Wireless Network Design, RFID and NFC Technologies: A Detailed Report
VerifiedAdded on 2023/06/04
|25
|885
|138
Report
AI Summary
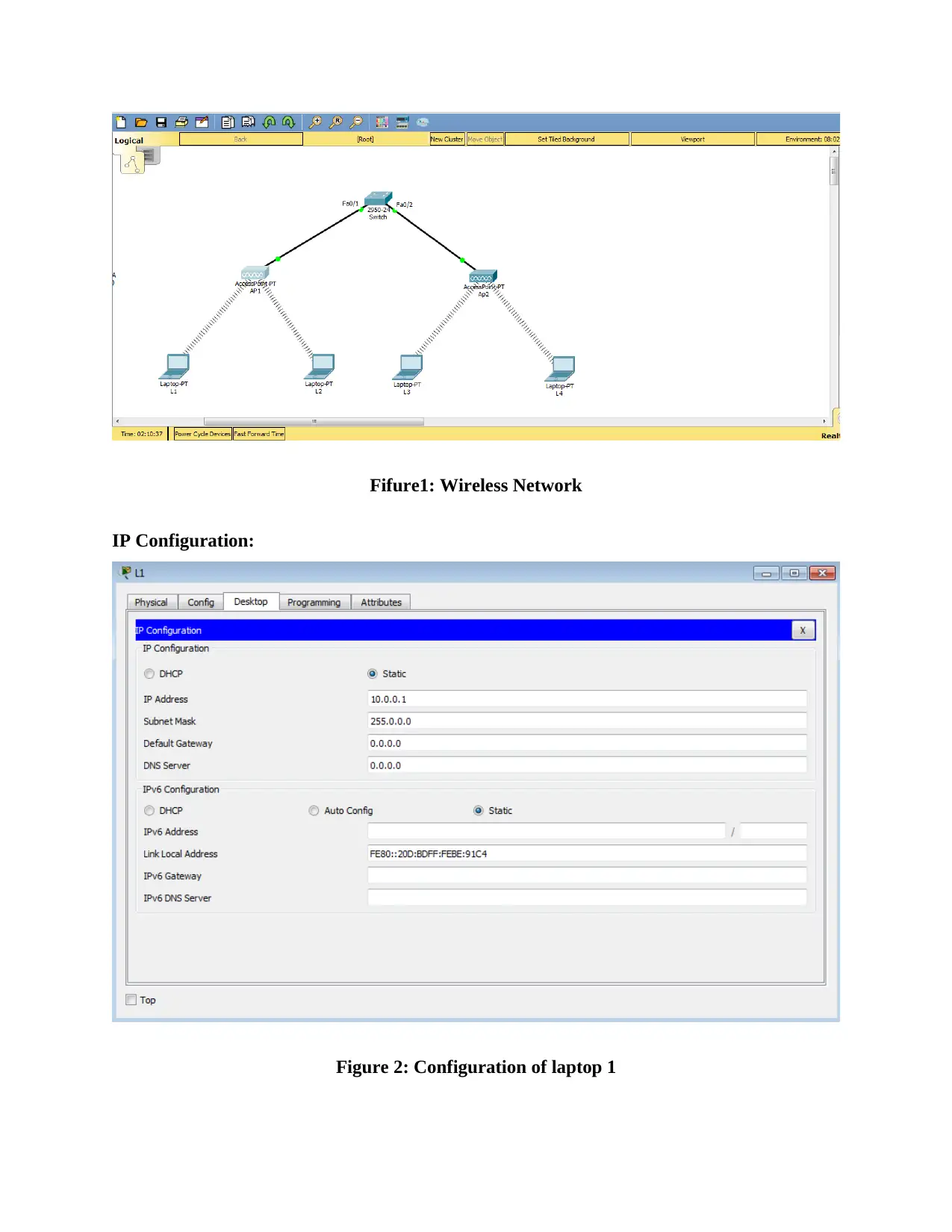
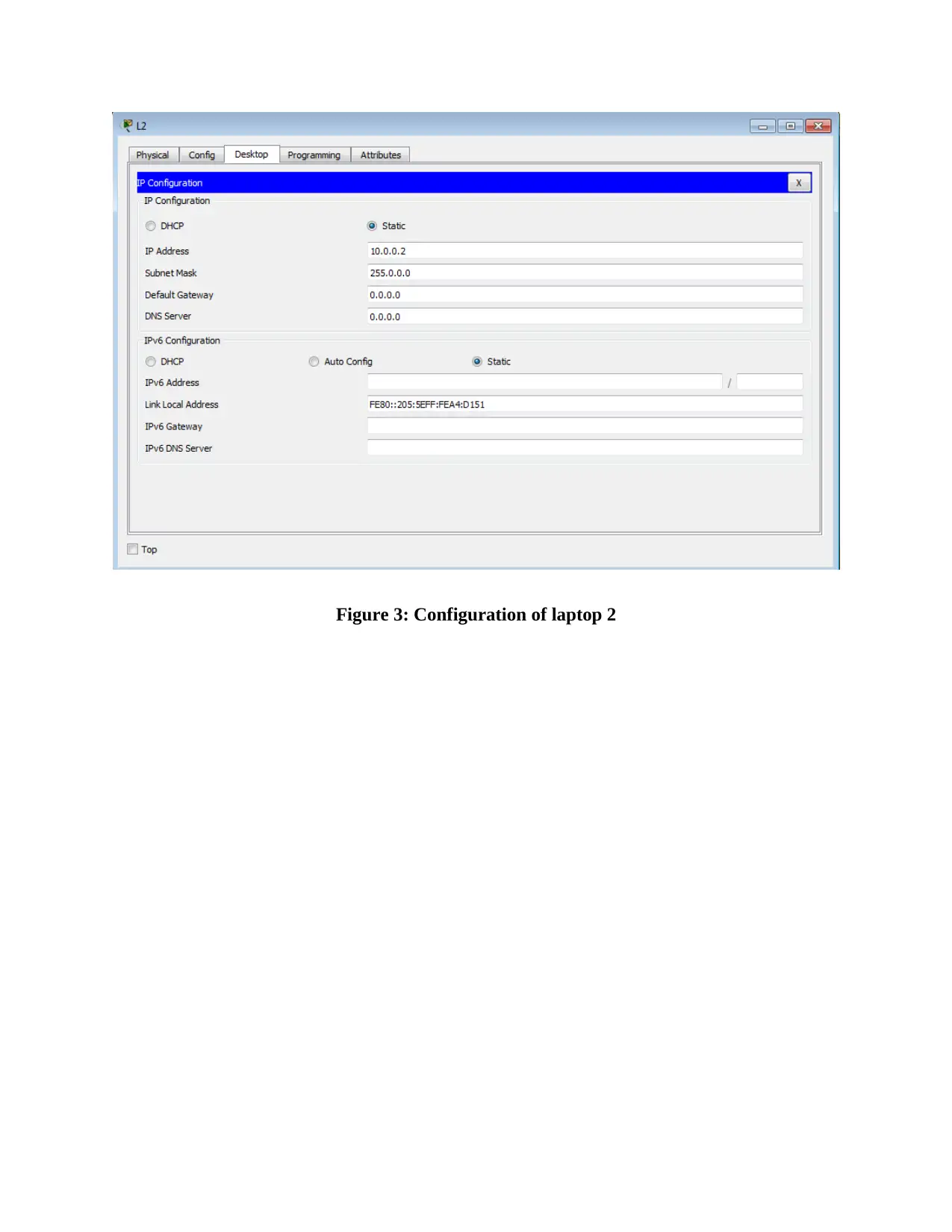
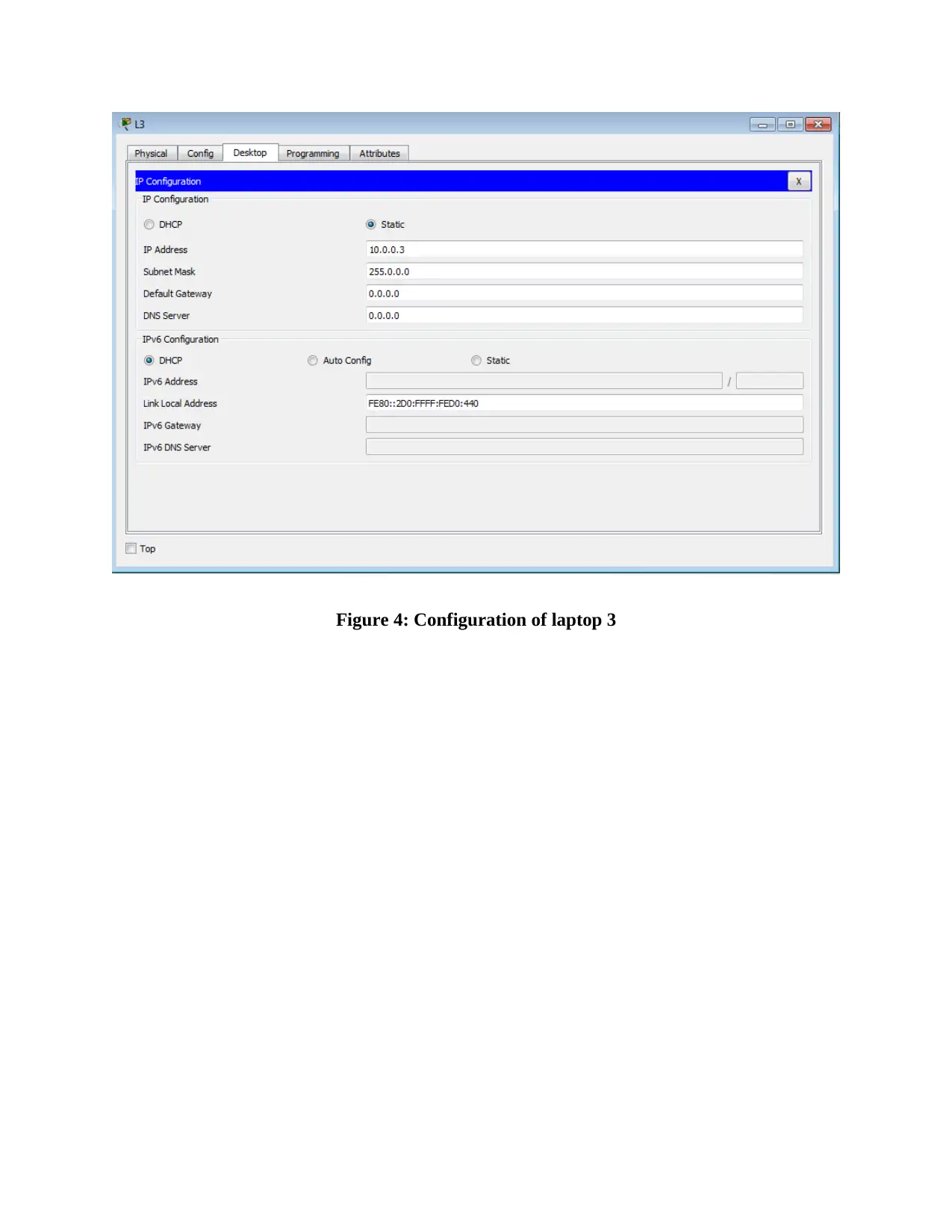
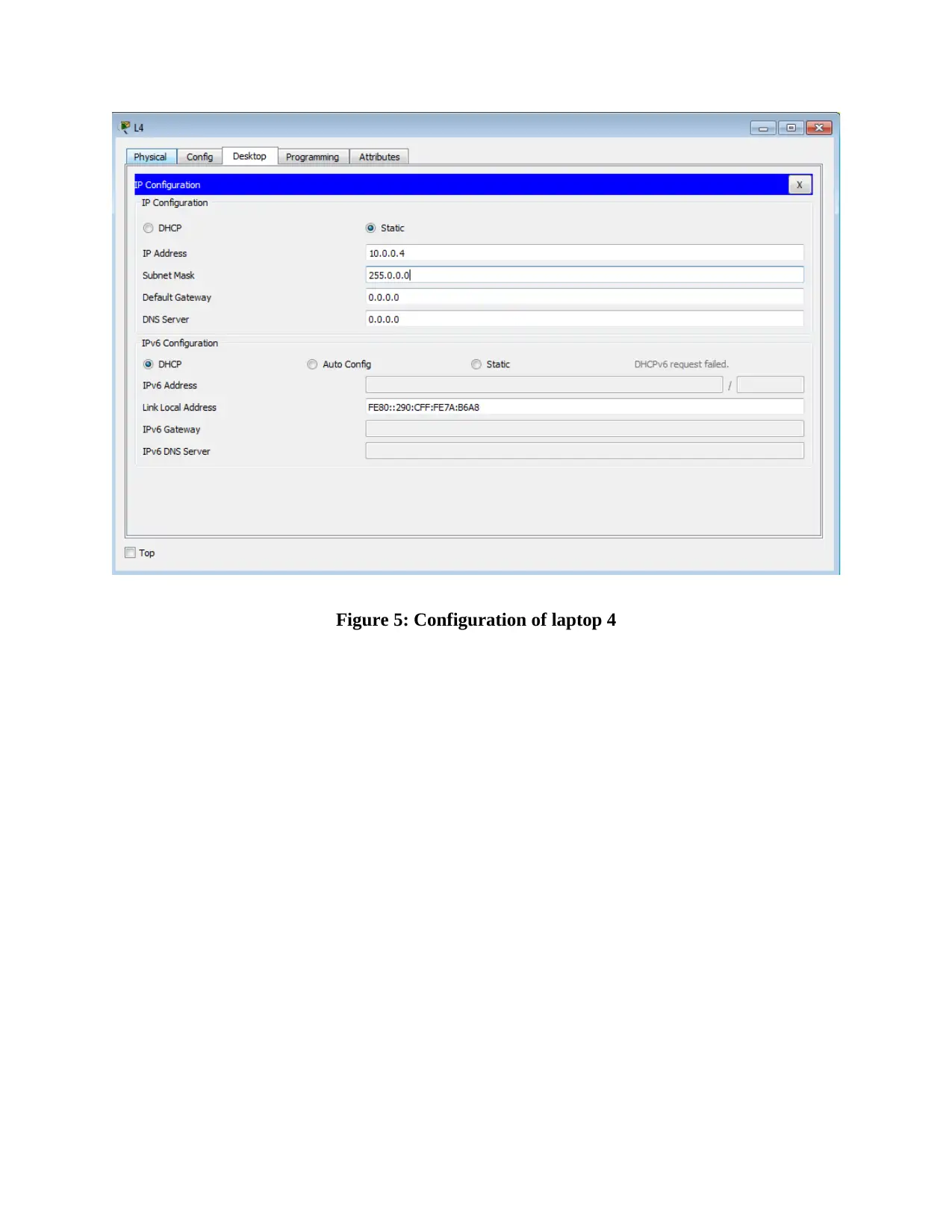
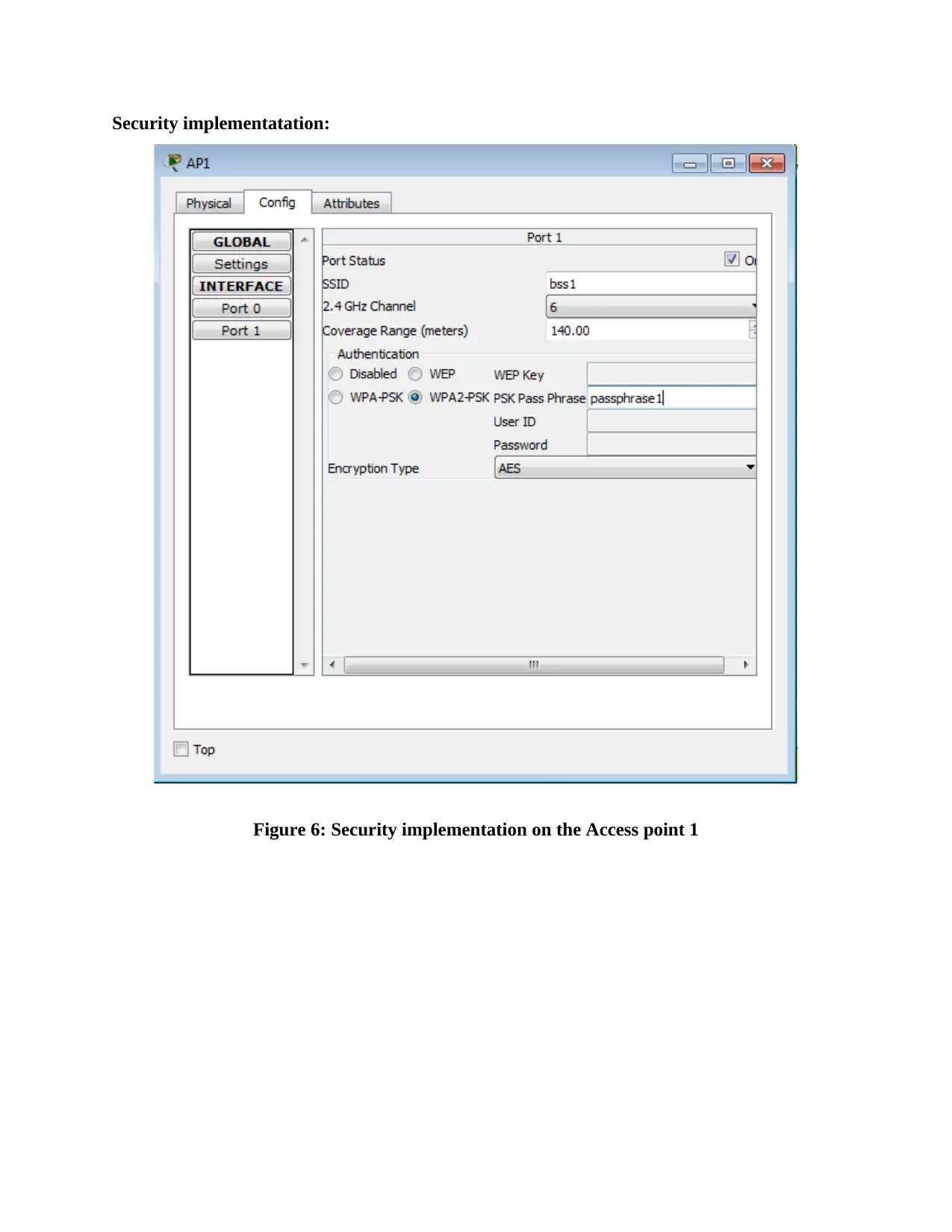
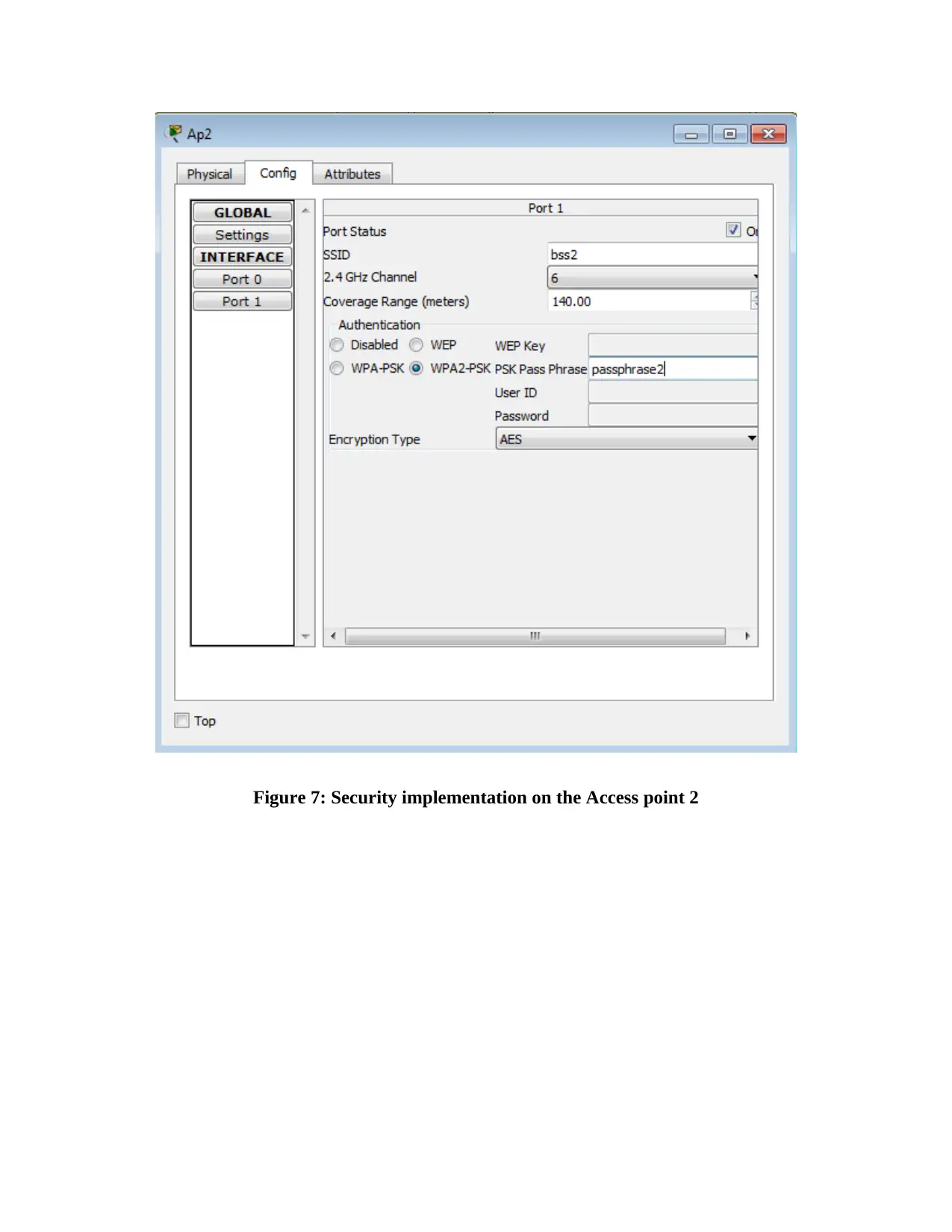
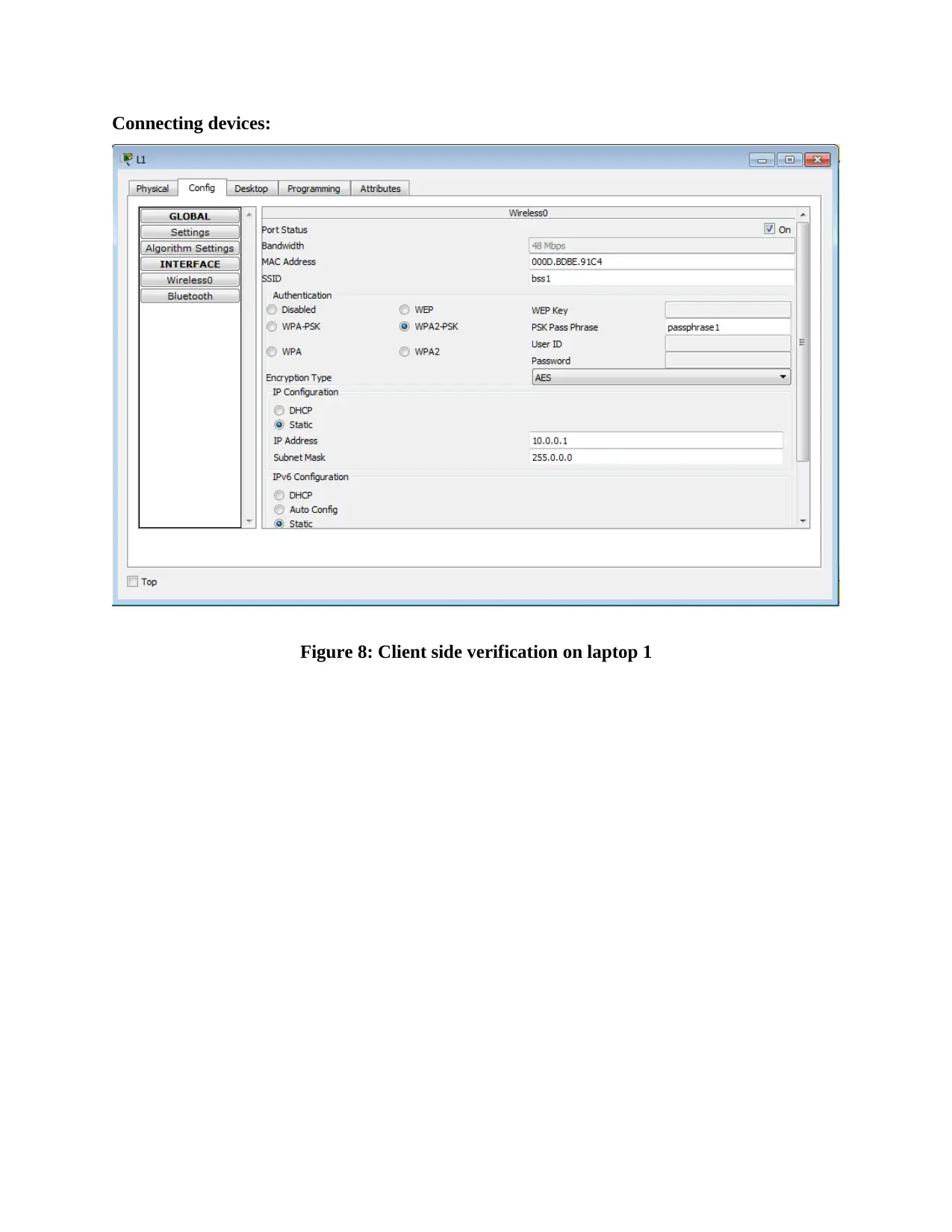
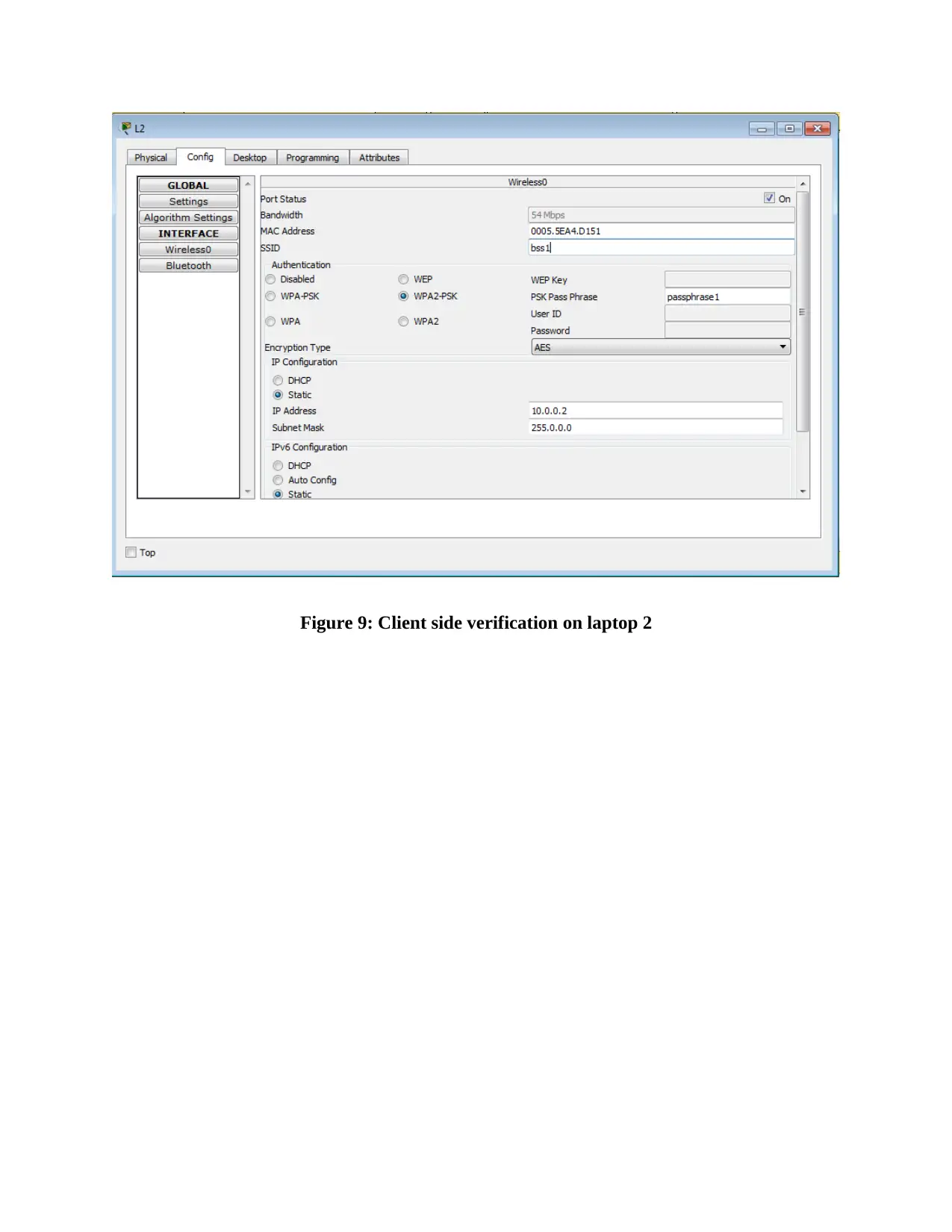
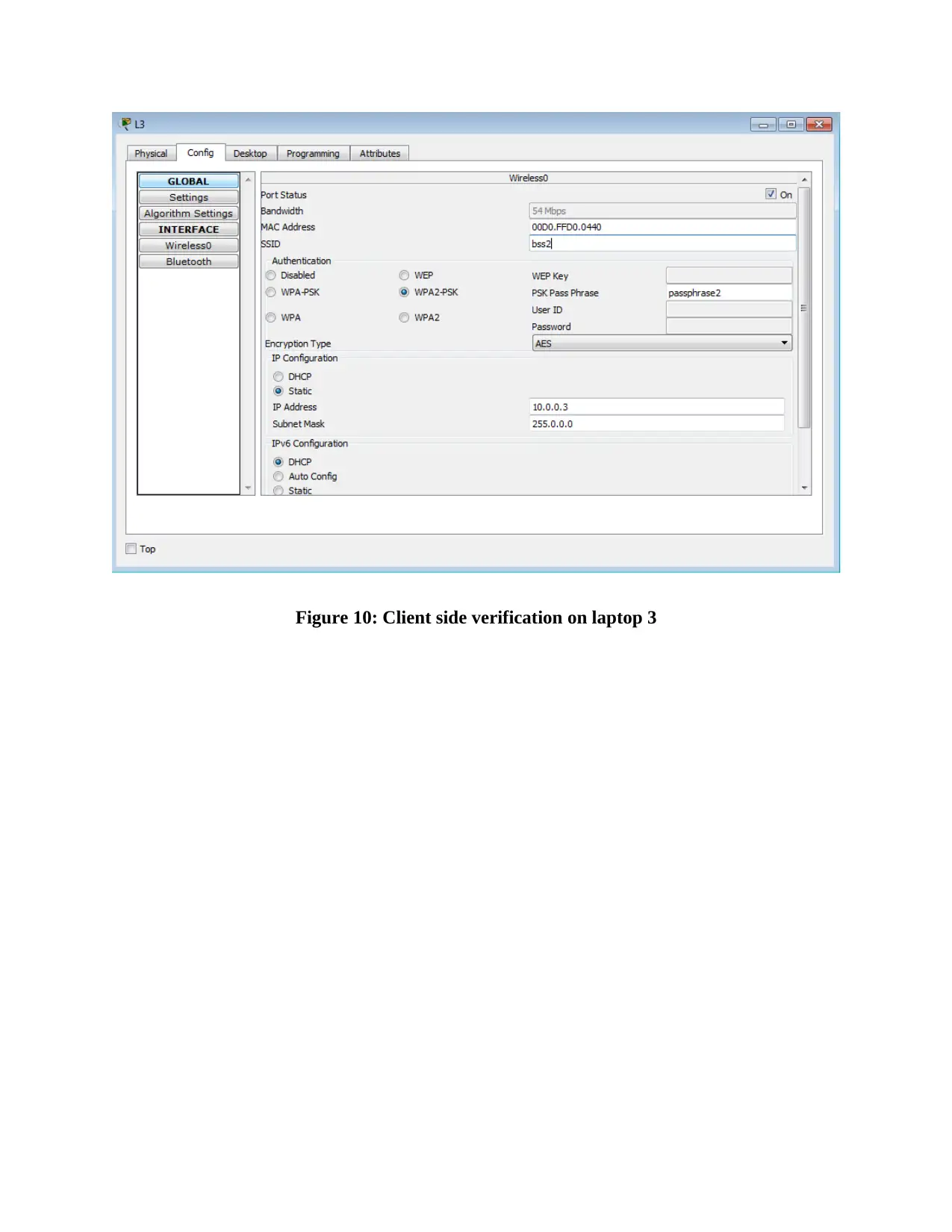
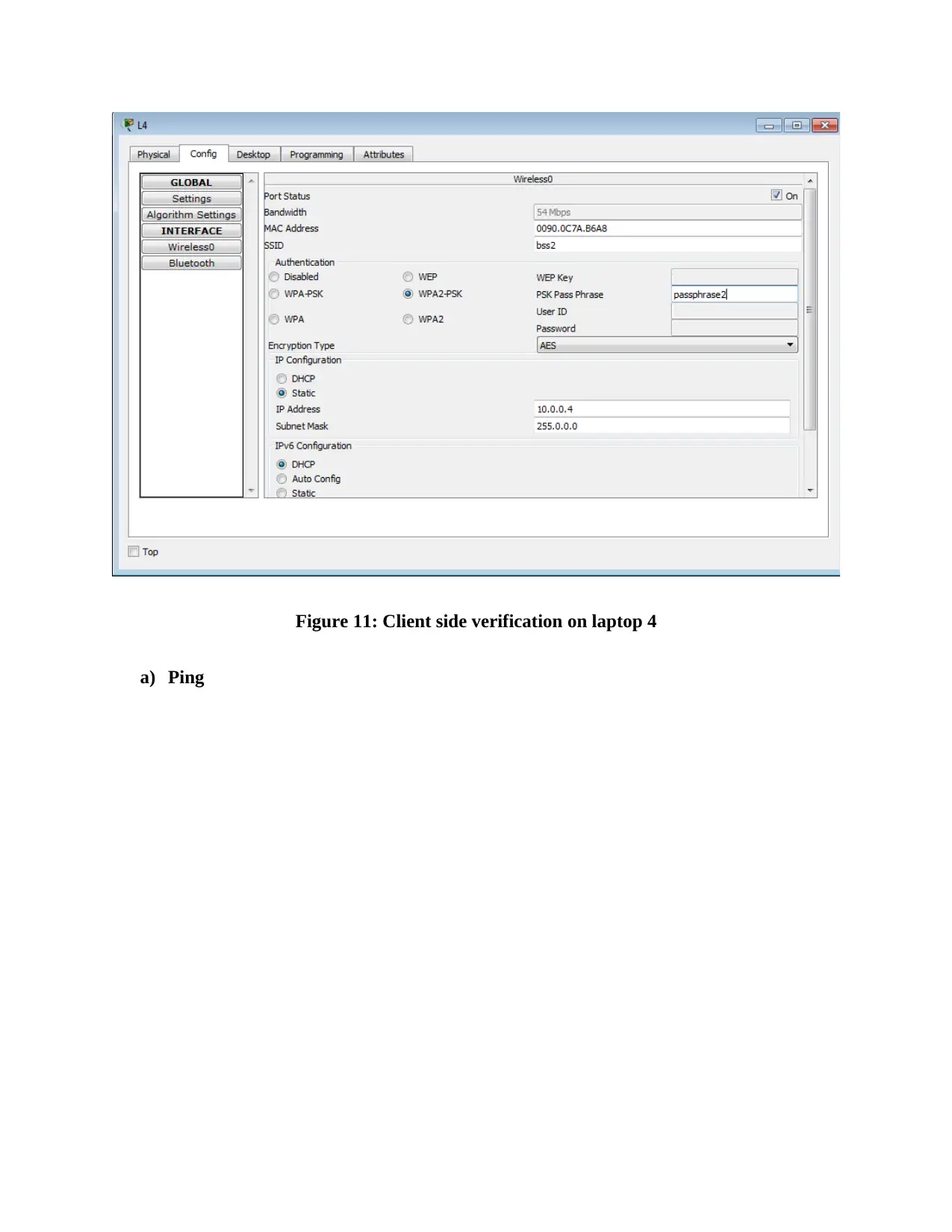
This report provides an overview of RFID (Radio Frequency Identification) and NFC (Near Field Communication) technologies, detailing their functionalities, applications, and challenges. It compares and contrasts the two technologies, highlighting their operational differences, security aspects, and potential vulnerabilities. The report also delves into wireless network design, including IP configuration of multiple laptops, security implementations on access points, and client-side verification processes. Furthermore, it presents the results of ping tests, channel configurations, and mismatch tests to assess network performance and identify potential issues. The report concludes with a comprehensive analysis of the practical aspects of wireless network setup and the application of RFID and NFC technologies in real-world scenarios, supported by relevant figures and references.
1 out of 25








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)