Risk Management Process for Information Security at CommDev
An overview of CommDev, a tier-2 not-for-profit organization focused on community development in marginalized areas in developing and/or 3rd world countries.
14 Pages4806 Words131 Views
Added on 2023-06-03
About This Document
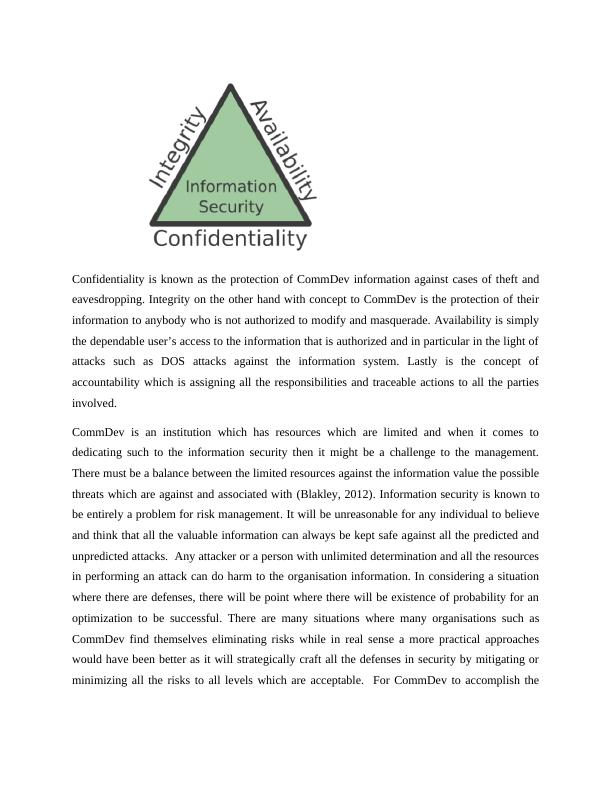
This article discusses the risk management process for information security at CommDev, an organisation that supports needy children in the Pacific and Asian regions. It explains the steps involved in assessing risks, threat assessment, and vulnerable analysis. The article also highlights the importance of confidentiality, integrity, and availability of information, and the need for continuous evaluation and updating of risk mitigation strategies.
Risk Management Process for Information Security at CommDev
An overview of CommDev, a tier-2 not-for-profit organization focused on community development in marginalized areas in developing and/or 3rd world countries.
Added on 2023-06-03
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Security Issues in Information Technology (pdf)
|12
|2988
|346
The advancement of the technology
|4
|466
|13
Target Data Breach: Threats, Protections, and Legal/Ethical Issues
|8
|1725
|99
Assignment on Information Security
|13
|2568
|146
Security Principles
|8
|1397
|436
Cyber-security Assesment Report
|4
|890
|8