IT Risk Management: Tools, Techniques, & Innovative Solutions
VerifiedAdded on 2023/06/05
|15
|3988
|360
Report
AI Summary
This report provides an in-depth analysis of risk management tools and techniques applicable to IT systems, particularly in the context of the London Fire Brigade (LFB). It identifies key tools such as authentication, data encryption, digital signatures, antivirus software, firewalls, API-led connectivity, and smart grids, evaluating their effectiveness and potential drawbacks. The report highlights the problems faced by the LFB due to inadequate IT security, including system crashes and potential data breaches, and reviews previous research focusing on antivirus solutions and password security. It proposes an innovative solution involving cloud computing security to enhance data protection and regulatory compliance. The report emphasizes the importance of implementing robust IT risk mitigation strategies to safeguard sensitive information and ensure operational efficiency within the LFB.

RISK MANAGEMENT
ASSIGNMENT PART 2
TOOLS, TECHNIQUES & PROBLEM-SOLVING
0
ASSIGNMENT PART 2
TOOLS, TECHNIQUES & PROBLEM-SOLVING
0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1: Risk management tools and techniques for IT....................................................................2
Task 2: Problems and previous research on IT risk management...................................................5
Task 3: Innovative solution to mitigate risk in the IT infrastructure of the organization................7
References......................................................................................................................................10
Appendices....................................................................................................................................13
1
Task 1: Risk management tools and techniques for IT....................................................................2
Task 2: Problems and previous research on IT risk management...................................................5
Task 3: Innovative solution to mitigate risk in the IT infrastructure of the organization................7
References......................................................................................................................................10
Appendices....................................................................................................................................13
1
Task 1: Risk management tools and techniques for IT
Cybersecurity has been gaining steady recognition due to increase in a number of security
breaches and unauthorized access. As opined by Buczak and Guven (2016), hackers use effective
techniques through which they gain access to a network system. These actions have caused
stealing of important and also resulted in a breach of privacy. Therefore, in order to secure the
information technology system of the London Fire Brigade, it is essential to analyze the risk
mitigation tools and techniques (london-fire.gov.uk, 2018). The most important tools and
techniques required in IT have been stated as follows:
Authentication
One of the most basic forms of ensuring proper cyber-security is through the process of
authentication. This method helps in identifying the authorized user by accessing the credentials
of the user which is already stored in the domain system. It works a lot like password
technology; however, it can be considered much more effective than that. As asserted by Fielder
et al. (2016), the process of authentication helps in unique identification of the authorized user
and disengages any eavesdropping on authentic messages. The organization of the London Fire
Brigade can essentially benefit from this method as through this method, the information
technology system can only be accessed by authorized users. This would also help the
organization to protect its information from being stolen. However, the process of authentication
is not devoid of its faults. Experienced hackers can breach the security by using strong malware.
Therefore, this risk management tool has both advantages and disadvantages (Refer to Appendix
1).
Data encryption
2
Cybersecurity has been gaining steady recognition due to increase in a number of security
breaches and unauthorized access. As opined by Buczak and Guven (2016), hackers use effective
techniques through which they gain access to a network system. These actions have caused
stealing of important and also resulted in a breach of privacy. Therefore, in order to secure the
information technology system of the London Fire Brigade, it is essential to analyze the risk
mitigation tools and techniques (london-fire.gov.uk, 2018). The most important tools and
techniques required in IT have been stated as follows:
Authentication
One of the most basic forms of ensuring proper cyber-security is through the process of
authentication. This method helps in identifying the authorized user by accessing the credentials
of the user which is already stored in the domain system. It works a lot like password
technology; however, it can be considered much more effective than that. As asserted by Fielder
et al. (2016), the process of authentication helps in unique identification of the authorized user
and disengages any eavesdropping on authentic messages. The organization of the London Fire
Brigade can essentially benefit from this method as through this method, the information
technology system can only be accessed by authorized users. This would also help the
organization to protect its information from being stolen. However, the process of authentication
is not devoid of its faults. Experienced hackers can breach the security by using strong malware.
Therefore, this risk management tool has both advantages and disadvantages (Refer to Appendix
1).
Data encryption
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 1: Data encryption
(Source: openstack.org, 2018)
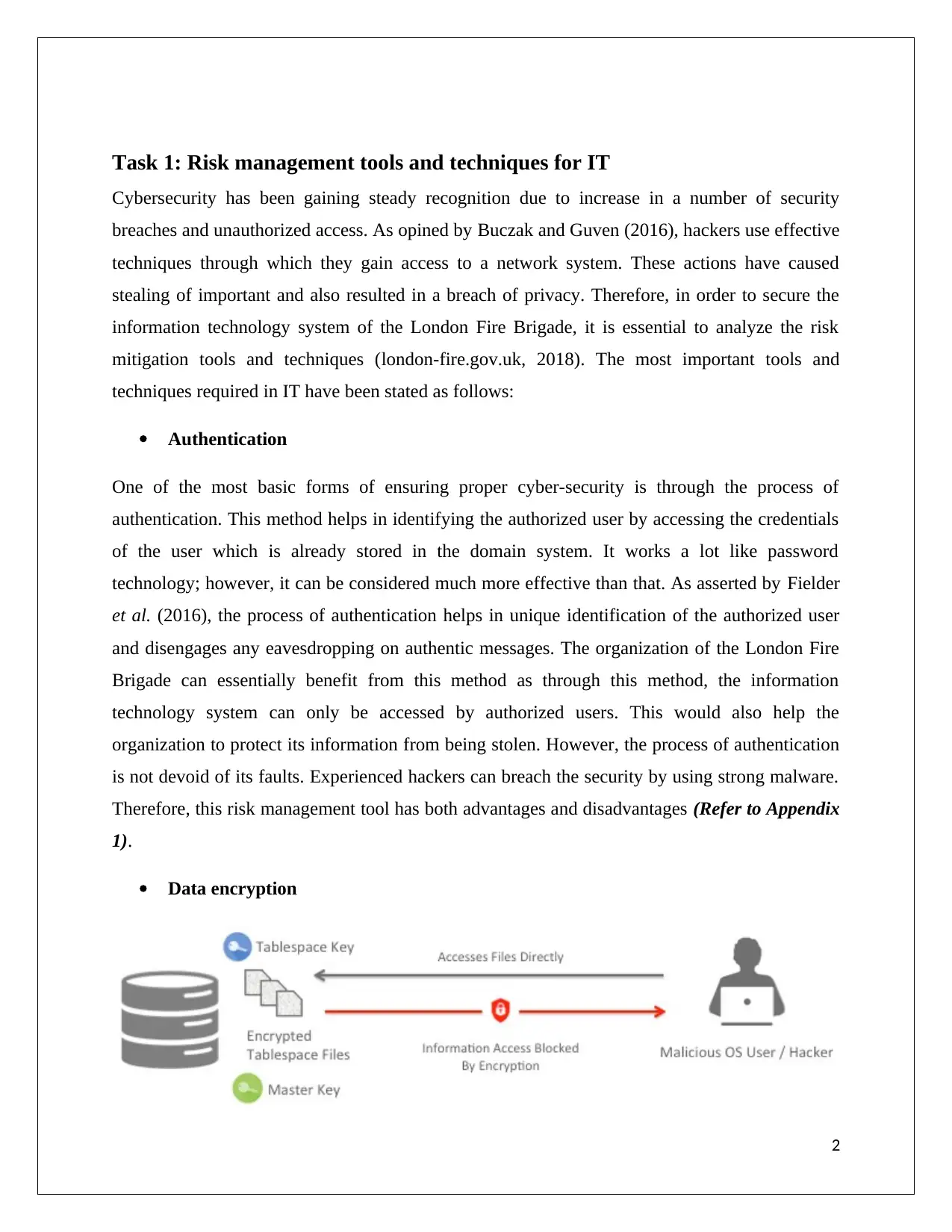
The process o data encryption is becoming really popular in the 21st century. This method
encrypts the data into a format which cannot be deciphered by the third party unless that
individual possesses the decryption key. As forwarded by Sukumara et al. (2018), this is an
effective method which locks the information n a secure system and only the two authorized
parties can gain access to it. The encoded information is passed to the desired individual who has
the other set of key. This information transfer can be done in a secure manner. However, the
distribution of the key is needed to be done with utmost importance. In case, the decryption key
is attained by a third party, the information can be misused (encryption.bsa.org, 2018). The
organization of the London Fire Brigade can use this technique in order to transfer its important
data. This process is needed to be done with the utmost care if the organization wants their data
to be in a perfectly safe condition.
Digital signature
Digital signatures allow one away access for an authorized user to gain access to a system.
Dunjko, Wallden and Andersson (2014) commented that it can be stated as a unique
identification method which uses mathematical algorithms for encryption. This aspect can be
used in the information technology system of the London Fire Brigade. Each and every
employee should be assigned a unique digital signature through which they can access the IT
system of the organization. This would provide adequate security internally as well as externally.
The process of the digital signature is a kind of replica like the data encryption process (Wallden
et al. 2015). The only difference is that data encryption is mainly used for transferring data
between two parties while this method helps in gaining access to the IT system.
Antivirus
Antivirus is the most basic form of protection which provides trigger warnings if there is any
authorized breach. According to Kantchelian et al. (2015), the function of antivirus in an IT
system alone would not be of much help but its significance in the protection of data cannot be
denied. Antivirus helps in identification of potential malware that can harm the IT system and it
3
(Source: openstack.org, 2018)
The process o data encryption is becoming really popular in the 21st century. This method
encrypts the data into a format which cannot be deciphered by the third party unless that
individual possesses the decryption key. As forwarded by Sukumara et al. (2018), this is an
effective method which locks the information n a secure system and only the two authorized
parties can gain access to it. The encoded information is passed to the desired individual who has
the other set of key. This information transfer can be done in a secure manner. However, the
distribution of the key is needed to be done with utmost importance. In case, the decryption key
is attained by a third party, the information can be misused (encryption.bsa.org, 2018). The
organization of the London Fire Brigade can use this technique in order to transfer its important
data. This process is needed to be done with the utmost care if the organization wants their data
to be in a perfectly safe condition.
Digital signature
Digital signatures allow one away access for an authorized user to gain access to a system.
Dunjko, Wallden and Andersson (2014) commented that it can be stated as a unique
identification method which uses mathematical algorithms for encryption. This aspect can be
used in the information technology system of the London Fire Brigade. Each and every
employee should be assigned a unique digital signature through which they can access the IT
system of the organization. This would provide adequate security internally as well as externally.
The process of the digital signature is a kind of replica like the data encryption process (Wallden
et al. 2015). The only difference is that data encryption is mainly used for transferring data
between two parties while this method helps in gaining access to the IT system.
Antivirus
Antivirus is the most basic form of protection which provides trigger warnings if there is any
authorized breach. According to Kantchelian et al. (2015), the function of antivirus in an IT
system alone would not be of much help but its significance in the protection of data cannot be
denied. Antivirus helps in identification of potential malware that can harm the IT system and it
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
stops that particular item from installing itself in the IT system (Gjøsteen and Jager, 2018).
Therefore, the organization of the London Fire Brigade should access their IT system and
implement the antivirus which would be of the most use in the IT system.
Firewall
Figure 2: Function of firewall
(Source: encryption.bsa.org, 2018)
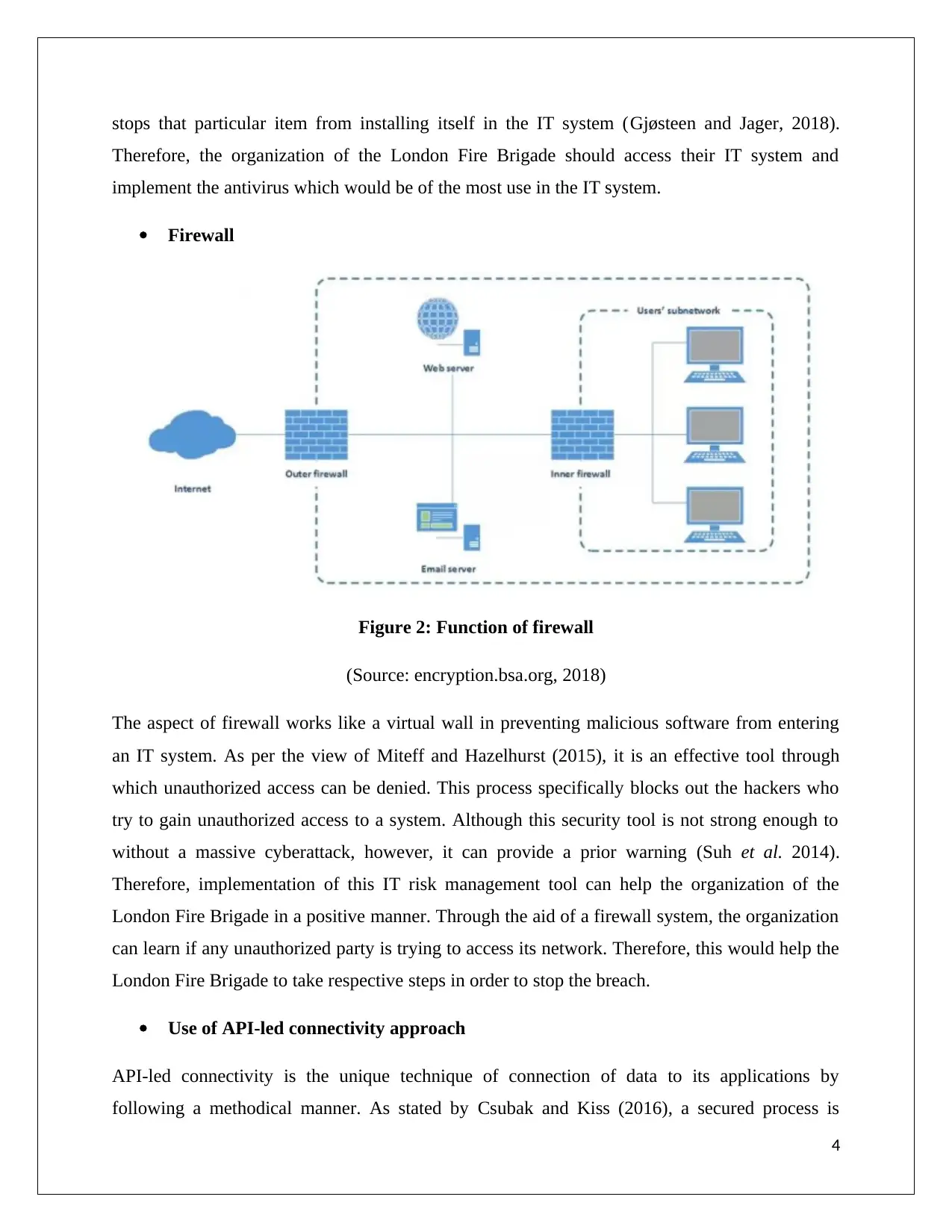
The aspect of firewall works like a virtual wall in preventing malicious software from entering
an IT system. As per the view of Miteff and Hazelhurst (2015), it is an effective tool through
which unauthorized access can be denied. This process specifically blocks out the hackers who
try to gain unauthorized access to a system. Although this security tool is not strong enough to
without a massive cyberattack, however, it can provide a prior warning (Suh et al. 2014).
Therefore, implementation of this IT risk management tool can help the organization of the
London Fire Brigade in a positive manner. Through the aid of a firewall system, the organization
can learn if any unauthorized party is trying to access its network. Therefore, this would help the
London Fire Brigade to take respective steps in order to stop the breach.
Use of API-led connectivity approach
API-led connectivity is the unique technique of connection of data to its applications by
following a methodical manner. As stated by Csubak and Kiss (2016), a secured process is
4
Therefore, the organization of the London Fire Brigade should access their IT system and
implement the antivirus which would be of the most use in the IT system.
Firewall
Figure 2: Function of firewall
(Source: encryption.bsa.org, 2018)
The aspect of firewall works like a virtual wall in preventing malicious software from entering
an IT system. As per the view of Miteff and Hazelhurst (2015), it is an effective tool through
which unauthorized access can be denied. This process specifically blocks out the hackers who
try to gain unauthorized access to a system. Although this security tool is not strong enough to
without a massive cyberattack, however, it can provide a prior warning (Suh et al. 2014).
Therefore, implementation of this IT risk management tool can help the organization of the
London Fire Brigade in a positive manner. Through the aid of a firewall system, the organization
can learn if any unauthorized party is trying to access its network. Therefore, this would help the
London Fire Brigade to take respective steps in order to stop the breach.
Use of API-led connectivity approach
API-led connectivity is the unique technique of connection of data to its applications by
following a methodical manner. As stated by Csubak and Kiss (2016), a secured process is
4

important for various applications in an organization to be connected. This work can be
effectively done through the use of this technique which provides additional security measures.
This technique provides a well-defined entry as well as exit points that can be only be accessed
by an authentic and authorized source. This technique would also provide enough security
through information can be shared in a secured manner. The organization of the London Fire
Brigade would benefit from using this technique as it would help it from accessing various
documentation and sharing it without the fear of security breach.
Use of smart grid
Last but not the least, the aspect of the smart grid is slowly gaining popularity for its effective
security measurements. It is an effective technique through of supply network which allows
digital communication with any hindrance. According to the opinion of Gan and Yang (2015), a
proper aspect of security can be maintained through the use of a smart grid. The organization of
the London Fire Brigade can implement this technique for its network transmission in a safe and
secure manner. It would essentially help the organization to two-way digital communication
without the network being breached (Sun, Hahn and Liu, 2018). Although the aspect of a smart
grid is still developing, it is not quite strong enough to handle a ton of information. However, this
technique has a lot of scope in the future for efficient transmission of resources.
From the above-stated points, various tools and techniques have been identified in respect of an
aspect of risk management for IT systems. Through this list, it can be clearly understood that can
some tools and techniques can effectively help the organization of the London Fire Brigade in
the present day while some tools and techniques are still being improvised. The latter tools and
techniques such as data encryption, API-led connectivity and smart consist of a lot of potentials
and therefore, can be considered by the organization for future use. This would help the London
Fire Brigade to save important information about various organization data from being misused.
Task 2: Problems and previous research on IT risk management
The organization of the London Fire Brigade lacks the providing proper security for its IT
infrastructure. Due to this, the organization had to face various challenges in the recent decade.
One of the most recent incidents includes crashing of the IT system which causes a significant
5
effectively done through the use of this technique which provides additional security measures.
This technique provides a well-defined entry as well as exit points that can be only be accessed
by an authentic and authorized source. This technique would also provide enough security
through information can be shared in a secured manner. The organization of the London Fire
Brigade would benefit from using this technique as it would help it from accessing various
documentation and sharing it without the fear of security breach.
Use of smart grid
Last but not the least, the aspect of the smart grid is slowly gaining popularity for its effective
security measurements. It is an effective technique through of supply network which allows
digital communication with any hindrance. According to the opinion of Gan and Yang (2015), a
proper aspect of security can be maintained through the use of a smart grid. The organization of
the London Fire Brigade can implement this technique for its network transmission in a safe and
secure manner. It would essentially help the organization to two-way digital communication
without the network being breached (Sun, Hahn and Liu, 2018). Although the aspect of a smart
grid is still developing, it is not quite strong enough to handle a ton of information. However, this
technique has a lot of scope in the future for efficient transmission of resources.
From the above-stated points, various tools and techniques have been identified in respect of an
aspect of risk management for IT systems. Through this list, it can be clearly understood that can
some tools and techniques can effectively help the organization of the London Fire Brigade in
the present day while some tools and techniques are still being improvised. The latter tools and
techniques such as data encryption, API-led connectivity and smart consist of a lot of potentials
and therefore, can be considered by the organization for future use. This would help the London
Fire Brigade to save important information about various organization data from being misused.
Task 2: Problems and previous research on IT risk management
The organization of the London Fire Brigade lacks the providing proper security for its IT
infrastructure. Due to this, the organization had to face various challenges in the recent decade.
One of the most recent incidents includes crashing of the IT system which causes a significant
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

delay for the firefighters to provide their aid during emergencies. Although the officials have
stated it was stated it was due to overloading of servers, there is no guarantee that the next server
crash would not be due to a breach of IT security. London Fire Brigade used Vision 4DS system;
however, it keeps crashing due to lack of adequate action.
There are multiple reasons behind the crash information technology system of an organization.
As asserted by Gordon et al. (2015), configuration errors to hardware problems may result in the
crashing of a system. Apart from that, London has faced quite a lot of issues regarding IT
security in 2017. A harmful malware attack in hospitals had led to a huge loss of data and breach
of personal information (Saxe and Berlin, 2015). Such risks have been observed in for safety
departments of London where the aspect of privacy has been violated due to a data breach.
In order to avoid such risks; various studies have been done on information technology risk
management. According to these studies, most of the focus has been on the development of more
space to avoid frequency freezing and crashing of the computer. Other than this, development of
better antivirus software has been given adequate importance. As per the view of Abomhara and
Køien (2015), implementation of adequate online security is of utmost importance. Past studies
have indicated towards the importance of antivirus as the ultimate mitigation policies. Even in
fire service departments, this policy has been used to reduce security breaches.
Another aspect which has been learned from past studies is the use of complex passwords to
ensure more security. According to Yuan et al. (2014), password security denies access to
unauthorized sources. An aspect of strong passwords contains the use of lower case and upper
case alphabets along with numerical as well as special characters. Implementation of these
factors in fire service departments would help in securing the information and data stored on its
computer base. These are the two most important aspects of IT risk mitigation strategy
understood from past research.
However, according to the recent trends, these two aspects are not enough to provide adequate
security for an information technology system. Due to this, it is important to understand the
basics that are the types of information presented in a fire service department. It might include
stakeholder information along with key strategies for firefighting (Saracino et al. 2018). Breach
of the information system of the London Fire Brigade may also cause a delay in finding proper
6
stated it was stated it was due to overloading of servers, there is no guarantee that the next server
crash would not be due to a breach of IT security. London Fire Brigade used Vision 4DS system;
however, it keeps crashing due to lack of adequate action.
There are multiple reasons behind the crash information technology system of an organization.
As asserted by Gordon et al. (2015), configuration errors to hardware problems may result in the
crashing of a system. Apart from that, London has faced quite a lot of issues regarding IT
security in 2017. A harmful malware attack in hospitals had led to a huge loss of data and breach
of personal information (Saxe and Berlin, 2015). Such risks have been observed in for safety
departments of London where the aspect of privacy has been violated due to a data breach.
In order to avoid such risks; various studies have been done on information technology risk
management. According to these studies, most of the focus has been on the development of more
space to avoid frequency freezing and crashing of the computer. Other than this, development of
better antivirus software has been given adequate importance. As per the view of Abomhara and
Køien (2015), implementation of adequate online security is of utmost importance. Past studies
have indicated towards the importance of antivirus as the ultimate mitigation policies. Even in
fire service departments, this policy has been used to reduce security breaches.
Another aspect which has been learned from past studies is the use of complex passwords to
ensure more security. According to Yuan et al. (2014), password security denies access to
unauthorized sources. An aspect of strong passwords contains the use of lower case and upper
case alphabets along with numerical as well as special characters. Implementation of these
factors in fire service departments would help in securing the information and data stored on its
computer base. These are the two most important aspects of IT risk mitigation strategy
understood from past research.
However, according to the recent trends, these two aspects are not enough to provide adequate
security for an information technology system. Due to this, it is important to understand the
basics that are the types of information presented in a fire service department. It might include
stakeholder information along with key strategies for firefighting (Saracino et al. 2018). Breach
of the information system of the London Fire Brigade may also cause a delay in finding proper
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information during emergencies. If the system is affected by a malware, the organization would
be unable to access any corner of it. This could lead to utterly dangerous situations where
significant delay can cause a threat to life. In fact, this case has already been observed in the past.
Due to this, it is important to use innovative solutions such as cloud technology and data
encryption methods to provide hundred percentage protections to its system of information
technology.
Task 3: Innovative solution to mitigate risk in the IT infrastructure of the
organization
It is essential for the organization of London Fire to implement effective mitigation strategy in
order to protect its system of information technology. As regarded by He, Chan and Guizani
(2017), security breaches can cause a huge impact on the reputation of an organization. There it
is important to implement effective yet practical solutions in order to overcome any security-
related issues. In the 21st century, there is plenty of IT solutions available in the market but it is
important to carefully evaluate which one would be the best for the organization. London Fire
Brigade can implement the method of cloud computing security in order to keep its information
safe and secure.
Cloud computing security can be defined as a set of control-based technology which follows
policies according to regulatory compliance rules for data protection (Singh, Jeong and Park,
2016). One of the key aspects of cloud-based technology is its availability of storage space. The
organization of the London Fire Brigade needs to deal with a lot of important issues and
therefore, it needs to proceeds tons of information. The main system server of the organization
keeps crashing due to overload. Due to this reason, the London Fire Brigade can transport all its
information and data in a cloud computing device. It would not only help in reducing the
overload but also help the IT system function in a much faster manner.
The aspect of cloud computing security also provides additional benefits such as privacy and
access control. As per the opinion of Wei et al. (2014), this process helps gives direct authority
to an organization to process its data in an organized manner. Due to this, it can be stated that the
London Fire Brigade would essentially benefit from implementing this technology. However,
like any other software, cloud computing security is of certain faults. One of the main
7
be unable to access any corner of it. This could lead to utterly dangerous situations where
significant delay can cause a threat to life. In fact, this case has already been observed in the past.
Due to this, it is important to use innovative solutions such as cloud technology and data
encryption methods to provide hundred percentage protections to its system of information
technology.
Task 3: Innovative solution to mitigate risk in the IT infrastructure of the
organization
It is essential for the organization of London Fire to implement effective mitigation strategy in
order to protect its system of information technology. As regarded by He, Chan and Guizani
(2017), security breaches can cause a huge impact on the reputation of an organization. There it
is important to implement effective yet practical solutions in order to overcome any security-
related issues. In the 21st century, there is plenty of IT solutions available in the market but it is
important to carefully evaluate which one would be the best for the organization. London Fire
Brigade can implement the method of cloud computing security in order to keep its information
safe and secure.
Cloud computing security can be defined as a set of control-based technology which follows
policies according to regulatory compliance rules for data protection (Singh, Jeong and Park,
2016). One of the key aspects of cloud-based technology is its availability of storage space. The
organization of the London Fire Brigade needs to deal with a lot of important issues and
therefore, it needs to proceeds tons of information. The main system server of the organization
keeps crashing due to overload. Due to this reason, the London Fire Brigade can transport all its
information and data in a cloud computing device. It would not only help in reducing the
overload but also help the IT system function in a much faster manner.
The aspect of cloud computing security also provides additional benefits such as privacy and
access control. As per the opinion of Wei et al. (2014), this process helps gives direct authority
to an organization to process its data in an organized manner. Due to this, it can be stated that the
London Fire Brigade would essentially benefit from implementing this technology. However,
like any other software, cloud computing security is of certain faults. One of the main
7
disadvantages of this system is that the storage is available with the aid of a third party (Khalil,
Khreishah & Azeem, 2014). This leads to a certain amount of risk even if an organization is the
only one handling its data (Refer to Appendix 2).
The most dangerous threat which is faced by cloud computing is a breach of security by hackers.
In some aspects, hackers release malicious software such as WannaCry which shuts down the
entire system. Until and unless the demands made by the hackers are met, the IT system cannot
be accessed (Ali, Khan and Vasilakos, 2015). Even after thorough compliance, there is no
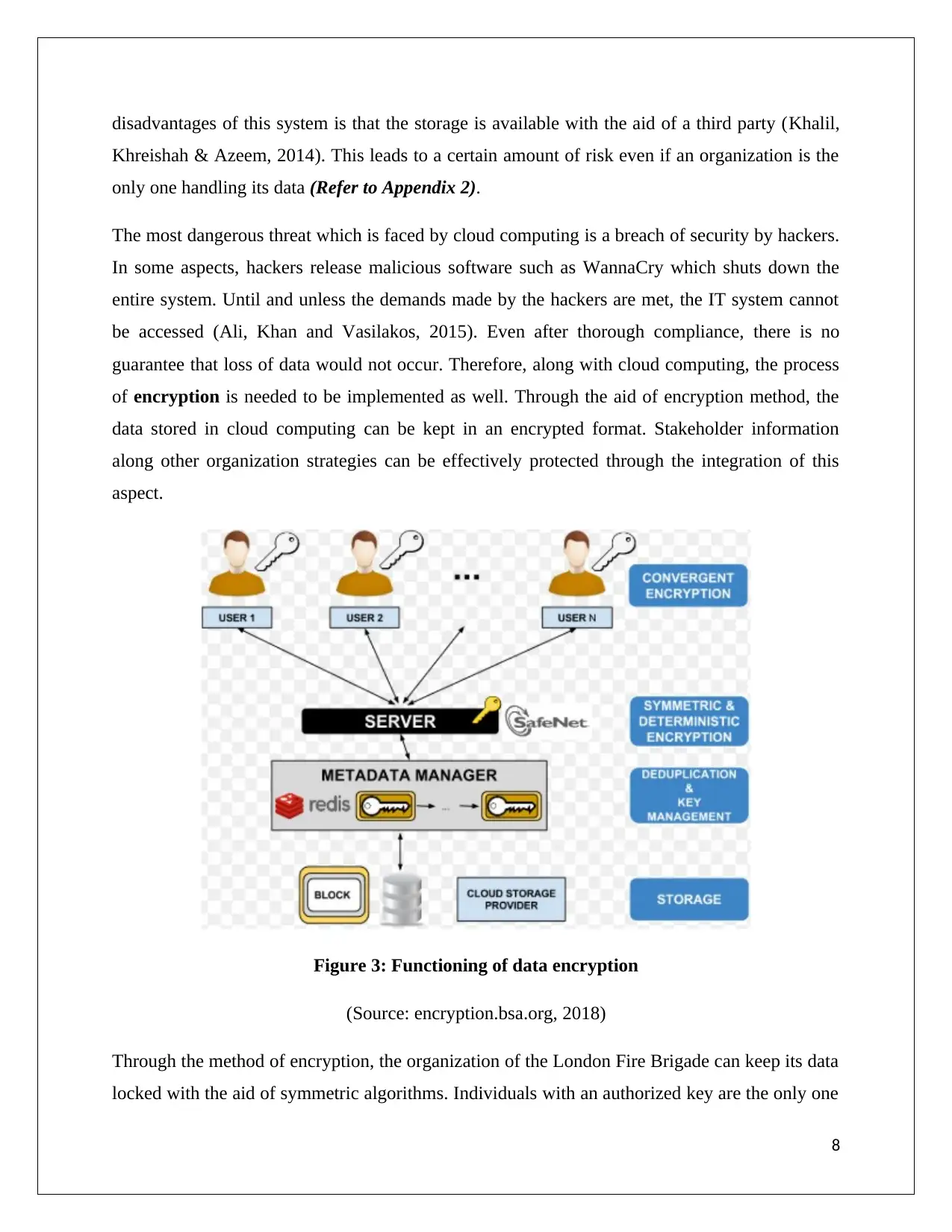
guarantee that loss of data would not occur. Therefore, along with cloud computing, the process
of encryption is needed to be implemented as well. Through the aid of encryption method, the
data stored in cloud computing can be kept in an encrypted format. Stakeholder information
along other organization strategies can be effectively protected through the integration of this
aspect.
Figure 3: Functioning of data encryption
(Source: encryption.bsa.org, 2018)
Through the method of encryption, the organization of the London Fire Brigade can keep its data
locked with the aid of symmetric algorithms. Individuals with an authorized key are the only one
8
Khreishah & Azeem, 2014). This leads to a certain amount of risk even if an organization is the
only one handling its data (Refer to Appendix 2).
The most dangerous threat which is faced by cloud computing is a breach of security by hackers.
In some aspects, hackers release malicious software such as WannaCry which shuts down the
entire system. Until and unless the demands made by the hackers are met, the IT system cannot
be accessed (Ali, Khan and Vasilakos, 2015). Even after thorough compliance, there is no
guarantee that loss of data would not occur. Therefore, along with cloud computing, the process
of encryption is needed to be implemented as well. Through the aid of encryption method, the
data stored in cloud computing can be kept in an encrypted format. Stakeholder information
along other organization strategies can be effectively protected through the integration of this
aspect.
Figure 3: Functioning of data encryption
(Source: encryption.bsa.org, 2018)
Through the method of encryption, the organization of the London Fire Brigade can keep its data
locked with the aid of symmetric algorithms. Individuals with an authorized key are the only one
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

who can access the encrypted data (openstack.org, 2018). This method would also help the
organization in transferring its data from cloud storage to another device in a secured manner.
However, it is of utmost importance for the organization to keep the key for decryption in a safe
place. The loss of the key can lead to unpleasant situations such as leakage of sensitive data. This
would cause the reputation of the organization to drastically fall down along with breach of data
privacy (Bhanot and Hans, 2015). Therefore, this key should be distributed using authentic
sources so that the organization and its stakeholder are the only ones able to access the required
information.
Therefore, from this analysis of innovative solutions, it can be asserted that cloud computing
security and encryption method are the most suited to the IT system of the London Fire Brigade.
Implementation of only one method would not provide strong security, however, if both methods
are implemented the organization stands a strong chance against harmful threats such data and
security breach by hackers. This method can be implemented in not only London Fire Brigade,
but also in other fire service departments for protection of important data and information. It is
always important to keep an additional backup for any system so that an organization can
recover quickly even if it is hit by a large cyber issue. Therefore, along with the aid of cloud
computing security, encryption method and adequate backup, the organization of London Fire
Brigade along with other fire services can eliminate potential risks and keep its data in a
protected manner.
9
organization in transferring its data from cloud storage to another device in a secured manner.
However, it is of utmost importance for the organization to keep the key for decryption in a safe
place. The loss of the key can lead to unpleasant situations such as leakage of sensitive data. This
would cause the reputation of the organization to drastically fall down along with breach of data
privacy (Bhanot and Hans, 2015). Therefore, this key should be distributed using authentic
sources so that the organization and its stakeholder are the only ones able to access the required
information.
Therefore, from this analysis of innovative solutions, it can be asserted that cloud computing
security and encryption method are the most suited to the IT system of the London Fire Brigade.
Implementation of only one method would not provide strong security, however, if both methods
are implemented the organization stands a strong chance against harmful threats such data and
security breach by hackers. This method can be implemented in not only London Fire Brigade,
but also in other fire service departments for protection of important data and information. It is
always important to keep an additional backup for any system so that an organization can
recover quickly even if it is hit by a large cyber issue. Therefore, along with the aid of cloud
computing security, encryption method and adequate backup, the organization of London Fire
Brigade along with other fire services can eliminate potential risks and keep its data in a
protected manner.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Abomhara, M. and Køien, G.M., 2015. Cybersecurity and the internet of things: vulnerabilities,
threats, intruders and attacks. Journal of Cyber Security, 4(1), pp.65-88.
Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security in cloud computing: Opportunities and
challenges. Information sciences, 305(4), pp.357-383.
Bhanot, R. and Hans, R., 2015. A review and comparative analysis of various encryption
algorithms. International Journal of Security and Its Applications, 9(4), pp.289-306.
Buczak, A.L. and Guven, E., 2016. A survey of data mining and machine learning methods for
cybersecurity intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), pp.1153-
1176.
Csubak, D. and Kiss, A., 2016. OpenStack Firewall as a Service Rule Analyser. In International
Conference on Human Aspects of Information Security, Privacy, and Trust, 11(4), pp.212-220.
Dunjko, V., Walden, P. and Andersson, E., 2014. Quantum digital signatures without quantum
memory. Physical review letters, 112(4), pp.40-52.
encryption.bsa.org, 2018, Encryption: Why It Matters, Available at: http://encryption.bsa.org/
[Accessed on: 10-09-2018]
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2016. Decision support
approaches for cybersecurity investment. Decision Support Systems, 86(3), pp.13-23.
Gan, C. and Yang, X., 2015. Theoretical and experimental analysis of the impacts of removable
storage media and antivirus software on viral spread. Communications in Nonlinear Science and
Numerical Simulation, 22(1), pp.167-174.
Gjøsteen, K. and Jager, T., 2018. Practical and Tightly-Secure Digital Signatures and
Authenticated Key Exchange. In Annual International Cryptology Conference, 9(2), pp.95-125.
10
Abomhara, M. and Køien, G.M., 2015. Cybersecurity and the internet of things: vulnerabilities,
threats, intruders and attacks. Journal of Cyber Security, 4(1), pp.65-88.
Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security in cloud computing: Opportunities and
challenges. Information sciences, 305(4), pp.357-383.
Bhanot, R. and Hans, R., 2015. A review and comparative analysis of various encryption
algorithms. International Journal of Security and Its Applications, 9(4), pp.289-306.
Buczak, A.L. and Guven, E., 2016. A survey of data mining and machine learning methods for
cybersecurity intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), pp.1153-
1176.
Csubak, D. and Kiss, A., 2016. OpenStack Firewall as a Service Rule Analyser. In International
Conference on Human Aspects of Information Security, Privacy, and Trust, 11(4), pp.212-220.
Dunjko, V., Walden, P. and Andersson, E., 2014. Quantum digital signatures without quantum
memory. Physical review letters, 112(4), pp.40-52.
encryption.bsa.org, 2018, Encryption: Why It Matters, Available at: http://encryption.bsa.org/
[Accessed on: 10-09-2018]
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2016. Decision support
approaches for cybersecurity investment. Decision Support Systems, 86(3), pp.13-23.
Gan, C. and Yang, X., 2015. Theoretical and experimental analysis of the impacts of removable
storage media and antivirus software on viral spread. Communications in Nonlinear Science and
Numerical Simulation, 22(1), pp.167-174.
Gjøsteen, K. and Jager, T., 2018. Practical and Tightly-Secure Digital Signatures and
Authenticated Key Exchange. In Annual International Cryptology Conference, 9(2), pp.95-125.
10

Gordon, L.A., Loeb, M.P., Lucyshyn, W. and Zhou, L., 2015. Externalities and the magnitude of
cybersecurity underinvestment by private sector firms: a modification of the Gordon-Loeb
model. Journal of Information Security, 6(1), pp.24-31.
He, D., Chan, S. and Guizani, M., 2017. Cyber security analysis and protection of wireless
sensor networks for smart grid monitoring. IEEE Wireless Communications, 24(6), pp.98-103.
Kantchelian, A., Tschantz, M.C., Afroz, S., Miller, B., Shankar, V., Bachwani, R., Joseph, A.D.
and Tygar, J.D., 2015, October. Better malware ground truth: Techniques for weighting anti-
virus vendor labels. In Proceedings of the 8th ACM Workshop on Artificial Intelligence and
Security, 5(2), pp.45-56.
Khalil, I. M., Khreishah, A., & Azeem, M. (2014). Cloud computing security: A
survey. Computers, 3(1), pp.1-35.
Miteff, S. and Hazelhurst, S., 2015. NFShunt: A Linux firewall with OpenFlow-enabled
hardware bypass. In Network Function Virtualization and Software Defined Network (NFV-
SDN), 2015 IEEE Conference, 6(2), pp.100-106.
openstack.org, 2018, Data encryption, Available at:
https://docs.openstack.org/security-guide/tenant-data/data-encryption.html [Accessed on: 10-09-
2018]
Saracino, A., Sgandurra, D., Dini, G. and Martinelli, F., 2018. Madam: Effective and efficient
behaviour-based android malware detection and prevention. IEEE Transactions on Dependable
and Secure Computing, 15(1), pp.83-97.
Saxe, J. and Berlin, K., 2015. Deep neural network based malware detection using two
dimensional binary program features. In Malicious and Unwanted Software (MALWARE), 2015
10th International Conference, 3(1), pp.11-20.
Singh, S., Jeong, Y.S. and Park, J.H., 2016. A survey on cloud computing security: Issues,
threats, and solutions. Journal of Network and Computer Applications, 75(3), pp.200-222.
11
cybersecurity underinvestment by private sector firms: a modification of the Gordon-Loeb
model. Journal of Information Security, 6(1), pp.24-31.
He, D., Chan, S. and Guizani, M., 2017. Cyber security analysis and protection of wireless
sensor networks for smart grid monitoring. IEEE Wireless Communications, 24(6), pp.98-103.
Kantchelian, A., Tschantz, M.C., Afroz, S., Miller, B., Shankar, V., Bachwani, R., Joseph, A.D.
and Tygar, J.D., 2015, October. Better malware ground truth: Techniques for weighting anti-
virus vendor labels. In Proceedings of the 8th ACM Workshop on Artificial Intelligence and
Security, 5(2), pp.45-56.
Khalil, I. M., Khreishah, A., & Azeem, M. (2014). Cloud computing security: A
survey. Computers, 3(1), pp.1-35.
Miteff, S. and Hazelhurst, S., 2015. NFShunt: A Linux firewall with OpenFlow-enabled
hardware bypass. In Network Function Virtualization and Software Defined Network (NFV-
SDN), 2015 IEEE Conference, 6(2), pp.100-106.
openstack.org, 2018, Data encryption, Available at:
https://docs.openstack.org/security-guide/tenant-data/data-encryption.html [Accessed on: 10-09-
2018]
Saracino, A., Sgandurra, D., Dini, G. and Martinelli, F., 2018. Madam: Effective and efficient
behaviour-based android malware detection and prevention. IEEE Transactions on Dependable
and Secure Computing, 15(1), pp.83-97.
Saxe, J. and Berlin, K., 2015. Deep neural network based malware detection using two
dimensional binary program features. In Malicious and Unwanted Software (MALWARE), 2015
10th International Conference, 3(1), pp.11-20.
Singh, S., Jeong, Y.S. and Park, J.H., 2016. A survey on cloud computing security: Issues,
threats, and solutions. Journal of Network and Computer Applications, 75(3), pp.200-222.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





