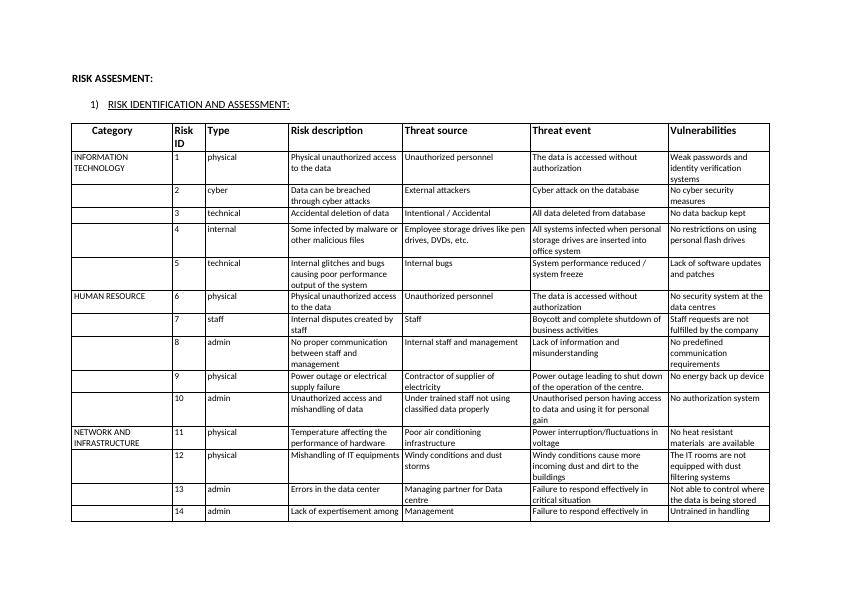
Risk Assessment for Information Technology, Human Resource, and Network Infrastructure
To critically evaluate the need for information security in organisations; To gain an understanding of the concepts of due care, due diligence, and vicarious liability in the context of Information Security and IS/IT Risk Management; To be able to evaluate the control requirements and/or needs for a business environment; To gain an understanding of the complementary nature of various types of controls in mitigating risks; and To gain an appreciation of the importance of an Enterprise Wide Risk Management.
Added on 2023-03-20
About This Document
Risk Assessment for Information Technology, Human Resource, and Network Infrastructure
To critically evaluate the need for information security in organisations; To gain an understanding of the concepts of due care, due diligence, and vicarious liability in the context of Information Security and IS/IT Risk Management; To be able to evaluate the control requirements and/or needs for a business environment; To gain an understanding of the complementary nature of various types of controls in mitigating risks; and To gain an appreciation of the importance of an Enterprise Wide Risk Management.
Added on 2023-03-20
End of preview
Want to access all the pages? Upload your documents or become a member.