ENISA: A Case Study of Big Data Security and Privacy
VerifiedAdded on 2019/11/20
|15
|3196
|160
Report
AI Summary
The assignment content discusses the importance of addressing security and privacy issues in Big Data analytics. It highlights the challenges posed by the increasing amount of sensitive data being generated daily, including social media posts, IoT devices, and other digital sources. The article emphasizes the need for effective data management and control measures to ensure the confidentiality, integrity, and availability of Big Data. Furthermore, it explores various security and privacy issues associated with Big Data, such as data breaches, unauthorized access, and lack of transparency. It also discusses different techniques and technologies being used to address these challenges, including encryption, secure communication protocols, and data anonymization. Overall, the assignment content underscores the significance of prioritizing Big Data security and privacy in today's digital age.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Risk Analysis and Security: ENISA case study
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Risk Analysis and Security: ENISA case study
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Table of Contents
Introduction..........................................................................................................................3
1. Scenario of Big Data security infrastructure...................................................................3
1.2 Big Data security infrastructure for ENISA..................................................................5
2. Top Threat in the ENISA.................................................................................................8
3. Key Threat Agents and their Impact Reduction Options.................................................9
4. Enhancement of ETL process........................................................................................12
5. Justification of IT security in ENISA............................................................................12
Conclusion.........................................................................................................................13
References..........................................................................................................................14
Table of Contents
Introduction..........................................................................................................................3
1. Scenario of Big Data security infrastructure...................................................................3
1.2 Big Data security infrastructure for ENISA..................................................................5
2. Top Threat in the ENISA.................................................................................................8
3. Key Threat Agents and their Impact Reduction Options.................................................9
4. Enhancement of ETL process........................................................................................12
5. Justification of IT security in ENISA............................................................................12
Conclusion.........................................................................................................................13
References..........................................................................................................................14

2RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Introduction
Risk analysis and security is considered as important for an organization to implement
effective operations as well as integration of improving the system. In this point of view,
improvement of the project would help to incorporate the procedure of advancement of
operations and in addition apply successful capacities inside the specific organization. In
addition, operational processing can be suggested keeping in mind the end goal to shape risk
analysis related with the association. The operational preparing can be suggested with a specific
end goal to shape investigation of dangers may be confronted by the associations at the season of
performing operations and in addition capacities in light of advancement of operations for mix of
capacities for strategies of the undertaking.
The report would help the way toward coordinating the capacities and operations of the
association so as to create risk assessment as well as analysis. Along with these, it would tend
assessing the part of innovation for execution of effective risk through breaking down the
contextual study of ENISA. In this aspect, practicing big data strategy would improve operations
inside the organization. Then again, the utilization of big data in the organization has
distinguished the issues and additionally dangers of security for the undertaking. Consequently,
examination of dangers of big data technique for ENISA would depict agents of threats.
1. Scenario of Big Data security infrastructure
The enterprise had deployed big data analytics keeping in mind the end goal to create
compelling operations and development of the organization. ENISA deployed big data strategy
inside the enterprise with a specific end goal to increase competitive advantage (Patil &
Introduction
Risk analysis and security is considered as important for an organization to implement
effective operations as well as integration of improving the system. In this point of view,
improvement of the project would help to incorporate the procedure of advancement of
operations and in addition apply successful capacities inside the specific organization. In
addition, operational processing can be suggested keeping in mind the end goal to shape risk
analysis related with the association. The operational preparing can be suggested with a specific
end goal to shape investigation of dangers may be confronted by the associations at the season of
performing operations and in addition capacities in light of advancement of operations for mix of
capacities for strategies of the undertaking.
The report would help the way toward coordinating the capacities and operations of the
association so as to create risk assessment as well as analysis. Along with these, it would tend
assessing the part of innovation for execution of effective risk through breaking down the
contextual study of ENISA. In this aspect, practicing big data strategy would improve operations
inside the organization. Then again, the utilization of big data in the organization has
distinguished the issues and additionally dangers of security for the undertaking. Consequently,
examination of dangers of big data technique for ENISA would depict agents of threats.
1. Scenario of Big Data security infrastructure
The enterprise had deployed big data analytics keeping in mind the end goal to create
compelling operations and development of the organization. ENISA deployed big data strategy
inside the enterprise with a specific end goal to increase competitive advantage (Patil &

3RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Seshadri, 2014). In this viewpoint, risk and threat management should be effectively implied for
creating powerful development of operations. Big data threats would bring about advancement of
incidental threats for ENISA in incorporating the framework inside the organization. The
undertaking is considered as one of the efficient system for security, which is proficient
observing the particular stream of the operations inside the endeavor and additionally suggest
productive security framework inside the enterprise (Sagiroglu & Sinanc, 2013). In any case,
protection in huge information is considered as central point assuming a pivotal part in
implantation of advancement show for ENISA. In this viewpoint, operations of the undertaking
would be profoundly upgraded through use of enormous information procedure inside the
association.
In addition, ENSIA had implied ICT based solutions enhancing security works with a
specific end goal to oversee enormous information procedure in the project. Thuraisingham
(2015) stated that various proprietors are giving different models to the change of the ICT
devices in the enterprise including information proprietors, information transformers as well as
computation. These models help in giving compelling management if the data is not secured in
the organization (Vatsalan et al. 2017). There are different practices that are analytics in the
enterprise for overseeing risk and management of information utilized the association. The
procedure of operating in the organizations suggested in the risk management for procuring the
security of data and information in the organization. Therefore, the advancement of the risk
management evaluation helps in keeping up the security of the information and data in the
association.
Seshadri, 2014). In this viewpoint, risk and threat management should be effectively implied for
creating powerful development of operations. Big data threats would bring about advancement of
incidental threats for ENISA in incorporating the framework inside the organization. The
undertaking is considered as one of the efficient system for security, which is proficient
observing the particular stream of the operations inside the endeavor and additionally suggest
productive security framework inside the enterprise (Sagiroglu & Sinanc, 2013). In any case,
protection in huge information is considered as central point assuming a pivotal part in
implantation of advancement show for ENISA. In this viewpoint, operations of the undertaking
would be profoundly upgraded through use of enormous information procedure inside the
association.
In addition, ENSIA had implied ICT based solutions enhancing security works with a
specific end goal to oversee enormous information procedure in the project. Thuraisingham
(2015) stated that various proprietors are giving different models to the change of the ICT
devices in the enterprise including information proprietors, information transformers as well as
computation. These models help in giving compelling management if the data is not secured in
the organization (Vatsalan et al. 2017). There are different practices that are analytics in the
enterprise for overseeing risk and management of information utilized the association. The
procedure of operating in the organizations suggested in the risk management for procuring the
security of data and information in the organization. Therefore, the advancement of the risk
management evaluation helps in keeping up the security of the information and data in the
association.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
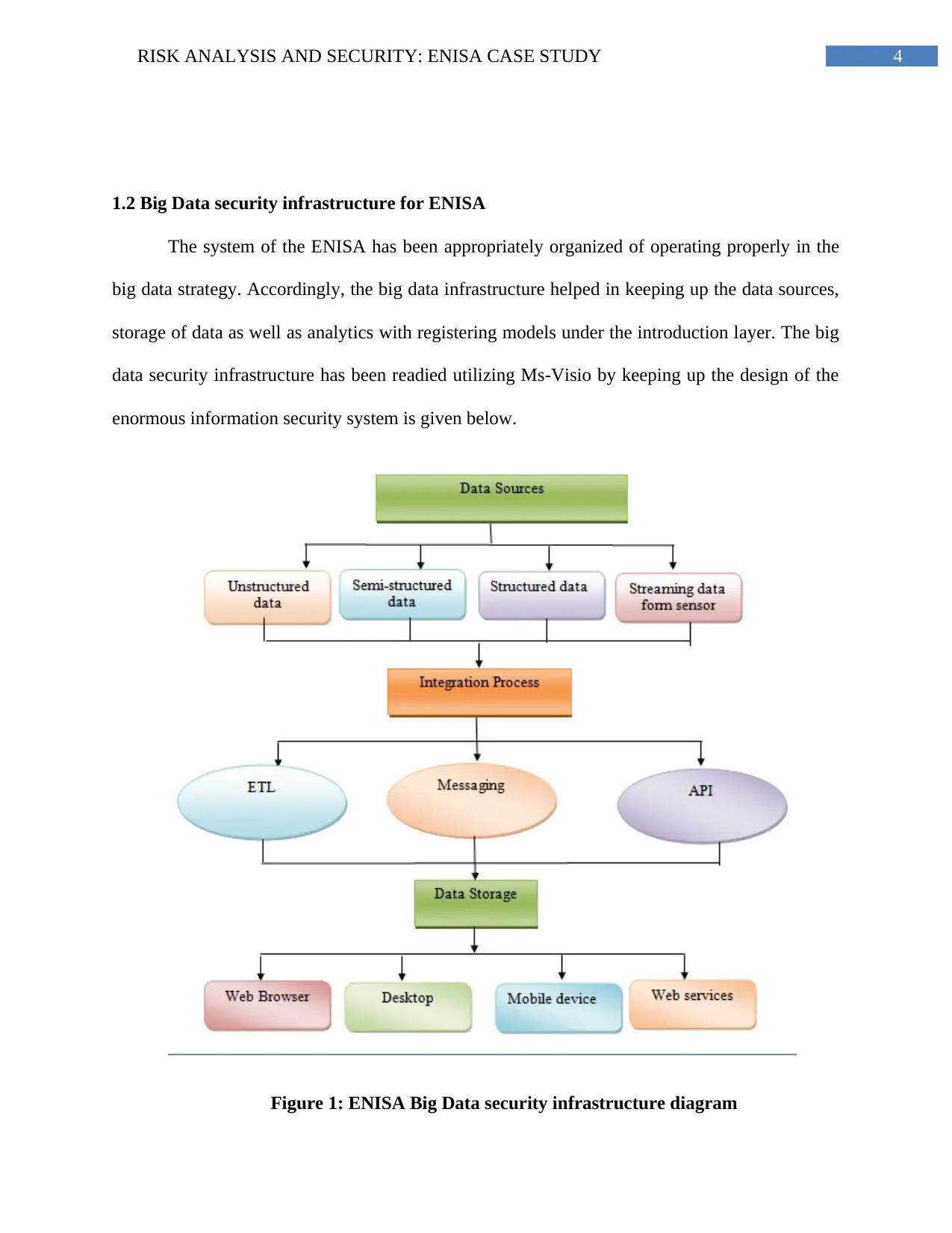
4RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
1.2 Big Data security infrastructure for ENISA
The system of the ENISA has been appropriately organized of operating properly in the
big data strategy. Accordingly, the big data infrastructure helped in keeping up the data sources,
storage of data as well as analytics with registering models under the introduction layer. The big
data security infrastructure has been readied utilizing Ms-Visio by keeping up the design of the
enormous information security system is given below.
Figure 1: ENISA Big Data security infrastructure diagram
1.2 Big Data security infrastructure for ENISA
The system of the ENISA has been appropriately organized of operating properly in the
big data strategy. Accordingly, the big data infrastructure helped in keeping up the data sources,
storage of data as well as analytics with registering models under the introduction layer. The big
data security infrastructure has been readied utilizing Ms-Visio by keeping up the design of the
enormous information security system is given below.
Figure 1: ENISA Big Data security infrastructure diagram
5RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
(Source: Created by author)
The layered structure of ENISA is able to keep up the big data implementation and
reconciliation for keeping up the improvement of the system in the organization (Wu et al.
2014). The successful execution of the big data analytics has helped in building up the
organization in the market. There are different layers of the enormous information including the
information sources, investigation, information stockpiling, and introduction layer and
computing models. The operations of the big data infrastructure have been capable to eliminate
the security threats in the database of the organization.
The security data of the organization has been keeping up the security of the information
and data of the association (Baumer, 2017). There are different security protocols utilized by the
organization in the market including Ranger, Encryption, KNOX as well as Firewall. This safety
effort helps in keeping up the security of the big data infrastructure of ENISA. The particular
capacity identified with the database of the ENISA has been appeared in the table underneath:
Security
Function
Description Big data
structure
layer of the
ENISA
Components in big data
structure layer of the
ENISA
KNOX It provides particular solution as
well as real time protection of data
sources when added (Cardenas et al.
2013). In addition, the KNOX gives
effective control of the strategies
Data Sources
layer
Data Sources layer
consists of components
of streaming data from
the sensors as well as
unstructured data and
(Source: Created by author)
The layered structure of ENISA is able to keep up the big data implementation and
reconciliation for keeping up the improvement of the system in the organization (Wu et al.
2014). The successful execution of the big data analytics has helped in building up the
organization in the market. There are different layers of the enormous information including the
information sources, investigation, information stockpiling, and introduction layer and
computing models. The operations of the big data infrastructure have been capable to eliminate
the security threats in the database of the organization.
The security data of the organization has been keeping up the security of the information
and data of the association (Baumer, 2017). There are different security protocols utilized by the
organization in the market including Ranger, Encryption, KNOX as well as Firewall. This safety
effort helps in keeping up the security of the big data infrastructure of ENISA. The particular
capacity identified with the database of the ENISA has been appeared in the table underneath:
Security
Function
Description Big data
structure
layer of the
ENISA
Components in big data
structure layer of the
ENISA
KNOX It provides particular solution as
well as real time protection of data
sources when added (Cardenas et al.
2013). In addition, the KNOX gives
effective control of the strategies
Data Sources
layer
Data Sources layer
consists of components
of streaming data from
the sensors as well as
unstructured data and
6RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
implied for developing the enhanced
control of the functions in terms of
security.
semi-structured data,
along with structured data
Ranger It is authorization system assisting in
making limitation for the user access
in big data system, defined by the
Ranger policies. The user needs to
request to Ranger to receive the
authenticated entry into specific
system
Analytics as
well as
Computing
Models layer
And
Integration
Process layer
Integration Process layer
consists of the
components of ETL and
Messaging
Encryption Encryption is considered as the most
secure way in order to protect data
from unknown as well as
unauthenticated source. In this
aspect, the data can be modified
through cryptography technique
resulting useless for different users.
Data Storage
layer
Data Storage layer
consists of No/New SQL
databases as well as
Distributed File System
along with RDF stores
Firewall Firewall is considered as one of the
best protection for the particular
Presentation It includes the
components of Web
implied for developing the enhanced
control of the functions in terms of
security.
semi-structured data,
along with structured data
Ranger It is authorization system assisting in
making limitation for the user access
in big data system, defined by the
Ranger policies. The user needs to
request to Ranger to receive the
authenticated entry into specific
system
Analytics as
well as
Computing
Models layer
And
Integration
Process layer
Integration Process layer
consists of the
components of ETL and
Messaging
Encryption Encryption is considered as the most
secure way in order to protect data
from unknown as well as
unauthenticated source. In this
aspect, the data can be modified
through cryptography technique
resulting useless for different users.
Data Storage
layer
Data Storage layer
consists of No/New SQL
databases as well as
Distributed File System
along with RDF stores
Firewall Firewall is considered as one of the
best protection for the particular
Presentation It includes the
components of Web
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
network associated with security
issues.
layer Browser, Mobile Devices
as well as Web Services
Table 1: Security functions for ENISA Big Data framework
(Source: Created by author)
2. Top Threat in the ENISA
The threats associated with ENISA big data strategy of the organization have been
delineated by the accidental threats, technical threats, threats to the organization and distinctive
legitimate treats (Chen & Zhang, 2014). These sorts of threats are exceptionally common in the
enterprise. Accordingly, there are different techniques made to moderate these issues in the
organization. The prevention to the normal management of the organization has been kept up by
the operations in the market. There are different risks as well as threats for the ENISA have been
given in the forbidden organization beneath:
Threat Types Examples of the Risk Classification
Accidental Threats Destruction of records and leaks of data through web
application, loss of storage as well as loss of sensitive
information, inadequate design as well as planning threat
Deliberate Threats Deliberate threats related to network traffic issues and
interception of server as well as information interception
Organization Threat The threats related to organization including shortage of IT
skills
network associated with security
issues.
layer Browser, Mobile Devices
as well as Web Services
Table 1: Security functions for ENISA Big Data framework
(Source: Created by author)
2. Top Threat in the ENISA
The threats associated with ENISA big data strategy of the organization have been
delineated by the accidental threats, technical threats, threats to the organization and distinctive
legitimate treats (Chen & Zhang, 2014). These sorts of threats are exceptionally common in the
enterprise. Accordingly, there are different techniques made to moderate these issues in the
organization. The prevention to the normal management of the organization has been kept up by
the operations in the market. There are different risks as well as threats for the ENISA have been
given in the forbidden organization beneath:
Threat Types Examples of the Risk Classification
Accidental Threats Destruction of records and leaks of data through web
application, loss of storage as well as loss of sensitive
information, inadequate design as well as planning threat
Deliberate Threats Deliberate threats related to network traffic issues and
interception of server as well as information interception
Organization Threat The threats related to organization including shortage of IT
skills

8RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Legal Threats Legal threats are violating regulation and failure to encounter
contractual needs and abuse of personal data as well as judiciary
orders.
Table 2: Threats and Risk of the ENISA Organization
(Source: Created by author)
The risks to the big data analysis in the organization have been a noteworthy risk for the
organization the market. The threats of technology incorporate lack of data and business failure.
Authorization manhandle and vindictive code era in the organization. These thetas can be
likewise ordered by focused assaults, email hacking and data fraud in the organization. Along
these lines, there are a few systems arranged for keeping up the security from these dangers on
the organization (Chen et al., 2014). The risk innovation mishandle has been the most common
threat for the ENISA in the market. The digital world has been experienced this threat
everywhere throughout the world. The data has made much loss for the organization in the
market. The affectability if the information and data has been proactive in the organization that
has made threats the information and data of the organization in the market. The sensitivity of
the database of the organization has been causing the loss of information of the organization.
3. Key Threat Agents and their Impact Reduction Options
The technological mishandle risk in the ENISA has been portrayed by the hole if the data,
social engineering issues, dissent of administration, directed assaults and control of data in the
company. The key dangers of the ENISA are Human mistakes, individual increase and
technology.
Legal Threats Legal threats are violating regulation and failure to encounter
contractual needs and abuse of personal data as well as judiciary
orders.
Table 2: Threats and Risk of the ENISA Organization
(Source: Created by author)
The risks to the big data analysis in the organization have been a noteworthy risk for the
organization the market. The threats of technology incorporate lack of data and business failure.
Authorization manhandle and vindictive code era in the organization. These thetas can be
likewise ordered by focused assaults, email hacking and data fraud in the organization. Along
these lines, there are a few systems arranged for keeping up the security from these dangers on
the organization (Chen et al., 2014). The risk innovation mishandle has been the most common
threat for the ENISA in the market. The digital world has been experienced this threat
everywhere throughout the world. The data has made much loss for the organization in the
market. The affectability if the information and data has been proactive in the organization that
has made threats the information and data of the organization in the market. The sensitivity of
the database of the organization has been causing the loss of information of the organization.
3. Key Threat Agents and their Impact Reduction Options
The technological mishandle risk in the ENISA has been portrayed by the hole if the data,
social engineering issues, dissent of administration, directed assaults and control of data in the
company. The key dangers of the ENISA are Human mistakes, individual increase and
technology.

9RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Technology
The technology is an essential factor in the improvement of the effective operations in the
ENISA. The change in the technological domain of the organization may help in securing the
information and data of the organization in the market (Demchenko et al., 2013). The
technological arrangement of the break of information and data in the association has ready to
keep up the tact of the strategies. The ramifications of the innovative issues in the organization
have given powerful improvement in the effective stream of operations in the organization. The
recognized technological issues in the organization has been legitimately examined for the
finding the methodologies to relieve them.
Human generated errors
The human mistakes are the main considerations as the obstructions in the organization.
The framework coordinated operations have ready to deal with the security threats associated
with the management of the company. The errors that are made by the human cohesiveness are
making issues for the company (Enisa.europa.eu, 2017). There are different human mistakes
including data block attempt, replay if messages, capturing, unapproved information breaks and
control of hardware. The human including the workers and different staffs of the organization
controls these issues.
Designing Errors
The designing errors are portrayed because of the systematic in the enterprise. These
designing mistakes are affirmed by the implications of the operational handling. These errors are
set up for the basic assessment for the advancement of the association. In this way, the business
operations are dependable to the administration of the organization. For instance, threats in
Technology
The technology is an essential factor in the improvement of the effective operations in the
ENISA. The change in the technological domain of the organization may help in securing the
information and data of the organization in the market (Demchenko et al., 2013). The
technological arrangement of the break of information and data in the association has ready to
keep up the tact of the strategies. The ramifications of the innovative issues in the organization
have given powerful improvement in the effective stream of operations in the organization. The
recognized technological issues in the organization has been legitimately examined for the
finding the methodologies to relieve them.
Human generated errors
The human mistakes are the main considerations as the obstructions in the organization.
The framework coordinated operations have ready to deal with the security threats associated
with the management of the company. The errors that are made by the human cohesiveness are
making issues for the company (Enisa.europa.eu, 2017). There are different human mistakes
including data block attempt, replay if messages, capturing, unapproved information breaks and
control of hardware. The human including the workers and different staffs of the organization
controls these issues.
Designing Errors
The designing errors are portrayed because of the systematic in the enterprise. These
designing mistakes are affirmed by the implications of the operational handling. These errors are
set up for the basic assessment for the advancement of the association. In this way, the business
operations are dependable to the administration of the organization. For instance, threats in
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
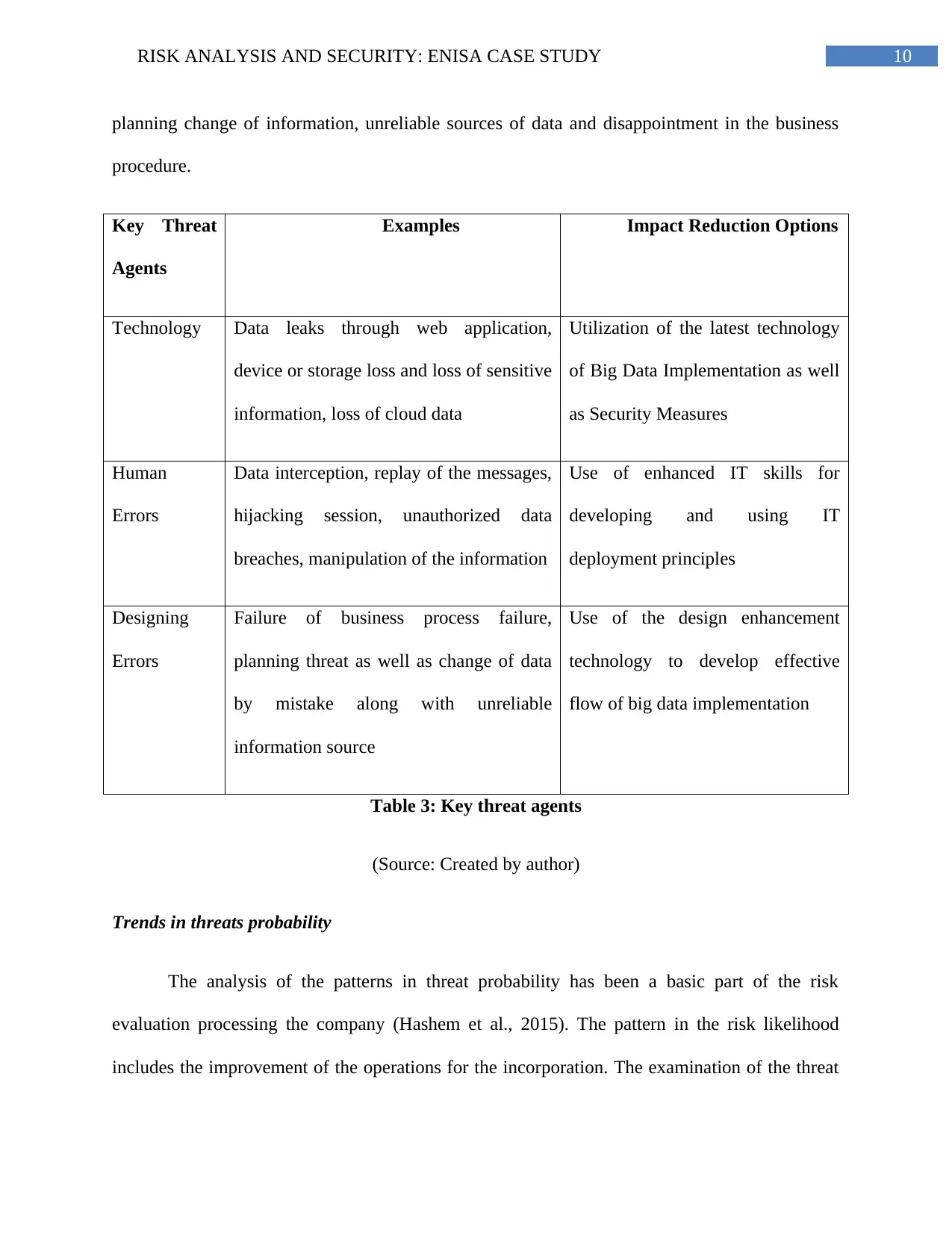
10RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
planning change of information, unreliable sources of data and disappointment in the business
procedure.
Key Threat
Agents
Examples Impact Reduction Options
Technology Data leaks through web application,
device or storage loss and loss of sensitive
information, loss of cloud data
Utilization of the latest technology
of Big Data Implementation as well
as Security Measures
Human
Errors
Data interception, replay of the messages,
hijacking session, unauthorized data
breaches, manipulation of the information
Use of enhanced IT skills for
developing and using IT
deployment principles
Designing
Errors
Failure of business process failure,
planning threat as well as change of data
by mistake along with unreliable
information source
Use of the design enhancement
technology to develop effective
flow of big data implementation
Table 3: Key threat agents
(Source: Created by author)
Trends in threats probability
The analysis of the patterns in threat probability has been a basic part of the risk
evaluation processing the company (Hashem et al., 2015). The pattern in the risk likelihood
includes the improvement of the operations for the incorporation. The examination of the threat
planning change of information, unreliable sources of data and disappointment in the business
procedure.
Key Threat
Agents
Examples Impact Reduction Options
Technology Data leaks through web application,
device or storage loss and loss of sensitive
information, loss of cloud data
Utilization of the latest technology
of Big Data Implementation as well
as Security Measures
Human
Errors
Data interception, replay of the messages,
hijacking session, unauthorized data
breaches, manipulation of the information
Use of enhanced IT skills for
developing and using IT
deployment principles
Designing
Errors
Failure of business process failure,
planning threat as well as change of data
by mistake along with unreliable
information source
Use of the design enhancement
technology to develop effective
flow of big data implementation
Table 3: Key threat agents
(Source: Created by author)
Trends in threats probability
The analysis of the patterns in threat probability has been a basic part of the risk
evaluation processing the company (Hashem et al., 2015). The pattern in the risk likelihood
includes the improvement of the operations for the incorporation. The examination of the threat

11RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
management in the company can be implemented for moderating the dangers engaged with the
risk likelihood.
4. Enhancement of ETL process
ENSIA had confronted numerous execution issues in enhancing the database of the
organization in the market (Kao et al., 2014). The ETL procedure in the organization can be
enhanced in the different procedure that is talked about underneath:
Usage of minimum data
The batch processing has depleted a sensible measure of memory stockpiling by pulling a
lot of information and data for operations in the ENISA. The extraction of least some of the
information and data are important for the advancement of the operation in ENISA.
Avoidance of row-by-row lookup
The procedure of the ETL for the most part utilizes push by-push query methodology for
performing data operations in the organization (Kim et al., 2014). Despite the fact that it is a
period taking procedure contrasted with the mass stacking process. The mass stacking process
the alternative of ETL is useful and process quick and substantial measure of information
volumes in information operations.
5. Justification of IT security in ENISA
The IT security of ENISA is produced for the keeping up the operation of the
organization in the market. The assurance of information and data in the organization has been
fundamental objective if the organization in the current market (Kshetri, 2014). The principle
management in the company can be implemented for moderating the dangers engaged with the
risk likelihood.
4. Enhancement of ETL process
ENSIA had confronted numerous execution issues in enhancing the database of the
organization in the market (Kao et al., 2014). The ETL procedure in the organization can be
enhanced in the different procedure that is talked about underneath:
Usage of minimum data
The batch processing has depleted a sensible measure of memory stockpiling by pulling a
lot of information and data for operations in the ENISA. The extraction of least some of the
information and data are important for the advancement of the operation in ENISA.
Avoidance of row-by-row lookup
The procedure of the ETL for the most part utilizes push by-push query methodology for
performing data operations in the organization (Kim et al., 2014). Despite the fact that it is a
period taking procedure contrasted with the mass stacking process. The mass stacking process
the alternative of ETL is useful and process quick and substantial measure of information
volumes in information operations.
5. Justification of IT security in ENISA
The IT security of ENISA is produced for the keeping up the operation of the
organization in the market. The assurance of information and data in the organization has been
fundamental objective if the organization in the current market (Kshetri, 2014). The principle

12RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
components in the security in ENISA incorporate Ranger, Firewall, KNOX and Encryption.
These components have been legitimately introduced I the security layers of the organization in
the market.
The current structure of the company has been legitimately kept up for securing the
information and data in the organization. The usage of the IPS/IDS has helped in ensuring
system invasion by distinguishing and keeping the entrance to the ENISA database.
Conclusion
It can be presumed that the security of the ENISA has been a slanting case in the market.
The organizational structure has prompted security dangers in the organization. The effect of the
enormous information examination in the organization has helped in keeping up the security of
the information and data of the organization. The mass stacking procedure of the ETL has helped
in giving quick handling speed dodging the column by-push lookup in the methodologies. The
KNOX, Ranger, Firewall, Encryption, and IDS/IPS are useful in ensuring the system invasion by
identifying and keeping the entrance to the database of ENISA
components in the security in ENISA incorporate Ranger, Firewall, KNOX and Encryption.
These components have been legitimately introduced I the security layers of the organization in
the market.
The current structure of the company has been legitimately kept up for securing the
information and data in the organization. The usage of the IPS/IDS has helped in ensuring
system invasion by distinguishing and keeping the entrance to the ENISA database.
Conclusion
It can be presumed that the security of the ENISA has been a slanting case in the market.
The organizational structure has prompted security dangers in the organization. The effect of the
enormous information examination in the organization has helped in keeping up the security of
the information and data of the organization. The mass stacking procedure of the ETL has helped
in giving quick handling speed dodging the column by-push lookup in the methodologies. The
KNOX, Ranger, Firewall, Encryption, and IDS/IPS are useful in ensuring the system invasion by
identifying and keeping the entrance to the database of ENISA
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
References
Baumer, B. S. (2017). A Grammar for Reproducible and Painless Extract-Transform-Load
Operations on Medium Data. arXiv preprint arXiv:1708.07073.
Cardenas, A. A., Manadhata, P. K., & Rajan, S. P. (2013). Big data analytics for security. IEEE
Security & Privacy, 11(6), 74-76.
Chen, C. P., & Zhang, C. Y. (2014). Data-intensive applications, challenges, techniques and
technologies: A survey on Big Data. Information Sciences, 275, 314-347.
Chen, M., Mao, S., & Liu, Y. (2014). Big data: A survey. Mobile Networks and
Applications, 19(2), 171-209.
Demchenko, Y., Grosso, P., De Laat, C., & Membrey, P. (2013, May). Addressing big data
issues in scientific data infrastructure. In Collaboration Technologies and Systems (CTS),
2013 International Conference on (pp. 48-55). IEEE.
Enisa.europa.eu. (2017). Big Data Threat Landscape — ENISA. [online] Available at:
https://www.enisa.europa.eu/publications/bigdata-threat-landscape [Accessed 5 Sep.
2017].
Hashem, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Khan, S. U. (2015). The
rise of “big data” on cloud computing: Review and open research issues. Information
Systems, 47, 98-115.
References
Baumer, B. S. (2017). A Grammar for Reproducible and Painless Extract-Transform-Load
Operations on Medium Data. arXiv preprint arXiv:1708.07073.
Cardenas, A. A., Manadhata, P. K., & Rajan, S. P. (2013). Big data analytics for security. IEEE
Security & Privacy, 11(6), 74-76.
Chen, C. P., & Zhang, C. Y. (2014). Data-intensive applications, challenges, techniques and
technologies: A survey on Big Data. Information Sciences, 275, 314-347.
Chen, M., Mao, S., & Liu, Y. (2014). Big data: A survey. Mobile Networks and
Applications, 19(2), 171-209.
Demchenko, Y., Grosso, P., De Laat, C., & Membrey, P. (2013, May). Addressing big data
issues in scientific data infrastructure. In Collaboration Technologies and Systems (CTS),
2013 International Conference on (pp. 48-55). IEEE.
Enisa.europa.eu. (2017). Big Data Threat Landscape — ENISA. [online] Available at:
https://www.enisa.europa.eu/publications/bigdata-threat-landscape [Accessed 5 Sep.
2017].
Hashem, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Khan, S. U. (2015). The
rise of “big data” on cloud computing: Review and open research issues. Information
Systems, 47, 98-115.

14RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Kao, R. R., Haydon, D. T., Lycett, S. J., & Murcia, P. R. (2014). Supersize me: how whole-
genome sequencing and big data are transforming epidemiology. Trends in
microbiology, 22(5), 282-291.
Kim, G. H., Trimi, S., & Chung, J. H. (2014). Big-data applications in the government
sector. Communications of the ACM, 57(3), 78-85.
Kshetri, N. (2014). Big data׳ s impact on privacy, security and consumer
welfare. Telecommunications Policy, 38(11), 1134-1145.
Patil, H. K., &Seshadri, R. (2014, June). Big data security and privacy issues in healthcare.
In Big Data (BigData Congress), 2014 IEEE International Congress on (pp. 762-765).
IEEE.
Sagiroglu, S., &Sinanc, D. (2013, May). Big data: A review. In Collaboration Technologies and
Systems (CTS), 2013 International Conference on (pp. 42-47). IEEE.
Thuraisingham, B. (2015, March). Big data security and privacy. In Proceedings of the 5th ACM
Conference on Data and Application Security and Privacy (pp. 279-280). ACM.
Vatsalan, D., Sehili, Z., Christen, P., & Rahm, E. (2017). Privacy-Preserving Record Linkage for
Big Data: Current Approaches and Research Challenges. In Handbook of Big Data
Technologies (pp. 851-895). Springer International Publishing.
Wu, X., Zhu, X., Wu, G. Q., & Ding, W. (2014). Data mining with big data. IEEE transactions
on knowledge and data engineering, 26(1), 97-107.
Kao, R. R., Haydon, D. T., Lycett, S. J., & Murcia, P. R. (2014). Supersize me: how whole-
genome sequencing and big data are transforming epidemiology. Trends in
microbiology, 22(5), 282-291.
Kim, G. H., Trimi, S., & Chung, J. H. (2014). Big-data applications in the government
sector. Communications of the ACM, 57(3), 78-85.
Kshetri, N. (2014). Big data׳ s impact on privacy, security and consumer
welfare. Telecommunications Policy, 38(11), 1134-1145.
Patil, H. K., &Seshadri, R. (2014, June). Big data security and privacy issues in healthcare.
In Big Data (BigData Congress), 2014 IEEE International Congress on (pp. 762-765).
IEEE.
Sagiroglu, S., &Sinanc, D. (2013, May). Big data: A review. In Collaboration Technologies and
Systems (CTS), 2013 International Conference on (pp. 42-47). IEEE.
Thuraisingham, B. (2015, March). Big data security and privacy. In Proceedings of the 5th ACM
Conference on Data and Application Security and Privacy (pp. 279-280). ACM.
Vatsalan, D., Sehili, Z., Christen, P., & Rahm, E. (2017). Privacy-Preserving Record Linkage for
Big Data: Current Approaches and Research Challenges. In Handbook of Big Data
Technologies (pp. 851-895). Springer International Publishing.
Wu, X., Zhu, X., Wu, G. Q., & Ding, W. (2014). Data mining with big data. IEEE transactions
on knowledge and data engineering, 26(1), 97-107.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





