Risk Management: ENISA Case Study, Threats, and Mitigation Strategies
VerifiedAdded on 2019/10/30
|16
|3811
|262
Report
AI Summary
This report presents a detailed analysis of the ENISA case study, focusing on risk management within a big data environment. It begins with an overview of the case study and a diagram of ENISA's big data security infrastructure. The report identifies and discusses significant threats, including unintentional or accidental threats, hijacking, abuse, legal threats, and organizational threats, with a particular emphasis on deliberate threats like malicious code. Key threat agents, such as employees, corporations, and script kiddies, are examined, along with strategies for minimizing their impact. The report also touches upon ETL process improvements and the overall IT security of ENISA. The conclusion reiterates the importance of risk assessment and mitigation techniques for effective operations. The report highlights the application of cryptographic techniques as a primary risk mitigation strategy, while acknowledging the need for continuous improvement in data security practices. The case study underscores the importance of a well-structured framework to ensure safe operations within the organization.

Running head: RISK MANAGEMENT: ENISA CASE STUDY
Risk Management: ENISA Case Study
Name of the Student
Name of the University
Author’s note
Risk Management: ENISA Case Study
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
RISK MANAGEMENT: ENISA CASE STUDY
Table of Contents
Introduction......................................................................................................................................2
1. Brief overview of the case study and diagram of ENISA big data security infrastructure.........2
1.1 Brief overview of the case study...........................................................................................2
1.2 Big data infrastructure diagram for ENISA...........................................................................4
2. Significant threats among the top threats.....................................................................................5
3. Identification and discussion on key threats agents and ways for minimizing their impact on
the system......................................................................................................................................10
3.1 Discussion of key threat agents...........................................................................................10
3.2Impact minimization.............................................................................................................11
3.3 Trend of Threat Probability.................................................................................................12
4. ETL Process Improvement........................................................................................................12
5. IT Security of ENISA...............................................................................................................12
Conclusion.....................................................................................................................................13
References......................................................................................................................................14
RISK MANAGEMENT: ENISA CASE STUDY
Table of Contents
Introduction......................................................................................................................................2
1. Brief overview of the case study and diagram of ENISA big data security infrastructure.........2
1.1 Brief overview of the case study...........................................................................................2
1.2 Big data infrastructure diagram for ENISA...........................................................................4
2. Significant threats among the top threats.....................................................................................5
3. Identification and discussion on key threats agents and ways for minimizing their impact on
the system......................................................................................................................................10
3.1 Discussion of key threat agents...........................................................................................10
3.2Impact minimization.............................................................................................................11
3.3 Trend of Threat Probability.................................................................................................12
4. ETL Process Improvement........................................................................................................12
5. IT Security of ENISA...............................................................................................................12
Conclusion.....................................................................................................................................13
References......................................................................................................................................14

2
RISK MANAGEMENT: ENISA CASE STUDY
Introduction
In this era of technology, risk analysis has become an essential factor for every
organization. It helps to develop a well secured functional and operational system in the
organization. In order to develop a successful project it must be incorporated with risk
assessment and management properties so that there is proper informational flow in the
organization (Baumer, 2017). Big data can be defined as an integration of technology, algorithms
and software for the purpose of collecting huge data volume. It focuses on analyzing the data to
find out hidden patterns and other information (Mahajan, Gaba & Chauhan, 2016). The
application of big data has gained huge importance over time. ENISA is the centre of
information security in network. It develops communities across various borders.
This report gives an explanation about the various threats of big data. It also figures out
the most significant threat among the rest. This report also talks about the key threat agents in
ENISA (Kao et al. 2014). It gives an explanation about how can the process of ETL be
improved. At the end it says whether the ENISA is satisfied with its security system or not. This
report also identifies strategies that can be implemented in order to overcome or mitigate the
threats. Efficient organizations need the risk assessment policy to be strong in order to get
success.
RISK MANAGEMENT: ENISA CASE STUDY
Introduction
In this era of technology, risk analysis has become an essential factor for every
organization. It helps to develop a well secured functional and operational system in the
organization. In order to develop a successful project it must be incorporated with risk
assessment and management properties so that there is proper informational flow in the
organization (Baumer, 2017). Big data can be defined as an integration of technology, algorithms
and software for the purpose of collecting huge data volume. It focuses on analyzing the data to
find out hidden patterns and other information (Mahajan, Gaba & Chauhan, 2016). The
application of big data has gained huge importance over time. ENISA is the centre of
information security in network. It develops communities across various borders.
This report gives an explanation about the various threats of big data. It also figures out
the most significant threat among the rest. This report also talks about the key threat agents in
ENISA (Kao et al. 2014). It gives an explanation about how can the process of ETL be
improved. At the end it says whether the ENISA is satisfied with its security system or not. This
report also identifies strategies that can be implemented in order to overcome or mitigate the
threats. Efficient organizations need the risk assessment policy to be strong in order to get
success.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
RISK MANAGEMENT: ENISA CASE STUDY
1. Brief overview of the case study and diagram of ENISA big data security
infrastructure
1.1 Brief overview of the case study
ENISA is the European Union Agency for the Network and Information System. ENISA
is the centre of information security in network. It develops communities across various borders.
ENISA works with different groups for the purpose of developing advice in the area of security
of data and information (Enisa.europa.eu 2017). This organization gives assistance to the
European Union and the states that are its members. Big data has a list of valuable assets that can
be affected by security threats. Data and metadata are the most important threats in big data.
Other assets are volatile, structured, streaming and semi structured data. Software and hardware
are also under the category of assets. There is storage as well as computing infrastructural
models. Privacy and security techniques are also present. Infrastructural security is the very first
aspect of the ecosystem security of big data. It mainly deals with secured distributed systems and
secured data storage (Vatsalan et al., 2017). The case study was based on a three step research
process. Here the initial step was to collect data and then assessment as well as gap analysis was
carried out. The last step was to define what good practices stand for. The architecture or
infrastructure of big data is classified or divided into five main layers like data sources, data
storage, integration process, analytics as well as presentation. The data sources consists of all
types of data like streaming, semi structured and structured data. The process of integration
consists of ETL, API and messaging. Data storage consists of RDF stores and file system that are
distributed. Analytics layer includes advanced and stream analytics. The presentation layer on
RISK MANAGEMENT: ENISA CASE STUDY
1. Brief overview of the case study and diagram of ENISA big data security
infrastructure
1.1 Brief overview of the case study
ENISA is the European Union Agency for the Network and Information System. ENISA
is the centre of information security in network. It develops communities across various borders.
ENISA works with different groups for the purpose of developing advice in the area of security
of data and information (Enisa.europa.eu 2017). This organization gives assistance to the
European Union and the states that are its members. Big data has a list of valuable assets that can
be affected by security threats. Data and metadata are the most important threats in big data.
Other assets are volatile, structured, streaming and semi structured data. Software and hardware
are also under the category of assets. There is storage as well as computing infrastructural
models. Privacy and security techniques are also present. Infrastructural security is the very first
aspect of the ecosystem security of big data. It mainly deals with secured distributed systems and
secured data storage (Vatsalan et al., 2017). The case study was based on a three step research
process. Here the initial step was to collect data and then assessment as well as gap analysis was
carried out. The last step was to define what good practices stand for. The architecture or
infrastructure of big data is classified or divided into five main layers like data sources, data
storage, integration process, analytics as well as presentation. The data sources consists of all
types of data like streaming, semi structured and structured data. The process of integration
consists of ETL, API and messaging. Data storage consists of RDF stores and file system that are
distributed. Analytics layer includes advanced and stream analytics. The presentation layer on
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
RISK MANAGEMENT: ENISA CASE STUDY
the other hand mobile devices, desktops, web browsers as well as web services. Each layer has
its own functions. Gap analysis is carried out. It has been identified in this case study that there
are gaps in the data, cryptographic use, storage models as well as roles. ENISA has carried out an
assessment that is oriented with privacy. They have observed severe gaps in the privacy and also
provided recommendations. It has highlighted privacy preservation by the methods of data
analytics. It has highlighted the needs for policies. There are top threats that exist and also key
agents are there. These threats have a different degree of exposure. The top level threats are
mentioned in the case study. The reason behind the occurrence of threats is the presence of key
agents that act like a catalyst for the occurrence of threats. The importance of developing risk
assessment and mitigation technique is high. Effective operations will be promoted through the
proper management and mitigation of threats. The countermeasure of threats are measured and
compared with the threats. The main scheme for mitigating risks in ENISA is the application of
cryptographic techniques. There are certain loopholes in the technique that needs to be taken care
of. This scheme of mitigating risk comes under the good practices. The main characteristics or
features of data are availability, integrity, non repudiation and confidentiality.
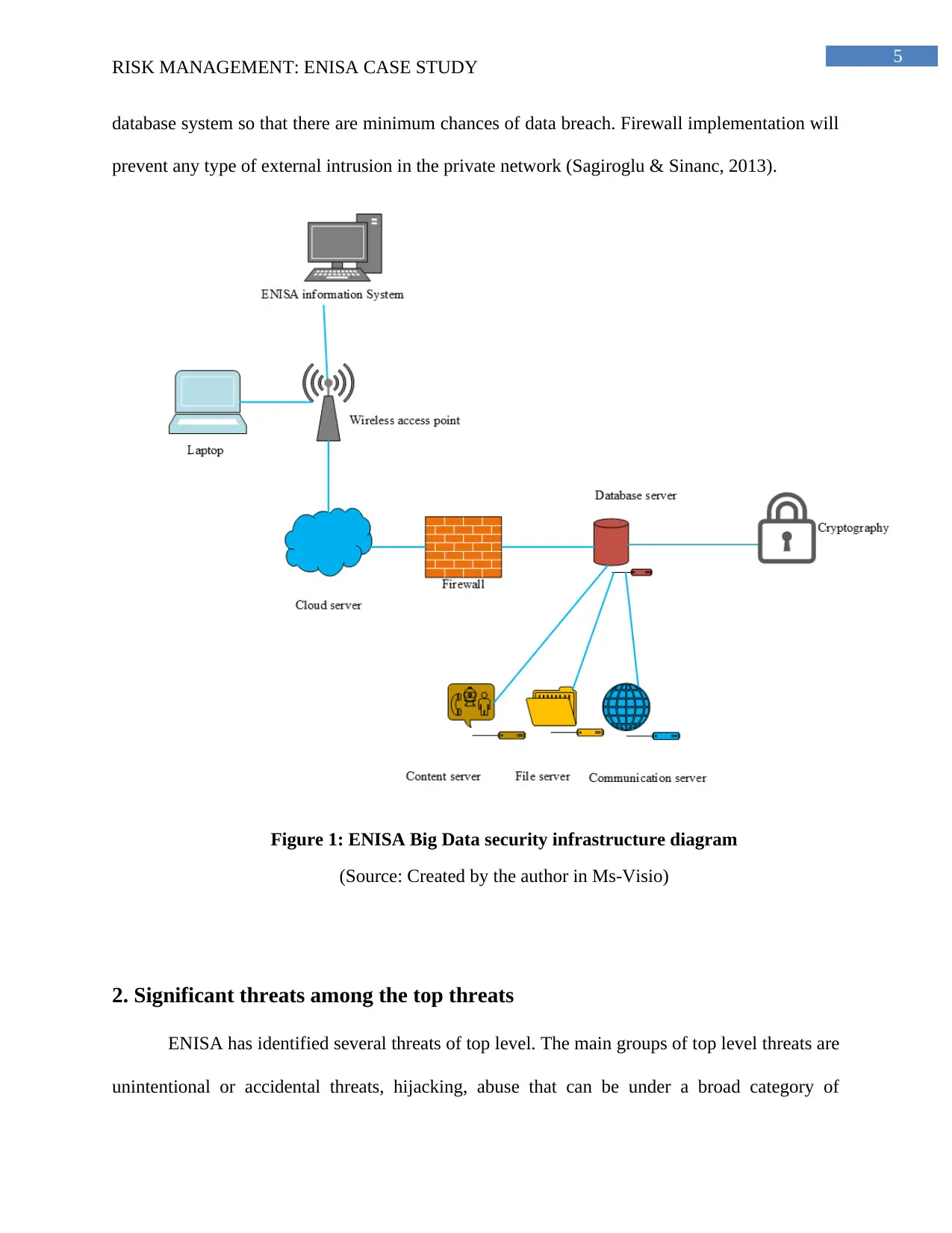
1.2 Big data infrastructure diagram for ENISA
The utilization of structured framework has been depicted in the big data infrastructure of
ENISA. Structured framework helps to carry out effective and efficient operations (Patil &
Seshadri, 2014). Well planned system of information system is implemented in the big data
infrastructure. The main purpose behind any type of infrastructure of security is to bring about
safe operations in the organization. Protocols are incorporated in big data analytics. There are
various strategies for mitigating the risks. Cryptography can be used for protecting the internal
RISK MANAGEMENT: ENISA CASE STUDY
the other hand mobile devices, desktops, web browsers as well as web services. Each layer has
its own functions. Gap analysis is carried out. It has been identified in this case study that there
are gaps in the data, cryptographic use, storage models as well as roles. ENISA has carried out an
assessment that is oriented with privacy. They have observed severe gaps in the privacy and also
provided recommendations. It has highlighted privacy preservation by the methods of data
analytics. It has highlighted the needs for policies. There are top threats that exist and also key
agents are there. These threats have a different degree of exposure. The top level threats are
mentioned in the case study. The reason behind the occurrence of threats is the presence of key
agents that act like a catalyst for the occurrence of threats. The importance of developing risk
assessment and mitigation technique is high. Effective operations will be promoted through the
proper management and mitigation of threats. The countermeasure of threats are measured and
compared with the threats. The main scheme for mitigating risks in ENISA is the application of
cryptographic techniques. There are certain loopholes in the technique that needs to be taken care
of. This scheme of mitigating risk comes under the good practices. The main characteristics or
features of data are availability, integrity, non repudiation and confidentiality.
1.2 Big data infrastructure diagram for ENISA
The utilization of structured framework has been depicted in the big data infrastructure of
ENISA. Structured framework helps to carry out effective and efficient operations (Patil &
Seshadri, 2014). Well planned system of information system is implemented in the big data
infrastructure. The main purpose behind any type of infrastructure of security is to bring about
safe operations in the organization. Protocols are incorporated in big data analytics. There are
various strategies for mitigating the risks. Cryptography can be used for protecting the internal
5
RISK MANAGEMENT: ENISA CASE STUDY
database system so that there are minimum chances of data breach. Firewall implementation will
prevent any type of external intrusion in the private network (Sagiroglu & Sinanc, 2013).
Figure 1: ENISA Big Data security infrastructure diagram
(Source: Created by the author in Ms-Visio)
2. Significant threats among the top threats
ENISA has identified several threats of top level. The main groups of top level threats are
unintentional or accidental threats, hijacking, abuse that can be under a broad category of
RISK MANAGEMENT: ENISA CASE STUDY
database system so that there are minimum chances of data breach. Firewall implementation will
prevent any type of external intrusion in the private network (Sagiroglu & Sinanc, 2013).
Figure 1: ENISA Big Data security infrastructure diagram
(Source: Created by the author in Ms-Visio)
2. Significant threats among the top threats
ENISA has identified several threats of top level. The main groups of top level threats are
unintentional or accidental threats, hijacking, abuse that can be under a broad category of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
RISK MANAGEMENT: ENISA CASE STUDY
deliberate threats (Wu et al., 2014). Another two categories of threats are legal and
organizational threats. The top threats are presented in the table below.
Top Group Type Definition
Unintentional or Accidental
Threats
Leakage of
information (human
error)
Leakage of
information (web
applications)
Inadequate designing
and adaptation
This is a type of threat where
human error plays a major role
(Erl, Khattak & Buhler, 2016).
An employee who is working
under an organization can make
mistakes while entering a data or
he can even delete or modify a
data by mistake. There can be
misconfiguration issues leading
to loss of IT assets.
Most of the application interfaces
are not secured (Hashem et al.,
2015). This leads to severe
problems. There can be data loss
via any application that is
running in the web.
There can be robustness issues
leading to high chances of data
leakage and disclosure (Kim,
Trimi & Chung, 2014). The
targeted assets are storage and
RISK MANAGEMENT: ENISA CASE STUDY
deliberate threats (Wu et al., 2014). Another two categories of threats are legal and
organizational threats. The top threats are presented in the table below.
Top Group Type Definition
Unintentional or Accidental
Threats
Leakage of
information (human
error)
Leakage of
information (web
applications)
Inadequate designing
and adaptation
This is a type of threat where
human error plays a major role
(Erl, Khattak & Buhler, 2016).
An employee who is working
under an organization can make
mistakes while entering a data or
he can even delete or modify a
data by mistake. There can be
misconfiguration issues leading
to loss of IT assets.
Most of the application interfaces
are not secured (Hashem et al.,
2015). This leads to severe
problems. There can be data loss
via any application that is
running in the web.
There can be robustness issues
leading to high chances of data
leakage and disclosure (Kim,
Trimi & Chung, 2014). The
targeted assets are storage and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
RISK MANAGEMENT: ENISA CASE STUDY
infrastructure models present in
the system.
Hijacking, Interception and
Eavesdropping
Information interception In this type of threats the
communication links are often
attacked and targeted. It is very
easy for any attacker to gain
access to sensitive information
via any social media platform.
Abuse or nefarious activity Identity fraud
Denial of service
Malicious code
Information systems are known
for storing several personal
details and financial information
like the credit card details (Chen
& Zhang, 2014). Hackers can get
access to these data and misuse it
causing loss to the users.
Organizations have limited
resources. Attackers tend to keep
the servers busy and utilize the
resources so that at the real time
the access is denied in case of
any useful activity.
Worms, viruses, Trojan horses
are common examples of
malware attacks. Worms are used
to duplicate and send the
duplicate copies to different
RISK MANAGEMENT: ENISA CASE STUDY
infrastructure models present in
the system.
Hijacking, Interception and
Eavesdropping
Information interception In this type of threats the
communication links are often
attacked and targeted. It is very
easy for any attacker to gain
access to sensitive information
via any social media platform.
Abuse or nefarious activity Identity fraud
Denial of service
Malicious code
Information systems are known
for storing several personal
details and financial information
like the credit card details (Chen
& Zhang, 2014). Hackers can get
access to these data and misuse it
causing loss to the users.
Organizations have limited
resources. Attackers tend to keep
the servers busy and utilize the
resources so that at the real time
the access is denied in case of
any useful activity.
Worms, viruses, Trojan horses
are common examples of
malware attacks. Worms are used
to duplicate and send the
duplicate copies to different

8
RISK MANAGEMENT: ENISA CASE STUDY
Rogue certificates
networks. There are exploit kits
that enable malware and virus
infections. Trojan horses are
dangerous because they can
access any computer system or
networks in an unauthorized
manner. Spoofing is a type of
malware where the attacker hides
his identity to fool the victim.
Spoofing is an act of hiding the
identity of another person to gain
access to sensitive data. There
can be certain web attacks where
by downloading files from the
internet can inject some kind of
malicious code in the system.
This can harm the system in
several ways. The data of the
system can be lost and the data
can also be misused.
Rogue certificates can be used by
the attacker to get unauthorized
access to useful and sensitive
data.
The audit tools can be misused
and this can ultimately result in
RISK MANAGEMENT: ENISA CASE STUDY
Rogue certificates
networks. There are exploit kits
that enable malware and virus
infections. Trojan horses are
dangerous because they can
access any computer system or
networks in an unauthorized
manner. Spoofing is a type of
malware where the attacker hides
his identity to fool the victim.
Spoofing is an act of hiding the
identity of another person to gain
access to sensitive data. There
can be certain web attacks where
by downloading files from the
internet can inject some kind of
malicious code in the system.
This can harm the system in
several ways. The data of the
system can be lost and the data
can also be misused.
Rogue certificates can be used by
the attacker to get unauthorized
access to useful and sensitive
data.
The audit tools can be misused
and this can ultimately result in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
RISK MANAGEMENT: ENISA CASE STUDY
Unauthorized activities
Business process
failure
some kind of unauthorized
activities.
This type of threat a damage the
business process in a severe
manner. This can lead to loss of
business.
Legal threats Breach of law or regulations Any organization needs to abide
by certain rules and laws. Non
adherence to the laws and
regulations can cause severe
problem leading to legal threats.
There can also be loss of data and
infrastructural issues in case of
this type of legal threat.
Organizational threats Shortage of skills This is a type of internal threat.
There can be issues like improper
training of employees or
unskilled employees. This can
lead to great trouble. The
productivity of the organization
can fall down. But since it is an
internal threat, this threat can be
controlled and mitigated by the
top management team as well as
any internal risk assessment and
RISK MANAGEMENT: ENISA CASE STUDY
Unauthorized activities
Business process
failure
some kind of unauthorized
activities.
This type of threat a damage the
business process in a severe
manner. This can lead to loss of
business.
Legal threats Breach of law or regulations Any organization needs to abide
by certain rules and laws. Non
adherence to the laws and
regulations can cause severe
problem leading to legal threats.
There can also be loss of data and
infrastructural issues in case of
this type of legal threat.
Organizational threats Shortage of skills This is a type of internal threat.
There can be issues like improper
training of employees or
unskilled employees. This can
lead to great trouble. The
productivity of the organization
can fall down. But since it is an
internal threat, this threat can be
controlled and mitigated by the
top management team as well as
any internal risk assessment and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
RISK MANAGEMENT: ENISA CASE STUDY
management team.
The most significant group of threat is the deliberate threats. Deliberate threats are dangerous
and have high risk exposure because they cannot be rectified. Most of the deliberate threats are
external type of threats. The most significant threat is the malicious code. Worms, viruses,
Trojan horses are common examples of malware attacks. Worms are used to duplicate and send
the duplicate copies to different networks (Kshetri, 2014). Trojan horses are dangerous because
they can access any computer system or networks in an unauthorized manner. There are exploit
kits that enable malware and virus infections. Spoofing is a type of malware where the attacker
hides his identity to fool the victim. Spoofing is an act of hiding the identity of another person to
gain access to sensitive data. There can be certain web attacks where by downloading files from
the internet can inject some kind of malicious code in the system. This can harm the system in
several ways. The data of the system can be lost and the data can also be misused. These codes
can inject into a system and harm the entire system. These are the most dangerous category of
threats among the top threats. They have several ways to attack a computer system or network.
3. Identification and discussion on key threats agents and ways for minimizing
their impact on the system
3.1 Discussion of key threat agents
There is existence of threats because of the presence of the key agents of threats. The key
agents of threats form the basis of threats (Lu et al., 2014). They have the capability to exploit
and take advantage of the weaknesses that are present in the systems or networks. This case
study of ENISA has pointed out certain agents of threats like:
RISK MANAGEMENT: ENISA CASE STUDY
management team.
The most significant group of threat is the deliberate threats. Deliberate threats are dangerous
and have high risk exposure because they cannot be rectified. Most of the deliberate threats are
external type of threats. The most significant threat is the malicious code. Worms, viruses,
Trojan horses are common examples of malware attacks. Worms are used to duplicate and send
the duplicate copies to different networks (Kshetri, 2014). Trojan horses are dangerous because
they can access any computer system or networks in an unauthorized manner. There are exploit
kits that enable malware and virus infections. Spoofing is a type of malware where the attacker
hides his identity to fool the victim. Spoofing is an act of hiding the identity of another person to
gain access to sensitive data. There can be certain web attacks where by downloading files from
the internet can inject some kind of malicious code in the system. This can harm the system in
several ways. The data of the system can be lost and the data can also be misused. These codes
can inject into a system and harm the entire system. These are the most dangerous category of
threats among the top threats. They have several ways to attack a computer system or network.
3. Identification and discussion on key threats agents and ways for minimizing
their impact on the system
3.1 Discussion of key threat agents
There is existence of threats because of the presence of the key agents of threats. The key
agents of threats form the basis of threats (Lu et al., 2014). They have the capability to exploit
and take advantage of the weaknesses that are present in the systems or networks. This case
study of ENISA has pointed out certain agents of threats like:

11
RISK MANAGEMENT: ENISA CASE STUDY
Employees: These are internal agents. There can be insider attacks where the employee
shares the data with a competitor company or hacker.
Corporation: Some organizations do not abide by any rules or laws. They adopt incorrect
strategies. This type of threat agent are called corporation.
Script kiddies: Systems and networks can get attacked by any type of scripts that are
developed by attackers and hackers. This is a type of code that is generated by the hacker.
Cyber terrorists: This threat agent is influenced by any political issue that aims at
harming the public infrastructures and also sectors like telecommunications.
Cyber criminals: These agents are hostile in nature and they target any weak system.
They try to get access to the sensitive data for their own benefits.
Nation: Sometimes a nation itself can be a threat agent.
Hacktivists: Political issues lead to this type of threats.
3.2Impact minimization
Cryptographic algorithms can be used for mitigating the highest degree of risks. The
internal databases can be encrypted so that no unauthorized access can take place. In
cryptography there can be two methods like public and private key cryptography. There must a
check function for checking integrity of the system (Thuraisingham, 2015). Strong and effective
security policies must be incorporated in the system and network so that there is no data breach.
Authentication processes must be followed so that there is no such issue in the future (Cardenas,
Manadhata & Rajan, 2013). Implementation of firewall is the most effective method of
protecting the internal network from any external intrusions.
RISK MANAGEMENT: ENISA CASE STUDY
Employees: These are internal agents. There can be insider attacks where the employee
shares the data with a competitor company or hacker.
Corporation: Some organizations do not abide by any rules or laws. They adopt incorrect
strategies. This type of threat agent are called corporation.
Script kiddies: Systems and networks can get attacked by any type of scripts that are
developed by attackers and hackers. This is a type of code that is generated by the hacker.
Cyber terrorists: This threat agent is influenced by any political issue that aims at
harming the public infrastructures and also sectors like telecommunications.
Cyber criminals: These agents are hostile in nature and they target any weak system.
They try to get access to the sensitive data for their own benefits.
Nation: Sometimes a nation itself can be a threat agent.
Hacktivists: Political issues lead to this type of threats.
3.2Impact minimization
Cryptographic algorithms can be used for mitigating the highest degree of risks. The
internal databases can be encrypted so that no unauthorized access can take place. In
cryptography there can be two methods like public and private key cryptography. There must a
check function for checking integrity of the system (Thuraisingham, 2015). Strong and effective
security policies must be incorporated in the system and network so that there is no data breach.
Authentication processes must be followed so that there is no such issue in the future (Cardenas,
Manadhata & Rajan, 2013). Implementation of firewall is the most effective method of
protecting the internal network from any external intrusions.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





