Risk Management Plan: Inventory System for ABS Leather Manufacturing
VerifiedAdded on 2023/04/21
|32
|5522
|454
Report
AI Summary
This report presents a comprehensive risk management plan developed for the ABS Private Limited, a leather manufacturing industry located in Queensland, Australia, facing challenges in managing its livestock and inventory. The primary objective is to establish an effective inventory management system to minimize wastage and achieve sustainability. The report details the risk management process, communication and consultation strategies, including stakeholder analysis, and the establishment of internal and external contexts. It outlines the risk assessment process, including identification, analysis, and evaluation, culminating in the development of a risk register. The report also covers risk treatment options, monitoring, and review processes, referencing Australian risk management standards AS/NZS ISO 31000 and ISO 31010. The executive summary, introduction, communication plan, context establishment, risk assessment, treatment, and monitoring are all detailed. The report also includes appendices such as the risk register to provide a detailed overview of the project.

Risk Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
The ABS Private limited is the leather manufacturing industry which is facing problem in
managing the livestock. The organization is located in Queensland, Australia. The purpose of
this project is to develop an effective inventory management system for the industry. The
major objective of the project is to achieve sustainability in managing the leather inventory so
that wastage can be minimized. The communication between the internal and external parties
helps in identifying the gaps and problems which exists with the management of leather
inventory. The coordination and cooperation among the stakeholders helps in retrieving the
success of the project. The assessment of the risks at an early stage of the project helps in
developing the risks treatment and mitigation structure so that valuable infrastructure for
handling inventory can be developed. The risk register is prepared for managing the risks
effectively by analysing the risk impact and severity on the business operation for managing
the inventory control policies and program. The focus should be given on calculating the
risks ranking by adding the estimated values of risks severity and risks likelihood. The risk
monitoring and reviewing are the core processes of the risks management program. It helps in
developing the secured project. It helps in minimizing the conflict and area of concern of the
inventory management system.
The ABS Private limited is the leather manufacturing industry which is facing problem in
managing the livestock. The organization is located in Queensland, Australia. The purpose of
this project is to develop an effective inventory management system for the industry. The
major objective of the project is to achieve sustainability in managing the leather inventory so
that wastage can be minimized. The communication between the internal and external parties
helps in identifying the gaps and problems which exists with the management of leather
inventory. The coordination and cooperation among the stakeholders helps in retrieving the
success of the project. The assessment of the risks at an early stage of the project helps in
developing the risks treatment and mitigation structure so that valuable infrastructure for
handling inventory can be developed. The risk register is prepared for managing the risks
effectively by analysing the risk impact and severity on the business operation for managing
the inventory control policies and program. The focus should be given on calculating the
risks ranking by adding the estimated values of risks severity and risks likelihood. The risk
monitoring and reviewing are the core processes of the risks management program. It helps in
developing the secured project. It helps in minimizing the conflict and area of concern of the
inventory management system.

Contents
Executive Summary...................................................................................................................1
1 Introduction.........................................................................................................................4
Project information.................................................................................................................4
Project Scope..........................................................................................................................4
Project Objectives...................................................................................................................5
Risk management process......................................................................................................6
2 Communication and Consultation plan...............................................................................7
Main objectives......................................................................................................................7
Stakeholder analysis...............................................................................................................8
3 Establishing Context.........................................................................................................11
Internal context.....................................................................................................................12
External Context...................................................................................................................12
Organization Context............................................................................................................12
Risk management context.....................................................................................................12
Risk criteria..........................................................................................................................13
Stakeholders.........................................................................................................................13
Role and Responsibilities.....................................................................................................13
Risk management policy......................................................................................................15
4 Risk Assessment process..................................................................................................15
Risk identification................................................................................................................15
Identification method........................................................................................................16
Risk scope.........................................................................................................................16
Risk Register.....................................................................................................................16
Risk Analysis........................................................................................................................19
Analysis method...............................................................................................................20
Executive Summary...................................................................................................................1
1 Introduction.........................................................................................................................4
Project information.................................................................................................................4
Project Scope..........................................................................................................................4
Project Objectives...................................................................................................................5
Risk management process......................................................................................................6
2 Communication and Consultation plan...............................................................................7
Main objectives......................................................................................................................7
Stakeholder analysis...............................................................................................................8
3 Establishing Context.........................................................................................................11
Internal context.....................................................................................................................12
External Context...................................................................................................................12
Organization Context............................................................................................................12
Risk management context.....................................................................................................12
Risk criteria..........................................................................................................................13
Stakeholders.........................................................................................................................13
Role and Responsibilities.....................................................................................................13
Risk management policy......................................................................................................15
4 Risk Assessment process..................................................................................................15
Risk identification................................................................................................................15
Identification method........................................................................................................16
Risk scope.........................................................................................................................16
Risk Register.....................................................................................................................16
Risk Analysis........................................................................................................................19
Analysis method...............................................................................................................20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Existing risk controls........................................................................................................20
Risk acceptance criteria....................................................................................................20
Risk Evaluation....................................................................................................................21
Evaluation method............................................................................................................22
Key risks for treatment.....................................................................................................22
5 Risk Treatment..................................................................................................................23
Probable Treatment options..................................................................................................23
Effective treatment option....................................................................................................24
6 Risk monitoring and review..............................................................................................24
Process..................................................................................................................................24
Risk Closure.........................................................................................................................25
7 References:........................................................................................................................25
8 Appendix 1: Risk Register................................................................................................27
Risk acceptance criteria....................................................................................................20
Risk Evaluation....................................................................................................................21
Evaluation method............................................................................................................22
Key risks for treatment.....................................................................................................22
5 Risk Treatment..................................................................................................................23
Probable Treatment options..................................................................................................23
Effective treatment option....................................................................................................24
6 Risk monitoring and review..............................................................................................24
Process..................................................................................................................................24
Risk Closure.........................................................................................................................25
7 References:........................................................................................................................25
8 Appendix 1: Risk Register................................................................................................27
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 Introduction
The project can be successfully completed by identified the risks and associated action plan
to resolve the complexity during the project initialization. The risk management plan is the
key process for achieving the organization goal and objectives within specified time and cost.
The scope of the project should concentrate on identifying the potential risks and its impact
associated with the business core processes and operational plan. The research paper is design
by following Australian risk management standard AS/NZS ISO 31000 and ISO 31010 to
develop and implement a proactive risk management process in undertaken engineering
project.
Project information
The ABS Private limited is the leather manufacturing industry which is facing problem in
managing the livestock. The organization is located in Queensland, Australia. The purpose of
this project is to develop an effective inventory management system for the industry. The
systematic approach of handling the livestock and inventory is not handled which creates the
operational functionality and results in delivering the production of poor quality of leather.
The existing staff members are not having relevant skills to work on the new technology for
fostering the production of good quality leather products. The industry space is not properly
utilized for managing the inventory. The policies and strategies of the enterprise is not
properly constructed which creates a problematic situation in working culture of the
environment.
Project Scope
The scope of the undertaken project is to design an inventory management system for the
ABS leather industry. The approved project budget is $ 675000 and has to be completed
within the timeframe of 6 months. The scope management plan for the project is defined in
the table below:
In-scope activities
Identifying the problem domain of the existing architecture of the organization
Organizing meeting with top executives and employees to analyse their requirement
Designing of requirement plan
Determining alternative solutions
Selection of the alternative
The project can be successfully completed by identified the risks and associated action plan
to resolve the complexity during the project initialization. The risk management plan is the
key process for achieving the organization goal and objectives within specified time and cost.
The scope of the project should concentrate on identifying the potential risks and its impact
associated with the business core processes and operational plan. The research paper is design
by following Australian risk management standard AS/NZS ISO 31000 and ISO 31010 to
develop and implement a proactive risk management process in undertaken engineering
project.
Project information
The ABS Private limited is the leather manufacturing industry which is facing problem in
managing the livestock. The organization is located in Queensland, Australia. The purpose of
this project is to develop an effective inventory management system for the industry. The
systematic approach of handling the livestock and inventory is not handled which creates the
operational functionality and results in delivering the production of poor quality of leather.
The existing staff members are not having relevant skills to work on the new technology for
fostering the production of good quality leather products. The industry space is not properly
utilized for managing the inventory. The policies and strategies of the enterprise is not
properly constructed which creates a problematic situation in working culture of the
environment.
Project Scope
The scope of the undertaken project is to design an inventory management system for the
ABS leather industry. The approved project budget is $ 675000 and has to be completed
within the timeframe of 6 months. The scope management plan for the project is defined in
the table below:
In-scope activities
Identifying the problem domain of the existing architecture of the organization
Organizing meeting with top executives and employees to analyse their requirement
Designing of requirement plan
Determining alternative solutions
Selection of the alternative

Project charter and proposal
Defining hardware and software requirement
Defining networking plan
Analysing resources required
Designing of inventory management system
Identifying risks
Risks assessment and evaluation
Risk Treatment process
Communication management system
Designing of stakeholder register
Implementation of inventory management system
Testing and monitoring of the new system
Out-of-scope activities
Monitoring program
Maintenance program
Training and development program organized for staff members
Hiring of new staff
Service level agreement
Assumption
Having skilled and expertise staff
Having required funds
Managing supply of hardware and software required
Success Criteria
Fulfilling requirement plan
Within time limit project gets complete
Within Expected cost project gets complete
Project Objectives
The major objective of the project is to achieve sustainability in managing the leather
inventory so that wastage can be minimized. The objectives of the project are as follows
Identifying the problem domain of the existing working environment of the
organization
Designing of communication management plan
Defining hardware and software requirement
Defining networking plan
Analysing resources required
Designing of inventory management system
Identifying risks
Risks assessment and evaluation
Risk Treatment process
Communication management system
Designing of stakeholder register
Implementation of inventory management system
Testing and monitoring of the new system
Out-of-scope activities
Monitoring program
Maintenance program
Training and development program organized for staff members
Hiring of new staff
Service level agreement
Assumption
Having skilled and expertise staff
Having required funds
Managing supply of hardware and software required
Success Criteria
Fulfilling requirement plan
Within time limit project gets complete
Within Expected cost project gets complete
Project Objectives
The major objective of the project is to achieve sustainability in managing the leather
inventory so that wastage can be minimized. The objectives of the project are as follows
Identifying the problem domain of the existing working environment of the
organization
Designing of communication management plan
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Designing of Stakeholder register
Identifying risks
Risks Criteria
Stakeholder register
Division of responsibilities and required authorities
Development of risks management policies
Development of risks control
Risks Analysis
Risk Acceptance criteria
Designing of Risk Treatment process
Risk management process
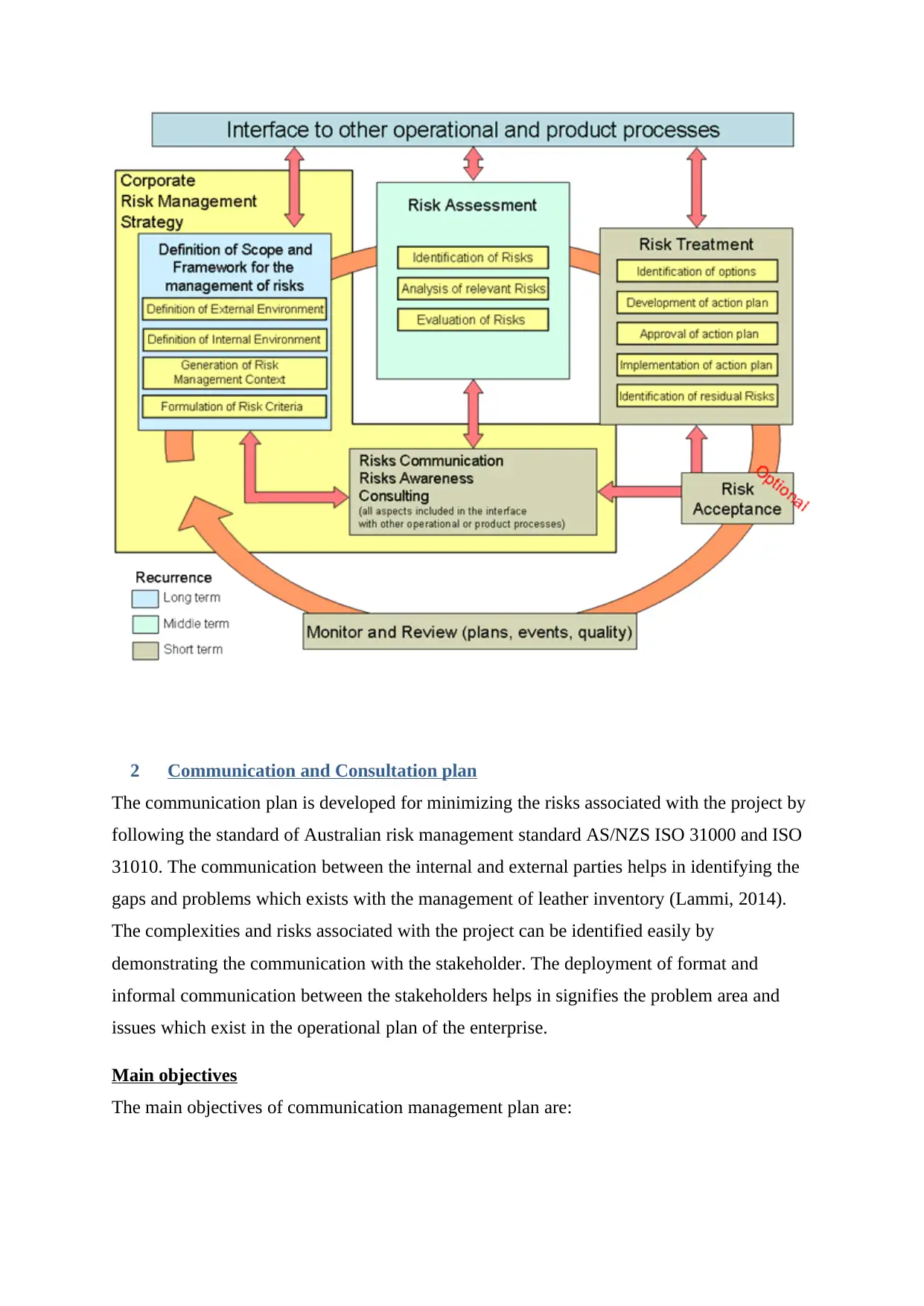
The risks management process is designed for identifying the risks and setting priority to it so
that desired mitigation policies can be developed. The project risks are identified according to
the project charter plan. The internal and external environment of the business units are
interlinked so that risks can be clearly visualized (Kang, 2010). The diagram below shows the
risks management process which is comprised of five processes which are classified as risks
identification, risk assessment, risk treatment, risks communication, risk acceptance, and
monitoring and reviewing according to the Australian risk management standard AS/NZS
ISO 31000 and ISO 31010.
Identifying risks
Risks Criteria
Stakeholder register
Division of responsibilities and required authorities
Development of risks management policies
Development of risks control
Risks Analysis
Risk Acceptance criteria
Designing of Risk Treatment process
Risk management process
The risks management process is designed for identifying the risks and setting priority to it so
that desired mitigation policies can be developed. The project risks are identified according to
the project charter plan. The internal and external environment of the business units are
interlinked so that risks can be clearly visualized (Kang, 2010). The diagram below shows the
risks management process which is comprised of five processes which are classified as risks
identification, risk assessment, risk treatment, risks communication, risk acceptance, and
monitoring and reviewing according to the Australian risk management standard AS/NZS
ISO 31000 and ISO 31010.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2 Communication and Consultation plan
The communication plan is developed for minimizing the risks associated with the project by
following the standard of Australian risk management standard AS/NZS ISO 31000 and ISO
31010. The communication between the internal and external parties helps in identifying the
gaps and problems which exists with the management of leather inventory (Lammi, 2014).
The complexities and risks associated with the project can be identified easily by
demonstrating the communication with the stakeholder. The deployment of format and
informal communication between the stakeholders helps in signifies the problem area and
issues which exist in the operational plan of the enterprise.
Main objectives
The main objectives of communication management plan are:
The communication plan is developed for minimizing the risks associated with the project by
following the standard of Australian risk management standard AS/NZS ISO 31000 and ISO
31010. The communication between the internal and external parties helps in identifying the
gaps and problems which exists with the management of leather inventory (Lammi, 2014).
The complexities and risks associated with the project can be identified easily by
demonstrating the communication with the stakeholder. The deployment of format and
informal communication between the stakeholders helps in signifies the problem area and
issues which exist in the operational plan of the enterprise.
Main objectives
The main objectives of communication management plan are:
Identifying risks and complexities associated with the undertaken project of inventory
system
Analysing the impact of risks on the current working infrastructure of the organization
Prioritizing risks
Developing risk register
Identifying status report of the project
Risk evaluation and analysis
Preparing risks management plan
Preparing risks control policies and strategies
Designing risks mitigation and treatment plan
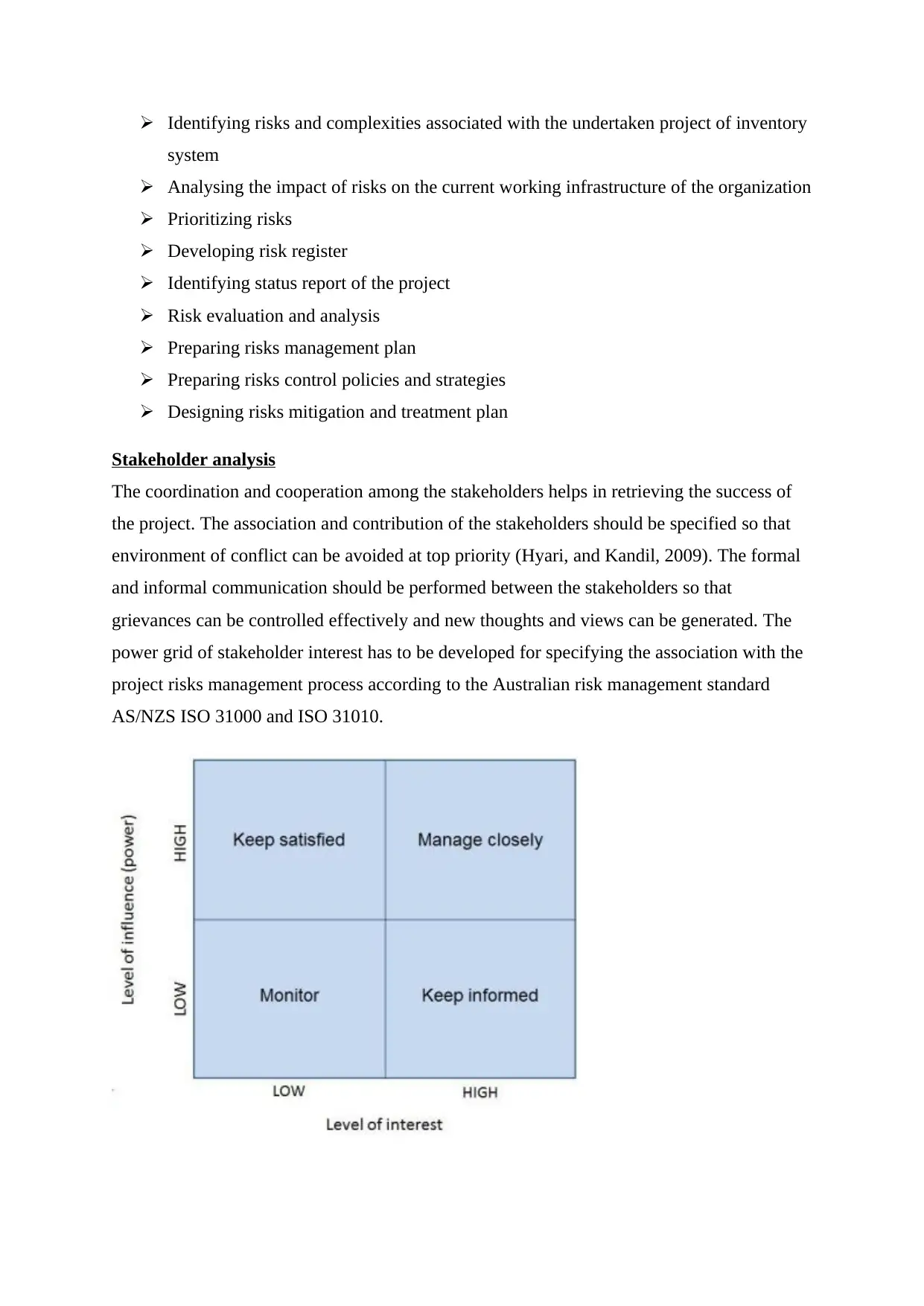
Stakeholder analysis
The coordination and cooperation among the stakeholders helps in retrieving the success of
the project. The association and contribution of the stakeholders should be specified so that
environment of conflict can be avoided at top priority (Hyari, and Kandil, 2009). The formal
and informal communication should be performed between the stakeholders so that
grievances can be controlled effectively and new thoughts and views can be generated. The
power grid of stakeholder interest has to be developed for specifying the association with the
project risks management process according to the Australian risk management standard
AS/NZS ISO 31000 and ISO 31010.
system
Analysing the impact of risks on the current working infrastructure of the organization
Prioritizing risks
Developing risk register
Identifying status report of the project
Risk evaluation and analysis
Preparing risks management plan
Preparing risks control policies and strategies
Designing risks mitigation and treatment plan
Stakeholder analysis
The coordination and cooperation among the stakeholders helps in retrieving the success of
the project. The association and contribution of the stakeholders should be specified so that
environment of conflict can be avoided at top priority (Hyari, and Kandil, 2009). The formal
and informal communication should be performed between the stakeholders so that
grievances can be controlled effectively and new thoughts and views can be generated. The
power grid of stakeholder interest has to be developed for specifying the association with the
project risks management process according to the Australian risk management standard
AS/NZS ISO 31000 and ISO 31010.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Communication Method:
Power interest Region Communication Methods
Manage Closely The communication between the internal and
external parties by deploying various
communication tools for exchanging on-time
information such as Emails, Video calling,
Teleconferencing, Audio calling, Face to face
interaction, Interview, Newsletter, Social
Media, Notices, and Circulars
Keep satisfied Face to face interaction for collecting
relevant reports from the sub-ordinates with
respect to the project status report, financial
status report, and others
Keep informed Formal letters and emails are drafted for
sending information to the internal and
external stakeholders
Monitor The awareness program is arranged for the
stakeholders according to the requirement of
the project
3 Establishing Context
The Australian risk management standard AS/NZS ISO 31000 and ISO 31010 is used for
identifying the internal context, external context, organization context, risk criteria,
stakeholders, and risks management plan. The risk management policies can be effectively
designed by identifying the internal and external context of the ABS leather industry. The
risks criteria and parameters of risks avoidance can be judged by analysing the internal and
external situation of the enterprise.
Internal context
The ABS leather industry was developed in the year 2000 for supplying the good quality
leather in whole of Australia. The head office of the organization was located in Queensland,
Australia. The organization is having 2000 employees for keeping the plan operational. High
Power interest Region Communication Methods
Manage Closely The communication between the internal and
external parties by deploying various
communication tools for exchanging on-time
information such as Emails, Video calling,
Teleconferencing, Audio calling, Face to face
interaction, Interview, Newsletter, Social
Media, Notices, and Circulars
Keep satisfied Face to face interaction for collecting
relevant reports from the sub-ordinates with
respect to the project status report, financial
status report, and others
Keep informed Formal letters and emails are drafted for
sending information to the internal and
external stakeholders
Monitor The awareness program is arranged for the
stakeholders according to the requirement of
the project
3 Establishing Context
The Australian risk management standard AS/NZS ISO 31000 and ISO 31010 is used for
identifying the internal context, external context, organization context, risk criteria,
stakeholders, and risks management plan. The risk management policies can be effectively
designed by identifying the internal and external context of the ABS leather industry. The
risks criteria and parameters of risks avoidance can be judged by analysing the internal and
external situation of the enterprise.
Internal context
The ABS leather industry was developed in the year 2000 for supplying the good quality
leather in whole of Australia. The head office of the organization was located in Queensland,
Australia. The organization is having 2000 employees for keeping the plan operational. High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

standard of accuracy and transparency is maintained in the reporting system of the
organization so that chaotic environment can be avoided and business operational plan can be
smoothly completed within the dedicated exposure of time. The ABS organization is looking
forward to increase their turnover and profitability up to 30% of their current profit.
External Context
The ABS is the fastest growing company and had establishes its branch offices at five sites of
Australia which are named as Sydney, New South Wales, Queensland, Brisbane, and Darwin.
The organization is facing problem in managing transfer of inventory status report between
the different branch office and head office. The inventory available in the industry is not
effectively circulated which results in the poor quality of leather generation (Kharaiweish,
2013). The reputation of the company gets negatively affected.
Organization Context
The systematic approach of handling the livestock and inventory is not handled which creates
the operational functionality and results in delivering the production of poor quality of
leather. The existing staff members are not having relevant skills to work on the new
technology for fostering the production of good quality leather products. The industry space
is not properly utilized for managing the inventory. The policies and strategies of the
enterprise is not properly constructed which creates a problematic situation in working
culture of the environment (Monnappa, 2017). The organization is looking forward to
develop an effective inventory management system for the industry. The project risks are
identified according to the project charter plan. The internal and external environment of the
business units are interlinked so that risks can be clearly visualized.
Risk management context
The Australian risk management standard AS/NZS ISO 31000 and ISO 31010 is used for
identifying risks and develop associated proactive action plan. The issues and challenges of
the enterprise should be searched and analysed so that risks can be identified effectively
(LLveskoski, 2014). The assessment of the risks at an early stage of the project helps in
developing the risks treatment and mitigation structure so that valuable infrastructure for
handling inventory can be developed.
organization so that chaotic environment can be avoided and business operational plan can be
smoothly completed within the dedicated exposure of time. The ABS organization is looking
forward to increase their turnover and profitability up to 30% of their current profit.
External Context
The ABS is the fastest growing company and had establishes its branch offices at five sites of
Australia which are named as Sydney, New South Wales, Queensland, Brisbane, and Darwin.
The organization is facing problem in managing transfer of inventory status report between
the different branch office and head office. The inventory available in the industry is not
effectively circulated which results in the poor quality of leather generation (Kharaiweish,
2013). The reputation of the company gets negatively affected.
Organization Context
The systematic approach of handling the livestock and inventory is not handled which creates
the operational functionality and results in delivering the production of poor quality of
leather. The existing staff members are not having relevant skills to work on the new
technology for fostering the production of good quality leather products. The industry space
is not properly utilized for managing the inventory. The policies and strategies of the
enterprise is not properly constructed which creates a problematic situation in working
culture of the environment (Monnappa, 2017). The organization is looking forward to
develop an effective inventory management system for the industry. The project risks are
identified according to the project charter plan. The internal and external environment of the
business units are interlinked so that risks can be clearly visualized.
Risk management context
The Australian risk management standard AS/NZS ISO 31000 and ISO 31010 is used for
identifying risks and develop associated proactive action plan. The issues and challenges of
the enterprise should be searched and analysed so that risks can be identified effectively
(LLveskoski, 2014). The assessment of the risks at an early stage of the project helps in
developing the risks treatment and mitigation structure so that valuable infrastructure for
handling inventory can be developed.

Risk criteria
The criteria of the risks are limited to the following:
Definition of In-scope activities
Risks Management
Estimation and Scheduling of time
Analysis of risks
Budget and cost estimation
Sequencing of project activities
Developing monitoring program
Identifying team leadership
Stakeholders
Stakeholder Type of Stakeholder
Project Owner Internal
Project Sponsor External
Project Manager Internal
Risk Manager Internal
IT engineer Internal
Software Designer Internal
Accountant Internal
Planning Manager Internal
Consultant External
Role and Responsibilities
The division of role and responsibilities helps in minimizing the chaotic working
environment within the organization. The table below shows the division of role and
responsibilities of the staff members. The stakeholders which are associated with the
undertake project are categorised as project owner, project sponsor, project manager, IT
engineer, Software designer, risk manager, planning manager, accountant, and consultant.
The project can be successfully completed by managing strong communication links between
the internal and external stakeholders.
Role Responsibilities
Project Owner Designing of the Requirement plan
The criteria of the risks are limited to the following:
Definition of In-scope activities
Risks Management
Estimation and Scheduling of time
Analysis of risks
Budget and cost estimation
Sequencing of project activities
Developing monitoring program
Identifying team leadership
Stakeholders
Stakeholder Type of Stakeholder
Project Owner Internal
Project Sponsor External
Project Manager Internal
Risk Manager Internal
IT engineer Internal
Software Designer Internal
Accountant Internal
Planning Manager Internal
Consultant External
Role and Responsibilities
The division of role and responsibilities helps in minimizing the chaotic working
environment within the organization. The table below shows the division of role and
responsibilities of the staff members. The stakeholders which are associated with the
undertake project are categorised as project owner, project sponsor, project manager, IT
engineer, Software designer, risk manager, planning manager, accountant, and consultant.
The project can be successfully completed by managing strong communication links between
the internal and external stakeholders.
Role Responsibilities
Project Owner Designing of the Requirement plan
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 32
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





