Comprehensive Risk Assessment of Timesheet Reporting Tool Project
VerifiedAdded on 2023/06/04
|23
|3426
|272
Project
AI Summary
This document presents a comprehensive risk assessment for a Timesheet Reporting Tool project, outlining the project's scope, risk measurement strategies for both development and operational phases, and a detailed analysis of stakeholder involvement and risk perception. It addresses how to determine risk acceptance among different stakeholder groups and proposes a methodology, specifically the OCTAVE method, for conducting the risk assessment. The document also specifies the necessary project team specializations, data collection methods, and validation processes. Furthermore, it includes a stakeholder communication plan to ensure understanding and input into the risk management approach, concluding with a review and monitoring program to maintain ongoing risk oversight. The ultimate goal is to provide a structured and thorough approach to managing potential risks throughout the project lifecycle.

Running head: RISK ASSESSMENT OF PROJECT
RISK ASSESSMENT OF PROJECT
Name of the Student
Name of the University
Author note
RISK ASSESSMENT OF PROJECT
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
RISK ASSESSMENT OF PROJECT
Table of Contents
1. Scope of the project:.........................................................................................................................2
2. Risk measurement of the development and operational phase:.......................................................3
2.1. Development phase:...................................................................................................................3
2.2. Operational phase:.....................................................................................................................4
3. Project stakeholders:.........................................................................................................................5
3.1. Stakeholder involved in the project:...........................................................................................5
3.2. Perception of risk:.......................................................................................................................6
4. Determination of risk acceptance:...................................................................................................11
5. Proposed methodology to conduct the risk assessment:................................................................12
6. Project team involvement based on specializations/professions:...................................................14
7. Data collection method:..................................................................................................................15
8. Data validation:...............................................................................................................................19
9. Stakeholder communication plan:...................................................................................................19
10. Review and monitor program:.......................................................................................................20
Reference:...........................................................................................................................................22
RISK ASSESSMENT OF PROJECT
Table of Contents
1. Scope of the project:.........................................................................................................................2
2. Risk measurement of the development and operational phase:.......................................................3
2.1. Development phase:...................................................................................................................3
2.2. Operational phase:.....................................................................................................................4
3. Project stakeholders:.........................................................................................................................5
3.1. Stakeholder involved in the project:...........................................................................................5
3.2. Perception of risk:.......................................................................................................................6
4. Determination of risk acceptance:...................................................................................................11
5. Proposed methodology to conduct the risk assessment:................................................................12
6. Project team involvement based on specializations/professions:...................................................14
7. Data collection method:..................................................................................................................15
8. Data validation:...............................................................................................................................19
9. Stakeholder communication plan:...................................................................................................19
10. Review and monitor program:.......................................................................................................20
Reference:...........................................................................................................................................22
2
RISK ASSESSMENT OF PROJECT
1. Scope of the project:
Title Timesheet Reporting Tool Date September 23, 2018
Project
Manager
Andrew Jason
Project
Justification
The tool is intended to provide a web based application that is user
friendly and provide the automatic means to track time entries that the
employee makes on daily basis
Project Scope
Description
To provide the option to tack and review time entries globally for the
Information Technology employees
Project
Objective
To felicitate all the Information Technology employees with the tool that
help them in tracking the timesheet entries for
High Level
Requirements
1. User access for the tool granted to all employees
2. provide the Admin access for support team
3. facility to Report the generation access to the project managers
4. help the users to have remote access to the tool
5. provide Standard templates for every reports
In Scope
1. Multi – level approvals made available for the timesheets
2. additions of Timesheet tasks to the tool through Admin approved
access users
3. ‘Copy Previous Week’ timesheets feature
4. Access tool for Desktop
Out of Scope
1. addition of New project/task for the managers
2. HRMS connectivity for updating leaves taken by employee
3. and that too automatically
4. template providing task list based on role
5. facility of obtaining the Access tool via mobile and tablet
RISK ASSESSMENT OF PROJECT
1. Scope of the project:
Title Timesheet Reporting Tool Date September 23, 2018
Project
Manager
Andrew Jason
Project
Justification
The tool is intended to provide a web based application that is user
friendly and provide the automatic means to track time entries that the
employee makes on daily basis
Project Scope
Description
To provide the option to tack and review time entries globally for the
Information Technology employees
Project
Objective
To felicitate all the Information Technology employees with the tool that
help them in tracking the timesheet entries for
High Level
Requirements
1. User access for the tool granted to all employees
2. provide the Admin access for support team
3. facility to Report the generation access to the project managers
4. help the users to have remote access to the tool
5. provide Standard templates for every reports
In Scope
1. Multi – level approvals made available for the timesheets
2. additions of Timesheet tasks to the tool through Admin approved
access users
3. ‘Copy Previous Week’ timesheets feature
4. Access tool for Desktop
Out of Scope
1. addition of New project/task for the managers
2. HRMS connectivity for updating leaves taken by employee
3. and that too automatically
4. template providing task list based on role
5. facility of obtaining the Access tool via mobile and tablet
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
RISK ASSESSMENT OF PROJECT
Cost Estimate
Cost Item Estimated
Project Cost
Actual
Spend
Cost until
completio
n
Variance
Software $2300 $900 $1400 NA
Hardware $5000 $1500 $3500 +/- 1000
Other $750 $0 $750 +/- $100
Total $8050 $2400 $5650
Assumptions 1. users will update Timesheet on daily basis
2. task listed in the Timesheets will be updated twice a month
Deliverables
1. Single system to record time hours for FTE and Contractors
2. execution of the timesheet reports to for detecting entries that are not
present in the list
3. reports generation for the identification of the productive tasks along
with the work hours
4. charts generation for the steering committee packs
5. Detailed assistance for the user for updating tolls that belongs to all the
users
Constraints
1. no facility to capture the leave from the leave system that are not
planned
2. access for the timesheet view associated with the team is only available
to the Direct managers
2. Risk measurement of the development and operational phase:
In order to measure risk there should be proper framework and this varies according
to the scope and requirement of the project (Cleary, Horsfall and Hayter 2014).
2.1. Development phase:
Risk considered Impact of risk
Time frame High
RISK ASSESSMENT OF PROJECT
Cost Estimate
Cost Item Estimated
Project Cost
Actual
Spend
Cost until
completio
n
Variance
Software $2300 $900 $1400 NA
Hardware $5000 $1500 $3500 +/- 1000
Other $750 $0 $750 +/- $100
Total $8050 $2400 $5650
Assumptions 1. users will update Timesheet on daily basis
2. task listed in the Timesheets will be updated twice a month
Deliverables
1. Single system to record time hours for FTE and Contractors
2. execution of the timesheet reports to for detecting entries that are not
present in the list
3. reports generation for the identification of the productive tasks along
with the work hours
4. charts generation for the steering committee packs
5. Detailed assistance for the user for updating tolls that belongs to all the
users
Constraints
1. no facility to capture the leave from the leave system that are not
planned
2. access for the timesheet view associated with the team is only available
to the Direct managers
2. Risk measurement of the development and operational phase:
In order to measure risk there should be proper framework and this varies according
to the scope and requirement of the project (Cleary, Horsfall and Hayter 2014).
2.1. Development phase:
Risk considered Impact of risk
Time frame High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
RISK ASSESSMENT OF PROJECT
exceeds than the
estimated time
significantly
Cost exceeds
significantly
High
Requirement of the
system is not clear
to the developer
High
Code does not
integrate well with
the system
High
2.2. Operational phase:
System crashes and
the performance is
bellow acceptance
High
Security of the
system is not top
notch
High
The interface of the
system is not
attractive and
simple
Medium
System take more medium
RISK ASSESSMENT OF PROJECT
exceeds than the
estimated time
significantly
Cost exceeds
significantly
High
Requirement of the
system is not clear
to the developer
High
Code does not
integrate well with
the system
High
2.2. Operational phase:
System crashes and
the performance is
bellow acceptance
High
Security of the
system is not top
notch
High
The interface of the
system is not
attractive and
simple
Medium
System take more medium
5
RISK ASSESSMENT OF PROJECT
time to store and
process data
3. Project stakeholders:
The study of how each stakeholder involved in the project will perceive the risk is an
important factor, as without the study of stakeholder risk perception, it is not possible to
manage the project successfully as stakeholder engagement and stakeholder satisfaction one
of the key elements for project success. This is where analysis of stakeholder risk perception
becomes significantly important as without integrating each stakeholder perception about the
project risk, the overall risk of the project is not possible to identify and have proper control
over that. In the following section, the stakeholder for the project has been identified with
detailed risk perception of each of the stakeholder.
3.1. Stakeholder involved in the project:
Stakeholder Role
Project manager Monitor and control overall progress of the
project with control over the cost, timeline
approval and review on the project progress
Employee Only access to the feature approved by the
admin of the Timesheet Reporting Tool
Admin
Monitor and approve the user access to the
Timesheet Reporting Tool, hence responsible for
overall system security and performance
Developer Develop the code for the software
RISK ASSESSMENT OF PROJECT
time to store and
process data
3. Project stakeholders:
The study of how each stakeholder involved in the project will perceive the risk is an
important factor, as without the study of stakeholder risk perception, it is not possible to
manage the project successfully as stakeholder engagement and stakeholder satisfaction one
of the key elements for project success. This is where analysis of stakeholder risk perception
becomes significantly important as without integrating each stakeholder perception about the
project risk, the overall risk of the project is not possible to identify and have proper control
over that. In the following section, the stakeholder for the project has been identified with
detailed risk perception of each of the stakeholder.
3.1. Stakeholder involved in the project:
Stakeholder Role
Project manager Monitor and control overall progress of the
project with control over the cost, timeline
approval and review on the project progress
Employee Only access to the feature approved by the
admin of the Timesheet Reporting Tool
Admin
Monitor and approve the user access to the
Timesheet Reporting Tool, hence responsible for
overall system security and performance
Developer Develop the code for the software
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
RISK ASSESSMENT OF PROJECT
Tester Review the code designed by the developer to
make the code integrated with the system and
platform
User interface design Design the interface for the software. The
interface is something through which the user
the
3.2. Perception of risk:
3.2.1. For the project manager
Once the stakeholder and the responsibility is defined it will help to define the risk
perception of the stakeholders. Only the project manager will have same view and risk
perception for the all the risk parameters described below as the project manager is
responsible for each and every aspect of the project progress and the associated risk (Brace
2018).
Project
manager
Risk considered Perceive of risk
Time frame
exceeds than
the estimated
time
significantly
High
Cost exceeds
significantly
High
Requirement of
the system is
High
RISK ASSESSMENT OF PROJECT
Tester Review the code designed by the developer to
make the code integrated with the system and
platform
User interface design Design the interface for the software. The
interface is something through which the user
the
3.2. Perception of risk:
3.2.1. For the project manager
Once the stakeholder and the responsibility is defined it will help to define the risk
perception of the stakeholders. Only the project manager will have same view and risk
perception for the all the risk parameters described below as the project manager is
responsible for each and every aspect of the project progress and the associated risk (Brace
2018).
Project
manager
Risk considered Perceive of risk
Time frame
exceeds than
the estimated
time
significantly
High
Cost exceeds
significantly
High
Requirement of
the system is
High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
RISK ASSESSMENT OF PROJECT
not clear to the
developer
Code does not
integrate well
with the system
High
System crashes
and the
performance is
bellow
acceptance
High
Security of the
system is not
top notch
High
The interface of
the system is
not attractive
and simple
High
System take
more time to
store and
process data
High
RISK ASSESSMENT OF PROJECT
not clear to the
developer
Code does not
integrate well
with the system
High
System crashes
and the
performance is
bellow
acceptance
High
Security of the
system is not
top notch
High
The interface of
the system is
not attractive
and simple
High
System take
more time to
store and
process data
High
8
RISK ASSESSMENT OF PROJECT
3.2.2. Other stakeholder:
Apart from the project manger the other stakeholders will have different viewpoint on
the risks considered and they will perceive different risk aspect as high and low.
Stakeholder Risk(high ) Risk(low)
Employee None Time frame exceeds than
the estimated time
significantly
Cost exceeds significantly
Requirement of the system
is not clear to the developer
Code does not integrate well
with the system
System crashes and the
performance is bellow
acceptance
Security of the system is not
top notch
The interface of the system
is not attractive and simple
System take more time to
store and process data
Admin
Security of the system is not
top notch
Time frame exceeds than
the estimated time
significantly
Cost exceeds significantly
Requirement of the system
RISK ASSESSMENT OF PROJECT
3.2.2. Other stakeholder:
Apart from the project manger the other stakeholders will have different viewpoint on
the risks considered and they will perceive different risk aspect as high and low.
Stakeholder Risk(high ) Risk(low)
Employee None Time frame exceeds than
the estimated time
significantly
Cost exceeds significantly
Requirement of the system
is not clear to the developer
Code does not integrate well
with the system
System crashes and the
performance is bellow
acceptance
Security of the system is not
top notch
The interface of the system
is not attractive and simple
System take more time to
store and process data
Admin
Security of the system is not
top notch
Time frame exceeds than
the estimated time
significantly
Cost exceeds significantly
Requirement of the system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
RISK ASSESSMENT OF PROJECT
is not clear to the developer
Code does not integrate well
with the system
System crashes and the
performance is bellow
acceptance
Security of the system is not
top notch
The interface of the system
is not attractive and simple
System take more time to
store and process data
Developer Time frame exceeds than
the estimated time
significantly
Requirement of the system
is not clear to the developer
Code does not integrate well
with the system
System crashes and the
performance is bellow
The interface of the system
is not attractive and simple
System take more time to
store and process data
RISK ASSESSMENT OF PROJECT
is not clear to the developer
Code does not integrate well
with the system
System crashes and the
performance is bellow
acceptance
Security of the system is not
top notch
The interface of the system
is not attractive and simple
System take more time to
store and process data
Developer Time frame exceeds than
the estimated time
significantly
Requirement of the system
is not clear to the developer
Code does not integrate well
with the system
System crashes and the
performance is bellow
The interface of the system
is not attractive and simple
System take more time to
store and process data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
RISK ASSESSMENT OF PROJECT
acceptance
Security of the system is not
top notch
Tester Code does not integrate well
with the system
System crashes and the
performance is bellow
acceptance
Time frame exceeds than
the estimated time
significantly
Cost exceeds significantly
Requirement of the system
is not clear to the developer
Security of the system is not
top notch
The interface of the system
is not attractive and simple
System take more time to
store and process data
User interface design The interface of the system Time frame exceeds than
RISK ASSESSMENT OF PROJECT
acceptance
Security of the system is not
top notch
Tester Code does not integrate well
with the system
System crashes and the
performance is bellow
acceptance
Time frame exceeds than
the estimated time
significantly
Cost exceeds significantly
Requirement of the system
is not clear to the developer
Security of the system is not
top notch
The interface of the system
is not attractive and simple
System take more time to
store and process data
User interface design The interface of the system Time frame exceeds than
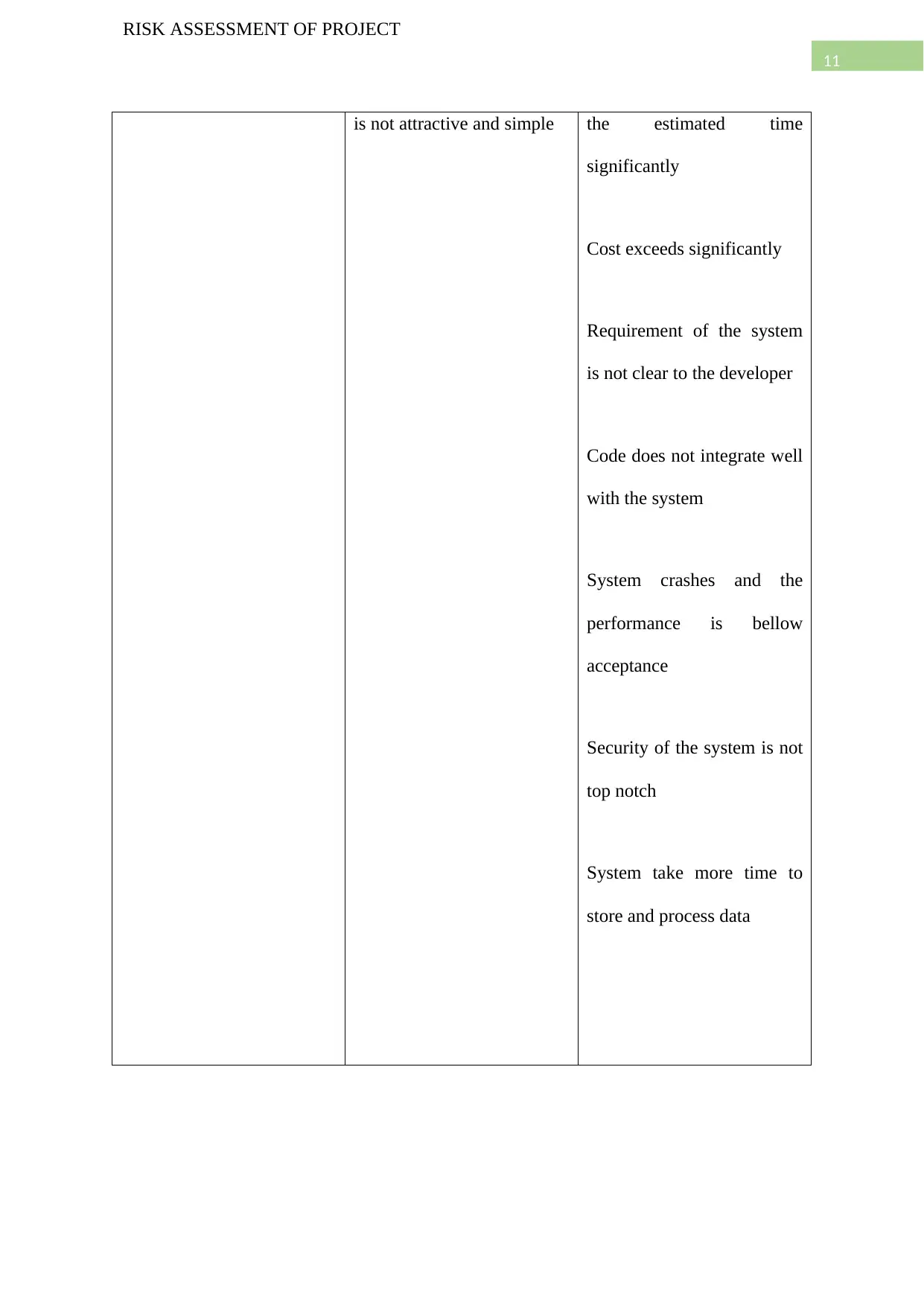
11
RISK ASSESSMENT OF PROJECT
is not attractive and simple the estimated time
significantly
Cost exceeds significantly
Requirement of the system
is not clear to the developer
Code does not integrate well
with the system
System crashes and the
performance is bellow
acceptance
Security of the system is not
top notch
System take more time to
store and process data
RISK ASSESSMENT OF PROJECT
is not attractive and simple the estimated time
significantly
Cost exceeds significantly
Requirement of the system
is not clear to the developer
Code does not integrate well
with the system
System crashes and the
performance is bellow
acceptance
Security of the system is not
top notch
System take more time to
store and process data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



