Risk Assessment of IT Security & Control - HND Digital Tech
VerifiedAdded on 2023/04/24
|18
|5374
|103
Report
AI Summary
This report provides a comprehensive assessment of IT security risks for JIN Investment Ltd, following a security breach in the finance department. It details various security threats, vulnerabilities, and risks, emphasizing the importance of business continuity planning. The report includes an IT security risk assessment and treatment plan, covering risk identification, investigation, and estimation. It explores IT security solutions such as firewall policies, VPN configurations, network security implementations like DMZ, static IP, and NAT, and network monitoring systems. Furthermore, it outlines physical and virtual security measures to ensure the integrity of JIN Investments Ltd's system. The document concludes with a review of mechanisms to control organizational IT security and manage overall security strategies.

risk assessment of it security possible solutions and mechanisms to control it security risk
Unit 8: Security
2022
HND Digital Technologies GBS
Student:
Tutor:
Jun 2022 – Group A1 or B1
Word Count: x,xxx
Unit 8: Security
2022
HND Digital Technologies GBS
Student:
Tutor:
Jun 2022 – Group A1 or B1
Word Count: x,xxx
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction........................................................................................................................................5
LO1 Assessment of IT Security Risks.........................................................................................6
1. Different Types of security, threats, and Vulnerabilities.............................................6
1.1 Security vulnerability...................................................................................................6
1.2 Security Threat..............................................................................................................6
1.3 Security Risk..................................................................................................................7
2. Security Procedures for business continuity................................................................7
3. IT security risks assessment and treatment..................................................................8
3.1 Risks assessment.........................................................................................................8
3.2 Risks treatment.............................................................................................................8
LO2 - IT security solutions.............................................................................................................9
1. Configuration of Firewall policies and third-party VPNs.............................................9
1.1 Configuration of Firewall policies.............................................................................9
1.2 Configuration of third-party VPNs..........................................................................11
2. Implementation of network security DMZ, Static IP, and NAT.................................11
2.1 Explanation of DMZ implementation......................................................................12
2.2 Configuration of static IP and NAT.........................................................................12
3. Implementation of a network monitoring system.......................................................12
4. Security measures to ensure the integrity of the JIN Investments Ltd system...13
4.1 Three physical security measures..........................................................................13
4.2 Three virtual security measures..............................................................................13
LO3 Review mechanisms to control organisational IT security.........................................14
LO4 Manage organisational security.........................................................................................14
Conclusion.......................................................................................................................................15
References.......................................................................................................................................16
pg. 1
Introduction........................................................................................................................................5
LO1 Assessment of IT Security Risks.........................................................................................6
1. Different Types of security, threats, and Vulnerabilities.............................................6
1.1 Security vulnerability...................................................................................................6
1.2 Security Threat..............................................................................................................6
1.3 Security Risk..................................................................................................................7
2. Security Procedures for business continuity................................................................7
3. IT security risks assessment and treatment..................................................................8
3.1 Risks assessment.........................................................................................................8
3.2 Risks treatment.............................................................................................................8
LO2 - IT security solutions.............................................................................................................9
1. Configuration of Firewall policies and third-party VPNs.............................................9
1.1 Configuration of Firewall policies.............................................................................9
1.2 Configuration of third-party VPNs..........................................................................11
2. Implementation of network security DMZ, Static IP, and NAT.................................11
2.1 Explanation of DMZ implementation......................................................................12
2.2 Configuration of static IP and NAT.........................................................................12
3. Implementation of a network monitoring system.......................................................12
4. Security measures to ensure the integrity of the JIN Investments Ltd system...13
4.1 Three physical security measures..........................................................................13
4.2 Three virtual security measures..............................................................................13
LO3 Review mechanisms to control organisational IT security.........................................14
LO4 Manage organisational security.........................................................................................14
Conclusion.......................................................................................................................................15
References.......................................................................................................................................16
pg. 1
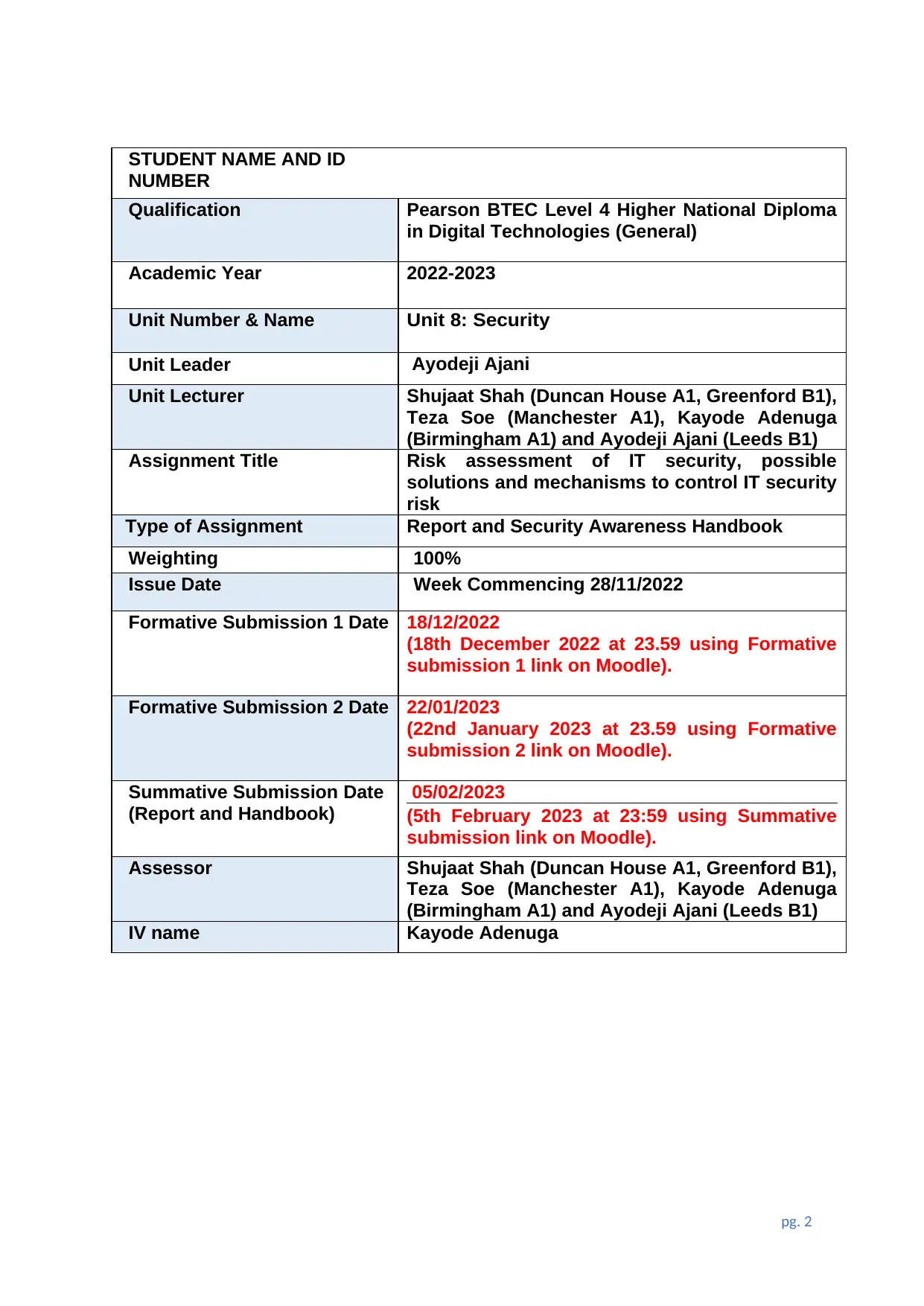
STUDENT NAME AND ID
NUMBER
Qualification Pearson BTEC Level 4 Higher National Diploma
in Digital Technologies (General)
Academic Year 2022-2023
Unit Number & Name Unit 8: Security
Unit Leader Ayodeji Ajani
Unit Lecturer Shujaat Shah (Duncan House A1, Greenford B1),
Teza Soe (Manchester A1), Kayode Adenuga
(Birmingham A1) and Ayodeji Ajani (Leeds B1)
Assignment Title Risk assessment of IT security, possible
solutions and mechanisms to control IT security
risk
Type of Assignment Report and Security Awareness Handbook
Weighting 100%
Issue Date Week Commencing 28/11/2022
Formative Submission 1 Date 18/12/2022
(18th December 2022 at 23.59 using Formative
submission 1 link on Moodle).
Formative Submission 2 Date 22/01/2023
(22nd January 2023 at 23.59 using Formative
submission 2 link on Moodle).
Summative Submission Date
(Report and Handbook)
05/02/2023
(5th February 2023 at 23:59 using Summative
submission link on Moodle).
Assessor Shujaat Shah (Duncan House A1, Greenford B1),
Teza Soe (Manchester A1), Kayode Adenuga
(Birmingham A1) and Ayodeji Ajani (Leeds B1)
IV name Kayode Adenuga
pg. 2
NUMBER
Qualification Pearson BTEC Level 4 Higher National Diploma
in Digital Technologies (General)
Academic Year 2022-2023
Unit Number & Name Unit 8: Security
Unit Leader Ayodeji Ajani
Unit Lecturer Shujaat Shah (Duncan House A1, Greenford B1),
Teza Soe (Manchester A1), Kayode Adenuga
(Birmingham A1) and Ayodeji Ajani (Leeds B1)
Assignment Title Risk assessment of IT security, possible
solutions and mechanisms to control IT security
risk
Type of Assignment Report and Security Awareness Handbook
Weighting 100%
Issue Date Week Commencing 28/11/2022
Formative Submission 1 Date 18/12/2022
(18th December 2022 at 23.59 using Formative
submission 1 link on Moodle).
Formative Submission 2 Date 22/01/2023
(22nd January 2023 at 23.59 using Formative
submission 2 link on Moodle).
Summative Submission Date
(Report and Handbook)
05/02/2023
(5th February 2023 at 23:59 using Summative
submission link on Moodle).
Assessor Shujaat Shah (Duncan House A1, Greenford B1),
Teza Soe (Manchester A1), Kayode Adenuga
(Birmingham A1) and Ayodeji Ajani (Leeds B1)
IV name Kayode Adenuga
pg. 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Student Declaration
This is to confirm that this submission is my own work, produced without any
external help except for acceptable support from my lecturer. It has not been
copied from any other person’s work (published or unpublished) and has not
previously been submitted for assessment either at GBS or elsewhere. I confirm
that I have read and understood the ‘GBS Academic Good Practice and Academic
Misconduct: Policy and Procedure’ available on Moodle.
I confirm I have read and understood the above Student Declaration.
Student Name (print)
Signature
Date
pg. 3
This is to confirm that this submission is my own work, produced without any
external help except for acceptable support from my lecturer. It has not been
copied from any other person’s work (published or unpublished) and has not
previously been submitted for assessment either at GBS or elsewhere. I confirm
that I have read and understood the ‘GBS Academic Good Practice and Academic
Misconduct: Policy and Procedure’ available on Moodle.
I confirm I have read and understood the above Student Declaration.
Student Name (print)
Signature
Date
pg. 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
In today’s world, data and information are two of the most valuable resources. These
resources require appropriate protection against various malicious interests. To
ensure the safety of data, security systems are needed to be implemented (Chen et
al., 2010). As I have recently joined JIN Investment Ltd as a Junior Information
Security Analyst. I’ve been appointed by my line manager to critically evaluate the
company. According to my evaluation, a security breach has occurred in the finance
department. As result, necessary accounting information is revealed. to wire fraud by
a mistake done by the finance manager. The amount of loss is more than 1.2 million
pounds. In this report, different security standards are described and security
procedures are explained. It also includes IT security risk assessment and treatment,
as well as IT security solutions, are also demonstrated. Finally, it provides the
implementation of network security and security standards to ensure the integrity of
JIN Investment Ltd.
pg. 4
In today’s world, data and information are two of the most valuable resources. These
resources require appropriate protection against various malicious interests. To
ensure the safety of data, security systems are needed to be implemented (Chen et
al., 2010). As I have recently joined JIN Investment Ltd as a Junior Information
Security Analyst. I’ve been appointed by my line manager to critically evaluate the
company. According to my evaluation, a security breach has occurred in the finance
department. As result, necessary accounting information is revealed. to wire fraud by
a mistake done by the finance manager. The amount of loss is more than 1.2 million
pounds. In this report, different security standards are described and security
procedures are explained. It also includes IT security risk assessment and treatment,
as well as IT security solutions, are also demonstrated. Finally, it provides the
implementation of network security and security standards to ensure the integrity of
JIN Investment Ltd.
pg. 4

LO1 Assessment of IT Security Risks
Do not type anything here!!!
1. Different Types of security, threats, and Vulnerabilities
Do not type anything here!!!
1.1 Security vulnerability
A security vulnerability is an unwanted nature of a calculating element or setting up a
process that amplifies the peril of an unfavourable incident or a decrease in profit
either because of unintentional revelation, measured ambush, or dispute with new
process elements (Alhazmi et al., 2012). From its definition we get the idea that a
vulnerability can be sorted by the utilisation of a software patch, redesign, making
the user competent, updating the computer codes of the firm, or replacing the
hardware. Since digital technology is evolving with time, new vulnerabilities will also
continue to appear with it. It is obligatory to examine the security systems of a firm
on a regular basis. For example, vulnerabilities in software may include limited
checking, scarcity of audit trail, faults in design and memory safety breaches, etc and
vulnerabilities in the network may include unsafe communication wires and
unprotected network construction. For example, malicious software, advertisement
software, and spoofing.
1.2 Security Threat
A threat can be defined as the latest or recently identified event that has the possible
chance of injuring a system or the whole corporation (Jouini et al., 2014). The three
major types of threats are,
- Environmental threats, such as tornadoes, cyclones, and earthquakes
- Unwanted threats, such as an official member making mistakes in maintaining
important information.
pg. 5
Do not type anything here!!!
1. Different Types of security, threats, and Vulnerabilities
Do not type anything here!!!
1.1 Security vulnerability
A security vulnerability is an unwanted nature of a calculating element or setting up a
process that amplifies the peril of an unfavourable incident or a decrease in profit
either because of unintentional revelation, measured ambush, or dispute with new
process elements (Alhazmi et al., 2012). From its definition we get the idea that a
vulnerability can be sorted by the utilisation of a software patch, redesign, making
the user competent, updating the computer codes of the firm, or replacing the
hardware. Since digital technology is evolving with time, new vulnerabilities will also
continue to appear with it. It is obligatory to examine the security systems of a firm
on a regular basis. For example, vulnerabilities in software may include limited
checking, scarcity of audit trail, faults in design and memory safety breaches, etc and
vulnerabilities in the network may include unsafe communication wires and
unprotected network construction. For example, malicious software, advertisement
software, and spoofing.
1.2 Security Threat
A threat can be defined as the latest or recently identified event that has the possible
chance of injuring a system or the whole corporation (Jouini et al., 2014). The three
major types of threats are,
- Environmental threats, such as tornadoes, cyclones, and earthquakes
- Unwanted threats, such as an official member making mistakes in maintaining
important information.
pg. 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

- Deliberate threats, such as malicious software, advertisement-supported software
companies, or the activities of a resentful employee.
Examples are a harmful user accessing the personal files of the employees, and an
offender altering the central database of a company.
1.3 Security Risk
Risk is described as the probable reason for deprivation or harm while a threat
utilises a vulnerability (Joshi et al., 2017). For instance, profit reduction, exposure of
confidential information, losing privacy control, etc. Risks can be decreased by
developing and actualising a risk management strategy.
2. Security Procedures for business continuity
To ensure the consistency of a business, business continuity planning is very
necessary. Business continuity planning is the system of generating defensive and
retrieval options to handle possible cyber hazards to a firm or to make sure of the
continuity of the business (Speight, 2011). The business continuity process's
secondary objective is to make sure of functional consistency prior to and during the
implementation of retrieval systems. The designing of the strategy includes wealth
and human resource protection, thus securing an instant retrieval of functions in the
time of a tragedy. In short, the fundamental requirement for ensuring the continuity of
the business is to maintain necessary operations properly while a catastrophe is
going on and to retrieve them as quickly as possible (Ligget, 2020). A business
continuity strategy includes different unforeseeable incidents such as environmental
disasters, fires, pandemics, and other natural threats.
In certain times when an intermission is intolerable for any corporation, maintaining
continuity is crucial to execute customer management, retaining the clients, and
functional safety. Reasons for an intermission in a business process are many, but
the attack on IT infrastructure and recalcitrant natural conditions are two of the most
widespread affairs that can damage a business in a very limited time (Lykou et al.,
2018). That’s why it is compulsory to have a strategy to maintain the continuity of the
business that can manage the operations fluently and make the business run again
in a short period.
Steps in business continuity strategy
- Running business effect research and assessing the risks
- Designing retrieval plans
- Actualisation of solutions
- Checking and undertaking
- Maintenance on a regular basis
pg. 6
companies, or the activities of a resentful employee.
Examples are a harmful user accessing the personal files of the employees, and an
offender altering the central database of a company.
1.3 Security Risk
Risk is described as the probable reason for deprivation or harm while a threat
utilises a vulnerability (Joshi et al., 2017). For instance, profit reduction, exposure of
confidential information, losing privacy control, etc. Risks can be decreased by
developing and actualising a risk management strategy.
2. Security Procedures for business continuity
To ensure the consistency of a business, business continuity planning is very
necessary. Business continuity planning is the system of generating defensive and
retrieval options to handle possible cyber hazards to a firm or to make sure of the
continuity of the business (Speight, 2011). The business continuity process's
secondary objective is to make sure of functional consistency prior to and during the
implementation of retrieval systems. The designing of the strategy includes wealth
and human resource protection, thus securing an instant retrieval of functions in the
time of a tragedy. In short, the fundamental requirement for ensuring the continuity of
the business is to maintain necessary operations properly while a catastrophe is
going on and to retrieve them as quickly as possible (Ligget, 2020). A business
continuity strategy includes different unforeseeable incidents such as environmental
disasters, fires, pandemics, and other natural threats.
In certain times when an intermission is intolerable for any corporation, maintaining
continuity is crucial to execute customer management, retaining the clients, and
functional safety. Reasons for an intermission in a business process are many, but
the attack on IT infrastructure and recalcitrant natural conditions are two of the most
widespread affairs that can damage a business in a very limited time (Lykou et al.,
2018). That’s why it is compulsory to have a strategy to maintain the continuity of the
business that can manage the operations fluently and make the business run again
in a short period.
Steps in business continuity strategy
- Running business effect research and assessing the risks
- Designing retrieval plans
- Actualisation of solutions
- Checking and undertaking
- Maintenance on a regular basis
pg. 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. IT security risks assessment and treatment
Do not type anything here!!!
3.1 Risks assessment
Security risk assessment recognises, assumes, and actualises main security
commands and programs. It also concentrates on reducing software safety flaws
and susceptibilities. Executing a risk estimation enables a firm to see the
software portfolio entirely (Wangen, 2017). Not only is IT risk estimation
significant for securing an enterprise but it may also be obligatory for properly
shaping the security investment of an organization. The risk assessment system
entails the following approaches,
Risk recognition: It is the system of estimating risks that could possibly stop the
event or business initiative from acquiring its goals. It involves enlisting and
transmitting the related issues.
Risk investigation: Risk investigation includes testing project consequences and
goals that might get altered because of the aftermaths of the risk incident. When
the risks are recognised, they are investigated to determine the theoretical and
quantifiable effect of the risk on the project so that necessary steps can be taken
to diminish them (Ralston et al., 2015).
Risk estimation: Risk estimation is the system which is used to differentiate the
predetermined risk from the provided risk requirement to find out the severity of
the risk.
3.2 Risks treatment
Risk treatment is the system of choosing and actualising standards to adjust risk.
Risk treatment standards can involve averting, reducing, transmitting, or holding
peril. The standards can be chosen out of groups of safety standards that are
used inside the data safety management system of the company (Oliveira et al.,
2022). At this rate, safety standards are oral explanations of different safety
functions that are actualised scientifically or institutionally. After recognising and
estimating the risks, the company should evaluate the available alternative
actions for handling these risks, the assumption, and estimation of their
consequences or effect, and the specialisation and actualisation of treatment
strategies. As recognised risks may possess many effects on the company, not
all risks contain the probability of loss or harm. Chances may also emerge from
the risk recognition system, as kinds of risk with positive effects or results are
recognised. Hence, the risk treatment methods to mitigate IT security risks are
Averting risks: By implementing a plan to avert the risks, an organisation can
determine standards to avert the risks from affecting the operations of an
organisation. Averting risks may require sacrificing other assets or plans to
pg. 7
Do not type anything here!!!
3.1 Risks assessment
Security risk assessment recognises, assumes, and actualises main security
commands and programs. It also concentrates on reducing software safety flaws
and susceptibilities. Executing a risk estimation enables a firm to see the
software portfolio entirely (Wangen, 2017). Not only is IT risk estimation
significant for securing an enterprise but it may also be obligatory for properly
shaping the security investment of an organization. The risk assessment system
entails the following approaches,
Risk recognition: It is the system of estimating risks that could possibly stop the
event or business initiative from acquiring its goals. It involves enlisting and
transmitting the related issues.
Risk investigation: Risk investigation includes testing project consequences and
goals that might get altered because of the aftermaths of the risk incident. When
the risks are recognised, they are investigated to determine the theoretical and
quantifiable effect of the risk on the project so that necessary steps can be taken
to diminish them (Ralston et al., 2015).
Risk estimation: Risk estimation is the system which is used to differentiate the
predetermined risk from the provided risk requirement to find out the severity of
the risk.
3.2 Risks treatment
Risk treatment is the system of choosing and actualising standards to adjust risk.
Risk treatment standards can involve averting, reducing, transmitting, or holding
peril. The standards can be chosen out of groups of safety standards that are
used inside the data safety management system of the company (Oliveira et al.,
2022). At this rate, safety standards are oral explanations of different safety
functions that are actualised scientifically or institutionally. After recognising and
estimating the risks, the company should evaluate the available alternative
actions for handling these risks, the assumption, and estimation of their
consequences or effect, and the specialisation and actualisation of treatment
strategies. As recognised risks may possess many effects on the company, not
all risks contain the probability of loss or harm. Chances may also emerge from
the risk recognition system, as kinds of risk with positive effects or results are
recognised. Hence, the risk treatment methods to mitigate IT security risks are
Averting risks: By implementing a plan to avert the risks, an organisation can
determine standards to avert the risks from affecting the operations of an
organisation. Averting risks may require sacrificing other assets or plans to
pg. 7

ensure that the company is trying its best to avert the risk (Bojanc & Jerman,
2013). For instance, one can experience a risk where he/she won’t be capable of
finishing their job because of a scarcity of experts. To avert the risk, he/she could
appoint numerous experts to complete the task but it would require a lion's share
of the budget to hire them.
Reducing risks: In this step, an organisation has to implement strategies for
diminishing risks. The organisation attempts to decrease the loss, rather than
totally vanish it. Therefore, there is some risk that remains and the organization
tries to minimize the risk so that it can operate its usual business functions
without any hindrance. For example, a company that is suffering from a shortage
of funds and its production may stop due to a lack of raw materials. In this
scenario, the company can reduce the risk by choosing cheaper options for raw
materials, so it will be able to continue to produce goods.
Transmitting risks: The utilisation of health insurance is an illustration of
transmitting risk because the monetary risk linked with health support is
transmitted from the insured to the insurer. Insurance corporations accept the
monetary risk in barter of an installment paid by the insured and a written
agreement between the insured and the insurance company (Blakely et al.,
2011). IT security risks are also transferred by developing a contractual
agreement in which a party provides funds for another to be responsible for
reducing certain risks that may or may not emerge.
Retaining risks: It is the system in which a company approves the monetary risks
and does not take action until they actually appear. Retention of risks aids
companies avert tiny risks while focusing on business functions. It is a significant
method appropriate for preparing budgets and placing a list of priorities. It is a
part of the risk treatment strategy in which less harmful risks are regarded as
tolerable costs.
LO2 - IT security solutions
Do not type anything here!!!
1. Configuration of Firewall policies and third-party VPNs
Do not type anything here!!!
1.1 Configuration of Firewall policies
Firewalls are a basic element of an organisation’s security policy. Firewalls can
provide safety against malware attacks, accessing confidential data, and other
threats by supervising network transmissions and resisting harmful transmissions
(Jeffrey & Samak, 2011). One of the major patterns that firewalls estimate is
pg. 8
2013). For instance, one can experience a risk where he/she won’t be capable of
finishing their job because of a scarcity of experts. To avert the risk, he/she could
appoint numerous experts to complete the task but it would require a lion's share
of the budget to hire them.
Reducing risks: In this step, an organisation has to implement strategies for
diminishing risks. The organisation attempts to decrease the loss, rather than
totally vanish it. Therefore, there is some risk that remains and the organization
tries to minimize the risk so that it can operate its usual business functions
without any hindrance. For example, a company that is suffering from a shortage
of funds and its production may stop due to a lack of raw materials. In this
scenario, the company can reduce the risk by choosing cheaper options for raw
materials, so it will be able to continue to produce goods.
Transmitting risks: The utilisation of health insurance is an illustration of
transmitting risk because the monetary risk linked with health support is
transmitted from the insured to the insurer. Insurance corporations accept the
monetary risk in barter of an installment paid by the insured and a written
agreement between the insured and the insurance company (Blakely et al.,
2011). IT security risks are also transferred by developing a contractual
agreement in which a party provides funds for another to be responsible for
reducing certain risks that may or may not emerge.
Retaining risks: It is the system in which a company approves the monetary risks
and does not take action until they actually appear. Retention of risks aids
companies avert tiny risks while focusing on business functions. It is a significant
method appropriate for preparing budgets and placing a list of priorities. It is a
part of the risk treatment strategy in which less harmful risks are regarded as
tolerable costs.
LO2 - IT security solutions
Do not type anything here!!!
1. Configuration of Firewall policies and third-party VPNs
Do not type anything here!!!
1.1 Configuration of Firewall policies
Firewalls are a basic element of an organisation’s security policy. Firewalls can
provide safety against malware attacks, accessing confidential data, and other
threats by supervising network transmissions and resisting harmful transmissions
(Jeffrey & Samak, 2011). One of the major patterns that firewalls estimate is
pg. 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

whether to approve or resist a transition on the basis of a sum of predetermined
regulations and fixing other security arrangements on a firewall. Firewalls
ascertain which transmission can proceed through a network border on the basis
of some predetermined regulations. The value of these regulations is determined
on the basis of the firewalls' ability to effectively resist harmful transmissions and
allow legitimate connections to pass. In addition, if a firewall is not adequately
built and protected, hackers and other malicious threats can discover
vulnerabilities and ways to acquire permission to get valuable information. A
firewall has a great impact on maintaining network safety and requires it to be
appropriately built to protect companies from data misplacement and malware
attacks (Liu et al., 2010). This has become possible by establishing domain
names and Internet Protocol (IP) addresses to ensure the safety of the firewall.
Configuring the firewall is very necessary because default technologies may not
deliver maximum security against malware or a cyberattack. Inappropriate firewall
establishment may result in hackers obtaining illegal control of the secured
networks and assets. Thus, hackers are continuously looking for networks that
are secured by software that is out of date. The automatic settings on many
firewalls and protocols such as the File Transfer Protocol (FTP) do not deliver the
required degree of security to protect networks from malware or adware attacks.
The process of configuring firewalls may include,
- Protect the firewall: Protecting the firewall is the most crucial step to make sure
that only authorised personnel have access to the firewall. This entails activities
like updating the firewall with the latest technology, never placing firewalls into
practice without properly building and using distinctive, safe passcodes.
- Set up firewall areas and IP address composition: It is necessary to recognise
network resources that must be secured. This involves generating a formation
that segments business resources into areas on the basis of alike operations and
the degree of risk (Hu et al., 2012). For example, servers- such as social media
servers, and VPN servers which are located in an allocated area that reduces
incoming web transmission, are defined as a demilitarized zone (DMZ).
- Compose lists of personnel with authorised control: These lists provide
companies with the capability of estimating which transmission is approved to
pass through each area. The lists of authorised control function as firewall
regulations, which can be used for each firewall interface (Wangen, 2017). These
lists need to be made certain of the appropriate origin and arriving point port
numbers and IP addresses.
Design other firewall facilities and registering: Several firewalls can be designed
to sustain other facilities like a Dynamic Host Composition Protocol server and
intervention prohibition system. It is significant to also deactivate the additional
facilities that will not be utilised. Moreover, firewalls must be composed to notify a
registering service to abide by and acquire the criteria of Payment Card Industry
Data security measures.
Examine the firewall composition: Besides composing the firewalls, it is crucial to
examine them to make sure that the malicious transmissions are being restricted
and the firewall functions as wanted. The composition can be examined by
utilising methods like checking the ability to penetrate and scanning the
vulnerabilities.
pg. 9
regulations and fixing other security arrangements on a firewall. Firewalls
ascertain which transmission can proceed through a network border on the basis
of some predetermined regulations. The value of these regulations is determined
on the basis of the firewalls' ability to effectively resist harmful transmissions and
allow legitimate connections to pass. In addition, if a firewall is not adequately
built and protected, hackers and other malicious threats can discover
vulnerabilities and ways to acquire permission to get valuable information. A
firewall has a great impact on maintaining network safety and requires it to be
appropriately built to protect companies from data misplacement and malware
attacks (Liu et al., 2010). This has become possible by establishing domain
names and Internet Protocol (IP) addresses to ensure the safety of the firewall.
Configuring the firewall is very necessary because default technologies may not
deliver maximum security against malware or a cyberattack. Inappropriate firewall
establishment may result in hackers obtaining illegal control of the secured
networks and assets. Thus, hackers are continuously looking for networks that
are secured by software that is out of date. The automatic settings on many
firewalls and protocols such as the File Transfer Protocol (FTP) do not deliver the
required degree of security to protect networks from malware or adware attacks.
The process of configuring firewalls may include,
- Protect the firewall: Protecting the firewall is the most crucial step to make sure
that only authorised personnel have access to the firewall. This entails activities
like updating the firewall with the latest technology, never placing firewalls into
practice without properly building and using distinctive, safe passcodes.
- Set up firewall areas and IP address composition: It is necessary to recognise
network resources that must be secured. This involves generating a formation
that segments business resources into areas on the basis of alike operations and
the degree of risk (Hu et al., 2012). For example, servers- such as social media
servers, and VPN servers which are located in an allocated area that reduces
incoming web transmission, are defined as a demilitarized zone (DMZ).
- Compose lists of personnel with authorised control: These lists provide
companies with the capability of estimating which transmission is approved to
pass through each area. The lists of authorised control function as firewall
regulations, which can be used for each firewall interface (Wangen, 2017). These
lists need to be made certain of the appropriate origin and arriving point port
numbers and IP addresses.
Design other firewall facilities and registering: Several firewalls can be designed
to sustain other facilities like a Dynamic Host Composition Protocol server and
intervention prohibition system. It is significant to also deactivate the additional
facilities that will not be utilised. Moreover, firewalls must be composed to notify a
registering service to abide by and acquire the criteria of Payment Card Industry
Data security measures.
Examine the firewall composition: Besides composing the firewalls, it is crucial to
examine them to make sure that the malicious transmissions are being restricted
and the firewall functions as wanted. The composition can be examined by
utilising methods like checking the ability to penetrate and scanning the
vulnerabilities.
pg. 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Maintain firewall regularly: Firewall maintenance is very important to ensure the
operability of the firewall. This involves supervising records, executing scans, and
reviewing the regulations frequently.
1.2 Configuration of third-party VPNs
A virtual private network or VPN is a major tech that is applied to improve internet
safety and provide secure isolated access for operators who have to get approval
for organisational WANs and their assets. A VPN links every type of user around
the globe. Before configuring a VPN, network composers should assess the basic
principles of the VPN, and choose attributes that are favourable to their
companies' operators (Rahimi et al., 2012). VPNs provide a protocol coating,
often known as a tunnelling protocol that summarises and inscribes network
transmissions.
The company must possess a router compatible with the desired operations to be
executed. Then utilising the quick start wizard guide for setting up the VPN. This
guide provides the necessary instructions to complete the whole process. After
setting up the VPN, the firm has to select the configuration of security. It is better
to select a stronger security system to protect valuable information (Degefa,
2015). Then enabling the operators to use the facilities. To do so, they need to
create accounts for each operator desiring access to the VPN. The final job is to
connect the computers to the network for enjoying isolated access to necessary
files. A VPN functions in the binary digital system. So, either the transmission is
completed or it is not. If the connection is not established, the transmission of
malicious traffic will also be impossible. When the VPN connection is unable to
function, the client-side program will show an error notification conveying some
codes. There are numerous various types of VPN codes such as VPN 800, VPN
619, VPN 691, etc.
2. Implementation of network security DMZ, Static IP, and NAT
Do not type anything here!!!
2.1 Explanation of DMZ implementation
A DMZ network is utilised as a subordinate network that bears a corporation's
exposed and open services. The DMZs goal is to deliver an additional coating of
safety to a company's LAN. A safe and supervised network junction that
manages externally the inner network can obtain access to the disclosed
pg. 10
operability of the firewall. This involves supervising records, executing scans, and
reviewing the regulations frequently.
1.2 Configuration of third-party VPNs
A virtual private network or VPN is a major tech that is applied to improve internet
safety and provide secure isolated access for operators who have to get approval
for organisational WANs and their assets. A VPN links every type of user around
the globe. Before configuring a VPN, network composers should assess the basic
principles of the VPN, and choose attributes that are favourable to their
companies' operators (Rahimi et al., 2012). VPNs provide a protocol coating,
often known as a tunnelling protocol that summarises and inscribes network
transmissions.
The company must possess a router compatible with the desired operations to be
executed. Then utilising the quick start wizard guide for setting up the VPN. This
guide provides the necessary instructions to complete the whole process. After
setting up the VPN, the firm has to select the configuration of security. It is better
to select a stronger security system to protect valuable information (Degefa,
2015). Then enabling the operators to use the facilities. To do so, they need to
create accounts for each operator desiring access to the VPN. The final job is to
connect the computers to the network for enjoying isolated access to necessary
files. A VPN functions in the binary digital system. So, either the transmission is
completed or it is not. If the connection is not established, the transmission of
malicious traffic will also be impossible. When the VPN connection is unable to
function, the client-side program will show an error notification conveying some
codes. There are numerous various types of VPN codes such as VPN 800, VPN
619, VPN 691, etc.
2. Implementation of network security DMZ, Static IP, and NAT
Do not type anything here!!!
2.1 Explanation of DMZ implementation
A DMZ network is utilised as a subordinate network that bears a corporation's
exposed and open services. The DMZs goal is to deliver an additional coating of
safety to a company's LAN. A safe and supervised network junction that
manages externally the inner network can obtain access to the disclosed
pg. 10

information in the DMZ, while the rest of the network is secured by a firewall (Dart
et al., 2013). A DMZ server is always situated on a distant part of the network.
Therefore, a distinct computer to act as a host is not necessary. The
implementation of the DMZ in the finance department requires three firewall
network interfaces. Each one of them has different purposes such as one for
managing networks, the next for the DMZ, and the final one for the inner network.
Every server that needs network connection from the external part, will be placed
in the DMZ network when the servers carrying precise data shall be protected
with the firewall (Murphy, 2013). It can turn into less resistance with the
transmission in the DMZ.
2.2 Configuration of static IP and NAT
A static IP is an IP address that cannot be altered. It is a perpetual digit
delivered to a computer by an Internet service vendor (Wan et al., 2011). In
terms of static IP, the computer connects to the internet by using the same IP
address over and over.
NAT has many utilisations, its main objective is to protect public Ipv4 addresses.
It operates by approving networks to utilise private Ipv4 addresses inside and
delivering transportation to a public address when required (Natali et al, 2016).
NAT has the additional advantage of increasing the level of privacy and safety in
a network due to its concealment of the inner Ipv4 addresses from the external
networks. Static NAT is a one-to-one banding between an internal and an
external address. Static NAT permits outer machines to start connections to inner
machines by utilising the statically allocated public address (Smith & Hunt, 2012).
There are two fundamental processes while establishing static NAT,
- The initial job is to produce a mapping between the internal local address and
the internal global address.
- The next job is to configure the interfaces that are taking part in the
transportation as internal or external relative to NAT.
3. Implementation of a network monitoring system
A network monitoring system supervises an inner network for difficulties. It can
determine and solve existing problems. Network monitoring systems are quite
dissimilar to intervention identification systems, it describes how well the
network is functioning (Sovoda et al., 2015). The main focus of the network
monitoring system is on ensuring the security of the network. Network
supervising can be done by utilising different software or a union of stopples
and play hardware and software device solutions. Any type of network can be
supervised artificially (Ranum et al., 2010). The type of network is not
considered in implementing the supervision of networks. The necessary
elements of a network monitoring system are event gathering and processing,
alteration of network and establishment management, supervising performance,
pg. 11
et al., 2013). A DMZ server is always situated on a distant part of the network.
Therefore, a distinct computer to act as a host is not necessary. The
implementation of the DMZ in the finance department requires three firewall
network interfaces. Each one of them has different purposes such as one for
managing networks, the next for the DMZ, and the final one for the inner network.
Every server that needs network connection from the external part, will be placed
in the DMZ network when the servers carrying precise data shall be protected
with the firewall (Murphy, 2013). It can turn into less resistance with the
transmission in the DMZ.
2.2 Configuration of static IP and NAT
A static IP is an IP address that cannot be altered. It is a perpetual digit
delivered to a computer by an Internet service vendor (Wan et al., 2011). In
terms of static IP, the computer connects to the internet by using the same IP
address over and over.
NAT has many utilisations, its main objective is to protect public Ipv4 addresses.
It operates by approving networks to utilise private Ipv4 addresses inside and
delivering transportation to a public address when required (Natali et al, 2016).
NAT has the additional advantage of increasing the level of privacy and safety in
a network due to its concealment of the inner Ipv4 addresses from the external
networks. Static NAT is a one-to-one banding between an internal and an
external address. Static NAT permits outer machines to start connections to inner
machines by utilising the statically allocated public address (Smith & Hunt, 2012).
There are two fundamental processes while establishing static NAT,
- The initial job is to produce a mapping between the internal local address and
the internal global address.
- The next job is to configure the interfaces that are taking part in the
transportation as internal or external relative to NAT.
3. Implementation of a network monitoring system
A network monitoring system supervises an inner network for difficulties. It can
determine and solve existing problems. Network monitoring systems are quite
dissimilar to intervention identification systems, it describes how well the
network is functioning (Sovoda et al., 2015). The main focus of the network
monitoring system is on ensuring the security of the network. Network
supervising can be done by utilising different software or a union of stopples
and play hardware and software device solutions. Any type of network can be
supervised artificially (Ranum et al., 2010). The type of network is not
considered in implementing the supervision of networks. The necessary
elements of a network monitoring system are event gathering and processing,
alteration of network and establishment management, supervising performance,
pg. 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.