Network Security and Cloud Computing
VerifiedAdded on 2020/03/16
|9
|2164
|116
AI Summary
This assignment delves into the crucial aspects of network security, analyzing different firewall types like rule-based and application-aware, and examining their capabilities in mitigating breaches. It emphasizes the significance of secure key management throughout the lifecycle, highlighting organizational responsibilities. Furthermore, the document explores the advantages of cloud computing for educational institutions and workplaces, including scalability, cost-efficiency, data management, and resource sharing.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Internet Security
10/6/2017
10/6/2017
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Internet Security
Table of Contents
Attack Experience.......................................................................................................................................3
Researching Trojan Attacks.........................................................................................................................3
Zero Day Attacks.........................................................................................................................................4
Anti-Virus...................................................................................................................................................4
Key Management Life Cycle.......................................................................................................................6
Network Firewall Vendors..........................................................................................................................7
Cloud Computing Benefits..........................................................................................................................7
References...................................................................................................................................................9
2
Table of Contents
Attack Experience.......................................................................................................................................3
Researching Trojan Attacks.........................................................................................................................3
Zero Day Attacks.........................................................................................................................................4
Anti-Virus...................................................................................................................................................4
Key Management Life Cycle.......................................................................................................................6
Network Firewall Vendors..........................................................................................................................7
Cloud Computing Benefits..........................................................................................................................7
References...................................................................................................................................................9
2

Internet Security
Attack Experience
The attack experience that has been described is of a friend that was working for a small scale
finance firm. The firm experienced a large scale ransomware attack earlier this year that led to
the unavailability of the systems and the information that was present in the systems. The
ransomware attack was given shape by using the networks as the agents of the threat and the
reproducible malware got multiplied and impacted all of the computer systems that were being
used in the firm. The impact resulted in the damage causing deterioration of the system
availability and also led to the compromise on the confidentiality and privacy of the information.
The primary reason of the attack was the security vulnerabilities that were present in the
computer systems and networks that were associated with the organization. There were security
loopholes that were present which were utilized by the attackers and the ransomware was
launched. The fix was done by using the patching and upgrade of the system along with
reporting of the same to the information security bodies of the country.
The attack could have been prevented by using anti-malware tools and system monitoring tools
that would have generated an alert at the first attempt of the attack itself.
Researching Trojan Attacks
Trojans are defined as the form of malware which allow the hacker or the attacker to have
remote access to the system which is attacked. There is an executable file or a complier that is
required to install Trojans in a particular computer system. These cannot multiply by themselves
but can have extremely severe damages and impacts.
The damage that is caused by a Trojan attack is the compromise of the security and
confidentiality of the information that is present in the system and applications that are attacked.
The latest form of Trojan attacks is the Android based Trojans which make use of Android based
mobile device as the platform and can lead to the damage along with enhanced probability of
further cyber risks and attacks.
The sensitive information that is present in the mobile devices or the computer systems get
compromised as a result. There can also be further damages that may be caused by a Trojan
3
Attack Experience
The attack experience that has been described is of a friend that was working for a small scale
finance firm. The firm experienced a large scale ransomware attack earlier this year that led to
the unavailability of the systems and the information that was present in the systems. The
ransomware attack was given shape by using the networks as the agents of the threat and the
reproducible malware got multiplied and impacted all of the computer systems that were being
used in the firm. The impact resulted in the damage causing deterioration of the system
availability and also led to the compromise on the confidentiality and privacy of the information.
The primary reason of the attack was the security vulnerabilities that were present in the
computer systems and networks that were associated with the organization. There were security
loopholes that were present which were utilized by the attackers and the ransomware was
launched. The fix was done by using the patching and upgrade of the system along with
reporting of the same to the information security bodies of the country.
The attack could have been prevented by using anti-malware tools and system monitoring tools
that would have generated an alert at the first attempt of the attack itself.
Researching Trojan Attacks
Trojans are defined as the form of malware which allow the hacker or the attacker to have
remote access to the system which is attacked. There is an executable file or a complier that is
required to install Trojans in a particular computer system. These cannot multiply by themselves
but can have extremely severe damages and impacts.
The damage that is caused by a Trojan attack is the compromise of the security and
confidentiality of the information that is present in the system and applications that are attacked.
The latest form of Trojan attacks is the Android based Trojans which make use of Android based
mobile device as the platform and can lead to the damage along with enhanced probability of
further cyber risks and attacks.
The sensitive information that is present in the mobile devices or the computer systems get
compromised as a result. There can also be further damages that may be caused by a Trojan
3
Internet Security
attack, such as, DNS server manipulation and many more. The security vulnerabilities are the
primary reasons and causes of the occurrence of the Trojan attacks.
Zero Day Attacks
There may be security vulnerabilities and loopholes that may be present in a product or a service
and the vendor may not be aware about the same. The attackers may get hold of this information
and may cause the occurrence of other attacks taking advantage of these unknown vulnerabilities
and weaknesses. Such attacks are termed as the zero-day attacks.
The security vulnerabilities are highlighted during the next round of validation and verification
and may also be highlighted during the installation of the updates and the regression testing
phase.
There have been many zero day attacks that have been observed recently. These include the
Encapsulated PostScript (EPS) type confusion and restore use-after free along with SOAP
WSDL parser code injection. There can be some significant damage that may be observed as a
result of the occurrence of the zero-day attacks. It is because the damage intensifies with such
occurrences. The targeted systems become liable to rectify the security vulnerability that gets
highlighted with the occurrence of the zero day attack and also need to control the damage cause
by the attack itself. These may have an adverse impact on the confidentiality and privacy of the
information and can also lead to the overall system weakness.
The cause of the zero-day attacks are not pre-determined or known and get highlighted at the
time of the attack itself. It is therefore, not easy to form the defense against such attacks. There
are certain tools and techniques that can be used for the prevention and avoidance of these
attacks comprising of efficient patch management along with the use and installation of anti-
malware tools.
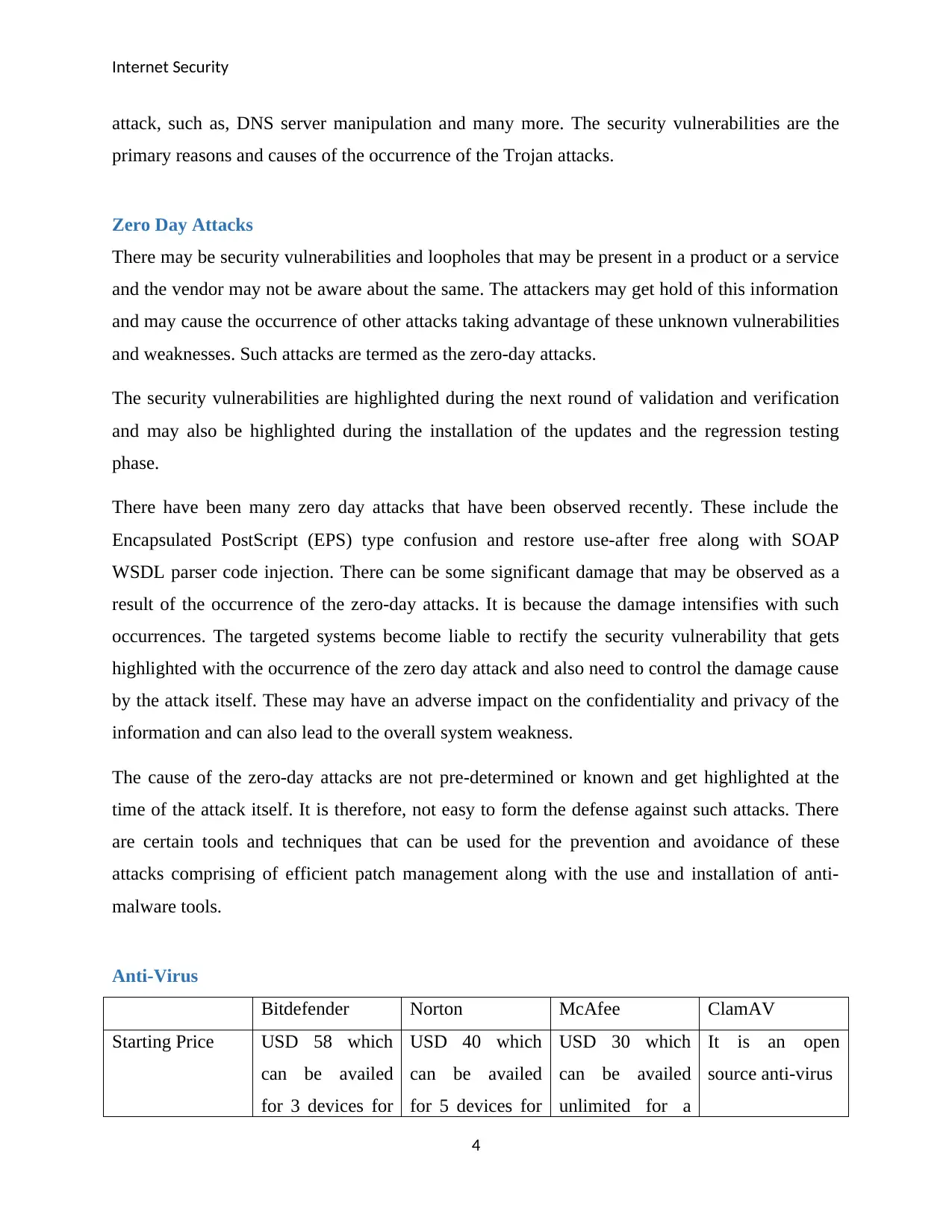
Anti-Virus
Bitdefender Norton McAfee ClamAV
Starting Price USD 58 which
can be availed
for 3 devices for
USD 40 which
can be availed
for 5 devices for
USD 30 which
can be availed
unlimited for a
It is an open
source anti-virus
4
attack, such as, DNS server manipulation and many more. The security vulnerabilities are the
primary reasons and causes of the occurrence of the Trojan attacks.
Zero Day Attacks
There may be security vulnerabilities and loopholes that may be present in a product or a service
and the vendor may not be aware about the same. The attackers may get hold of this information
and may cause the occurrence of other attacks taking advantage of these unknown vulnerabilities
and weaknesses. Such attacks are termed as the zero-day attacks.
The security vulnerabilities are highlighted during the next round of validation and verification
and may also be highlighted during the installation of the updates and the regression testing
phase.
There have been many zero day attacks that have been observed recently. These include the
Encapsulated PostScript (EPS) type confusion and restore use-after free along with SOAP
WSDL parser code injection. There can be some significant damage that may be observed as a
result of the occurrence of the zero-day attacks. It is because the damage intensifies with such
occurrences. The targeted systems become liable to rectify the security vulnerability that gets
highlighted with the occurrence of the zero day attack and also need to control the damage cause
by the attack itself. These may have an adverse impact on the confidentiality and privacy of the
information and can also lead to the overall system weakness.
The cause of the zero-day attacks are not pre-determined or known and get highlighted at the
time of the attack itself. It is therefore, not easy to form the defense against such attacks. There
are certain tools and techniques that can be used for the prevention and avoidance of these
attacks comprising of efficient patch management along with the use and installation of anti-
malware tools.
Anti-Virus
Bitdefender Norton McAfee ClamAV
Starting Price USD 58 which
can be availed
for 3 devices for
USD 40 which
can be availed
for 5 devices for
USD 30 which
can be availed
unlimited for a
It is an open
source anti-virus
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
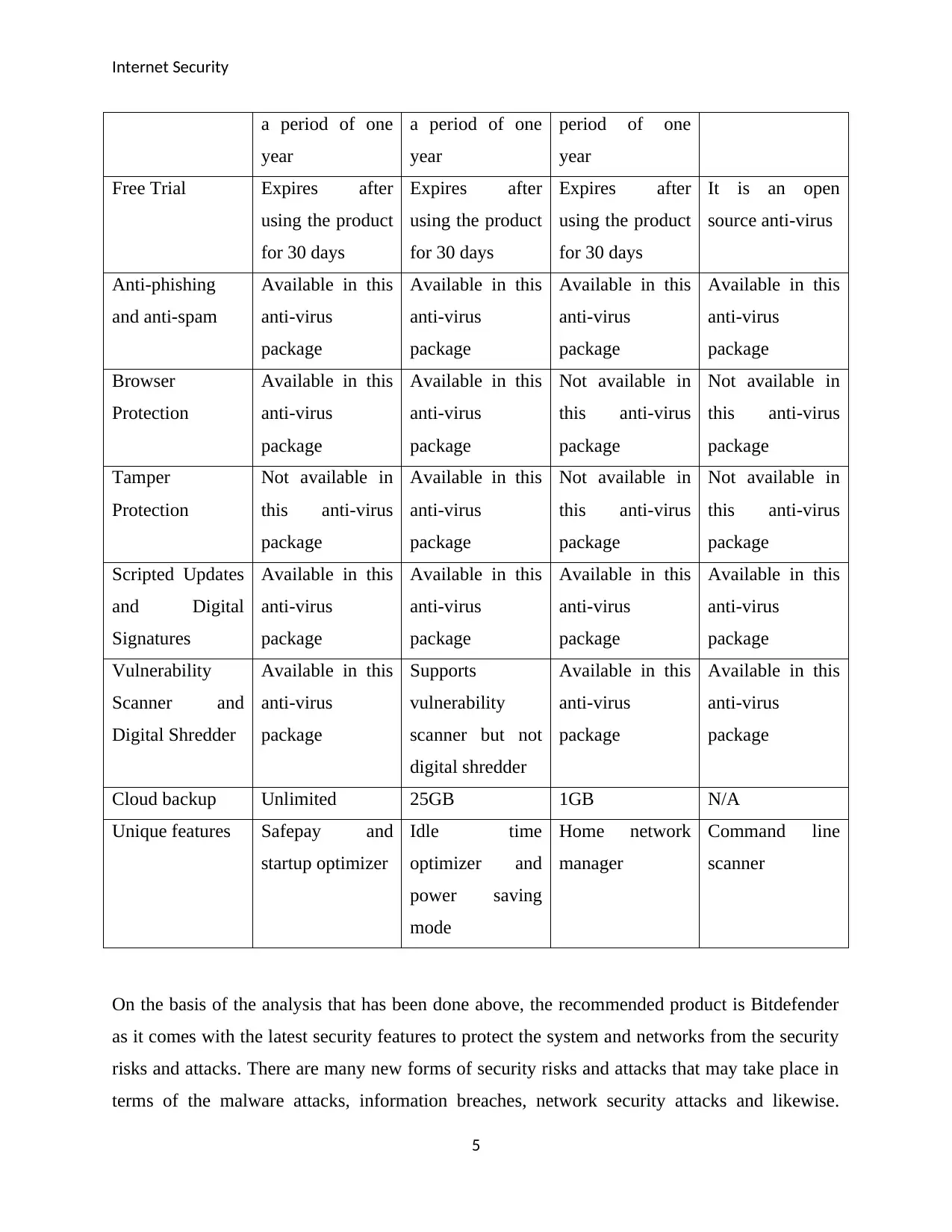
Internet Security
a period of one
year
a period of one
year
period of one
year
Free Trial Expires after
using the product
for 30 days
Expires after
using the product
for 30 days
Expires after
using the product
for 30 days
It is an open
source anti-virus
Anti-phishing
and anti-spam
Available in this
anti-virus
package
Available in this
anti-virus
package
Available in this
anti-virus
package
Available in this
anti-virus
package
Browser
Protection
Available in this
anti-virus
package
Available in this
anti-virus
package
Not available in
this anti-virus
package
Not available in
this anti-virus
package
Tamper
Protection
Not available in
this anti-virus
package
Available in this
anti-virus
package
Not available in
this anti-virus
package
Not available in
this anti-virus
package
Scripted Updates
and Digital
Signatures
Available in this
anti-virus
package
Available in this
anti-virus
package
Available in this
anti-virus
package
Available in this
anti-virus
package
Vulnerability
Scanner and
Digital Shredder
Available in this
anti-virus
package
Supports
vulnerability
scanner but not
digital shredder
Available in this
anti-virus
package
Available in this
anti-virus
package
Cloud backup Unlimited 25GB 1GB N/A
Unique features Safepay and
startup optimizer
Idle time
optimizer and
power saving
mode
Home network
manager
Command line
scanner
On the basis of the analysis that has been done above, the recommended product is Bitdefender
as it comes with the latest security features to protect the system and networks from the security
risks and attacks. There are many new forms of security risks and attacks that may take place in
terms of the malware attacks, information breaches, network security attacks and likewise.
5
a period of one
year
a period of one
year
period of one
year
Free Trial Expires after
using the product
for 30 days
Expires after
using the product
for 30 days
Expires after
using the product
for 30 days
It is an open
source anti-virus
Anti-phishing
and anti-spam
Available in this
anti-virus
package
Available in this
anti-virus
package
Available in this
anti-virus
package
Available in this
anti-virus
package
Browser
Protection
Available in this
anti-virus
package
Available in this
anti-virus
package
Not available in
this anti-virus
package
Not available in
this anti-virus
package
Tamper
Protection
Not available in
this anti-virus
package
Available in this
anti-virus
package
Not available in
this anti-virus
package
Not available in
this anti-virus
package
Scripted Updates
and Digital
Signatures
Available in this
anti-virus
package
Available in this
anti-virus
package
Available in this
anti-virus
package
Available in this
anti-virus
package
Vulnerability
Scanner and
Digital Shredder
Available in this
anti-virus
package
Supports
vulnerability
scanner but not
digital shredder
Available in this
anti-virus
package
Available in this
anti-virus
package
Cloud backup Unlimited 25GB 1GB N/A
Unique features Safepay and
startup optimizer
Idle time
optimizer and
power saving
mode
Home network
manager
Command line
scanner
On the basis of the analysis that has been done above, the recommended product is Bitdefender
as it comes with the latest security features to protect the system and networks from the security
risks and attacks. There are many new forms of security risks and attacks that may take place in
terms of the malware attacks, information breaches, network security attacks and likewise.
5

Internet Security
Bitdefender is an anti-virus package that has the ability to handle these new forms of risks and
attacks.
The one that is currently being used on a personal level is the same product and the experience
has been pretty good so far. Bitdefender has made sure that the security of the applications and
services is not impacted.
Hash Algorithms
Hash function is a mathematical function which is used to change the numerical input value to a
secure mathematical form. There are various hash functions and hash algorithms that are used.
Some of the popular hash functions are message digest, secure hashing algorithm, RIPEMD and
Whirlpool.
Message Digest
Message Digest 5 (MD5) is an upgraded version of Message Direct 4 (MD4). Security of MD5 is
the major strength of this hashing algorithm. However, it is a bit slower than its predecessor. In
the applications where a high degree of security is demanded, MD5 is the hashing algorithm that
is most preferred.
Secure Hashing Algorithm (SHA)
Secure Hashing Algorithms are also known as SHA and there are different variations of this
algorithm. The avalanche effect that is involved in the SHA includes the randomizing feature.
SHA-256 is the algorithm in which a hashing string of 256 bits is produced.
RIPEMD
RIPEMD is a hashing algorithm that stands for RACE Integrity Primitives Evaluation Message
Digest. The algorithm provides the ability to make sure that longer hash strings are developed
and implemented. RIPEMD-320 is an algorithm in which double string of the widely used
RIPEMD-160. The speed of the algorithm is an issue in this case.
Whirlpool Algorithm
The latest release in the field of hashing algorithms is the Whirlpool algorithm. It is an algorithm
in which 128 digit hexadecimal string is used and there have been many variations that have
6
Bitdefender is an anti-virus package that has the ability to handle these new forms of risks and
attacks.
The one that is currently being used on a personal level is the same product and the experience
has been pretty good so far. Bitdefender has made sure that the security of the applications and
services is not impacted.
Hash Algorithms
Hash function is a mathematical function which is used to change the numerical input value to a
secure mathematical form. There are various hash functions and hash algorithms that are used.
Some of the popular hash functions are message digest, secure hashing algorithm, RIPEMD and
Whirlpool.
Message Digest
Message Digest 5 (MD5) is an upgraded version of Message Direct 4 (MD4). Security of MD5 is
the major strength of this hashing algorithm. However, it is a bit slower than its predecessor. In
the applications where a high degree of security is demanded, MD5 is the hashing algorithm that
is most preferred.
Secure Hashing Algorithm (SHA)
Secure Hashing Algorithms are also known as SHA and there are different variations of this
algorithm. The avalanche effect that is involved in the SHA includes the randomizing feature.
SHA-256 is the algorithm in which a hashing string of 256 bits is produced.
RIPEMD
RIPEMD is a hashing algorithm that stands for RACE Integrity Primitives Evaluation Message
Digest. The algorithm provides the ability to make sure that longer hash strings are developed
and implemented. RIPEMD-320 is an algorithm in which double string of the widely used
RIPEMD-160. The speed of the algorithm is an issue in this case.
Whirlpool Algorithm
The latest release in the field of hashing algorithms is the Whirlpool algorithm. It is an algorithm
in which 128 digit hexadecimal string is used and there have been many variations that have
6

Internet Security
been done in this algorithm since its release. This algorithm is an advanced version of Advanced
Encryption Standard (AES).
Key Management Life Cycle
Key Management Life Cycle
There are various processes and steps that are present in the key management life cycle. These
phases or steps include creation, backup, deployment, monitoring, rotation, expiration, archival
and destruction. Each of these phases is significant in the efficient management of the key.
The duration of the validity of a key depends upon a number of different factors. Some of these
factors include the sensitivity of the data or information sets that are required to be protected.
The length or the size of the data sets also plays a significant role in this decision. The duration
of the validity of the key may also be impacted by certain unpredictable circumstances like a
security occurrence.
Current and past instances of the key shall be adequately managed at the time of the expiration.
The accountability of these tasks shall be on the key manager. The replacement must be done as
7
been done in this algorithm since its release. This algorithm is an advanced version of Advanced
Encryption Standard (AES).
Key Management Life Cycle
Key Management Life Cycle
There are various processes and steps that are present in the key management life cycle. These
phases or steps include creation, backup, deployment, monitoring, rotation, expiration, archival
and destruction. Each of these phases is significant in the efficient management of the key.
The duration of the validity of a key depends upon a number of different factors. Some of these
factors include the sensitivity of the data or information sets that are required to be protected.
The length or the size of the data sets also plays a significant role in this decision. The duration
of the validity of the key may also be impacted by certain unpredictable circumstances like a
security occurrence.
Current and past instances of the key shall be adequately managed at the time of the expiration.
The accountability of these tasks shall be on the key manager. The replacement must be done as
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Internet Security
per the pre-determined schedule and the expiration shall be followed by the processes of archival
and destruction.
The organization is responsible for the key management and the organization. The users shall be
informed about the certain practices that they must follow for the security of the key. It is the
duty of the organization to make sure that all the steps in the key management life cycle are
followed.
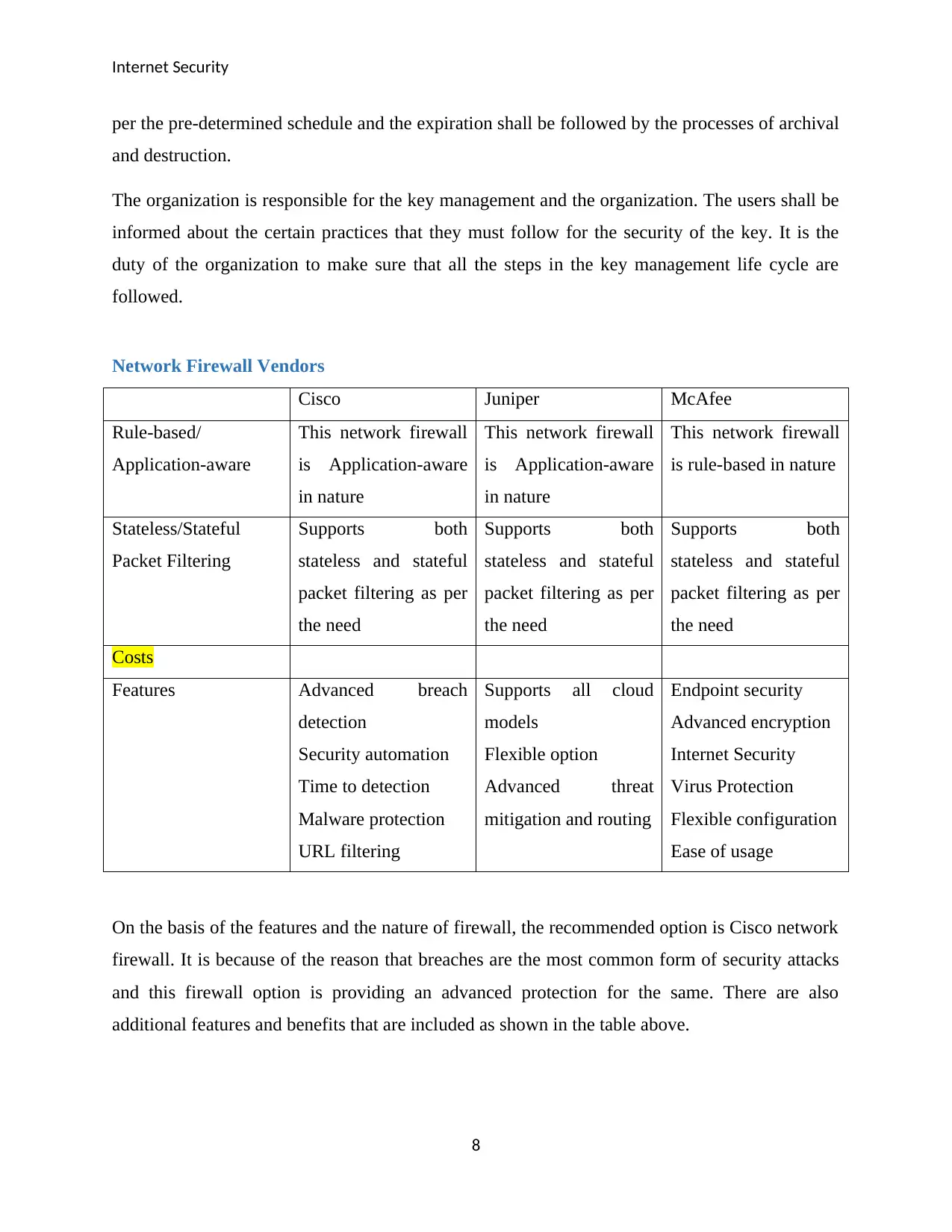
Network Firewall Vendors
Cisco Juniper McAfee
Rule-based/
Application-aware
This network firewall
is Application-aware
in nature
This network firewall
is Application-aware
in nature
This network firewall
is rule-based in nature
Stateless/Stateful
Packet Filtering
Supports both
stateless and stateful
packet filtering as per
the need
Supports both
stateless and stateful
packet filtering as per
the need
Supports both
stateless and stateful
packet filtering as per
the need
Costs
Features Advanced breach
detection
Security automation
Time to detection
Malware protection
URL filtering
Supports all cloud
models
Flexible option
Advanced threat
mitigation and routing
Endpoint security
Advanced encryption
Internet Security
Virus Protection
Flexible configuration
Ease of usage
On the basis of the features and the nature of firewall, the recommended option is Cisco network
firewall. It is because of the reason that breaches are the most common form of security attacks
and this firewall option is providing an advanced protection for the same. There are also
additional features and benefits that are included as shown in the table above.
8
per the pre-determined schedule and the expiration shall be followed by the processes of archival
and destruction.
The organization is responsible for the key management and the organization. The users shall be
informed about the certain practices that they must follow for the security of the key. It is the
duty of the organization to make sure that all the steps in the key management life cycle are
followed.
Network Firewall Vendors
Cisco Juniper McAfee
Rule-based/
Application-aware
This network firewall
is Application-aware
in nature
This network firewall
is Application-aware
in nature
This network firewall
is rule-based in nature
Stateless/Stateful
Packet Filtering
Supports both
stateless and stateful
packet filtering as per
the need
Supports both
stateless and stateful
packet filtering as per
the need
Supports both
stateless and stateful
packet filtering as per
the need
Costs
Features Advanced breach
detection
Security automation
Time to detection
Malware protection
URL filtering
Supports all cloud
models
Flexible option
Advanced threat
mitigation and routing
Endpoint security
Advanced encryption
Internet Security
Virus Protection
Flexible configuration
Ease of usage
On the basis of the features and the nature of firewall, the recommended option is Cisco network
firewall. It is because of the reason that breaches are the most common form of security attacks
and this firewall option is providing an advanced protection for the same. There are also
additional features and benefits that are included as shown in the table above.
8

Internet Security
Cloud Computing Benefits
Cloud computing will provide many benefits to the school and the work place. There will be
benefits as described below:
The operations and activities that are carried out will become flexible and scalable in
nature. It will provide the school/workplace with the ability to modify its operations and
business activities as per the need and requirements in terms of the technology, usage and
nature of operations.
The overall management of the information and data sets will become easier and the
backing up of the data will also be easy. There are automated schedules that will be
followed in the backing up process.
There will be elimination of infrastructural and additional costs from the expenses. Cloud
services and operations make use of the virtual platforms which eliminates the need of
the infrastructural setups.
Resource sharing is an inherent feature of cloud computing which would allow the
sharing and optimization of the resources.
The integration of the activities that are carried out will improve. There are cloud services
that have been developed that are compatible with the latest operating systems and
applications.
It will be easier to retrieve the information and execution the business functions. There
will be automated queries that will be executed for the retrieval of data and information.
There are many cloud vendors in the market. The two of the most popular include Amazon and
Microsoft. Amazon has its cloud services by the name of Amazon Web Services (AWS). It
provides cloud services such as cloud databases, data analysis, Big Data tools, Business
Intelligence, digital marketing and many more. Microsoft has its cloud services by the name of
Microsoft Azure as the cloud vendor. It provides a number of cloud models such as public,
private or hybrid cloud and also supports cloud as a platform, service or infrastructure.
The use of cloud in school or the workplace would be feasible as the tools and techniques that
are necessary for the implementation of cloud can be easily achieved.
9
Cloud Computing Benefits
Cloud computing will provide many benefits to the school and the work place. There will be
benefits as described below:
The operations and activities that are carried out will become flexible and scalable in
nature. It will provide the school/workplace with the ability to modify its operations and
business activities as per the need and requirements in terms of the technology, usage and
nature of operations.
The overall management of the information and data sets will become easier and the
backing up of the data will also be easy. There are automated schedules that will be
followed in the backing up process.
There will be elimination of infrastructural and additional costs from the expenses. Cloud
services and operations make use of the virtual platforms which eliminates the need of
the infrastructural setups.
Resource sharing is an inherent feature of cloud computing which would allow the
sharing and optimization of the resources.
The integration of the activities that are carried out will improve. There are cloud services
that have been developed that are compatible with the latest operating systems and
applications.
It will be easier to retrieve the information and execution the business functions. There
will be automated queries that will be executed for the retrieval of data and information.
There are many cloud vendors in the market. The two of the most popular include Amazon and
Microsoft. Amazon has its cloud services by the name of Amazon Web Services (AWS). It
provides cloud services such as cloud databases, data analysis, Big Data tools, Business
Intelligence, digital marketing and many more. Microsoft has its cloud services by the name of
Microsoft Azure as the cloud vendor. It provides a number of cloud models such as public,
private or hybrid cloud and also supports cloud as a platform, service or infrastructure.
The use of cloud in school or the workplace would be feasible as the tools and techniques that
are necessary for the implementation of cloud can be easily achieved.
9
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




