Risk Management for Kevin's Music: Security Threats, Probability-Impact Matrix, and Risk Controls
VerifiedAdded on 2023/06/07
|8
|1573
|305
AI Summary
This report discusses the security threats, probability-impact matrix, and risk controls for Kevin's Music's information system. Malware attacks, denial of service attacks, data breaches, SQL injection attacks, man in the middle attacks, and message and media alteration attacks are analyzed. The report also suggests security controls to avoid and mitigate these risks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Kevin’s Music
Risk Management
9/4/2018
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Kevin’s Music
Risk Management
9/4/2018
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Risk Management
Table of Contents
Introduction...........................................................................................................................................2
EER diagram.........................................................................................................................................2
SQL queries...........................................................................................................................................3
Security Threats.....................................................................................................................................3
Probability-Impact Matrix.....................................................................................................................4
Risk Controls.........................................................................................................................................5
Conclusion.............................................................................................................................................6
References.............................................................................................................................................7
1
Table of Contents
Introduction...........................................................................................................................................2
EER diagram.........................................................................................................................................2
SQL queries...........................................................................................................................................3
Security Threats.....................................................................................................................................3
Probability-Impact Matrix.....................................................................................................................4
Risk Controls.........................................................................................................................................5
Conclusion.............................................................................................................................................6
References.............................................................................................................................................7
1
Risk Management
Introduction
Kevin’s Music is a business that is based out of Burwood. The business is expanding rapidly
and it is now needed to implement and information system for the business to make the
booking process automated and online. The automation of the processes would make use of
various computing resources and networks and there may be various security threats that may
emerge as an outcome. The report lists out such security threats and analyses them to specify
the probability and impact associated with each. The risk controls for the security threats are
also specified.
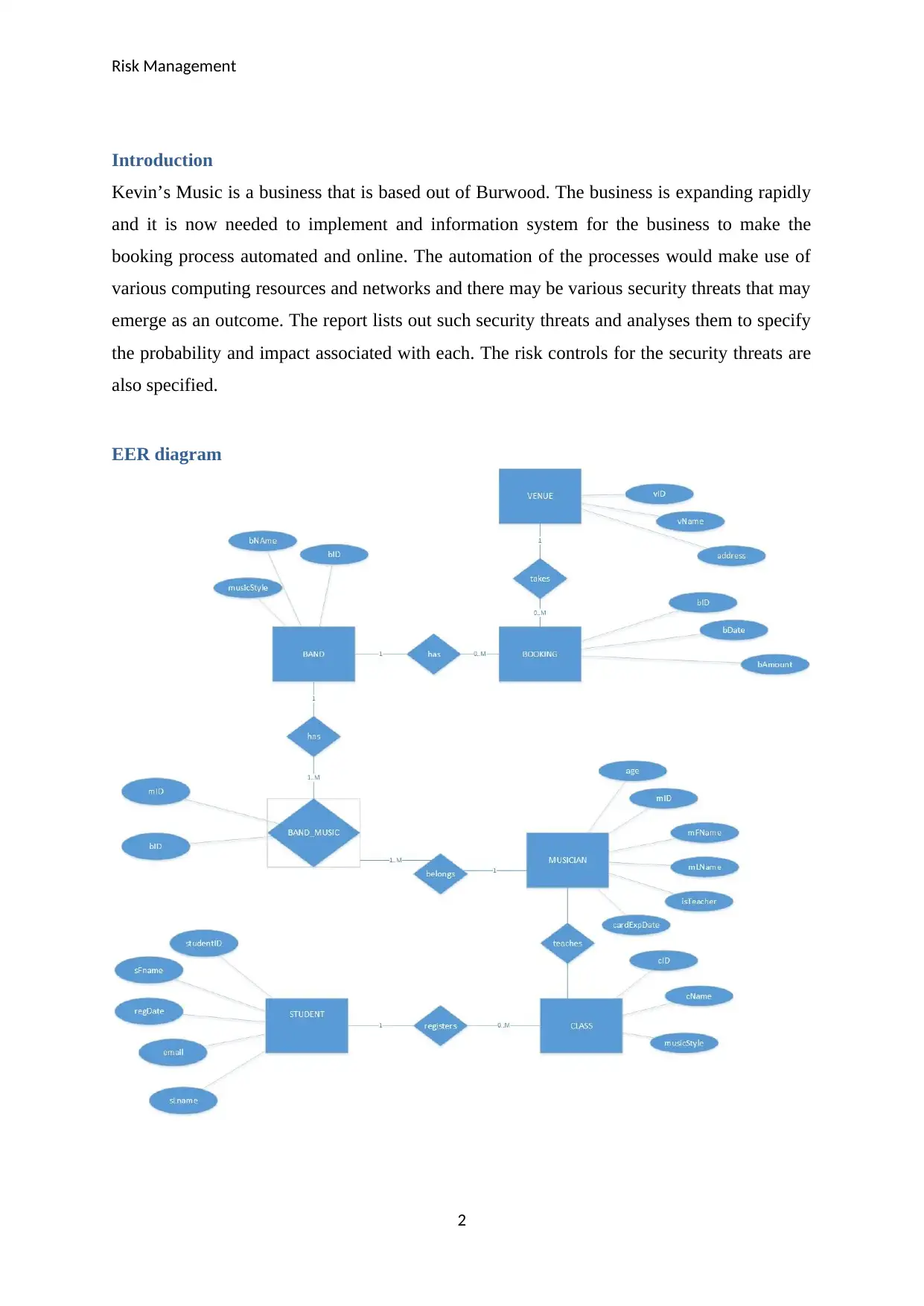
EER diagram
2
Introduction
Kevin’s Music is a business that is based out of Burwood. The business is expanding rapidly
and it is now needed to implement and information system for the business to make the
booking process automated and online. The automation of the processes would make use of
various computing resources and networks and there may be various security threats that may
emerge as an outcome. The report lists out such security threats and analyses them to specify
the probability and impact associated with each. The risk controls for the security threats are
also specified.
EER diagram
2

Risk Management
SQL queries
1. count(s.studentID) from STUDENT s WHERE s.registrationDate = ’01-07-2018’
GROUP BY s.studentID;
2. SELECT * FROM MUSICIAN m WHERE m.age <=18 ORDER BY m.fName;
3. SELECT m.fName, m.lName, m.cardExpDate, m.age FROM MUSICIAN m
WHERE m.cardExpDate < sysDate() AND m.isTeacher = ‘Yes’ order by sysdate();
4. SELECT b.styleMusic, bk.bookingDate FROM BAND b, BOOKING bk,
BAND_MUSIC bm, MUSICIAN m WHERE m.mID = bm.mID AND bm.bID =
b.bID AND b.bID = bk.bID AND month(bk.bookingDate) = month(sysDate())
ORDEr BY bk.bookingDate;
5. SELECT s. studentID, s.fName, s.lName, c.musicStyle, m.fName, m.lName FROM
STUDENT s, CLASS c, MUSICIAN m WHERE s.cID = c.cID AND c.teacher =
m.mID AND m.isTeacher = ‘Yes’ AND month(c.classDate)=month(sysDate());
Security Threats
There may be various security threats that may emerge on the information system that will be
implemented for Kevin’s Music.
Malware Attacks: This is the most common form of security threat that may emerge
due to vulnerabilities in the system and the utilization of the access points. The
attackers may launch the malware, such as viruses, ransomware, worms, Trojan
horses, logic bombs, etc. on the system (El Hadi, 2014).
Denial of Service Attacks: The availability of the system and the information sets
present in the system may be impacted by the execution of the attack. In this attack,
the network or service will be broken down by launching garbage traffic on the same.
Data Breaches: The confidentiality and integrity of the data and information will be
hampered with these attacks in which an attacker may gain unauthorized access to the
same. These may be deliberate or accidental in nature. Insider threats will lead to the
emergence of this attack (Tsohou et al., 2006).
SQL Injection Attacks: The malicious SQL queries may be used to extract sensitive
data sets from the databases by injecting the same.
Man in the Middle Attacks: Network-based security threats and attacks may be given
shape by these attacks and the attacker may sit on the network between the server and
the client. All of the activities taking place on the network will then be captured by
the attacker in an unauthorized manner (Park and Lee, 2014).
3
SQL queries
1. count(s.studentID) from STUDENT s WHERE s.registrationDate = ’01-07-2018’
GROUP BY s.studentID;
2. SELECT * FROM MUSICIAN m WHERE m.age <=18 ORDER BY m.fName;
3. SELECT m.fName, m.lName, m.cardExpDate, m.age FROM MUSICIAN m
WHERE m.cardExpDate < sysDate() AND m.isTeacher = ‘Yes’ order by sysdate();
4. SELECT b.styleMusic, bk.bookingDate FROM BAND b, BOOKING bk,
BAND_MUSIC bm, MUSICIAN m WHERE m.mID = bm.mID AND bm.bID =
b.bID AND b.bID = bk.bID AND month(bk.bookingDate) = month(sysDate())
ORDEr BY bk.bookingDate;
5. SELECT s. studentID, s.fName, s.lName, c.musicStyle, m.fName, m.lName FROM
STUDENT s, CLASS c, MUSICIAN m WHERE s.cID = c.cID AND c.teacher =
m.mID AND m.isTeacher = ‘Yes’ AND month(c.classDate)=month(sysDate());
Security Threats
There may be various security threats that may emerge on the information system that will be
implemented for Kevin’s Music.
Malware Attacks: This is the most common form of security threat that may emerge
due to vulnerabilities in the system and the utilization of the access points. The
attackers may launch the malware, such as viruses, ransomware, worms, Trojan
horses, logic bombs, etc. on the system (El Hadi, 2014).
Denial of Service Attacks: The availability of the system and the information sets
present in the system may be impacted by the execution of the attack. In this attack,
the network or service will be broken down by launching garbage traffic on the same.
Data Breaches: The confidentiality and integrity of the data and information will be
hampered with these attacks in which an attacker may gain unauthorized access to the
same. These may be deliberate or accidental in nature. Insider threats will lead to the
emergence of this attack (Tsohou et al., 2006).
SQL Injection Attacks: The malicious SQL queries may be used to extract sensitive
data sets from the databases by injecting the same.
Man in the Middle Attacks: Network-based security threats and attacks may be given
shape by these attacks and the attacker may sit on the network between the server and
the client. All of the activities taking place on the network will then be captured by
the attacker in an unauthorized manner (Park and Lee, 2014).
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Risk Management
Message & Media Alteration Attacks: The integrity of the data sets will be hampered
negatively as the attackers may alter the contents or properties of the data packets
being transmitted on the system.
The security threats listed above may be internal or external in nature depending upon the
threat agent. In the case of insider threats, the employees of Kevin’s Music will be involved
in giving shape to the attack. These attacks will be internal and deliberate in nature. The
involvement of external parties and deliberate/unintentional mode of attack may also be
involved.
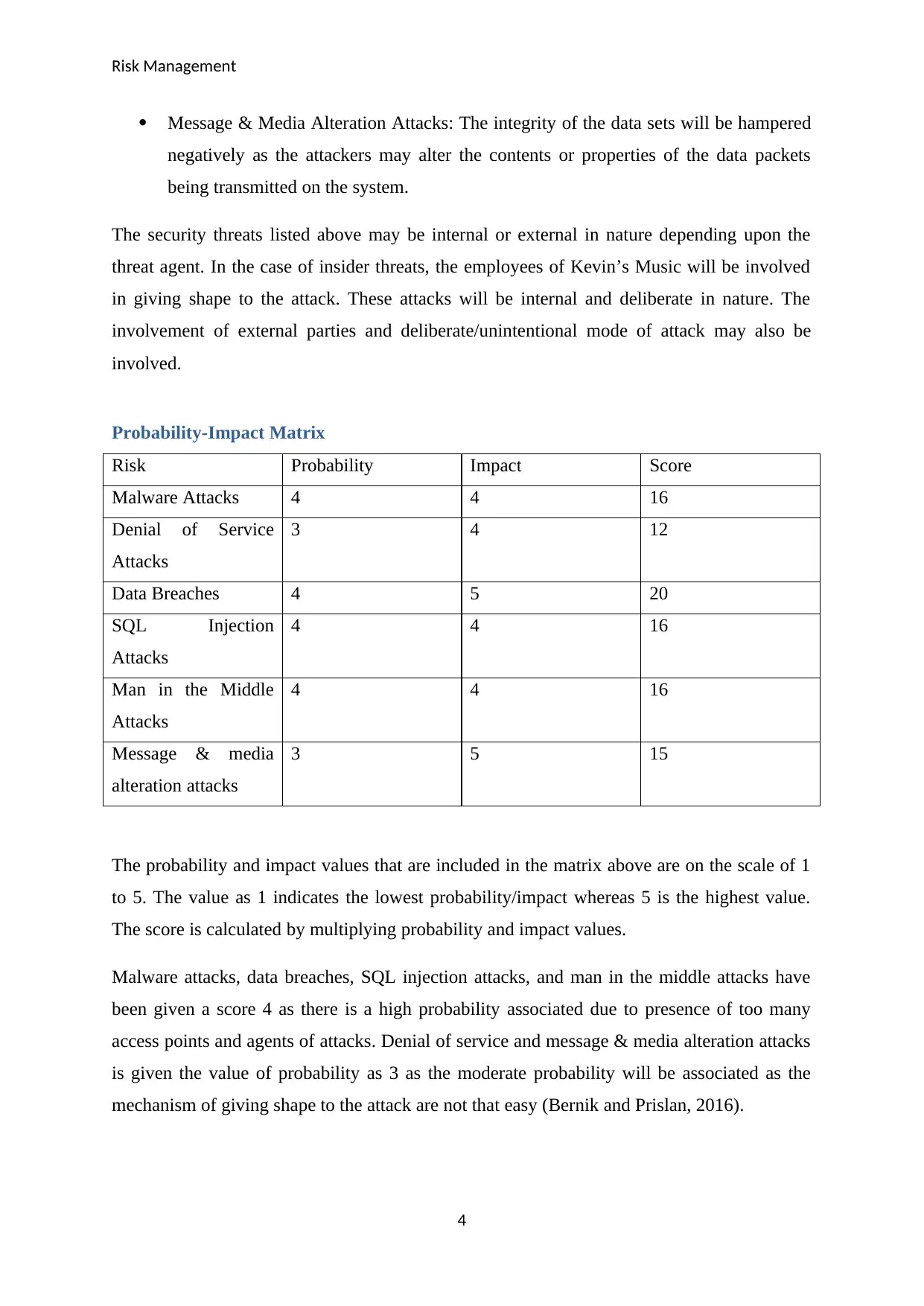
Probability-Impact Matrix
Risk Probability Impact Score
Malware Attacks 4 4 16
Denial of Service
Attacks
3 4 12
Data Breaches 4 5 20
SQL Injection
Attacks
4 4 16
Man in the Middle
Attacks
4 4 16
Message & media
alteration attacks
3 5 15
The probability and impact values that are included in the matrix above are on the scale of 1
to 5. The value as 1 indicates the lowest probability/impact whereas 5 is the highest value.
The score is calculated by multiplying probability and impact values.
Malware attacks, data breaches, SQL injection attacks, and man in the middle attacks have
been given a score 4 as there is a high probability associated due to presence of too many
access points and agents of attacks. Denial of service and message & media alteration attacks
is given the value of probability as 3 as the moderate probability will be associated as the
mechanism of giving shape to the attack are not that easy (Bernik and Prislan, 2016).
4
Message & Media Alteration Attacks: The integrity of the data sets will be hampered
negatively as the attackers may alter the contents or properties of the data packets
being transmitted on the system.
The security threats listed above may be internal or external in nature depending upon the
threat agent. In the case of insider threats, the employees of Kevin’s Music will be involved
in giving shape to the attack. These attacks will be internal and deliberate in nature. The
involvement of external parties and deliberate/unintentional mode of attack may also be
involved.
Probability-Impact Matrix
Risk Probability Impact Score
Malware Attacks 4 4 16
Denial of Service
Attacks
3 4 12
Data Breaches 4 5 20
SQL Injection
Attacks
4 4 16
Man in the Middle
Attacks
4 4 16
Message & media
alteration attacks
3 5 15
The probability and impact values that are included in the matrix above are on the scale of 1
to 5. The value as 1 indicates the lowest probability/impact whereas 5 is the highest value.
The score is calculated by multiplying probability and impact values.
Malware attacks, data breaches, SQL injection attacks, and man in the middle attacks have
been given a score 4 as there is a high probability associated due to presence of too many
access points and agents of attacks. Denial of service and message & media alteration attacks
is given the value of probability as 3 as the moderate probability will be associated as the
mechanism of giving shape to the attack are not that easy (Bernik and Prislan, 2016).
4

Risk Management
The impact of these risks and attacks are assigned with the values as 4 or 5 as the impact will
be severe and negative in nature. The information properties will be impacted due to the
occurrence of these risks and attacks. The confidentiality, availability, integrity, and privacy
of the data sets will be impacted in a negative manner (Feng and Zheng, 2014).
Risk Controls
All of the 6 security risks that have been explained above shall be avoided or mitigated.
For malware attacks, it will be required to implement and install anti-malware tools as the
security controls. These will keep a check on the malicious activities and the ones offering
ransomware protection shall be installed.
Denial of service attacks shall be avoided and mitigated with the use of anti-denial tools.
There shall also be used of data analytics tools done to analyse the network activities and
logs.
The security controls for data breaches shall include the use of advanced access control and
authentication. There must be use of role-based and attribute-based access control that shall
be done. Also, the system shall be authenticated using multi-fold authentication measure so
that the breaching of the data sets may be avoided.
SQL injection attacks shall be avoided and controlled with the use of anti-malware and
network security controls installed in the database being used for the information system.
Man in the middle attacks shall be controlled, avoided, and mitigated by using network-based
security controls. The basic security shall be enhanced with the use of firewalls. Network-
based intrusion detection and intrusion prevention systems shall be implemented so that the
network activities may be analysed at regular intervals.
Message and media alteration attacks shall be avoided and mitigated by implementation of
advanced access control and authentication measures along with the implementation of
network0based security controls.
Apart from the security controls for the risks as listed above, there are additional measures
that shall be undertaken. Administrative security controls shall be used which shall include
regular conduction of security reviews and audits to identify any of the security gaps (Bozkus
5
The impact of these risks and attacks are assigned with the values as 4 or 5 as the impact will
be severe and negative in nature. The information properties will be impacted due to the
occurrence of these risks and attacks. The confidentiality, availability, integrity, and privacy
of the data sets will be impacted in a negative manner (Feng and Zheng, 2014).
Risk Controls
All of the 6 security risks that have been explained above shall be avoided or mitigated.
For malware attacks, it will be required to implement and install anti-malware tools as the
security controls. These will keep a check on the malicious activities and the ones offering
ransomware protection shall be installed.
Denial of service attacks shall be avoided and mitigated with the use of anti-denial tools.
There shall also be used of data analytics tools done to analyse the network activities and
logs.
The security controls for data breaches shall include the use of advanced access control and
authentication. There must be use of role-based and attribute-based access control that shall
be done. Also, the system shall be authenticated using multi-fold authentication measure so
that the breaching of the data sets may be avoided.
SQL injection attacks shall be avoided and controlled with the use of anti-malware and
network security controls installed in the database being used for the information system.
Man in the middle attacks shall be controlled, avoided, and mitigated by using network-based
security controls. The basic security shall be enhanced with the use of firewalls. Network-
based intrusion detection and intrusion prevention systems shall be implemented so that the
network activities may be analysed at regular intervals.
Message and media alteration attacks shall be avoided and mitigated by implementation of
advanced access control and authentication measures along with the implementation of
network0based security controls.
Apart from the security controls for the risks as listed above, there are additional measures
that shall be undertaken. Administrative security controls shall be used which shall include
regular conduction of security reviews and audits to identify any of the security gaps (Bozkus
5

Risk Management
Kahyaoglu and Caliyurt, 2018). There shall also be security updates and patches installed to
control the security threats.
Conclusion
Security of the information system and the data sets present within the system will be
extremely critical. It will be required to maintain the security so that the information
properties can be preserved. The six such security risks as discussed above may take place
and there are controls developed to avoid and mitigate the same. Physical security controls
shall also be used and integrated for enhanced security of the system.
6
Kahyaoglu and Caliyurt, 2018). There shall also be security updates and patches installed to
control the security threats.
Conclusion
Security of the information system and the data sets present within the system will be
extremely critical. It will be required to maintain the security so that the information
properties can be preserved. The six such security risks as discussed above may take place
and there are controls developed to avoid and mitigate the same. Physical security controls
shall also be used and integrated for enhanced security of the system.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk Management
References
Bernik, I. and Prislan, K. (2016). Measuring Information Security Performance with 10 by 10
Model for Holistic State Evaluation. PLOS ONE, 11(9), p.e0163050.
Bozkus Kahyaoglu, S. and Caliyurt, K. (2018). Cyber security assurance process from the
internal audit perspective. Managerial Auditing Journal, 33(4), pp.360-376.
El Hadi, M. (2014). Assessing Information Security Risk Management in Organizations.
Compunet ( The Egyptian Information Journal ), 13(14), pp.18-32.
Feng, N. and Zheng, C. (2014). A Cooperative Model for IS Security Risk Management in
Distributed Environment. The Scientific World Journal, 2014, pp.1-6.
Park, S. and Lee, K. (2014). Advanced Approach to Information Security Management
System Model for Industrial Control System.
Tsohou, A., Karyda, M., Kokolakis, S. and Kiountouzis, E. (2006). Formulating information
systems risk management strategies through cultural theory. Information Management &
Computer Security, 14(3), pp.198-217.
7
References
Bernik, I. and Prislan, K. (2016). Measuring Information Security Performance with 10 by 10
Model for Holistic State Evaluation. PLOS ONE, 11(9), p.e0163050.
Bozkus Kahyaoglu, S. and Caliyurt, K. (2018). Cyber security assurance process from the
internal audit perspective. Managerial Auditing Journal, 33(4), pp.360-376.
El Hadi, M. (2014). Assessing Information Security Risk Management in Organizations.
Compunet ( The Egyptian Information Journal ), 13(14), pp.18-32.
Feng, N. and Zheng, C. (2014). A Cooperative Model for IS Security Risk Management in
Distributed Environment. The Scientific World Journal, 2014, pp.1-6.
Park, S. and Lee, K. (2014). Advanced Approach to Information Security Management
System Model for Industrial Control System.
Tsohou, A., Karyda, M., Kokolakis, S. and Kiountouzis, E. (2006). Formulating information
systems risk management strategies through cultural theory. Information Management &
Computer Security, 14(3), pp.198-217.
7
1 out of 8
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
