Risk Perception and Analysis in Cyber Risk
VerifiedAdded on 2023/03/17
|13
|3748
|28
AI Summary
This document discusses the topic of Risk Perception and Analysis in the context of Cyber Risk. It explores the risks faced by healthcare facilities, particularly in terms of patient privacy and electronic service delivery. The document highlights the importance of cyber vulnerability and the need for risk parameters and factors to compare risks. It also discusses the practical utility of scales and provides insights into the possible outcomes of cyber attacks. Additionally, the document touches upon the threat of cyber terrorism in the healthcare sector.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Risk Perception and Analysis
Cyber Risk
Student`s Name
Institutional Affiliation
Cyber Risk
Student`s Name
Institutional Affiliation
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Risk Perception and Analysis
Topic 1: Listing Risks and Their Relative Significance
1. Define the Risk carefully
The world is ever changing and adapting, with current day technology influencing even the
healthcare centre. The standing promise being that more efficient and reliable service
delivery can be done but it also poses a great cyber risk especially in regards to patient
privacy and electronic health care delivery (Wetsman, 2019).
The cyber risk faces the healthcare sector especially in regards to patient privacy, electronic
service delivery, and even critical system shutdown. This is all due to the inevitable
connection to the internet, thus opening a window for cybercriminals and also other
organizations to access a health care facility's records and operation schemes (Infosec
Resources, 2019). In 2015, the healthcare industry was the most attacked by cybercriminals,
over 100 million healthcare records were compromised during that year, from more than
8,000 devices in more than 100 countries (Infosec Resources, 2019). The question therefore
is, why is this a threat to the healthcare system?
With roughly 8 out every 10 healthcare institutions being hit with two or more data breaches
between 2014 and 2015, the clients are in risk of theft and hacking. The healthcare centres are
also sued for not being able to maintain that client privacy and thus lose a lot of money, data
hacks can also lead to the inevitable shutdown of critical systems in the healthcare facility
bringing client service to a standstill which may lead to crowding in hospitals and even the
likelihood of death for some patients (Argaw, Bempong, Eshaya-Chauvin, and Flahault,
2019). With demand in the black market for more and more Electronic Health Records,
healthcare facilities have become prime targets for cybercriminals looking for an easy payout,
these records are later on utilized to create fake IDs and passports, or even file counterfeit
claims to the client’s medical insurers (Conaty-Buck, 2017).
2. What Risk parameters would you use to describe this Risk in a manner that enabled
it to be compared in significance with other Risks of a different nature? Briefly explain
your reasons for choosing them and for not choosing others.
The risk of cyber vulnerability in health care facilities is of primary importance due to the
ignorance that most people have towards it; therefore before anyone notices the "leak", it is
far too late to pick themselves up again. There have been very minimal investments put in by
Topic 1: Listing Risks and Their Relative Significance
1. Define the Risk carefully
The world is ever changing and adapting, with current day technology influencing even the
healthcare centre. The standing promise being that more efficient and reliable service
delivery can be done but it also poses a great cyber risk especially in regards to patient
privacy and electronic health care delivery (Wetsman, 2019).
The cyber risk faces the healthcare sector especially in regards to patient privacy, electronic
service delivery, and even critical system shutdown. This is all due to the inevitable
connection to the internet, thus opening a window for cybercriminals and also other
organizations to access a health care facility's records and operation schemes (Infosec
Resources, 2019). In 2015, the healthcare industry was the most attacked by cybercriminals,
over 100 million healthcare records were compromised during that year, from more than
8,000 devices in more than 100 countries (Infosec Resources, 2019). The question therefore
is, why is this a threat to the healthcare system?
With roughly 8 out every 10 healthcare institutions being hit with two or more data breaches
between 2014 and 2015, the clients are in risk of theft and hacking. The healthcare centres are
also sued for not being able to maintain that client privacy and thus lose a lot of money, data
hacks can also lead to the inevitable shutdown of critical systems in the healthcare facility
bringing client service to a standstill which may lead to crowding in hospitals and even the
likelihood of death for some patients (Argaw, Bempong, Eshaya-Chauvin, and Flahault,
2019). With demand in the black market for more and more Electronic Health Records,
healthcare facilities have become prime targets for cybercriminals looking for an easy payout,
these records are later on utilized to create fake IDs and passports, or even file counterfeit
claims to the client’s medical insurers (Conaty-Buck, 2017).
2. What Risk parameters would you use to describe this Risk in a manner that enabled
it to be compared in significance with other Risks of a different nature? Briefly explain
your reasons for choosing them and for not choosing others.
The risk of cyber vulnerability in health care facilities is of primary importance due to the
ignorance that most people have towards it; therefore before anyone notices the "leak", it is
far too late to pick themselves up again. There have been very minimal investments put in by

Risk Perception and Analysis
healthcare facilities into the safety of their electronic data, most of them are oblivious to the
danger that it can pose to the systems (Infosec Resources, 2019).
Amid other risks facing the healthcare sector, cybercrime is still relatively new and thus
doesn't seem to pose a significant threat, especially in third world countries, but on a grand
scale, the influence and threat it represents on more significant healthcare facilities may
create a ripple effect to the more remote hospitals. This will, later on, create a more
significant requirement for facility placement on the much smaller hospitals.
Therefore, in comparison to the other risks facing the healthcare sector, cybercrime could be
ranked lower on a threat level scale because most hospitals, especially in African countries,
have not completely moved to the more technological format of service delivery.
3. Propose both nominal and associated ordinal scales that would suite your chosen Risk
parameters given the situation in which the Risk exists
To determine how this threat may affect an institution, a nominal scale maybe is used to, first
of all, ask an institution whether they are power dependent or power independent, this is to
understand that most of their services require electricity support or provide a much more
basic form of medical aid. Secondly, an institution should be asked whether they record data
digitally or manually, this is to assess if they are capable of being attacked by cyber terrorists
(Wetsman, 2019).
If an institution can be attacked, the next question would be to assess if their data is backed
up temporarily on servers or backed up on permanent servers, this would be to determine the
vulnerability of their data and how easy it would be for a cyber-terrorist to access their data.
Lastly, it would be to know what kind of systems they have set up to protect their data from
being lost or accessed without authority; a description should be done in detail.
To obtain ordinal data, a questionnaire can be given to the staff, and more importantly the
staff in charge of data recording and the IT sector. The questionnaire would be to assess, how
satisfied they are with the method of data recording, how satisfied they are with data
protection, how they feel about their treatment on a day to day basis, how satisfied they are
about access to said data and how well are the critical systems of the institution maintained
(Wetsman, 2019).
healthcare facilities into the safety of their electronic data, most of them are oblivious to the
danger that it can pose to the systems (Infosec Resources, 2019).
Amid other risks facing the healthcare sector, cybercrime is still relatively new and thus
doesn't seem to pose a significant threat, especially in third world countries, but on a grand
scale, the influence and threat it represents on more significant healthcare facilities may
create a ripple effect to the more remote hospitals. This will, later on, create a more
significant requirement for facility placement on the much smaller hospitals.
Therefore, in comparison to the other risks facing the healthcare sector, cybercrime could be
ranked lower on a threat level scale because most hospitals, especially in African countries,
have not completely moved to the more technological format of service delivery.
3. Propose both nominal and associated ordinal scales that would suite your chosen Risk
parameters given the situation in which the Risk exists
To determine how this threat may affect an institution, a nominal scale maybe is used to, first
of all, ask an institution whether they are power dependent or power independent, this is to
understand that most of their services require electricity support or provide a much more
basic form of medical aid. Secondly, an institution should be asked whether they record data
digitally or manually, this is to assess if they are capable of being attacked by cyber terrorists
(Wetsman, 2019).
If an institution can be attacked, the next question would be to assess if their data is backed
up temporarily on servers or backed up on permanent servers, this would be to determine the
vulnerability of their data and how easy it would be for a cyber-terrorist to access their data.
Lastly, it would be to know what kind of systems they have set up to protect their data from
being lost or accessed without authority; a description should be done in detail.
To obtain ordinal data, a questionnaire can be given to the staff, and more importantly the
staff in charge of data recording and the IT sector. The questionnaire would be to assess, how
satisfied they are with the method of data recording, how satisfied they are with data
protection, how they feel about their treatment on a day to day basis, how satisfied they are
about access to said data and how well are the critical systems of the institution maintained
(Wetsman, 2019).

Risk Perception and Analysis
4. What Risk Factors do you believe should be used to allow this particular Risk to be
compared with other Risks of the same type? Identify them and briefly explain your
choice.
Factors that affect cybersecurity and link to other risks in the sector may be assessed through
factors like alarm fatigue which make those who are supposed to watch over the protection of
data unable to do their work effectively. Also, hospitals are places of healing, but at times
even the doctors are unable to save a life, the clients out of frustration may end up blaming
the devices in the hospital for the loss of life. The doctors should however not heavily rely on
their tools and technology to save a life, instinct over technology, doctors and nurses having
minimal training and only technologically competent (Coventry and Branley, 2018).
5. Propose both nominal and associated ordinal scales that would suite your chosen Risk
Factors given the situation in which the Risk exists.
A proposed nominal vote on the capability of doctors to run the hours on various shifts and
ensure the safety of the data in their servers; should ask whether the doctors and nurses are
overworked, it should also ask whether the shifts are viable for the number of patients and
services to maintain, a question should also be posted on the number of available breaks for
the staff. Keeping the staff happy and comfortable in their workspace, kills the possibility of
cyber-attack from an “inside man”, this increases the safety of the data centres and critical
systems (Vogenberg and Santili, 2018).
Ordinal data collection may be done depending on the satisfaction of the staff in their work
space, and also client satisfaction towards the institution. Clients who both faced patient loss
and those that did not should be asked; how satisfied they were with the services they
received, whether they had any problems in terms of service payment, there level of
satisfaction with the staff.
6. Having read the various papers provided on the subject of the Risk Matrix, discuss
the practical utility of the scales you have proposed. This discussion will need to
consider any possible ambiguities in the words used or their interpretation and your
views on the subjectivity of the decision a use will make in choosing a particular part of
a scale.
By collecting both nominal and ordinal data from both the staff and the clients a fair analysis
can be derived. This data will therefore eventually lead to the ultimate protection of client and
4. What Risk Factors do you believe should be used to allow this particular Risk to be
compared with other Risks of the same type? Identify them and briefly explain your
choice.
Factors that affect cybersecurity and link to other risks in the sector may be assessed through
factors like alarm fatigue which make those who are supposed to watch over the protection of
data unable to do their work effectively. Also, hospitals are places of healing, but at times
even the doctors are unable to save a life, the clients out of frustration may end up blaming
the devices in the hospital for the loss of life. The doctors should however not heavily rely on
their tools and technology to save a life, instinct over technology, doctors and nurses having
minimal training and only technologically competent (Coventry and Branley, 2018).
5. Propose both nominal and associated ordinal scales that would suite your chosen Risk
Factors given the situation in which the Risk exists.
A proposed nominal vote on the capability of doctors to run the hours on various shifts and
ensure the safety of the data in their servers; should ask whether the doctors and nurses are
overworked, it should also ask whether the shifts are viable for the number of patients and
services to maintain, a question should also be posted on the number of available breaks for
the staff. Keeping the staff happy and comfortable in their workspace, kills the possibility of
cyber-attack from an “inside man”, this increases the safety of the data centres and critical
systems (Vogenberg and Santili, 2018).
Ordinal data collection may be done depending on the satisfaction of the staff in their work
space, and also client satisfaction towards the institution. Clients who both faced patient loss
and those that did not should be asked; how satisfied they were with the services they
received, whether they had any problems in terms of service payment, there level of
satisfaction with the staff.
6. Having read the various papers provided on the subject of the Risk Matrix, discuss
the practical utility of the scales you have proposed. This discussion will need to
consider any possible ambiguities in the words used or their interpretation and your
views on the subjectivity of the decision a use will make in choosing a particular part of
a scale.
By collecting both nominal and ordinal data from both the staff and the clients a fair analysis
can be derived. This data will therefore eventually lead to the ultimate protection of client and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Risk Perception and Analysis
staff data and the overall satisfaction in terms of service delivery, although cybercriminals
tend to attack smaller institutions the medical sector is increasingly becoming an easy target
for the terrorists, this is done through the staff and also through the use of the internet
(Vogenberg and Santili, 2018).
This can although be brought to debate since words such as “satisfactory” cannot be
accurately measured, and the degree to which the data in question, is valid is also up for
debate. To clear such ambiguity the questionnaire should also provide a slot for additional
information and any questions posed.
Anonymity should also be key in the collection of this data this should be done to reassure
the target audience that each and everyone of them have their privacy intact, in my view the
collection of this data should be fool proof if the privacy and security of data collected is
maintained (Conaty-Buck, 2017).
staff data and the overall satisfaction in terms of service delivery, although cybercriminals
tend to attack smaller institutions the medical sector is increasingly becoming an easy target
for the terrorists, this is done through the staff and also through the use of the internet
(Vogenberg and Santili, 2018).
This can although be brought to debate since words such as “satisfactory” cannot be
accurately measured, and the degree to which the data in question, is valid is also up for
debate. To clear such ambiguity the questionnaire should also provide a slot for additional
information and any questions posed.
Anonymity should also be key in the collection of this data this should be done to reassure
the target audience that each and everyone of them have their privacy intact, in my view the
collection of this data should be fool proof if the privacy and security of data collected is
maintained (Conaty-Buck, 2017).
Risk Perception and Analysis
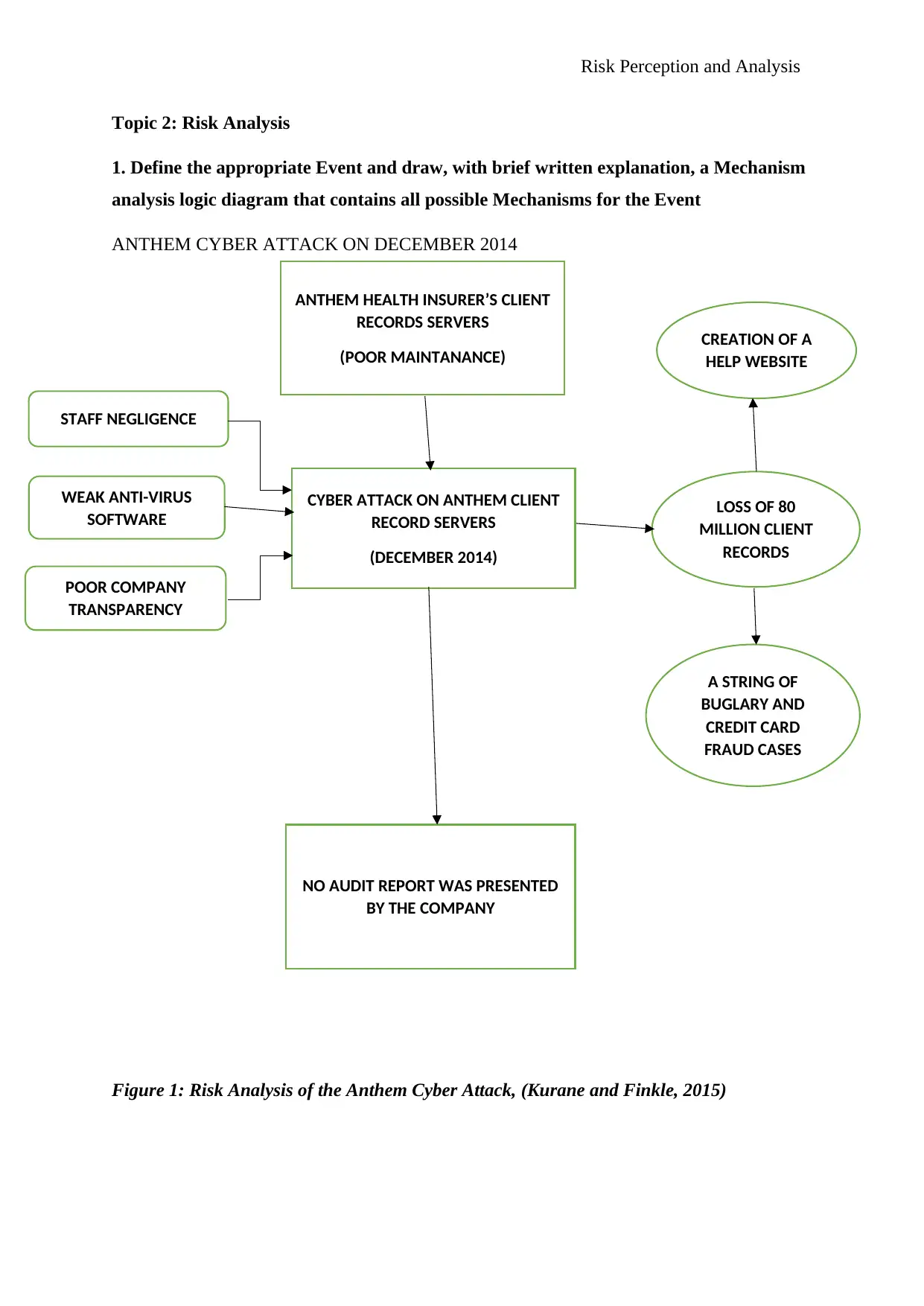
Topic 2: Risk Analysis
1. Define the appropriate Event and draw, with brief written explanation, a Mechanism
analysis logic diagram that contains all possible Mechanisms for the Event
ANTHEM CYBER ATTACK ON DECEMBER 2014
Figure 1: Risk Analysis of the Anthem Cyber Attack, (Kurane and Finkle, 2015)
ANTHEM HEALTH INSURER’S CLIENT
RECORDS SERVERS
(POOR MAINTANANCE)
CYBER ATTACK ON ANTHEM CLIENT
RECORD SERVERS
(DECEMBER 2014)
LOSS OF 80
MILLION CLIENT
RECORDS
A STRING OF
BUGLARY AND
CREDIT CARD
FRAUD CASES
STAFF NEGLIGENCE
WEAK ANTI-VIRUS
SOFTWARE
POOR COMPANY
TRANSPARENCY
NO AUDIT REPORT WAS PRESENTED
BY THE COMPANY
CREATION OF A
HELP WEBSITE
Topic 2: Risk Analysis
1. Define the appropriate Event and draw, with brief written explanation, a Mechanism
analysis logic diagram that contains all possible Mechanisms for the Event
ANTHEM CYBER ATTACK ON DECEMBER 2014
Figure 1: Risk Analysis of the Anthem Cyber Attack, (Kurane and Finkle, 2015)
ANTHEM HEALTH INSURER’S CLIENT
RECORDS SERVERS
(POOR MAINTANANCE)
CYBER ATTACK ON ANTHEM CLIENT
RECORD SERVERS
(DECEMBER 2014)
LOSS OF 80
MILLION CLIENT
RECORDS
A STRING OF
BUGLARY AND
CREDIT CARD
FRAUD CASES
STAFF NEGLIGENCE
WEAK ANTI-VIRUS
SOFTWARE
POOR COMPANY
TRANSPARENCY
NO AUDIT REPORT WAS PRESENTED
BY THE COMPANY
CREATION OF A
HELP WEBSITE

Risk Perception and Analysis
This is known to be one of the biggest cyber-attacks on a healthcare facility, 80 million
clients had their information disclosed including; names, dates of birth, social security
numbers, healthcare ID numbers, home addresses, email addresses, and employment
information, including income data. The company refused to give an audit report arguing
that, they would have to disable their anti-virus software which could lead to a new attack,
the company is although known for its lack of transparency and mistreatment of its staff at
the time (Kurane and Finkle, 2015).
This is known to be one of the biggest cyber-attacks on a healthcare facility, 80 million
clients had their information disclosed including; names, dates of birth, social security
numbers, healthcare ID numbers, home addresses, email addresses, and employment
information, including income data. The company refused to give an audit report arguing
that, they would have to disable their anti-virus software which could lead to a new attack,
the company is although known for its lack of transparency and mistreatment of its staff at
the time (Kurane and Finkle, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Risk Perception and Analysis
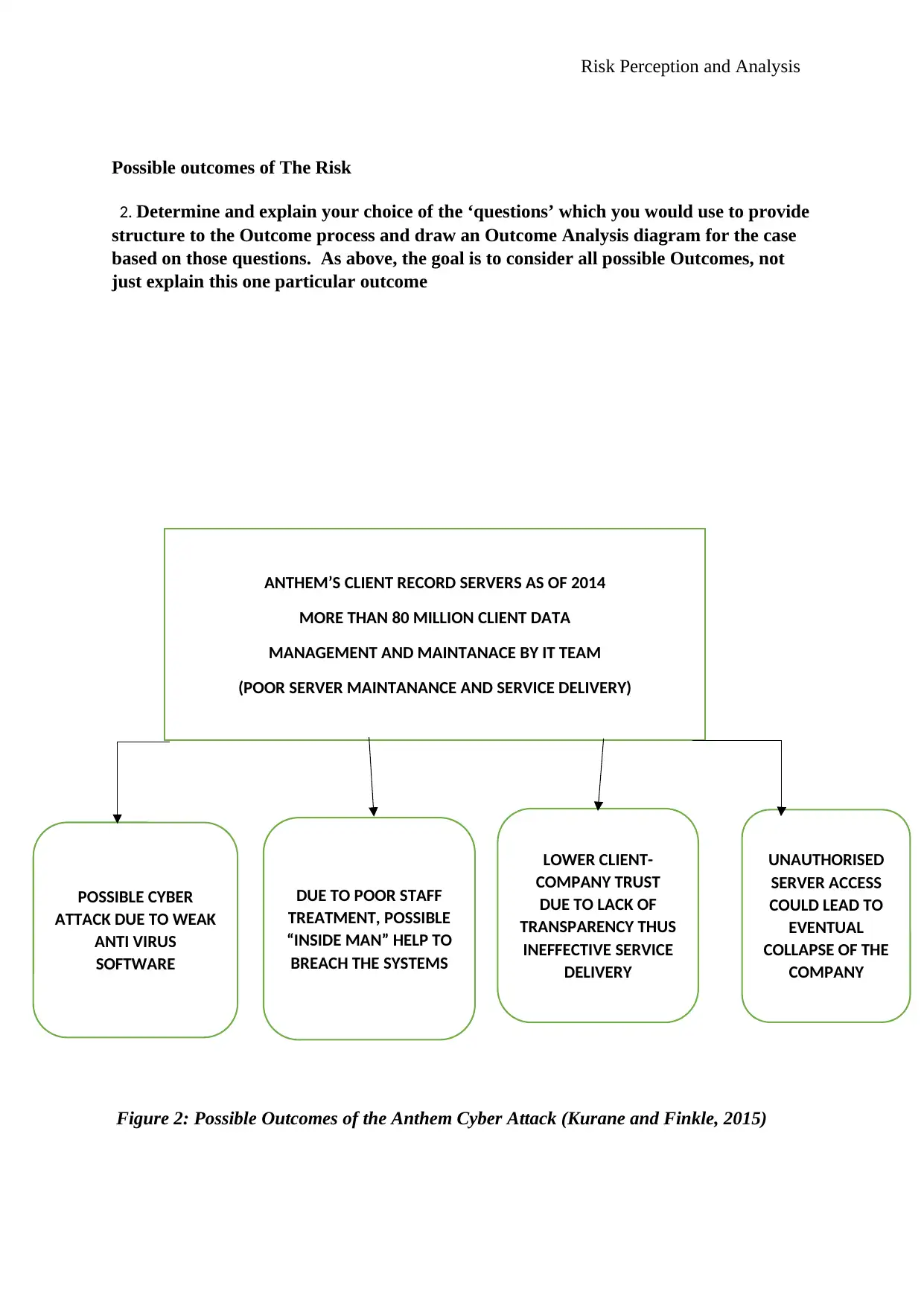
Possible outcomes of The Risk
2. Determine and explain your choice of the ‘questions’ which you would use to provide
structure to the Outcome process and draw an Outcome Analysis diagram for the case
based on those questions. As above, the goal is to consider all possible Outcomes, not
just explain this one particular outcome
Figure 2: Possible Outcomes of the Anthem Cyber Attack (Kurane and Finkle, 2015)
ANTHEM’S CLIENT RECORD SERVERS AS OF 2014
MORE THAN 80 MILLION CLIENT DATA
MANAGEMENT AND MAINTANACE BY IT TEAM
(POOR SERVER MAINTANANCE AND SERVICE DELIVERY)
POSSIBLE CYBER
ATTACK DUE TO WEAK
ANTI VIRUS
SOFTWARE
DUE TO POOR STAFF
TREATMENT, POSSIBLE
“INSIDE MAN” HELP TO
BREACH THE SYSTEMS
LOWER CLIENT-
COMPANY TRUST
DUE TO LACK OF
TRANSPARENCY THUS
INEFFECTIVE SERVICE
DELIVERY
UNAUTHORISED
SERVER ACCESS
COULD LEAD TO
EVENTUAL
COLLAPSE OF THE
COMPANY
Possible outcomes of The Risk
2. Determine and explain your choice of the ‘questions’ which you would use to provide
structure to the Outcome process and draw an Outcome Analysis diagram for the case
based on those questions. As above, the goal is to consider all possible Outcomes, not
just explain this one particular outcome
Figure 2: Possible Outcomes of the Anthem Cyber Attack (Kurane and Finkle, 2015)
ANTHEM’S CLIENT RECORD SERVERS AS OF 2014
MORE THAN 80 MILLION CLIENT DATA
MANAGEMENT AND MAINTANACE BY IT TEAM
(POOR SERVER MAINTANANCE AND SERVICE DELIVERY)
POSSIBLE CYBER
ATTACK DUE TO WEAK
ANTI VIRUS
SOFTWARE
DUE TO POOR STAFF
TREATMENT, POSSIBLE
“INSIDE MAN” HELP TO
BREACH THE SYSTEMS
LOWER CLIENT-
COMPANY TRUST
DUE TO LACK OF
TRANSPARENCY THUS
INEFFECTIVE SERVICE
DELIVERY
UNAUTHORISED
SERVER ACCESS
COULD LEAD TO
EVENTUAL
COLLAPSE OF THE
COMPANY

Risk Perception and Analysis
The standing question in this case, therefore, would be, what would poor server maintenance
and service delivery lead to?
For such a big company that heavily relies on digital records to keep track of their many
clients, it would pose a big threat, especially because, although they had most services many
of their clients wanted, very many people were skeptical about the company including their
employees. This is due to the lack of transparency and the connection between the company
and the politicians at the time. The company felt untouchable because of the monopoly they
posed in the sector with support from major political figures, the company thus neglected
most of is most prime facilities and therefore left itself open to cyber-attacks. It would be
easy picking for the terrorists due to the outdated anti-virus software they used and the
negligence by the staff (Kurane and Finkle, 2015)
The entire hack could have been prevented as the possibility of a hack was very high, this
could have been avoided if the regular system maintenance programs would have continually
been done (the company halted the process by not funding it), the corruption within the
company lead to its ultimate loophole, the senior company officials neglected their staff
leading to the slow degeneration of their services. The attack could have been as a means of
revenge by a staff member to show dissatisfaction, or a client due to the poor service delivery
to their midrange income to low-income clients (Olcott, 2016).
Topic 3
Cyber terrorism is still a relatively new threat in comparison to other risks faced in the
various fields, but with the ever-changing world, it is increasingly becoming a threat due to
reliance on the internet and the efficiency given devices bring.
Technology has in various ways brought positive change not only to the healthcare centre but
to the economy and social sectors at large, much like any other new field it faces its
challenges. In the healthcare sector the major problem has been the security of patient data,
there have been numerous reports ever since 2014 when the United States decided to turn to
digital data entry in their healthcare facilities, the general greed for money has driven some
while others cyber-attacks have been fuelled by industrial espionage.
The intention behind this cyber hacking can only be presumed to be money. These hackers
get access to patient records and in turn, sell them to some bidders. However, in recent times
The standing question in this case, therefore, would be, what would poor server maintenance
and service delivery lead to?
For such a big company that heavily relies on digital records to keep track of their many
clients, it would pose a big threat, especially because, although they had most services many
of their clients wanted, very many people were skeptical about the company including their
employees. This is due to the lack of transparency and the connection between the company
and the politicians at the time. The company felt untouchable because of the monopoly they
posed in the sector with support from major political figures, the company thus neglected
most of is most prime facilities and therefore left itself open to cyber-attacks. It would be
easy picking for the terrorists due to the outdated anti-virus software they used and the
negligence by the staff (Kurane and Finkle, 2015)
The entire hack could have been prevented as the possibility of a hack was very high, this
could have been avoided if the regular system maintenance programs would have continually
been done (the company halted the process by not funding it), the corruption within the
company lead to its ultimate loophole, the senior company officials neglected their staff
leading to the slow degeneration of their services. The attack could have been as a means of
revenge by a staff member to show dissatisfaction, or a client due to the poor service delivery
to their midrange income to low-income clients (Olcott, 2016).
Topic 3
Cyber terrorism is still a relatively new threat in comparison to other risks faced in the
various fields, but with the ever-changing world, it is increasingly becoming a threat due to
reliance on the internet and the efficiency given devices bring.
Technology has in various ways brought positive change not only to the healthcare centre but
to the economy and social sectors at large, much like any other new field it faces its
challenges. In the healthcare sector the major problem has been the security of patient data,
there have been numerous reports ever since 2014 when the United States decided to turn to
digital data entry in their healthcare facilities, the general greed for money has driven some
while others cyber-attacks have been fuelled by industrial espionage.
The intention behind this cyber hacking can only be presumed to be money. These hackers
get access to patient records and in turn, sell them to some bidders. However, in recent times

Risk Perception and Analysis
hackers have developed a habit of asking for ransom from the health centres in order to
release the information. Such an atrocity is sure to have devastating effects on the victims,
and in this case, it's the healthcare centres. This is because it will attract hundreds of lawsuits
from the patients, which evidently means the patient trust will be lost along with any credible
reputation. When we talk about patient records we don’t mean records on their illnesses only,
but also records on monetary transfers that might have secret information on the patients
(Vogenberg and Santili, 2018).
The problems facing cybersecurity can, however, be prevented, most of them are foreseeable
since most of the cyber terrorists have very minimal ways to gain access; they require to
collect patient data. Therefore, a team with a precise understanding of how the IT sector
works and what should be done to ensure the safety of their data and servers should be
formulated to provide that their data is only accessible by a handful of people, in the event of
a breach they will be brought to question, this improves on accountability. The managing IT
team are also human though so occasional rest and proper treatment and pay would work well
to ensure their loyalty and thus reduce the risk of inside help to bring down the company. Due
to the rapid progress of technology and introduction of critical technological advancements in
hospitals like the MRI, all the data recorded is streamed into a hospital database making all
the hospital records vulnerable in case of a cyber-attack. Hence the IT team can work to
strengthen the systems, closing any loopholes or unnecessary glitches in the system (Hartwig,
and Wilkinson 2014).
On the more positive side, healthcare, unlike other economic sectors, does not have a high
competition because the end goal is to save lives; therefore the risk of a planned attack by a
different healthcare facility is shallow. This further lessens the risk of cyber-attacks, this
although should not be taken as an excuse not to maintain their digital facilities (Kruse
Frederick, Jacobson, and Monticone, 2016). A company called Premera in March 2015 was
the victim of a cyber-attack because for an entire month they had not effectively maintained
their data servers, a lot of data was initially lost while the rest was hacked and disclosed to
the public. This also has an effect on the surrounding community, since more health centres
will be presumed to be vulnerable hence welcoming an eruption of cyber-attacks (Olcott,
2016).
In third world countries, cybersecurity might not be as big of a threat as it is in much more
developed countries, this is due to the more straight forward and traditional method of service
hackers have developed a habit of asking for ransom from the health centres in order to
release the information. Such an atrocity is sure to have devastating effects on the victims,
and in this case, it's the healthcare centres. This is because it will attract hundreds of lawsuits
from the patients, which evidently means the patient trust will be lost along with any credible
reputation. When we talk about patient records we don’t mean records on their illnesses only,
but also records on monetary transfers that might have secret information on the patients
(Vogenberg and Santili, 2018).
The problems facing cybersecurity can, however, be prevented, most of them are foreseeable
since most of the cyber terrorists have very minimal ways to gain access; they require to
collect patient data. Therefore, a team with a precise understanding of how the IT sector
works and what should be done to ensure the safety of their data and servers should be
formulated to provide that their data is only accessible by a handful of people, in the event of
a breach they will be brought to question, this improves on accountability. The managing IT
team are also human though so occasional rest and proper treatment and pay would work well
to ensure their loyalty and thus reduce the risk of inside help to bring down the company. Due
to the rapid progress of technology and introduction of critical technological advancements in
hospitals like the MRI, all the data recorded is streamed into a hospital database making all
the hospital records vulnerable in case of a cyber-attack. Hence the IT team can work to
strengthen the systems, closing any loopholes or unnecessary glitches in the system (Hartwig,
and Wilkinson 2014).
On the more positive side, healthcare, unlike other economic sectors, does not have a high
competition because the end goal is to save lives; therefore the risk of a planned attack by a
different healthcare facility is shallow. This further lessens the risk of cyber-attacks, this
although should not be taken as an excuse not to maintain their digital facilities (Kruse
Frederick, Jacobson, and Monticone, 2016). A company called Premera in March 2015 was
the victim of a cyber-attack because for an entire month they had not effectively maintained
their data servers, a lot of data was initially lost while the rest was hacked and disclosed to
the public. This also has an effect on the surrounding community, since more health centres
will be presumed to be vulnerable hence welcoming an eruption of cyber-attacks (Olcott,
2016).
In third world countries, cybersecurity might not be as big of a threat as it is in much more
developed countries, this is due to the more straight forward and traditional method of service
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Risk Perception and Analysis
delivery done by their healthcare facilities. Although this might change soon due to the rising
number of patients, it would be tedious to save their records on written book files and sorted
in a storeroom. This accompanied by the technological wave will require most health
facilities to shift to a more efficient way of storing data. The change will come soon and
education on the dangers posed by cybersecurity should be done prior. (Jalali, Razak,
Gordon, Perakslis, and Madnick, 2019).
My reasoning behind picking this as a risk to educate on is because of the ignorance posed by
most institutions towards the level of threat is poses, none of the recorded attacks are minor,
they all lead to major data loss and vulnerability on the clients side, facilities such as Mass
General Hospital in 2016 faced so many lawsuits due to a data breach on 4300 of their
patients, the institution almost closed down. Staff education should also be done to ensure
every staff member is competent enough not to bring ransomware or malware into the
institution's systems through the available devices, proper education should be done before
the establishment of said systems and a regular test should be done to make sure they do not
forget. With the ever-increasing demand for such records on the black market, the risk grows
by the day, the records are primarily used to create fake IDs for underage teenagers or fake
passports for illegal immigrants, on a larger scale they may be used for burglary, as ransom,
leaked to tarnish a person’s name or even to access their credit cards and steal money
(Conaty-Buck, 2017).
In summary, every health institution should be aware of cyber-attacks as a risk to their
service delivery, installation of such systems should be done in a secure way and client
feedback on service delivery should also be considered and their consent taken. Staff should
also be well taken care of and effective security and service delivery will inevitably follow
suit. This is to prevent any rogue staff members who might facilitate the hacking.
delivery done by their healthcare facilities. Although this might change soon due to the rising
number of patients, it would be tedious to save their records on written book files and sorted
in a storeroom. This accompanied by the technological wave will require most health
facilities to shift to a more efficient way of storing data. The change will come soon and
education on the dangers posed by cybersecurity should be done prior. (Jalali, Razak,
Gordon, Perakslis, and Madnick, 2019).
My reasoning behind picking this as a risk to educate on is because of the ignorance posed by
most institutions towards the level of threat is poses, none of the recorded attacks are minor,
they all lead to major data loss and vulnerability on the clients side, facilities such as Mass
General Hospital in 2016 faced so many lawsuits due to a data breach on 4300 of their
patients, the institution almost closed down. Staff education should also be done to ensure
every staff member is competent enough not to bring ransomware or malware into the
institution's systems through the available devices, proper education should be done before
the establishment of said systems and a regular test should be done to make sure they do not
forget. With the ever-increasing demand for such records on the black market, the risk grows
by the day, the records are primarily used to create fake IDs for underage teenagers or fake
passports for illegal immigrants, on a larger scale they may be used for burglary, as ransom,
leaked to tarnish a person’s name or even to access their credit cards and steal money
(Conaty-Buck, 2017).
In summary, every health institution should be aware of cyber-attacks as a risk to their
service delivery, installation of such systems should be done in a secure way and client
feedback on service delivery should also be considered and their consent taken. Staff should
also be well taken care of and effective security and service delivery will inevitably follow
suit. This is to prevent any rogue staff members who might facilitate the hacking.

Risk Perception and Analysis
References
Argaw, S.T., Bempong, N.E., Eshaya-Chauvin, B. and Flahault, A., 2019. The state of
research on cyberattacks against hospitals and available best practice recommendations: a
scoping review. BMC medical informatics and decision making, 19(1), p.10.
https://doi.org/10.1186/s12911-018-0724-5
Conaty-Buck, S. (2017).Cybersecurity and healthcare records. American Nurse Today, 12(9),
pp.61-65. Available at:
https://www.americannursetoday.com/wp-content/uploads/2017/09/ant9-Focus-0n-
Cybersecurity-824a.pdf (Assessed 12th May, 2019).
Coventry, L. and Branley, D., 2018. Cybersecurity in healthcare: A narrative review of
trends, threats and ways forward. Maturitas, 113, pp.48-52.
https://doi.org/10.1016/j.maturitas.2018.04.008
Jalali, M.S., Razak, S., Gordon, W., Perakslis, E. and Madnick, S., 2019. Health Care and
Cybersecurity: Bibliometric Analysis of the Literature. Journal of medical Internet
research, 21(2), p.e12644. doi:10.2196/12644
Kruse, C.S., Frederick, B., Jacobson, T. and Monticone, D.K., 2017. Cybersecurity in
healthcare: A systematic review of modern threats and trends. Technology and Health
Care, 25(1), pp.1-10. doi: 10.3233/THC-161263
Kurane, S, Finkle, J. (2015).Health Insurer Anthem Hit with Cyber Attack. Insurance
Journal. Available at:
https://www.insurancejournal.com/news/national/2015/02/05/356649.htm (Assessed 12th
May, 2019).
Olcott, J. (2016). Security Breaches In Healthcare: How These 7 Recent Cases Happened.
[Online] BitSight. Available at: https://www.bitsight.com/blog/security-breaches-healthcare
[Accessed 14 May 2019].
Infosec Resources. (2019). Top Cyber Security Risks in Healthcare. [Online] Available at:
https://resources.infosecinstitute.com/category/healthcare-information-security/healthcare-
cyber-threat-landscape/top-cyber-security-risks-in-healthcare/#gref [Accessed 14 May 2019].
References
Argaw, S.T., Bempong, N.E., Eshaya-Chauvin, B. and Flahault, A., 2019. The state of
research on cyberattacks against hospitals and available best practice recommendations: a
scoping review. BMC medical informatics and decision making, 19(1), p.10.
https://doi.org/10.1186/s12911-018-0724-5
Conaty-Buck, S. (2017).Cybersecurity and healthcare records. American Nurse Today, 12(9),
pp.61-65. Available at:
https://www.americannursetoday.com/wp-content/uploads/2017/09/ant9-Focus-0n-
Cybersecurity-824a.pdf (Assessed 12th May, 2019).
Coventry, L. and Branley, D., 2018. Cybersecurity in healthcare: A narrative review of
trends, threats and ways forward. Maturitas, 113, pp.48-52.
https://doi.org/10.1016/j.maturitas.2018.04.008
Jalali, M.S., Razak, S., Gordon, W., Perakslis, E. and Madnick, S., 2019. Health Care and
Cybersecurity: Bibliometric Analysis of the Literature. Journal of medical Internet
research, 21(2), p.e12644. doi:10.2196/12644
Kruse, C.S., Frederick, B., Jacobson, T. and Monticone, D.K., 2017. Cybersecurity in
healthcare: A systematic review of modern threats and trends. Technology and Health
Care, 25(1), pp.1-10. doi: 10.3233/THC-161263
Kurane, S, Finkle, J. (2015).Health Insurer Anthem Hit with Cyber Attack. Insurance
Journal. Available at:
https://www.insurancejournal.com/news/national/2015/02/05/356649.htm (Assessed 12th
May, 2019).
Olcott, J. (2016). Security Breaches In Healthcare: How These 7 Recent Cases Happened.
[Online] BitSight. Available at: https://www.bitsight.com/blog/security-breaches-healthcare
[Accessed 14 May 2019].
Infosec Resources. (2019). Top Cyber Security Risks in Healthcare. [Online] Available at:
https://resources.infosecinstitute.com/category/healthcare-information-security/healthcare-
cyber-threat-landscape/top-cyber-security-risks-in-healthcare/#gref [Accessed 14 May 2019].

Risk Perception and Analysis
Vogenberg, F.R. and Santilli, J., 2018. Healthcare trends for 2018. American health & drug
benefits, 11(1), p.48. Available at: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5902765/
Accessed 11th May, 2019).
Wetsman, N. (2019). Health Care`s Huge Cybersecurity Problem. The Verge. Available at:
https://www.theverge.com/2019/4/4/18293817/cybersecurity-hosptals-health-care-scan-
stimulation (Accessed 11th May, 2019).
Hartwig, R.P. and Wilkinson, C., 2014. Cyber risks: The growing threat. Insurance
information institute, pp.1-27. Available at:
https://www.iii.org/sites/default/files/docs/pdf/paper_cyberrisk_2014.pdf (Accessed 11th
May, 2019).
Vogenberg, F.R. and Santilli, J., 2018. Healthcare trends for 2018. American health & drug
benefits, 11(1), p.48. Available at: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5902765/
Accessed 11th May, 2019).
Wetsman, N. (2019). Health Care`s Huge Cybersecurity Problem. The Verge. Available at:
https://www.theverge.com/2019/4/4/18293817/cybersecurity-hosptals-health-care-scan-
stimulation (Accessed 11th May, 2019).
Hartwig, R.P. and Wilkinson, C., 2014. Cyber risks: The growing threat. Insurance
information institute, pp.1-27. Available at:
https://www.iii.org/sites/default/files/docs/pdf/paper_cyberrisk_2014.pdf (Accessed 11th
May, 2019).
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.

