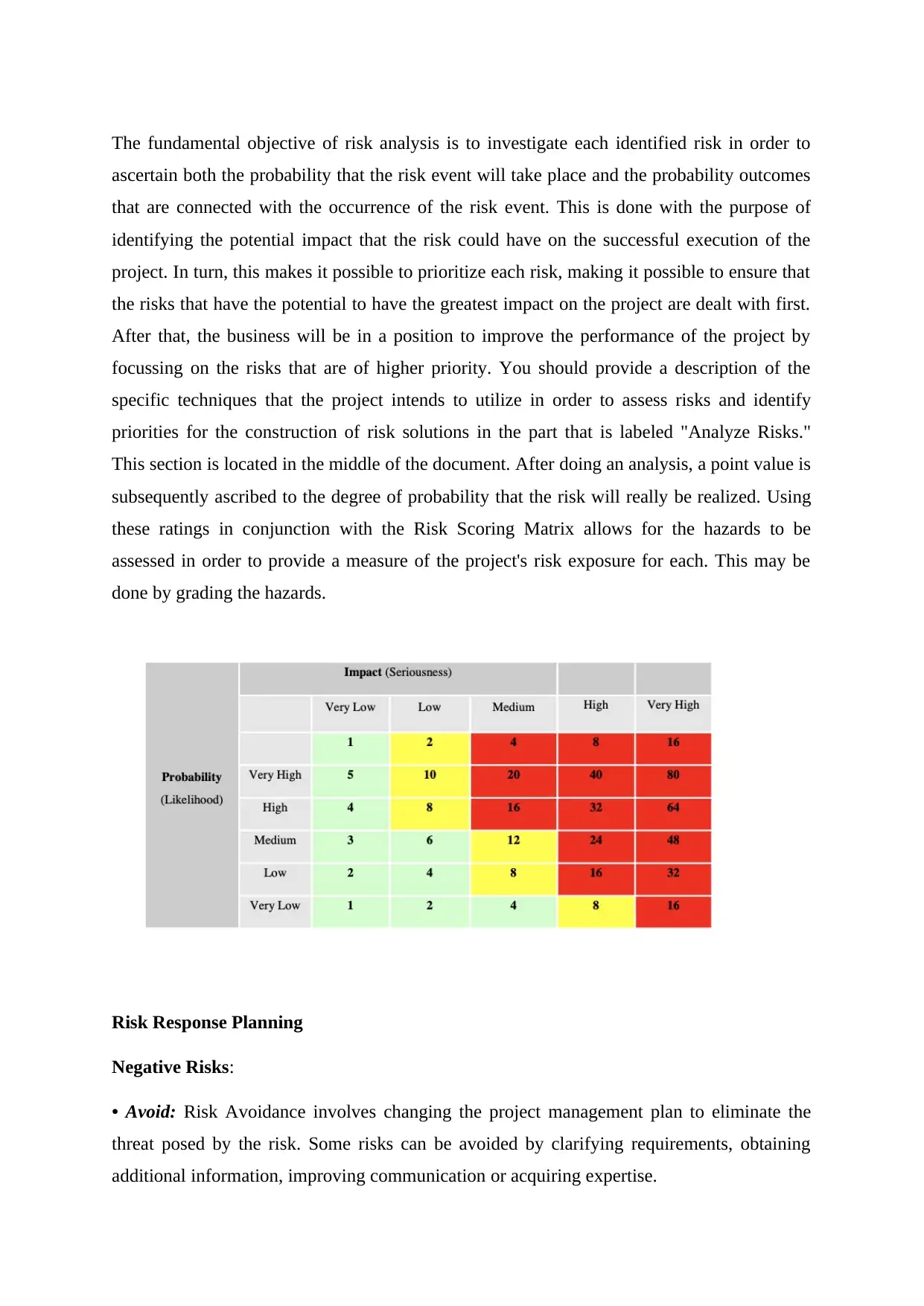
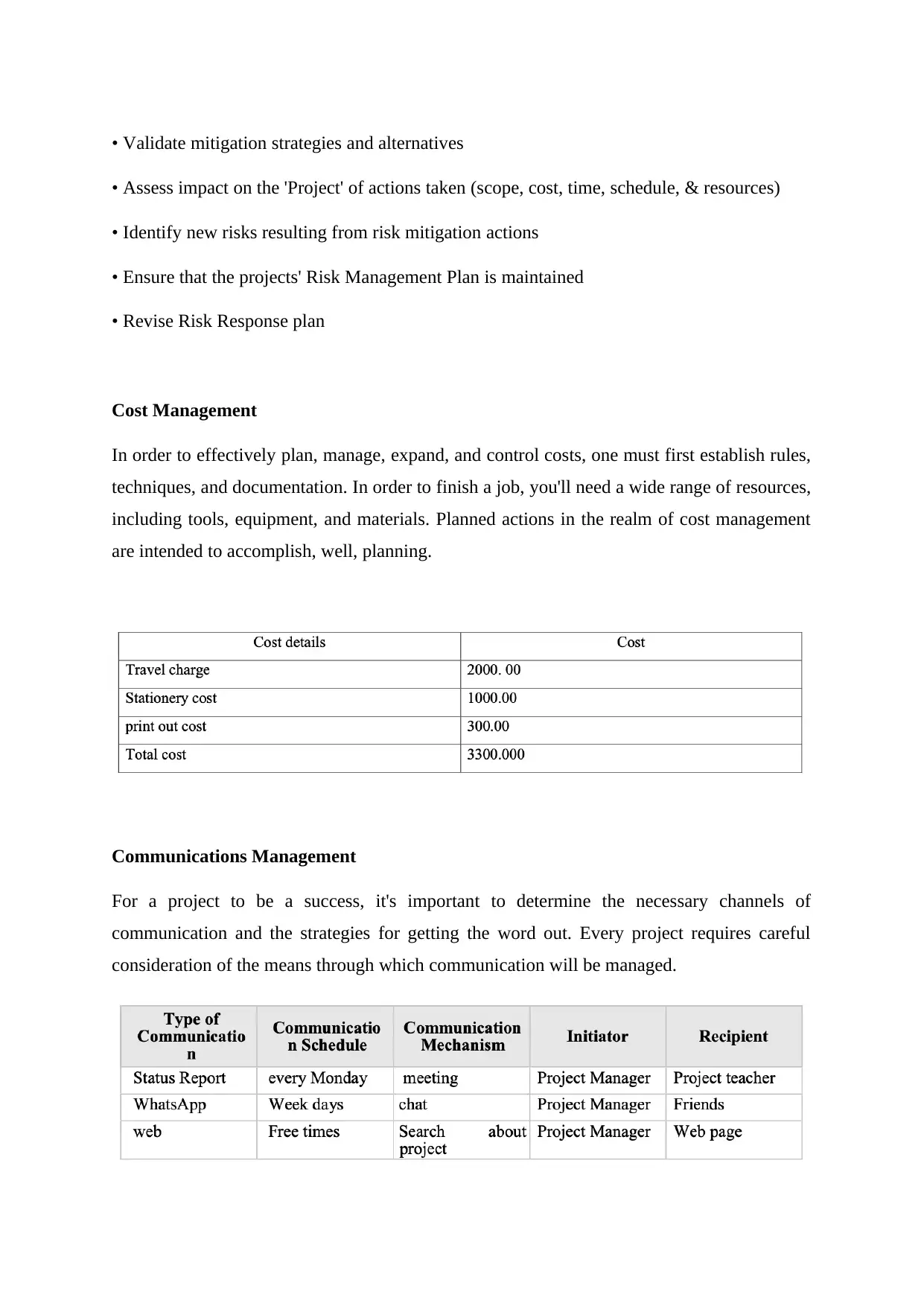
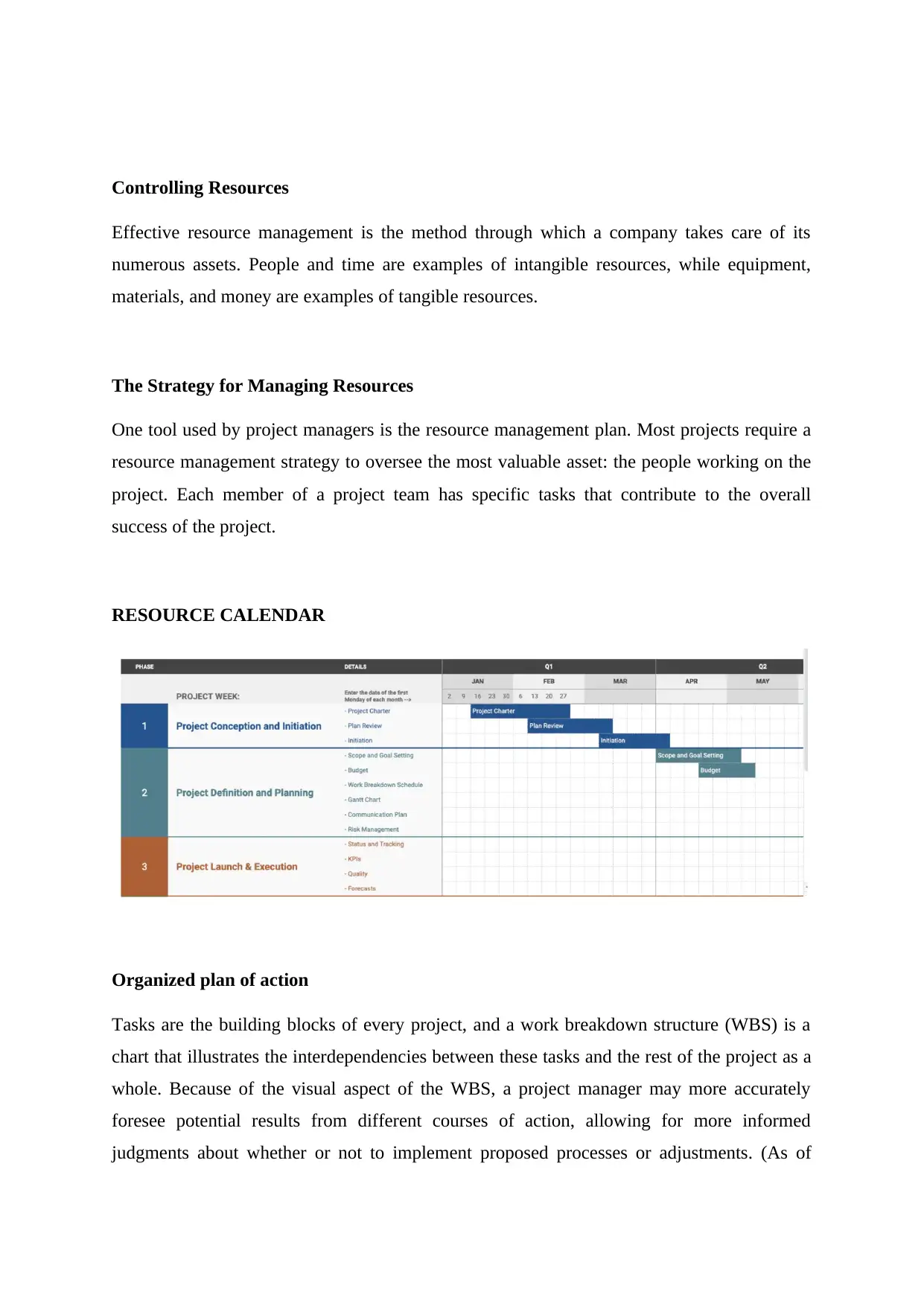
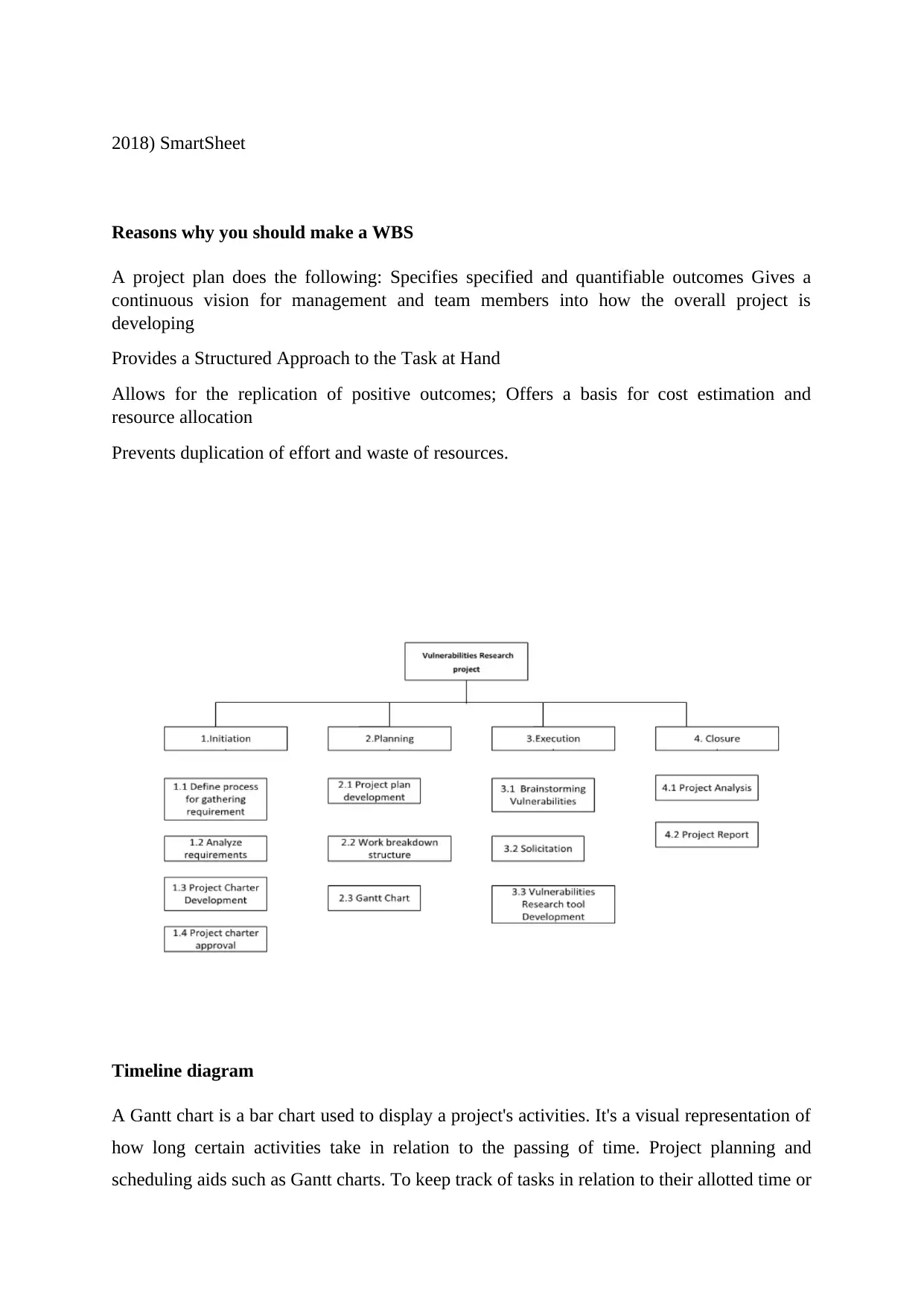
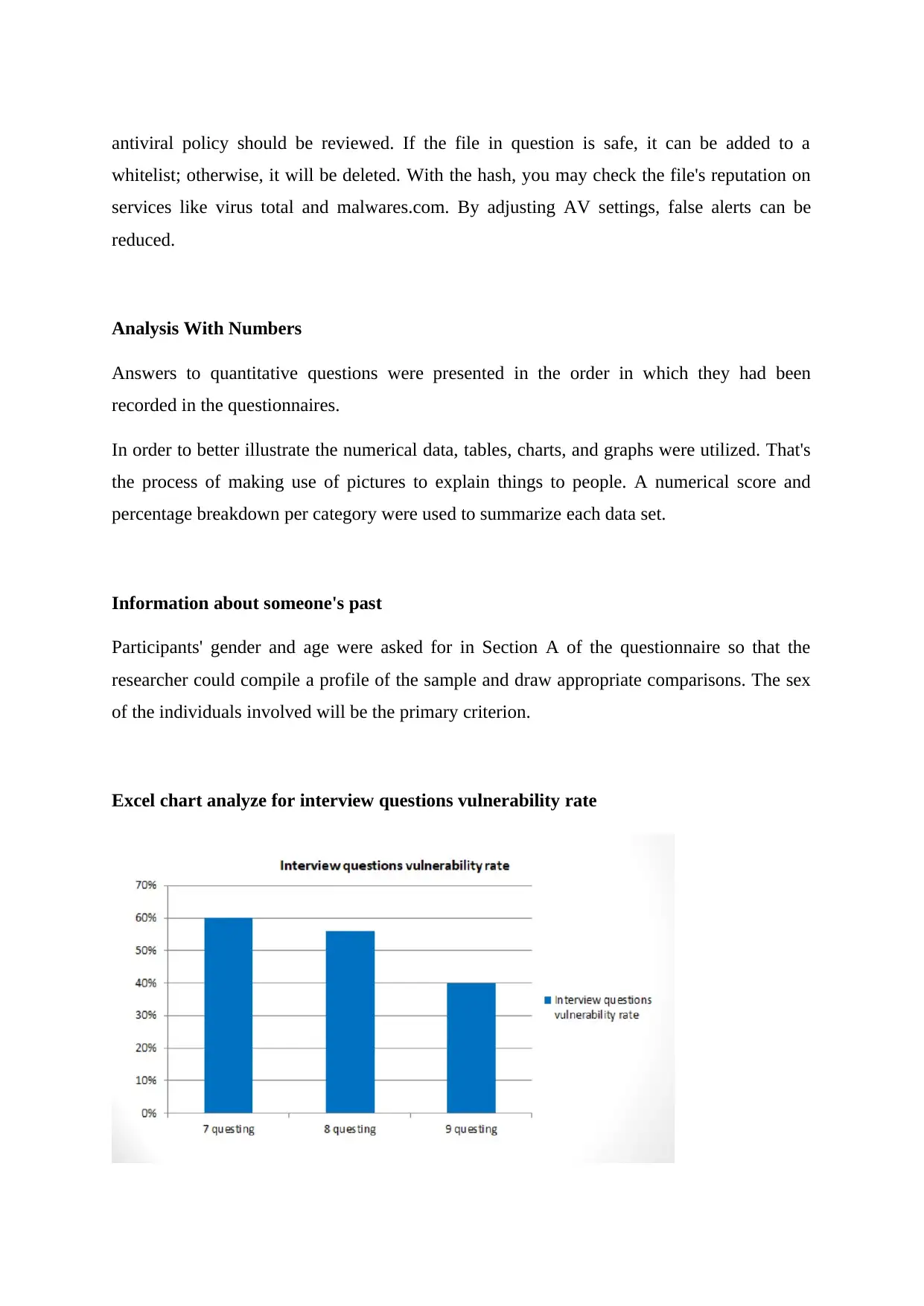
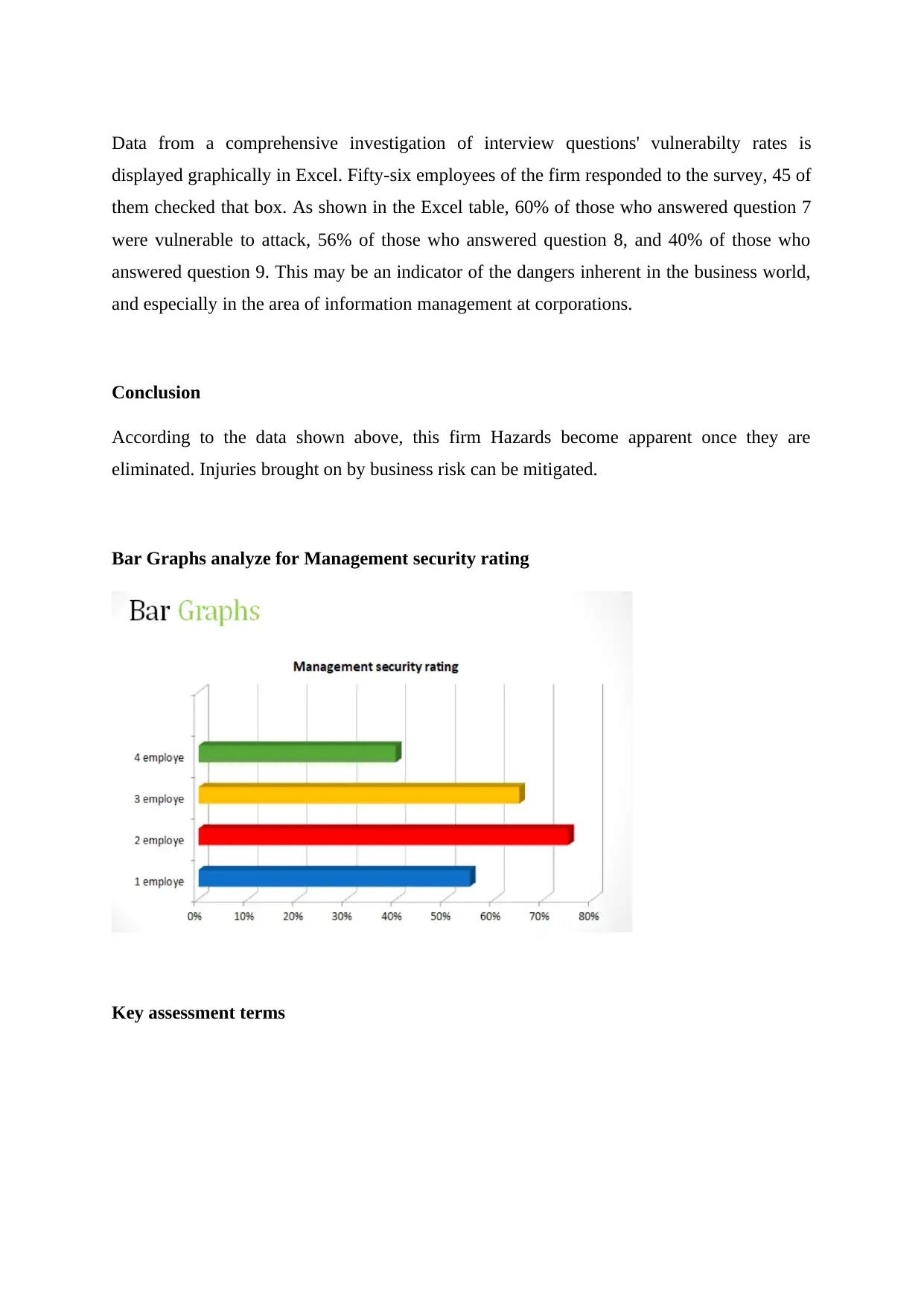
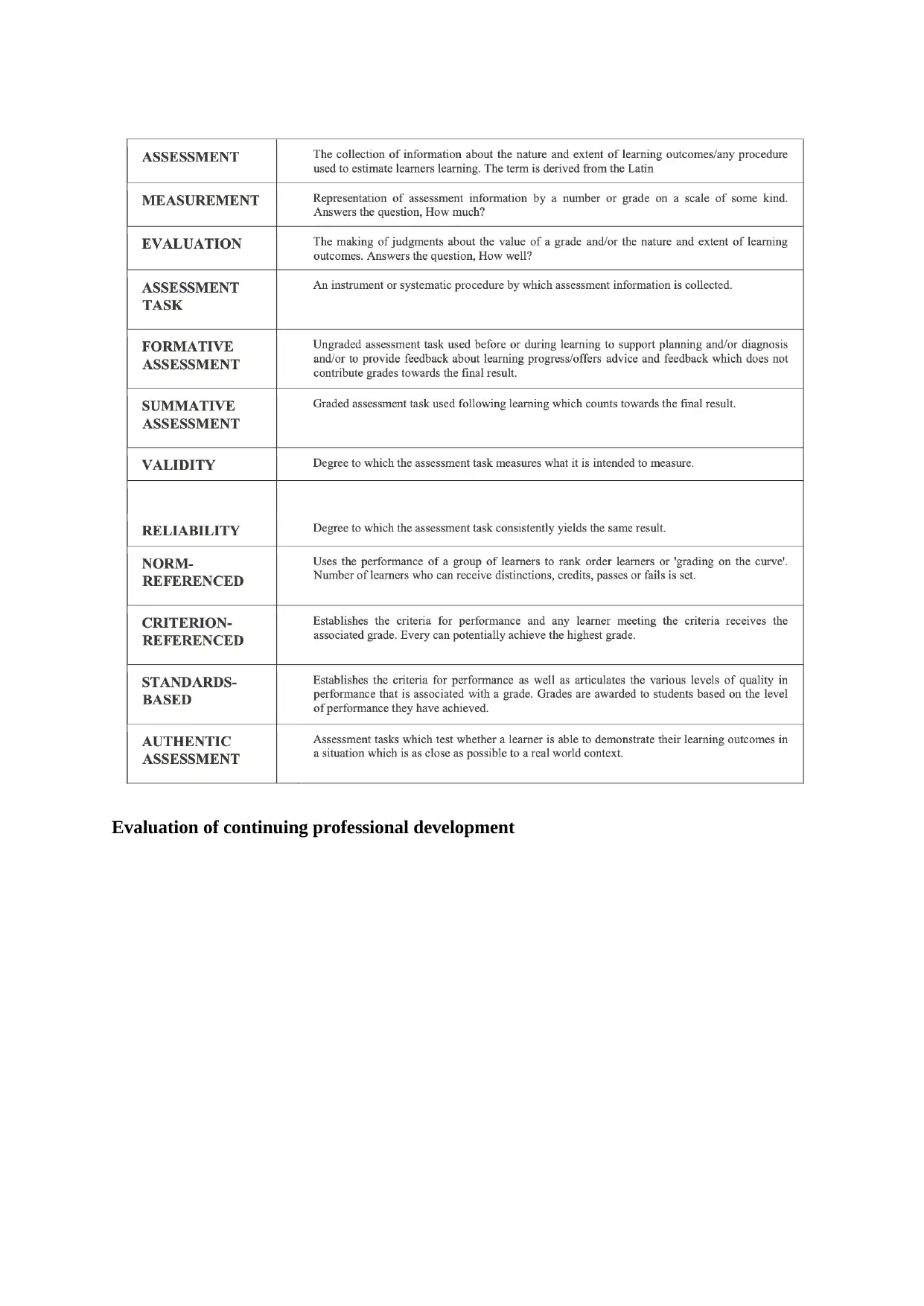
This summary discusses the importance of risk management in information systems and vulnerability assessment. The authors propose a strategy that combines the scenario method and structured interview method to quantify information and create a hierarchy of risks. IT security professionals play a vital role in assisting management in understanding and addressing uncertainties. Vulnerability assessment involves identifying and cataloging vulnerabilities present in a system or application. The study of vulnerability helps organizations make informed decisions and develop countermeasures to secure their systems effectively. A vulnerability assessment project is discussed, focusing on analyzing vulnerabilities in a Management Information System (MIS). The CIA triangle, emphasizing data confidentiality, integrity, and availability, guides information security policies within organizations.
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)