physical security, environment security and the
virtualisation software security. In this case, the consumer is responsible for securing
everything else above this layer including operating system, applications and data (Brundo
and Nicola 2018). However, in a SaaS cloud service model, the provider is responsible not
only for the physical and environmental security but also for all the software services he uses
to provide that particular software service to the client. In this case, the responsibilities of the
consumer in the field of security are much lowered.
Data security and confidentiality issues: One of the biggest security concerns people
have when moving to the cloud is related to the problem of keeping data. In this respect,
some particular issues arise who can create data, where the data is stored, who can access and
modify data, what happens when information is deleted, how the back-up is done, how the
data transfer occurs and others. This lifecycle also exists in the classic architecture, but in a
cloud environment, its stages are much more complex, posing higher security risks and
requiring more careful management (Liang et al. 2017). Worth reminding in this respect is
that it is much more difficult for the cloud customer to effectively check the data handling
practices of the cloud provider and thus be sure that the data is appropriately handled. To
counter such a risk, strategies like data encryption, particularly public key infrastructure, data
dispersion, standardisation of APIs and others are proposed to customers as security measures
to create a trusted and secure environment.
Not understanding the maturity of Standards: The immaturity of this technology
makes it challenging to develop a comprehensive and commonly accepted set of standards.
As a result, many standard development organisations were established to research and
develop the specifications. Organisations like Cloud Security Alliance, European Network
and Information Security Agency, Cloud Standards Customer Council, etc. have developed

15RESEARCH PAPER
best practices regulations and recommendations. Other establishments, like Distributed
Management Task Force, The European Telecommunications Standards Institute, Open Grid
Forum, Open Cloud Consortium, National Institute of Standards and Technology, Storage
Networking Industry Association and others have centred their activity on the development of
working standards for different aspects of the cloud technology. The excitement around the
cloud has created a standard and open source activity leading to market confusion. That is
why certain working groups like Cloud Standards Coordination, TM Forum and other acts to
improve collaboration, coordination, information and resource sharing between the
organisations acting in this research field.
Interoperability issues: Cloud computing technology offers a degree of resource
scalability, which has never been reached before. Companies can benefit from additional
computational needs, storage space, bandwidth allocation, etc. whenever they need and
without great investments to support peak demands. If the application falls back, the
additional capacity can be shut down just as quickly as it was scaled up without any hardware
equipment sitting idle. This great advantage also has a significant drawback. It comes
alongside the risk of managing data within a shared environment, including computation,
storage, and network with other cloud clients.
Additionally, at one time, one company may have multiple cloud providers for
different services which have to be interoperable. In time, for various reasons, companies
may decide to move their services to another cloud, and in such a case, the lack of
interoperability can block or raise substantial obstacles to such a process. Cloud providers
may find the customer lock-in system attractive, but for the customers, interoperability issues
mean that they are vulnerable to price increases and quality of services not meeting their
best practices regulations and recommendations. Other establishments, like Distributed
Management Task Force, The European Telecommunications Standards Institute, Open Grid
Forum, Open Cloud Consortium, National Institute of Standards and Technology, Storage
Networking Industry Association and others have centred their activity on the development of
working standards for different aspects of the cloud technology. The excitement around the
cloud has created a standard and open source activity leading to market confusion. That is
why certain working groups like Cloud Standards Coordination, TM Forum and other acts to
improve collaboration, coordination, information and resource sharing between the
organisations acting in this research field.
Interoperability issues: Cloud computing technology offers a degree of resource
scalability, which has never been reached before. Companies can benefit from additional
computational needs, storage space, bandwidth allocation, etc. whenever they need and
without great investments to support peak demands. If the application falls back, the
additional capacity can be shut down just as quickly as it was scaled up without any hardware
equipment sitting idle. This great advantage also has a significant drawback. It comes
alongside the risk of managing data within a shared environment, including computation,
storage, and network with other cloud clients.
Additionally, at one time, one company may have multiple cloud providers for
different services which have to be interoperable. In time, for various reasons, companies
may decide to move their services to another cloud, and in such a case, the lack of
interoperability can block or raise substantial obstacles to such a process. Cloud providers
may find the customer lock-in system attractive, but for the customers, interoperability issues
mean that they are vulnerable to price increases and quality of services not meeting their
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16RESEARCH PAPER
needs. The other issues are closure of one or more cloud services, provider going out of
business and disputes between with the cloud provider.
2.7 Cloud ERP Blockchain solution to provide services to the customers
Davidson, De Filippi and Potts (2016) stated that Cloud Enterprise Resource Planning
solutions are to be provided via the software as service model (SaaS) for overcoming with the
Blockchain issues and providing better services to the customers. It has capability to connect
with the business application such as ERP. Usage of the ERP system in the industry is being
increasing over the time. In order to provide effective services to customers, ERP services are
offering with entire suite of the applications into the cloud as cloud ERP system. Mills et al.
(2016) discussed that cloud ERP is faster as well as lower expensive as the users are not
willing to reduce from traditional ERP system to cloud based. Concept of distributed ledger
technology is used in this literature study which is implemented in cloud ERP to provide data
security, data ownership, transparency and encryption. As a solution, cloud based ERP is
focused on latest trend of blockchain termed as distributed ledger technology.
Singh and Lee (2017) discussed that Blockchain is an element into bundle of
Blockchain technologies is determined as value transfer technology. It is a technology which
is used for transferring digital money from one individual to other. In origins of
cryptocurrency, it is a form of the digital money and Blockchain technology is about
recordkeeping. The synthesis of this literature study is based on supposition that it is
recordkeeping technology focused on its nature. Dorri, Kanhere and Jurdak (2016) pointed
that recordkeeping system is set of rules governed storage, usage and maintain of records and
information used to implement rules. Ledger entry records the financial transactions and
accounting records while distributed ledger records transactions by qualifying new types of
financial records. The new digital ledgers for economical transactions are programmed to
needs. The other issues are closure of one or more cloud services, provider going out of
business and disputes between with the cloud provider.
2.7 Cloud ERP Blockchain solution to provide services to the customers
Davidson, De Filippi and Potts (2016) stated that Cloud Enterprise Resource Planning
solutions are to be provided via the software as service model (SaaS) for overcoming with the
Blockchain issues and providing better services to the customers. It has capability to connect
with the business application such as ERP. Usage of the ERP system in the industry is being
increasing over the time. In order to provide effective services to customers, ERP services are
offering with entire suite of the applications into the cloud as cloud ERP system. Mills et al.
(2016) discussed that cloud ERP is faster as well as lower expensive as the users are not
willing to reduce from traditional ERP system to cloud based. Concept of distributed ledger
technology is used in this literature study which is implemented in cloud ERP to provide data
security, data ownership, transparency and encryption. As a solution, cloud based ERP is
focused on latest trend of blockchain termed as distributed ledger technology.
Singh and Lee (2017) discussed that Blockchain is an element into bundle of
Blockchain technologies is determined as value transfer technology. It is a technology which
is used for transferring digital money from one individual to other. In origins of
cryptocurrency, it is a form of the digital money and Blockchain technology is about
recordkeeping. The synthesis of this literature study is based on supposition that it is
recordkeeping technology focused on its nature. Dorri, Kanhere and Jurdak (2016) pointed
that recordkeeping system is set of rules governed storage, usage and maintain of records and
information used to implement rules. Ledger entry records the financial transactions and
accounting records while distributed ledger records transactions by qualifying new types of
financial records. The new digital ledgers for economical transactions are programmed to

17RESEARCH PAPER
record each thing of value as well as consequence to humankind such as financial accounts,
insurance claims and others.
The author Uchibayashi et al. (2018) identified that the Blockchain technology
involvement helps businesses in keeping a timestamp that makes a business organisation
make a proof of the digitised assets that is in existence. The researchers believe that it has the
potential of becoming the latest development in the field of business and industry. There is
hardly any existence of digital assets or digitised assets right at the moment where there are
higher chances of attaining a competitive advantage over the others. This is where the authors
Jiao et al. 2018 stated that there are possibilities that the technology of Blockchain when
involved in the business organisations is a considerable advantage added to it. There is a
possibility of creating the unique identity specified of the artefacts and assets where there are
other ways by which the duplication of these assets can be minimised.
2.8 A gap in the Literature
Following the proper methodology for reviewing the literature, it has been found that
the existing pieces of writing that have been presented by the researchers and the analysts
have all focused on the probable ways of finding out the security vulnerabilities in the
Blockchain technology (Tosh et al. 2017). They have figured out the security vulnerabilities
associated with the technology and the ways by which the transaction system and the
financial scenario in business organisations can be affected by changing the customers’
demands. However, all of the literature reviewed has focused on finding some of the
vulnerabilities but have not focused on the exact impact and ways to find a solution for
eliminating them. After the thorough research process, this had been the gap in the literature
found, which should further be researched on through the research process. The exact impact
of the issues regarding cloud implementation and the cloud issues need to be identified
record each thing of value as well as consequence to humankind such as financial accounts,
insurance claims and others.
The author Uchibayashi et al. (2018) identified that the Blockchain technology
involvement helps businesses in keeping a timestamp that makes a business organisation
make a proof of the digitised assets that is in existence. The researchers believe that it has the
potential of becoming the latest development in the field of business and industry. There is
hardly any existence of digital assets or digitised assets right at the moment where there are
higher chances of attaining a competitive advantage over the others. This is where the authors
Jiao et al. 2018 stated that there are possibilities that the technology of Blockchain when
involved in the business organisations is a considerable advantage added to it. There is a
possibility of creating the unique identity specified of the artefacts and assets where there are
other ways by which the duplication of these assets can be minimised.
2.8 A gap in the Literature
Following the proper methodology for reviewing the literature, it has been found that
the existing pieces of writing that have been presented by the researchers and the analysts
have all focused on the probable ways of finding out the security vulnerabilities in the
Blockchain technology (Tosh et al. 2017). They have figured out the security vulnerabilities
associated with the technology and the ways by which the transaction system and the
financial scenario in business organisations can be affected by changing the customers’
demands. However, all of the literature reviewed has focused on finding some of the
vulnerabilities but have not focused on the exact impact and ways to find a solution for
eliminating them. After the thorough research process, this had been the gap in the literature
found, which should further be researched on through the research process. The exact impact
of the issues regarding cloud implementation and the cloud issues need to be identified

18RESEARCH PAPER
through the following research as the crust of this particular thesis. In addition to that, the
business services and way of enhancement removing some of the vulnerabilities need to be
additionally found out through the research process since they are not found in the reviewed
articles.
2.9 Summary
It is summarized that the Blockchain technology is done with the server for excluding the
involvement of central authority as well as facilitating transactions to store the records in a
secured place. This technology has distributed structures and utilized peer network as well as
computing resources for the peers. The security over the Blockchain is enhanced, problems
are continued to report as well as there are studies on the security. The attacker is taken
different attempts to access the personal key of the users stored into user's computers for
hacking the bitcoin. There are various studies which are based on the secured token in order
to protect the personal key. In this research study, different types of issues are also analyzed
for using Blockchain technology into cloud computing.
through the following research as the crust of this particular thesis. In addition to that, the
business services and way of enhancement removing some of the vulnerabilities need to be
additionally found out through the research process since they are not found in the reviewed
articles.
2.9 Summary
It is summarized that the Blockchain technology is done with the server for excluding the
involvement of central authority as well as facilitating transactions to store the records in a
secured place. This technology has distributed structures and utilized peer network as well as
computing resources for the peers. The security over the Blockchain is enhanced, problems
are continued to report as well as there are studies on the security. The attacker is taken
different attempts to access the personal key of the users stored into user's computers for
hacking the bitcoin. There are various studies which are based on the secured token in order
to protect the personal key. In this research study, different types of issues are also analyzed
for using Blockchain technology into cloud computing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19RESEARCH PAPER
Chapter 3: Proposed methodology
3.1 Introduction
This chapter is addressing the data gathering and the process that is utilized to conduct
the study process as well as for addressing the questions that are research-related and for
triangulating the data collected from the literature review. There exist several methods for the
approaches of the research and the concepts that can be used for making sure that the right
methods have been used for understanding the topic that is selected for the research. The
theories are related to the research and the concepts are adopted into that methodology that
can help for deeper and better understanding of the topic that is selected for the research. In
addition, the researcher tried to apply the procedure in detail that helps for better study on the
performance of the business.
3.2 Research philosophy
In this research methodology, the philosophy of the research is assistance for
determining the proper path and for analysing the topic that is selected for the research. It
helps to explain the assumptions that have been taken for conducting the study. Two types of
research philosophy are there; they are interpretivism and positivism. The interpretivism is
supported by the concept that is related to the structure that is complex and involved in the
social network for the activities that are business related (Bresler and Stake 2017). The
positivism is subjected to helping for analysing the hidden facts that are related to the topic of
the research.
In this study for evaluating the factors that are significance, impacting of Blockchain
technology in cloud computing in the performance of the business, the researcher selected of
the positivism as the philosophy of research. It is allowed by the positivism the researchers
Chapter 3: Proposed methodology
3.1 Introduction
This chapter is addressing the data gathering and the process that is utilized to conduct
the study process as well as for addressing the questions that are research-related and for
triangulating the data collected from the literature review. There exist several methods for the
approaches of the research and the concepts that can be used for making sure that the right
methods have been used for understanding the topic that is selected for the research. The
theories are related to the research and the concepts are adopted into that methodology that
can help for deeper and better understanding of the topic that is selected for the research. In
addition, the researcher tried to apply the procedure in detail that helps for better study on the
performance of the business.
3.2 Research philosophy
In this research methodology, the philosophy of the research is assistance for
determining the proper path and for analysing the topic that is selected for the research. It
helps to explain the assumptions that have been taken for conducting the study. Two types of
research philosophy are there; they are interpretivism and positivism. The interpretivism is
supported by the concept that is related to the structure that is complex and involved in the
social network for the activities that are business related (Bresler and Stake 2017). The
positivism is subjected to helping for analysing the hidden facts that are related to the topic of
the research.
In this study for evaluating the factors that are significance, impacting of Blockchain
technology in cloud computing in the performance of the business, the researcher selected of
the positivism as the philosophy of research. It is allowed by the positivism the researchers

20RESEARCH PAPER
can reveal the data that are hidden that are related to the procedure of record storage in the
business organization. For a limited time, some philosophies of the research have not been
utilized as well as those that have been eliminated from the considerations. The method that
is selected is not easily available; it is restricted to the study related activities for the
interpretation of the data.
3.3 Research approach
In this specific area, distinctive existing approaches for the study are being utilized to
choose a reasonable methodology for this research approach. There are two kinds of research
related approach, for example, deductive and inductive methodology. The deductive
approach will be worked from the topic that is wide for a particular topic that is aimed for
testing the theory that is aimed as well as this is required for providing the hypothesis that is
mentioned to provide the assumptions for the research. The researchers have been enabled for
the particular approach for resolving the issues by collecting several types of data and
information for confirming the theory that is rejected. The deductive approach will be suited
into the related scientific research which is required for the proper hypothesis testing as the
explanation as well as the description of it.
3.4 Research design
As indicated by Flick (2015), the research design is helped for developing the
required system to gather and analysis of information. Utilization of research design can help
to reveal the pattern as information sources that are required for finishing the study. The
information collection processes other than study strategies are required for directing the
study in a manner that is in detail. There is also existed of three kinds of research design, as
explanatory, exploratory as well as Descriptive. The exploratory design has enabled the
can reveal the data that are hidden that are related to the procedure of record storage in the
business organization. For a limited time, some philosophies of the research have not been
utilized as well as those that have been eliminated from the considerations. The method that
is selected is not easily available; it is restricted to the study related activities for the
interpretation of the data.
3.3 Research approach
In this specific area, distinctive existing approaches for the study are being utilized to
choose a reasonable methodology for this research approach. There are two kinds of research
related approach, for example, deductive and inductive methodology. The deductive
approach will be worked from the topic that is wide for a particular topic that is aimed for
testing the theory that is aimed as well as this is required for providing the hypothesis that is
mentioned to provide the assumptions for the research. The researchers have been enabled for
the particular approach for resolving the issues by collecting several types of data and
information for confirming the theory that is rejected. The deductive approach will be suited
into the related scientific research which is required for the proper hypothesis testing as the
explanation as well as the description of it.
3.4 Research design
As indicated by Flick (2015), the research design is helped for developing the
required system to gather and analysis of information. Utilization of research design can help
to reveal the pattern as information sources that are required for finishing the study. The
information collection processes other than study strategies are required for directing the
study in a manner that is in detail. There is also existed of three kinds of research design, as
explanatory, exploratory as well as Descriptive. The exploratory design has enabled the

21RESEARCH PAPER
researchers to characterize the required information to lead the study. An explanatory design
is expected to characterize the incidents that have happened in regard to time and impact. The
Descriptive plan is given of depiction of the events that are happened while represented the
research timeline alongside the effect of the chosen topic.
As this specific research study about is crossly sectional, thusly explanatory research
design is mostly appropriated with the chosen research topic. Descriptive design is chosen as
it depends on the assessment of key components impact of Blockchain technology in cloud
computing in business. This research design is suited, as the researchers cannot portray of
procedures that are followed into the Blockchain in the cloud computing in business.
3.5 Data collection and analysis
While directing a study in chosen research, the information has been being accounted
for as significant data that are required for the study. Valuable data and information are given
insight into the attempted topic in a comprehensive way (Flick 2015). As indicated by
Ledford and Gast (2018), application of proper as well as the detailed information is
important to this specific study, which helped to deliver of the accuracy of information
analysis alongside maintaining the standard for the research.
3.5.1 Data collection methods
The identification of proper data collection methods is so much critical for conducting
the analysis of data with the interpretation of the information. Excavation of proper
information sources in the study gives of appropriate data, which is applicable to the research
study. On the basis of the data collection methods, there are existed two kinds of data
collection methods, secondary and primary data collection methods. Mackey and Gass (2015)
characterized the primary data collection method as the accumulation of the first time that is
researchers to characterize the required information to lead the study. An explanatory design
is expected to characterize the incidents that have happened in regard to time and impact. The
Descriptive plan is given of depiction of the events that are happened while represented the
research timeline alongside the effect of the chosen topic.
As this specific research study about is crossly sectional, thusly explanatory research
design is mostly appropriated with the chosen research topic. Descriptive design is chosen as
it depends on the assessment of key components impact of Blockchain technology in cloud
computing in business. This research design is suited, as the researchers cannot portray of
procedures that are followed into the Blockchain in the cloud computing in business.
3.5 Data collection and analysis
While directing a study in chosen research, the information has been being accounted
for as significant data that are required for the study. Valuable data and information are given
insight into the attempted topic in a comprehensive way (Flick 2015). As indicated by
Ledford and Gast (2018), application of proper as well as the detailed information is
important to this specific study, which helped to deliver of the accuracy of information
analysis alongside maintaining the standard for the research.
3.5.1 Data collection methods
The identification of proper data collection methods is so much critical for conducting
the analysis of data with the interpretation of the information. Excavation of proper
information sources in the study gives of appropriate data, which is applicable to the research
study. On the basis of the data collection methods, there are existed two kinds of data
collection methods, secondary and primary data collection methods. Mackey and Gass (2015)
characterized the primary data collection method as the accumulation of the first time that is
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22RESEARCH PAPER
all over the study. The primary information is the raw information that helps to investigate as
the requirement of the research. The raw information gives of point-by-point understanding
data identified with the chosen research topic. The raw information is utilized as the method
for the research, which is expected of legitimate validation of information sources regarding
validity and reliability. The secondary information ate those that are gathered and assembled
by other people.
In this specific study, primary data collection method is utilized, which recognizes for
identifying of the impact of Blockchain in cloud computing for business execution. The
information is gathered through the utilization of a survey and online questionnaire
responses. Lot of open ended questions are prepared based on the chosen research topic.
There is an acknowledgement of effect of the Blockchain technology on cloud computing in
business (Alvesson, and Sköldberg 2017). For the gathering of data, the analyst assessed of
the feedback from the respondents as well as the questions have been considered for
extracting of delicate data dependent on the selected research related topic.
3.5.2 Data analysis methods
In this specific study, the researchers are utilized of quantitative and qualitative data
analysis to confer at the research findings. Silverman (2016) perceived that there are some
confinements of a research method that is remunerated by the quality of different strategies.
The study is focused on the fact that there is a mix of both qualitative and quantitative
strategy that is useful for a research plan to get reliable research findings. The employees are
selected for getting quantitative information from various business industries. The selected
industries are banking, IT, retail and manufacturing by means of utilization of study survey
strategy. This data analysis method is utilized to triangulate essential research to add evidence
to the literature study. There is a mix of deductive and inductive strategy for the research.
all over the study. The primary information is the raw information that helps to investigate as
the requirement of the research. The raw information gives of point-by-point understanding
data identified with the chosen research topic. The raw information is utilized as the method
for the research, which is expected of legitimate validation of information sources regarding
validity and reliability. The secondary information ate those that are gathered and assembled
by other people.
In this specific study, primary data collection method is utilized, which recognizes for
identifying of the impact of Blockchain in cloud computing for business execution. The
information is gathered through the utilization of a survey and online questionnaire
responses. Lot of open ended questions are prepared based on the chosen research topic.
There is an acknowledgement of effect of the Blockchain technology on cloud computing in
business (Alvesson, and Sköldberg 2017). For the gathering of data, the analyst assessed of
the feedback from the respondents as well as the questions have been considered for
extracting of delicate data dependent on the selected research related topic.
3.5.2 Data analysis methods
In this specific study, the researchers are utilized of quantitative and qualitative data
analysis to confer at the research findings. Silverman (2016) perceived that there are some
confinements of a research method that is remunerated by the quality of different strategies.
The study is focused on the fact that there is a mix of both qualitative and quantitative
strategy that is useful for a research plan to get reliable research findings. The employees are
selected for getting quantitative information from various business industries. The selected
industries are banking, IT, retail and manufacturing by means of utilization of study survey
strategy. This data analysis method is utilized to triangulate essential research to add evidence
to the literature study. There is a mix of deductive and inductive strategy for the research.

23RESEARCH PAPER
Quantitative information is being collected from the question in the form of diagrams and
charts.
In this specific study, quantitative data analysis is being utilized where the researchers
have taken employees of four selected industries as well as it takes their responses through
the strategy for online survey. The result of this data analysis method is to assess the
commitment of the representatives to give their input on impact of Blockchain technology on
cloud computing in business. This specific technique enabled the researchers to get numerical
information that is interpreted to show into a graphical configuration, which displays the
patterns and the triangulation.
3.6 Population and sample
As said by Kumar (2019) in this research method, the population is the number of
individuals those are legitimately and by implication required into the research process. The
employees of four selected industries of Bahrain have been utilized of re-appropriating for
selected topic that has been considered as the population of this study. Taylor, Bogdan and
DeVault (2015) examined that example is considered for contemplate the effect of
Blockchain technology on cloud computing in business. The employees of the industries that
has been taken where the overview is being performed by the impression that is reflected of
them dependent on 1 = Strongly Disagree, 2= Disagree, 3=Neutral, 4=Agree and 5=Strongly
Agree. So as to direct quantitative research methods, 50 employees have been considered and
interacted with the assistance of the online survey forms. In this way, the sample size of the
study is 50.
Quantitative information is being collected from the question in the form of diagrams and
charts.
In this specific study, quantitative data analysis is being utilized where the researchers
have taken employees of four selected industries as well as it takes their responses through
the strategy for online survey. The result of this data analysis method is to assess the
commitment of the representatives to give their input on impact of Blockchain technology on
cloud computing in business. This specific technique enabled the researchers to get numerical
information that is interpreted to show into a graphical configuration, which displays the
patterns and the triangulation.
3.6 Population and sample
As said by Kumar (2019) in this research method, the population is the number of
individuals those are legitimately and by implication required into the research process. The
employees of four selected industries of Bahrain have been utilized of re-appropriating for
selected topic that has been considered as the population of this study. Taylor, Bogdan and
DeVault (2015) examined that example is considered for contemplate the effect of
Blockchain technology on cloud computing in business. The employees of the industries that
has been taken where the overview is being performed by the impression that is reflected of
them dependent on 1 = Strongly Disagree, 2= Disagree, 3=Neutral, 4=Agree and 5=Strongly
Agree. So as to direct quantitative research methods, 50 employees have been considered and
interacted with the assistance of the online survey forms. In this way, the sample size of the
study is 50.

24RESEARCH PAPER
3.7 Ethical consideration
Leading of the ethical research is standard with the rights of the human acted that is
specific for esteeming for the correspondence. The respondents are given their reactions
dependent on gave survey poll are given alternatives to uncover and right for answering as
well as not to answer in entire and part the questions. The right not to answer the survey
depends on their opinions and contemplations. As the study is directed with the gathering of
organisational information and data, in this way, it is managed about the privacy of that
information, and it is not published openly.
3.8 Research limitations
The research study helps for gaining the results that are identified with the concerned
research topic is permitted to the experience of avoidable and the unavoidable within nature.
Effect of research limitations decreased with the use of various research strategies and
procedures. There are different research limitations, which are recognized as follows:
Time constraint: There is an unmistakable time is assigned for leading the exploration
to think about which give sway on the re-appropriating pursued into the selected firms.
Because of the limitation of time, the analyst is directed of the cross-sectional study, which
restricted the creator to lead off the itemized study and assess various hidden details that are
related to the topic. Because of the restriction of time, the analyst has led the essential
information accumulation in selected industries only.
Reliability: Raw information is to be gathered from the employees in a type of
overview that is needed to check for legitimacy and reliability. The respondents depend on
the association while giving their input, which affects this research study outcomes. In order
3.7 Ethical consideration
Leading of the ethical research is standard with the rights of the human acted that is
specific for esteeming for the correspondence. The respondents are given their reactions
dependent on gave survey poll are given alternatives to uncover and right for answering as
well as not to answer in entire and part the questions. The right not to answer the survey
depends on their opinions and contemplations. As the study is directed with the gathering of
organisational information and data, in this way, it is managed about the privacy of that
information, and it is not published openly.
3.8 Research limitations
The research study helps for gaining the results that are identified with the concerned
research topic is permitted to the experience of avoidable and the unavoidable within nature.
Effect of research limitations decreased with the use of various research strategies and
procedures. There are different research limitations, which are recognized as follows:
Time constraint: There is an unmistakable time is assigned for leading the exploration
to think about which give sway on the re-appropriating pursued into the selected firms.
Because of the limitation of time, the analyst is directed of the cross-sectional study, which
restricted the creator to lead off the itemized study and assess various hidden details that are
related to the topic. Because of the restriction of time, the analyst has led the essential
information accumulation in selected industries only.
Reliability: Raw information is to be gathered from the employees in a type of
overview that is needed to check for legitimacy and reliability. The respondents depend on
the association while giving their input, which affects this research study outcomes. In order
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25RESEARCH PAPER
to gather information for the study, the employees are utilized for essential information
accumulation.
Lack of budget: This study is furnished with a constrained budget which limited the
degree and the nature of this specific study. With a budget, the specialist has comprised of the
restricted time to think about the idea of the association and recognize the variables related to
impact of Blockchain technology on cloud computing in business. The researcher has
confined to SPSS study because of lack of budget.
3.9 Summary
Throughout the strategy, the researcher has the ability to identifying the research
methods in proper that are utilized for analysing the research topic that is selected. The
researcher aligned with study nature as well as the framed that is based on the techniques that
are selected for evaluating it. Proper methods and techniques have been utilized for the
research study for providing the standard that is required for developing the entire research.
to gather information for the study, the employees are utilized for essential information
accumulation.
Lack of budget: This study is furnished with a constrained budget which limited the
degree and the nature of this specific study. With a budget, the specialist has comprised of the
restricted time to think about the idea of the association and recognize the variables related to
impact of Blockchain technology on cloud computing in business. The researcher has
confined to SPSS study because of lack of budget.
3.9 Summary
Throughout the strategy, the researcher has the ability to identifying the research
methods in proper that are utilized for analysing the research topic that is selected. The
researcher aligned with study nature as well as the framed that is based on the techniques that
are selected for evaluating it. Proper methods and techniques have been utilized for the
research study for providing the standard that is required for developing the entire research.

26RESEARCH PAPER
Chapter 4: Data Analysis and Findings
4.1 Introduction
In this particular chapter, the researcher is required to show the data analysis of the
impact of Blockchain in cloud computing from a business perspective. By means of the
quantitative data analysis, data analysis will help the researcher as a part of the research
process to raise the quality of the collected information as well as make a better analysis of
the research topic. The data analysis will help the researcher to implement theoretical skills as
well as knowledge into the statistical form. The data analysis is involved with complexities as
well as limitations with manipulation of the data. Impact of the Blockchain technology on
cloud computing from a business perspective is evaluated by means of taking survey
responses from the participants. The researcher tried to analyse research findings based on
adding validity to the data collection processes.
4.2 Quantitative Data Analysis
In this section, the employees of various business organisations are taken into
considerations for performing the quantitative data analysis such that the researcher can able
to become familiar with the impact of the Blockchain technology on cloud computing from a
business perspective. The total number of respondents selected for this research study is 50 as
other employees are not interested in filling the survey, and therefore, they are being
discarded from the entire research study.
Chapter 4: Data Analysis and Findings
4.1 Introduction
In this particular chapter, the researcher is required to show the data analysis of the
impact of Blockchain in cloud computing from a business perspective. By means of the
quantitative data analysis, data analysis will help the researcher as a part of the research
process to raise the quality of the collected information as well as make a better analysis of
the research topic. The data analysis will help the researcher to implement theoretical skills as
well as knowledge into the statistical form. The data analysis is involved with complexities as
well as limitations with manipulation of the data. Impact of the Blockchain technology on
cloud computing from a business perspective is evaluated by means of taking survey
responses from the participants. The researcher tried to analyse research findings based on
adding validity to the data collection processes.
4.2 Quantitative Data Analysis
In this section, the employees of various business organisations are taken into
considerations for performing the quantitative data analysis such that the researcher can able
to become familiar with the impact of the Blockchain technology on cloud computing from a
business perspective. The total number of respondents selected for this research study is 50 as
other employees are not interested in filling the survey, and therefore, they are being
discarded from the entire research study.
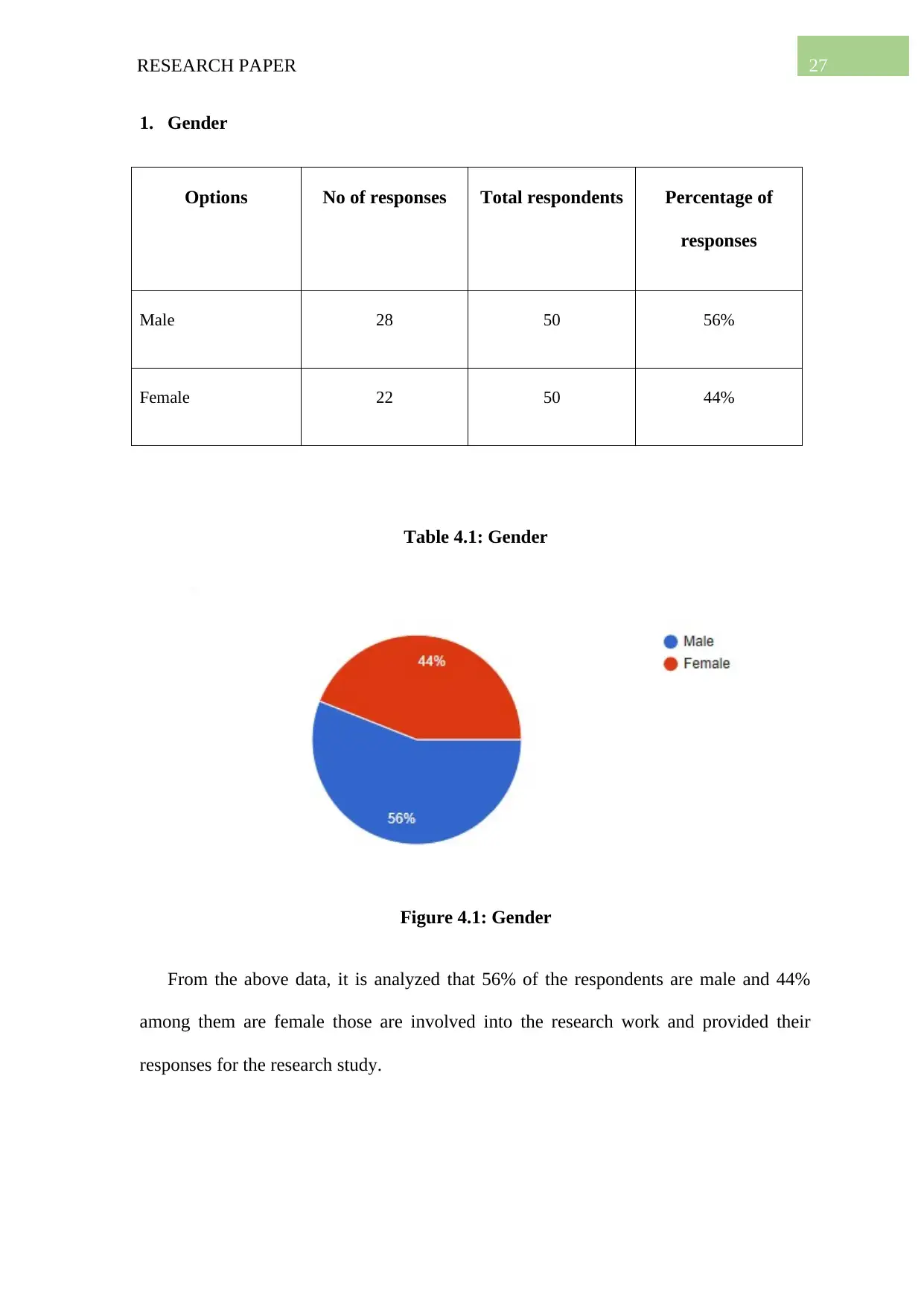
27RESEARCH PAPER
1. Gender
Options No of responses Total respondents Percentage of
responses
Male 28 50 56%
Female 22 50 44%
Table 4.1: Gender
Figure 4.1: Gender
From the above data, it is analyzed that 56% of the respondents are male and 44%
among them are female those are involved into the research work and provided their
responses for the research study.
1. Gender
Options No of responses Total respondents Percentage of
responses
Male 28 50 56%
Female 22 50 44%
Table 4.1: Gender
Figure 4.1: Gender
From the above data, it is analyzed that 56% of the respondents are male and 44%
among them are female those are involved into the research work and provided their
responses for the research study.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

28RESEARCH PAPER
2. Age group
Options No of responses Total respondents Percentage of
responses
24-29 years 20 50 40%
30-39 years 13 50 26%
40-49 years 13 50 26%
Above 50 years 4 50 8%
Table 4.2: Age group
Figure4.2: Age group
2. Age group
Options No of responses Total respondents Percentage of
responses
24-29 years 20 50 40%
30-39 years 13 50 26%
40-49 years 13 50 26%
Above 50 years 4 50 8%
Table 4.2: Age group
Figure4.2: Age group

29RESEARCH PAPER
From the above data, it is analyzed that 40% of the respondents are age group
between 24-29 years, 26% of them are between 30-39 years, 26% of them are between
40-49 years and 8% of them are above 50 years.
3. Please mention your workplace position
Options No of responses Total respondents Percentage of responses
Chief Executive
Officer
8 50 16%
Chief Operation
Officer
4 50 8%
Financial Officer 10 50 20%
Senior Manager 11 50 22%
Strategy Officer 11 50 22%
Business unit head 6 50 12%
Table 4.3: Position in the workplace
From the above data, it is analyzed that 40% of the respondents are age group
between 24-29 years, 26% of them are between 30-39 years, 26% of them are between
40-49 years and 8% of them are above 50 years.
3. Please mention your workplace position
Options No of responses Total respondents Percentage of responses
Chief Executive
Officer
8 50 16%
Chief Operation
Officer
4 50 8%
Financial Officer 10 50 20%
Senior Manager 11 50 22%
Strategy Officer 11 50 22%
Business unit head 6 50 12%
Table 4.3: Position in the workplace
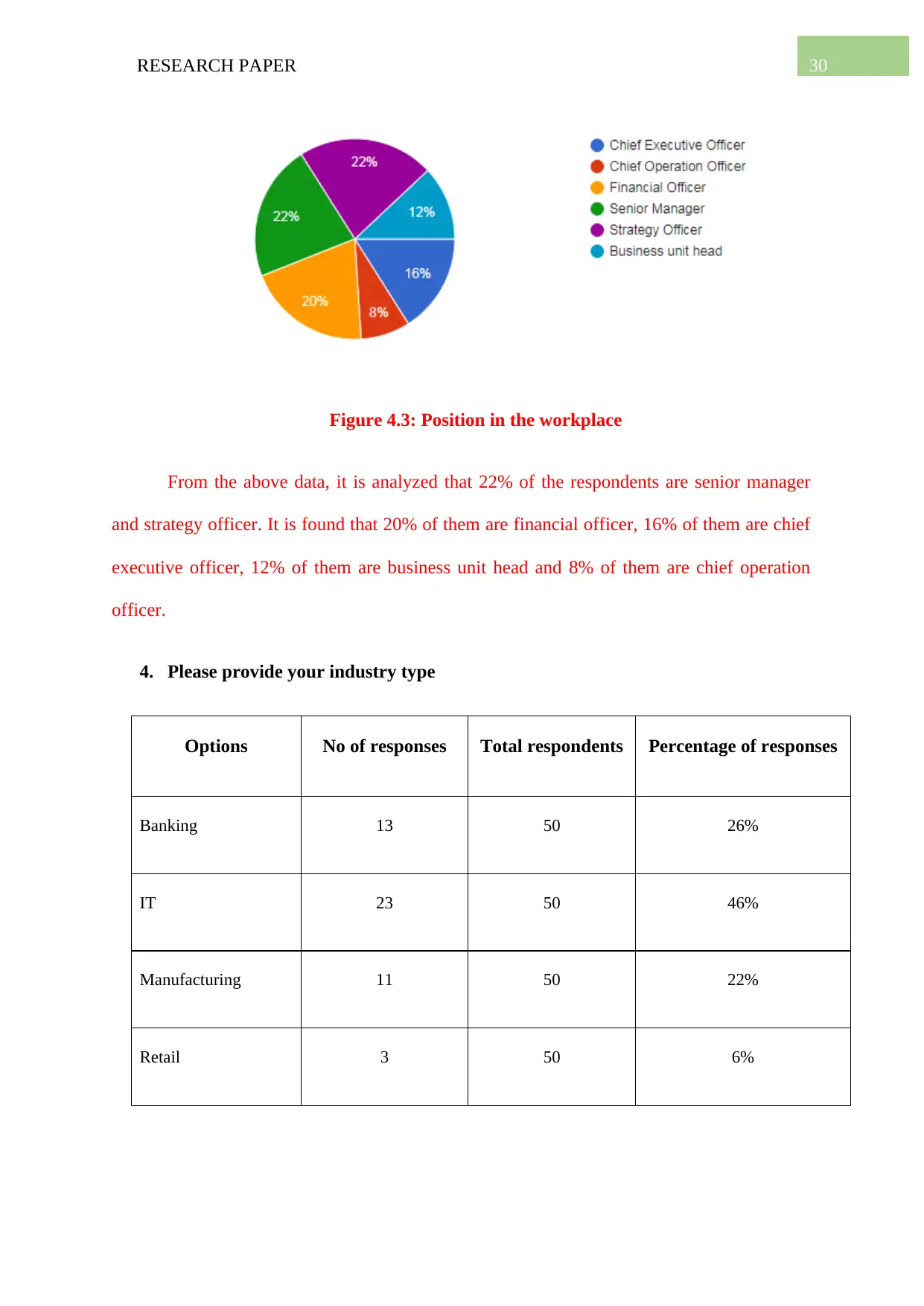
30RESEARCH PAPER
Figure 4.3: Position in the workplace
From the above data, it is analyzed that 22% of the respondents are senior manager
and strategy officer. It is found that 20% of them are financial officer, 16% of them are chief
executive officer, 12% of them are business unit head and 8% of them are chief operation
officer.
4. Please provide your industry type
Options No of responses Total respondents Percentage of responses
Banking 13 50 26%
IT 23 50 46%
Manufacturing 11 50 22%
Retail 3 50 6%
Figure 4.3: Position in the workplace
From the above data, it is analyzed that 22% of the respondents are senior manager
and strategy officer. It is found that 20% of them are financial officer, 16% of them are chief
executive officer, 12% of them are business unit head and 8% of them are chief operation
officer.
4. Please provide your industry type
Options No of responses Total respondents Percentage of responses
Banking 13 50 26%
IT 23 50 46%
Manufacturing 11 50 22%
Retail 3 50 6%
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
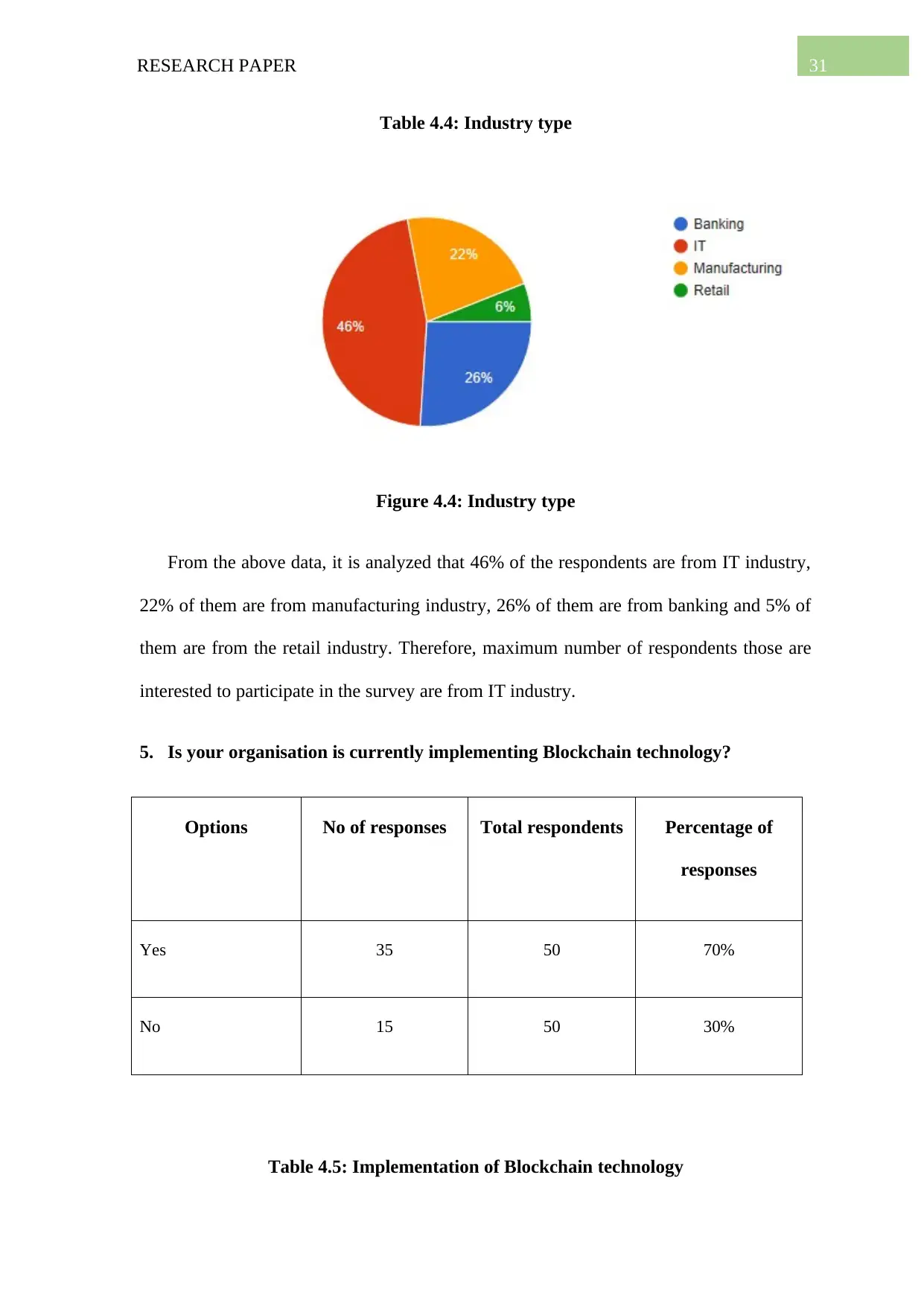
31RESEARCH PAPER
Table 4.4: Industry type
Figure 4.4: Industry type
From the above data, it is analyzed that 46% of the respondents are from IT industry,
22% of them are from manufacturing industry, 26% of them are from banking and 5% of
them are from the retail industry. Therefore, maximum number of respondents those are
interested to participate in the survey are from IT industry.
5. Is your organisation is currently implementing Blockchain technology?
Options No of responses Total respondents Percentage of
responses
Yes 35 50 70%
No 15 50 30%
Table 4.5: Implementation of Blockchain technology
Table 4.4: Industry type
Figure 4.4: Industry type
From the above data, it is analyzed that 46% of the respondents are from IT industry,
22% of them are from manufacturing industry, 26% of them are from banking and 5% of
them are from the retail industry. Therefore, maximum number of respondents those are
interested to participate in the survey are from IT industry.
5. Is your organisation is currently implementing Blockchain technology?
Options No of responses Total respondents Percentage of
responses
Yes 35 50 70%
No 15 50 30%
Table 4.5: Implementation of Blockchain technology

32RESEARCH PAPER
Figure 4.4: Implementation of Blockchain technology
From the above data, it is analyzed that 70% of the respondents are said that their
organisation has implemented Blockchain technology so that they can secure their
transactions made with other organisation. On the other hand, 30% of them said that there
is no implementation of Blockchain technology in the cloud computing.
6. Has your organisation developed budget for Blockchain efforts?
Options No of responses Total respondents Percentage of
responses
Yes 33 50 66%
No 17 50 34%
Table 4.6: Organisation developed budget for Blockchain efforts
Figure 4.4: Implementation of Blockchain technology
From the above data, it is analyzed that 70% of the respondents are said that their
organisation has implemented Blockchain technology so that they can secure their
transactions made with other organisation. On the other hand, 30% of them said that there
is no implementation of Blockchain technology in the cloud computing.
6. Has your organisation developed budget for Blockchain efforts?
Options No of responses Total respondents Percentage of
responses
Yes 33 50 66%
No 17 50 34%
Table 4.6: Organisation developed budget for Blockchain efforts
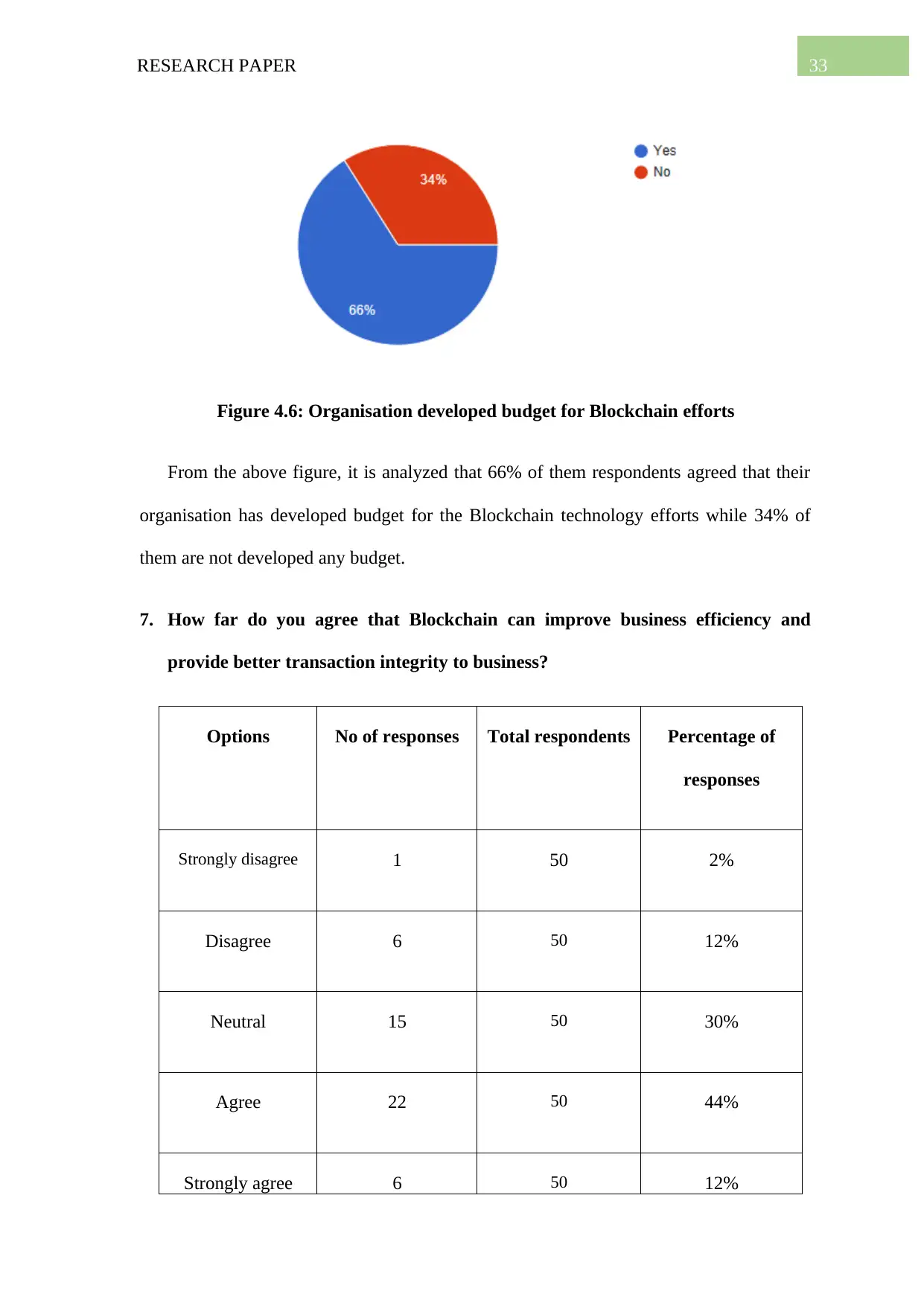
33RESEARCH PAPER
Figure 4.6: Organisation developed budget for Blockchain efforts
From the above figure, it is analyzed that 66% of them respondents agreed that their
organisation has developed budget for the Blockchain technology efforts while 34% of
them are not developed any budget.
7. How far do you agree that Blockchain can improve business efficiency and
provide better transaction integrity to business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 6 50 12%
Neutral 15 50 30%
Agree 22 50 44%
Strongly agree 6 50 12%
Figure 4.6: Organisation developed budget for Blockchain efforts
From the above figure, it is analyzed that 66% of them respondents agreed that their
organisation has developed budget for the Blockchain technology efforts while 34% of
them are not developed any budget.
7. How far do you agree that Blockchain can improve business efficiency and
provide better transaction integrity to business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 6 50 12%
Neutral 15 50 30%
Agree 22 50 44%
Strongly agree 6 50 12%
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
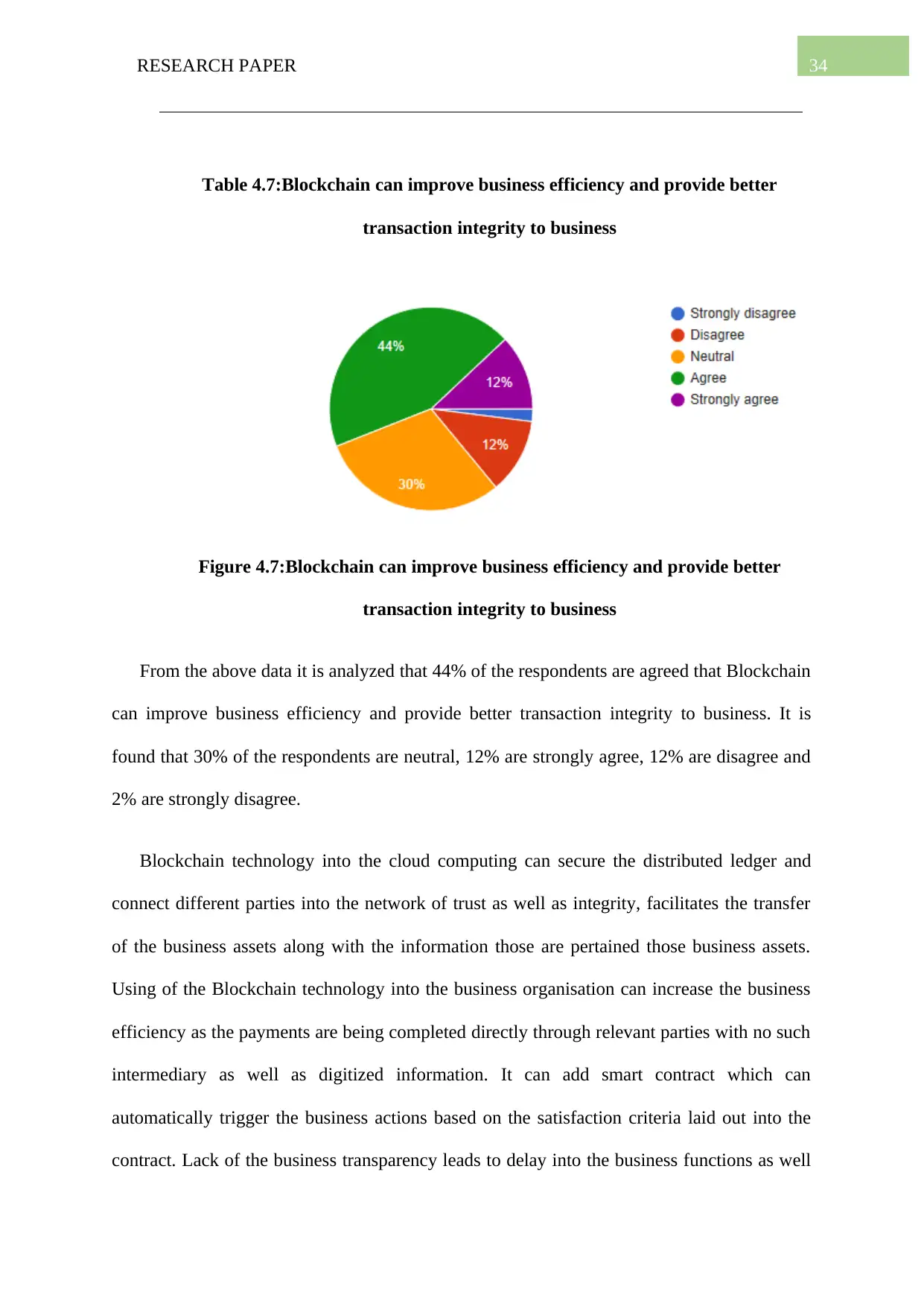
34RESEARCH PAPER
Table 4.7:Blockchain can improve business efficiency and provide better
transaction integrity to business
Figure 4.7:Blockchain can improve business efficiency and provide better
transaction integrity to business
From the above data it is analyzed that 44% of the respondents are agreed that Blockchain
can improve business efficiency and provide better transaction integrity to business. It is
found that 30% of the respondents are neutral, 12% are strongly agree, 12% are disagree and
2% are strongly disagree.
Blockchain technology into the cloud computing can secure the distributed ledger and
connect different parties into the network of trust as well as integrity, facilitates the transfer
of the business assets along with the information those are pertained those business assets.
Using of the Blockchain technology into the business organisation can increase the business
efficiency as the payments are being completed directly through relevant parties with no such
intermediary as well as digitized information. It can add smart contract which can
automatically trigger the business actions based on the satisfaction criteria laid out into the
contract. Lack of the business transparency leads to delay into the business functions as well
Table 4.7:Blockchain can improve business efficiency and provide better
transaction integrity to business
Figure 4.7:Blockchain can improve business efficiency and provide better
transaction integrity to business
From the above data it is analyzed that 44% of the respondents are agreed that Blockchain
can improve business efficiency and provide better transaction integrity to business. It is
found that 30% of the respondents are neutral, 12% are strongly agree, 12% are disagree and
2% are strongly disagree.
Blockchain technology into the cloud computing can secure the distributed ledger and
connect different parties into the network of trust as well as integrity, facilitates the transfer
of the business assets along with the information those are pertained those business assets.
Using of the Blockchain technology into the business organisation can increase the business
efficiency as the payments are being completed directly through relevant parties with no such
intermediary as well as digitized information. It can add smart contract which can
automatically trigger the business actions based on the satisfaction criteria laid out into the
contract. Lack of the business transparency leads to delay into the business functions as well
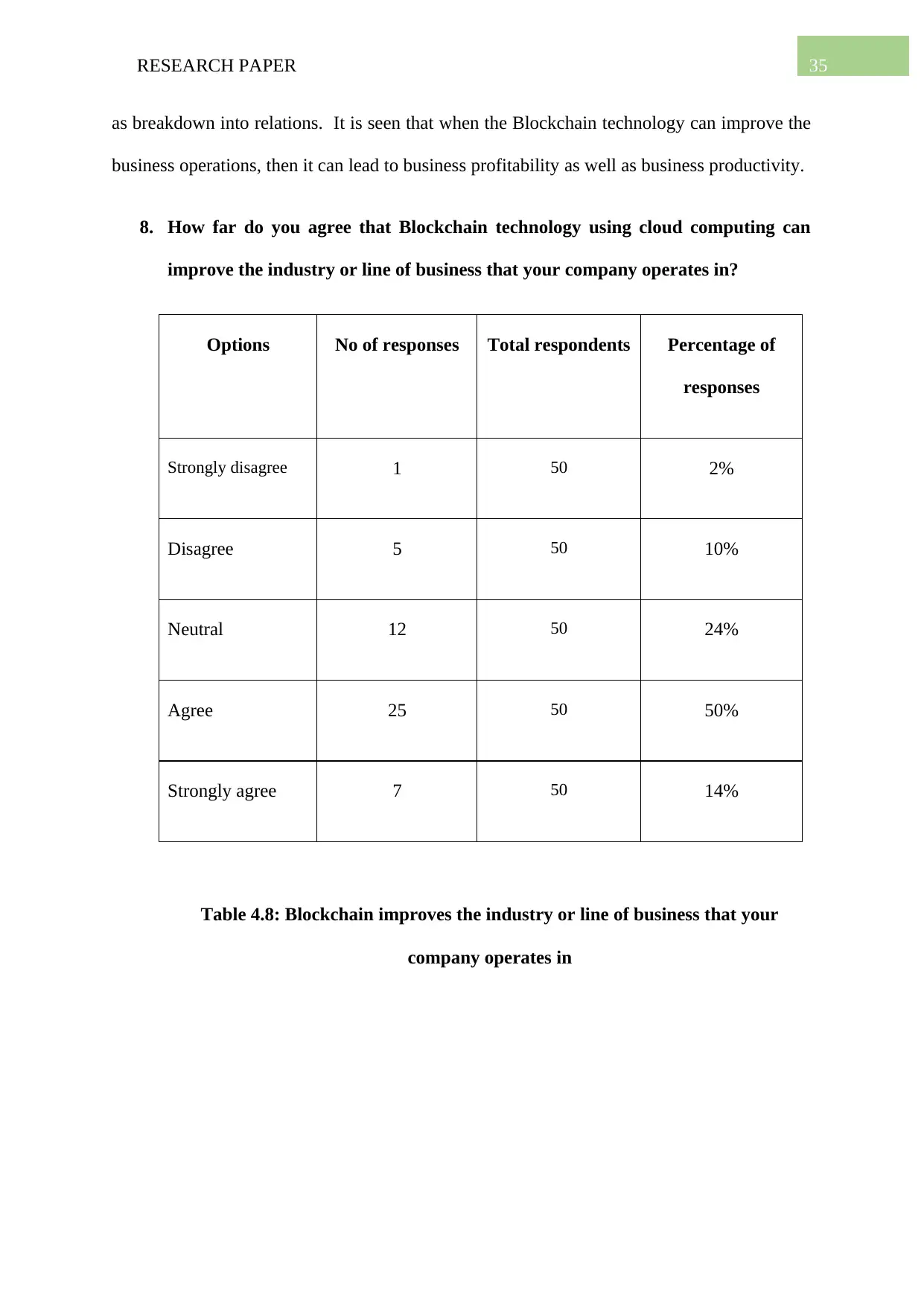
35RESEARCH PAPER
as breakdown into relations. It is seen that when the Blockchain technology can improve the
business operations, then it can lead to business profitability as well as business productivity.
8. How far do you agree that Blockchain technology using cloud computing can
improve the industry or line of business that your company operates in?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 5 50 10%
Neutral 12 50 24%
Agree 25 50 50%
Strongly agree 7 50 14%
Table 4.8: Blockchain improves the industry or line of business that your
company operates in
as breakdown into relations. It is seen that when the Blockchain technology can improve the
business operations, then it can lead to business profitability as well as business productivity.
8. How far do you agree that Blockchain technology using cloud computing can
improve the industry or line of business that your company operates in?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 5 50 10%
Neutral 12 50 24%
Agree 25 50 50%
Strongly agree 7 50 14%
Table 4.8: Blockchain improves the industry or line of business that your
company operates in
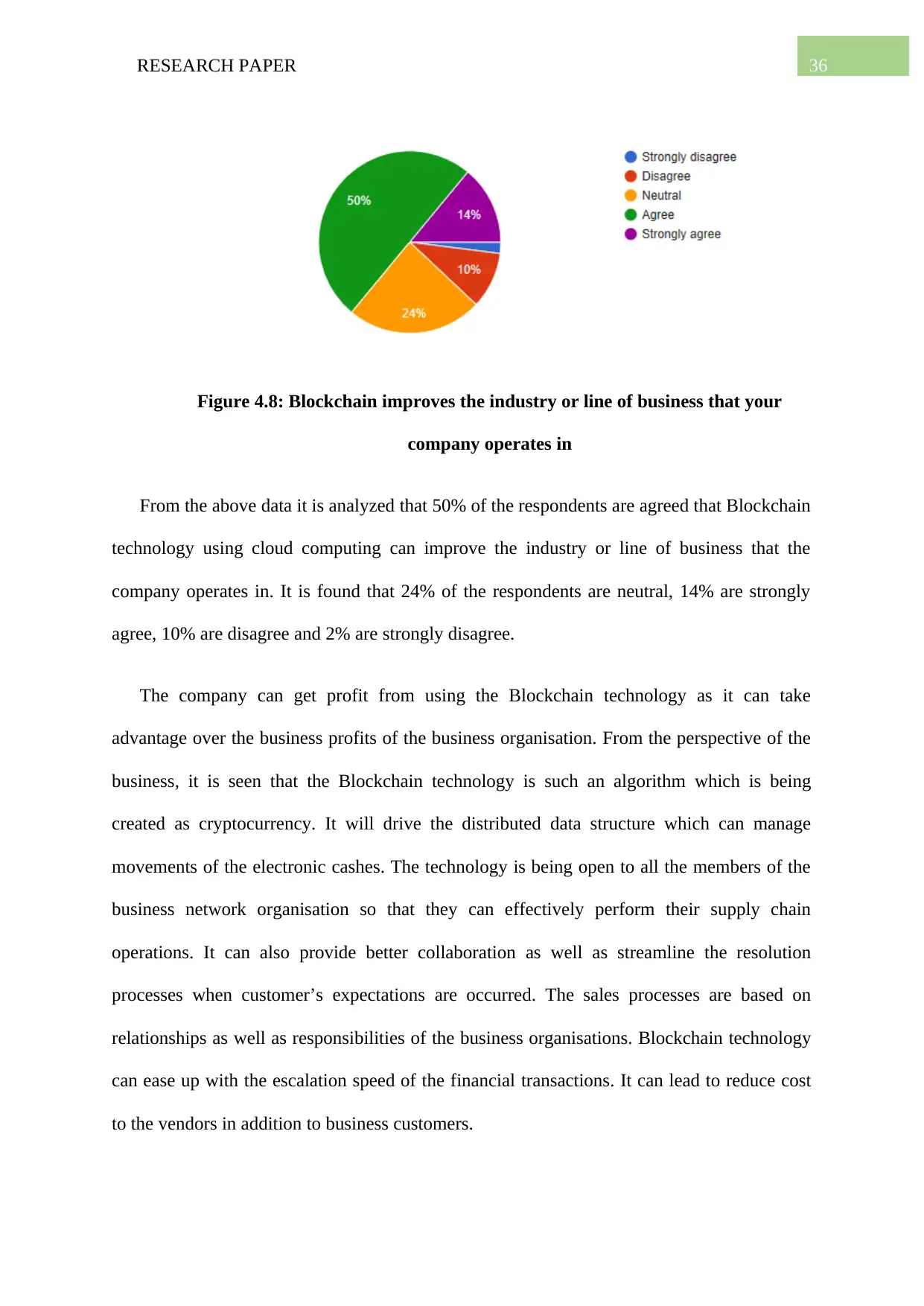
36RESEARCH PAPER
Figure 4.8: Blockchain improves the industry or line of business that your
company operates in
From the above data it is analyzed that 50% of the respondents are agreed that Blockchain
technology using cloud computing can improve the industry or line of business that the
company operates in. It is found that 24% of the respondents are neutral, 14% are strongly
agree, 10% are disagree and 2% are strongly disagree.
The company can get profit from using the Blockchain technology as it can take
advantage over the business profits of the business organisation. From the perspective of the
business, it is seen that the Blockchain technology is such an algorithm which is being
created as cryptocurrency. It will drive the distributed data structure which can manage
movements of the electronic cashes. The technology is being open to all the members of the
business network organisation so that they can effectively perform their supply chain
operations. It can also provide better collaboration as well as streamline the resolution
processes when customer’s expectations are occurred. The sales processes are based on
relationships as well as responsibilities of the business organisations. Blockchain technology
can ease up with the escalation speed of the financial transactions. It can lead to reduce cost
to the vendors in addition to business customers.
Figure 4.8: Blockchain improves the industry or line of business that your
company operates in
From the above data it is analyzed that 50% of the respondents are agreed that Blockchain
technology using cloud computing can improve the industry or line of business that the
company operates in. It is found that 24% of the respondents are neutral, 14% are strongly
agree, 10% are disagree and 2% are strongly disagree.
The company can get profit from using the Blockchain technology as it can take
advantage over the business profits of the business organisation. From the perspective of the
business, it is seen that the Blockchain technology is such an algorithm which is being
created as cryptocurrency. It will drive the distributed data structure which can manage
movements of the electronic cashes. The technology is being open to all the members of the
business network organisation so that they can effectively perform their supply chain
operations. It can also provide better collaboration as well as streamline the resolution
processes when customer’s expectations are occurred. The sales processes are based on
relationships as well as responsibilities of the business organisations. Blockchain technology
can ease up with the escalation speed of the financial transactions. It can lead to reduce cost
to the vendors in addition to business customers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
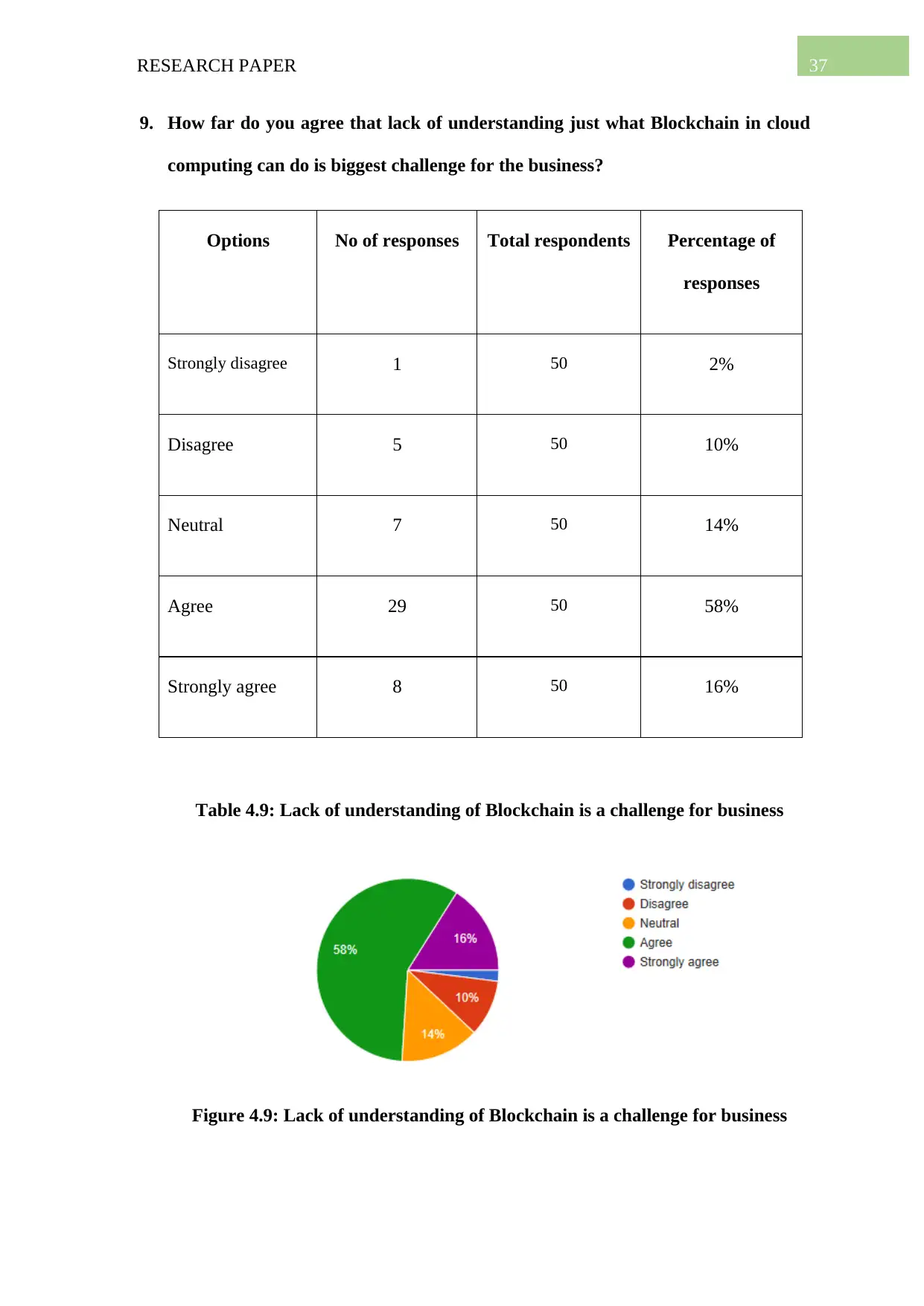
37RESEARCH PAPER
9. How far do you agree that lack of understanding just what Blockchain in cloud
computing can do is biggest challenge for the business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 5 50 10%
Neutral 7 50 14%
Agree 29 50 58%
Strongly agree 8 50 16%
Table 4.9: Lack of understanding of Blockchain is a challenge for business
Figure 4.9: Lack of understanding of Blockchain is a challenge for business
9. How far do you agree that lack of understanding just what Blockchain in cloud
computing can do is biggest challenge for the business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 5 50 10%
Neutral 7 50 14%
Agree 29 50 58%
Strongly agree 8 50 16%
Table 4.9: Lack of understanding of Blockchain is a challenge for business
Figure 4.9: Lack of understanding of Blockchain is a challenge for business
38RESEARCH PAPER
From the above data it is analyzed that 58% of the respondents are agreed that lack of
understanding just what Blockchain in cloud computing can do is biggest challenge for the
business. It is found that 14% of the respondents are neutral, 16% are strongly agree, 10% are
disagree and 2% are strongly disagree.
The employees those are employing into the business organisations, most of them have
lack of technical knowledge of the Blockchain technology. When the employees those are
using the technology have no knowledge of how to handle it as well as use it, then it is
difficult for the business organisation to implement the technology so that it can improve over
the business operation, transparency as well as business functions. In addition to this, the
other areas of concern is that the regulation is not certain like smart contracts as the
employees do not know what is Blockchain technology and its respective usage into the cloud
computing. In this case, as a solution training is required for the employees as well as staffs
so that they can get training on how to handle the technology and use it for the business
benefits. In this case, the employees cab able to understand its standardization and benefits.
10. How far do you agree that privacy and security are main priority of the business
for adoption of Blockchain in cloud computing?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 4 50 8%
Neutral 7 50 14%
From the above data it is analyzed that 58% of the respondents are agreed that lack of
understanding just what Blockchain in cloud computing can do is biggest challenge for the
business. It is found that 14% of the respondents are neutral, 16% are strongly agree, 10% are
disagree and 2% are strongly disagree.
The employees those are employing into the business organisations, most of them have
lack of technical knowledge of the Blockchain technology. When the employees those are
using the technology have no knowledge of how to handle it as well as use it, then it is
difficult for the business organisation to implement the technology so that it can improve over
the business operation, transparency as well as business functions. In addition to this, the
other areas of concern is that the regulation is not certain like smart contracts as the
employees do not know what is Blockchain technology and its respective usage into the cloud
computing. In this case, as a solution training is required for the employees as well as staffs
so that they can get training on how to handle the technology and use it for the business
benefits. In this case, the employees cab able to understand its standardization and benefits.
10. How far do you agree that privacy and security are main priority of the business
for adoption of Blockchain in cloud computing?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 4 50 8%
Neutral 7 50 14%
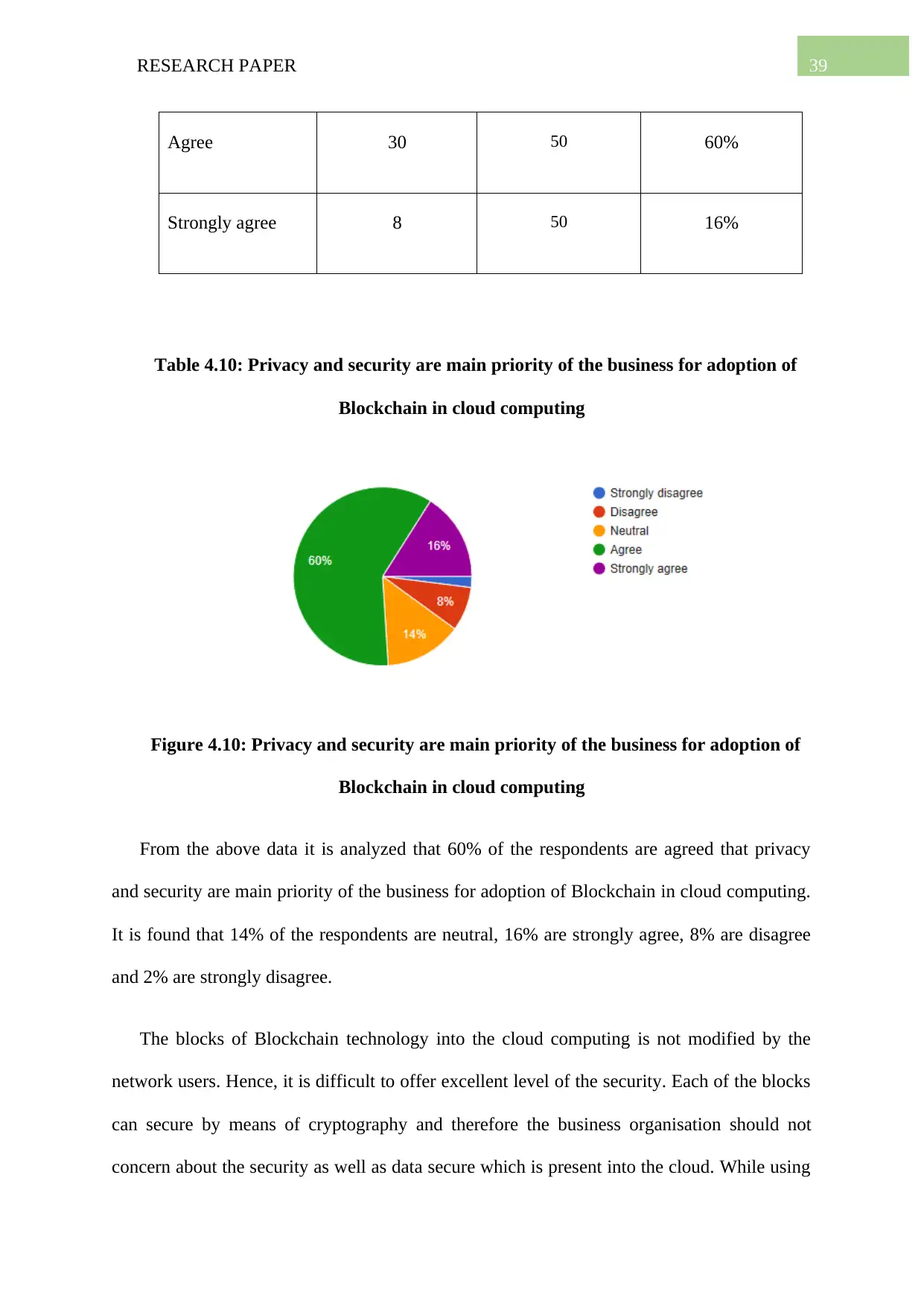
39RESEARCH PAPER
Agree 30 50 60%
Strongly agree 8 50 16%
Table 4.10: Privacy and security are main priority of the business for adoption of
Blockchain in cloud computing
Figure 4.10: Privacy and security are main priority of the business for adoption of
Blockchain in cloud computing
From the above data it is analyzed that 60% of the respondents are agreed that privacy
and security are main priority of the business for adoption of Blockchain in cloud computing.
It is found that 14% of the respondents are neutral, 16% are strongly agree, 8% are disagree
and 2% are strongly disagree.
The blocks of Blockchain technology into the cloud computing is not modified by the
network users. Hence, it is difficult to offer excellent level of the security. Each of the blocks
can secure by means of cryptography and therefore the business organisation should not
concern about the security as well as data secure which is present into the cloud. While using
Agree 30 50 60%
Strongly agree 8 50 16%
Table 4.10: Privacy and security are main priority of the business for adoption of
Blockchain in cloud computing
Figure 4.10: Privacy and security are main priority of the business for adoption of
Blockchain in cloud computing
From the above data it is analyzed that 60% of the respondents are agreed that privacy
and security are main priority of the business for adoption of Blockchain in cloud computing.
It is found that 14% of the respondents are neutral, 16% are strongly agree, 8% are disagree
and 2% are strongly disagree.
The blocks of Blockchain technology into the cloud computing is not modified by the
network users. Hence, it is difficult to offer excellent level of the security. Each of the blocks
can secure by means of cryptography and therefore the business organisation should not
concern about the security as well as data secure which is present into the cloud. While using
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
40RESEARCH PAPER
the Blockchain technology, there is no such specific network conditions which are followed.
The network can be peer-to-peer network under concerned protocols. It is being validated
new block as well as help the business organisation to keep pace with not investment into the
third party applications. In order to concern on privacy as well as security, no third party
person can able to access to the transactional data, therefore using this technology all the data
are kept secured.
11. How far do you agree that encryption is best approach to help business for
keeping data secured?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 3 50 6%
Disagree 5 50 10%
Neutral 7 50 14%
Agree 26 50 52%
Strongly agree 9 50 18%
Table 4.11: Encryption is best approach to help business to keep data secure
the Blockchain technology, there is no such specific network conditions which are followed.
The network can be peer-to-peer network under concerned protocols. It is being validated
new block as well as help the business organisation to keep pace with not investment into the
third party applications. In order to concern on privacy as well as security, no third party
person can able to access to the transactional data, therefore using this technology all the data
are kept secured.
11. How far do you agree that encryption is best approach to help business for
keeping data secured?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 3 50 6%
Disagree 5 50 10%
Neutral 7 50 14%
Agree 26 50 52%
Strongly agree 9 50 18%
Table 4.11: Encryption is best approach to help business to keep data secure

41RESEARCH PAPER
Figure 4.11: Encryption is best approach to help business to keep data secure
From the above data it is analyzed that 52% of the respondents are agreed that encryption
is best approach to help business for keeping data secured. It is found that 14% of the
respondents are neutral, 6% are strongly agree, 10% are disagree and 18% are strongly
disagree.
Data security is a main concern for the business organisation to secure the business
confidential data, therefore Blockchain technology solutions can help the business to secure
their data in safe place. Encryption is the best way as well as approach which help the
business organisations to keep their data secured. The data is being encoded as well as
changed to such extent before it is being sent of network by means of the sender. The receiver
can able to understand how to decode it. Into the Blockchain technology, the encryption
method is used as it can add more to entire security as well as authenticity of Blockchain
blocks as well as help them to keep it secured. Based on the respondent’s responses, it is the
best method to keep the data secured in a place and no third party person can able to hack as
well as access it in any conditions.
12. How far do you agree that Blockchain technology in cloud computing provides
secured online transactions in business?
Figure 4.11: Encryption is best approach to help business to keep data secure
From the above data it is analyzed that 52% of the respondents are agreed that encryption
is best approach to help business for keeping data secured. It is found that 14% of the
respondents are neutral, 6% are strongly agree, 10% are disagree and 18% are strongly
disagree.
Data security is a main concern for the business organisation to secure the business
confidential data, therefore Blockchain technology solutions can help the business to secure
their data in safe place. Encryption is the best way as well as approach which help the
business organisations to keep their data secured. The data is being encoded as well as
changed to such extent before it is being sent of network by means of the sender. The receiver
can able to understand how to decode it. Into the Blockchain technology, the encryption
method is used as it can add more to entire security as well as authenticity of Blockchain
blocks as well as help them to keep it secured. Based on the respondent’s responses, it is the
best method to keep the data secured in a place and no third party person can able to hack as
well as access it in any conditions.
12. How far do you agree that Blockchain technology in cloud computing provides
secured online transactions in business?
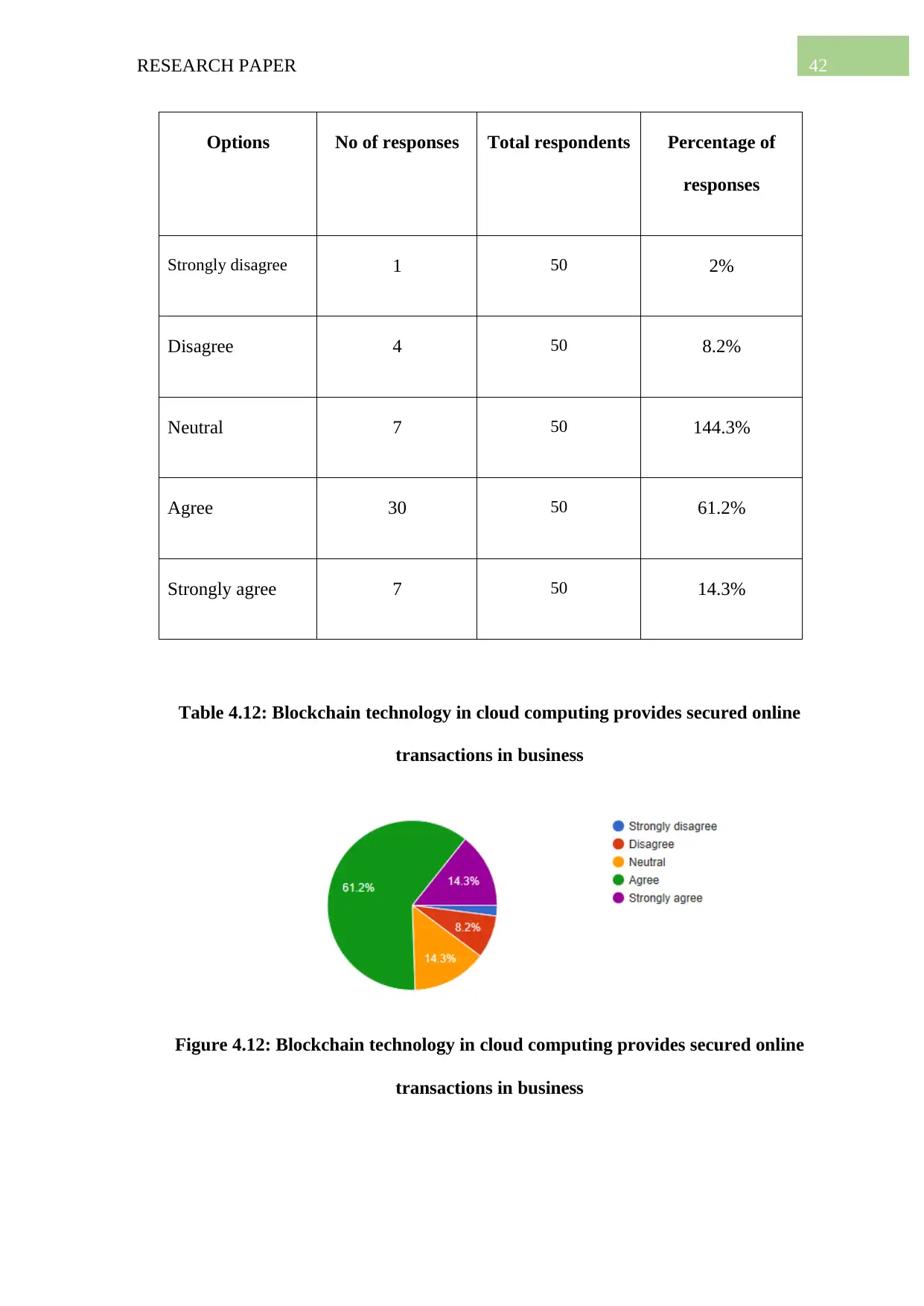
42RESEARCH PAPER
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 4 50 8.2%
Neutral 7 50 144.3%
Agree 30 50 61.2%
Strongly agree 7 50 14.3%
Table 4.12: Blockchain technology in cloud computing provides secured online
transactions in business
Figure 4.12: Blockchain technology in cloud computing provides secured online
transactions in business
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 4 50 8.2%
Neutral 7 50 144.3%
Agree 30 50 61.2%
Strongly agree 7 50 14.3%
Table 4.12: Blockchain technology in cloud computing provides secured online
transactions in business
Figure 4.12: Blockchain technology in cloud computing provides secured online
transactions in business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
43RESEARCH PAPER
From the above data it is analyzed that 61.2% of the respondents are agreed that
Blockchain technology in cloud computing provides secured online transactions in business.
It is found that 14.3% of the respondents are neutral, 14.3% are strongly agree, 8.2% are
disagree and 2% are strongly disagree.
As per the respondents, it is found that there is no such restriction to keep the records into
any kind of Blockchain approaches. There are lot of organisations in entire world those are
using the Blockchain approaches and the fact is that the records are related to business
transactions, events related to the business, management processes as well as transaction
processing. There is also used of proper documentation in case of gathering the business
records. Therefore, it is seen that record keeping is not limited into the applications only. The
blockchain technology in cloud computing can encourage to provide secured online
transactions. There is distributed as well as decentralized ledger which keep eye on the
transactional records. It enhances security of the business data. Blockchain in each block and
unit is being transferred only at one time which can eliminate the problems of hacking of
data.
13. How far do you agree that there is required to improve security policy to secure
information and financial records of business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 5 50 10%
From the above data it is analyzed that 61.2% of the respondents are agreed that
Blockchain technology in cloud computing provides secured online transactions in business.
It is found that 14.3% of the respondents are neutral, 14.3% are strongly agree, 8.2% are
disagree and 2% are strongly disagree.
As per the respondents, it is found that there is no such restriction to keep the records into
any kind of Blockchain approaches. There are lot of organisations in entire world those are
using the Blockchain approaches and the fact is that the records are related to business
transactions, events related to the business, management processes as well as transaction
processing. There is also used of proper documentation in case of gathering the business
records. Therefore, it is seen that record keeping is not limited into the applications only. The
blockchain technology in cloud computing can encourage to provide secured online
transactions. There is distributed as well as decentralized ledger which keep eye on the
transactional records. It enhances security of the business data. Blockchain in each block and
unit is being transferred only at one time which can eliminate the problems of hacking of
data.
13. How far do you agree that there is required to improve security policy to secure
information and financial records of business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 5 50 10%
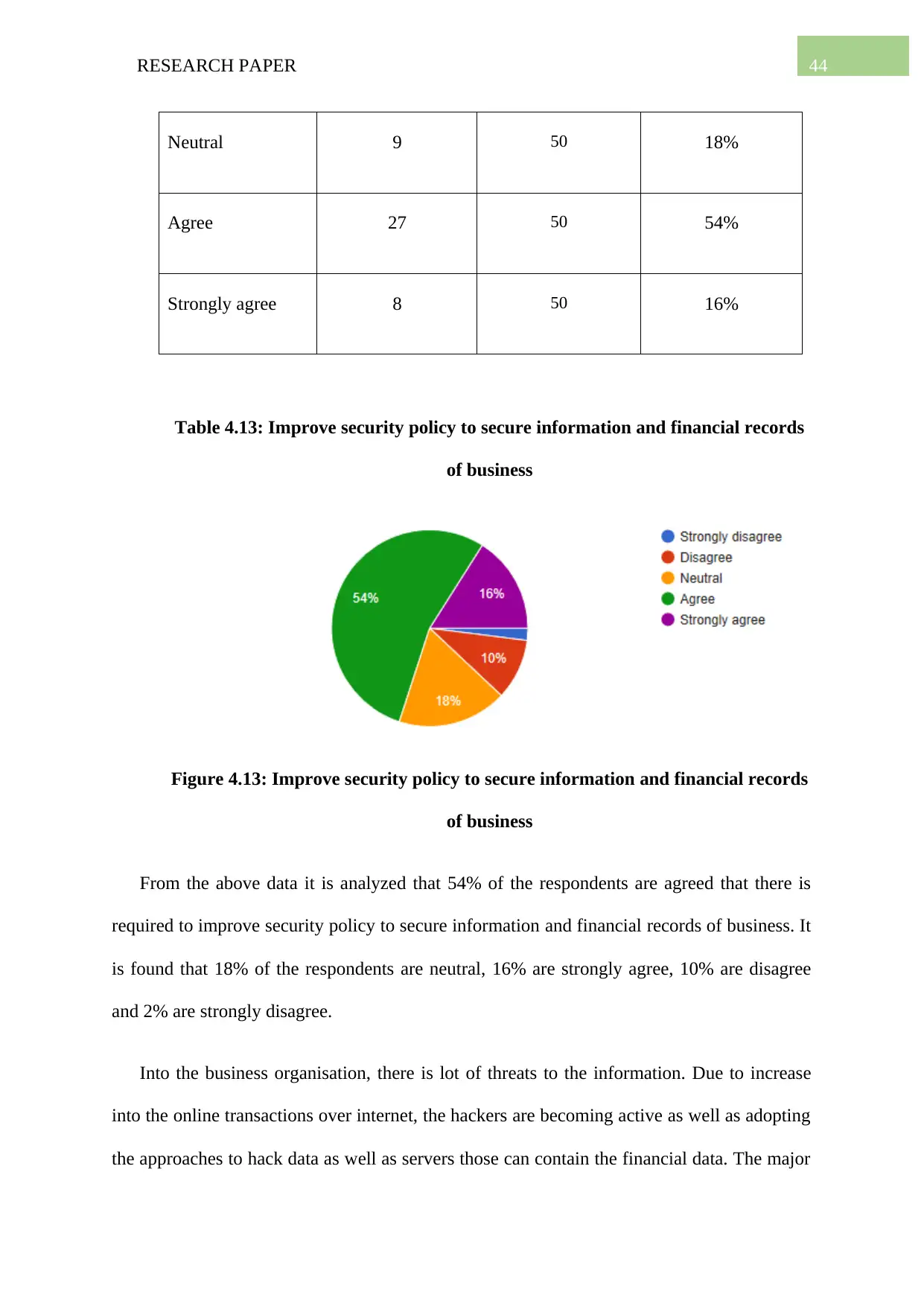
44RESEARCH PAPER
Neutral 9 50 18%
Agree 27 50 54%
Strongly agree 8 50 16%
Table 4.13: Improve security policy to secure information and financial records
of business
Figure 4.13: Improve security policy to secure information and financial records
of business
From the above data it is analyzed that 54% of the respondents are agreed that there is
required to improve security policy to secure information and financial records of business. It
is found that 18% of the respondents are neutral, 16% are strongly agree, 10% are disagree
and 2% are strongly disagree.
Into the business organisation, there is lot of threats to the information. Due to increase
into the online transactions over internet, the hackers are becoming active as well as adopting
the approaches to hack data as well as servers those can contain the financial data. The major
Neutral 9 50 18%
Agree 27 50 54%
Strongly agree 8 50 16%
Table 4.13: Improve security policy to secure information and financial records
of business
Figure 4.13: Improve security policy to secure information and financial records
of business
From the above data it is analyzed that 54% of the respondents are agreed that there is
required to improve security policy to secure information and financial records of business. It
is found that 18% of the respondents are neutral, 16% are strongly agree, 10% are disagree
and 2% are strongly disagree.
Into the business organisation, there is lot of threats to the information. Due to increase
into the online transactions over internet, the hackers are becoming active as well as adopting
the approaches to hack data as well as servers those can contain the financial data. The major
45RESEARCH PAPER
threat related to using the blockchain technology in cloud computing is software attack, theft
of the business data, extortion of the information and others. In order to secure the data which
are transferred through online model, the business should adopt strict security policy so that
they can better provide security solutions to their business confidential data. The security
policy is defined on requirements to be secured on the information system. It is bound to the
network users under core protocols. It should be followed with the strict security policies so
that it can enhance entire security. When it comes to secure the information as well as
financial records into the business organisation, security policies are being implemented in it.
14. How far do you agree that implementation of cloud computing benefits the
business where employees become self-sufficient?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 5 50 10%
Neutral 8 50 16%
Agree 28 50 56%
Strongly agree 8 50 16%
Figure 4.14: Implementation of cloud computing benefits the business
threat related to using the blockchain technology in cloud computing is software attack, theft
of the business data, extortion of the information and others. In order to secure the data which
are transferred through online model, the business should adopt strict security policy so that
they can better provide security solutions to their business confidential data. The security
policy is defined on requirements to be secured on the information system. It is bound to the
network users under core protocols. It should be followed with the strict security policies so
that it can enhance entire security. When it comes to secure the information as well as
financial records into the business organisation, security policies are being implemented in it.
14. How far do you agree that implementation of cloud computing benefits the
business where employees become self-sufficient?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 5 50 10%
Neutral 8 50 16%
Agree 28 50 56%
Strongly agree 8 50 16%
Figure 4.14: Implementation of cloud computing benefits the business
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
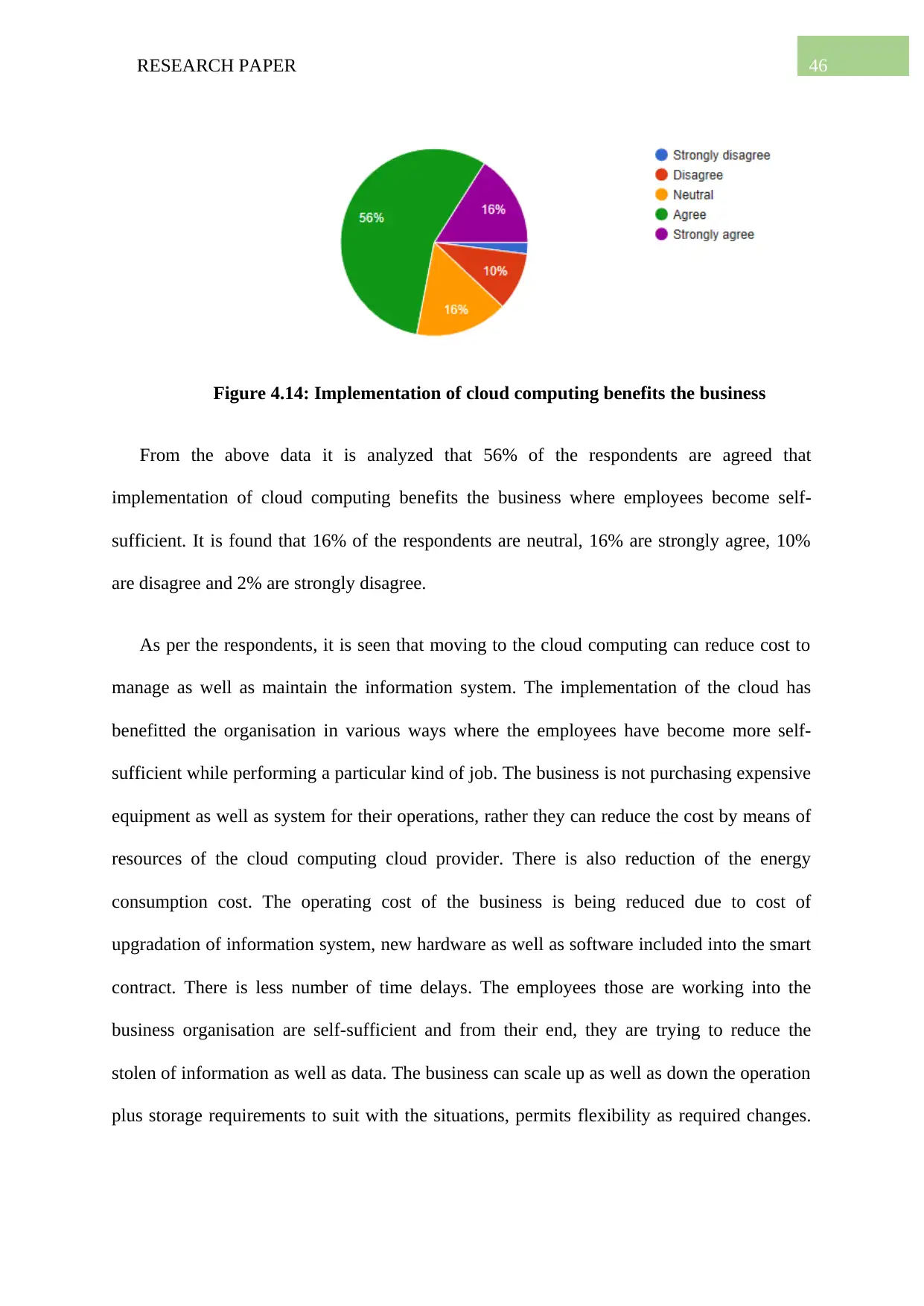
46RESEARCH PAPER
Figure 4.14: Implementation of cloud computing benefits the business
From the above data it is analyzed that 56% of the respondents are agreed that
implementation of cloud computing benefits the business where employees become self-
sufficient. It is found that 16% of the respondents are neutral, 16% are strongly agree, 10%
are disagree and 2% are strongly disagree.
As per the respondents, it is seen that moving to the cloud computing can reduce cost to
manage as well as maintain the information system. The implementation of the cloud has
benefitted the organisation in various ways where the employees have become more self-
sufficient while performing a particular kind of job. The business is not purchasing expensive
equipment as well as system for their operations, rather they can reduce the cost by means of
resources of the cloud computing cloud provider. There is also reduction of the energy
consumption cost. The operating cost of the business is being reduced due to cost of
upgradation of information system, new hardware as well as software included into the smart
contract. There is less number of time delays. The employees those are working into the
business organisation are self-sufficient and from their end, they are trying to reduce the
stolen of information as well as data. The business can scale up as well as down the operation
plus storage requirements to suit with the situations, permits flexibility as required changes.
Figure 4.14: Implementation of cloud computing benefits the business
From the above data it is analyzed that 56% of the respondents are agreed that
implementation of cloud computing benefits the business where employees become self-
sufficient. It is found that 16% of the respondents are neutral, 16% are strongly agree, 10%
are disagree and 2% are strongly disagree.
As per the respondents, it is seen that moving to the cloud computing can reduce cost to
manage as well as maintain the information system. The implementation of the cloud has
benefitted the organisation in various ways where the employees have become more self-
sufficient while performing a particular kind of job. The business is not purchasing expensive
equipment as well as system for their operations, rather they can reduce the cost by means of
resources of the cloud computing cloud provider. There is also reduction of the energy
consumption cost. The operating cost of the business is being reduced due to cost of
upgradation of information system, new hardware as well as software included into the smart
contract. There is less number of time delays. The employees those are working into the
business organisation are self-sufficient and from their end, they are trying to reduce the
stolen of information as well as data. The business can scale up as well as down the operation
plus storage requirements to suit with the situations, permits flexibility as required changes.
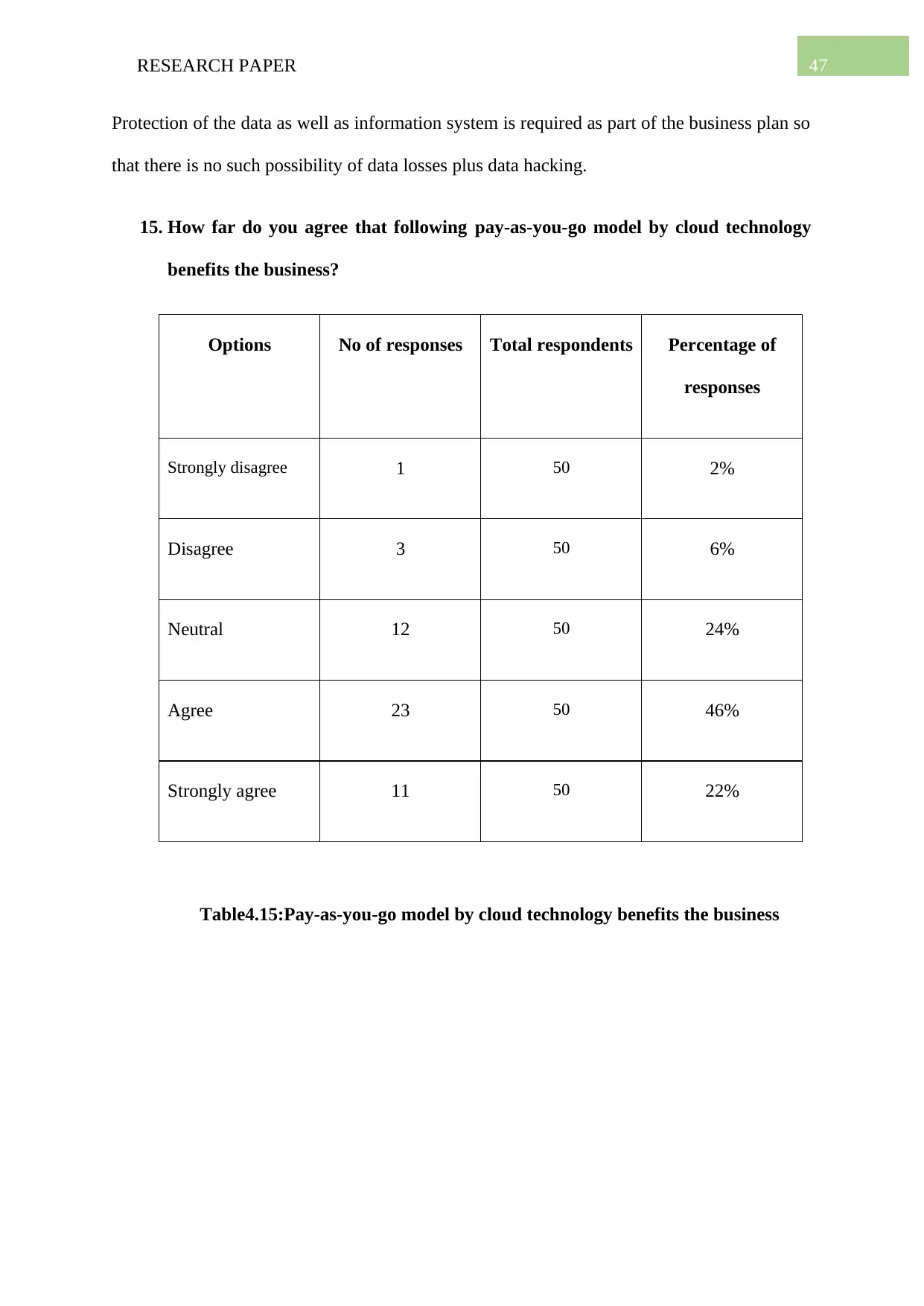
47RESEARCH PAPER
Protection of the data as well as information system is required as part of the business plan so
that there is no such possibility of data losses plus data hacking.
15. How far do you agree that following pay-as-you-go model by cloud technology
benefits the business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 3 50 6%
Neutral 12 50 24%
Agree 23 50 46%
Strongly agree 11 50 22%
Table4.15:Pay-as-you-go model by cloud technology benefits the business
Protection of the data as well as information system is required as part of the business plan so
that there is no such possibility of data losses plus data hacking.
15. How far do you agree that following pay-as-you-go model by cloud technology
benefits the business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 1 50 2%
Disagree 3 50 6%
Neutral 12 50 24%
Agree 23 50 46%
Strongly agree 11 50 22%
Table4.15:Pay-as-you-go model by cloud technology benefits the business
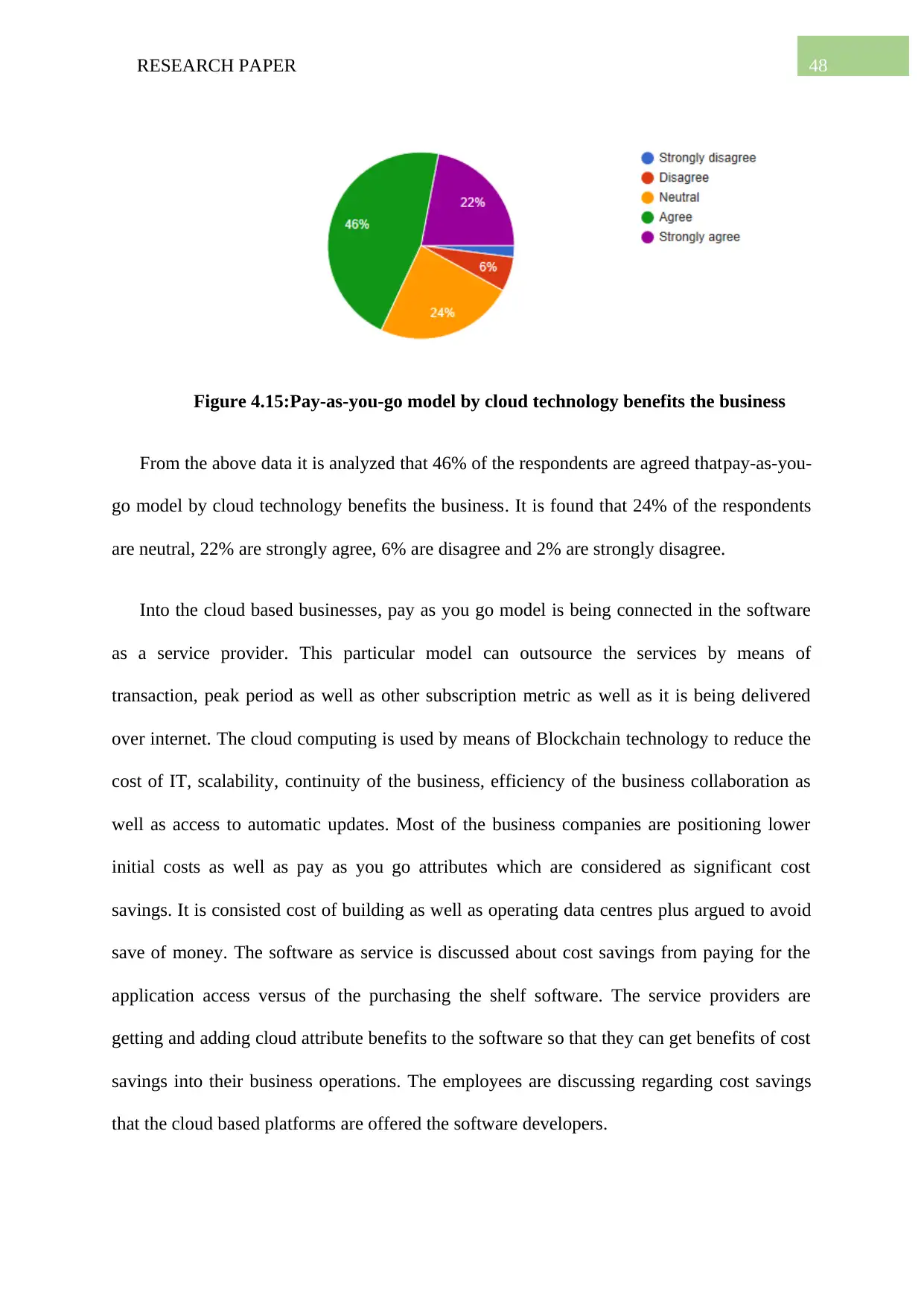
48RESEARCH PAPER
Figure 4.15:Pay-as-you-go model by cloud technology benefits the business
From the above data it is analyzed that 46% of the respondents are agreed thatpay-as-you-
go model by cloud technology benefits the business. It is found that 24% of the respondents
are neutral, 22% are strongly agree, 6% are disagree and 2% are strongly disagree.
Into the cloud based businesses, pay as you go model is being connected in the software
as a service provider. This particular model can outsource the services by means of
transaction, peak period as well as other subscription metric as well as it is being delivered
over internet. The cloud computing is used by means of Blockchain technology to reduce the
cost of IT, scalability, continuity of the business, efficiency of the business collaboration as
well as access to automatic updates. Most of the business companies are positioning lower
initial costs as well as pay as you go attributes which are considered as significant cost
savings. It is consisted cost of building as well as operating data centres plus argued to avoid
save of money. The software as service is discussed about cost savings from paying for the
application access versus of the purchasing the shelf software. The service providers are
getting and adding cloud attribute benefits to the software so that they can get benefits of cost
savings into their business operations. The employees are discussing regarding cost savings
that the cloud based platforms are offered the software developers.
Figure 4.15:Pay-as-you-go model by cloud technology benefits the business
From the above data it is analyzed that 46% of the respondents are agreed thatpay-as-you-
go model by cloud technology benefits the business. It is found that 24% of the respondents
are neutral, 22% are strongly agree, 6% are disagree and 2% are strongly disagree.
Into the cloud based businesses, pay as you go model is being connected in the software
as a service provider. This particular model can outsource the services by means of
transaction, peak period as well as other subscription metric as well as it is being delivered
over internet. The cloud computing is used by means of Blockchain technology to reduce the
cost of IT, scalability, continuity of the business, efficiency of the business collaboration as
well as access to automatic updates. Most of the business companies are positioning lower
initial costs as well as pay as you go attributes which are considered as significant cost
savings. It is consisted cost of building as well as operating data centres plus argued to avoid
save of money. The software as service is discussed about cost savings from paying for the
application access versus of the purchasing the shelf software. The service providers are
getting and adding cloud attribute benefits to the software so that they can get benefits of cost
savings into their business operations. The employees are discussing regarding cost savings
that the cloud based platforms are offered the software developers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
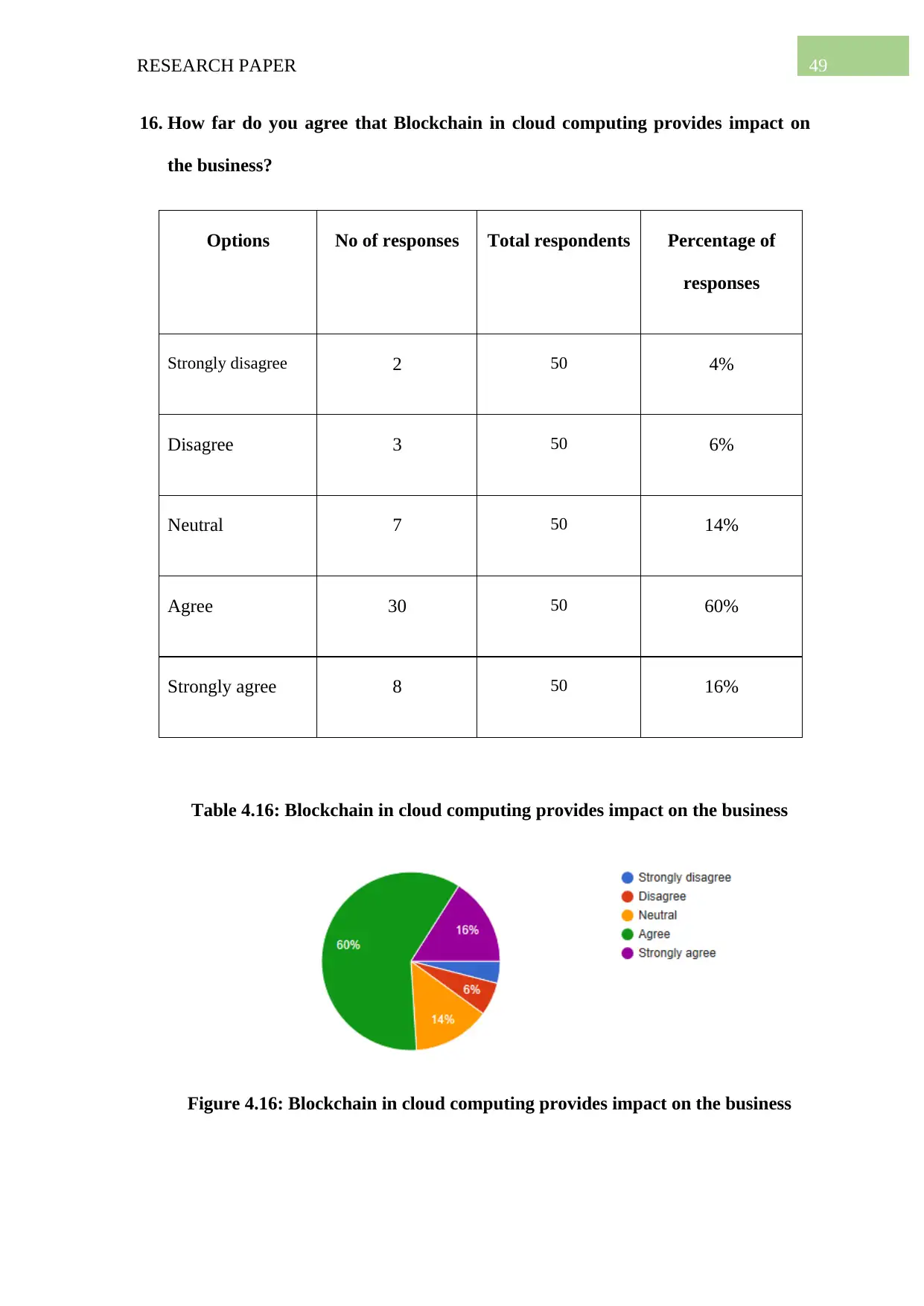
49RESEARCH PAPER
16. How far do you agree that Blockchain in cloud computing provides impact on
the business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 2 50 4%
Disagree 3 50 6%
Neutral 7 50 14%
Agree 30 50 60%
Strongly agree 8 50 16%
Table 4.16: Blockchain in cloud computing provides impact on the business
Figure 4.16: Blockchain in cloud computing provides impact on the business
16. How far do you agree that Blockchain in cloud computing provides impact on
the business?
Options No of responses Total respondents Percentage of
responses
Strongly disagree 2 50 4%
Disagree 3 50 6%
Neutral 7 50 14%
Agree 30 50 60%
Strongly agree 8 50 16%
Table 4.16: Blockchain in cloud computing provides impact on the business
Figure 4.16: Blockchain in cloud computing provides impact on the business

50RESEARCH PAPER
From the above data it is analyzed that 60% of the respondents are agreed that Blockchain
in cloud computing provides impact on the business. It is found that 14% of the respondents
are neutral, 16% are strongly agree, 6% are disagree and 6% are strongly disagree.
One of the challenges of the cloud computing is that the Blockchain is seek to address the
cost. The solutions of cloud computing is cheaper when it is used for the applications by
means of predictable workloads. The solutions are considered as cost effective when it is
used for the occasional requirements. The Blockchain technology plays a key role into
existing cloud computing to make the infrastructure better and improved. The security system
would be even more vulnerable if the Blockchain technology is utilised for the transactions
involving bitcoin and taken to the cloud services. Implementation process of Blockchain
Technology in Cloud Computing and their impact on the service provisions of the business
organisation is also dependent on the security system. If it is porous enough, customers would
not like to invest their time and online money to the business services.
4.3 Regression Analysis
The research study is based on three hypotheses which are:
Hypothesis 1: There is positive impact of business efficiency on the business
transactions.
Hypothesis 2: There is positive impact of secured Blockchain technology in the
business efficiency.
Hypothesis 3: There is positive impact of Blockchain technology in the cloud
computing.
The regression model of the hypothesis can be stated as the following:
From the above data it is analyzed that 60% of the respondents are agreed that Blockchain
in cloud computing provides impact on the business. It is found that 14% of the respondents
are neutral, 16% are strongly agree, 6% are disagree and 6% are strongly disagree.
One of the challenges of the cloud computing is that the Blockchain is seek to address the
cost. The solutions of cloud computing is cheaper when it is used for the applications by
means of predictable workloads. The solutions are considered as cost effective when it is
used for the occasional requirements. The Blockchain technology plays a key role into
existing cloud computing to make the infrastructure better and improved. The security system
would be even more vulnerable if the Blockchain technology is utilised for the transactions
involving bitcoin and taken to the cloud services. Implementation process of Blockchain
Technology in Cloud Computing and their impact on the service provisions of the business
organisation is also dependent on the security system. If it is porous enough, customers would
not like to invest their time and online money to the business services.
4.3 Regression Analysis
The research study is based on three hypotheses which are:
Hypothesis 1: There is positive impact of business efficiency on the business
transactions.
Hypothesis 2: There is positive impact of secured Blockchain technology in the
business efficiency.
Hypothesis 3: There is positive impact of Blockchain technology in the cloud
computing.
The regression model of the hypothesis can be stated as the following:
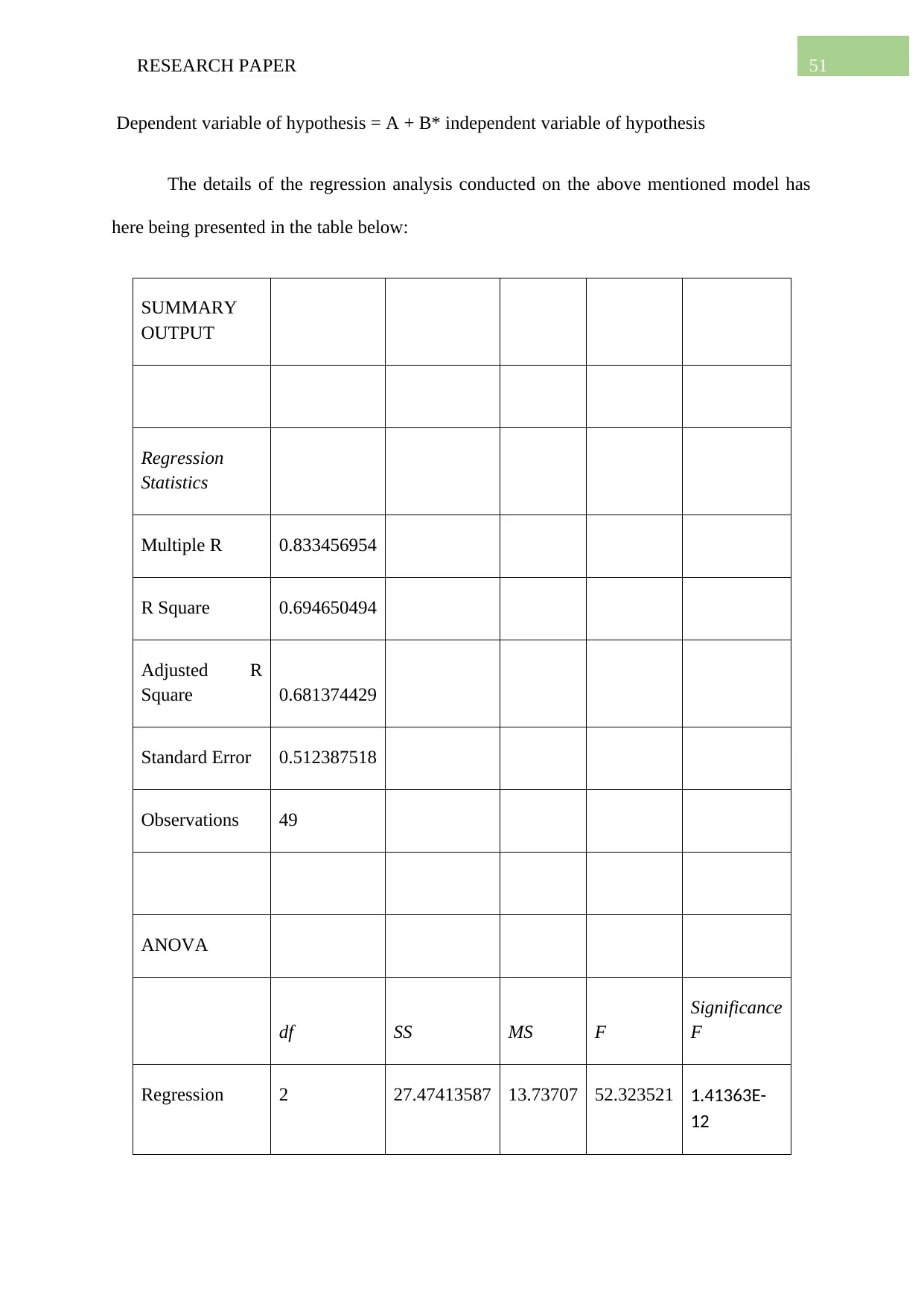
51RESEARCH PAPER
Dependent variable of hypothesis = A + B* independent variable of hypothesis
The details of the regression analysis conducted on the above mentioned model has
here being presented in the table below:
SUMMARY
OUTPUT
Regression
Statistics
Multiple R 0.833456954
R Square 0.694650494
Adjusted R
Square 0.681374429
Standard Error 0.512387518
Observations 49
ANOVA
df SS MS F
Significance
F
Regression 2 27.47413587 13.73707 52.323521 1.41363E-
12
Dependent variable of hypothesis = A + B* independent variable of hypothesis
The details of the regression analysis conducted on the above mentioned model has
here being presented in the table below:
SUMMARY
OUTPUT
Regression
Statistics
Multiple R 0.833456954
R Square 0.694650494
Adjusted R
Square 0.681374429
Standard Error 0.512387518
Observations 49
ANOVA
df SS MS F
Significance
F
Regression 2 27.47413587 13.73707 52.323521 1.41363E-
12
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
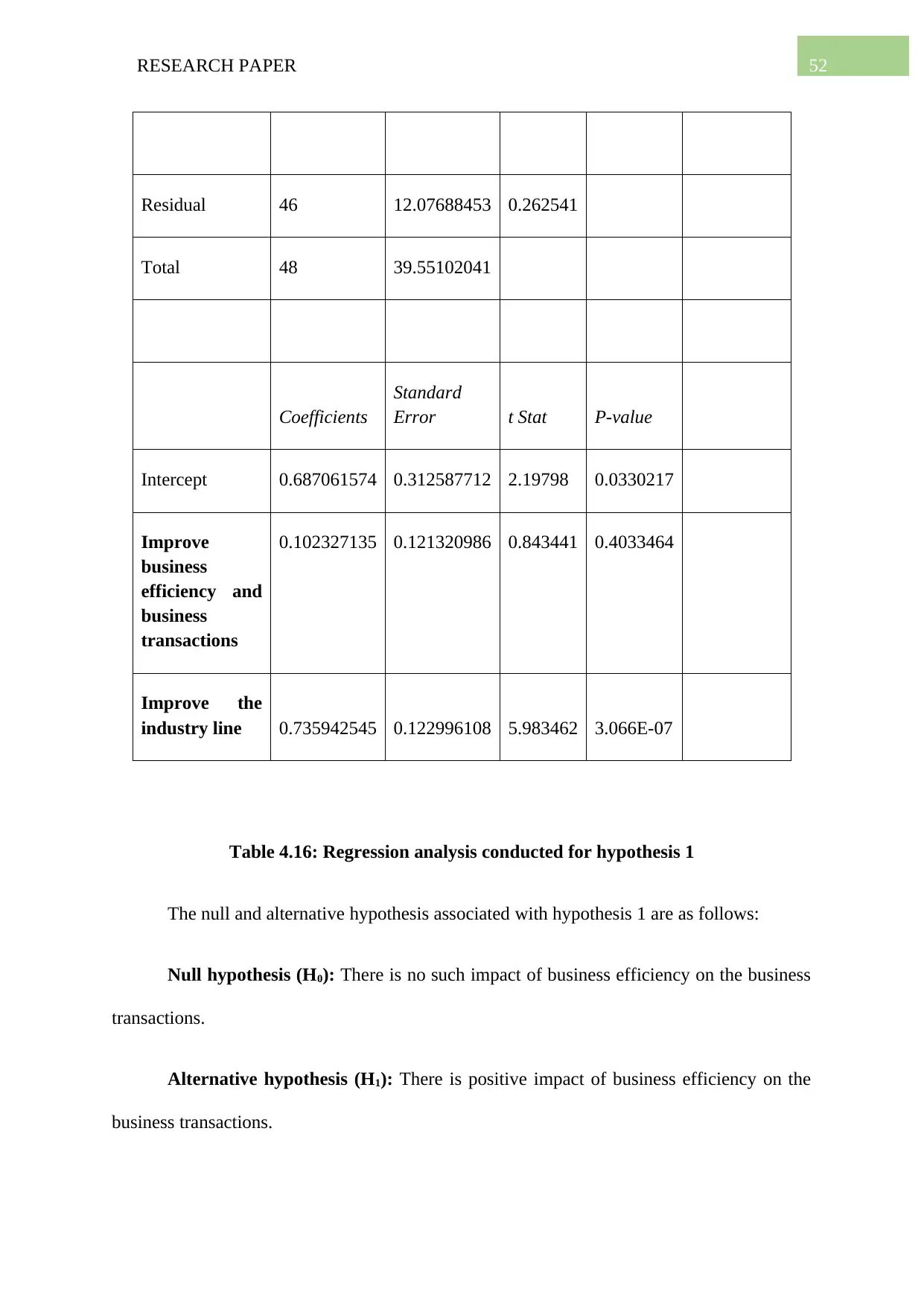
52RESEARCH PAPER
Residual 46 12.07688453 0.262541
Total 48 39.55102041
Coefficients
Standard
Error t Stat P-value
Intercept 0.687061574 0.312587712 2.19798 0.0330217
Improve
business
efficiency and
business
transactions
0.102327135 0.121320986 0.843441 0.4033464
Improve the
industry line 0.735942545 0.122996108 5.983462 3.066E-07
Table 4.16: Regression analysis conducted for hypothesis 1
The null and alternative hypothesis associated with hypothesis 1 are as follows:
Null hypothesis (H0): There is no such impact of business efficiency on the business
transactions.
Alternative hypothesis (H1): There is positive impact of business efficiency on the
business transactions.
Residual 46 12.07688453 0.262541
Total 48 39.55102041
Coefficients
Standard
Error t Stat P-value
Intercept 0.687061574 0.312587712 2.19798 0.0330217
Improve
business
efficiency and
business
transactions
0.102327135 0.121320986 0.843441 0.4033464
Improve the
industry line 0.735942545 0.122996108 5.983462 3.066E-07
Table 4.16: Regression analysis conducted for hypothesis 1
The null and alternative hypothesis associated with hypothesis 1 are as follows:
Null hypothesis (H0): There is no such impact of business efficiency on the business
transactions.
Alternative hypothesis (H1): There is positive impact of business efficiency on the
business transactions.
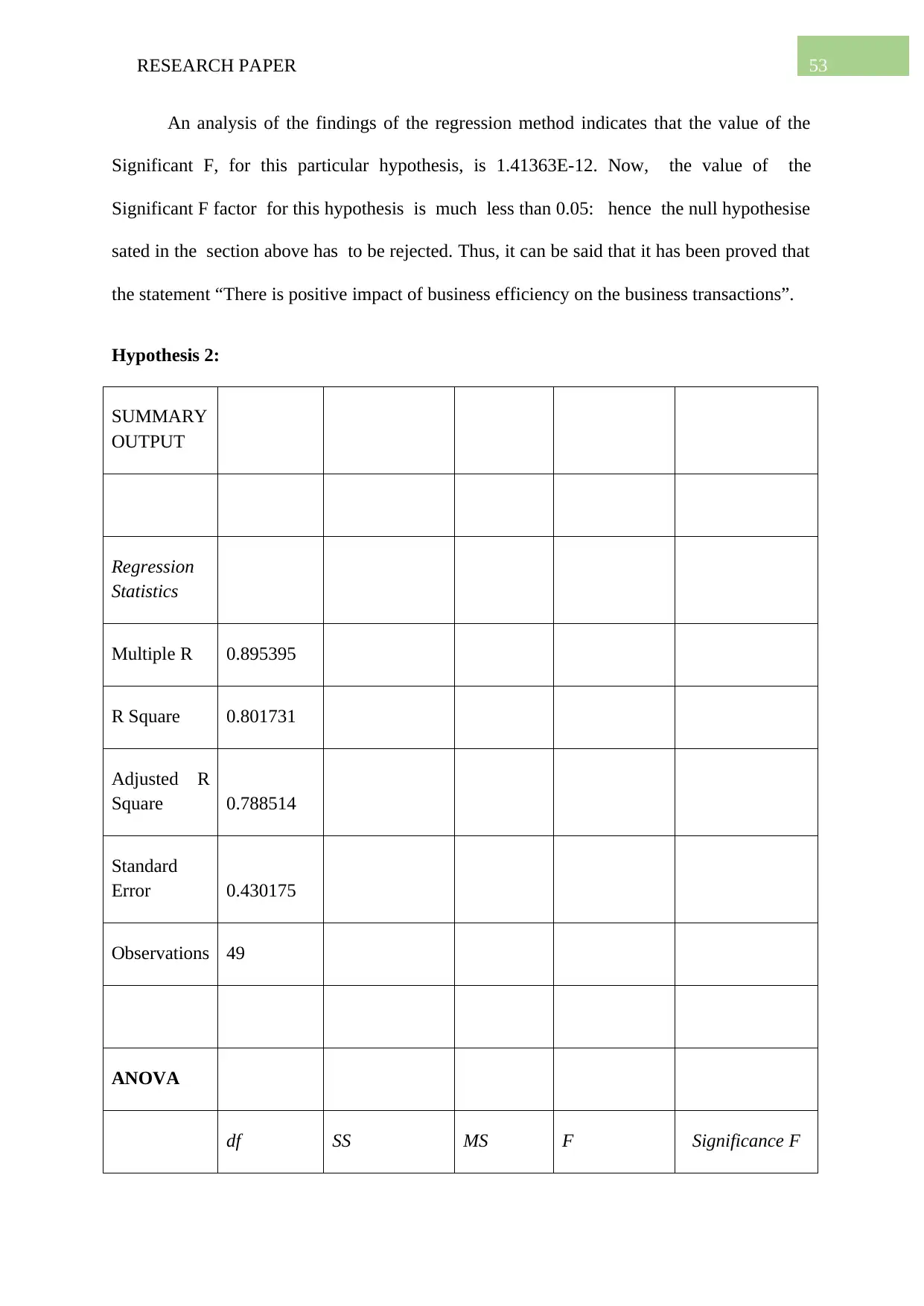
53RESEARCH PAPER
An analysis of the findings of the regression method indicates that the value of the
Significant F, for this particular hypothesis, is 1.41363E-12. Now, the value of the
Significant F factor for this hypothesis is much less than 0.05: hence the null hypothesise
sated in the section above has to be rejected. Thus, it can be said that it has been proved that
the statement “There is positive impact of business efficiency on the business transactions”.
Hypothesis 2:
SUMMARY
OUTPUT
Regression
Statistics
Multiple R 0.895395
R Square 0.801731
Adjusted R
Square 0.788514
Standard
Error 0.430175
Observations 49
ANOVA
df SS MS F Significance F
An analysis of the findings of the regression method indicates that the value of the
Significant F, for this particular hypothesis, is 1.41363E-12. Now, the value of the
Significant F factor for this hypothesis is much less than 0.05: hence the null hypothesise
sated in the section above has to be rejected. Thus, it can be said that it has been proved that
the statement “There is positive impact of business efficiency on the business transactions”.
Hypothesis 2:
SUMMARY
OUTPUT
Regression
Statistics
Multiple R 0.895395
R Square 0.801731
Adjusted R
Square 0.788514
Standard
Error 0.430175
Observations 49
ANOVA
df SS MS F Significance F
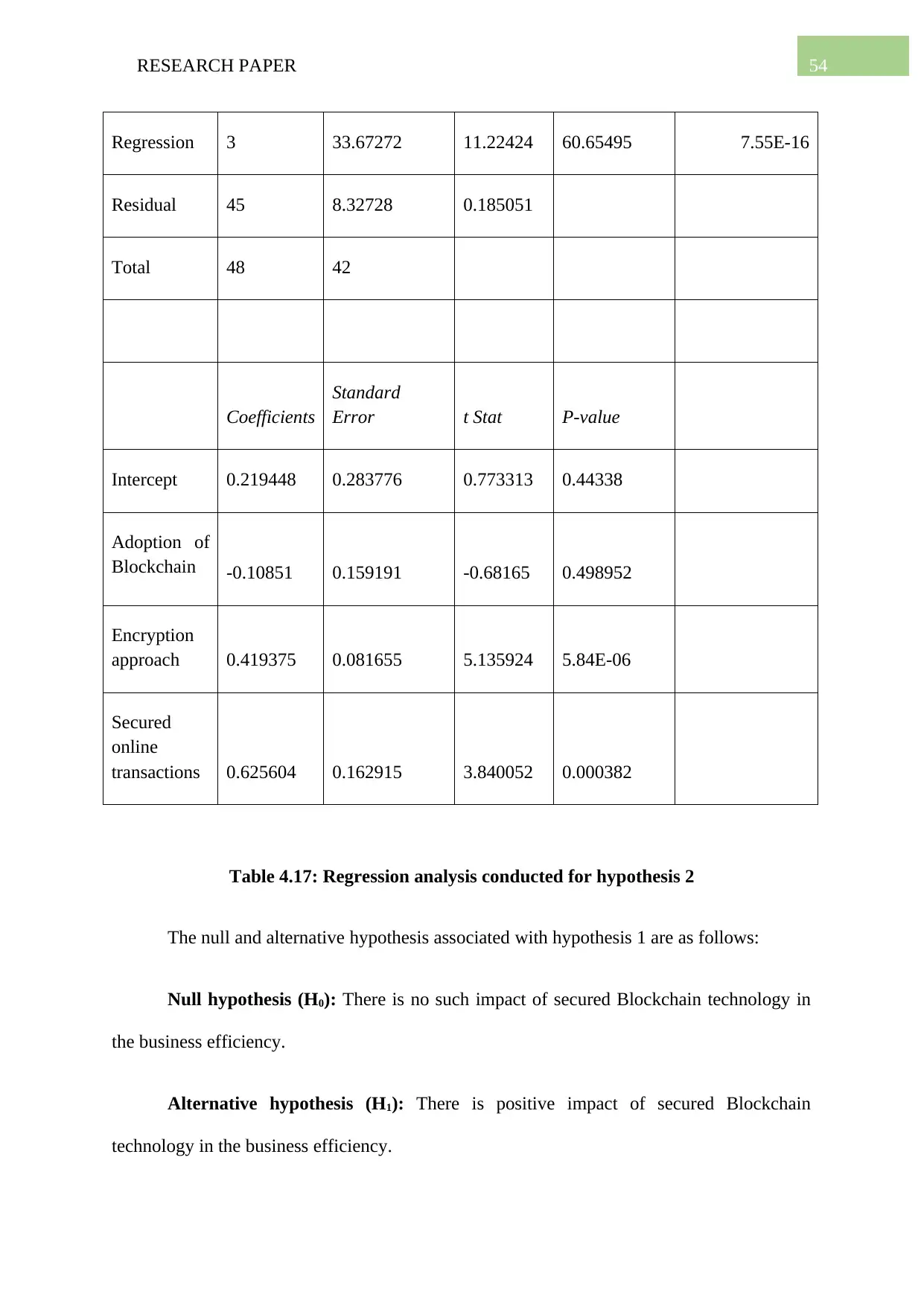
54RESEARCH PAPER
Regression 3 33.67272 11.22424 60.65495 7.55E-16
Residual 45 8.32728 0.185051
Total 48 42
Coefficients
Standard
Error t Stat P-value
Intercept 0.219448 0.283776 0.773313 0.44338
Adoption of
Blockchain -0.10851 0.159191 -0.68165 0.498952
Encryption
approach 0.419375 0.081655 5.135924 5.84E-06
Secured
online
transactions 0.625604 0.162915 3.840052 0.000382
Table 4.17: Regression analysis conducted for hypothesis 2
The null and alternative hypothesis associated with hypothesis 1 are as follows:
Null hypothesis (H0): There is no such impact of secured Blockchain technology in
the business efficiency.
Alternative hypothesis (H1): There is positive impact of secured Blockchain
technology in the business efficiency.
Regression 3 33.67272 11.22424 60.65495 7.55E-16
Residual 45 8.32728 0.185051
Total 48 42
Coefficients
Standard
Error t Stat P-value
Intercept 0.219448 0.283776 0.773313 0.44338
Adoption of
Blockchain -0.10851 0.159191 -0.68165 0.498952
Encryption
approach 0.419375 0.081655 5.135924 5.84E-06
Secured
online
transactions 0.625604 0.162915 3.840052 0.000382
Table 4.17: Regression analysis conducted for hypothesis 2
The null and alternative hypothesis associated with hypothesis 1 are as follows:
Null hypothesis (H0): There is no such impact of secured Blockchain technology in
the business efficiency.
Alternative hypothesis (H1): There is positive impact of secured Blockchain
technology in the business efficiency.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
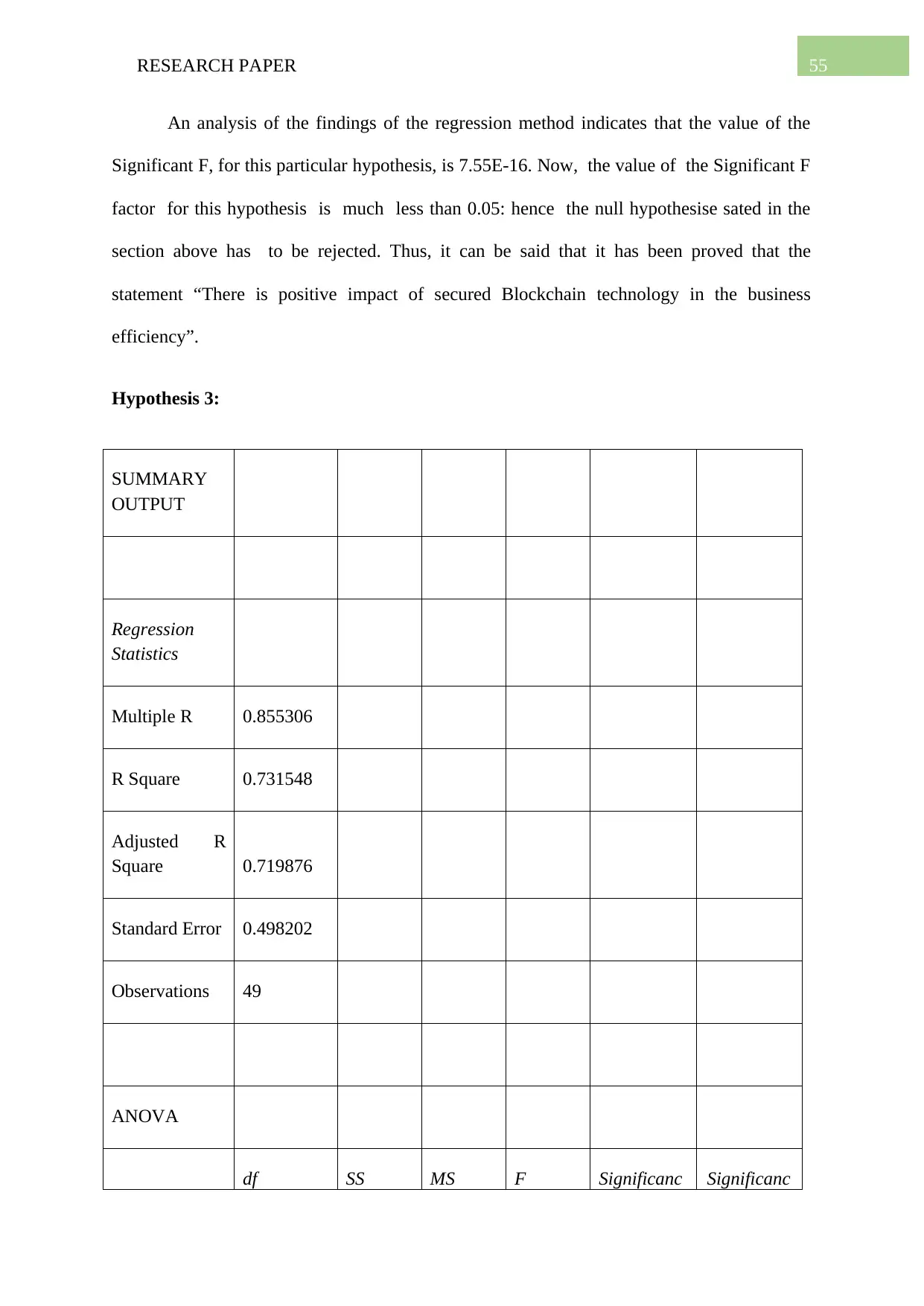
55RESEARCH PAPER
An analysis of the findings of the regression method indicates that the value of the
Significant F, for this particular hypothesis, is 7.55E-16. Now, the value of the Significant F
factor for this hypothesis is much less than 0.05: hence the null hypothesise sated in the
section above has to be rejected. Thus, it can be said that it has been proved that the
statement “There is positive impact of secured Blockchain technology in the business
efficiency”.
Hypothesis 3:
SUMMARY
OUTPUT
Regression
Statistics
Multiple R 0.855306
R Square 0.731548
Adjusted R
Square 0.719876
Standard Error 0.498202
Observations 49
ANOVA
df SS MS F Significanc Significanc
An analysis of the findings of the regression method indicates that the value of the
Significant F, for this particular hypothesis, is 7.55E-16. Now, the value of the Significant F
factor for this hypothesis is much less than 0.05: hence the null hypothesise sated in the
section above has to be rejected. Thus, it can be said that it has been proved that the
statement “There is positive impact of secured Blockchain technology in the business
efficiency”.
Hypothesis 3:
SUMMARY
OUTPUT
Regression
Statistics
Multiple R 0.855306
R Square 0.731548
Adjusted R
Square 0.719876
Standard Error 0.498202
Observations 49
ANOVA
df SS MS F Significanc Significanc
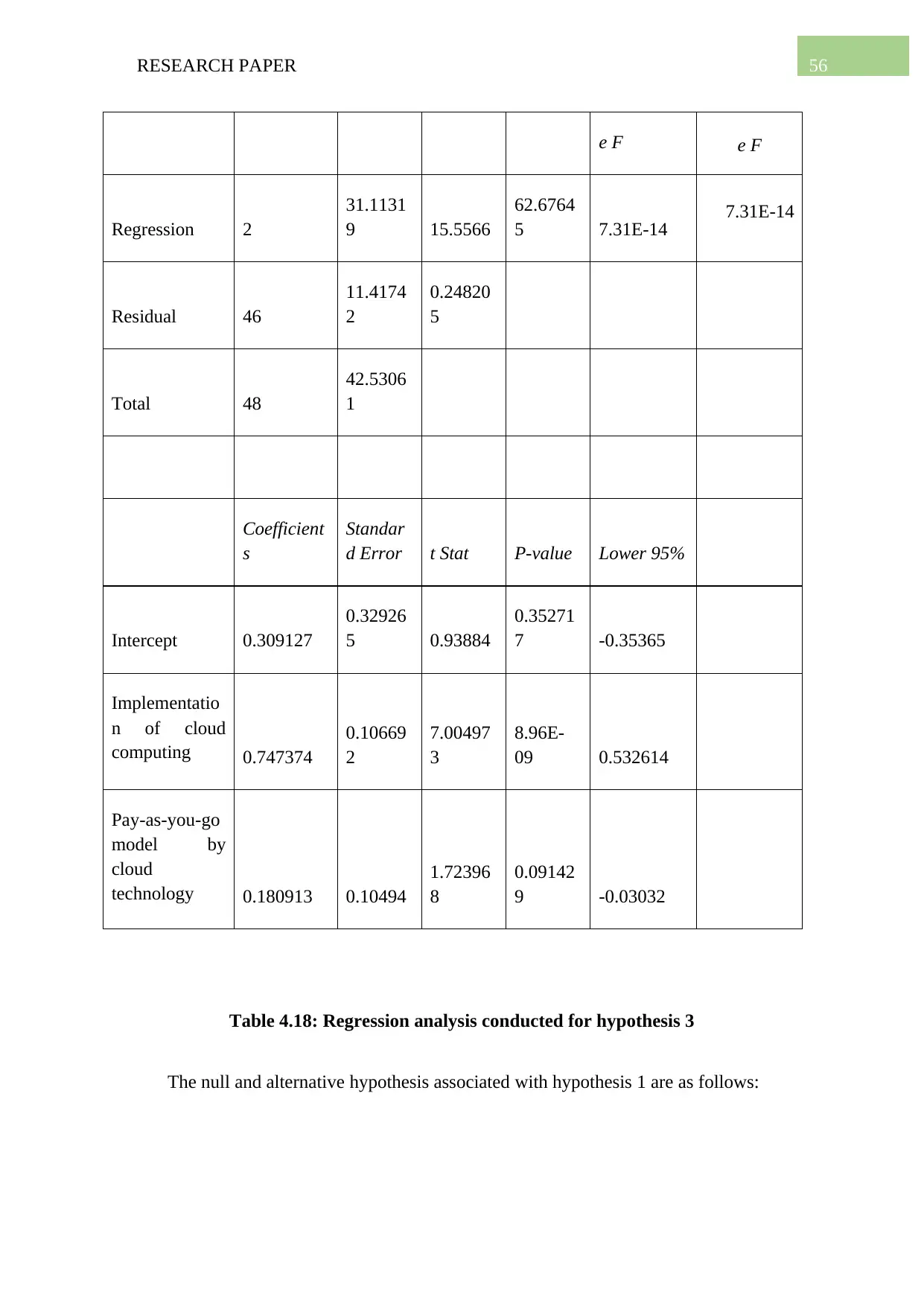
56RESEARCH PAPER
e F e F
Regression 2
31.1131
9 15.5566
62.6764
5 7.31E-14 7.31E-14
Residual 46
11.4174
2
0.24820
5
Total 48
42.5306
1
Coefficient
s
Standar
d Error t Stat P-value Lower 95%
Intercept 0.309127
0.32926
5 0.93884
0.35271
7 -0.35365
Implementatio
n of cloud
computing 0.747374
0.10669
2
7.00497
3
8.96E-
09 0.532614
Pay-as-you-go
model by
cloud
technology 0.180913 0.10494
1.72396
8
0.09142
9 -0.03032
Table 4.18: Regression analysis conducted for hypothesis 3
The null and alternative hypothesis associated with hypothesis 1 are as follows:
e F e F
Regression 2
31.1131
9 15.5566
62.6764
5 7.31E-14 7.31E-14
Residual 46
11.4174
2
0.24820
5
Total 48
42.5306
1
Coefficient
s
Standar
d Error t Stat P-value Lower 95%
Intercept 0.309127
0.32926
5 0.93884
0.35271
7 -0.35365
Implementatio
n of cloud
computing 0.747374
0.10669
2
7.00497
3
8.96E-
09 0.532614
Pay-as-you-go
model by
cloud
technology 0.180913 0.10494
1.72396
8
0.09142
9 -0.03032
Table 4.18: Regression analysis conducted for hypothesis 3
The null and alternative hypothesis associated with hypothesis 1 are as follows:

57RESEARCH PAPER
Null hypothesis (H0): There is no such impact of Blockchain technology in the cloud
computing.
Alternative hypothesis (H1): There is positive impact of Blockchain technology in
the cloud computing.
An analysis of the findings of the regression method indicates that the value of the
Significant F, for this particular hypothesis, is 7.31E-14. Now, the value of the Significant F
factor for this hypothesis is much less than 0.05: hence the null hypothesise sated in the
section above has to be rejected. Thus, it can be said that it has been proved that the
statement “There is positive impact of Blockchain technology in the cloud computing”.
4.4 Summary
From entire study, it is summarized that the researcher will highlight relationship
which are existed among the Blockchain technology as well as cloud computing. The entire
research findings are discussed based on the responses of selected respondents and their
understanding of impact of the Blockchain technology on cloud computing from business
perspective. From the primary research study, it is observed that there is high impact of the
Blockchain technology on cloud computing from business perspective. The entire research
study from this particular chapter, it is discussed that response of the employees at this level
provide effect on the Blockchain technology. The data collection method is tried to highlight
role played by the Blockchain technology into the cloud computing while it is conducted
from the business perspective. Quantitative data analysis is performed on collected data using
regression analysis to check validity as well as reliability of collected data.
Null hypothesis (H0): There is no such impact of Blockchain technology in the cloud
computing.
Alternative hypothesis (H1): There is positive impact of Blockchain technology in
the cloud computing.
An analysis of the findings of the regression method indicates that the value of the
Significant F, for this particular hypothesis, is 7.31E-14. Now, the value of the Significant F
factor for this hypothesis is much less than 0.05: hence the null hypothesise sated in the
section above has to be rejected. Thus, it can be said that it has been proved that the
statement “There is positive impact of Blockchain technology in the cloud computing”.
4.4 Summary
From entire study, it is summarized that the researcher will highlight relationship
which are existed among the Blockchain technology as well as cloud computing. The entire
research findings are discussed based on the responses of selected respondents and their
understanding of impact of the Blockchain technology on cloud computing from business
perspective. From the primary research study, it is observed that there is high impact of the
Blockchain technology on cloud computing from business perspective. The entire research
study from this particular chapter, it is discussed that response of the employees at this level
provide effect on the Blockchain technology. The data collection method is tried to highlight
role played by the Blockchain technology into the cloud computing while it is conducted
from the business perspective. Quantitative data analysis is performed on collected data using
regression analysis to check validity as well as reliability of collected data.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

58RESEARCH PAPER
References
Alvesson, M. and Sköldberg, K., 2017. Reflexive methodology: New vistas for qualitative
research. Sage.
Aste, T., Tasca, P. and Di Matteo, T., 2017. Blockchain technologies: The foreseeable impact
on society and industry. Computer, 50(9), pp.18-28.
Atlam, H.F., Alenezi, A., Alassafi, M.O. and Wills, G., 2018. Blockchain with Internet of
Things: Benefits, challenges, and future directions. International Journal of Intelligent
Systems and Applications, 10(6), pp.40-48.
Bresler, L. and Stake, R.E., 2017. Qualitative research methodology in music education.
In Critical Essays in Music Education (pp. 113-128). Routledge.
Brundo, R. and De Nicola, R., 2018. Blockchain-based decentralized cloud/fog solutions:
Challenges, opportunities, and standards. IEEE Communications Standards Magazine, 2(3),
pp.22-28.
Davcev, D., Kocarev, L., Carbone, A., Stankovski, V. and Mitresk, K., 2018. Blockchain-
based Distributed Cloud/Fog Platform for IoT Supply Chain Management.
Davidson, S., De Filippi, P. and Potts, J., 2016. Disrupting governance: The new institutional
economics of distributed ledger technology. Available at SSRN 2811995.
Deng, Z., Ren, Y., Liu, Y., Yin, X., Shen, Z. and Kim, H.J., 2019. Blockchain-Based Trusted
Electronic Records Preservation in Cloud Storage. Computers, Materials & Continua, 58(1),
pp.135-151.
References
Alvesson, M. and Sköldberg, K., 2017. Reflexive methodology: New vistas for qualitative
research. Sage.
Aste, T., Tasca, P. and Di Matteo, T., 2017. Blockchain technologies: The foreseeable impact
on society and industry. Computer, 50(9), pp.18-28.
Atlam, H.F., Alenezi, A., Alassafi, M.O. and Wills, G., 2018. Blockchain with Internet of
Things: Benefits, challenges, and future directions. International Journal of Intelligent
Systems and Applications, 10(6), pp.40-48.
Bresler, L. and Stake, R.E., 2017. Qualitative research methodology in music education.
In Critical Essays in Music Education (pp. 113-128). Routledge.
Brundo, R. and De Nicola, R., 2018. Blockchain-based decentralized cloud/fog solutions:
Challenges, opportunities, and standards. IEEE Communications Standards Magazine, 2(3),
pp.22-28.
Davcev, D., Kocarev, L., Carbone, A., Stankovski, V. and Mitresk, K., 2018. Blockchain-
based Distributed Cloud/Fog Platform for IoT Supply Chain Management.
Davidson, S., De Filippi, P. and Potts, J., 2016. Disrupting governance: The new institutional
economics of distributed ledger technology. Available at SSRN 2811995.
Deng, Z., Ren, Y., Liu, Y., Yin, X., Shen, Z. and Kim, H.J., 2019. Blockchain-Based Trusted
Electronic Records Preservation in Cloud Storage. Computers, Materials & Continua, 58(1),
pp.135-151.

59RESEARCH PAPER
Dorri, A., Kanhere, S.S. and Jurdak, R., 2016. Blockchain in internet of things: challenges
and solutions. arXiv preprint arXiv:1608.05187.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Jiao, Y., Wang, P., Niyato, D. and Suankaewmanee, K., 2018. Auction Mechanisms in
Cloud/Fog Computing Resource Allocation for Public Blockchain Networks. arXiv preprint
arXiv:1804.09961.
Kumar, R., 2019. Research methodology: A step-by-step guide for beginners. Sage
Publications Limited.
Kuvvarapu, B.R.P., 2018. ANALYSIS AND APPLICATION OF BLOCKCHAIN IN
CLOUD ERP. STEP into the FUTURE, p.12.
Li, J., Liu, Z., Chen, L., Chen, P. and Wu, J., 2017, December. Blockchain-based security
architecture for distributed cloud storage. In 2017 IEEE International Symposium on Parallel
and Distributed Processing with Applications and 2017 IEEE International Conference on
Ubiquitous Computing and Communications (ISPA/IUCC) (pp. 408-411). IEEE.
Liang, X., Shetty, S., Tosh, D., Kamhoua, C., Kwiat, K. and Njilla, L., 2017, May. Provchain:
A blockchain-based data provenance architecture in cloud environment with enhanced
privacy and availability. In Proceedings of the 17th IEEE/ACM international symposium on
cluster, cloud and grid computing(pp. 468-477). IEEE Press.
Liu, S. and He, S., 2019, January. Application of Block Chaining Technology in Finance and
Accounting Field. In 2019 International Conference on Intelligent Transportation, Big Data
& Smart City (ICITBS) (pp. 342-344). IEEE.
Dorri, A., Kanhere, S.S. and Jurdak, R., 2016. Blockchain in internet of things: challenges
and solutions. arXiv preprint arXiv:1608.05187.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Jiao, Y., Wang, P., Niyato, D. and Suankaewmanee, K., 2018. Auction Mechanisms in
Cloud/Fog Computing Resource Allocation for Public Blockchain Networks. arXiv preprint
arXiv:1804.09961.
Kumar, R., 2019. Research methodology: A step-by-step guide for beginners. Sage
Publications Limited.
Kuvvarapu, B.R.P., 2018. ANALYSIS AND APPLICATION OF BLOCKCHAIN IN
CLOUD ERP. STEP into the FUTURE, p.12.
Li, J., Liu, Z., Chen, L., Chen, P. and Wu, J., 2017, December. Blockchain-based security
architecture for distributed cloud storage. In 2017 IEEE International Symposium on Parallel
and Distributed Processing with Applications and 2017 IEEE International Conference on
Ubiquitous Computing and Communications (ISPA/IUCC) (pp. 408-411). IEEE.
Liang, X., Shetty, S., Tosh, D., Kamhoua, C., Kwiat, K. and Njilla, L., 2017, May. Provchain:
A blockchain-based data provenance architecture in cloud environment with enhanced
privacy and availability. In Proceedings of the 17th IEEE/ACM international symposium on
cluster, cloud and grid computing(pp. 468-477). IEEE Press.
Liu, S. and He, S., 2019, January. Application of Block Chaining Technology in Finance and
Accounting Field. In 2019 International Conference on Intelligent Transportation, Big Data
& Smart City (ICITBS) (pp. 342-344). IEEE.

60RESEARCH PAPER
Mackey, A. and Gass, S.M., 2015. Second language research: Methodology and design.
Routledge.
Mills, D.C., Wang, K., Malone, B., Ravi, A., Marquardt, J., Badev, A.I., Brezinski, T., Fahy,
L., Liao, K., Kargenian, V. and Ellithorpe, M., 2016. Distributed ledger technology in
payments, clearing, and settlement.
Miraz, M.H. and Ali, M., 2018. Applications of blockchain technology beyond
cryptocurrency. arXiv preprint arXiv:1801.03528.
Novais, L., Maqueira, J.M. and Ortiz-Bas, Á., 2019. A systematic literature review of cloud
computing use in supply chain integration. Computers & Industrial Engineering, 129,
pp.296-314.
Riasanow, T., Burckhardt, F., Soto Setzke, D., Böhm, M. and Krcmar, H., 2018. The Generic
Blockchain Ecosystem and its Strategic Implications.
Samaniego, M. and Deters, R., 2016, December. Blockchain as a Service for IoT. In 2016
IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing
and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing
(CPSCom) and IEEE Smart Data (SmartData) (pp. 433-436). IEEE.
Shafagh, H., Burkhalter, L., Hithnawi, A. and Duquennoy, S., 2017, November. Towards
blockchain-based auditable storage and sharing of iot data. In Proceedings of the 2017 on
Cloud Computing Security Workshop (pp. 45-50). ACM.
Sharma, P.K., Moon, S.Y. and Park, J.H., 2017. Block-VN: A Distributed Blockchain Based
Vehicular Network Architecture in Smart City. JIPS, 13(1), pp.184-195.
Silverman, D. ed., 2016. Qualitative research. Sage.
Mackey, A. and Gass, S.M., 2015. Second language research: Methodology and design.
Routledge.
Mills, D.C., Wang, K., Malone, B., Ravi, A., Marquardt, J., Badev, A.I., Brezinski, T., Fahy,
L., Liao, K., Kargenian, V. and Ellithorpe, M., 2016. Distributed ledger technology in
payments, clearing, and settlement.
Miraz, M.H. and Ali, M., 2018. Applications of blockchain technology beyond
cryptocurrency. arXiv preprint arXiv:1801.03528.
Novais, L., Maqueira, J.M. and Ortiz-Bas, Á., 2019. A systematic literature review of cloud
computing use in supply chain integration. Computers & Industrial Engineering, 129,
pp.296-314.
Riasanow, T., Burckhardt, F., Soto Setzke, D., Böhm, M. and Krcmar, H., 2018. The Generic
Blockchain Ecosystem and its Strategic Implications.
Samaniego, M. and Deters, R., 2016, December. Blockchain as a Service for IoT. In 2016
IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing
and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing
(CPSCom) and IEEE Smart Data (SmartData) (pp. 433-436). IEEE.
Shafagh, H., Burkhalter, L., Hithnawi, A. and Duquennoy, S., 2017, November. Towards
blockchain-based auditable storage and sharing of iot data. In Proceedings of the 2017 on
Cloud Computing Security Workshop (pp. 45-50). ACM.
Sharma, P.K., Moon, S.Y. and Park, J.H., 2017. Block-VN: A Distributed Blockchain Based
Vehicular Network Architecture in Smart City. JIPS, 13(1), pp.184-195.
Silverman, D. ed., 2016. Qualitative research. Sage.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

61RESEARCH PAPER
Singh, I. and Lee, S.W., 2017, November. Comparative requirements analysis for the
feasibility of blockchain for secure cloud. In Asia Pacific Requirements Engeneering
Conference (pp. 57-72). Springer, Singapore.
Taghavi, M., Bentahar, J., Otrok, H. and Bakhtiyari, K., 2018, November. Cloudchain: A
Blockchain-Based Coopetition Differential Game Model for Cloud Computing.
In International Conference on Service-Oriented Computing (pp. 146-161). Springer, Cham.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research
methods: A guidebook and resource. John Wiley & Sons.
Tosh, D.K., Shetty, S., Liang, X., Kamhoua, C. and Njilla, L., 2017, October. Consensus
protocols for blockchain-based data provenance: Challenges and opportunities. In 2017 IEEE
8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference
(UEMCON) (pp. 469-474). IEEE.
Tosh, D.K., Shetty, S., Liang, X., Kamhoua, C.A., Kwiat, K.A. and Njilla, L., 2017, May.
Security implications of blockchain cloud with analysis of block withholding attack. In
Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid
Computing (pp. 458-467). IEEE Press.
Tosh, D.K., Shetty, S., Liang, X., Kamhoua, C.A., Kwiat, K.A. and Njilla, L., 2017, May.
Security implications of blockchain cloud with analysis of block withholding attack.
In Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid
Computing (pp. 458-467). IEEE Press.
Treiblmaier, H. and Beck, R. eds., 2019. Business Transformation Through Blockchain.
Springer International Publishing.
Singh, I. and Lee, S.W., 2017, November. Comparative requirements analysis for the
feasibility of blockchain for secure cloud. In Asia Pacific Requirements Engeneering
Conference (pp. 57-72). Springer, Singapore.
Taghavi, M., Bentahar, J., Otrok, H. and Bakhtiyari, K., 2018, November. Cloudchain: A
Blockchain-Based Coopetition Differential Game Model for Cloud Computing.
In International Conference on Service-Oriented Computing (pp. 146-161). Springer, Cham.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research
methods: A guidebook and resource. John Wiley & Sons.
Tosh, D.K., Shetty, S., Liang, X., Kamhoua, C. and Njilla, L., 2017, October. Consensus
protocols for blockchain-based data provenance: Challenges and opportunities. In 2017 IEEE
8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference
(UEMCON) (pp. 469-474). IEEE.
Tosh, D.K., Shetty, S., Liang, X., Kamhoua, C.A., Kwiat, K.A. and Njilla, L., 2017, May.
Security implications of blockchain cloud with analysis of block withholding attack. In
Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid
Computing (pp. 458-467). IEEE Press.
Tosh, D.K., Shetty, S., Liang, X., Kamhoua, C.A., Kwiat, K.A. and Njilla, L., 2017, May.
Security implications of blockchain cloud with analysis of block withholding attack.
In Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid
Computing (pp. 458-467). IEEE Press.
Treiblmaier, H. and Beck, R. eds., 2019. Business Transformation Through Blockchain.
Springer International Publishing.

62RESEARCH PAPER
Uchibayashi, T., Apduhan, B., Suganuma, T. and Hiji, M., 2018, May. Toward a Secure VM
Migration Control Mechanism Using Blockchain Technique for Cloud Computing
Environment. In International Conference on Computational Science and Its
Applications (pp. 177-186). Springer, Cham.
Viriyasitavat, W., Da Xu, L., Bi, Z. and Sapsomboon, A., 2018. Blockchain-based business
process management (BPM) framework for service composition in industry 4.0. Journal of
Intelligent Manufacturing, pp.1-12.
Xiong, Z., Zhang, Y., Niyato, D., Wang, P. and Han, Z., 2018. When mobile blockchain
meets edge computing. IEEE Communications Magazine, 56(8), pp.33-39.
Yeniyurt, S., Wu, F., Kim, D. and Cavusgil, S.T., 2019. Information technology resources,
innovativeness, and supply chain capabilities as drivers of business performance: A
retrospective and future research directions. Industrial Marketing Management.
Zhao, Y. and Duncan, B., 2018, July. The Impact of Crypto-Currency Risks on the Use of
Blockchain for Cloud Security and Privacy. In 2018 International Conference on High
Performance Computing & Simulation (HPCS) (pp. 677-684). IEEE.
Zhao, Y. and Duncan, B., 2018. Could Block Chain Technology Help Resolve the Cloud
Forensic Problem?. Cloud Computing.
Zheng, X., Mukkamala, R.R., Vatrapu, R. and Ordieres-Mere, J., 2018, September.
Blockchain-based Personal Health Data Sharing System Using Cloud Storage. In 2018 IEEE
20th International Conference on e-Health Networking, Applications and Services
(Healthcom) (pp. 1-6). IEEE.
Uchibayashi, T., Apduhan, B., Suganuma, T. and Hiji, M., 2018, May. Toward a Secure VM
Migration Control Mechanism Using Blockchain Technique for Cloud Computing
Environment. In International Conference on Computational Science and Its
Applications (pp. 177-186). Springer, Cham.
Viriyasitavat, W., Da Xu, L., Bi, Z. and Sapsomboon, A., 2018. Blockchain-based business
process management (BPM) framework for service composition in industry 4.0. Journal of
Intelligent Manufacturing, pp.1-12.
Xiong, Z., Zhang, Y., Niyato, D., Wang, P. and Han, Z., 2018. When mobile blockchain
meets edge computing. IEEE Communications Magazine, 56(8), pp.33-39.
Yeniyurt, S., Wu, F., Kim, D. and Cavusgil, S.T., 2019. Information technology resources,
innovativeness, and supply chain capabilities as drivers of business performance: A
retrospective and future research directions. Industrial Marketing Management.
Zhao, Y. and Duncan, B., 2018, July. The Impact of Crypto-Currency Risks on the Use of
Blockchain for Cloud Security and Privacy. In 2018 International Conference on High
Performance Computing & Simulation (HPCS) (pp. 677-684). IEEE.
Zhao, Y. and Duncan, B., 2018. Could Block Chain Technology Help Resolve the Cloud
Forensic Problem?. Cloud Computing.
Zheng, X., Mukkamala, R.R., Vatrapu, R. and Ordieres-Mere, J., 2018, September.
Blockchain-based Personal Health Data Sharing System Using Cloud Storage. In 2018 IEEE
20th International Conference on e-Health Networking, Applications and Services
(Healthcom) (pp. 1-6). IEEE.

63RESEARCH PAPER
Appendix
Appendix
1 out of 64
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





