Risk Management: A Practical Guide
VerifiedAdded on 2020/03/02
|15
|2687
|458
AI Summary
This assignment delves into the fundamental principles of risk management. It explores various stages involved in managing risks, such as identifying potential threats, analyzing their impact, assessing the likelihood of occurrence, developing mitigation strategies, and implementing control measures. The emphasis is on understanding how to effectively manage risks in projects and organizations.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: RISK MANAGEMENT
Risk Management: VIC
Government
Risk Management: VIC
Government
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2
RISK MANAGEMENT
Table of Contents
1. Introduction......................................................................................................................................3
2. Security Risk and Concern in Victoria Government........................................................................3
3. Detailed Explanation of the Diagram...............................................................................................4
3.1 Explanation of the diagram........................................................................................................4
3.2 Risk Exposure Area........................................................................................................................5
4. Analysis of Deliberate and Accidental threats.................................................................................8
4.1 Comparison between Deliberate and Accidental Threats..........................................................8
4. 2 Ranking and Justification of the Threats...................................................................................9
5. Challenges faced by Victoria Government....................................................................................10
6. Difference between Risks and Uncertainty....................................................................................11
7. Risk Control and Mitigation...........................................................................................................12
8. Conclusion......................................................................................................................................13
References..........................................................................................................................................14
RISK MANAGEMENT
Table of Contents
1. Introduction......................................................................................................................................3
2. Security Risk and Concern in Victoria Government........................................................................3
3. Detailed Explanation of the Diagram...............................................................................................4
3.1 Explanation of the diagram........................................................................................................4
3.2 Risk Exposure Area........................................................................................................................5
4. Analysis of Deliberate and Accidental threats.................................................................................8
4.1 Comparison between Deliberate and Accidental Threats..........................................................8
4. 2 Ranking and Justification of the Threats...................................................................................9
5. Challenges faced by Victoria Government....................................................................................10
6. Difference between Risks and Uncertainty....................................................................................11
7. Risk Control and Mitigation...........................................................................................................12
8. Conclusion......................................................................................................................................13
References..........................................................................................................................................14
3
RISK MANAGEMENT
1. Introduction
Victorian Government mainly offers various services as well as information to public based
on various services in a single place. Apart from that, the Government mainly stores different
information regarding events, services related to the VIC. However, the Government also stores all
types of relevant information of events, different services present in Victoria. Apart from that, it
also discussed of different facilities that mainly includes both website and application of Victorian
Public Services that mainly stored in the information system of VIC Government. It also discussed
that both data stores and information security in information system of VIC Government and
different policies of framework as well as security techniques mainly prepared and developed to
prevent and secure all types of threats and security of information system.
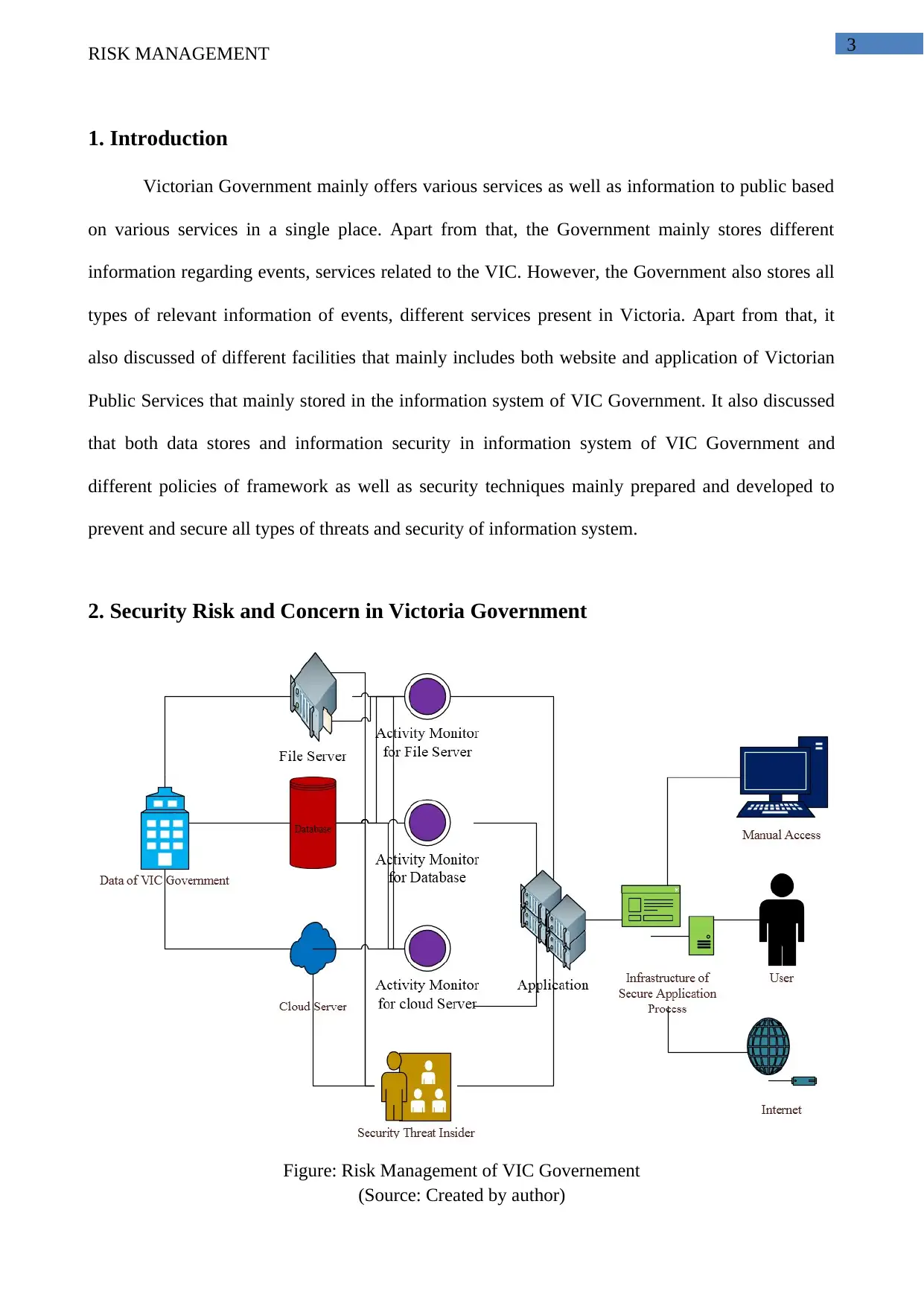
2. Security Risk and Concern in Victoria Government
Figure: Risk Management of VIC Governement
(Source: Created by author)
RISK MANAGEMENT
1. Introduction
Victorian Government mainly offers various services as well as information to public based
on various services in a single place. Apart from that, the Government mainly stores different
information regarding events, services related to the VIC. However, the Government also stores all
types of relevant information of events, different services present in Victoria. Apart from that, it
also discussed of different facilities that mainly includes both website and application of Victorian
Public Services that mainly stored in the information system of VIC Government. It also discussed
that both data stores and information security in information system of VIC Government and
different policies of framework as well as security techniques mainly prepared and developed to
prevent and secure all types of threats and security of information system.
2. Security Risk and Concern in Victoria Government
Figure: Risk Management of VIC Governement
(Source: Created by author)

4
RISK MANAGEMENT
3. Detailed Explanation of the Diagram
3.1 Explanation of the diagram
The Victorian Government mainly introduced different norms and policies to protect all data as well
as information that mainly stored in the information system (McNeil, Frey & Embrechts, 2015).
The Government is mainly related with all types of legal and sensitive information of public sector.
It also discussed that all types of concern and risks are not contrasting than other information
system used in both public and private sectors. The identification and evaluation of all associated
issues and risks of VIC Government assists all employees to reduce and manage the impacts of
system (Kerzner, 2013). Some of the important factors that mainly pointed out in the picture are
listed below:
VIC Government: Victorian Government is one the significant administrative authority that
mainly functional in Victoria, Australia. It also collects and stores all types of significant and
sensitive information of different public sectors and agencies. It also employs different types
obligations detailing the data security (Kendrick, 2015). All sensitive information mainly consists of
different personal information that mainly obtained from Government and other public sectors. The
Government also applied different types of security practices and measures as well as different
management framework regarding different risks connected with information system.
Internal Risks: Some of the internal risks become vital threats of information system and
sensitive data becomes the source from the functional and operational area of Victorian
Government. The internal risks that mainly related with VIC Government becomes deliberate for
the negative impact of information that stored in information warehouse. Some of the information
risks includes Software Failure, Malicious code, Network failure, Hardware failure, Misuse of
system, Data losses, Data Theft, Social Engineering as well as Unauthorized access. All the internal
RISK MANAGEMENT
3. Detailed Explanation of the Diagram
3.1 Explanation of the diagram
The Victorian Government mainly introduced different norms and policies to protect all data as well
as information that mainly stored in the information system (McNeil, Frey & Embrechts, 2015).
The Government is mainly related with all types of legal and sensitive information of public sector.
It also discussed that all types of concern and risks are not contrasting than other information
system used in both public and private sectors. The identification and evaluation of all associated
issues and risks of VIC Government assists all employees to reduce and manage the impacts of
system (Kerzner, 2013). Some of the important factors that mainly pointed out in the picture are
listed below:
VIC Government: Victorian Government is one the significant administrative authority that
mainly functional in Victoria, Australia. It also collects and stores all types of significant and
sensitive information of different public sectors and agencies. It also employs different types
obligations detailing the data security (Kendrick, 2015). All sensitive information mainly consists of
different personal information that mainly obtained from Government and other public sectors. The
Government also applied different types of security practices and measures as well as different
management framework regarding different risks connected with information system.
Internal Risks: Some of the internal risks become vital threats of information system and
sensitive data becomes the source from the functional and operational area of Victorian
Government. The internal risks that mainly related with VIC Government becomes deliberate for
the negative impact of information that stored in information warehouse. Some of the information
risks includes Software Failure, Malicious code, Network failure, Hardware failure, Misuse of
system, Data losses, Data Theft, Social Engineering as well as Unauthorized access. All the internal
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5
RISK MANAGEMENT
risks that mainly associated with information system needed more attention as they rise within the
VIC Government.
External Risks: All types of risks that mainly related with information system are
characterized on the basis of different types of generating sources. All the external risks of VIC
Government are mainly characterized as threats which mainly generated outside of operational and
functional environment of the Victorian Government. Some of the risks that mainly related in
project include data misuse, hacking, malicious code, financial frauds, SQL injection, intrusion,
DdoS etc.
System Requirement: It also identified that all types of risks management strategies and the
proper information system are the two important requirements based on developed picture of the
VIC Government. In addition to this, it also highlighted that data integrity, data confidentiality
become the basic requirement to provide proper stream of information that also reduce the
percentage of associated risks. Apart from different frameworks and policies, VIC Government
become vital in both external and internal risks that mainly affects the information system.
However, to manage as well as secure all types of risks, different strategies of risks identification,
management and mitigation are mainly getting identified.
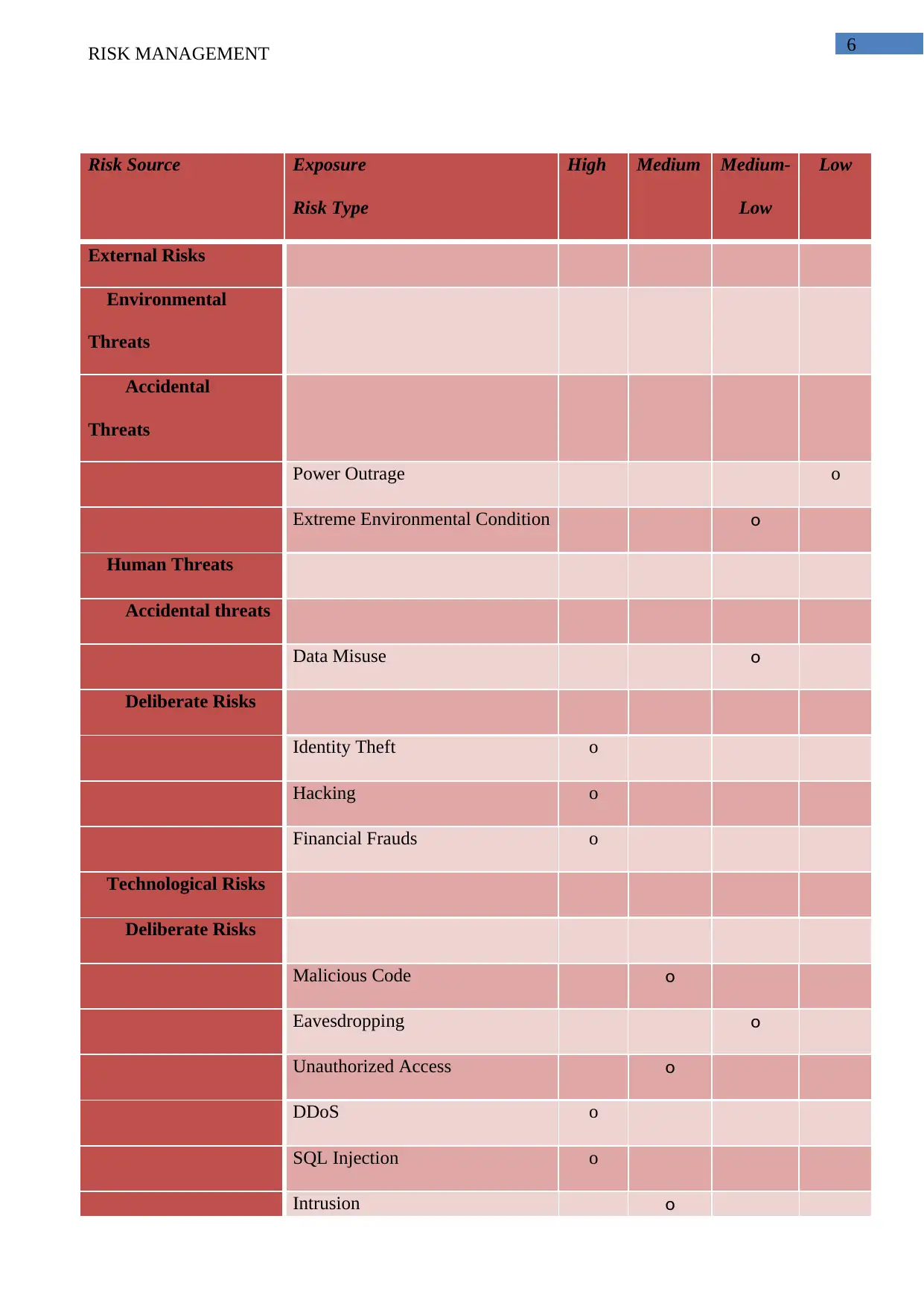
3.2 Risk Exposure Area
Kerzner (2013) discussed that, all assessment of different identified risks that mainly assists to
develop and evaluate all risks management strategies and framework of VIC Government. The
identification of proper exposure risks provides better evaluation of the both potential and impact of
risks regarding information system. Depending on identified risks for VIC Government, exposure of
risks are get characterized in 4 important domain that includes all high, medium, low etc. Below
table provide the proper picture of exposure of all identified risks:
RISK MANAGEMENT
risks that mainly associated with information system needed more attention as they rise within the
VIC Government.
External Risks: All types of risks that mainly related with information system are
characterized on the basis of different types of generating sources. All the external risks of VIC
Government are mainly characterized as threats which mainly generated outside of operational and
functional environment of the Victorian Government. Some of the risks that mainly related in
project include data misuse, hacking, malicious code, financial frauds, SQL injection, intrusion,
DdoS etc.
System Requirement: It also identified that all types of risks management strategies and the
proper information system are the two important requirements based on developed picture of the
VIC Government. In addition to this, it also highlighted that data integrity, data confidentiality
become the basic requirement to provide proper stream of information that also reduce the
percentage of associated risks. Apart from different frameworks and policies, VIC Government
become vital in both external and internal risks that mainly affects the information system.
However, to manage as well as secure all types of risks, different strategies of risks identification,
management and mitigation are mainly getting identified.
3.2 Risk Exposure Area
Kerzner (2013) discussed that, all assessment of different identified risks that mainly assists to
develop and evaluate all risks management strategies and framework of VIC Government. The
identification of proper exposure risks provides better evaluation of the both potential and impact of
risks regarding information system. Depending on identified risks for VIC Government, exposure of
risks are get characterized in 4 important domain that includes all high, medium, low etc. Below
table provide the proper picture of exposure of all identified risks:
6
RISK MANAGEMENT
Risk Source Exposure
Risk Type
High Medium Medium-
Low
Low
External Risks
Environmental
Threats
Accidental
Threats
Power Outrage o
Extreme Environmental Condition o
Human Threats
Accidental threats
Data Misuse o
Deliberate Risks
Identity Theft o
Hacking o
Financial Frauds o
Technological Risks
Deliberate Risks
Malicious Code o
Eavesdropping o
Unauthorized Access o
DDoS o
SQL Injection o
Intrusion o
RISK MANAGEMENT
Risk Source Exposure
Risk Type
High Medium Medium-
Low
Low
External Risks
Environmental
Threats
Accidental
Threats
Power Outrage o
Extreme Environmental Condition o
Human Threats
Accidental threats
Data Misuse o
Deliberate Risks
Identity Theft o
Hacking o
Financial Frauds o
Technological Risks
Deliberate Risks
Malicious Code o
Eavesdropping o
Unauthorized Access o
DDoS o
SQL Injection o
Intrusion o
7
RISK MANAGEMENT
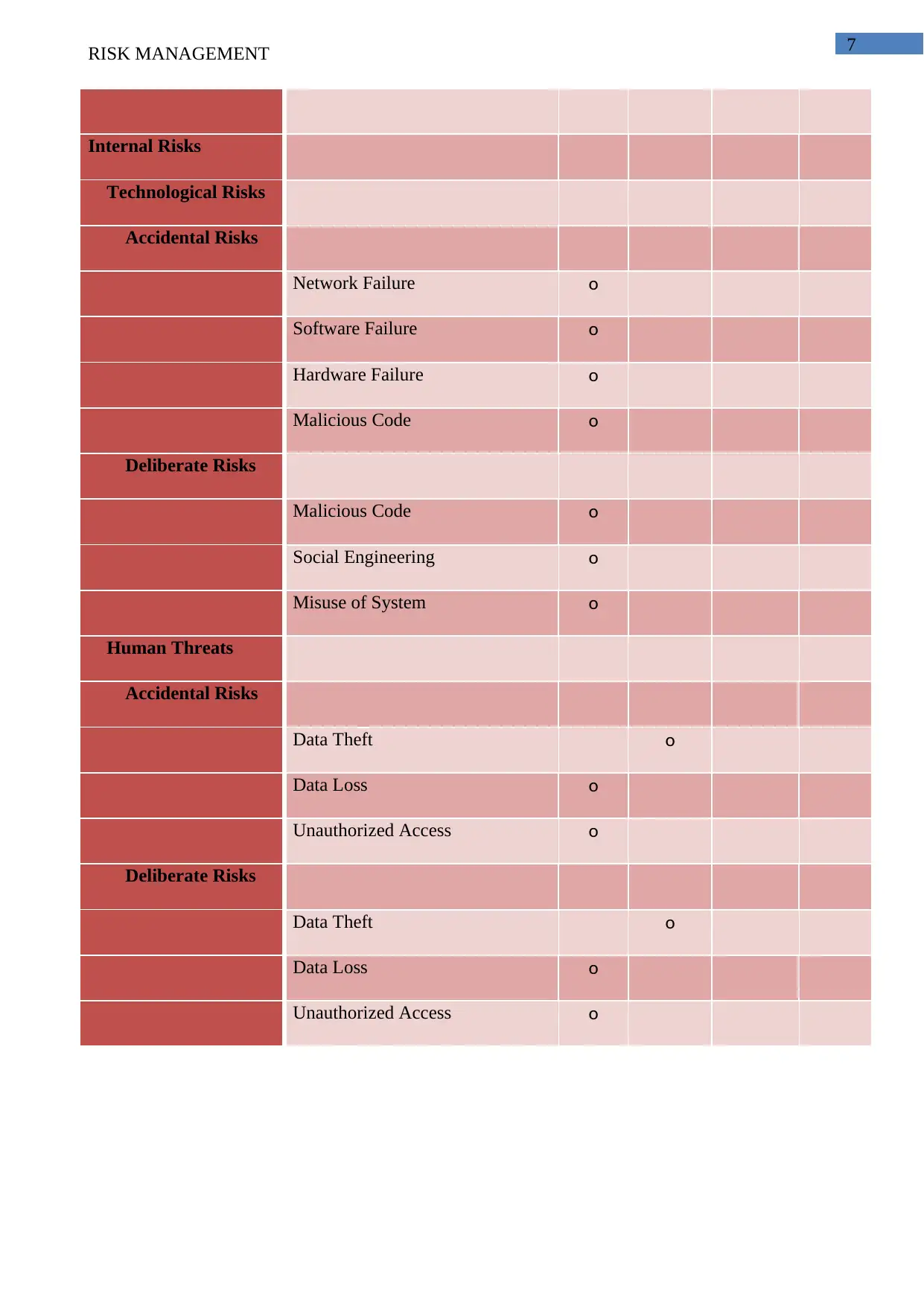
Internal Risks
Technological Risks
Accidental Risks
Network Failure o
Software Failure o
Hardware Failure o
Malicious Code o
Deliberate Risks
Malicious Code o
Social Engineering o
Misuse of System o
Human Threats
Accidental Risks
Data Theft o
Data Loss o
Unauthorized Access o
Deliberate Risks
Data Theft o
Data Loss o
Unauthorized Access o
RISK MANAGEMENT
Internal Risks
Technological Risks
Accidental Risks
Network Failure o
Software Failure o
Hardware Failure o
Malicious Code o
Deliberate Risks
Malicious Code o
Social Engineering o
Misuse of System o
Human Threats
Accidental Risks
Data Theft o
Data Loss o
Unauthorized Access o
Deliberate Risks
Data Theft o
Data Loss o
Unauthorized Access o
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
RISK MANAGEMENT
4. Analysis of Deliberate and Accidental threats
4.1 Comparison between Deliberate and Accidental Threats
All types of threats and security risks become one of the unavoidable and necessary parts of the
information system. Some risks that are mainly identified as deliberate and accidental in criteria
based on the information system of VIC Government.
Deliberate Threats: In this type of threat, Jouini et al., (2014) mainly discussed that the information
system as one of the wilful modifications and destruction, manipulation as well as creation of
negative effect. Deliberate action also discussed that any person willingly tries to create any
negative impact in the organization. Apart from that, Hopkin (2017) also pointed out that all
deliberate threats of the information system are become the important source of the outside of VIC
Government. This type of risks are more easier in order to do identification of security framework
and management application that mainly developed for information system based on all activities
and vulnerabilities associate with deliberate risks. This type of risk also includes different types of
financial frauds, SQL injection, DdoS, unauthorised access and different others.
Accidental Threats: It is mainly defined that the accidental risks to information becomes threats that
mainly occurs without the knowledge of risk owners. Apart from that, Lopes and Oliveira. (2014,
March) also pointed out that accidental risks creates some negative impact based on information
security. Apart from that, Haimes, (2015) also claimed there are no technology that mainly prevents
all types of accidental threats to get occurred.
According to various researchers, it is mainly discussed that the organization mainly experienced
numerous data losses incidence because of accidental threats. Some of the threats include
programming errors, malware attacks, programming errors, viruses are some of the common
accidental threats.
RISK MANAGEMENT
4. Analysis of Deliberate and Accidental threats
4.1 Comparison between Deliberate and Accidental Threats
All types of threats and security risks become one of the unavoidable and necessary parts of the
information system. Some risks that are mainly identified as deliberate and accidental in criteria
based on the information system of VIC Government.
Deliberate Threats: In this type of threat, Jouini et al., (2014) mainly discussed that the information
system as one of the wilful modifications and destruction, manipulation as well as creation of
negative effect. Deliberate action also discussed that any person willingly tries to create any
negative impact in the organization. Apart from that, Hopkin (2017) also pointed out that all
deliberate threats of the information system are become the important source of the outside of VIC
Government. This type of risks are more easier in order to do identification of security framework
and management application that mainly developed for information system based on all activities
and vulnerabilities associate with deliberate risks. This type of risk also includes different types of
financial frauds, SQL injection, DdoS, unauthorised access and different others.
Accidental Threats: It is mainly defined that the accidental risks to information becomes threats that
mainly occurs without the knowledge of risk owners. Apart from that, Lopes and Oliveira. (2014,
March) also pointed out that accidental risks creates some negative impact based on information
security. Apart from that, Haimes, (2015) also claimed there are no technology that mainly prevents
all types of accidental threats to get occurred.
According to various researchers, it is mainly discussed that the organization mainly experienced
numerous data losses incidence because of accidental threats. Some of the threats include
programming errors, malware attacks, programming errors, viruses are some of the common
accidental threats.

9
RISK MANAGEMENT
All risks that mainly linked with the VIC Government are mentioned in a table format:
Risks Associated with the VIC Government
External Threats to VIC Internal Threats to VIC
Accidental Threats Deliberate Threats Accidental Threats Deliberate Threats
Power Outrage,
Extreme
Environmental
Condition, Data
Misuse
Identity Theft, Hacking,
Financial Frauds,
Malicious Code,
Eavesdropping,
Unauthorized Access,
DDoS, SQL Injection,
Intrusion
Network Failure,
Software Failure,
Hardware Failure,
Malicious Code, Data
Theft, Data Loss,
Unauthorized Access
Data Theft, Data
Loss, Unauthorized
Access, Malicious
Code, Social
Engineering,
Misuse of System
4. 2 Rank and Justification of the Threats
Rank First – Accidental Risks: In organization, accidental risks are mainly identified to have
occurrence frequency more than deliberate risks. It also showed that the accidental risk in
information system mainly happens because of negligence, occurrence and causalities that mainly
done by internal person of any organization. Verner et al. (2014) mentioned that internal risks of
information system also can be prevented by gathering information, proper guidance as well as
training and also taking acknowledgment of employees. Herbsleb and Moitra, (2001) discussed
about the example of doing the unauthorized access, misuse of information can get prevented by
following the proper application of verification as well as password protected system to the
employees. Hence, the accidental risk is mainly marked in second position these are mainly done
unintentionally by any person that causes threats to the system.
RISK MANAGEMENT
All risks that mainly linked with the VIC Government are mentioned in a table format:
Risks Associated with the VIC Government
External Threats to VIC Internal Threats to VIC
Accidental Threats Deliberate Threats Accidental Threats Deliberate Threats
Power Outrage,
Extreme
Environmental
Condition, Data
Misuse
Identity Theft, Hacking,
Financial Frauds,
Malicious Code,
Eavesdropping,
Unauthorized Access,
DDoS, SQL Injection,
Intrusion
Network Failure,
Software Failure,
Hardware Failure,
Malicious Code, Data
Theft, Data Loss,
Unauthorized Access
Data Theft, Data
Loss, Unauthorized
Access, Malicious
Code, Social
Engineering,
Misuse of System
4. 2 Rank and Justification of the Threats
Rank First – Accidental Risks: In organization, accidental risks are mainly identified to have
occurrence frequency more than deliberate risks. It also showed that the accidental risk in
information system mainly happens because of negligence, occurrence and causalities that mainly
done by internal person of any organization. Verner et al. (2014) mentioned that internal risks of
information system also can be prevented by gathering information, proper guidance as well as
training and also taking acknowledgment of employees. Herbsleb and Moitra, (2001) discussed
about the example of doing the unauthorized access, misuse of information can get prevented by
following the proper application of verification as well as password protected system to the
employees. Hence, the accidental risk is mainly marked in second position these are mainly done
unintentionally by any person that causes threats to the system.

10
RISK MANAGEMENT
Rank Second – Deliberate Risks: According to McNeil, A. J., Frey, R., and Embrechts, P. (2015),
deliberate risks mainly occur in any information system with the significance of causing negative
impact and losses. It also discussed that deliberate risks also have chances to do important harm to
both organization and system. Chance and Brooks (2015) also illustrated that in capabilities of one
organization are to do the identification, stop as well as mitigation of all types of deliberate risks
based on information system that causes organization losses in market positions, public image as
well as important negative impact. Financial fraud is one type of important deliberate risks that
occurs when any risk owner originated deliberate action to any employee due to improper financial
transaction based on personal benefits. In addition to this, Kendrick, (2015) discussed that DdoS
attacks may not causes any direct impact to financial transaction but it also limit both the
availability and operation of data that mainly impacts large financial losses.
5. Challenges faced by Victoria Government
The VIC Government is one of the public sectors that mainly operate with different events and
function. Alike with different other information system, this particular system mainly use as well as
utilize with the help Victorian Government that mainly associated with different types of threats and
risks that causes different negative impact on the organization. Apart from that, it also discussed
different risks management and mitigation strategies that mainly get implemented in information
system and also get developed based on evaluation and analysis techniques of risk impacts. On the
other hand, it is also discussed about the VIC Government that mainly developed required risk
management system and strategy to reduce and mitigate all negative effects of risks. All decisions
related to VIC Government is mainly based on the selection of supply of in-house development
based on outsourcing of different risks that associated with information system.
It also discussed that the Victorian Government is one of the governmental association that mainly
works based on personal and professional information. Hence, it also discussed that the Victorian
Government mainly shows lack age in the employees knowledge and understanding which helps to
RISK MANAGEMENT
Rank Second – Deliberate Risks: According to McNeil, A. J., Frey, R., and Embrechts, P. (2015),
deliberate risks mainly occur in any information system with the significance of causing negative
impact and losses. It also discussed that deliberate risks also have chances to do important harm to
both organization and system. Chance and Brooks (2015) also illustrated that in capabilities of one
organization are to do the identification, stop as well as mitigation of all types of deliberate risks
based on information system that causes organization losses in market positions, public image as
well as important negative impact. Financial fraud is one type of important deliberate risks that
occurs when any risk owner originated deliberate action to any employee due to improper financial
transaction based on personal benefits. In addition to this, Kendrick, (2015) discussed that DdoS
attacks may not causes any direct impact to financial transaction but it also limit both the
availability and operation of data that mainly impacts large financial losses.
5. Challenges faced by Victoria Government
The VIC Government is one of the public sectors that mainly operate with different events and
function. Alike with different other information system, this particular system mainly use as well as
utilize with the help Victorian Government that mainly associated with different types of threats and
risks that causes different negative impact on the organization. Apart from that, it also discussed
different risks management and mitigation strategies that mainly get implemented in information
system and also get developed based on evaluation and analysis techniques of risk impacts. On the
other hand, it is also discussed about the VIC Government that mainly developed required risk
management system and strategy to reduce and mitigate all negative effects of risks. All decisions
related to VIC Government is mainly based on the selection of supply of in-house development
based on outsourcing of different risks that associated with information system.
It also discussed that the Victorian Government is one of the governmental association that mainly
works based on personal and professional information. Hence, it also discussed that the Victorian
Government mainly shows lack age in the employees knowledge and understanding which helps to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

11
RISK MANAGEMENT
provide considerable information as well as supports to mitigate all identified risks of Victorian
Government.
However, it is advised that the Victorian Government is needed to farm out a team that mainly helps
to manage as well as mitigate all threats based on information system. Furthermore, it is mainly
discussed that the concerned process mainly allows the Victorian Government to decrease the work
load as well as budget to manage the associated risks in expert hand.
6. Difference between Risks and Uncertainty
According to different researchers, based on all theories as well as concepts of internet security as
well as risks both are inter-related. It also discussed that, Pieters et al., (2014) are get defined that
risks of information security of both threats and events have the potentiality to cause financial
losses. All the risks are mainly observed and identified as treat type depending on causing of
impairment and high occurrence frequencies. Apart from that, it discussed that risks are mainly
controlled supported by effective and appropriate risk management strategies. In the VIC
Government case, DdoS attack mainly considered as significant risk.
On the other side, Haimes (2015) discussed that uncertainty of any types of activities and events are
not be predicted before from the occurrence. The types of uncertain threats also causes negative
impact and financial losses based on the VIC Government Information System. Hopkin (2017)
debated that the types of events are not be predicted with the negative impact caused in any
organization which is described as uncertainties. In this VIC Government case, the environment
condition mainly includes floods, earthquakes and types of natural calamities are considered as
types of uncertainties.
RISK MANAGEMENT
provide considerable information as well as supports to mitigate all identified risks of Victorian
Government.
However, it is advised that the Victorian Government is needed to farm out a team that mainly helps
to manage as well as mitigate all threats based on information system. Furthermore, it is mainly
discussed that the concerned process mainly allows the Victorian Government to decrease the work
load as well as budget to manage the associated risks in expert hand.
6. Difference between Risks and Uncertainty
According to different researchers, based on all theories as well as concepts of internet security as
well as risks both are inter-related. It also discussed that, Pieters et al., (2014) are get defined that
risks of information security of both threats and events have the potentiality to cause financial
losses. All the risks are mainly observed and identified as treat type depending on causing of
impairment and high occurrence frequencies. Apart from that, it discussed that risks are mainly
controlled supported by effective and appropriate risk management strategies. In the VIC
Government case, DdoS attack mainly considered as significant risk.
On the other side, Haimes (2015) discussed that uncertainty of any types of activities and events are
not be predicted before from the occurrence. The types of uncertain threats also causes negative
impact and financial losses based on the VIC Government Information System. Hopkin (2017)
debated that the types of events are not be predicted with the negative impact caused in any
organization which is described as uncertainties. In this VIC Government case, the environment
condition mainly includes floods, earthquakes and types of natural calamities are considered as
types of uncertainties.
12
RISK MANAGEMENT
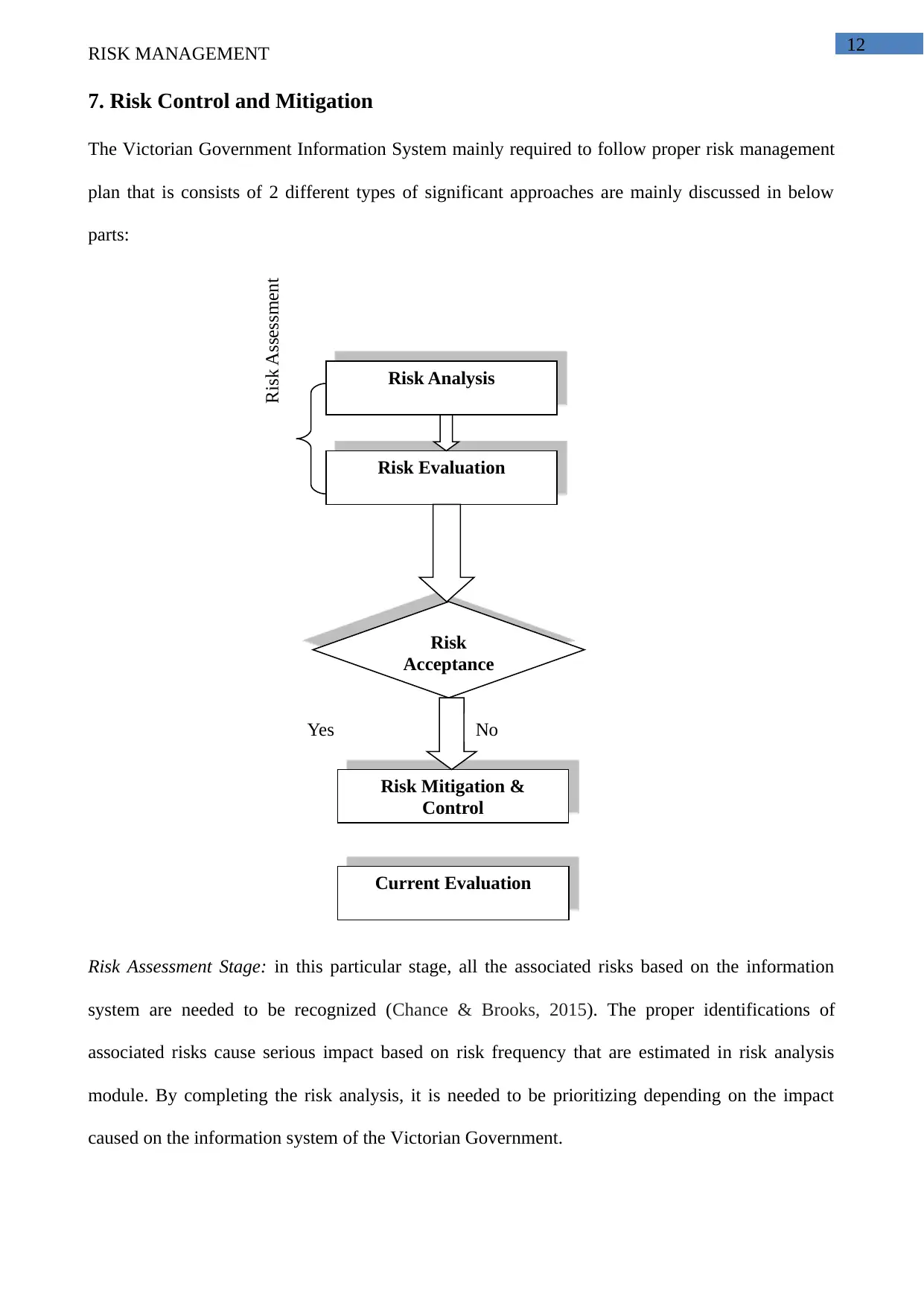
7. Risk Control and Mitigation
The Victorian Government Information System mainly required to follow proper risk management
plan that is consists of 2 different types of significant approaches are mainly discussed in below
parts:
Risk Assessment Stage: in this particular stage, all the associated risks based on the information
system are needed to be recognized (Chance & Brooks, 2015). The proper identifications of
associated risks cause serious impact based on risk frequency that are estimated in risk analysis
module. By completing the risk analysis, it is needed to be prioritizing depending on the impact
caused on the information system of the Victorian Government.
Risk Analysis
Risk Evaluation
Risk Mitigation &
Control
Current Evaluation
Risk
Acceptance
Yes No
Risk Assessment
RISK MANAGEMENT
7. Risk Control and Mitigation
The Victorian Government Information System mainly required to follow proper risk management
plan that is consists of 2 different types of significant approaches are mainly discussed in below
parts:
Risk Assessment Stage: in this particular stage, all the associated risks based on the information
system are needed to be recognized (Chance & Brooks, 2015). The proper identifications of
associated risks cause serious impact based on risk frequency that are estimated in risk analysis
module. By completing the risk analysis, it is needed to be prioritizing depending on the impact
caused on the information system of the Victorian Government.
Risk Analysis
Risk Evaluation
Risk Mitigation &
Control
Current Evaluation
Risk
Acceptance
Yes No
Risk Assessment

13
RISK MANAGEMENT
Risk Control Stage: Pritchard and PMP (2014) discussed that based on proper identification and
evaluation of different security risks are mainly got associated with the Victorian Government that
needed to develop a proper mitigation plan to restrict the occurrence of risks on the information
system. After the completion of verification stage, a proper mitigation strategy is considered and
developed to do regular monitor of all associated uncertainties.
8. Conclusion
It is mainly concluded that the VIC Government information system is mainly associated with
different types of risks that will be in both accidental and deliberate in nature. Based on the detailed
analysis, it also get identified that depending on the severity of risks deliberate risks are get ranked
in first position than accidental threats. Apart from that, it also discussed that the discovery of risk
exposure of VIC Government are mainly allowed to provide risk analysis that mainly involved with
VIC information system. It also discussed that the risk management strategy is mainly taken in to
consideration to aid the Victorian Government for doing the identification as well as mitigation of
both types of risks related with this particular information system.
RISK MANAGEMENT
Risk Control Stage: Pritchard and PMP (2014) discussed that based on proper identification and
evaluation of different security risks are mainly got associated with the Victorian Government that
needed to develop a proper mitigation plan to restrict the occurrence of risks on the information
system. After the completion of verification stage, a proper mitigation strategy is considered and
developed to do regular monitor of all associated uncertainties.
8. Conclusion
It is mainly concluded that the VIC Government information system is mainly associated with
different types of risks that will be in both accidental and deliberate in nature. Based on the detailed
analysis, it also get identified that depending on the severity of risks deliberate risks are get ranked
in first position than accidental threats. Apart from that, it also discussed that the discovery of risk
exposure of VIC Government are mainly allowed to provide risk analysis that mainly involved with
VIC information system. It also discussed that the risk management strategy is mainly taken in to
consideration to aid the Victorian Government for doing the identification as well as mitigation of
both types of risks related with this particular information system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

14
RISK MANAGEMENT
References
Chance, D. M., & Brooks, R. (2015). Introduction to derivatives and risk management. Cengage
Learning.
Haimes, Y. Y. (2015). Risk modeling, assessment, and management. John Wiley & Sons.
Herbsleb, J. D., & Moitra, D. (2001). Global software development. IEEE software, 18(2), 16-20.
Hopkin, P. (2017). Fundamentals of risk management: understanding, evaluating and implementing
effective risk management. Kogan Page Publishers.
Jaeger, C. C., Webler, T., Rosa, E. A., & Renn, O. (2013). Risk, uncertainty and rational action.
Routledge.
Jouini, M., Rabai, L. B. A., & Aissa, A. B. (2014). Classification of security threats in information
systems. Procedia Computer Science, 32, 489-496.
Jouini, M., Rabai, L. B. A., & Aissa, A. B. (2014). Classification of security threats in information
systems. Procedia Computer Science, 32, 489-496.
Kendrick, T. (2015). Identifying and managing project risk: essential tools for failure-proofing your
project. AMACOM Div American Mgmt Assn.
Kerzner, H. (2013). Project management: a systems approach to planning, scheduling, and
controlling. John Wiley & Sons.
Kerzner, H. (2013). Project management: a systems approach to planning, scheduling, and
controlling. John Wiley & Sons.
Lopes, I., & Oliveira, P. (2014, March). Understanding Information Security Culture: A Survey in
Small and Medium Sized Enterprises. In WorldCIST (1)(pp. 277-286).
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Pieters, W., Lukszo, Z., Hadžiosmanović, D., & van den Berg, J. (2014). Reconciling malicious and
accidental risk in cyber security.
RISK MANAGEMENT
References
Chance, D. M., & Brooks, R. (2015). Introduction to derivatives and risk management. Cengage
Learning.
Haimes, Y. Y. (2015). Risk modeling, assessment, and management. John Wiley & Sons.
Herbsleb, J. D., & Moitra, D. (2001). Global software development. IEEE software, 18(2), 16-20.
Hopkin, P. (2017). Fundamentals of risk management: understanding, evaluating and implementing
effective risk management. Kogan Page Publishers.
Jaeger, C. C., Webler, T., Rosa, E. A., & Renn, O. (2013). Risk, uncertainty and rational action.
Routledge.
Jouini, M., Rabai, L. B. A., & Aissa, A. B. (2014). Classification of security threats in information
systems. Procedia Computer Science, 32, 489-496.
Jouini, M., Rabai, L. B. A., & Aissa, A. B. (2014). Classification of security threats in information
systems. Procedia Computer Science, 32, 489-496.
Kendrick, T. (2015). Identifying and managing project risk: essential tools for failure-proofing your
project. AMACOM Div American Mgmt Assn.
Kerzner, H. (2013). Project management: a systems approach to planning, scheduling, and
controlling. John Wiley & Sons.
Kerzner, H. (2013). Project management: a systems approach to planning, scheduling, and
controlling. John Wiley & Sons.
Lopes, I., & Oliveira, P. (2014, March). Understanding Information Security Culture: A Survey in
Small and Medium Sized Enterprises. In WorldCIST (1)(pp. 277-286).
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative risk management: Concepts,
techniques and tools. Princeton university press.
Pieters, W., Lukszo, Z., Hadžiosmanović, D., & van den Berg, J. (2014). Reconciling malicious and
accidental risk in cyber security.
15
RISK MANAGEMENT
Pritchard, C. L., & PMP, P. R. (2014). Risk management: concepts and guidance. CRC Press.
Verner, J. M., Brereton, O. P., Kitchenham, B. A., Turner, M., & Niazi, M. (2014). Risks and risk
mitigation in global software development: A tertiary study. Information and Software
Technology, 56(1), 54-78.
RISK MANAGEMENT
Pritchard, C. L., & PMP, P. R. (2014). Risk management: concepts and guidance. CRC Press.
Verner, J. M., Brereton, O. P., Kitchenham, B. A., Turner, M., & Niazi, M. (2014). Risks and risk
mitigation in global software development: A tertiary study. Information and Software
Technology, 56(1), 54-78.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





