Analyzing Risks in Business Systems: A Comprehensive Control Report
VerifiedAdded on 2023/06/17
|8
|1727
|497
Report
AI Summary
This report provides a risk analysis of a business system, focusing on identifying and mitigating potential risks. It emphasizes the importance of policies and procedures in guiding employees and ensuring compliance. The report outlines different types of information security policies, including technical, organizational, system-specific, and issue-specific policies. It also details the purpose and process of risk assessment and risk management planning, covering risk identification, analysis, prioritization, treatment, and monitoring. The report includes an asset priority table and a TVA (Threat, Vulnerability, Asset) table to assess potential threats and vulnerabilities. Suggested controls are provided to mitigate risks related to technology, political factors, and software attacks. The conclusion highlights the significance of policies and risk assessment in maintaining the confidentiality and integrity of information systems.

Perform a risk analysis on a small part
of a business system and provide a list
of possible controls
of a business system and provide a list
of possible controls
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
Importance of policies.................................................................................................................3
Policy documents........................................................................................................................3
Types of policies required for information security....................................................................4
Purpose and advantage of risk assessment plan..........................................................................4
Process of risk assessment..........................................................................................................4
Process for making risk management plan..................................................................................5
Asset priority table......................................................................................................................5
CONCLUSION................................................................................................................................6
REFERENCES................................................................................................................................8
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
Importance of policies.................................................................................................................3
Policy documents........................................................................................................................3
Types of policies required for information security....................................................................4
Purpose and advantage of risk assessment plan..........................................................................4
Process of risk assessment..........................................................................................................4
Process for making risk management plan..................................................................................5
Asset priority table......................................................................................................................5
CONCLUSION................................................................................................................................6
REFERENCES................................................................................................................................8

INTRODUCTION
Risk analysis is related to the study of uncertainty about some action within the
organisation. It helps in identifying, measuring and mitigating different risks that are faced by the
business of an organisation. It is important to assess the risks that are important to determine the
worth of a project and the risks associated with it. Denisovan medical supplies is a firm
producing chemical products that are important in the making pharmacological medicines. The
company uses different techniques for producing such products. This report deals with the risk
analysis of the assets for this firm and the importance of policies and risk assessments in the
process.
MAIN BODY
Importance of policies
Policies and procedures are an important part in an organisation and helps in guiding the
employees of the company to perform their day to day operations. Policies helps in ensuring the
level of compliance with regards to the laws and regulations. It helps in the decision- making
process and streamlining it with the internal processes (Connolly, Lang, and Tygar, 2018).
Policies are important in providing consistency, accountability and enabling clarity in the ways
by which the Denisovan medical supplies operates. The employees and workers of the company
will have co- operative guidelines and principles that are supposed to be followed. It will provide
direction regarding the functions that are appropriate and the ones that are inappropriate.
Policy documents
Policy document of an organisation must include header that incudes the name of the
organisation and name of individuals for which this policy is created. It must have a date of when
the policy is proposed and from when it is made operative within the company. It must be written
in simple words that are easily understandable by the readers (Landoll, 2017). A policy
document must be consistent with the terminologies. It should include the purpose of the policy
and the scope for the same. The title of a policy document must reflect the overall content of the
policy.
Risk analysis is related to the study of uncertainty about some action within the
organisation. It helps in identifying, measuring and mitigating different risks that are faced by the
business of an organisation. It is important to assess the risks that are important to determine the
worth of a project and the risks associated with it. Denisovan medical supplies is a firm
producing chemical products that are important in the making pharmacological medicines. The
company uses different techniques for producing such products. This report deals with the risk
analysis of the assets for this firm and the importance of policies and risk assessments in the
process.
MAIN BODY
Importance of policies
Policies and procedures are an important part in an organisation and helps in guiding the
employees of the company to perform their day to day operations. Policies helps in ensuring the
level of compliance with regards to the laws and regulations. It helps in the decision- making
process and streamlining it with the internal processes (Connolly, Lang, and Tygar, 2018).
Policies are important in providing consistency, accountability and enabling clarity in the ways
by which the Denisovan medical supplies operates. The employees and workers of the company
will have co- operative guidelines and principles that are supposed to be followed. It will provide
direction regarding the functions that are appropriate and the ones that are inappropriate.
Policy documents
Policy document of an organisation must include header that incudes the name of the
organisation and name of individuals for which this policy is created. It must have a date of when
the policy is proposed and from when it is made operative within the company. It must be written
in simple words that are easily understandable by the readers (Landoll, 2017). A policy
document must be consistent with the terminologies. It should include the purpose of the policy
and the scope for the same. The title of a policy document must reflect the overall content of the
policy.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Types of policies required for information security
Information security policies are documents that are outlines on the security issues. These are
supported by the senior members of the management of the company in the intention of
providing security throughout the operations of Denisovan medical supplies. There are different
policies required for the purpose of information security (Tagarev, and Polimirova, 2019).
Technical security policies are made with the purpose to describe the configuration of the
technology to make it convenient for use. Organisational security policy helps in providing
commitment to information security and is a primary source of document from which security
policies are derived. The system- specific security policies are related to customer applications
and fulfils the security objectives and rules intended to support the same. Lastly, there are issue
specific policies that provide the guidelines for the threats. It addresses low- level issues.
Purpose and advantage of risk assessment plan
The main purpose of making risk assessment plan is to identify the issues before they
take place so that risk handling activities can be made in order to imitate the risk. This plan helps
the company in facing risks effectively which can occur in the future. With the help of risk
assessment, workplace hazards can be recognised and also controlled. Company can also set risk
standards and bring safe practices at workplace (Chemweno and et.al., 2018). It is helpful in
decreasing workplace accidents. When risks are already ascertained then company can take
actions through which the impact of risk can be reduced.
Process of risk assessment
Risk assessment process helps company in identifying risky situations which can harm
employees. It is also used to check that how frequently each risk can occur and how severe it
going to impact the company. It also describes or give the steps which company will use to
control the risk. Workplace hazards can be anything can can cause harm to the employees which
are toxic chemicals, stress, incidents or accidents, emergency situations etc. after identifying the
hazards company should identify that who will be harmed by the hazard (Lin, 2018). Then
likelihood of the hazards are checked. This will tell that how constantly it will occur and what
consequences it will bring. If risk will gets evaluated then precautions will be taken to reduce the
level of risk. nowadays it has become mandatory to write risk assessment process. Denisovan
medical supplies should also ascertain risk assessment process so that can save their employees
for hazardous risk. As this organisation deals with chemical products so for them it is essential to
Information security policies are documents that are outlines on the security issues. These are
supported by the senior members of the management of the company in the intention of
providing security throughout the operations of Denisovan medical supplies. There are different
policies required for the purpose of information security (Tagarev, and Polimirova, 2019).
Technical security policies are made with the purpose to describe the configuration of the
technology to make it convenient for use. Organisational security policy helps in providing
commitment to information security and is a primary source of document from which security
policies are derived. The system- specific security policies are related to customer applications
and fulfils the security objectives and rules intended to support the same. Lastly, there are issue
specific policies that provide the guidelines for the threats. It addresses low- level issues.
Purpose and advantage of risk assessment plan
The main purpose of making risk assessment plan is to identify the issues before they
take place so that risk handling activities can be made in order to imitate the risk. This plan helps
the company in facing risks effectively which can occur in the future. With the help of risk
assessment, workplace hazards can be recognised and also controlled. Company can also set risk
standards and bring safe practices at workplace (Chemweno and et.al., 2018). It is helpful in
decreasing workplace accidents. When risks are already ascertained then company can take
actions through which the impact of risk can be reduced.
Process of risk assessment
Risk assessment process helps company in identifying risky situations which can harm
employees. It is also used to check that how frequently each risk can occur and how severe it
going to impact the company. It also describes or give the steps which company will use to
control the risk. Workplace hazards can be anything can can cause harm to the employees which
are toxic chemicals, stress, incidents or accidents, emergency situations etc. after identifying the
hazards company should identify that who will be harmed by the hazard (Lin, 2018). Then
likelihood of the hazards are checked. This will tell that how constantly it will occur and what
consequences it will bring. If risk will gets evaluated then precautions will be taken to reduce the
level of risk. nowadays it has become mandatory to write risk assessment process. Denisovan
medical supplies should also ascertain risk assessment process so that can save their employees
for hazardous risk. As this organisation deals with chemical products so for them it is essential to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

be designed. Risks in the company changes with time so it is important to update risk assessment
process if necessary.
Process for making risk management plan
Risk identification:
It is initial and most important step in risk management plan. At this process management of the
company identify the risk which can take place in the company. Denisovan medical supplies is
facing major risk related to information and communication security services.
Analyse risk:
Once the risk is identified then it is very important to analyse the risk. It will tell that how
frequently risk will occur. Under this step risks are evaluated which can financial loss, time lost
etc.
Prioritizing risk:
Now company can give priority to the risk. Those risks should be given high priority which will
have more chances of occurrence and those risks should be given low priority which have
probability of less occurrence.
Treating risk:
After company have identified the risk then they should have made treatment plan for that. At
this stage the risks which are of higher priority should be treated by the company. Solution
should be found out for such risks at least mitigate them (Ilbahar and et.al., 2018). So that it is no
longer occur as threat to the company.
Monitoring risk:
In order to monitor threats it is important to have effective communication with employees. It s
the final and important step because t will tell that risks are mitigated or not.
Asset priority table
Asset Impact Priority score
Employees They are important to the company
but are not urgent.
2
Research and development It is of high importance and urgent 4
Computers Low importance and urgent 2
process if necessary.
Process for making risk management plan
Risk identification:
It is initial and most important step in risk management plan. At this process management of the
company identify the risk which can take place in the company. Denisovan medical supplies is
facing major risk related to information and communication security services.
Analyse risk:
Once the risk is identified then it is very important to analyse the risk. It will tell that how
frequently risk will occur. Under this step risks are evaluated which can financial loss, time lost
etc.
Prioritizing risk:
Now company can give priority to the risk. Those risks should be given high priority which will
have more chances of occurrence and those risks should be given low priority which have
probability of less occurrence.
Treating risk:
After company have identified the risk then they should have made treatment plan for that. At
this stage the risks which are of higher priority should be treated by the company. Solution
should be found out for such risks at least mitigate them (Ilbahar and et.al., 2018). So that it is no
longer occur as threat to the company.
Monitoring risk:
In order to monitor threats it is important to have effective communication with employees. It s
the final and important step because t will tell that risks are mitigated or not.
Asset priority table
Asset Impact Priority score
Employees They are important to the company
but are not urgent.
2
Research and development It is of high importance and urgent 4
Computers Low importance and urgent 2
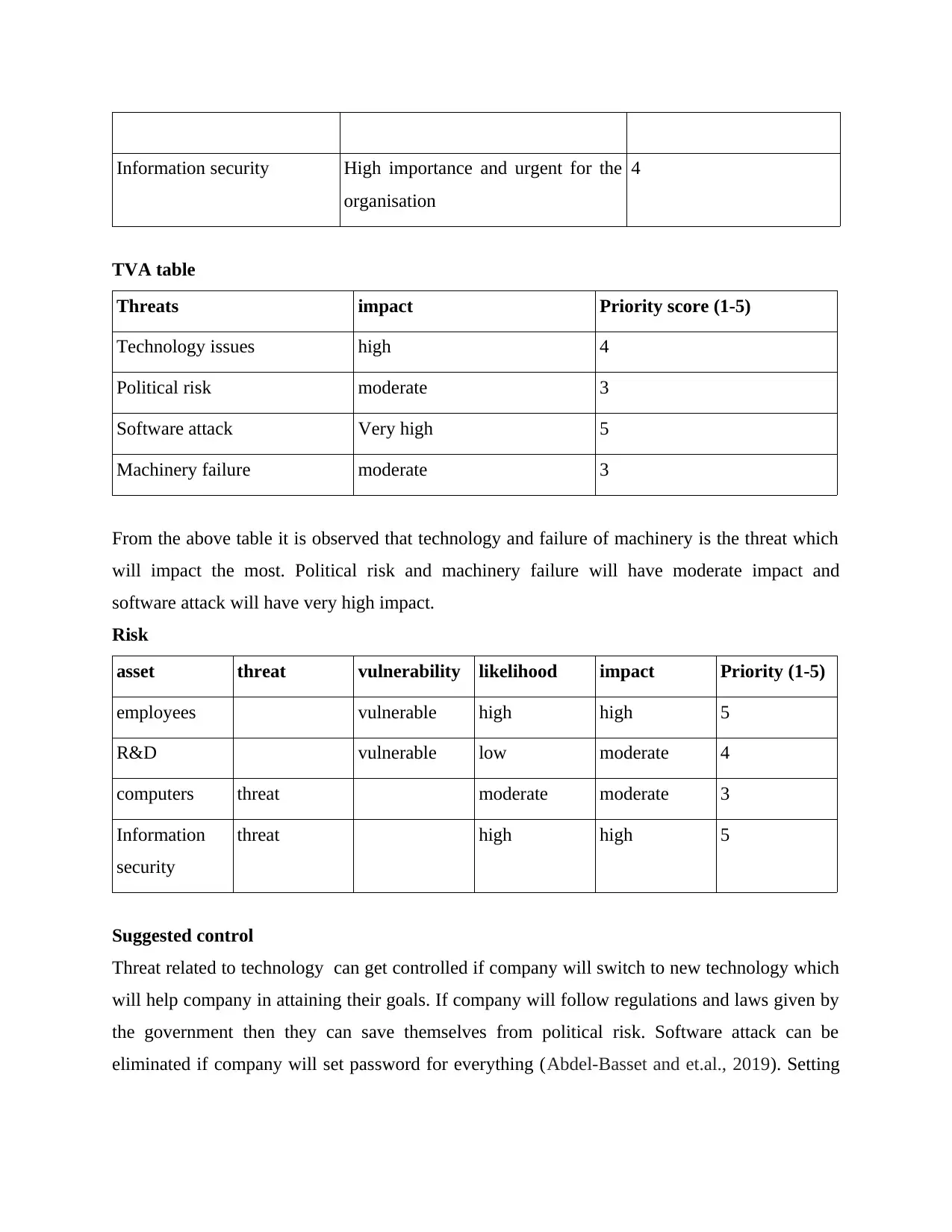
Information security High importance and urgent for the
organisation
4
TVA table
Threats impact Priority score (1-5)
Technology issues high 4
Political risk moderate 3
Software attack Very high 5
Machinery failure moderate 3
From the above table it is observed that technology and failure of machinery is the threat which
will impact the most. Political risk and machinery failure will have moderate impact and
software attack will have very high impact.
Risk
asset threat vulnerability likelihood impact Priority (1-5)
employees vulnerable high high 5
R&D vulnerable low moderate 4
computers threat moderate moderate 3
Information
security
threat high high 5
Suggested control
Threat related to technology can get controlled if company will switch to new technology which
will help company in attaining their goals. If company will follow regulations and laws given by
the government then they can save themselves from political risk. Software attack can be
eliminated if company will set password for everything (Abdel-Basset and et.al., 2019). Setting
organisation
4
TVA table
Threats impact Priority score (1-5)
Technology issues high 4
Political risk moderate 3
Software attack Very high 5
Machinery failure moderate 3
From the above table it is observed that technology and failure of machinery is the threat which
will impact the most. Political risk and machinery failure will have moderate impact and
software attack will have very high impact.
Risk
asset threat vulnerability likelihood impact Priority (1-5)
employees vulnerable high high 5
R&D vulnerable low moderate 4
computers threat moderate moderate 3
Information
security
threat high high 5
Suggested control
Threat related to technology can get controlled if company will switch to new technology which
will help company in attaining their goals. If company will follow regulations and laws given by
the government then they can save themselves from political risk. Software attack can be
eliminated if company will set password for everything (Abdel-Basset and et.al., 2019). Setting
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

password will help company in safeguarding themselves from cyber attack. If machines and
equipment will get checked on regular basis then company can reduce such threat.
CONCLUSION
It can be concluded that policies are an important aspect within an organisation to guide
its employees. There are different types of policies related to the information security that helps
in providing confidentiality, integrity of information systems that are used by the employees of
the organisation. Risk assessment is an essential plan for the organisation to mention the risks
associated with the business operations and actions.
equipment will get checked on regular basis then company can reduce such threat.
CONCLUSION
It can be concluded that policies are an important aspect within an organisation to guide
its employees. There are different types of policies related to the information security that helps
in providing confidentiality, integrity of information systems that are used by the employees of
the organisation. Risk assessment is an essential plan for the organisation to mention the risks
associated with the business operations and actions.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Abdel-Basset, M. and et.al., 2019. A framework for risk assessment, management and
evaluation: Economic tool for quantifying risks in supply chain. Future Generation
Computer Systems, 90(1), pp.489-502.
Books and Journals
Chemweno, P. and et.al., 2018. Risk assessment methodologies in maintenance decision making:
A review of dependability modelling approaches. Reliability Engineering & System
Safety. 173. pp.64-77.
Connolly, L.Y., Lang, M. and Tygar, D.J., 2018. Employee security behaviour: the importance of
education and policies in organisational settings. In Advances in Information Systems
Development (pp. 79-96). Springer, Cham.
Ilbahar, E. and et.al., 2018. A novel approach to risk assessment for occupational health and
safety using Pythagorean fuzzy AHP & fuzzy inference system. Safety science. 103.
pp.124-136.
Landoll, D.J., 2017. Information Security Policies, Procedures, and Standards: A Practitioner's
Reference. CRC Press.
Lin, L., 2018. Integrating a national risk assessment into a disaster risk management system:
Process and practice. International journal of disaster risk reduction, 27, pp.625-631.
Tagarev, T. and Polimirova, D., 2019, June. Main Considerations in Elaborating Organizational
Information Security Policies. In Proceedings of the 20th International Conference on
Computer Systems and Technologies (pp. 68-73).
Abdel-Basset, M. and et.al., 2019. A framework for risk assessment, management and
evaluation: Economic tool for quantifying risks in supply chain. Future Generation
Computer Systems, 90(1), pp.489-502.
Books and Journals
Chemweno, P. and et.al., 2018. Risk assessment methodologies in maintenance decision making:
A review of dependability modelling approaches. Reliability Engineering & System
Safety. 173. pp.64-77.
Connolly, L.Y., Lang, M. and Tygar, D.J., 2018. Employee security behaviour: the importance of
education and policies in organisational settings. In Advances in Information Systems
Development (pp. 79-96). Springer, Cham.
Ilbahar, E. and et.al., 2018. A novel approach to risk assessment for occupational health and
safety using Pythagorean fuzzy AHP & fuzzy inference system. Safety science. 103.
pp.124-136.
Landoll, D.J., 2017. Information Security Policies, Procedures, and Standards: A Practitioner's
Reference. CRC Press.
Lin, L., 2018. Integrating a national risk assessment into a disaster risk management system:
Process and practice. International journal of disaster risk reduction, 27, pp.625-631.
Tagarev, T. and Polimirova, D., 2019, June. Main Considerations in Elaborating Organizational
Information Security Policies. In Proceedings of the 20th International Conference on
Computer Systems and Technologies (pp. 68-73).
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





