Cybersecurity Risk Assessment for Advanced Medicos Limited (AML)
VerifiedAdded on 2022/09/08
|13
|2339
|20
Report
AI Summary
This report presents a comprehensive cybersecurity risk assessment for Advanced Medicos Limited (AML), a healthcare product selling company transitioning to an online platform. The report begins with an introduction outlining the company's objectives and the arising cybersecurity concerns. It then identifies critical assets such as customer information, servers, email accounts, and employee data. These assets are categorized into infrastructural, software, information, service, and people assets. The importance of information governance in the healthcare sector, emphasizing trust and accuracy, is explained, along with the principles guiding it. The report details security policies, including objectives, principles, and legal obligations. A risk management framework based on ISO standards is discussed, covering the phases from context establishment to risk treatment. The report identifies various threats in an online business information system, including malware, viruses, spyware, unpatched servers, and physical damage, followed by a detailed risk assessment table. The assessment evaluates the likelihood and impact of each threat, along with recommended controls. Finally, the report provides references to support the analysis.

Running head: RISK MANAGEMENT
RISK MANAGEMENT
Name of the Student:
Name of the University:
Author note:
RISK MANAGEMENT
Name of the Student:
Name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK MANAGEMENT
Table of Contents
Introduction:....................................................................................................................................2
Identification of Assets:...................................................................................................................2
Classification of the identified assets:.............................................................................................3
Explanation of the importance of the information governance:......................................................4
Security policies for the information system:..................................................................................5
Risk Management Phases in ISO Framework:................................................................................7
Threats in online business information system................................................................................8
Risk assessment...............................................................................................................................9
References:....................................................................................................................................11
Table of Contents
Introduction:....................................................................................................................................2
Identification of Assets:...................................................................................................................2
Classification of the identified assets:.............................................................................................3
Explanation of the importance of the information governance:......................................................4
Security policies for the information system:..................................................................................5
Risk Management Phases in ISO Framework:................................................................................7
Threats in online business information system................................................................................8
Risk assessment...............................................................................................................................9
References:....................................................................................................................................11

2RISK MANAGEMENT
Task 1:
Introduction:
Advanced Medicos Limited (AML) is a healthcare product selling company which facing
certain difficulties in the contemporary information system of the company. They have currently
planned upon selling products to their customers online such that more of the customers can be
accommodated in the business and the business can gradually bloom. In order to do so, certain
cyber security concerns has aroused leading to an asset identification and the risk assessment of
the project (Singer and Friedman 2014).
Identification of Assets:
As the company has decided upon shifting their entire system online for the aiding the customers
in their purchase the major assets includes the following:
Customer Information Asset: One of the major assets of any organization is its customer details.
The more numbers of customers getting involved in the organization, the more are the details of
the customers getting to the system. These details are used for the purpose of the company or for
providing suggestion. The pattern of the customer buying behavior can be provided which will
lead to increasing the efficiency of the business as better suggestions can be provided (Goglia
and Siddiqui 2018).
Server assets: The system’s server is one of the major asset of the company as well. This is
because, all the activities of the business can be stored in the server which the employees of the
organization can access as per their requirements while they are working in the company.
Task 1:
Introduction:
Advanced Medicos Limited (AML) is a healthcare product selling company which facing
certain difficulties in the contemporary information system of the company. They have currently
planned upon selling products to their customers online such that more of the customers can be
accommodated in the business and the business can gradually bloom. In order to do so, certain
cyber security concerns has aroused leading to an asset identification and the risk assessment of
the project (Singer and Friedman 2014).
Identification of Assets:
As the company has decided upon shifting their entire system online for the aiding the customers
in their purchase the major assets includes the following:
Customer Information Asset: One of the major assets of any organization is its customer details.
The more numbers of customers getting involved in the organization, the more are the details of
the customers getting to the system. These details are used for the purpose of the company or for
providing suggestion. The pattern of the customer buying behavior can be provided which will
lead to increasing the efficiency of the business as better suggestions can be provided (Goglia
and Siddiqui 2018).
Server assets: The system’s server is one of the major asset of the company as well. This is
because, all the activities of the business can be stored in the server which the employees of the
organization can access as per their requirements while they are working in the company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RISK MANAGEMENT
Email accounts: Today, majority of the signing into the system is conducted with the help of the
email, thus emails are important for an individual or an organization which has to be dealt
properly as well.
Computer or devices: This is a mandatory asset of the company which is dealing with online
services. This is considered to be the basic needs of a process, without which the organization is
most likely not to work.
Workstation: the place where the work or the business is being conducted is an organizational
asset as well. Health care organization here is an asset in itself (de Carvalho Junior, Ortolani and
Pisa 2016).
Routers: The routers are the sources of the internet access in the organization. With the help of
the routers, the internet usage can be enhanced in the organization.
Employee assets: Against all the odds, conflicts and other challenges, the employees are
undeniably one of the most precious asset of the organization. Without them, running an
organization would have been impossible.
Classification of the identified assets:
The organizational assets can be classified in to Infrastructure assets, Software assets,
information assets, service assets and people assets.
The infrastructural assets are also known as the physical assets of the organization. This includes,
the Servers, networks and workstation.
Email accounts: Today, majority of the signing into the system is conducted with the help of the
email, thus emails are important for an individual or an organization which has to be dealt
properly as well.
Computer or devices: This is a mandatory asset of the company which is dealing with online
services. This is considered to be the basic needs of a process, without which the organization is
most likely not to work.
Workstation: the place where the work or the business is being conducted is an organizational
asset as well. Health care organization here is an asset in itself (de Carvalho Junior, Ortolani and
Pisa 2016).
Routers: The routers are the sources of the internet access in the organization. With the help of
the routers, the internet usage can be enhanced in the organization.
Employee assets: Against all the odds, conflicts and other challenges, the employees are
undeniably one of the most precious asset of the organization. Without them, running an
organization would have been impossible.
Classification of the identified assets:
The organizational assets can be classified in to Infrastructure assets, Software assets,
information assets, service assets and people assets.
The infrastructural assets are also known as the physical assets of the organization. This includes,
the Servers, networks and workstation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RISK MANAGEMENT
Software assets: these are the tools or the applications that are used by the organization for
increasing the benefits and the efficiency of the work, like the windows and other operating
software.
Information assets: These are one of the most critical assets of a business. The customer
databases here, along with their email account or the log in details can be termed as one of the
greatest information assets of the company.
Service assets: Here the customer service is the main focus of the company and selling goods
online is their main focus, hence the services assets are the services to the customers, both online
and offline.
People Assets: employees as mentioned before are the major assets of the organization as the
organization is directly dependent upon them to improve the production and increase efficiency
of the organization along with the business of the organization. Apart from this the customers are
also considered as the people assets for the organization.
Explanation of the importance of the information governance:
In the health care sector, building up a trust is very important. Trust helps in marinating the
customer’s loyalty towards that particular organization. Maintaining accuracy in the healthcare is
not a demand it is rather a necessity such that the organization can work efficiently with less
amount of error. Information governance helps in the improvement of the safety and security of
the patient care. It helps in the process of the cost reduction in the company by reducing the risks
as well. There are certain principles which are followed by the information governance in order
to ensure work efficiency and maintain better customer relationship and they are, principles of
accountability, principle of transparency, principle of integrity, principle of protection, principle
Software assets: these are the tools or the applications that are used by the organization for
increasing the benefits and the efficiency of the work, like the windows and other operating
software.
Information assets: These are one of the most critical assets of a business. The customer
databases here, along with their email account or the log in details can be termed as one of the
greatest information assets of the company.
Service assets: Here the customer service is the main focus of the company and selling goods
online is their main focus, hence the services assets are the services to the customers, both online
and offline.
People Assets: employees as mentioned before are the major assets of the organization as the
organization is directly dependent upon them to improve the production and increase efficiency
of the organization along with the business of the organization. Apart from this the customers are
also considered as the people assets for the organization.
Explanation of the importance of the information governance:
In the health care sector, building up a trust is very important. Trust helps in marinating the
customer’s loyalty towards that particular organization. Maintaining accuracy in the healthcare is
not a demand it is rather a necessity such that the organization can work efficiently with less
amount of error. Information governance helps in the improvement of the safety and security of
the patient care. It helps in the process of the cost reduction in the company by reducing the risks
as well. There are certain principles which are followed by the information governance in order
to ensure work efficiency and maintain better customer relationship and they are, principles of
accountability, principle of transparency, principle of integrity, principle of protection, principle

5RISK MANAGEMENT
of compliance, principle of availability, principle of disposition and lastly principle of retention
(Smallwood 2019).
Security policies for the information system:
The objective:
The objective for creating this information security policy is to make the employers as
well as the employees of the organization aware of the facts that what they should do and what
they should not while they are accessing the information as well as other assets of the
organization
Principles:
The information should be classified according to the level of their integrity,
confidentiality and availability of the information.
The employees or the staff who are in charge of the information must be careful and
abide by the laws as well.
The users involved in the scope of the policy must be aware of the classification of the
information and handle the information appropriately.
The information will be protected against any unauthorised access.
The physical systems of the organization must be dealt with care as well, preventing the
breakage in the system (Peltier 2016).
Legal obligations of the security policy:
Advanced Medicos Limited (AML) has the sole responsibility to adhere to and abide by
all the current active laws of the country along with all the contractual requirement.
of compliance, principle of availability, principle of disposition and lastly principle of retention
(Smallwood 2019).
Security policies for the information system:
The objective:
The objective for creating this information security policy is to make the employers as
well as the employees of the organization aware of the facts that what they should do and what
they should not while they are accessing the information as well as other assets of the
organization
Principles:
The information should be classified according to the level of their integrity,
confidentiality and availability of the information.
The employees or the staff who are in charge of the information must be careful and
abide by the laws as well.
The users involved in the scope of the policy must be aware of the classification of the
information and handle the information appropriately.
The information will be protected against any unauthorised access.
The physical systems of the organization must be dealt with care as well, preventing the
breakage in the system (Peltier 2016).
Legal obligations of the security policy:
Advanced Medicos Limited (AML) has the sole responsibility to adhere to and abide by
all the current active laws of the country along with all the contractual requirement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RISK MANAGEMENT
Suppliers:
The suppliers will abide by the Advanced Medicos Limited (AML) information security policies
while they are viewing any information or data on site of the project or from the remote access.
Suppliers:
The suppliers will abide by the Advanced Medicos Limited (AML) information security policies
while they are viewing any information or data on site of the project or from the remote access.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RISK MANAGEMENT
Task 2:
Risk Management Phases in ISO Framework:
A process is developed after the framework of risk management has been established. This
process can be iterative and have multiple steps which are designed for identification and
analysis of the risks regarding the context of organization (Kruse et al. 2017). This process has
several elements which include:
Active Communication
Consulting and communicating with all stakeholders
Execution of process
Context establishment
Identification of the risks
Analysis of the risks
Evaluation of the risks
Treatment of the risks
Oversight
Reviewing and monitoring regularly is also required
The risk assessment process requires context as defined by ISO 31000. Setting the
context begins during the phase of framework when the external and internal environments of the
organization is checked. A context is thus a combination of both external and internal
environments which is related to the strategies and objectives of the organization. The checking
Task 2:
Risk Management Phases in ISO Framework:
A process is developed after the framework of risk management has been established. This
process can be iterative and have multiple steps which are designed for identification and
analysis of the risks regarding the context of organization (Kruse et al. 2017). This process has
several elements which include:
Active Communication
Consulting and communicating with all stakeholders
Execution of process
Context establishment
Identification of the risks
Analysis of the risks
Evaluation of the risks
Treatment of the risks
Oversight
Reviewing and monitoring regularly is also required
The risk assessment process requires context as defined by ISO 31000. Setting the
context begins during the phase of framework when the external and internal environments of the
organization is checked. A context is thus a combination of both external and internal
environments which is related to the strategies and objectives of the organization. The checking

8RISK MANAGEMENT
done should be continued in detail and focusing on the extent of the process of risk management
developed (Safa, Von Solms and Furnell 2016).
The other steps of checking the process of risk management is the identification, analysis
and evaluation of various specific tasks. Although the techniques and methods for documentation
are several, the following few elements are key contents of those techniques (Evans 2016).
Risk identification: It is very important to identify the source, causes,
consequences and the impacts of a particular risk in order to develop a good risk
management technique. The sources of external and internal risk analysis must be
classified.
Risk analysis: It is important to identify the consequences and their causes and
factors and also assess the likelihood. It is also important to identify and evaluate
the currently working controls.
Risk evaluation: Compare the risks identified according o the criteria of risks
established. Decisions are made accordingly to accept and treat those risks
considering the requirements of the legal, external and internal party.
Threats in online business information system:
There are 6 types of security threats which the business information systems are facing.
Ransomware and Malware: Malwares and Ransomware are software which can install in
a computer on their own and can perform their actions behind the users’ back without
them getting to know about it, be it encrypting files, locking systems or stealing or hiding
files from the user.
done should be continued in detail and focusing on the extent of the process of risk management
developed (Safa, Von Solms and Furnell 2016).
The other steps of checking the process of risk management is the identification, analysis
and evaluation of various specific tasks. Although the techniques and methods for documentation
are several, the following few elements are key contents of those techniques (Evans 2016).
Risk identification: It is very important to identify the source, causes,
consequences and the impacts of a particular risk in order to develop a good risk
management technique. The sources of external and internal risk analysis must be
classified.
Risk analysis: It is important to identify the consequences and their causes and
factors and also assess the likelihood. It is also important to identify and evaluate
the currently working controls.
Risk evaluation: Compare the risks identified according o the criteria of risks
established. Decisions are made accordingly to accept and treat those risks
considering the requirements of the legal, external and internal party.
Threats in online business information system:
There are 6 types of security threats which the business information systems are facing.
Ransomware and Malware: Malwares and Ransomware are software which can install in
a computer on their own and can perform their actions behind the users’ back without
them getting to know about it, be it encrypting files, locking systems or stealing or hiding
files from the user.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RISK MANAGEMENT
Virus: It is software which can replicate itself inside a system and destroy files, software,
and data or slow down computers.
Spyware: Spyware can gather and share information to any unauthorized user. They
cannot be detected but can show symptoms like slowing down of system or increased
advertisements. All kinds of viruses, malwares and others spread through emails, spam,
or infected USB devices
Un-patched server and vulnerability to the software: A common security threat is the
accessibility of software and servers that are un-patched. This can lead to DDOS or
distributed denial of service attacks or remote desktop protocol attacks (Wang et al.
2015).
Physical damage: Physical damage to hardware is a major problem to any business
causing loss of data and work issues.
Access threats: due to the lack of the security of the present in Advanced Medicos
Limited (AML), the routers are un-protected, the information in the server can be
accessed by all, the threat of the manipulation of the information or even the loss of the
privacy or the integrity of the data can occur.
Risk assessment:
Sl.
no.
Threats Source Existing
Controls
Likeli
hood
Impact Rating Recommendation
1 Malwares and
Ransomware
SQL
Injection
Outdated
antiviruses,
no system of
back up to
retrieve the
data which
may get lost
by these
attack.
High High High Update to the
latest version of
the antiviruses.
Keeping the
entire system up
to date.
Implementation
of Cloud
computing
Virus: It is software which can replicate itself inside a system and destroy files, software,
and data or slow down computers.
Spyware: Spyware can gather and share information to any unauthorized user. They
cannot be detected but can show symptoms like slowing down of system or increased
advertisements. All kinds of viruses, malwares and others spread through emails, spam,
or infected USB devices
Un-patched server and vulnerability to the software: A common security threat is the
accessibility of software and servers that are un-patched. This can lead to DDOS or
distributed denial of service attacks or remote desktop protocol attacks (Wang et al.
2015).
Physical damage: Physical damage to hardware is a major problem to any business
causing loss of data and work issues.
Access threats: due to the lack of the security of the present in Advanced Medicos
Limited (AML), the routers are un-protected, the information in the server can be
accessed by all, the threat of the manipulation of the information or even the loss of the
privacy or the integrity of the data can occur.
Risk assessment:
Sl.
no.
Threats Source Existing
Controls
Likeli
hood
Impact Rating Recommendation
1 Malwares and
Ransomware
SQL
Injection
Outdated
antiviruses,
no system of
back up to
retrieve the
data which
may get lost
by these
attack.
High High High Update to the
latest version of
the antiviruses.
Keeping the
entire system up
to date.
Implementation
of Cloud
computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
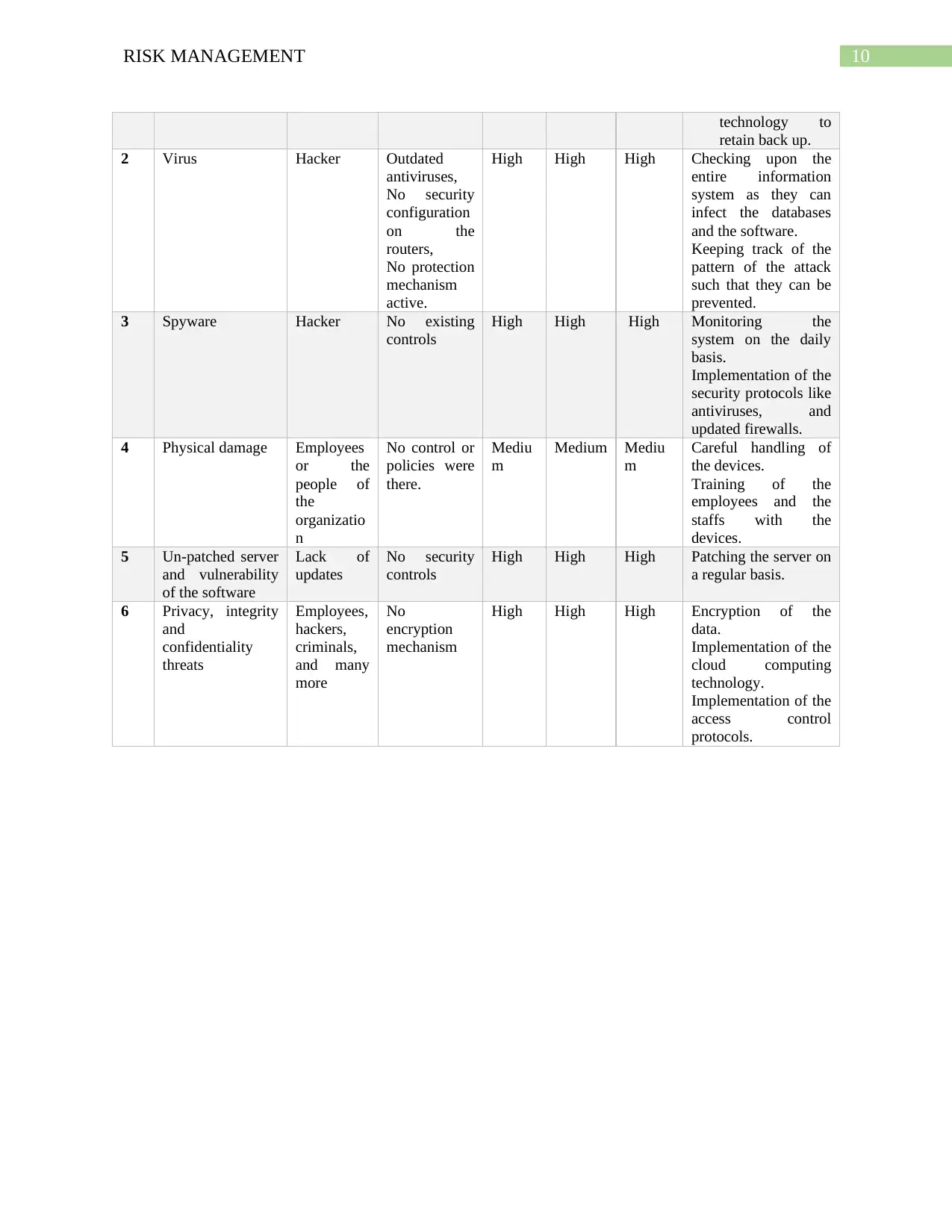
10RISK MANAGEMENT
technology to
retain back up.
2 Virus Hacker Outdated
antiviruses,
No security
configuration
on the
routers,
No protection
mechanism
active.
High High High Checking upon the
entire information
system as they can
infect the databases
and the software.
Keeping track of the
pattern of the attack
such that they can be
prevented.
3 Spyware Hacker No existing
controls
High High High Monitoring the
system on the daily
basis.
Implementation of the
security protocols like
antiviruses, and
updated firewalls.
4 Physical damage Employees
or the
people of
the
organizatio
n
No control or
policies were
there.
Mediu
m
Medium Mediu
m
Careful handling of
the devices.
Training of the
employees and the
staffs with the
devices.
5 Un-patched server
and vulnerability
of the software
Lack of
updates
No security
controls
High High High Patching the server on
a regular basis.
6 Privacy, integrity
and
confidentiality
threats
Employees,
hackers,
criminals,
and many
more
No
encryption
mechanism
High High High Encryption of the
data.
Implementation of the
cloud computing
technology.
Implementation of the
access control
protocols.
technology to
retain back up.
2 Virus Hacker Outdated
antiviruses,
No security
configuration
on the
routers,
No protection
mechanism
active.
High High High Checking upon the
entire information
system as they can
infect the databases
and the software.
Keeping track of the
pattern of the attack
such that they can be
prevented.
3 Spyware Hacker No existing
controls
High High High Monitoring the
system on the daily
basis.
Implementation of the
security protocols like
antiviruses, and
updated firewalls.
4 Physical damage Employees
or the
people of
the
organizatio
n
No control or
policies were
there.
Mediu
m
Medium Mediu
m
Careful handling of
the devices.
Training of the
employees and the
staffs with the
devices.
5 Un-patched server
and vulnerability
of the software
Lack of
updates
No security
controls
High High High Patching the server on
a regular basis.
6 Privacy, integrity
and
confidentiality
threats
Employees,
hackers,
criminals,
and many
more
No
encryption
mechanism
High High High Encryption of the
data.
Implementation of the
cloud computing
technology.
Implementation of the
access control
protocols.

11RISK MANAGEMENT
References:
de Carvalho Junior, M.A., Ortolani, C.L.F. and Pisa, I.T., 2016. Health Information System
(HIS) security standards and guidelines history and content analysis. Journal of Health
Informatics, 8(3).
Evans, L., 2016. Protecting information assets using ISO/IEC security standards. Information
Management, 50(6), p.28.
Goglia, R. and Siddiqui, K., 2018. Non-Healthcare Data is Now Healthcare’s Biggest
Information Asset-an Analysis of Geographic Social Determinant Data and Its Relationship to
Hypertension. Circulation, 138(Suppl_1), pp.A16502-A16502.
Kruse, C.S., Frederick, B., Jacobson, T. and Monticone, D.K., 2017. Cybersecurity in healthcare:
A systematic review of modern threats and trends. Technology and Health Care, 25(1), pp.1-10.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. computers & security, 56, pp.70-82.
Singer, P.W. and Friedman, A., 2014. Cybersecurity: What everyone needs to know. oup usa.
Smallwood, R.F., 2019. Information governance: Concepts, strategies and best practices. John
Wiley & Sons.
Wang, B., Zheng, Y., Lou, W. and Hou, Y.T., 2015. DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, pp.308-319.
References:
de Carvalho Junior, M.A., Ortolani, C.L.F. and Pisa, I.T., 2016. Health Information System
(HIS) security standards and guidelines history and content analysis. Journal of Health
Informatics, 8(3).
Evans, L., 2016. Protecting information assets using ISO/IEC security standards. Information
Management, 50(6), p.28.
Goglia, R. and Siddiqui, K., 2018. Non-Healthcare Data is Now Healthcare’s Biggest
Information Asset-an Analysis of Geographic Social Determinant Data and Its Relationship to
Hypertension. Circulation, 138(Suppl_1), pp.A16502-A16502.
Kruse, C.S., Frederick, B., Jacobson, T. and Monticone, D.K., 2017. Cybersecurity in healthcare:
A systematic review of modern threats and trends. Technology and Health Care, 25(1), pp.1-10.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. computers & security, 56, pp.70-82.
Singer, P.W. and Friedman, A., 2014. Cybersecurity: What everyone needs to know. oup usa.
Smallwood, R.F., 2019. Information governance: Concepts, strategies and best practices. John
Wiley & Sons.
Wang, B., Zheng, Y., Lou, W. and Hou, Y.T., 2015. DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, pp.308-319.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




