Risk Management in IT Sector
VerifiedAdded on 2023/04/07
|13
|2155
|446
AI Summary
This report aims to discuss the prospects of risk management of ABC organisation in the IT sector. A brief discussion of the vulnerabilities of the organisation is discussed in this report with a detailed explanation of the vulnerabilities. The threats that are faced by the organisation are briefly stated in this report. A brief discussion of the assets of the organisation is provided in this report. A risk register is provided in this report. A brief discussion of the risk control strategy for the identified risks is provided in this report. Lastly, this report concludes with an appropriate conclusion for the report.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head:RISK MANAGEMENT
RISK MANAGEMENT
Name of student
Name of university
Author’s note:
RISK MANAGEMENT
Name of student
Name of university
Author’s note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
RISK MANAGEMENT
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Vulnerabilities............................................................................................................2
Threats faced by the organisation..............................................................................3
Assets of the organisation..........................................................................................4
Weighted factor analysis............................................................................................5
Risk register...............................................................................................................6
Risk control strategy..................................................................................................8
Conclusion..................................................................................................................9
Bibliography.................................................................................................................11
RISK MANAGEMENT
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Vulnerabilities............................................................................................................2
Threats faced by the organisation..............................................................................3
Assets of the organisation..........................................................................................4
Weighted factor analysis............................................................................................5
Risk register...............................................................................................................6
Risk control strategy..................................................................................................8
Conclusion..................................................................................................................9
Bibliography.................................................................................................................11

2
RISK MANAGEMENT
Introduction
This report aims to discuss the prospects of risk management of ABC organisation in
the IT sector.A brief discussion of the vulnerabilities of the organisation isdiscussed in this
report with a detailed explanation of the vulnerabilities. The threats that are faced by the
organisation are briefly stated in this report. A brief discussion of the assets of the
organisation is provided in this report. A risk register is provided in this report. A brief
discussion of the risk control strategy for the identified risks is provided in this report. Lastly,
this report concludes with an appropriate conclusion for the report.
Discussion
Vulnerabilities
The organisations in the IT sector face several vulnerabilities in working. Some of the
common vulnerabilities are:
SQL injections: This is critical for the operations of the organisation,and the cyber
attackers could exploit this for their own advantage. The penetration testing for the SQL
breaches are significantly imperative (Aven and Zio 2014). As most of the web developers in
the present business situations confounded by the idea of how the cyber attackers manage the
exploitation and the tampering of the SQL for their own advantage, this is the most
significant vulnerability for the organisation.
Vulnerabilities due to the reuse of the passwords: the reusing of the passwords could
create vulnerability in the computing system of the organisation. It might lead to the exposure
of the passwords of any individual to any unauthorised user who could exploit these
passwords and gain sensitive information from the database of the organisation.
RISK MANAGEMENT
Introduction
This report aims to discuss the prospects of risk management of ABC organisation in
the IT sector.A brief discussion of the vulnerabilities of the organisation isdiscussed in this
report with a detailed explanation of the vulnerabilities. The threats that are faced by the
organisation are briefly stated in this report. A brief discussion of the assets of the
organisation is provided in this report. A risk register is provided in this report. A brief
discussion of the risk control strategy for the identified risks is provided in this report. Lastly,
this report concludes with an appropriate conclusion for the report.
Discussion
Vulnerabilities
The organisations in the IT sector face several vulnerabilities in working. Some of the
common vulnerabilities are:
SQL injections: This is critical for the operations of the organisation,and the cyber
attackers could exploit this for their own advantage. The penetration testing for the SQL
breaches are significantly imperative (Aven and Zio 2014). As most of the web developers in
the present business situations confounded by the idea of how the cyber attackers manage the
exploitation and the tampering of the SQL for their own advantage, this is the most
significant vulnerability for the organisation.
Vulnerabilities due to the reuse of the passwords: the reusing of the passwords could
create vulnerability in the computing system of the organisation. It might lead to the exposure
of the passwords of any individual to any unauthorised user who could exploit these
passwords and gain sensitive information from the database of the organisation.

3
RISK MANAGEMENT
Outdated patches: The hackers fishes around the computing systems in the ongoing
quest for the outdated patches (Aven 2016). This vulnerability is faced when the employees
and the employers of the organisation do not update the patches upon release.
Custom crafted URL queries and the misconfigured settings of the servers: The
vulnerability caused due to this reason is very difficult to intercept,but it could be discovered
using the constant pen tests in the servers.
Developed software and in-house designing: There could be significant vulnerability
due to the development of personalised applications and software by the organisation. It
could contain any kind of bugs and gateways that could be exploited by the cyber attackers
(Bessis 2015).
Threats faced by the organisation
Technology with weaker security:modern technology is being provided to common
people almost everyday. The new gadgets that are utilised by the organisation might comprise
of bugs and malware gateways that could be exploited by the cyber attackers.
Social media attacks: In recent times, social media is extensively exploited for
executing cyber attacks (Bromiley et al. 2015). The social media websites are used for
increasing the traffic on the websites that could damage the mainwebsites of the organisation.
The competitive organisation might attempt to damage the reputation of the organisation by
posting several bad things on the social media platform.
Cyber criminals: According to a recent survey, there have been almost one attack in
the IT organisations in the recent times (Chance and Brooks 2015). It leads to the utilisation
of the resources of the organisation by any unauthorised user. The programmers who are the
cyber criminals might write the codes for exploiting the vulnerabilities of the systems of the
organisations. The distributors might attempt to distribute,andsell the stolen data along with
RISK MANAGEMENT
Outdated patches: The hackers fishes around the computing systems in the ongoing
quest for the outdated patches (Aven 2016). This vulnerability is faced when the employees
and the employers of the organisation do not update the patches upon release.
Custom crafted URL queries and the misconfigured settings of the servers: The
vulnerability caused due to this reason is very difficult to intercept,but it could be discovered
using the constant pen tests in the servers.
Developed software and in-house designing: There could be significant vulnerability
due to the development of personalised applications and software by the organisation. It
could contain any kind of bugs and gateways that could be exploited by the cyber attackers
(Bessis 2015).
Threats faced by the organisation
Technology with weaker security:modern technology is being provided to common
people almost everyday. The new gadgets that are utilised by the organisation might comprise
of bugs and malware gateways that could be exploited by the cyber attackers.
Social media attacks: In recent times, social media is extensively exploited for
executing cyber attacks (Bromiley et al. 2015). The social media websites are used for
increasing the traffic on the websites that could damage the mainwebsites of the organisation.
The competitive organisation might attempt to damage the reputation of the organisation by
posting several bad things on the social media platform.
Cyber criminals: According to a recent survey, there have been almost one attack in
the IT organisations in the recent times (Chance and Brooks 2015). It leads to the utilisation
of the resources of the organisation by any unauthorised user. The programmers who are the
cyber criminals might write the codes for exploiting the vulnerabilities of the systems of the
organisations. The distributors might attempt to distribute,andsell the stolen data along with
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
RISK MANAGEMENT
the goods from the associated organisation. They obtain the major data of the organisations
and then distribute to the people who might be the competitors.
Malicious insider: The staff of any organisation could develop to be the greatest
security weakness. The employees might attempt to steal the data of the organisation for
several reasons. It is significantly hard to prevent insider breaches as the majority of the
employees might pose a serious threat for the organisation. This is the main reason why the
organisations are recommended to implement the proper strategies for dealing with the
insider threat. The strict policies could be implemented for dealing with the utilisation of the
removable devices.
Unintentional breaches: The organisation could be exposed to the threats of the
unintentional breaches any time.This denotes that any sensitive information has been
provided to the competition or any malicious user without the knowledge of the value of the
information.It could be numerous kinds of acts like the loss of any removable device,
forgetting the password for protecting the data or even transfer the confidential information
without knowledge.
Technological failures: The organisation is required to be prepared for any kind
oftechnologicalfailures. This kind of threat comprises of the systems crash, missing
documents, and the loss of sensitive files.
Assets of the organisation
The identification of the assets is essential for the organisation as it would help the
organisation for managing the critical assets and manage the working of the organisation. The
appropriate level of the security that must be provided for the protection of the assets could
be decided with the proper identification of the critical assets of the organisation (Farrell and
Gallagher 2015). Some of the assets of the ABC organisation are:
RISK MANAGEMENT
the goods from the associated organisation. They obtain the major data of the organisations
and then distribute to the people who might be the competitors.
Malicious insider: The staff of any organisation could develop to be the greatest
security weakness. The employees might attempt to steal the data of the organisation for
several reasons. It is significantly hard to prevent insider breaches as the majority of the
employees might pose a serious threat for the organisation. This is the main reason why the
organisations are recommended to implement the proper strategies for dealing with the
insider threat. The strict policies could be implemented for dealing with the utilisation of the
removable devices.
Unintentional breaches: The organisation could be exposed to the threats of the
unintentional breaches any time.This denotes that any sensitive information has been
provided to the competition or any malicious user without the knowledge of the value of the
information.It could be numerous kinds of acts like the loss of any removable device,
forgetting the password for protecting the data or even transfer the confidential information
without knowledge.
Technological failures: The organisation is required to be prepared for any kind
oftechnologicalfailures. This kind of threat comprises of the systems crash, missing
documents, and the loss of sensitive files.
Assets of the organisation
The identification of the assets is essential for the organisation as it would help the
organisation for managing the critical assets and manage the working of the organisation. The
appropriate level of the security that must be provided for the protection of the assets could
be decided with the proper identification of the critical assets of the organisation (Farrell and
Gallagher 2015). Some of the assets of the ABC organisation are:

5
RISK MANAGEMENT
Information: Each information about the various working departments of the
organisation is crucial for the development of the company. The information is required to be
collected, organised, classified and then stored in the appropriate forms (McNeil, Frey and
Embrechts 2015). It comprises of the databases, data files, the support and the operational
procedures, the archived information and the fallback arrangements along with the continuity
plans.
Software: The classification of the software assets could be done as the application
software and system software (Olson and Wu 2015). The application software performs the
implementation of the rules of the business of the organisation. The integrity of the
application software is significantly crucial for the proper working of the organisation.
Physical assets: The physical assets of the organisation comprises of the computer
equipment, equipment of communication, storage media, fixtures and furniture and the
technical equipment (Glendon and Clarke 2015). The computer equipment includes
mainframe computers, desktops and notebook computers.
Services: This comprises of the computing services that have been outsourced by the
organisation, the communication services like the data communications, voice
communication, the value-added services and the wide area network and the environmental
conditioning services like the heating, air conditioning, lighting and the power (Haimes
2015).
Weighted factor analysis
Information
asset
Criteria 1:
impact to
revenue
Criteria 2:
impact to
profitability
Criteria 3:
impact to public
image
Weighted score
RISK MANAGEMENT
Information: Each information about the various working departments of the
organisation is crucial for the development of the company. The information is required to be
collected, organised, classified and then stored in the appropriate forms (McNeil, Frey and
Embrechts 2015). It comprises of the databases, data files, the support and the operational
procedures, the archived information and the fallback arrangements along with the continuity
plans.
Software: The classification of the software assets could be done as the application
software and system software (Olson and Wu 2015). The application software performs the
implementation of the rules of the business of the organisation. The integrity of the
application software is significantly crucial for the proper working of the organisation.
Physical assets: The physical assets of the organisation comprises of the computer
equipment, equipment of communication, storage media, fixtures and furniture and the
technical equipment (Glendon and Clarke 2015). The computer equipment includes
mainframe computers, desktops and notebook computers.
Services: This comprises of the computing services that have been outsourced by the
organisation, the communication services like the data communications, voice
communication, the value-added services and the wide area network and the environmental
conditioning services like the heating, air conditioning, lighting and the power (Haimes
2015).
Weighted factor analysis
Information
asset
Criteria 1:
impact to
revenue
Criteria 2:
impact to
profitability
Criteria 3:
impact to public
image
Weighted score
6
RISK MANAGEMENT
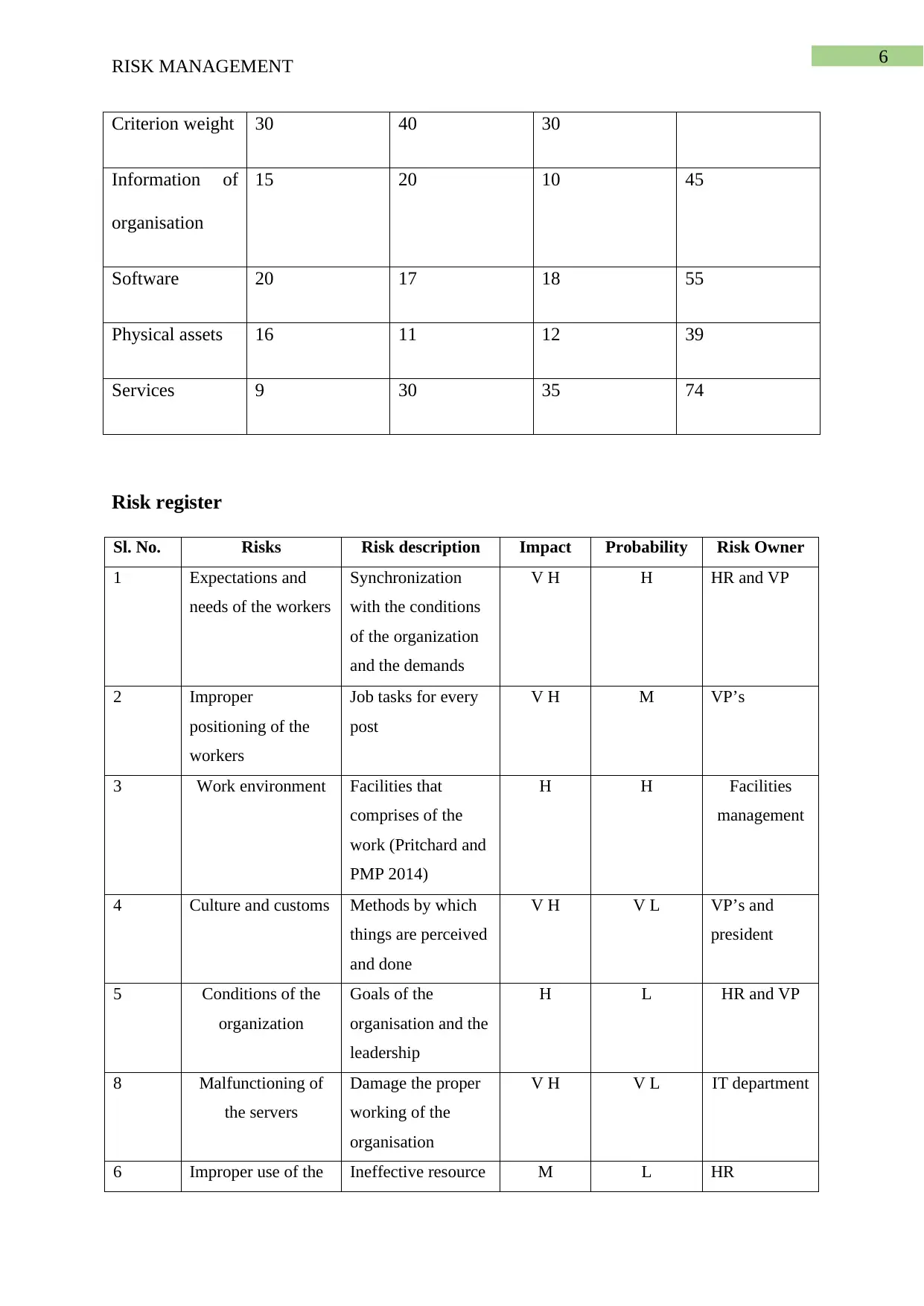
Criterion weight 30 40 30
Information of
organisation
15 20 10 45
Software 20 17 18 55
Physical assets 16 11 12 39
Services 9 30 35 74
Risk register
Sl. No. Risks Risk description Impact Probability Risk Owner
1 Expectations and
needs of the workers
Synchronization
with the conditions
of the organization
and the demands
V H H HR and VP
2 Improper
positioning of the
workers
Job tasks for every
post
V H M VP’s
3 Work environment Facilities that
comprises of the
work (Pritchard and
PMP 2014)
H H Facilities
management
4 Culture and customs Methods by which
things are perceived
and done
V H V L VP’s and
president
5 Conditions of the
organization
Goals of the
organisation and the
leadership
H L HR and VP
8 Malfunctioning of
the servers
Damage the proper
working of the
organisation
V H V L IT department
6 Improper use of the Ineffective resource M L HR
RISK MANAGEMENT
Criterion weight 30 40 30
Information of
organisation
15 20 10 45
Software 20 17 18 55
Physical assets 16 11 12 39
Services 9 30 35 74
Risk register
Sl. No. Risks Risk description Impact Probability Risk Owner
1 Expectations and
needs of the workers
Synchronization
with the conditions
of the organization
and the demands
V H H HR and VP
2 Improper
positioning of the
workers
Job tasks for every
post
V H M VP’s
3 Work environment Facilities that
comprises of the
work (Pritchard and
PMP 2014)
H H Facilities
management
4 Culture and customs Methods by which
things are perceived
and done
V H V L VP’s and
president
5 Conditions of the
organization
Goals of the
organisation and the
leadership
H L HR and VP
8 Malfunctioning of
the servers
Damage the proper
working of the
organisation
V H V L IT department
6 Improper use of the Ineffective resource M L HR
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
RISK MANAGEMENT
resources management
7 Malware attacks Theft of the data in
the database
H V L IT department
9 Improper
management
Less experienced
manager
H M Manager and
management
team
10 Lack in resources Less experienced
manager
L V L Resource
Manager
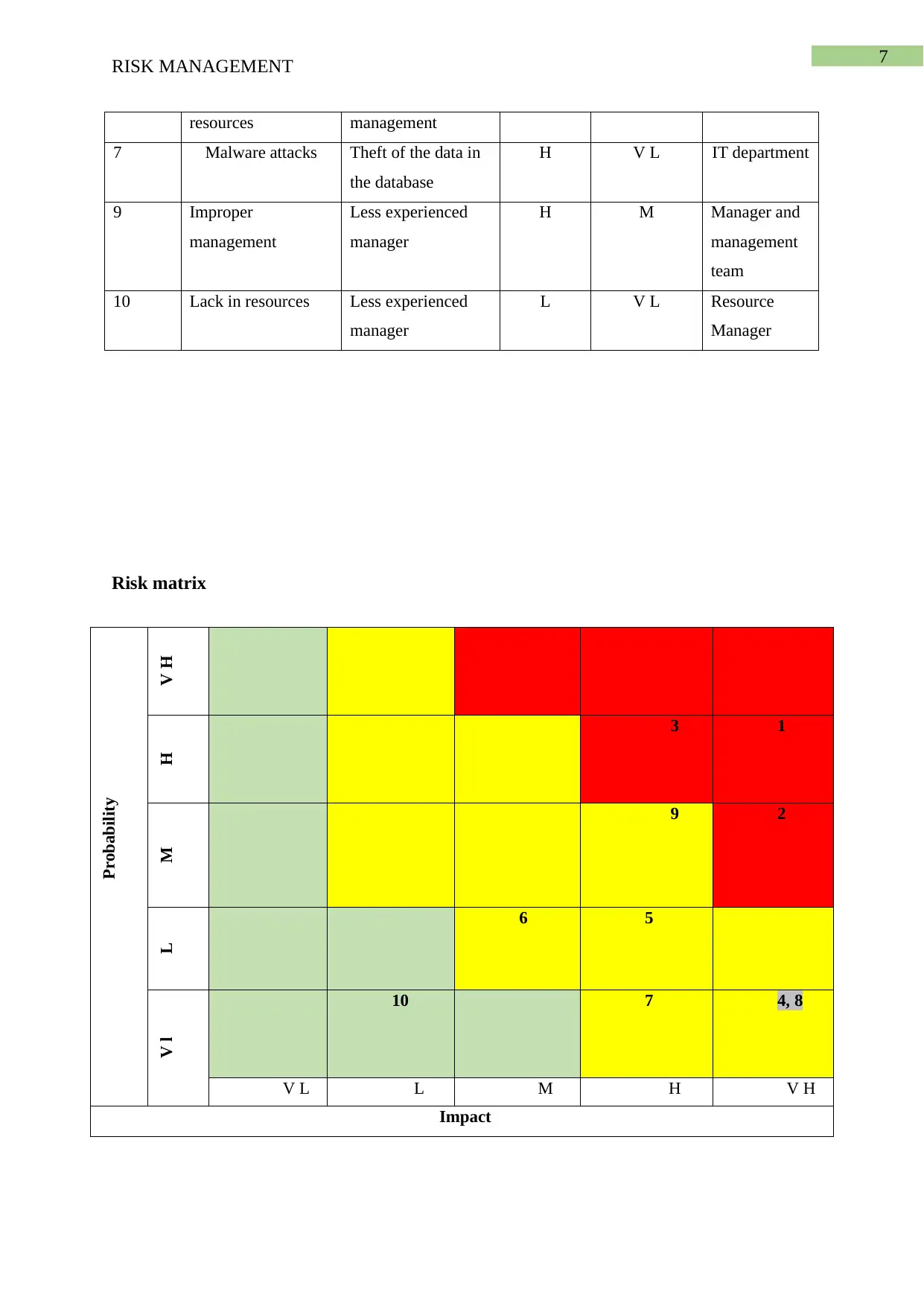
Risk matrix
Probability
V HH
3 1
M
9 2
L
6 5
V l
10 7 4, 8
V L L M H V H
Impact
RISK MANAGEMENT
resources management
7 Malware attacks Theft of the data in
the database
H V L IT department
9 Improper
management
Less experienced
manager
H M Manager and
management
team
10 Lack in resources Less experienced
manager
L V L Resource
Manager
Risk matrix
Probability
V HH
3 1
M
9 2
L
6 5
V l
10 7 4, 8
V L L M H V H
Impact

8
RISK MANAGEMENT
Risk control strategy
The risk control strategy for the identified risks are:
Risk of improper identification of the expectation of the workers: It might lead to the
loss of the workers and the basic needs of the workers could not be fulfilled (Hillson and
Murray-Webster 2017). The control for this risk is the constant interactive discussions with
the workers and then perceive about the basic needs of the workers. It might help in gaining
the proper insight into the basic needs of the workers.
The control strategy for the improper positioning of the skilled workers is the
allocation of the proper job roles for the workers of the organisation and provide the job roles
that the workers are most fit for (Hopkin 2018). The inexperienced workers must be provided
with the tasks from which they could gain significant advantage and the skilled workers must
be providedwith theimportanttasks.
The control strategy for the improper work environment could be a hospitable
environment of working in the organisation and keep the workers interested in their job by
providing the incentives (Lam 2014).
The control strategy for the malfunctioning of the servers could be the implementation
of the testing team for the servers regularly and maintain the constant updating the servers
and implement the most personalised security measures for preventing the unauthorised users
from accessing the servers of the organisation.
The control strategy for the malware attacks could be the implementation of the strict
and robust antivirus software for detecting the malware attacks and mitigate the effects of the
attacks before these attacks have rendered serious damage on the files of the organisation.
The files and the documents that have not been used for a significant long time must be
RISK MANAGEMENT
Risk control strategy
The risk control strategy for the identified risks are:
Risk of improper identification of the expectation of the workers: It might lead to the
loss of the workers and the basic needs of the workers could not be fulfilled (Hillson and
Murray-Webster 2017). The control for this risk is the constant interactive discussions with
the workers and then perceive about the basic needs of the workers. It might help in gaining
the proper insight into the basic needs of the workers.
The control strategy for the improper positioning of the skilled workers is the
allocation of the proper job roles for the workers of the organisation and provide the job roles
that the workers are most fit for (Hopkin 2018). The inexperienced workers must be provided
with the tasks from which they could gain significant advantage and the skilled workers must
be providedwith theimportanttasks.
The control strategy for the improper work environment could be a hospitable
environment of working in the organisation and keep the workers interested in their job by
providing the incentives (Lam 2014).
The control strategy for the malfunctioning of the servers could be the implementation
of the testing team for the servers regularly and maintain the constant updating the servers
and implement the most personalised security measures for preventing the unauthorised users
from accessing the servers of the organisation.
The control strategy for the malware attacks could be the implementation of the strict
and robust antivirus software for detecting the malware attacks and mitigate the effects of the
attacks before these attacks have rendered serious damage on the files of the organisation.
The files and the documents that have not been used for a significant long time must be

9
RISK MANAGEMENT
removed and prevent the infection of the files with virus (Rampini, Sufi and Viswanathan
2014.).
The control strategy for the risk of lack of resources could be the implementation of
the proper HR department that could function appropriately for the organisation and provide
the extensive management of the resources of the organisation and prevent the misuse of the
anyresource (Sadgrove 2016). It would help the organisation to save significant capital and
utilise the capital in other departments.
Conclusion
Therefore, it can be concluded that the organisation comprise of several
vulnerabilities and faces some threats that could lead to serious damage to the working of the
organisation. Some of the vulnerabilities of the organisation comprises of the SQL injections,
Vulnerabilities due to the reuse of the passwords, Outdated patches, Custom crafted URL
queries and the misconfigured settings of the servers and the Developed software and in-
house designing. These vulnerabilities might be exploited by unauthorised users and pose a
significant threat to the proper working of the organisation. The major threats that are faced
by the organisation are Technology with the weaker security, Social media attacks, Cyber
criminals, Malicious insider, Unintentional breaches, and Technological failures. These
threats could impact at the highest level for the ABC organisation,and sensitive data might be
lost that could not be retrieved easily,and significant capital might be lost.There are several
risks that are faced by the organisation that could impact severely on the working of the
organisation and the mitigation strategies for the risks are provided in the risk control strategy
as it would help in understanding the methods by which the impact of the risks could be
minimised.
RISK MANAGEMENT
removed and prevent the infection of the files with virus (Rampini, Sufi and Viswanathan
2014.).
The control strategy for the risk of lack of resources could be the implementation of
the proper HR department that could function appropriately for the organisation and provide
the extensive management of the resources of the organisation and prevent the misuse of the
anyresource (Sadgrove 2016). It would help the organisation to save significant capital and
utilise the capital in other departments.
Conclusion
Therefore, it can be concluded that the organisation comprise of several
vulnerabilities and faces some threats that could lead to serious damage to the working of the
organisation. Some of the vulnerabilities of the organisation comprises of the SQL injections,
Vulnerabilities due to the reuse of the passwords, Outdated patches, Custom crafted URL
queries and the misconfigured settings of the servers and the Developed software and in-
house designing. These vulnerabilities might be exploited by unauthorised users and pose a
significant threat to the proper working of the organisation. The major threats that are faced
by the organisation are Technology with the weaker security, Social media attacks, Cyber
criminals, Malicious insider, Unintentional breaches, and Technological failures. These
threats could impact at the highest level for the ABC organisation,and sensitive data might be
lost that could not be retrieved easily,and significant capital might be lost.There are several
risks that are faced by the organisation that could impact severely on the working of the
organisation and the mitigation strategies for the risks are provided in the risk control strategy
as it would help in understanding the methods by which the impact of the risks could be
minimised.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
RISK MANAGEMENT
RISK MANAGEMENT

11
RISK MANAGEMENT
Bibliography
Aven, T. and Zio, E., 2014. Foundational issues in risk assessment and risk
management. Risk Analysis, 34(7), pp.1164-1172.
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Bessis, J., 2015. Risk management in banking. John Wiley & Sons.
Bromiley, P., McShane, M., Nair, A. and Rustambekov, E., 2015. Enterprise risk
management: Review, critique, and research directions. Long range planning, 48(4), pp.265-
276.
Chance, D.M. and Brooks, R., 2015. Introduction to derivatives and risk management.
Cengage Learning.
Farrell, M. and Gallagher, R., 2015. The valuation implications of enterprise risk
management maturity. Journal of Risk and Insurance, 82(3), pp.625-657.
Glendon, A.I. and Clarke, S., 2015. Human safety and risk management: A psychological
perspective. Crc Press.
Haimes, Y.Y., 2015. Risk modeling, assessment, and management. John Wiley & Sons.
Hillson, D. and Murray-Webster, R., 2017. Understanding and managing risk attitude.
Routledge.
Hopkin, P., 2018. Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Lam, J., 2014. Enterprise risk management: from incentives to controls. John Wiley & Sons.
RISK MANAGEMENT
Bibliography
Aven, T. and Zio, E., 2014. Foundational issues in risk assessment and risk
management. Risk Analysis, 34(7), pp.1164-1172.
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Bessis, J., 2015. Risk management in banking. John Wiley & Sons.
Bromiley, P., McShane, M., Nair, A. and Rustambekov, E., 2015. Enterprise risk
management: Review, critique, and research directions. Long range planning, 48(4), pp.265-
276.
Chance, D.M. and Brooks, R., 2015. Introduction to derivatives and risk management.
Cengage Learning.
Farrell, M. and Gallagher, R., 2015. The valuation implications of enterprise risk
management maturity. Journal of Risk and Insurance, 82(3), pp.625-657.
Glendon, A.I. and Clarke, S., 2015. Human safety and risk management: A psychological
perspective. Crc Press.
Haimes, Y.Y., 2015. Risk modeling, assessment, and management. John Wiley & Sons.
Hillson, D. and Murray-Webster, R., 2017. Understanding and managing risk attitude.
Routledge.
Hopkin, P., 2018. Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Lam, J., 2014. Enterprise risk management: from incentives to controls. John Wiley & Sons.

12
RISK MANAGEMENT
McNeil, A.J., Frey, R. and Embrechts, P., 2015. Quantitative Risk Management: Concepts,
Techniques and Tools-revised edition. Princeton university press.
Olson, D.L. and Wu, D.D., 2015. Enterprise risk management(Vol. 3). World Scientific
Publishing Company.
Pritchard, C.L. and PMP, P.R., 2014. Risk management: concepts and guidance. Auerbach
Publications.
Rampini, A.A., Sufi, A. and Viswanathan, S., 2014. Dynamic risk management. Journal of
Financial Economics, 111(2), pp.271-296.
Sadgrove, K., 2016. The complete guide to business risk management. Routledge.
RISK MANAGEMENT
McNeil, A.J., Frey, R. and Embrechts, P., 2015. Quantitative Risk Management: Concepts,
Techniques and Tools-revised edition. Princeton university press.
Olson, D.L. and Wu, D.D., 2015. Enterprise risk management(Vol. 3). World Scientific
Publishing Company.
Pritchard, C.L. and PMP, P.R., 2014. Risk management: concepts and guidance. Auerbach
Publications.
Rampini, A.A., Sufi, A. and Viswanathan, S., 2014. Dynamic risk management. Journal of
Financial Economics, 111(2), pp.271-296.
Sadgrove, K., 2016. The complete guide to business risk management. Routledge.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





