Implementation of RF Source for Communication in Wireless Sensors
VerifiedAdded on 2023/03/29
|25
|8478
|27
Report
AI Summary
This report investigates the implementation of RF sources for communication in wireless passive sensor networks (WPSN). It focuses on modulated backscattering (MB) as a promising design option for sensor nodes. The study analyzes the system analytically, considering factors such as RF source output power, transmission frequency, network dimensions, and WPSN client characteristics. The report explores how these parameters affect communication coverage and the required number of RF sources to minimize power consumption in WPSN. It also touches upon the applications and challenges of Wireless Sensor Networks (WSN) and Radio Frequency Identification (RFID) systems, discussing their advantages and the integration of both technologies. The report also provides insights into wireless technologies, potential risks, and strategies for ensuring data integrity and security in wireless medical devices, highlighting the importance of error management, wireless coexistence, and the protection of wireless signals and data.

RF source implementation for
communication in wireless passive
sensor network
communication in wireless passive
sensor network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
A wireless sensor network (WSN) is a wireless network including spatially
distributed autonomous gadgetsusing sensors to cooperatively monitor
physical or environment conditions, such as temperature, audio,vibration,
pressure, motion or pollutants, in different locations. During RF transmission
energy consumed simply byvitally energy-constrained sensor nodes within a
WSN is related to the full lifetime system, however the full life time of
thestrategy is inversely proportional to the power consumed by sensor
nodes. In this regard, modulatedbackscattering (MB) is a promising design
option, by which sensor nodes send their particular data just by
switchingtheir antenna impedance and reflecting the event signal coming
from an RF source. Therefore wireless passivesensor systems (WPSN)
designed to operate making use of MB do not have the life time constraints.
In this we arelikely to investigate the system analytically. To obtain
interference-free communication connection with theWPSN nodes number of
RF resources is analyzed and motivated in terms of output power as well as
the transmissionfrequency associated with RF sources, network dimension,
RF source and WPSN client characteristics. The entire results of this
paperdisclose that communication coverage plus RF Source Power could be
practically maintained in WPSN throughcautious selection of design
parameters.
A wireless sensor network (WSN) is a wireless network including spatially
distributed autonomous gadgetsusing sensors to cooperatively monitor
physical or environment conditions, such as temperature, audio,vibration,
pressure, motion or pollutants, in different locations. During RF transmission
energy consumed simply byvitally energy-constrained sensor nodes within a
WSN is related to the full lifetime system, however the full life time of
thestrategy is inversely proportional to the power consumed by sensor
nodes. In this regard, modulatedbackscattering (MB) is a promising design
option, by which sensor nodes send their particular data just by
switchingtheir antenna impedance and reflecting the event signal coming
from an RF source. Therefore wireless passivesensor systems (WPSN)
designed to operate making use of MB do not have the life time constraints.
In this we arelikely to investigate the system analytically. To obtain
interference-free communication connection with theWPSN nodes number of
RF resources is analyzed and motivated in terms of output power as well as
the transmissionfrequency associated with RF sources, network dimension,
RF source and WPSN client characteristics. The entire results of this
paperdisclose that communication coverage plus RF Source Power could be
practically maintained in WPSN throughcautious selection of design
parameters.

Introduction
A radio frequency (RF) signal refers to a wireless electromagnetic signal used
as a type of communication, if one is talking about wireless electronics.
Radio surf are a form of electromagnetic rays with identified radio
frequencies that will range from 3 kHz to three hundred GHz. Frequency
refers to the pace of oscillation (of radio stations waves.) RF distribution
occurs at the speed associated with light and does not need a moderate like
air in order to journey. RF waves occur from sunlight flares naturally,
lightning, and through stars in space that will radiate RF waves because they
age. Mankind communicates with artificially produced radio waves that
oscillate at various chosen frequencies. RF conversation is used in many
industries which includes television broadcasting, radar techniques,
computer and mobile system networks, remote control, remote
metering/monitoring, and many more.
WSN is one of the most evolving R&D field for microelectronics quickly. Their
apps and market potentials are usually increasing day-by-day. According to
Frost &Sullivan, the particular expected market size is going to be US$
2billion by this year at an approximatelycompound annual development of
41.9%.
WSN aims to monitor and to manage an environment sometimes. The
particular operational system operates to getperiods varying through weeks
to years within an autonomous way. The network iscomposed of many
sensor nodes that can be used on the ground, up,in automobile, inside
building. The Sensor Client comprises of sensing (measuring),processing, and
communication elements. The sink aggregates some or even all the
nodeinformation. Since sensor power cannot support long variety
communication to reach akitchen sink, multi-hop wireless connectivity is
needed to forward data to the remote control sink. Each ofthe dispersed
sensor nodes has the capacity to collect data, process all of them, and route
themin order to sink node. Router nodes are deployed in field to forward
information from sensor nodesin order to remote sink node. To aid node
operation, open supply operating system (OS) ismade for WSN specially. It
utilizes a component-based architecture that enables rapiddevelopment and
implementation while lessening code size as necessary by the
memoryconstraints in sensor systems. It includes network protocols,
dispersed services, sensordrivers, plus data acquisition tools. It really is
event driven execution design, which enables fine-grainedenergy
management, yet allowing arranging flexibility needed for
unpredictablecharacter of wireless communication plus physical world
interfaces.
A radio frequency (RF) signal refers to a wireless electromagnetic signal used
as a type of communication, if one is talking about wireless electronics.
Radio surf are a form of electromagnetic rays with identified radio
frequencies that will range from 3 kHz to three hundred GHz. Frequency
refers to the pace of oscillation (of radio stations waves.) RF distribution
occurs at the speed associated with light and does not need a moderate like
air in order to journey. RF waves occur from sunlight flares naturally,
lightning, and through stars in space that will radiate RF waves because they
age. Mankind communicates with artificially produced radio waves that
oscillate at various chosen frequencies. RF conversation is used in many
industries which includes television broadcasting, radar techniques,
computer and mobile system networks, remote control, remote
metering/monitoring, and many more.
WSN is one of the most evolving R&D field for microelectronics quickly. Their
apps and market potentials are usually increasing day-by-day. According to
Frost &Sullivan, the particular expected market size is going to be US$
2billion by this year at an approximatelycompound annual development of
41.9%.
WSN aims to monitor and to manage an environment sometimes. The
particular operational system operates to getperiods varying through weeks
to years within an autonomous way. The network iscomposed of many
sensor nodes that can be used on the ground, up,in automobile, inside
building. The Sensor Client comprises of sensing (measuring),processing, and
communication elements. The sink aggregates some or even all the
nodeinformation. Since sensor power cannot support long variety
communication to reach akitchen sink, multi-hop wireless connectivity is
needed to forward data to the remote control sink. Each ofthe dispersed
sensor nodes has the capacity to collect data, process all of them, and route
themin order to sink node. Router nodes are deployed in field to forward
information from sensor nodesin order to remote sink node. To aid node
operation, open supply operating system (OS) ismade for WSN specially. It
utilizes a component-based architecture that enables rapiddevelopment and
implementation while lessening code size as necessary by the
memoryconstraints in sensor systems. It includes network protocols,
dispersed services, sensordrivers, plus data acquisition tools. It really is
event driven execution design, which enables fine-grainedenergy
management, yet allowing arranging flexibility needed for
unpredictablecharacter of wireless communication plus physical world
interfaces.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CMOS chipsets optimized for WSN are key to the commercialization success.
Sensing,processing, plus communication can be performed on a single nick
now, additional reducingthe cost plus allowing deployment of many nodes.
Advances in MEMS (Microelectro-mechanical system) technologies will
produce sensors which are even more capableand flexible and yet are tiny
sufficient to fit inside a 1mm3 area. Available MEMS includestress,
temperature, humidity, strain measure, and various pies plus capacitive
transducersfor closeness, position, velocity, and speed and vibration
measurements.
Among the current R&D challenge would be to develop low power
conversation with low coston-node digesting and self-organizing
connectivity/protocols. One more critical challengeis limited power (battery
life). Power performance in WSN can be achieved inthree ways: lower duty
cycle operation, local/in-network processing to reduce data
quantity(transmission time), and multi-hop networking to reduce
requirement for lengthy range transmitting since signal path reduction is an
inverse exponent along with range or distance.The apps are varied. Ships,
airplane, and building can ‘self-detect’ structural faults;earthquake-oriented
sensors in building may locate potential survivors; tsunami-alertingdetectors
might be set up along the considerable coastal lines. Sensors can be used
within battlefieldto get surveillance and reconnaissance. This is merely a
potential list of ever-increasingapps in this certain area.
The introduction of wireless sensor networks had been motivated by
originallymilitary applications like battlefield surveillance. However, cellular
sensorsystems are now used in many commercial and civilian application
places, including commercialprocedure monitoring and control, machine
health supervising, environment and environmentmonitoring, healthcare
Sensing,processing, plus communication can be performed on a single nick
now, additional reducingthe cost plus allowing deployment of many nodes.
Advances in MEMS (Microelectro-mechanical system) technologies will
produce sensors which are even more capableand flexible and yet are tiny
sufficient to fit inside a 1mm3 area. Available MEMS includestress,
temperature, humidity, strain measure, and various pies plus capacitive
transducersfor closeness, position, velocity, and speed and vibration
measurements.
Among the current R&D challenge would be to develop low power
conversation with low coston-node digesting and self-organizing
connectivity/protocols. One more critical challengeis limited power (battery
life). Power performance in WSN can be achieved inthree ways: lower duty
cycle operation, local/in-network processing to reduce data
quantity(transmission time), and multi-hop networking to reduce
requirement for lengthy range transmitting since signal path reduction is an
inverse exponent along with range or distance.The apps are varied. Ships,
airplane, and building can ‘self-detect’ structural faults;earthquake-oriented
sensors in building may locate potential survivors; tsunami-alertingdetectors
might be set up along the considerable coastal lines. Sensors can be used
within battlefieldto get surveillance and reconnaissance. This is merely a
potential list of ever-increasingapps in this certain area.
The introduction of wireless sensor networks had been motivated by
originallymilitary applications like battlefield surveillance. However, cellular
sensorsystems are now used in many commercial and civilian application
places, including commercialprocedure monitoring and control, machine
health supervising, environment and environmentmonitoring, healthcare
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

apps, home automation, and visitors control [1]. Along with oneor more
sensors, every node in a sensor system is equipped with a radio transceiver
or typicallyother wireless communications gadget, a small microcontroller,
and a power source, generally abattery. The particular envisaged size of an
individual sensor node can vary through shoebox-sized nodes down to
gadgets the size of grain of dirt, although functioning 'motes' associated with
genuine microscopic dimensionshave got yet to be created. The price of
sensor nodes is likewise variable, ranging from hundreds ofpounds couple of
pence, depending on the size from the sensor network and the difficulty
required ofindividual nodes. Price and size constraints upon sensor nodes
result in relatedconstraints upon resources such as energy, storage,
computational bandwidth and speed.
Radio Frequency Identification (RFID) systems and Wireless Networks
(WSNs)are growing as the most ubiquitous processing technologies in history
due to theirimportant advantages and their wide applicability. RFID
communication is definitely fast, convenient, and the application can
substantially conserve time, improve services, decrease laborcost,
circumvent product counterfeiting and fraud, raise productivity gains, and
maintainquality standards. Common applications vary from highway toll
collection, providechain management, public transportation, managing
building access, animal monitoring,developing smart home appliances, plus
remote keyless entry for cars to locatingchildren.
RFID systems are mainly utilized to identify objects or to monitor their
location withoutproviding any indication about the health of the object. WSNs
in theother hand, are systems of small, cost-effective products that can
cooperate to gather and provide information by realizing environmental
conditions such as temperatures,light, humidity, pressure, oscillation, and
sound. WSNs offer cost-effectivemonitoring· of critical apps including
industrial control, edge monitoring, environmental· monitoring, army,
home applications, and health care applications.
RFID technology provides received great attention and contains been
deployed extensivelyin industrial applications. On the other hand, networks
have been the focus associated withgreat research activity however they
have been around mainly as a evidence of concept with· the primary
exception of their adoption within military applications. The advancement of
RFIDandWSNs provides followed separate research and development
pathways and has led to distincttechnologies. Nevertheless, there are many
applications in which the identity or the locationof an object is not sufficient
and additional information that can be retrieved via sensing ·environmental
conditions is essential. Even though sensor networks might be utilized in
theseenvironments as well, the place and identity of an item remain critical
informationthat can be retrieved via RFID systems. The perfect solution in
these full situations is theintegration of both technologies simply because
they complement each other.
sensors, every node in a sensor system is equipped with a radio transceiver
or typicallyother wireless communications gadget, a small microcontroller,
and a power source, generally abattery. The particular envisaged size of an
individual sensor node can vary through shoebox-sized nodes down to
gadgets the size of grain of dirt, although functioning 'motes' associated with
genuine microscopic dimensionshave got yet to be created. The price of
sensor nodes is likewise variable, ranging from hundreds ofpounds couple of
pence, depending on the size from the sensor network and the difficulty
required ofindividual nodes. Price and size constraints upon sensor nodes
result in relatedconstraints upon resources such as energy, storage,
computational bandwidth and speed.
Radio Frequency Identification (RFID) systems and Wireless Networks
(WSNs)are growing as the most ubiquitous processing technologies in history
due to theirimportant advantages and their wide applicability. RFID
communication is definitely fast, convenient, and the application can
substantially conserve time, improve services, decrease laborcost,
circumvent product counterfeiting and fraud, raise productivity gains, and
maintainquality standards. Common applications vary from highway toll
collection, providechain management, public transportation, managing
building access, animal monitoring,developing smart home appliances, plus
remote keyless entry for cars to locatingchildren.
RFID systems are mainly utilized to identify objects or to monitor their
location withoutproviding any indication about the health of the object. WSNs
in theother hand, are systems of small, cost-effective products that can
cooperate to gather and provide information by realizing environmental
conditions such as temperatures,light, humidity, pressure, oscillation, and
sound. WSNs offer cost-effectivemonitoring· of critical apps including
industrial control, edge monitoring, environmental· monitoring, army,
home applications, and health care applications.
RFID technology provides received great attention and contains been
deployed extensivelyin industrial applications. On the other hand, networks
have been the focus associated withgreat research activity however they
have been around mainly as a evidence of concept with· the primary
exception of their adoption within military applications. The advancement of
RFIDandWSNs provides followed separate research and development
pathways and has led to distincttechnologies. Nevertheless, there are many
applications in which the identity or the locationof an object is not sufficient
and additional information that can be retrieved via sensing ·environmental
conditions is essential. Even though sensor networks might be utilized in
theseenvironments as well, the place and identity of an item remain critical
informationthat can be retrieved via RFID systems. The perfect solution in
these full situations is theintegration of both technologies simply because
they complement each other.
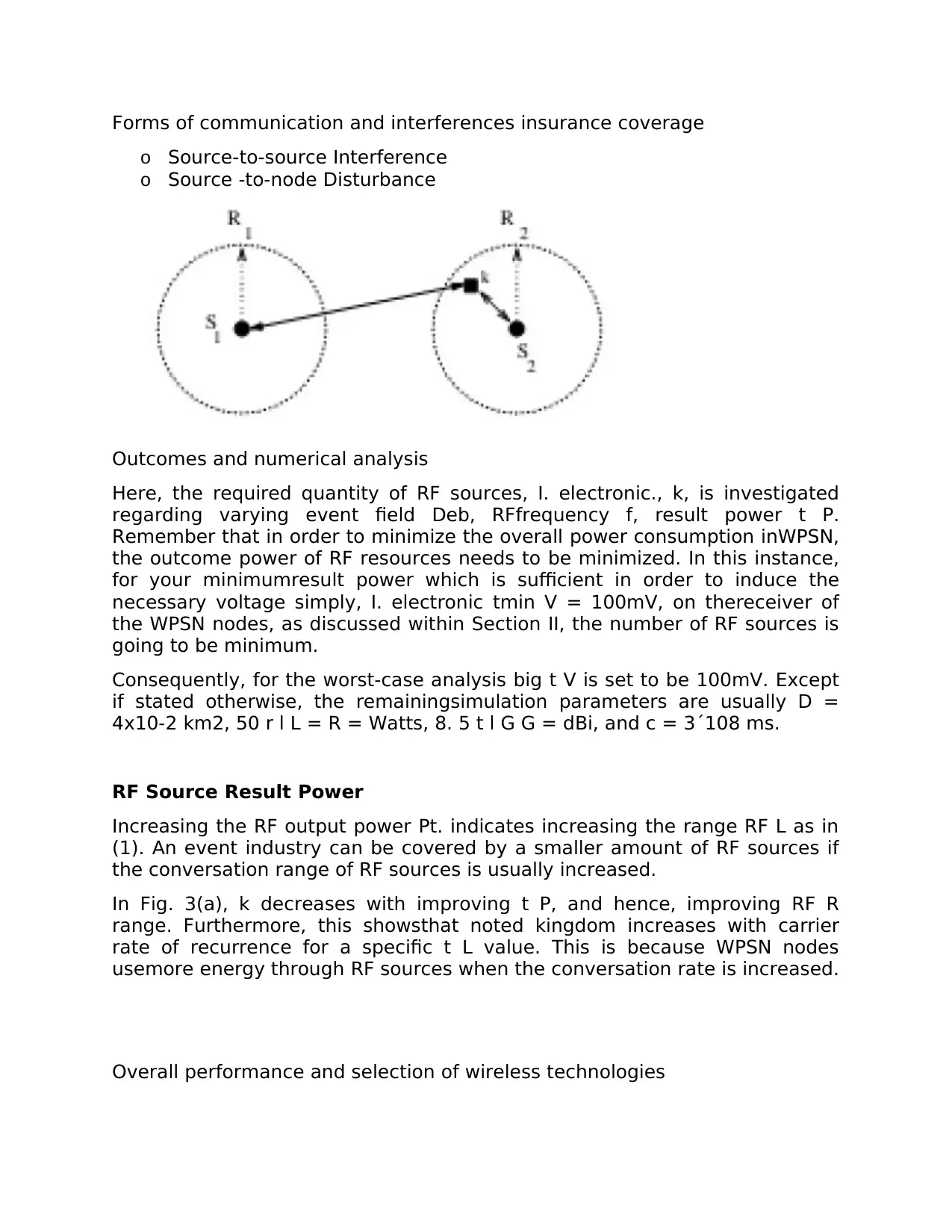
Forms of communication and interferences insurance coverage
o Source-to-source Interference
o Source -to-node Disturbance
Outcomes and numerical analysis
Here, the required quantity of RF sources, I. electronic., k, is investigated
regarding varying event field Deb, RFfrequency f, result power t P.
Remember that in order to minimize the overall power consumption inWPSN,
the outcome power of RF resources needs to be minimized. In this instance,
for your minimumresult power which is sufficient in order to induce the
necessary voltage simply, I. electronic tmin V = 100mV, on thereceiver of
the WPSN nodes, as discussed within Section II, the number of RF sources is
going to be minimum.
Consequently, for the worst-case analysis big t V is set to be 100mV. Except
if stated otherwise, the remainingsimulation parameters are usually D =
4x10-2 km2, 50 r l L = R = Watts, 8. 5 t l G G = dBi, and c = 3´108 ms.
RF Source Result Power
Increasing the RF output power Pt. indicates increasing the range RF L as in
(1). An event industry can be covered by a smaller amount of RF sources if
the conversation range of RF sources is usually increased.
In Fig. 3(a), k decreases with improving t P, and hence, improving RF R
range. Furthermore, this showsthat noted kingdom increases with carrier
rate of recurrence for a specific t L value. This is because WPSN nodes
usemore energy through RF sources when the conversation rate is increased.
Overall performance and selection of wireless technologies
o Source-to-source Interference
o Source -to-node Disturbance
Outcomes and numerical analysis
Here, the required quantity of RF sources, I. electronic., k, is investigated
regarding varying event field Deb, RFfrequency f, result power t P.
Remember that in order to minimize the overall power consumption inWPSN,
the outcome power of RF resources needs to be minimized. In this instance,
for your minimumresult power which is sufficient in order to induce the
necessary voltage simply, I. electronic tmin V = 100mV, on thereceiver of
the WPSN nodes, as discussed within Section II, the number of RF sources is
going to be minimum.
Consequently, for the worst-case analysis big t V is set to be 100mV. Except
if stated otherwise, the remainingsimulation parameters are usually D =
4x10-2 km2, 50 r l L = R = Watts, 8. 5 t l G G = dBi, and c = 3´108 ms.
RF Source Result Power
Increasing the RF output power Pt. indicates increasing the range RF L as in
(1). An event industry can be covered by a smaller amount of RF sources if
the conversation range of RF sources is usually increased.
In Fig. 3(a), k decreases with improving t P, and hence, improving RF R
range. Furthermore, this showsthat noted kingdom increases with carrier
rate of recurrence for a specific t L value. This is because WPSN nodes
usemore energy through RF sources when the conversation rate is increased.
Overall performance and selection of wireless technologies
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

When choosing the type(s) of Wi-Fi technology, it is vital to determine plus
understand the medical device features that are to be wirelessly allowed and
the intended use of the healthcare device. The medical gadget functions and
intended utilizes should be appropriately matched using the wireless
technology’s capabilities plus expected performance. In addition, problems
relating to the integrity associated with data transmitted wirelessly
(including latency and throughput, recognition, correction, and corruption
manage and/or prevention) and safety-related requirements of your device
should be thought about. Potential risks that can influence consistent and
timely cellular medical device functions consist of data corruption or
reduction and interference from simultaneous transmitters in a given place,
which increase and transmitted signal mistake rates latency. To get wireless
medical device plus devices systems, error manage processes should be
incorporated to make sure the integrity of information transmitted wirelessly
and to take care of potential risks related to optimum delay of data transfer.
Guidelines such as bit error price, packet loss, plus signal-to-noise ratio are
useful equipment in assessing and guaranteeing data timeliness and ethics
of data transmission.
Think about a RF wireless rate of recurrence band or a commercial Wi-Fi
radio component,
FDA suggests that you consider:
• Global availability and band share (e. g., applicable
GlobalTelecommunication Union Radio communication Industry (ITU-R)
4recommendations) for healthcare devices because medical gadgets serve
patientspositioned in multiple geographic locations plus patients might
change their own geographicplaces.
• Whether your device should have secondary or primary radio stations
serviceclassification, which is determined by the wireless frequency music
group you choose.
• Incumbent users of the adjoining and selected bands, if any kind of, and
how they canimpact the medical device’s operation.
• Applicable interference mitigation strategies if you are planning to use a
sharedRF wireless frequency band.
• For implantable and body-worn medical devices, tissue
distributioncharacteristics and specific assimilation rate as appropriate.
Risk-based approach to verification and affirmation
Wireless Quality associated with Service - The distribution should include
information toexplain the wireless QoS necessary for the intended use plus
understand the medical device features that are to be wirelessly allowed and
the intended use of the healthcare device. The medical gadget functions and
intended utilizes should be appropriately matched using the wireless
technology’s capabilities plus expected performance. In addition, problems
relating to the integrity associated with data transmitted wirelessly
(including latency and throughput, recognition, correction, and corruption
manage and/or prevention) and safety-related requirements of your device
should be thought about. Potential risks that can influence consistent and
timely cellular medical device functions consist of data corruption or
reduction and interference from simultaneous transmitters in a given place,
which increase and transmitted signal mistake rates latency. To get wireless
medical device plus devices systems, error manage processes should be
incorporated to make sure the integrity of information transmitted wirelessly
and to take care of potential risks related to optimum delay of data transfer.
Guidelines such as bit error price, packet loss, plus signal-to-noise ratio are
useful equipment in assessing and guaranteeing data timeliness and ethics
of data transmission.
Think about a RF wireless rate of recurrence band or a commercial Wi-Fi
radio component,
FDA suggests that you consider:
• Global availability and band share (e. g., applicable
GlobalTelecommunication Union Radio communication Industry (ITU-R)
4recommendations) for healthcare devices because medical gadgets serve
patientspositioned in multiple geographic locations plus patients might
change their own geographicplaces.
• Whether your device should have secondary or primary radio stations
serviceclassification, which is determined by the wireless frequency music
group you choose.
• Incumbent users of the adjoining and selected bands, if any kind of, and
how they canimpact the medical device’s operation.
• Applicable interference mitigation strategies if you are planning to use a
sharedRF wireless frequency band.
• For implantable and body-worn medical devices, tissue
distributioncharacteristics and specific assimilation rate as appropriate.
Risk-based approach to verification and affirmation
Wireless Quality associated with Service - The distribution should include
information toexplain the wireless QoS necessary for the intended use plus
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

use environment of thehealthcare device. This includes addressing any kind
of risks and potential efficiency issuesthat might be associated with
information rates, latency, and marketing communications reliability
asdescribed within Section 3-b.
Wi-Fi coexistence - Any dangers and potential performance problems that
might beassociated with wireless coexistence in a shared wireless
atmosphere should beresolved via testing and evaluation with other wireless
products or even devices that can beexpected to end up being located in the
wireless healthcare device’s intended use atmosphere
Protection of wireless signals plus data - The submitting should identify any
dangers,potential performance problems, and, if appropriate, danger
mitigation measures that mightend up being associated with wireless
security. The particular given information should include the
particularmeasures needed to protect against illegal wireless access to the
healthcare devicemanage or data and to make sure that given information
and information received by a device are usuallyintended for that will device.
For wireless technologies with a discovery mode or even similaractive
connection setting, specific information should be incorporated addressing
thediscovery setting and how outside users could be prevented from sensing
or even connecting tothe healthcare device. See Section 3-d.
EMC of the Wi-Fi technology - Information must be provided about howEMC
continues to be addressed for the device and everything wireless functions.
However, sincementioned in section 3-e., the particular widely used IEC
60601-1-2 general opinion standard does notcurrently address wireless
technology ELECTRONIC COUNTER MEASURE (ECM) adequately. Therefore,
assessment, analysis,plus appropriate mitigation might be essential to
address any risks or even adequatelypotential efficiency issues that might be
associated with the ELECTRONIC COUNTER MEASURE (ECM) of the
wirelessmedical gadget. If modifications to the healthcare device were made
to complete any EMCtesting, make sure you include a description of, plus
justification for, the adjustments.
Test data summaries
RF wireless and EMC outcomes and testing14 besummarized in your
premarket submitting, which should contain the followingdetails:
o Description of the assessments performed (e. g., RF wireless
performance, EMCdefenses and emissions, test levels or limits) and the
protocol used;
o Reference to appropriate medical gadget, RF wireless technology, or
even EMCstandards for the checks;
of risks and potential efficiency issuesthat might be associated with
information rates, latency, and marketing communications reliability
asdescribed within Section 3-b.
Wi-Fi coexistence - Any dangers and potential performance problems that
might beassociated with wireless coexistence in a shared wireless
atmosphere should beresolved via testing and evaluation with other wireless
products or even devices that can beexpected to end up being located in the
wireless healthcare device’s intended use atmosphere
Protection of wireless signals plus data - The submitting should identify any
dangers,potential performance problems, and, if appropriate, danger
mitigation measures that mightend up being associated with wireless
security. The particular given information should include the
particularmeasures needed to protect against illegal wireless access to the
healthcare devicemanage or data and to make sure that given information
and information received by a device are usuallyintended for that will device.
For wireless technologies with a discovery mode or even similaractive
connection setting, specific information should be incorporated addressing
thediscovery setting and how outside users could be prevented from sensing
or even connecting tothe healthcare device. See Section 3-d.
EMC of the Wi-Fi technology - Information must be provided about howEMC
continues to be addressed for the device and everything wireless functions.
However, sincementioned in section 3-e., the particular widely used IEC
60601-1-2 general opinion standard does notcurrently address wireless
technology ELECTRONIC COUNTER MEASURE (ECM) adequately. Therefore,
assessment, analysis,plus appropriate mitigation might be essential to
address any risks or even adequatelypotential efficiency issues that might be
associated with the ELECTRONIC COUNTER MEASURE (ECM) of the
wirelessmedical gadget. If modifications to the healthcare device were made
to complete any EMCtesting, make sure you include a description of, plus
justification for, the adjustments.
Test data summaries
RF wireless and EMC outcomes and testing14 besummarized in your
premarket submitting, which should contain the followingdetails:
o Description of the assessments performed (e. g., RF wireless
performance, EMCdefenses and emissions, test levels or limits) and the
protocol used;
o Reference to appropriate medical gadget, RF wireless technology, or
even EMCstandards for the checks;

o Explanations for any deviations from the selected standards;
o Mode(s) of device procedure during testing, with an description of
thesignificance of these settings;
o Specific pass/fail requirements for the testing such as particular
device-related acceptability criteria for each device setting or function
tested.
The particular integration of the promising systems of WSNs and RFID will
maximize theirefficiency, give new perspectives to some broad range of
useful apps, and bridgethe distance between the real and the
research/academic world. This is because theproducingbuilt-in technology
will have extended features, scalability, and movability as wellas reduced
unwanted costs.
Expansion of capabilities and benefits: Considering the fact that RFID
networkscan offer critical information, such as the identification and the
location of anitem, by merging RFIDs along with WSNs additional information
can be recovered, whilethe opportunity of exploiting this information is
increased. For instance, within supply chainmanagement we have been able
not only to track foods but also to monitor theirenvironment conditions and
detect whenever perishables go off.
Scalability-portability: RFID systems integrated with WSNs enjoy the
advantagesof Wi-Fi communication. The particular transmission and
processing associated with critical data and infois caused without the burden
and hassle of wired transactions whilstsaving valuable time. Transportable
RFID readers can more speed the collection of information andrelieve
procedures in varying programs. For instance, healthcare applications, which
includesmonitoring everyday medication associated with elderly or
o Mode(s) of device procedure during testing, with an description of
thesignificance of these settings;
o Specific pass/fail requirements for the testing such as particular
device-related acceptability criteria for each device setting or function
tested.
The particular integration of the promising systems of WSNs and RFID will
maximize theirefficiency, give new perspectives to some broad range of
useful apps, and bridgethe distance between the real and the
research/academic world. This is because theproducingbuilt-in technology
will have extended features, scalability, and movability as wellas reduced
unwanted costs.
Expansion of capabilities and benefits: Considering the fact that RFID
networkscan offer critical information, such as the identification and the
location of anitem, by merging RFIDs along with WSNs additional information
can be recovered, whilethe opportunity of exploiting this information is
increased. For instance, within supply chainmanagement we have been able
not only to track foods but also to monitor theirenvironment conditions and
detect whenever perishables go off.
Scalability-portability: RFID systems integrated with WSNs enjoy the
advantagesof Wi-Fi communication. The particular transmission and
processing associated with critical data and infois caused without the burden
and hassle of wired transactions whilstsaving valuable time. Transportable
RFID readers can more speed the collection of information andrelieve
procedures in varying programs. For instance, healthcare applications, which
includesmonitoring everyday medication associated with elderly or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

monitoring individuals for diagnosingdeceases, can be hugely facilitated
without rendering individuals immobile throughcumbersome data wirings.
Decrease unnecessary costs: Reducing the price of employed services is a
vital factorin many applications which includes industrial ones. The
requirement would be to achievethe desiredgoal along with the minimum
possible cost simply by supporting backup solutions in the event of
undesiredcircumstances. For instance, perishable goods can be monitored to
ensure that in case they arenot really preserved their transport could be
terminated properly, therefore avoiding unnecessaryadditional transport
costs.
Wi-Fi Quality of Service
Cellular Quality of Service (QoS) refers to the necessary level of assistance
and performance needed for the particular wireless functions of the
healthcare device. As the QoS of cellular phone networks might be
acceptable regarding voice communication, it may not be sufficient for
certain healthcare functions. Cable connections lost without warning, failure
to determine connections, or degradation associated with service can have
serious outcomes, especially when the medical device depends heavily on
the wireless link. Such situations may compromise the wireless transmitting
of high-priority medical gadget alarms, time-sensitive continuous physical
waveform data, and current control of therapeutic medical products (such as
wireless footswitches).
When the wireless medical device is going to be part of a network, wireless
QoS needs to be carefully considered in conjunction with the designed use of
the wireless medical gadget. The following should be assessed: suitable
latency, acceptable level of possibility for loss of information inside the
network, accessibility, and transmission priorities of the network.
without rendering individuals immobile throughcumbersome data wirings.
Decrease unnecessary costs: Reducing the price of employed services is a
vital factorin many applications which includes industrial ones. The
requirement would be to achievethe desiredgoal along with the minimum
possible cost simply by supporting backup solutions in the event of
undesiredcircumstances. For instance, perishable goods can be monitored to
ensure that in case they arenot really preserved their transport could be
terminated properly, therefore avoiding unnecessaryadditional transport
costs.
Wi-Fi Quality of Service
Cellular Quality of Service (QoS) refers to the necessary level of assistance
and performance needed for the particular wireless functions of the
healthcare device. As the QoS of cellular phone networks might be
acceptable regarding voice communication, it may not be sufficient for
certain healthcare functions. Cable connections lost without warning, failure
to determine connections, or degradation associated with service can have
serious outcomes, especially when the medical device depends heavily on
the wireless link. Such situations may compromise the wireless transmitting
of high-priority medical gadget alarms, time-sensitive continuous physical
waveform data, and current control of therapeutic medical products (such as
wireless footswitches).
When the wireless medical device is going to be part of a network, wireless
QoS needs to be carefully considered in conjunction with the designed use of
the wireless medical gadget. The following should be assessed: suitable
latency, acceptable level of possibility for loss of information inside the
network, accessibility, and transmission priorities of the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SAW VHMS Device
Since SAW devices are small, low power, tolerant to radiation, and work in
harsh environments at temperatures between -200°C and 910°C, the authors
at NASA are investigating them for aerospace applications. For VHMS
applications, a SAW device was fabricated on Langasite (La3Ga5SiO14)
substrate. The sensor has four Orthogonal Frequency Coded (OFC) reflector
gratings that spread the device’s response across multiple frequencies using
OFC reflectors [20]. The gratings are grouped into two reflector banks. To
avoid interference, the reflector banks are positioned on either side of an
interdigitated transducer (IDT) and are spaced so the reflections do not
overlap in time. The reflector banks are spaced 1.722 mm (left) and 3.710
mm (right) from the IDT. The number of fingers in each grating is 98, 99,
100, and 101. The four gratings have frequencies of 300.05, 303.04, 306.10,
and 309.28 MHz arranged in order from f1, f2, f3, to f4, with f1 closest to the
IDT. More diverse frequency arrangements comprising a reflector bank would
allow more code diversity when uniquely identifying the sensor in a
multisensory environment.
The IDT must be broadband and encompass the frequency content of all four
reflectors so it effectively has 23 finger pairs, a center frequency of 304.61
MHz, and a null bandwidth of 13.25 MHz for the main lobe. The reflectors
have a null bandwidth of ~3.061 MHz each. The IDT fingers are 1.5 μm wide
by 899.83 μm in length.
The SAW device can be used to take measurements because physical
changes in the device will result in achange in operating frequency.
Expansion of the SAW device results in a decreased operating frequency due
Since SAW devices are small, low power, tolerant to radiation, and work in
harsh environments at temperatures between -200°C and 910°C, the authors
at NASA are investigating them for aerospace applications. For VHMS
applications, a SAW device was fabricated on Langasite (La3Ga5SiO14)
substrate. The sensor has four Orthogonal Frequency Coded (OFC) reflector
gratings that spread the device’s response across multiple frequencies using
OFC reflectors [20]. The gratings are grouped into two reflector banks. To
avoid interference, the reflector banks are positioned on either side of an
interdigitated transducer (IDT) and are spaced so the reflections do not
overlap in time. The reflector banks are spaced 1.722 mm (left) and 3.710
mm (right) from the IDT. The number of fingers in each grating is 98, 99,
100, and 101. The four gratings have frequencies of 300.05, 303.04, 306.10,
and 309.28 MHz arranged in order from f1, f2, f3, to f4, with f1 closest to the
IDT. More diverse frequency arrangements comprising a reflector bank would
allow more code diversity when uniquely identifying the sensor in a
multisensory environment.
The IDT must be broadband and encompass the frequency content of all four
reflectors so it effectively has 23 finger pairs, a center frequency of 304.61
MHz, and a null bandwidth of 13.25 MHz for the main lobe. The reflectors
have a null bandwidth of ~3.061 MHz each. The IDT fingers are 1.5 μm wide
by 899.83 μm in length.
The SAW device can be used to take measurements because physical
changes in the device will result in achange in operating frequency.
Expansion of the SAW device results in a decreased operating frequency due

to tensile strain or a temperature increase, while contraction due to
compressive strain or reduced temperature results in
an increase in the operating frequency. These changes are due in part to a
change in the wavelength and a change in the average propagation velocity
of the surface acoustic wave. The velocity changes are due to changes in the
stiffness parameters and the density of the material.
To demonstrate its capabilities, the SAW device is measuring strain on a
panel with bolted side stiffeners to simulate repeatable fastener failure. This
panel is similar to panels suggested by Worden for structural health
monitoring [23]. The aluminum panel is 635 mm wide and 939 mm long. The
panel is 2.29 mm thick, aluminum (6051 alloy). The side stiffeners are made
of 254 mm “L” shaped aluminum (6051 alloy) extrusions that are 1.587 mm
thick. The bolts are spaced 50.8 mm apart. The root of the panel mounts to a
steel plate using 26 bolts and a 629 mm x 50.8 mm x 76.2 mm base plate of
aluminum on top of both the panel and side stiffeners. To distribute the force
from hanging weights, a 629 mm x 25.4 mm x 12.7 mm steel plate attaches
to the end of the panel.
Formulae and Equations Involved
(i) Pr=PtGtGr(λ/4ΠRrf) -------------------------(1)
Pt = Transmitted power by the RF source
Pr = Received power on the passive sensor node,
GtGr = Antenna gains
Rrf = communication range of an RF source.
(ii) Pr= ׀Vt2 ׀/( 8(Rr+Rl))---------------------- (2)
Vt2 = Incident signal from RF source.
Rr+Rl = antenna impedance
(iii) k= ∆/(ΠR2rf)---------------------------------(3)
k= Required number of RF sources to provide MB based
communication coverage
∆= Event area of size
(iv) k= 2 Π ∆ f2 ׀Vt2 /( c2PtGtGr(Rr+Rl))) ------(4)
The above represents the final equation for calculating the number of RF
sources required for interference free communication.
compressive strain or reduced temperature results in
an increase in the operating frequency. These changes are due in part to a
change in the wavelength and a change in the average propagation velocity
of the surface acoustic wave. The velocity changes are due to changes in the
stiffness parameters and the density of the material.
To demonstrate its capabilities, the SAW device is measuring strain on a
panel with bolted side stiffeners to simulate repeatable fastener failure. This
panel is similar to panels suggested by Worden for structural health
monitoring [23]. The aluminum panel is 635 mm wide and 939 mm long. The
panel is 2.29 mm thick, aluminum (6051 alloy). The side stiffeners are made
of 254 mm “L” shaped aluminum (6051 alloy) extrusions that are 1.587 mm
thick. The bolts are spaced 50.8 mm apart. The root of the panel mounts to a
steel plate using 26 bolts and a 629 mm x 50.8 mm x 76.2 mm base plate of
aluminum on top of both the panel and side stiffeners. To distribute the force
from hanging weights, a 629 mm x 25.4 mm x 12.7 mm steel plate attaches
to the end of the panel.
Formulae and Equations Involved
(i) Pr=PtGtGr(λ/4ΠRrf) -------------------------(1)
Pt = Transmitted power by the RF source
Pr = Received power on the passive sensor node,
GtGr = Antenna gains
Rrf = communication range of an RF source.
(ii) Pr= ׀Vt2 ׀/( 8(Rr+Rl))---------------------- (2)
Vt2 = Incident signal from RF source.
Rr+Rl = antenna impedance
(iii) k= ∆/(ΠR2rf)---------------------------------(3)
k= Required number of RF sources to provide MB based
communication coverage
∆= Event area of size
(iv) k= 2 Π ∆ f2 ׀Vt2 /( c2PtGtGr(Rr+Rl))) ------(4)
The above represents the final equation for calculating the number of RF
sources required for interference free communication.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




