Cloud Security Risk Assessment Report for Gigantic Corporation's IT
VerifiedAdded on 2023/06/04
|11
|4088
|214
Report
AI Summary
This report provides a detailed risk assessment of implementing a cloud security platform and intrusion detection system (IDS) within Gigantic Corporation, an IT company based in Australia. It outlines the role of the IT Risk Assessment lead consultant in identifying and mitigating security risks, particularly focusing on cloud security. The report discusses the architecture of IDS, strategic planning, and financial aspects of the project. It identifies potential threat agents, vulnerabilities, and consequences, recommending industry best practices for mitigating risks and system impacts. The report also includes a literature review on information security protection mechanisms and concludes with recommendations for enhancing the security posture of Gigantic Corporation. Desklib provides access to this and many other solved assignments for students.

Running head: RISK ASSESSMENT BASED ON CLOUD SECURITY
Risk Assessment based on Cloud Security
Name of the Student
Name of the University
Author’s note
Risk Assessment based on Cloud Security
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK ASSESSMENT BASED ON CLOUD SECURITY
Table of Contents
1. Executive Summary.....................................................................................................................2
1.1 Statement of the Intrusion Detection System within Gigantic Corporation..........................2
1.1.1 Outline of the Company..................................................................................................2
1.1.2 Outline of Role and Responsibility of the Lead Consultant of IT Risk Assessment......2
1.1.3 Outline of the New Technology used for Assessment....................................................3
1.2 Overview of Recommendations............................................................................................3
1.2.1 Security Architecture of Intrusion Detection Systems...................................................3
1.2.2 Strategic, Tactical and Contingency Planning................................................................4
1.2.3 Financial Aspects of the Concerned Project...................................................................4
2. Risk Assessment based on Threats, Vulnerabilities and Consequences......................................5
2.1 Existing IT Control Framework and Recommendations based on Industry Risk.................5
2.1.1 Policy and Procedures.....................................................................................................5
2.1.2 Best Recommended Practice..........................................................................................5
2.1.3 Current Evidences...........................................................................................................5
2.2 Identification and Discussion of the Key Agents of Threats.................................................6
2.2.1 List of Threat Agents......................................................................................................6
2.2.2 Issues...............................................................................................................................6
2.2.3 Consequences.................................................................................................................6
2.3 Mitigation of Risks and System Impacts...............................................................................7
2.3.1 Impact.............................................................................................................................7
2.3.2 Mitigation.......................................................................................................................7
3. Literature Review........................................................................................................................8
3.1 Protection Mechanisms for Employing Information Security...............................................8
3.1.1 Safe Guards.....................................................................................................................8
3.1.2 Security Mechanisms......................................................................................................8
3.1.3 Key Principle of Information Security...........................................................................8
4. Conclusion...................................................................................................................................8
5. References....................................................................................................................................9
Table of Contents
1. Executive Summary.....................................................................................................................2
1.1 Statement of the Intrusion Detection System within Gigantic Corporation..........................2
1.1.1 Outline of the Company..................................................................................................2
1.1.2 Outline of Role and Responsibility of the Lead Consultant of IT Risk Assessment......2
1.1.3 Outline of the New Technology used for Assessment....................................................3
1.2 Overview of Recommendations............................................................................................3
1.2.1 Security Architecture of Intrusion Detection Systems...................................................3
1.2.2 Strategic, Tactical and Contingency Planning................................................................4
1.2.3 Financial Aspects of the Concerned Project...................................................................4
2. Risk Assessment based on Threats, Vulnerabilities and Consequences......................................5
2.1 Existing IT Control Framework and Recommendations based on Industry Risk.................5
2.1.1 Policy and Procedures.....................................................................................................5
2.1.2 Best Recommended Practice..........................................................................................5
2.1.3 Current Evidences...........................................................................................................5
2.2 Identification and Discussion of the Key Agents of Threats.................................................6
2.2.1 List of Threat Agents......................................................................................................6
2.2.2 Issues...............................................................................................................................6
2.2.3 Consequences.................................................................................................................6
2.3 Mitigation of Risks and System Impacts...............................................................................7
2.3.1 Impact.............................................................................................................................7
2.3.2 Mitigation.......................................................................................................................7
3. Literature Review........................................................................................................................8
3.1 Protection Mechanisms for Employing Information Security...............................................8
3.1.1 Safe Guards.....................................................................................................................8
3.1.2 Security Mechanisms......................................................................................................8
3.1.3 Key Principle of Information Security...........................................................................8
4. Conclusion...................................................................................................................................8
5. References....................................................................................................................................9

2RISK ASSESSMENT BASED ON CLOUD SECURITY
1. Executive Summary
The report focuses on the impact of cloud security platforms based on resolving of the
kinds of affecting areas of risks within the IT organizations. The report is based on the
assessment of various kinds of risks that might be affecting Gigantic Corporation based on the
implementation of cloud security platform. This report focuses on the designing of a project
based on the implementation of the Intrusion Detection System within Gigantic Corporation
based on cloud security. This kind of system would be purely based on the ideas of cloud
computing (Liao et al., 2013). This project would thus help to build an interface between the
technologists and stakeholders. This would help in translating the potential difficulties into
effective form of decision making process by the stakeholders within the project. This report
helps in the assessment of the intrusion detection system that would be implemented within
Gigantic Corporation after a complete assessment based on cloud security aspects would be
considered.
1.1 Statement of the Intrusion Detection System within Gigantic Corporation
1.1.1 Outline of the Company
Gigantic Corporation is an IT based company, which is primarily based in Australia. The
company helps in providing various forms of IT based solutions to other companies. They help
in providing software and hardware solutions. The organisation is also responsible for
establishing business relations, monitor control and thus maintain services and solutions related
to information technology systems (Snapp et al., 2017).
As a major provider of IT based services, Gigantic Corporation plays a major role in
driving the growth of business of the organisation. They are responsible for designing several
kinds of IT based solutions, maintain the form of services that are provided for the business
clients and thus support other organizations based on their network infrastructure. The
organisation also makes use of cloud environment for bringing in efficiency within the processes
of work within the organisation.
1.1.2 Outline of Role and Responsibility of the Lead Consultant of IT Risk Assessment
As the Lead Consultant of IT Risk Assessment within Gigantic Corporation, the main
role of this position is to provide a complete assessment of the various kinds of risks within the
organisation. The main role of the lead consultant would be to conduct an assessment based on
the upcoming risks within the security of the organisation. Gigantic Corporation is facing some
form of challenges based on security aspects of the organisation. Hence the organisation has
hired the lead consultant of IT Risk Assessment to implement a project based on Intrusion
Detection System. This technological system
The main responsibilities of the Lead Consultant are:
Working with senior executives in order to understand the challenges of business,
identification of risk scenarios and thus the performance of the business with the
operational risks within the organization.
Communicate and perform high level of coordination with various stakeholders, technical
experts that would also include the ecosystem of the client business.
1. Executive Summary
The report focuses on the impact of cloud security platforms based on resolving of the
kinds of affecting areas of risks within the IT organizations. The report is based on the
assessment of various kinds of risks that might be affecting Gigantic Corporation based on the
implementation of cloud security platform. This report focuses on the designing of a project
based on the implementation of the Intrusion Detection System within Gigantic Corporation
based on cloud security. This kind of system would be purely based on the ideas of cloud
computing (Liao et al., 2013). This project would thus help to build an interface between the
technologists and stakeholders. This would help in translating the potential difficulties into
effective form of decision making process by the stakeholders within the project. This report
helps in the assessment of the intrusion detection system that would be implemented within
Gigantic Corporation after a complete assessment based on cloud security aspects would be
considered.
1.1 Statement of the Intrusion Detection System within Gigantic Corporation
1.1.1 Outline of the Company
Gigantic Corporation is an IT based company, which is primarily based in Australia. The
company helps in providing various forms of IT based solutions to other companies. They help
in providing software and hardware solutions. The organisation is also responsible for
establishing business relations, monitor control and thus maintain services and solutions related
to information technology systems (Snapp et al., 2017).
As a major provider of IT based services, Gigantic Corporation plays a major role in
driving the growth of business of the organisation. They are responsible for designing several
kinds of IT based solutions, maintain the form of services that are provided for the business
clients and thus support other organizations based on their network infrastructure. The
organisation also makes use of cloud environment for bringing in efficiency within the processes
of work within the organisation.
1.1.2 Outline of Role and Responsibility of the Lead Consultant of IT Risk Assessment
As the Lead Consultant of IT Risk Assessment within Gigantic Corporation, the main
role of this position is to provide a complete assessment of the various kinds of risks within the
organisation. The main role of the lead consultant would be to conduct an assessment based on
the upcoming risks within the security of the organisation. Gigantic Corporation is facing some
form of challenges based on security aspects of the organisation. Hence the organisation has
hired the lead consultant of IT Risk Assessment to implement a project based on Intrusion
Detection System. This technological system
The main responsibilities of the Lead Consultant are:
Working with senior executives in order to understand the challenges of business,
identification of risk scenarios and thus the performance of the business with the
operational risks within the organization.
Communicate and perform high level of coordination with various stakeholders, technical
experts that would also include the ecosystem of the client business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RISK ASSESSMENT BASED ON CLOUD SECURITY
Identification of the risks and issues that could impact the project and thus maximize the
success of the project (Peltier, 2016).
Building and implementation of solutions for the client that would fit the culture of the
business environment and would thus improve the business performance of the client.
1.1.3 Outline of the New Technology used for Assessment
The technological system that would be implemented within the IT systems of Gigantic
Corporation is Intrusion Detection System (IDS) with the use of cloud security. The advanced
technologies that includes IDS and various forms of analysis tools have become noticeable in the
network environment. IDS technology would be helpful for implementation within Gigantic
Corporation for enhancing the security within the IT systems and protecting the assets of the
organization. The IDS would be purely based on cloud platform and would also be able to
protect and secure the cloud platform of the organization (Patel et al., 2013).
In the recent times, it has been observed that there are various forms of upcoming attacks
based on the IT systems, which are meant for gaining access on the data of the organization. The
proper form of detection and thus responding to the attacks is a vital concern for the
organizations. The use of IDS systems could be defined as effective solutions within the
organisation for resisting the different kinds of attacks. These systems are able to provide
additional methods of protection based within the cloud based systems of the organisation. IDS
systems can help in identifying different forms of suspicious activities as they keep a track over
the activities within the network architecture of the organisation. These forms of IDS systems
would be able to send an alert message to the higher management of the organisation (Modi et
al., 2013).
The assessment of the report is aimed at providing definitions and discussing about the
properties about the vast form of attacks within the cloud computing environment of the
organisation. The report also focuses on the introduction of the detection of intrusions within the
systems and some models of prevention against those attacks.
1.2 Overview of Recommendations
1.2.1 Security Architecture of Intrusion Detection Systems
The architecture for the IDS systems is based on different system structures that would
comprise of software components, the external based visible properties of the components and
the different relationship among them. The external visible properties includes the different
properties such as characteristics of performance, fault handling mechanisms and usage of shared
resource (Alrajeh, Khan & Shams, 2013).
Identification of the risks and issues that could impact the project and thus maximize the
success of the project (Peltier, 2016).
Building and implementation of solutions for the client that would fit the culture of the
business environment and would thus improve the business performance of the client.
1.1.3 Outline of the New Technology used for Assessment
The technological system that would be implemented within the IT systems of Gigantic
Corporation is Intrusion Detection System (IDS) with the use of cloud security. The advanced
technologies that includes IDS and various forms of analysis tools have become noticeable in the
network environment. IDS technology would be helpful for implementation within Gigantic
Corporation for enhancing the security within the IT systems and protecting the assets of the
organization. The IDS would be purely based on cloud platform and would also be able to
protect and secure the cloud platform of the organization (Patel et al., 2013).
In the recent times, it has been observed that there are various forms of upcoming attacks
based on the IT systems, which are meant for gaining access on the data of the organization. The
proper form of detection and thus responding to the attacks is a vital concern for the
organizations. The use of IDS systems could be defined as effective solutions within the
organisation for resisting the different kinds of attacks. These systems are able to provide
additional methods of protection based within the cloud based systems of the organisation. IDS
systems can help in identifying different forms of suspicious activities as they keep a track over
the activities within the network architecture of the organisation. These forms of IDS systems
would be able to send an alert message to the higher management of the organisation (Modi et
al., 2013).
The assessment of the report is aimed at providing definitions and discussing about the
properties about the vast form of attacks within the cloud computing environment of the
organisation. The report also focuses on the introduction of the detection of intrusions within the
systems and some models of prevention against those attacks.
1.2 Overview of Recommendations
1.2.1 Security Architecture of Intrusion Detection Systems
The architecture for the IDS systems is based on different system structures that would
comprise of software components, the external based visible properties of the components and
the different relationship among them. The external visible properties includes the different
properties such as characteristics of performance, fault handling mechanisms and usage of shared
resource (Alrajeh, Khan & Shams, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
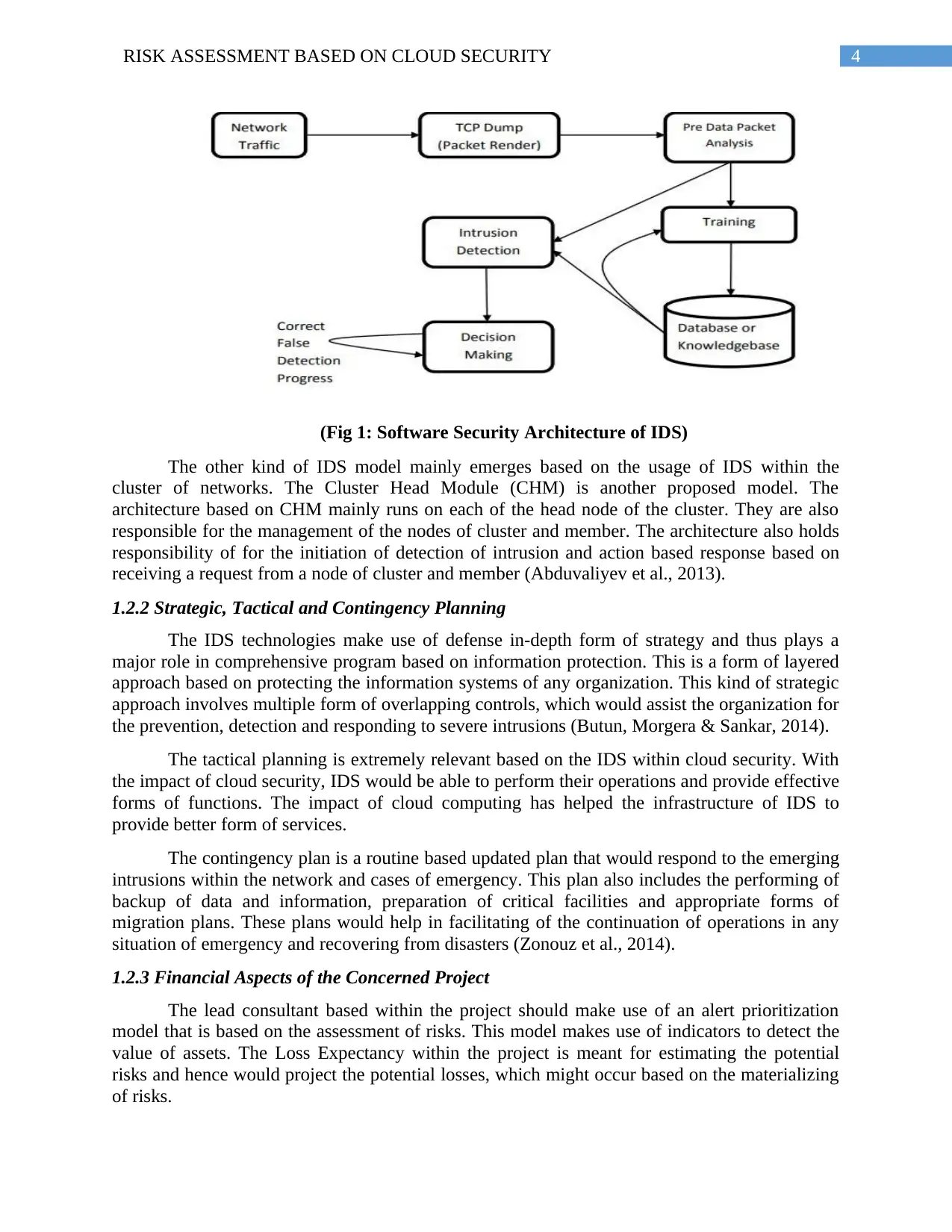
4RISK ASSESSMENT BASED ON CLOUD SECURITY
(Fig 1: Software Security Architecture of IDS)
The other kind of IDS model mainly emerges based on the usage of IDS within the
cluster of networks. The Cluster Head Module (CHM) is another proposed model. The
architecture based on CHM mainly runs on each of the head node of the cluster. They are also
responsible for the management of the nodes of cluster and member. The architecture also holds
responsibility of for the initiation of detection of intrusion and action based response based on
receiving a request from a node of cluster and member (Abduvaliyev et al., 2013).
1.2.2 Strategic, Tactical and Contingency Planning
The IDS technologies make use of defense in-depth form of strategy and thus plays a
major role in comprehensive program based on information protection. This is a form of layered
approach based on protecting the information systems of any organization. This kind of strategic
approach involves multiple form of overlapping controls, which would assist the organization for
the prevention, detection and responding to severe intrusions (Butun, Morgera & Sankar, 2014).
The tactical planning is extremely relevant based on the IDS within cloud security. With
the impact of cloud security, IDS would be able to perform their operations and provide effective
forms of functions. The impact of cloud computing has helped the infrastructure of IDS to
provide better form of services.
The contingency plan is a routine based updated plan that would respond to the emerging
intrusions within the network and cases of emergency. This plan also includes the performing of
backup of data and information, preparation of critical facilities and appropriate forms of
migration plans. These plans would help in facilitating of the continuation of operations in any
situation of emergency and recovering from disasters (Zonouz et al., 2014).
1.2.3 Financial Aspects of the Concerned Project
The lead consultant based within the project should make use of an alert prioritization
model that is based on the assessment of risks. This model makes use of indicators to detect the
value of assets. The Loss Expectancy within the project is meant for estimating the potential
risks and hence would project the potential losses, which might occur based on the materializing
of risks.
(Fig 1: Software Security Architecture of IDS)
The other kind of IDS model mainly emerges based on the usage of IDS within the
cluster of networks. The Cluster Head Module (CHM) is another proposed model. The
architecture based on CHM mainly runs on each of the head node of the cluster. They are also
responsible for the management of the nodes of cluster and member. The architecture also holds
responsibility of for the initiation of detection of intrusion and action based response based on
receiving a request from a node of cluster and member (Abduvaliyev et al., 2013).
1.2.2 Strategic, Tactical and Contingency Planning
The IDS technologies make use of defense in-depth form of strategy and thus plays a
major role in comprehensive program based on information protection. This is a form of layered
approach based on protecting the information systems of any organization. This kind of strategic
approach involves multiple form of overlapping controls, which would assist the organization for
the prevention, detection and responding to severe intrusions (Butun, Morgera & Sankar, 2014).
The tactical planning is extremely relevant based on the IDS within cloud security. With
the impact of cloud security, IDS would be able to perform their operations and provide effective
forms of functions. The impact of cloud computing has helped the infrastructure of IDS to
provide better form of services.
The contingency plan is a routine based updated plan that would respond to the emerging
intrusions within the network and cases of emergency. This plan also includes the performing of
backup of data and information, preparation of critical facilities and appropriate forms of
migration plans. These plans would help in facilitating of the continuation of operations in any
situation of emergency and recovering from disasters (Zonouz et al., 2014).
1.2.3 Financial Aspects of the Concerned Project
The lead consultant based within the project should make use of an alert prioritization
model that is based on the assessment of risks. This model makes use of indicators to detect the
value of assets. The Loss Expectancy within the project is meant for estimating the potential
risks and hence would project the potential losses, which might occur based on the materializing
of risks.

5RISK ASSESSMENT BASED ON CLOUD SECURITY
2. Risk Assessment based on Threats, Vulnerabilities and Consequences
2.1 Existing IT Control Framework and Recommendations based on Industry Risk
2.1.1 Policy and Procedures
The different kinds of security policies and procedures help in moving with the technical
form of countermeasure that includes the use of IDSs and firewalls. They are primarily meant to
leverage the security posture of Gigantic Corporation and mitigate risks while maintaining
competitive and financial viability. During the implementation of the IDS technologies, there
should be a proper process based on defining the policies and procedures with the help of
evaluation and implementation of different kinds of tools based on detection of intrusions. A
proper definition of the policies on implementation of IDS should be defined first. This would
help in increasing the chances of finding the proper IDS architecture (Elhag et al., 2015). The
different policies and procedures within the deployment of IDS would be helpful for protecting
the integrity of information and assets within the concerned organization.
2.1.2 Best Recommended Practice
The best form of recommended practices based on the implementation of IDS techniques
and protection against several kinds of intrusions within Gigantic Corporation are:
Use of tools based on IDS based on the industry standards for analyzing signatures and
behavior within the networks for various signs of attacks.
Scheduling of regular updates based on the detection of signatures such that emerging
threats might get detected.
Development of processes for sending alerts to the management of the organisation based
on the detection of suspicious activities.
Integration of procedures based on incident response for investigation and escalating
various kinds of confirmed incidents.
2.1.3 Current Evidences
The current evidences of the impact of IDS technologies are that they make use of ad hoc
approach for matching the characteristics of specific form of targeted environments. The use of
IDS could be used for issuing of alerts or alarms. In the current environment, the IDS are able to
take different kinds of automatic based actions based on shutting down of links of the internet or
some specific servers. These technologies also make active attempts for the identification of
attackers and hence can actively collect various kinds of evidences based on suspicious activities
(Mitchell & Chen, 2013).
In the recent times, the IDS systems could be based on software or they could be the
combination of software and hardware systems. Many of such kind of IDS based software
mainly run on the same kind of severs and devices in which the proxies, firewalls and various
other kinds of services would operate. Although various kinds of devices operate within the
peripheries of the network, the recent form of IDSs could be able to detect and thus deal with the
inside attacks as well as the external attacks on the system.
2. Risk Assessment based on Threats, Vulnerabilities and Consequences
2.1 Existing IT Control Framework and Recommendations based on Industry Risk
2.1.1 Policy and Procedures
The different kinds of security policies and procedures help in moving with the technical
form of countermeasure that includes the use of IDSs and firewalls. They are primarily meant to
leverage the security posture of Gigantic Corporation and mitigate risks while maintaining
competitive and financial viability. During the implementation of the IDS technologies, there
should be a proper process based on defining the policies and procedures with the help of
evaluation and implementation of different kinds of tools based on detection of intrusions. A
proper definition of the policies on implementation of IDS should be defined first. This would
help in increasing the chances of finding the proper IDS architecture (Elhag et al., 2015). The
different policies and procedures within the deployment of IDS would be helpful for protecting
the integrity of information and assets within the concerned organization.
2.1.2 Best Recommended Practice
The best form of recommended practices based on the implementation of IDS techniques
and protection against several kinds of intrusions within Gigantic Corporation are:
Use of tools based on IDS based on the industry standards for analyzing signatures and
behavior within the networks for various signs of attacks.
Scheduling of regular updates based on the detection of signatures such that emerging
threats might get detected.
Development of processes for sending alerts to the management of the organisation based
on the detection of suspicious activities.
Integration of procedures based on incident response for investigation and escalating
various kinds of confirmed incidents.
2.1.3 Current Evidences
The current evidences of the impact of IDS technologies are that they make use of ad hoc
approach for matching the characteristics of specific form of targeted environments. The use of
IDS could be used for issuing of alerts or alarms. In the current environment, the IDS are able to
take different kinds of automatic based actions based on shutting down of links of the internet or
some specific servers. These technologies also make active attempts for the identification of
attackers and hence can actively collect various kinds of evidences based on suspicious activities
(Mitchell & Chen, 2013).
In the recent times, the IDS systems could be based on software or they could be the
combination of software and hardware systems. Many of such kind of IDS based software
mainly run on the same kind of severs and devices in which the proxies, firewalls and various
other kinds of services would operate. Although various kinds of devices operate within the
peripheries of the network, the recent form of IDSs could be able to detect and thus deal with the
inside attacks as well as the external attacks on the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RISK ASSESSMENT BASED ON CLOUD SECURITY
2.2 Identification and Discussion of the Key Agents of Threats
2.2.1 List of Threat Agents
Threat agents could be defined as the potential actors who are primarily responsible for
posing a threat to the computing systems. They are also known as a system entity, which
performs an action of threat. The different kinds of threat agents within the IDS are ransomware
attacks, malware, Trojans and Hackers. These kinds of threats pose a major form of threats
within the internal systems of the organizations.
2.2.2 Issues
The most types of issues faced by IDSs are:
Management of high volume of alerts.
Ensuring of an effective form of deployment based on which the IDS would work
efficiently.
Understanding and Investigation of alerts automatically.
Proper knowledge about responding to threats (Can & Sahingoz, 2015).
2.2.3 Consequences
Based on the improper form of selection of IDSs, there would be some kind of
consequences, which might affect the concerned organization. These are:
Late Running of Projects – Different kinds of unforeseen risks might slow down the
efficiency of the project and thus might affect the management of project plans. There
might be also some form of delays that might take place during the activities of risk
management. These might push out other kinds of activities based on the schedule of the
project (Abduvaliyev et al., 2013).
Reputational Damage – The improper implementation of IDSs could lead to the damage
to the reputation of the organisation. Imposed threats could damage the internal processes
of the systems and steal valuable assets of the organisation.
Failure of Projects – The failure to manage risks within the projects could lead to the
failure of vital projects. This might cause the failure of business processes (Chung et al.,
2013).
2.2 Identification and Discussion of the Key Agents of Threats
2.2.1 List of Threat Agents
Threat agents could be defined as the potential actors who are primarily responsible for
posing a threat to the computing systems. They are also known as a system entity, which
performs an action of threat. The different kinds of threat agents within the IDS are ransomware
attacks, malware, Trojans and Hackers. These kinds of threats pose a major form of threats
within the internal systems of the organizations.
2.2.2 Issues
The most types of issues faced by IDSs are:
Management of high volume of alerts.
Ensuring of an effective form of deployment based on which the IDS would work
efficiently.
Understanding and Investigation of alerts automatically.
Proper knowledge about responding to threats (Can & Sahingoz, 2015).
2.2.3 Consequences
Based on the improper form of selection of IDSs, there would be some kind of
consequences, which might affect the concerned organization. These are:
Late Running of Projects – Different kinds of unforeseen risks might slow down the
efficiency of the project and thus might affect the management of project plans. There
might be also some form of delays that might take place during the activities of risk
management. These might push out other kinds of activities based on the schedule of the
project (Abduvaliyev et al., 2013).
Reputational Damage – The improper implementation of IDSs could lead to the damage
to the reputation of the organisation. Imposed threats could damage the internal processes
of the systems and steal valuable assets of the organisation.
Failure of Projects – The failure to manage risks within the projects could lead to the
failure of vital projects. This might cause the failure of business processes (Chung et al.,
2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
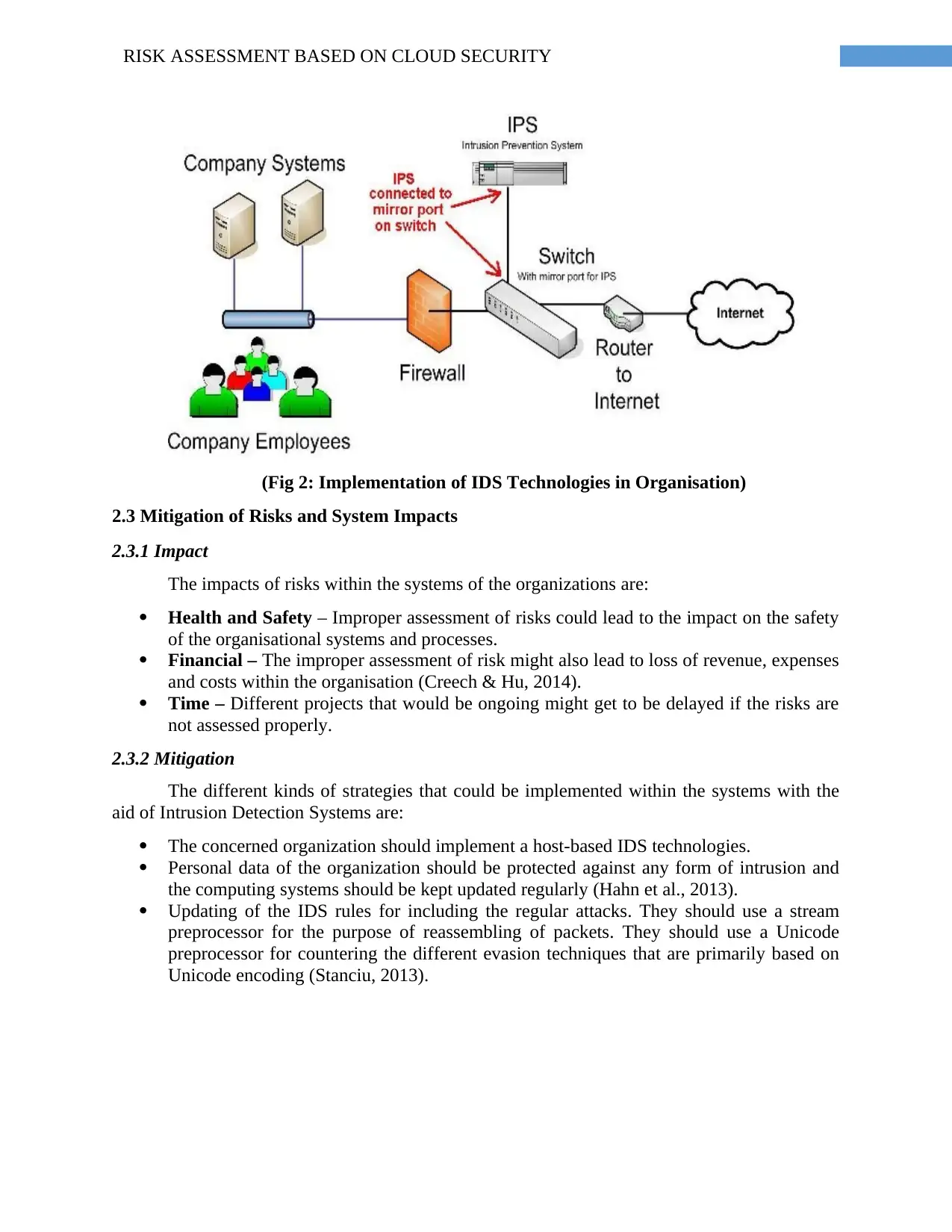
7RISK ASSESSMENT BASED ON CLOUD SECURITY
(Fig 2: Implementation of IDS Technologies in Organisation)
2.3 Mitigation of Risks and System Impacts
2.3.1 Impact
The impacts of risks within the systems of the organizations are:
Health and Safety – Improper assessment of risks could lead to the impact on the safety
of the organisational systems and processes.
Financial – The improper assessment of risk might also lead to loss of revenue, expenses
and costs within the organisation (Creech & Hu, 2014).
Time – Different projects that would be ongoing might get to be delayed if the risks are
not assessed properly.
2.3.2 Mitigation
The different kinds of strategies that could be implemented within the systems with the
aid of Intrusion Detection Systems are:
The concerned organization should implement a host-based IDS technologies.
Personal data of the organization should be protected against any form of intrusion and
the computing systems should be kept updated regularly (Hahn et al., 2013).
Updating of the IDS rules for including the regular attacks. They should use a stream
preprocessor for the purpose of reassembling of packets. They should use a Unicode
preprocessor for countering the different evasion techniques that are primarily based on
Unicode encoding (Stanciu, 2013).
(Fig 2: Implementation of IDS Technologies in Organisation)
2.3 Mitigation of Risks and System Impacts
2.3.1 Impact
The impacts of risks within the systems of the organizations are:
Health and Safety – Improper assessment of risks could lead to the impact on the safety
of the organisational systems and processes.
Financial – The improper assessment of risk might also lead to loss of revenue, expenses
and costs within the organisation (Creech & Hu, 2014).
Time – Different projects that would be ongoing might get to be delayed if the risks are
not assessed properly.
2.3.2 Mitigation
The different kinds of strategies that could be implemented within the systems with the
aid of Intrusion Detection Systems are:
The concerned organization should implement a host-based IDS technologies.
Personal data of the organization should be protected against any form of intrusion and
the computing systems should be kept updated regularly (Hahn et al., 2013).
Updating of the IDS rules for including the regular attacks. They should use a stream
preprocessor for the purpose of reassembling of packets. They should use a Unicode
preprocessor for countering the different evasion techniques that are primarily based on
Unicode encoding (Stanciu, 2013).

8RISK ASSESSMENT BASED ON CLOUD SECURITY
3. Literature Review
3.1 Protection Mechanisms for Employing Information Security
3.1.1 Safe Guards
The different kinds of safeguards that could be implemented within the strategic systems
include customizable electronic accessibility cards, perimeter fencing, biometrics and antivirus
software that could be implemented within the organisation for safeguarding the cloud
environment (Mitchell & Chen, 2015).
3.1.2 Security Mechanisms
Different other kinds of security mechanism based on the implementation of cloud
secured platforms are:
Digital Signature – This kind of mechanism helps in providing the means for providing
the authentic data and thus provide integrity with the aid of non-repudiation and
authentication. In this form of system, the message would be assigned a digital signature
prior to the transmission of information (Rewagad & Pawar, 2013).
Hashing – This form of mechanism is used in a one-way manner. On application of the
property of hashing to a particular message, it would be locked and no such key would
be provided for the unlocking of the message.
Encryption – This is a form of security mechanism in which the plaintext data would be
paired with a certain string of characters that would be known as an encryption key. In
this mechanism, the secret message would be established and shared among authorized
parties (Ryan, 2013).
3.1.3 Key Principle of Information Security
The main principle of information security is to secure the data and assets within various
organizations. In the recent times, the use of high form of information security is very much
essential. The major forms of benefits for information security based within cloud platform is
network based access within computing and services based on data storage (Webb et al., 2014).
Hence, the main principle of the security of information is to provide scalability, adaptability and
economical assurance within the organizations.
4. Conclusion
Based on the above discussion, it could be concluded that the Intrusion Detection
Systems could be deployed within the aspect of cloud security of Gigantic Corporations. The
organisation is dedicated to provide vast form of IT services to their business clients and hence
require high form of security within their systems. Hence the IDS technologies are deployed
within the cloud environment for the purpose of detecting any form of malicious behavior within
the network and the computing systems. The report discusses on the impact of applying the IDS
technologies in the cloud environment and thus maintain high form of security of the resources
of the organization.
3. Literature Review
3.1 Protection Mechanisms for Employing Information Security
3.1.1 Safe Guards
The different kinds of safeguards that could be implemented within the strategic systems
include customizable electronic accessibility cards, perimeter fencing, biometrics and antivirus
software that could be implemented within the organisation for safeguarding the cloud
environment (Mitchell & Chen, 2015).
3.1.2 Security Mechanisms
Different other kinds of security mechanism based on the implementation of cloud
secured platforms are:
Digital Signature – This kind of mechanism helps in providing the means for providing
the authentic data and thus provide integrity with the aid of non-repudiation and
authentication. In this form of system, the message would be assigned a digital signature
prior to the transmission of information (Rewagad & Pawar, 2013).
Hashing – This form of mechanism is used in a one-way manner. On application of the
property of hashing to a particular message, it would be locked and no such key would
be provided for the unlocking of the message.
Encryption – This is a form of security mechanism in which the plaintext data would be
paired with a certain string of characters that would be known as an encryption key. In
this mechanism, the secret message would be established and shared among authorized
parties (Ryan, 2013).
3.1.3 Key Principle of Information Security
The main principle of information security is to secure the data and assets within various
organizations. In the recent times, the use of high form of information security is very much
essential. The major forms of benefits for information security based within cloud platform is
network based access within computing and services based on data storage (Webb et al., 2014).
Hence, the main principle of the security of information is to provide scalability, adaptability and
economical assurance within the organizations.
4. Conclusion
Based on the above discussion, it could be concluded that the Intrusion Detection
Systems could be deployed within the aspect of cloud security of Gigantic Corporations. The
organisation is dedicated to provide vast form of IT services to their business clients and hence
require high form of security within their systems. Hence the IDS technologies are deployed
within the cloud environment for the purpose of detecting any form of malicious behavior within
the network and the computing systems. The report discusses on the impact of applying the IDS
technologies in the cloud environment and thus maintain high form of security of the resources
of the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RISK ASSESSMENT BASED ON CLOUD SECURITY
5. References
Abduvaliyev, A., Pathan, A. S. K., Zhou, J., Roman, R., & Wong, W. C. (2013). On the vital
areas of intrusion detection systems in wireless sensor networks. IEEE Communications
Surveys & Tutorials, 15(3), 1223-1237.
Alrajeh, N. A., Khan, S., & Shams, B. (2013). Intrusion detection systems in wireless sensor
networks: a review. International Journal of Distributed Sensor Networks, 9(5), 167575.
Butun, I., Morgera, S. D., & Sankar, R. (2014). A survey of intrusion detection systems in
wireless sensor networks. IEEE communications surveys & tutorials, 16(1), 266-282.
Can, O., & Sahingoz, O. K. (2015, May). A survey of intrusion detection systems in wireless
sensor networks. In Modeling, Simulation, and Applied Optimization (ICMSAO), 2015
6th International Conference on (pp. 1-6). IEEE.
Chung, C. J., Khatkar, P., Xing, T., Lee, J., & Huang, D. (2013). NICE: Network intrusion
detection and countermeasure selection in virtual network systems. IEEE transactions on
dependable and secure computing, 10(4), 198-211.
Creech, G., & Hu, J. (2014). A semantic approach to host-based intrusion detection systems
using contiguous and discontiguous system call patterns. IEEE Transactions on
Computers, 63(4), 807-819.
Elhag, S., Fernández, A., Bawakid, A., Alshomrani, S., & Herrera, F. (2015). On the
combination of genetic fuzzy systems and pairwise learning for improving detection rates
on intrusion detection systems. Expert Systems with Applications, 42(1), 193-202.
Hahn, A., Ashok, A., Sridhar, S., & Govindarasu, M. (2013). Cyber-physical security testbeds:
Architecture, application, and evaluation for smart grid. IEEE Transactions on Smart
Grid, 4(2), 847-855.
Liao, H. J., Lin, C. H. R., Lin, Y. C., & Tung, K. Y. (2013). Intrusion detection system: A
comprehensive review. Journal of Network and Computer Applications, 36(1), 16-24.
Mitchell, R., & Chen, R. (2013). Behavior-rule based intrusion detection systems for safety
critical smart grid applications. IEEE Transactions on Smart Grid, 4(3), 1254-1263.
Mitchell, R., & Chen, R. (2015). Behavior rule specification-based intrusion detection for safety
critical medical cyber physical systems. IEEE Transactions on Dependable and Secure
Computing, 12(1), 16-30.
Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A., & Rajarajan, M. (2013). A survey of
intrusion detection techniques in cloud. Journal of network and computer
applications, 36(1), 42-57.
Patel, A., Taghavi, M., Bakhtiyari, K., & JúNior, J. C. (2013). An intrusion detection and
prevention system in cloud computing: A systematic review. Journal of network and
computer applications, 36(1), 25-41.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
5. References
Abduvaliyev, A., Pathan, A. S. K., Zhou, J., Roman, R., & Wong, W. C. (2013). On the vital
areas of intrusion detection systems in wireless sensor networks. IEEE Communications
Surveys & Tutorials, 15(3), 1223-1237.
Alrajeh, N. A., Khan, S., & Shams, B. (2013). Intrusion detection systems in wireless sensor
networks: a review. International Journal of Distributed Sensor Networks, 9(5), 167575.
Butun, I., Morgera, S. D., & Sankar, R. (2014). A survey of intrusion detection systems in
wireless sensor networks. IEEE communications surveys & tutorials, 16(1), 266-282.
Can, O., & Sahingoz, O. K. (2015, May). A survey of intrusion detection systems in wireless
sensor networks. In Modeling, Simulation, and Applied Optimization (ICMSAO), 2015
6th International Conference on (pp. 1-6). IEEE.
Chung, C. J., Khatkar, P., Xing, T., Lee, J., & Huang, D. (2013). NICE: Network intrusion
detection and countermeasure selection in virtual network systems. IEEE transactions on
dependable and secure computing, 10(4), 198-211.
Creech, G., & Hu, J. (2014). A semantic approach to host-based intrusion detection systems
using contiguous and discontiguous system call patterns. IEEE Transactions on
Computers, 63(4), 807-819.
Elhag, S., Fernández, A., Bawakid, A., Alshomrani, S., & Herrera, F. (2015). On the
combination of genetic fuzzy systems and pairwise learning for improving detection rates
on intrusion detection systems. Expert Systems with Applications, 42(1), 193-202.
Hahn, A., Ashok, A., Sridhar, S., & Govindarasu, M. (2013). Cyber-physical security testbeds:
Architecture, application, and evaluation for smart grid. IEEE Transactions on Smart
Grid, 4(2), 847-855.
Liao, H. J., Lin, C. H. R., Lin, Y. C., & Tung, K. Y. (2013). Intrusion detection system: A
comprehensive review. Journal of Network and Computer Applications, 36(1), 16-24.
Mitchell, R., & Chen, R. (2013). Behavior-rule based intrusion detection systems for safety
critical smart grid applications. IEEE Transactions on Smart Grid, 4(3), 1254-1263.
Mitchell, R., & Chen, R. (2015). Behavior rule specification-based intrusion detection for safety
critical medical cyber physical systems. IEEE Transactions on Dependable and Secure
Computing, 12(1), 16-30.
Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A., & Rajarajan, M. (2013). A survey of
intrusion detection techniques in cloud. Journal of network and computer
applications, 36(1), 42-57.
Patel, A., Taghavi, M., Bakhtiyari, K., & JúNior, J. C. (2013). An intrusion detection and
prevention system in cloud computing: A systematic review. Journal of network and
computer applications, 36(1), 25-41.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RISK ASSESSMENT BASED ON CLOUD SECURITY
Rewagad, P., & Pawar, Y. (2013, April). Use of digital signature with diffie hellman key
exchange and AES encryption algorithm to enhance data security in cloud computing.
In Communication Systems and Network Technologies (CSNT), 2013 International
Conference on (pp. 437-439). IEEE.
Ryan, M. D. (2013). Cloud computing security: The scientific challenge, and a survey of
solutions. Journal of Systems and Software, 86(9), 2263-2268.
Snapp, S. R., Brentano, J., Dias, G., Goan, T. L., Heberlein, L. T., Ho, C. L., & Levitt, K. N.
(2017). DIDS (Distributed Intrusion Detection System)-Motivation, Architecture, and An
Early Prototype.
Stanciu, N. (2013). Technologies, methodologies and challenges in network intrusion detection
and prevention systems. Informatica Economica, 17(1).
Webb, J., Ahmad, A., Maynard, S. B., & Shanks, G. (2014). A situation awareness model for
information security risk management. Computers & security, 44, 1-15.
Zonouz, S., Davis, C. M., Davis, K. R., Berthier, R., Bobba, R. B., & Sanders, W. H. (2014).
SOCCA: A security-oriented cyber-physical contingency analysis in power
infrastructures. IEEE Transactions on Smart Grid, 5(1), 3-13.
Rewagad, P., & Pawar, Y. (2013, April). Use of digital signature with diffie hellman key
exchange and AES encryption algorithm to enhance data security in cloud computing.
In Communication Systems and Network Technologies (CSNT), 2013 International
Conference on (pp. 437-439). IEEE.
Ryan, M. D. (2013). Cloud computing security: The scientific challenge, and a survey of
solutions. Journal of Systems and Software, 86(9), 2263-2268.
Snapp, S. R., Brentano, J., Dias, G., Goan, T. L., Heberlein, L. T., Ho, C. L., & Levitt, K. N.
(2017). DIDS (Distributed Intrusion Detection System)-Motivation, Architecture, and An
Early Prototype.
Stanciu, N. (2013). Technologies, methodologies and challenges in network intrusion detection
and prevention systems. Informatica Economica, 17(1).
Webb, J., Ahmad, A., Maynard, S. B., & Shanks, G. (2014). A situation awareness model for
information security risk management. Computers & security, 44, 1-15.
Zonouz, S., Davis, C. M., Davis, K. R., Berthier, R., Bobba, R. B., & Sanders, W. H. (2014).
SOCCA: A security-oriented cyber-physical contingency analysis in power
infrastructures. IEEE Transactions on Smart Grid, 5(1), 3-13.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





