Risk Assessment for Cyber Security Management - Desklib
13 Pages3482 Words205 Views
Added on 2023-06-10
About This Document
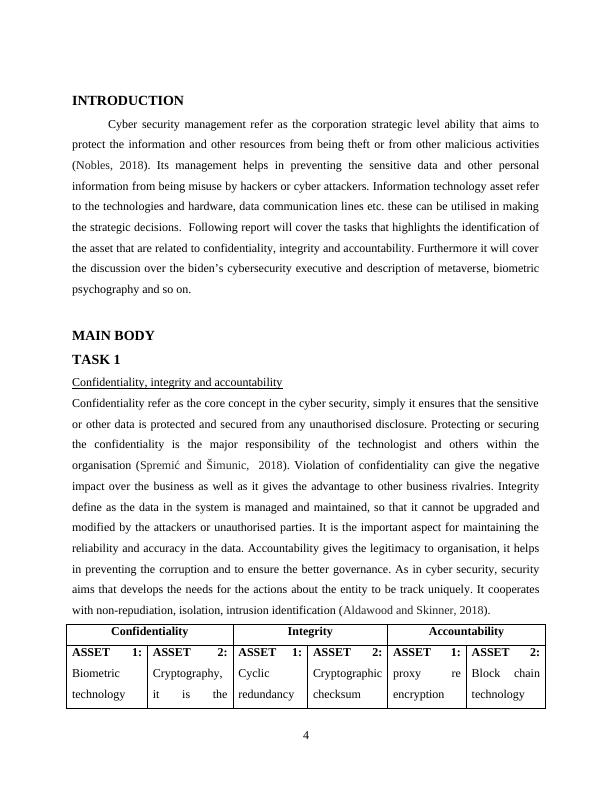
This report covers tasks related to confidentiality, integrity, and accountability in cyber security management. It discusses Biden's cybersecurity executive order, Metaverse, biometric psychography, and more. The report also includes solved assignments, essays, and dissertations on Desklib.
Risk Assessment for Cyber Security Management - Desklib
Added on 2023-06-10
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Biometrics and Cyber Security: Future Direction
|4
|825
|211
Principles of Information Security: Role of People and Physical Security in Data Centers
|10
|2296
|423
Assignment on Information Security
|13
|2568
|146
System Security Assessment using Vulnerability Repositories
|42
|12515
|74
IT Security: Types of Risks, Organizational Procedures, Impact of Firewall Configuration, Implementation of DMZ, Static IP and NAT
|18
|1181
|61
Information Security for ATM: Confidentiality, Integrity, Availability, Biometric and Cypher Code
|9
|1921
|244