Research Proposal: Cyber-Security Threats, Challenges, and Solutions
VerifiedAdded on 2022/11/26
|12
|2351
|492
Project
AI Summary
This research proposal delves into the critical domain of cyber-security, specifically focusing on the multifaceted challenges posed by internet terrorism. The study aims to identify the problems associated with combating internet terrorism, evaluate governmental strategies to mitigate cyber-security threats, and propose effective security solutions. The proposal includes a literature review, theoretical framework, and a detailed research methodology employing secondary research. The research schedule outlines the project's timeline, from topic selection to final submission. The expected outcomes will provide insights into current efforts to address cyber-security issues and highlight key areas requiring attention, including the reduction of internet security threats. The study also aims to offer a comprehensive understanding of the concerns and methodologies used in countering these threats, ultimately contributing to enhanced cyber-security measures.

Running head: RESEARCH PROPOSAL
Cyber-Security
[Name of the Student]
[Name of the University]
[Author note]
Cyber-Security
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RESEARCH PROPOSAL
Abstract:
The internet along with the foundations has turned out to be helpless against the different kind of
dangers which are being faced from the physical as well as the digital dangers and perils. The
research questions summarize various types of problems which are caused due to internet
terrorism. Securing the internet is very hard and the reason behind this the existence of different
components which includes the capacity of malignant on-screen characters so as to work from
anywhere, besides this the linkages which is seen to be existing amongst the internet and the
physical frameworks which are progressively being subjected to the advanced digital
interruptions which in turn is responsible for putting forward of different kind of dangers. The
purpose of this research study is to determine the ways the cyber-security has turned out to be
one of the major concerns of today’s world. For this reason it is very essential to make sure that
all people associated with it are being brought together so as to look out for proper solutions.
Abstract:
The internet along with the foundations has turned out to be helpless against the different kind of
dangers which are being faced from the physical as well as the digital dangers and perils. The
research questions summarize various types of problems which are caused due to internet
terrorism. Securing the internet is very hard and the reason behind this the existence of different
components which includes the capacity of malignant on-screen characters so as to work from
anywhere, besides this the linkages which is seen to be existing amongst the internet and the
physical frameworks which are progressively being subjected to the advanced digital
interruptions which in turn is responsible for putting forward of different kind of dangers. The
purpose of this research study is to determine the ways the cyber-security has turned out to be
one of the major concerns of today’s world. For this reason it is very essential to make sure that
all people associated with it are being brought together so as to look out for proper solutions.

2RESEARCH PROPOSAL
Table of Contents
1. Introduction..................................................................................................................................3
1.1 Statement of research question..............................................................................................3
1.2 Background and contextual materials....................................................................................4
1.3 Purpose statement and hypothesis.........................................................................................4
2. Literature review..........................................................................................................................5
3. Theoretical Framework................................................................................................................6
4. Research methodology.................................................................................................................6
5. Research Schedule.......................................................................................................................7
6. Conclusion...................................................................................................................................8
Reference:......................................................................................................................................10
Table of Contents
1. Introduction..................................................................................................................................3
1.1 Statement of research question..............................................................................................3
1.2 Background and contextual materials....................................................................................4
1.3 Purpose statement and hypothesis.........................................................................................4
2. Literature review..........................................................................................................................5
3. Theoretical Framework................................................................................................................6
4. Research methodology.................................................................................................................6
5. Research Schedule.......................................................................................................................7
6. Conclusion...................................................................................................................................8
Reference:......................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RESEARCH PROPOSAL
1. Introduction
The internet along with the foundations has turned out to be helpless against the different
kind of dangers which are being faced from the physical as well as the digital dangers and perils.
The modern day digital onscreen characters along with the country states abuse the
vulnerabilities so as to take the data and the cash which are responsible for the creation of the
capacities to upset pulverize and undermine the conveyances of the key administrators. Besides
this a scope of the customary violation is being presently executed throughout the internet. This
in turn has been associated with the incorporation of the creation along with the appropriation of
the kid erotic entertainment and the kid misuse schemes, being responsible for keeping the
money as well as the budgetary misrepresentation, infringement of the licensed innovations and
various kinds of violations all of which are having generous human and monetary results.
1.1 Statement of research question
The primary question which is to be undertaken for the specific research is associated
with including:
a. What are types of problems which seen to existing while combating with the internet
Terrorism?
b. What are governments doing so as to minimize this type of problems related to cyber-
security and the attacks which are associated with it?
c. What are strategies which have been put in place so as to combat the different problems
related to cyber security?
1. Introduction
The internet along with the foundations has turned out to be helpless against the different
kind of dangers which are being faced from the physical as well as the digital dangers and perils.
The modern day digital onscreen characters along with the country states abuse the
vulnerabilities so as to take the data and the cash which are responsible for the creation of the
capacities to upset pulverize and undermine the conveyances of the key administrators. Besides
this a scope of the customary violation is being presently executed throughout the internet. This
in turn has been associated with the incorporation of the creation along with the appropriation of
the kid erotic entertainment and the kid misuse schemes, being responsible for keeping the
money as well as the budgetary misrepresentation, infringement of the licensed innovations and
various kinds of violations all of which are having generous human and monetary results.
1.1 Statement of research question
The primary question which is to be undertaken for the specific research is associated
with including:
a. What are types of problems which seen to existing while combating with the internet
Terrorism?
b. What are governments doing so as to minimize this type of problems related to cyber-
security and the attacks which are associated with it?
c. What are strategies which have been put in place so as to combat the different problems
related to cyber security?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RESEARCH PROPOSAL
The research questions summarize various types of problems which are caused due to
internet terrorism. The governments are performed to minimize the problems related to the
cyber-security and the attack. In order to overcome with the strategies, it is required to
implement various security solutions against the identified cyber security problems.
1.2 Background and contextual materials
Securing the internet is very hard and the reason behind this the existence of different
components which includes the capacity of malignant on-screen characters so as to work from
anywhere, besides this the linkages which is seen to be existing amongst the internet and the
physical frameworks which are progressively being subjected to the advanced digital
interruptions which in turn is responsible for putting forward of different kind of dangers. With
the progress in the coordination of the innovation with the physical framework operations has
been responsible for increasing the danger for a wide scale or for the occasions which are having
high outcomes which are capable of bringing about of the damage or disturbed administrations
upon which the economy as well as the everyday lives of the huge number of peoples are
dependent. By considering the danger and the potential results of the digital occasions the
reinforcement of the security along with the vulnerability of the internet has seen out to be
turning in a vital security mission in every aspect.
1.3 Purpose statement and hypothesis
The purpose of this research study is to determine the ways the cyber-security has turned
out to be one of the major concerns of today’s world. For this reason it is very essential to make
sure that all people associated with it are being brought together so as to look out for proper
solutions. The research hypothesis is:
The research questions summarize various types of problems which are caused due to
internet terrorism. The governments are performed to minimize the problems related to the
cyber-security and the attack. In order to overcome with the strategies, it is required to
implement various security solutions against the identified cyber security problems.
1.2 Background and contextual materials
Securing the internet is very hard and the reason behind this the existence of different
components which includes the capacity of malignant on-screen characters so as to work from
anywhere, besides this the linkages which is seen to be existing amongst the internet and the
physical frameworks which are progressively being subjected to the advanced digital
interruptions which in turn is responsible for putting forward of different kind of dangers. With
the progress in the coordination of the innovation with the physical framework operations has
been responsible for increasing the danger for a wide scale or for the occasions which are having
high outcomes which are capable of bringing about of the damage or disturbed administrations
upon which the economy as well as the everyday lives of the huge number of peoples are
dependent. By considering the danger and the potential results of the digital occasions the
reinforcement of the security along with the vulnerability of the internet has seen out to be
turning in a vital security mission in every aspect.
1.3 Purpose statement and hypothesis
The purpose of this research study is to determine the ways the cyber-security has turned
out to be one of the major concerns of today’s world. For this reason it is very essential to make
sure that all people associated with it are being brought together so as to look out for proper
solutions. The research hypothesis is:

5RESEARCH PROPOSAL
H1: There is high impact of cyber security issues on the business organization.
2. Literature review
Cyber security can be classified into two types for example the attacks which ate
associated with including the actions which are targeted for destroying the cyber system. Along
with this there are also actions which are associated with trying for using the cyber infrastructure
in an unlawful manner which is done without creation of any kind of compromise or destruction
to the cyber infrastructure. Whereas the other form is associated with including intrusions which
is considered to be a form of cyber attack which might not be associated with leading to an
instant effect upon the functioning of the cyber systems and this type of intrusion might be
responsible for making of contributions in the destruction of the entire systems on a particular
computer.
Internet is presently seen to be secured by means of defensive strategies as well as by
private regulatory activities and different type of gl0bal regulation and corporations. Information
is considered to one of the most essential asset of any individual or country or organization. For
the purpose of ensuring safety of an individual who is associated with the usage of a computer
system or network, proving protection against any kind of unauthorized access from numerous
resources is one of the important factors and besides this accounts are also to be secured by
means of encryption so as to stop any kind of illegal access.
The exploitation of the cyber is associated with constituting of the usage of the internet
together with the other cyber systems so as to carry out different type of frauds as well as for
H1: There is high impact of cyber security issues on the business organization.
2. Literature review
Cyber security can be classified into two types for example the attacks which ate
associated with including the actions which are targeted for destroying the cyber system. Along
with this there are also actions which are associated with trying for using the cyber infrastructure
in an unlawful manner which is done without creation of any kind of compromise or destruction
to the cyber infrastructure. Whereas the other form is associated with including intrusions which
is considered to be a form of cyber attack which might not be associated with leading to an
instant effect upon the functioning of the cyber systems and this type of intrusion might be
responsible for making of contributions in the destruction of the entire systems on a particular
computer.
Internet is presently seen to be secured by means of defensive strategies as well as by
private regulatory activities and different type of gl0bal regulation and corporations. Information
is considered to one of the most essential asset of any individual or country or organization. For
the purpose of ensuring safety of an individual who is associated with the usage of a computer
system or network, proving protection against any kind of unauthorized access from numerous
resources is one of the important factors and besides this accounts are also to be secured by
means of encryption so as to stop any kind of illegal access.
The exploitation of the cyber is associated with constituting of the usage of the internet
together with the other cyber systems so as to carry out different type of frauds as well as for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RESEARCH PROPOSAL
training and recruiting terrorists along with violating the copyrights which are responsible for
limiting the illegal distribution of the various kind of information without any kind of
authorization of the authors.
The next section will demonstrate the methods and tools which are used to collect data
based on the selected research topic.
3. Theoretical Framework
It is also essential to makes sure that the loopholes which are invaded by the
cybercriminals are kept confidential along with making sure the hidden security weaknesses are
being learnt and understood in a proper way. So from this the research statement which can be
formulated is: For the purpose of mitigating the problems which are caused because of the rise in
terrorism and the related activities, the research has been entirely aimed at understanding the
strategies which might be used for the purpose of diminishing the problems which are already
existing along with the after effects of the internet terrorism activities.
4. Research methodology
The process of research is conducted by means of two different methods which includes
the primary research method and the secondary research method. The research which is to be
conducted here would be associated with employing the secondary research method and the
reason behind this it is associated with providing of a better understanding and the outcomes
which would be obtained would be mostly accurate. For conducting research information is to be
generated from different local as well as national government websites and along with this
different academic journals are also to be used along with books and newspaper articles. The tool
training and recruiting terrorists along with violating the copyrights which are responsible for
limiting the illegal distribution of the various kind of information without any kind of
authorization of the authors.
The next section will demonstrate the methods and tools which are used to collect data
based on the selected research topic.
3. Theoretical Framework
It is also essential to makes sure that the loopholes which are invaded by the
cybercriminals are kept confidential along with making sure the hidden security weaknesses are
being learnt and understood in a proper way. So from this the research statement which can be
formulated is: For the purpose of mitigating the problems which are caused because of the rise in
terrorism and the related activities, the research has been entirely aimed at understanding the
strategies which might be used for the purpose of diminishing the problems which are already
existing along with the after effects of the internet terrorism activities.
4. Research methodology
The process of research is conducted by means of two different methods which includes
the primary research method and the secondary research method. The research which is to be
conducted here would be associated with employing the secondary research method and the
reason behind this it is associated with providing of a better understanding and the outcomes
which would be obtained would be mostly accurate. For conducting research information is to be
generated from different local as well as national government websites and along with this
different academic journals are also to be used along with books and newspaper articles. The tool
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RESEARCH PROPOSAL
which is to be included in the plan for conducting the research is the Google Scholar Database on
the different kind of cybercrimes.
The primary method of research might be associated with putting forward of different
kind of disadvantages such as usage of large datasets would be responsible for consuming a huge
amount of time. In addition to this the respondents might be associated with interpreting the
questions in a different manner which in turn would be associated with making the process of
comparing the answers very difficult. Besides this in a primary research it is also very difficult to
check if the respondents are honestly responding or not. In addition to this there is an over
reliance upon the statistical data in the primary research methodology which initially makes it
losing the individual meaning and the data. For this reason the secondary research methodology
is to be used.
5. Research Schedule
Task Mode Task Name Duration Start Finish Predecessors
Auto
Scheduled Research Proposal 76 days Mon 20-05-
19
Mon 02-09-
19
Auto
Scheduled Selection of the Topic 16 days Mon 20-05-
19
Mon 10-06-
19
Auto
Scheduled Background Research 3 days Tue 03-09-
19
Thu 05-09-
19 1
Auto
Scheduled
Research Question
Development 6 days Fri 06-09-19 Fri 13-09-19 3
Auto
Scheduled
Conceptual Framework
Design 3 days Mon 16-09-
19
Wed 18-09-
19 4
Auto
Scheduled
Project Plan
Development 2 days Thu 19-09-
19 Fri 20-09-19 5
Auto
Scheduled
Submission of the
Research Proposal 2 days Mon 23-09-
19
Tue 24-09-
19 6
Auto
Scheduled
Literature Review
and Data Collection 0 days Sun 19-05-
19
Sun 19-05-
19
Auto Literature Review 48 days Wed 25-09- Fri 29-11-19 7
which is to be included in the plan for conducting the research is the Google Scholar Database on
the different kind of cybercrimes.
The primary method of research might be associated with putting forward of different
kind of disadvantages such as usage of large datasets would be responsible for consuming a huge
amount of time. In addition to this the respondents might be associated with interpreting the
questions in a different manner which in turn would be associated with making the process of
comparing the answers very difficult. Besides this in a primary research it is also very difficult to
check if the respondents are honestly responding or not. In addition to this there is an over
reliance upon the statistical data in the primary research methodology which initially makes it
losing the individual meaning and the data. For this reason the secondary research methodology
is to be used.
5. Research Schedule
Task Mode Task Name Duration Start Finish Predecessors
Auto
Scheduled Research Proposal 76 days Mon 20-05-
19
Mon 02-09-
19
Auto
Scheduled Selection of the Topic 16 days Mon 20-05-
19
Mon 10-06-
19
Auto
Scheduled Background Research 3 days Tue 03-09-
19
Thu 05-09-
19 1
Auto
Scheduled
Research Question
Development 6 days Fri 06-09-19 Fri 13-09-19 3
Auto
Scheduled
Conceptual Framework
Design 3 days Mon 16-09-
19
Wed 18-09-
19 4
Auto
Scheduled
Project Plan
Development 2 days Thu 19-09-
19 Fri 20-09-19 5
Auto
Scheduled
Submission of the
Research Proposal 2 days Mon 23-09-
19
Tue 24-09-
19 6
Auto
Scheduled
Literature Review
and Data Collection 0 days Sun 19-05-
19
Sun 19-05-
19
Auto Literature Review 48 days Wed 25-09- Fri 29-11-19 7
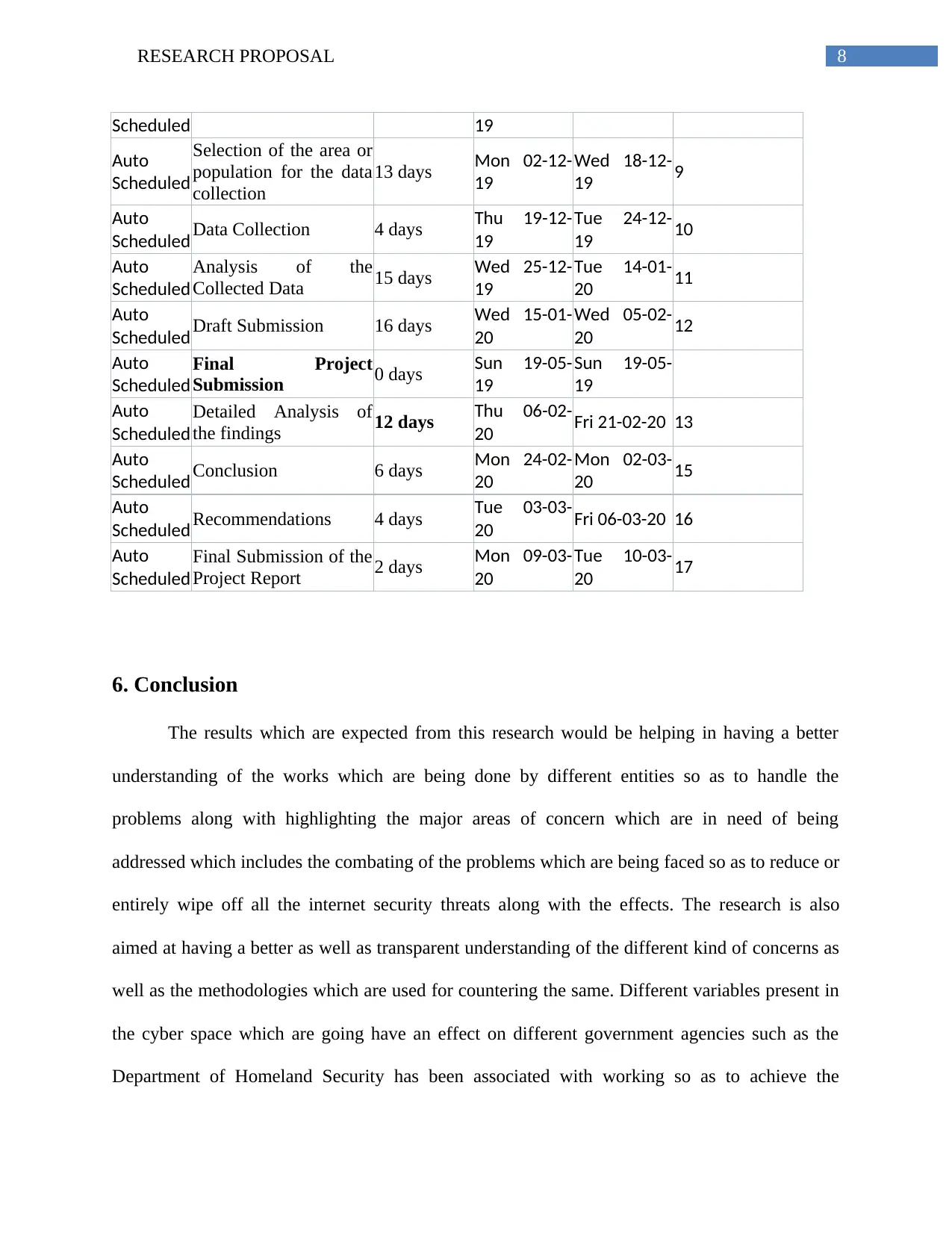
8RESEARCH PROPOSAL
Scheduled 19
Auto
Scheduled
Selection of the area or
population for the data
collection
13 days Mon 02-12-
19
Wed 18-12-
19 9
Auto
Scheduled Data Collection 4 days Thu 19-12-
19
Tue 24-12-
19 10
Auto
Scheduled
Analysis of the
Collected Data 15 days Wed 25-12-
19
Tue 14-01-
20 11
Auto
Scheduled Draft Submission 16 days Wed 15-01-
20
Wed 05-02-
20 12
Auto
Scheduled
Final Project
Submission 0 days Sun 19-05-
19
Sun 19-05-
19
Auto
Scheduled
Detailed Analysis of
the findings 12 days Thu 06-02-
20 Fri 21-02-20 13
Auto
Scheduled Conclusion 6 days Mon 24-02-
20
Mon 02-03-
20 15
Auto
Scheduled Recommendations 4 days Tue 03-03-
20 Fri 06-03-20 16
Auto
Scheduled
Final Submission of the
Project Report 2 days Mon 09-03-
20
Tue 10-03-
20 17
6. Conclusion
The results which are expected from this research would be helping in having a better
understanding of the works which are being done by different entities so as to handle the
problems along with highlighting the major areas of concern which are in need of being
addressed which includes the combating of the problems which are being faced so as to reduce or
entirely wipe off all the internet security threats along with the effects. The research is also
aimed at having a better as well as transparent understanding of the different kind of concerns as
well as the methodologies which are used for countering the same. Different variables present in
the cyber space which are going have an effect on different government agencies such as the
Department of Homeland Security has been associated with working so as to achieve the
Scheduled 19
Auto
Scheduled
Selection of the area or
population for the data
collection
13 days Mon 02-12-
19
Wed 18-12-
19 9
Auto
Scheduled Data Collection 4 days Thu 19-12-
19
Tue 24-12-
19 10
Auto
Scheduled
Analysis of the
Collected Data 15 days Wed 25-12-
19
Tue 14-01-
20 11
Auto
Scheduled Draft Submission 16 days Wed 15-01-
20
Wed 05-02-
20 12
Auto
Scheduled
Final Project
Submission 0 days Sun 19-05-
19
Sun 19-05-
19
Auto
Scheduled
Detailed Analysis of
the findings 12 days Thu 06-02-
20 Fri 21-02-20 13
Auto
Scheduled Conclusion 6 days Mon 24-02-
20
Mon 02-03-
20 15
Auto
Scheduled Recommendations 4 days Tue 03-03-
20 Fri 06-03-20 16
Auto
Scheduled
Final Submission of the
Project Report 2 days Mon 09-03-
20
Tue 10-03-
20 17
6. Conclusion
The results which are expected from this research would be helping in having a better
understanding of the works which are being done by different entities so as to handle the
problems along with highlighting the major areas of concern which are in need of being
addressed which includes the combating of the problems which are being faced so as to reduce or
entirely wipe off all the internet security threats along with the effects. The research is also
aimed at having a better as well as transparent understanding of the different kind of concerns as
well as the methodologies which are used for countering the same. Different variables present in
the cyber space which are going have an effect on different government agencies such as the
Department of Homeland Security has been associated with working so as to achieve the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RESEARCH PROPOSAL
objectives. The outcome of this research is expected to state the motives which are responsible
for causing or leading the terrorism. Terrorism is seen to be driven by different sheer forces of
aggregations so as to fulfill the personal motive of someone or might be including a collective
motive of a group because of some reason. The entire research is expected to be associated with
providing of the reasons why this type of activities are taking place and what are the roles that
can be placed by the government agencies so as to counter the problems.
objectives. The outcome of this research is expected to state the motives which are responsible
for causing or leading the terrorism. Terrorism is seen to be driven by different sheer forces of
aggregations so as to fulfill the personal motive of someone or might be including a collective
motive of a group because of some reason. The entire research is expected to be associated with
providing of the reasons why this type of activities are taking place and what are the roles that
can be placed by the government agencies so as to counter the problems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RESEARCH PROPOSAL
Reference:
Abomhara, Mohamed. "Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks." Journal of Cyber Security and Mobility 4, no. 1 (2015): 65-88.
Ben-Asher, Noam, and Cleotilde Gonzalez. "Effects of cyber security knowledge on attack
detection." Computers in Human Behavior 48 (2015): 51-61.
Buczak, Anna L., and Erhan Guven. "A survey of data mining and machine learning methods for
cyber security intrusion detection." IEEE Communications Surveys & Tutorials 18, no. 2 (2015):
1153-1176.
Carr, Madeline. "Public–private partnerships in national cyber-security strategies." International
Affairs 92, no. 1 (2016): 43-62.
Cherdantseva, Yulia, Pete Burnap, Andrew Blyth, Peter Eden, Kevin Jones, Hugh Soulsby, and
Kristan Stoddart. "A review of cyber security risk assessment methods for SCADA
systems." Computers & security 56 (2016): 1-27.
Dark, Melissa, Matt Bishop, Richard Linger, and Luanne Goldrich. "Realism in teaching
cybersecurity research: The agile research process." In IFIP World Conference on Information
Security Education, pp. 3-14. Springer, Cham, 2015.
Graham, James, Ryan Olson, and Rick Howard. Cyber security essentials. Auerbach
Publications, 2016.
Kent, Alexander D. "Cyber security data sources for dynamic network research." In Dynamic
Networks and Cyber-Security, pp. 37-65. 2016.
Reference:
Abomhara, Mohamed. "Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks." Journal of Cyber Security and Mobility 4, no. 1 (2015): 65-88.
Ben-Asher, Noam, and Cleotilde Gonzalez. "Effects of cyber security knowledge on attack
detection." Computers in Human Behavior 48 (2015): 51-61.
Buczak, Anna L., and Erhan Guven. "A survey of data mining and machine learning methods for
cyber security intrusion detection." IEEE Communications Surveys & Tutorials 18, no. 2 (2015):
1153-1176.
Carr, Madeline. "Public–private partnerships in national cyber-security strategies." International
Affairs 92, no. 1 (2016): 43-62.
Cherdantseva, Yulia, Pete Burnap, Andrew Blyth, Peter Eden, Kevin Jones, Hugh Soulsby, and
Kristan Stoddart. "A review of cyber security risk assessment methods for SCADA
systems." Computers & security 56 (2016): 1-27.
Dark, Melissa, Matt Bishop, Richard Linger, and Luanne Goldrich. "Realism in teaching
cybersecurity research: The agile research process." In IFIP World Conference on Information
Security Education, pp. 3-14. Springer, Cham, 2015.
Graham, James, Ryan Olson, and Rick Howard. Cyber security essentials. Auerbach
Publications, 2016.
Kent, Alexander D. "Cyber security data sources for dynamic network research." In Dynamic
Networks and Cyber-Security, pp. 37-65. 2016.

11RESEARCH PROPOSAL
Knowles, William, Daniel Prince, David Hutchison, Jules Ferdinand Pagna Disso, and Kevin
Jones. "A survey of cyber security management in industrial control systems." International
journal of critical infrastructure protection 9 (2015): 52-80.
Lee, Jay, Behrad Bagheri, and Chao Jin. "Introduction to cyber manufacturing." Manufacturing
Letters 8 (2016): 11-15.
Knowles, William, Daniel Prince, David Hutchison, Jules Ferdinand Pagna Disso, and Kevin
Jones. "A survey of cyber security management in industrial control systems." International
journal of critical infrastructure protection 9 (2015): 52-80.
Lee, Jay, Behrad Bagheri, and Chao Jin. "Introduction to cyber manufacturing." Manufacturing
Letters 8 (2016): 11-15.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





